The goal of this chapter is to introduce the Cisco Unified Wireless Network (UWN) architecture and to discuss wireless design principles. The chapter starts with an introduction to wireless technologies. Then the Cisco UWN is described. The chapter concludes with an exploration of considerations for designing Cisco UWNs in enterprise environments.
 Introduction to Wireless Technology
Introduction to Wireless Technology
![]() This section includes some material form the Cisco Press title Building Cisco Multilayer Switched Networks (BCMSN) (Authorized Self-Study Guide), 4th Edition, ISBN 1-58705-273-3, as an introduction to wireless technology.
This section includes some material form the Cisco Press title Building Cisco Multilayer Switched Networks (BCMSN) (Authorized Self-Study Guide), 4th Edition, ISBN 1-58705-273-3, as an introduction to wireless technology.
![]() A wireless communication system uses radio frequency (RF) energy to transmit data from one point to another, through the air; the term signal is used to refer to this RF energy. The data to be transmitted is first modulated onto a carrier and then sent; receivers demodulate the signal and process the data.
A wireless communication system uses radio frequency (RF) energy to transmit data from one point to another, through the air; the term signal is used to refer to this RF energy. The data to be transmitted is first modulated onto a carrier and then sent; receivers demodulate the signal and process the data.
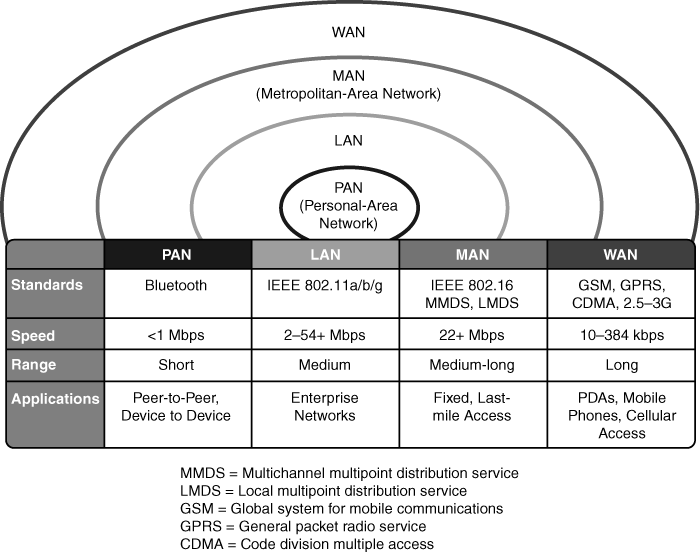
![]() There are many different types of wireless network technologies, each providing a defined coverage area. Figure 9-1 illustrates the following wireless technologies, along with a description of how the coverage areas are used:
There are many different types of wireless network technologies, each providing a defined coverage area. Figure 9-1 illustrates the following wireless technologies, along with a description of how the coverage areas are used:
-
 Personal-area network (PAN): A PAN typically covers a person’s personal workspace.
Personal-area network (PAN): A PAN typically covers a person’s personal workspace. -
 Local-area network: Wireless LANs (WLAN) are designed to be enterprise-based networks that allow the use of complete suites of enterprise applications, without wires.
Local-area network: Wireless LANs (WLAN) are designed to be enterprise-based networks that allow the use of complete suites of enterprise applications, without wires. -
 Metropolitan-area network (MAN): Wireless MANs are deployed inside a metropolitan area, allowing wireless connectivity throughout an urban area.
Metropolitan-area network (MAN): Wireless MANs are deployed inside a metropolitan area, allowing wireless connectivity throughout an urban area. -
 Wide-area network: Wireless WANs are typically slower but offer more coverage, such as across rural areas.
Wide-area network: Wireless WANs are typically slower but offer more coverage, such as across rural areas.
![]() WLANs replace the Layer 1 transmission medium of a traditional wired network (usually Category 5 cable) with radio transmission over the air. WLANs can plug into a wired network and function as an overlay to wired LANs, or they can be deployed as a standalone LAN where wired networking is not feasible. A computer with a wireless network interface card (NIC) connects to the wired LAN through an access point (AP). Properly deployed WLANs can provide instant access to the network from anywhere in a facility so that users can roam without losing their network connection.
WLANs replace the Layer 1 transmission medium of a traditional wired network (usually Category 5 cable) with radio transmission over the air. WLANs can plug into a wired network and function as an overlay to wired LANs, or they can be deployed as a standalone LAN where wired networking is not feasible. A computer with a wireless network interface card (NIC) connects to the wired LAN through an access point (AP). Properly deployed WLANs can provide instant access to the network from anywhere in a facility so that users can roam without losing their network connection.
![]() WLANs use spread-spectrum RF signals on the three unlicensed bands: 900 MHz, 2.4 GHz, and 5 GHz. The 900 MHz and 2.4 GHz bands are referred to as the industrial, scientific, and medical bands, and the 5 GHz band is commonly referred to as the Unlicensed National Information Infrastructure (UNII) band.
