![]() This chapter describes the Enterprise WAN and metropolitan-area network (MAN) architecture, and the Enterprise Branch and Teleworker architectures. The selection of WAN hardware and software components is also discussed.
This chapter describes the Enterprise WAN and metropolitan-area network (MAN) architecture, and the Enterprise Branch and Teleworker architectures. The selection of WAN hardware and software components is also discussed.
 Enterprise Edge WAN Technologies
Enterprise Edge WAN Technologies
![]() This section introduces the concept of the WAN, beginning with the definition of a WAN and the types of WAN interconnections. Various WAN technologies are described. The section concludes with a discussion of WAN pricing and contract considerations.
This section introduces the concept of the WAN, beginning with the definition of a WAN and the types of WAN interconnections. Various WAN technologies are described. The section concludes with a discussion of WAN pricing and contract considerations.
 Introduction to WANs
Introduction to WANs
![]() This section defines a WAN and describes its primary design objectives.
This section defines a WAN and describes its primary design objectives.
![]() Switches, or concentrators, connect the WAN links, relay information through the WAN, and enable the services it provides. A network provider often charges users a fee, called a tariff, for the services provided by the WAN. Therefore, WAN communication is often known as a service.
Switches, or concentrators, connect the WAN links, relay information through the WAN, and enable the services it provides. A network provider often charges users a fee, called a tariff, for the services provided by the WAN. Therefore, WAN communication is often known as a service.
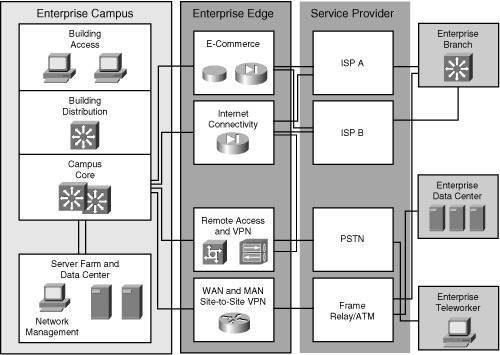
![]() Recall that the purpose of the Cisco Enterprise architecture is to modularize the enterprise network. All WAN connections are concentrated in a single functional area: the Enterprise Edge. A WAN provides the Enterprise Edge with access to remote sites and the outside world. Using various Layer 2 and Layer 3 technologies, WANs operate between the Enterprise Edge and the Service Provider Edge.
Recall that the purpose of the Cisco Enterprise architecture is to modularize the enterprise network. All WAN connections are concentrated in a single functional area: the Enterprise Edge. A WAN provides the Enterprise Edge with access to remote sites and the outside world. Using various Layer 2 and Layer 3 technologies, WANs operate between the Enterprise Edge and the Service Provider Edge.
![]() Designing a WAN is a challenging task. The first design step is to understand the WAN’s networking requirements, which are driven by two primary goals:
Designing a WAN is a challenging task. The first design step is to understand the WAN’s networking requirements, which are driven by two primary goals:
-
 Service level agreement (SLA): Networks carry application information between computers. If the applications are not available to network users, the network fails to achieve its design objectives. Organizations need to define the level of service, such as bandwidth, allowed latency, packet loss, and so forth, that is acceptable for the applications running across the WAN.
Service level agreement (SLA): Networks carry application information between computers. If the applications are not available to network users, the network fails to achieve its design objectives. Organizations need to define the level of service, such as bandwidth, allowed latency, packet loss, and so forth, that is acceptable for the applications running across the WAN. -
 Cost of investment and usage: WAN designs are always subject to budget limitations. Selecting the right type of WAN technology is critical to providing reliable services for end-user applications in a cost-effective and efficient manner.
Cost of investment and usage: WAN designs are always subject to budget limitations. Selecting the right type of WAN technology is critical to providing reliable services for end-user applications in a cost-effective and efficient manner.
![]() Flowing from these goals are the following objectives of an effective WAN design:
Flowing from these goals are the following objectives of an effective WAN design:
-
 A well-designed WAN must reflect the goals, characteristics, and policies of an organization.
A well-designed WAN must reflect the goals, characteristics, and policies of an organization. -
 The selected WAN technology should be sufficient for current and, to some extent, future application requirements.
The selected WAN technology should be sufficient for current and, to some extent, future application requirements. -
 The associated costs of investment and usage should stay within the budget limits.
The associated costs of investment and usage should stay within the budget limits.
 WAN Interconnections
WAN Interconnections
![]() Figure 5-1 illustrates the three ways that WAN technologies connect the Enterprise Edge modules with the outside world, represented by the service provider network. Typically, the intent is to provide the following connections:
Figure 5-1 illustrates the three ways that WAN technologies connect the Enterprise Edge modules with the outside world, represented by the service provider network. Typically, the intent is to provide the following connections:
-
 Connectivity between the Enterprise Edge modules and the Internet Service Provider (ISP) Edge module
Connectivity between the Enterprise Edge modules and the Internet Service Provider (ISP) Edge module -
 Connectivity between Enterprise sites across the ISP network
Connectivity between Enterprise sites across the ISP network -
 Connectivity between Enterprise sites across the SP or public switched telephone network (PSTN) carrier network
Connectivity between Enterprise sites across the SP or public switched telephone network (PSTN) carrier network
![]() WAN connections can be point-to-point between two locations or connections to a multipoint WAN service offering, such as a Frame Relay or Multiprotocol Label Switching (MPLS) network.
WAN connections can be point-to-point between two locations or connections to a multipoint WAN service offering, such as a Frame Relay or Multiprotocol Label Switching (MPLS