WLANs use spread-spectrum RF signals on the three unlicensed bands: 900 MHz, 2.4 GHz, and 5 GHz. The 900 MHz and 2.4 GHz bands are referred to as the industrial, scientific, and medical bands, and the 5 GHz band is commonly referred to as the Unlicensed National Information Infrastructure (UNII) band.
 RF Theory
RF Theory
![]() Radio frequencies are high-frequency AC signals radiated into the air via an antenna, creating radio waves. Radio waves propagate away from the antenna in a straight line in all directions at once, just as light from a light bulb does. And, just as more light bulbs spread around a room provide better overall lighting, more antennas spread around a room provide stronger RF signals for mobile clients.
Radio frequencies are high-frequency AC signals radiated into the air via an antenna, creating radio waves. Radio waves propagate away from the antenna in a straight line in all directions at once, just as light from a light bulb does. And, just as more light bulbs spread around a room provide better overall lighting, more antennas spread around a room provide stronger RF signals for mobile clients.
Phenomena Affecting RF
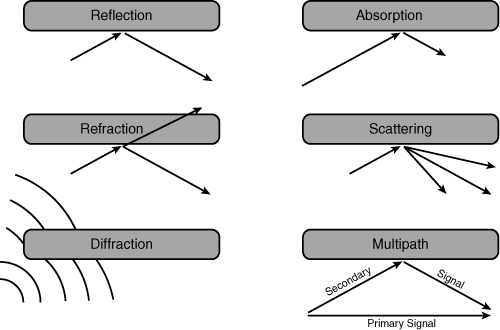
![]() When radio waves hit a wall, door, or any other obstruction, the signal is attenuated, or weakened, which might result in reduced throughput. The following natural phenomena affect RF signals, as illustrated in Figure 9-2:
When radio waves hit a wall, door, or any other obstruction, the signal is attenuated, or weakened, which might result in reduced throughput. The following natural phenomena affect RF signals, as illustrated in Figure 9-2:
-
 Reflection: Occurs when the RF signal bounces off objects such as metal or glass surfaces.
Reflection: Occurs when the RF signal bounces off objects such as metal or glass surfaces. -
 Refraction: Occurs when the RF signal passes through objects such as glass surfaces and changes direction.
Refraction: Occurs when the RF signal passes through objects such as glass surfaces and changes direction. -
 Absorption: Occurs when an object, such as a wall or furniture, absorbs the RF signal.
Absorption: Occurs when an object, such as a wall or furniture, absorbs the RF signal. -
 Scattering: Occurs when an RF wave strikes an uneven surface and reflects in many directions. Scattering also occurs when an RF wave travels through a medium that consists of objects that are much smaller than the signal’s wavelength, such as heavy dust.
Scattering: Occurs when an RF wave strikes an uneven surface and reflects in many directions. Scattering also occurs when an RF wave travels through a medium that consists of objects that are much smaller than the signal’s wavelength, such as heavy dust. -
 Diffraction: Occurs when an RF wave strikes sharp edges, such as external corners of buildings, which bend the signal.
Diffraction: Occurs when an RF wave strikes sharp edges, such as external corners of buildings, which bend the signal. -
 Multipath: Occurs when an RF signal has more than one path between the sender and receiver. The multiple signals at the receiver might result in a distorted, low-quality signal.
Multipath: Occurs when an RF signal has more than one path between the sender and receiver. The multiple signals at the receiver might result in a distorted, low-quality signal.
![]() Consider all these phenomena when designing, implementing, and troubleshooting WLANs.
Consider all these phenomena when designing, implementing, and troubleshooting WLANs.
RF Math
![]() WLANs transmit signals just as radio stations do to reach their listeners. The transmit power levels for WLANs are in milliwatts (mW), whereas for radio stations the power levels are in megawatts (MW).
WLANs transmit signals just as radio stations do to reach their listeners. The transmit power levels for WLANs are in milliwatts (mW), whereas for radio stations the power levels are in megawatts (MW).
![]() The following are some units of measure used in RF calculations:
The following are some units of measure used in RF calculations:
-
 Decibel (dB): The difference or ratio between two signal levels. dBs are used to measure relative gains or losses in an RF system and to describe the effect of system devices on signal strength. The dB is named after Alexander Graham Bell.
Decibel (dB): The difference or ratio between two signal levels. dBs are used to measure relative gains or losses in an RF system and to describe the effect of system devices on signal strength. The dB is named after Alexander Graham Bell. -
 dB milliwatt (dBm): A signal strength or power level. Zero dBm is defined as 1 mW of power into a terminating load such as an antenna or power meter. Small signals, those below 1 mW, are therefore negative numbers (such as −80 dBm); WLAN signals are in the range of −60 dBm to −80 dBm.
dB milliwatt (dBm): A signal strength or power level. Zero dBm is defined as 1 mW of power into a terminating load such as an antenna or power meter. Small signals, those below 1 mW, are therefore negative numbers (such as −80 dBm); WLAN signals are in the range of −60 dBm to −80 dBm. -
 dB watt (dBw): A signal strength or power level. Zero dBw is defined as 1 watt (W) of power; 1 W is one ampere (A) of current at 1 volt (V).
dB watt (dBw): A signal strength or power level. Zero dBw is defined as 1 watt (W) of power; 1 W is one ampere (A) of current at 1 volt (V). -
 dB isotropic (dBi): The gain a given antenna has over a theoretical isotropic (point source) antenna. Unfortunately, an isotropic antenna cannot be made in the real world, but it is useful for calculating theoretical system operating margins.
dB isotropic (dBi): The gain a given antenna has over a theoretical isotropic (point source) antenna. Unfortunately, an isotropic antenna cannot be made in the real world, but it is useful for calculating theoretical system operating margins.
![]() The formula used for calculating losses, gains, and power for WLANs is too complex for most people to solve without a calculator. Gains or losses in decibels are summed and then converted into an absolute power in milliwatts or watts.
The formula used for calculating losses, gains, and power for WLANs is too complex for most people to solve without a calculator. Gains or losses in decibels are summed and then converted into an absolute power in milliwatts or watts.
![]() The following formula calculates the transmit power:
The following formula calculates the transmit power:
|
|
![]() Table 9-1 indicates how various gains and losses relate to power levels; it is useful for WLAN calculations.
Table 9-1 indicates how various gains and losses relate to power levels; it is useful for WLAN calculations.
|
|
|
|
| |
|---|---|---|---|---|
|
|
|
|
| |
|
|
|
|
| |
|
|
|
|
| |
|
|
|
|
| |
|
|
|
|
| |
|
|
|
|
|
![]() Notice in Table 9-1 that RF math is easier when the following key points are considered:
Notice in Table 9-1 that RF math is easier when the following key points are considered:
-
 Every gain of 3 dBm means that the power is doubled. A loss of 3 dBm means that the power is cut in half.
Every gain of 3 dBm means that the power is doubled. A loss of 3 dBm means that the power is cut in half. -
 A gain of 10 dBm means that the power increases by a factor of 10. A loss of 10 dBm means that the power decreases by a factor of 10.
A gain of 10 dBm means that the power increases by a factor of 10. A loss of 10 dBm means that the power decreases by a factor of 10.
![]() To calculate the power increase or decrease for a given dBm, factor the given number into a sum of 3dBm and 10dBm, and then convert using these rules. For example, a 9 dBm loss is equivalent to −3dBm + −3dBm + −3dBm. The following illustrates how to calculate the power level that a 200 mW signal decreases to when it experiences a 9 dBm loss.
To calculate the power increase or decrease for a given dBm, factor the given number into a sum of 3dBm and 10dBm, and then convert using these rules. For example, a 9 dBm loss is equivalent to −3dBm + −3dBm + −3dBm. The following illustrates how to calculate the power level that a 200 mW signal decreases to when it experiences a 9 dBm loss.
![]() Therefore, the 200 mW signal decreases to 25 mW with a 9dBm loss.
Therefore, the 200 mW signal decreases to 25 mW with a 9dBm loss.
Antennas
![]() Antennas used in WLANs come in many shapes and sizes, depending on the differing RF characteristics desired. The physical dimensions of an antenna directly relate to the frequency at which the antenna transmits or receives radio waves. As the gain increases, the coverage area becomes more focused. High-gain antennas provide longer coverage areas than low-gain antennas at the same input power level. As frequency increases, the wavelength and the antennas become smaller. Antennas can be categorized into one of the three following types:
Antennas used in WLANs come in many shapes and sizes, depending on the differing RF characteristics desired. The physical dimensions of an antenna directly relate to the frequency at which the antenna transmits or receives radio waves. As the gain increases, the coverage area becomes more focused. High-gain antennas provide longer coverage areas than low-gain antennas at the same input power level. As frequency increases, the wavelength and the antennas become smaller. Antennas can be categorized into one of the three following types:
-
 Omnidirectional: These antennas are the most widely used today but are not always the best solution. The radiant energy is shaped like a doughnut; consequently, the transmit signal is weak or absent directly under the AP (in the “hole” of the doughnut).
Omnidirectional: These antennas are the most widely used today but are not always the best solution. The radiant energy is shaped like a doughnut; consequently, the transmit signal is weak or absent directly under the AP (in the “hole” of the doughnut). -
 Semidirectional: These antennas offer the capability to direct and apply gain to the signal. The radiant energy is in a cowbell shape.
Semidirectional: These antennas offer the capability to direct and apply gain to the signal. The radiant energy is in a cowbell shape. -
 Highly directional: These antennas are intended for highly directed signals that must travel a long distance. The radiant energy is in a telescope shape.
Highly directional: These antennas are intended for highly directed signals that must travel a long distance. The radiant energy is in a telescope shape.
 Agencies and Standards Groups
Agencies and Standards Groups
![]() Some of the agencies and standards groups related to WLANs are as follows:
Some of the agencies and standards groups related to WLANs are as follows:
-
 Institute of Electrical and Electronic Engineers (http://www.ieee.org/): Creates and maintains operational standards.
Institute of Electrical and Electronic Engineers (http://www.ieee.org/): Creates and maintains operational standards. -
 European Telecommunications Standards Institute (http://www.etsi.org/): Chartered to produce common standards in Europe.
European Telecommunications Standards Institute (http://www.etsi.org/): Chartered to produce common standards in Europe. -
 Wi-Fi Alliance (http://www.wi-fi.com/): Promotes and tests for WLAN interoperability.
Wi-Fi Alliance (http://www.wi-fi.com/): Promotes and tests for WLAN interoperability. -
 WLAN Association (http://www.wlana.org/): Educates and raises consumer awareness about WLANs.
WLAN Association (http://www.wlana.org/): Educates and raises consumer awareness about WLANs. -
 FCC (http://www.fcc.gov/): Regulates United States interstate and international communications by radio, television, wire, satellite, and cable.
FCC (http://www.fcc.gov/): Regulates United States interstate and international communications by radio, television, wire, satellite, and cable. -
 Canadian Radio-Television and Telecommunications Commission (http://www.crtc.gc.ca/): Regulates Canada’s broadcasting and telecommunications systems.
Canadian Radio-Television and Telecommunications Commission (http://www.crtc.gc.ca/): Regulates Canada’s broadcasting and telecommunications systems.
 IEEE 802.11 Operational Standards
IEEE 802.11 Operational Standards
![]() In September 1999 the IEEE ratified the IEEE 802.11a standard (5 GHz at 54 Mbps) and the IEEE 802.11b standard (2.4 GHz at 11 Mbps). In June 2003, the IEEE ratified the 802.11g standard (2.4 GHz at 54 Mbps); this standard is backward-compatible with 802.11b systems, because both use the same 2.4-GHz bandwidth. The following are the existing IEEE 802.11 standards for wireless communication:
In September 1999 the IEEE ratified the IEEE 802.11a standard (5 GHz at 54 Mbps) and the IEEE 802.11b standard (2.4 GHz at 11 Mbps). In June 2003, the IEEE ratified the 802.11g standard (2.4 GHz at 54 Mbps); this standard is backward-compatible with 802.11b systems, because both use the same 2.4-GHz bandwidth. The following are the existing IEEE 802.11 standards for wireless communication:
-
 802.11a: 54 Mbps at 5 GHz, ratified in 1999
802.11a: 54 Mbps at 5 GHz, ratified in 1999 -
 802.11b: 11 Mbps 2.4 GHz, ratified in 1999
802.11b: 11 Mbps 2.4 GHz, ratified in 1999 -
 802.11d: World mode, ratified in 2001
802.11d: World mode, ratified in 2001 -
 802.11e: Quality of service, ratified in 2005
802.11e: Quality of service, ratified in 2005 -
 802.11F: Inter-Access Point Protocol, withdrawn in 2006
802.11F: Inter-Access Point Protocol, withdrawn in 2006 -
 802.11g: 54 Mbps at 2.4 GHz, higher data rate than 802.11b, ratified in 2003
802.11g: 54 Mbps at 2.4 GHz, higher data rate than 802.11b, ratified in 2003 -
 802.11h: Dynamic frequency selection and transmit power control mechanisms, ratified in 2003
802.11h: Dynamic frequency selection and transmit power control mechanisms, ratified in 2003 -
 802.11i: Authentication and security, ratified in 2005
802.11i: Authentication and security, ratified in 2005 -
 802.11j: Additional Japanese frequencies, ratified in 2005
802.11j: Additional Japanese frequencies, ratified in 2005 -
 802.11k: Radio resource management draft, planned to be ratified in 2007
802.11k: Radio resource management draft, planned to be ratified in 2007 -
 802.11n: High-throughput draft, planned to be ratified in 2007
802.11n: High-throughput draft, planned to be ratified in 2007
IEEE 802.11b/g Standards in the 2.4 GHz Band
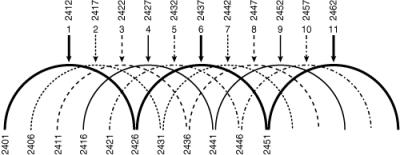
![]() The 2.4 GHz band used for 802.11b/g has multiple channels, each 22 MHz wide. In North America, 11 channels are defined, as illustrated in Figure 9-3. The top of the figure shows the channel’s center frequency (which is the frequency by which the channel is known); the lower numbers show the channel’s starting frequency. In North America, the 2.4 GHz band has three nonoverlapping channels: channels 1, 6, and 11.
The 2.4 GHz band used for 802.11b/g has multiple channels, each 22 MHz wide. In North America, 11 channels are defined, as illustrated in Figure 9-3. The top of the figure shows the channel’s center frequency (which is the frequency by which the channel is known); the lower numbers show the channel’s starting frequency. In North America, the 2.4 GHz band has three nonoverlapping channels: channels 1, 6, and 11.
![]() Careful channel placement eliminates overlapping cells on the same channel so that aggregate WLAN throughput is maximized. This concept is similar to the placement of FM radio stations throughout the country; two radio stations in the same geographic area are never on the same channel.
Careful channel placement eliminates overlapping cells on the same channel so that aggregate WLAN throughput is maximized. This concept is similar to the placement of FM radio stations throughout the country; two radio stations in the same geographic area are never on the same channel.
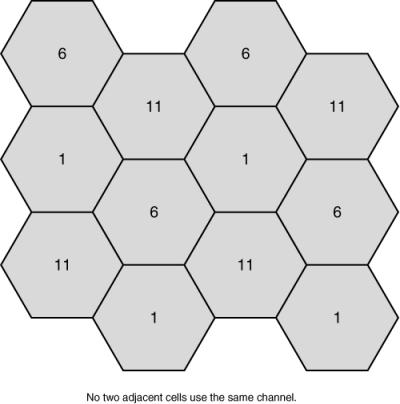
![]() Therefore, three APs, using the three nonoverlapping channels, could operate in the same area without sharing the medum. For example, an AP on channel 1 does not have any frequencies in common with an AP on channel 6 or with an AP on channel 11. Therefore, there is no degradation in throughput when three APs are in the same area if they are each on a nonoverlapping channel. Figure 9-4 illustrates how 802.11b/g cells can be placed so that no adjacent channels overlap.
Therefore, three APs, using the three nonoverlapping channels, could operate in the same area without sharing the medum. For example, an AP on channel 1 does not have any frequencies in common with an AP on channel 6 or with an AP on channel 11. Therefore, there is no degradation in throughput when three APs are in the same area if they are each on a nonoverlapping channel. Figure 9-4 illustrates how 802.11b/g cells can be placed so that no adjacent channels overlap.
![]() Different countries allow different channels and transmit power levels.
Different countries allow different channels and transmit power levels.
| Note |
|
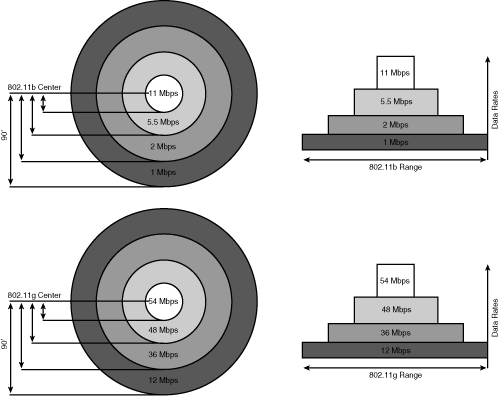
![]() The 802.11g data rates are 54, 48, 36, 24, 18, 12, 9, and 6 Mbps. The 802.11b data rates are 11, 5.5, 2, and 1 Mbps. Figure 9-5 compares the 2.4 GHz common data rates and ranges for 802.11b/g.
The 802.11g data rates are 54, 48, 36, 24, 18, 12, 9, and 6 Mbps. The 802.11b data rates are 11, 5.5, 2, and 1 Mbps. Figure 9-5 compares the 2.4 GHz common data rates and ranges for 802.11b/g.
802.11a Standard in the 5-GHz Band
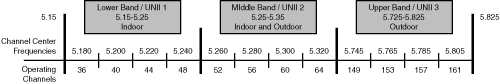
![]() The 5 GHz UNII band can be divided into multiple channels, depending on the regulations that vary by country. The U.S. now has three separate 100 MHz–wide bands known as the lower, middle, and upper bands. Within each of these three bands are four nonoverlapping channels. In the U.S., the FCC specifies that the lower band is for indoor use, the middle band is for indoor and outdoor use, and the upper band is for outdoor use. Figure 9-6 illustrates the nonoverlapping 802.11a channels.
The 5 GHz UNII band can be divided into multiple channels, depending on the regulations that vary by country. The U.S. now has three separate 100 MHz–wide bands known as the lower, middle, and upper bands. Within each of these three bands are four nonoverlapping channels. In the U.S., the FCC specifies that the lower band is for indoor use, the middle band is for indoor and outdoor use, and the upper band is for outdoor use. Figure 9-6 illustrates the nonoverlapping 802.11a channels.
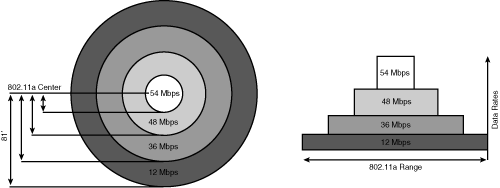
![]() 802.11a uses the same OFDM modulation and supports the same data rates as 802.11g. Figure 9-7 shows the 802.11a common data rates and ranges.
802.11a uses the same OFDM modulation and supports the same data rates as 802.11g. Figure 9-7 shows the 802.11a common data rates and ranges.
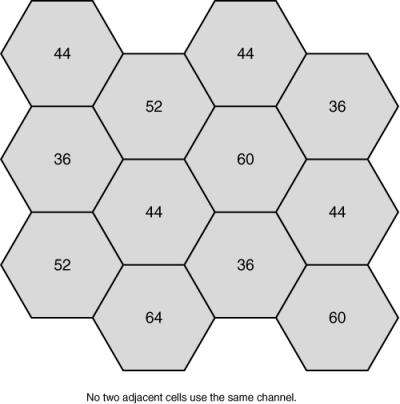
![]() 802.11a channel placement is easier to deploy than 802.11b/g, because 802.11a has 12 nonoverlapping channels that can provide a simpler channel reuse schema. However, the nonoverlapping channels for 802.11a (as shown in Figure 9-6) are close enough to each other that some clients might experience interference from adjacent channels (called side-band or side-channel interference). As a result, the recommendation for 802.11a is that neighboring cells not be placed on neighboring channels (in other words, neighboring channels are skipped) to reduce interference. Figure 9-8 illustrates 802.11a channel placement.
802.11a channel placement is easier to deploy than 802.11b/g, because 802.11a has 12 nonoverlapping channels that can provide a simpler channel reuse schema. However, the nonoverlapping channels for 802.11a (as shown in Figure 9-6) are close enough to each other that some clients might experience interference from adjacent channels (called side-band or side-channel interference). As a result, the recommendation for 802.11a is that neighboring cells not be placed on neighboring channels (in other words, neighboring channels are skipped) to reduce interference. Figure 9-8 illustrates 802.11a channel placement.
![]() Note that the 802.11a coverage area is smaller than the 802.11b/g coverage area, requiring more APs on a per-area basis.
Note that the 802.11a coverage area is smaller than the 802.11b/g coverage area, requiring more APs on a per-area basis.
802.11 WLANs Versus 802.3 Ethernet LANs
![]() Both 802.11 WLANs and 802.3 Ethernet wired LANs define the physical and data link layers, use MAC addresses, and support the same upper-layer protocols. Both 802.11 WLANs and 802.3 Ethernet LANs use the Carrier Sense Multiple Access protocol to control access to the media. Ethernet uses a collision-detection algorithm, whereas 802.11 WLANs use a collision-avoidance algorithm.
Both 802.11 WLANs and 802.3 Ethernet wired LANs define the physical and data link layers, use MAC addresses, and support the same upper-layer protocols. Both 802.11 WLANs and 802.3 Ethernet LANs use the Carrier Sense Multiple Access protocol to control access to the media. Ethernet uses a collision-detection algorithm, whereas 802.11 WLANs use a collision-avoidance algorithm.
![]() All the computers on the WLAN share the bandwidth. It is for this reason that collision detection is not possible on WLANs. A sending station cannot receive at the same time it is transmitting and therefore cannot detect whether another station is transmitting at the same time. Instead, devices avoid collisions by using request-to-send and clear-to-send messages.
All the computers on the WLAN share the bandwidth. It is for this reason that collision detection is not possible on WLANs. A sending station cannot receive at the same time it is transmitting and therefore cannot detect whether another station is transmitting at the same time. Instead, devices avoid collisions by using request-to-send and clear-to-send messages.
 WLAN Topologies
WLAN Topologies
![]() Cisco wireless products support the following three topologies:
Cisco wireless products support the following three topologies:
-
 Wireless client access: For mobile user connectivity
Wireless client access: For mobile user connectivity -
 Wireless bridging: To interconnect LANs that are physically separated—for example, in different buildings
Wireless bridging: To interconnect LANs that are physically separated—for example, in different buildings -
 Wireless mesh networking: To provide both client access and a dynamic, redundant connection between buildings
Wireless mesh networking: To provide both client access and a dynamic, redundant connection between buildings
 WLAN Components
WLAN Components
![]() Client devices use wireless NICs or adapters to connect to a wireless network in either ad hoc (peer-to-peer) mode or infrastructure mode using APs. Cisco APs can be either autonomous or lightweight.
Client devices use wireless NICs or adapters to connect to a wireless network in either ad hoc (peer-to-peer) mode or infrastructure mode using APs. Cisco APs can be either autonomous or lightweight.
| Note |
|
![]() These components are described in the following sections.
These components are described in the following sections.
Cisco-Compatible WLAN Clients
![]() The Cisco Compatible Extensions (CCX) program for WLAN client devices allows vendors of WLAN client devices or adapters to ensure interoperability with the Cisco WLAN infrastructure and take advantage of Cisco innovations. Wireless client products are submitted to an independent lab for rigorous testing; passing this testing process allows the devices to be marketed as Cisco Compatible client devices. There are four versions of the Cisco Compatible specification, versions 1 through 4. Each version builds on its predecessors; with a few exceptions, every feature that must be supported in one version must also be supported in each subsequent version.
The Cisco Compatible Extensions (CCX) program for WLAN client devices allows vendors of WLAN client devices or adapters to ensure interoperability with the Cisco WLAN infrastructure and take advantage of Cisco innovations. Wireless client products are submitted to an independent lab for rigorous testing; passing this testing process allows the devices to be marketed as Cisco Compatible client devices. There are four versions of the Cisco Compatible specification, versions 1 through 4. Each version builds on its predecessors; with a few exceptions, every feature that must be supported in one version must also be supported in each subsequent version.
Autonomous APs
![]() CiscoWorks WLSE is a turnkey and scalable management platform for managing hundreds to thousands of Cisco Aironet autonomous APs and wireless bridges. Autonomous APs may also be configured with CiscoWorks WLSE Express, a complete WLAN management solution with an integrated authentication, authorization, and accounting (AAA) server for small to medium-sized enterprise facilities or branch offices using Cisco Aironet autonomous APs and wireless bridges.
CiscoWorks WLSE is a turnkey and scalable management platform for managing hundreds to thousands of Cisco Aironet autonomous APs and wireless bridges. Autonomous APs may also be configured with CiscoWorks WLSE Express, a complete WLAN management solution with an integrated authentication, authorization, and accounting (AAA) server for small to medium-sized enterprise facilities or branch offices using Cisco Aironet autonomous APs and wireless bridges.
Lightweight APs
![]() The WLCs and lightweight APs communicate over any Layer 2 (Ethernet) or Layer 3 (IP) infrastructure using the Lightweight AP Protocol (LWAPP) to support automation of numerous WLAN configuration and management functions. WLCs are responsible for centralized systemwide WLAN management functions, such as security policies, intrusion prevention, RF management, quality of service (QoS), and mobility.
The WLCs and lightweight APs communicate over any Layer 2 (Ethernet) or Layer 3 (IP) infrastructure using the Lightweight AP Protocol (LWAPP) to support automation of numerous WLAN configuration and management functions. WLCs are responsible for centralized systemwide WLAN management functions, such as security policies, intrusion prevention, RF management, quality of service (QoS), and mobility.
![]() A Cisco wireless location appliance may be added to track the location of wireless devices.
A Cisco wireless location appliance may be added to track the location of wireless devices.
AP Power
![]() One issue for WLANs is that power might not be available where APs need to be located. Two solutions to this issue are Power over Ethernet (PoE) and power injectors. PoE, or inline power, provides operating current to a device, such as an AP, from an Ethernet port, over the Category 5 cable.
One issue for WLANs is that power might not be available where APs need to be located. Two solutions to this issue are Power over Ethernet (PoE) and power injectors. PoE, or inline power, provides operating current to a device, such as an AP, from an Ethernet port, over the Category 5 cable.
![]() A midspan power injector is a standalone unit that adds PoE capability to existing networking equipment. The power injector is inserted into the LAN between the Ethernet switch and the device requiring power, such as an AP.
A midspan power injector is a standalone unit that adds PoE capability to existing networking equipment. The power injector is inserted into the LAN between the Ethernet switch and the device requiring power, such as an AP.
 WLAN Operation
WLAN Operation
![]() If a single cell does not provide enough coverage, any number of cells can be added to extend the range to an extended service area (ESA). It is recommended that the ESA cells have 10 to 15 percent overlap to allow remote users to roam without losing RF connections. If VoIP is implemented in the wireless network, it is recommended that the ESA cells have a 15 to 20 percent overlap. As discussed earlier, bordering cells should be set to different nonoverlapping channels for best performance.
If a single cell does not provide enough coverage, any number of cells can be added to extend the range to an extended service area (ESA). It is recommended that the ESA cells have 10 to 15 percent overlap to allow remote users to roam without losing RF connections. If VoIP is implemented in the wireless network, it is recommended that the ESA cells have a 15 to 20 percent overlap. As discussed earlier, bordering cells should be set to different nonoverlapping channels for best performance.
![]() An SSID on an AP and on an associated client must match exactly. APs broadcast their SSIDs in a beacon, announcing their available services; clients associate with a specific SSID or learn the available SSIDs from the beacon and choose one with which to associate.
An SSID on an AP and on an associated client must match exactly. APs broadcast their SSIDs in a beacon, announcing their available services; clients associate with a specific SSID or learn the available SSIDs from the beacon and choose one with which to associate.
![]() APs can be configured not to broadcast a particular SSID, but the SSID is still sent in the header of all the packets sent and thus is discoverable by wireless survey tools. Therefore, configuring the AP not to broadcast an SSID is not considered a strong security mechanism by itself. This feature should be combined with some of the stronger mechanisms discussed in the next section.
APs can be configured not to broadcast a particular SSID, but the SSID is still sent in the header of all the packets sent and thus is discoverable by wireless survey tools. Therefore, configuring the AP not to broadcast an SSID is not considered a strong security mechanism by itself. This feature should be combined with some of the stronger mechanisms discussed in the next section.
 WLAN Security
WLAN Security
![]() WLAN security includes the following:
WLAN security includes the following:
-
 Authentication: Ensures that only legitimate clients access the network via trusted APs.
Authentication: Ensures that only legitimate clients access the network via trusted APs. -
 Encryption: Ensures the confidentiality of transmitted data.
Encryption: Ensures the confidentiality of transmitted data. -
 Intrusion detection and intrusion protection: Monitors, detects, and mitigates unauthorized access and attacks against the network.
Intrusion detection and intrusion protection: Monitors, detects, and mitigates unauthorized access and attacks against the network.
![]() Initially, basic 802.11 WLAN security was provided via Wired Equivalent Privacy (WEP) authentication and encryption, using static keys. With static WEP, the encryption keys must match on both the client and the access point. Unfortunately, the keys are relatively easy to compromise, so static WEP is no longer considered secure.
Initially, basic 802.11 WLAN security was provided via Wired Equivalent Privacy (WEP) authentication and encryption, using static keys. With static WEP, the encryption keys must match on both the client and the access point. Unfortunately, the keys are relatively easy to compromise, so static WEP is no longer considered secure.
![]() While the 802.11 committee was developing a more robust standard security solution, vendors incorporated the IEEE 802.1X Extensible Authentication Protocol (EAP) to authenticate users via a RADIUS authentication server such as Cisco Secure Access Control Server (ACS) and to enforce security policies for them. Basing the authentication transaction on users, rather than on machine credentials, reduces the risk of security compromise from lost or stolen equipment. 802.1X authentication also permits flexible credentials to be used for client authentication, including passwords, one-time tokens, public key infrastructure (PKI) certificates, and device IDs.
While the 802.11 committee was developing a more robust standard security solution, vendors incorporated the IEEE 802.1X Extensible Authentication Protocol (EAP) to authenticate users via a RADIUS authentication server such as Cisco Secure Access Control Server (ACS) and to enforce security policies for them. Basing the authentication transaction on users, rather than on machine credentials, reduces the risk of security compromise from lost or stolen equipment. 802.1X authentication also permits flexible credentials to be used for client authentication, including passwords, one-time tokens, public key infrastructure (PKI) certificates, and device IDs.
![]() When 802.1X is used for wireless client authentication, dynamic encryption keys can be distributed to each user, each time that user authenticates on the network. The Wi-Fi Alliance also introduced Wi-Fi Protected Access (WPA) to enhance encryption and protect against all known WEP key vulnerabilities. WPA includes the Temporal Key Integrity Protocol (TKIP) to provide per-packet keying that protects the WEP key from exploits that seek to derive the key using packet comparison, and a message integrity check (MIC) to protect against packet replay. MIC protects the wireless system from inductive attacks that seek to induce the system to send either key data or a predictable response that can be compared to known data to derive the WEP key.
When 802.1X is used for wireless client authentication, dynamic encryption keys can be distributed to each user, each time that user authenticates on the network. The Wi-Fi Alliance also introduced Wi-Fi Protected Access (WPA) to enhance encryption and protect against all known WEP key vulnerabilities. WPA includes the Temporal Key Integrity Protocol (TKIP) to provide per-packet keying that protects the WEP key from exploits that seek to derive the key using packet comparison, and a message integrity check (MIC) to protect against packet replay. MIC protects the wireless system from inductive attacks that seek to induce the system to send either key data or a predictable response that can be compared to known data to derive the WEP key.
![]() In late 2001, Cisco implemented a prestandard version of TKIP and MIC now called Cisco Key Integrity Protocol and Cisco Message Integrity Check, respectively. Cisco devices also now support the standard TKIP and MIC.
In late 2001, Cisco implemented a prestandard version of TKIP and MIC now called Cisco Key Integrity Protocol and Cisco Message Integrity Check, respectively. Cisco devices also now support the standard TKIP and MIC.
![]() The IEEE 802.11i standard now encompasses a number of security improvements, including those implemented in WPA. 802.1X authentication is still used; however, 802.11i specifies the use of the Advanced Encryption Standard (AES). AES is a stronger security algorithm than WEP, but it is more CPU-intensive and therefore requires updated hardware to run AES encryption while maintaining comparable throughput. The Wi-Fi Alliance–interoperable implementation of 802.11i with AES is called WPA2.
The IEEE 802.11i standard now encompasses a number of security improvements, including those implemented in WPA. 802.1X authentication is still used; however, 802.11i specifies the use of the Advanced Encryption Standard (AES). AES is a stronger security algorithm than WEP, but it is more CPU-intensive and therefore requires updated hardware to run AES encryption while maintaining comparable throughput. The Wi-Fi Alliance–interoperable implementation of 802.11i with AES is called WPA2.
| Note |
|
![]() Table 9-2 summarizes the WLAN security evolution.
Table 9-2 summarizes the WLAN security evolution.
|
|
|
|
|
|
|
|
|
|
|
|


0 comments
Post a Comment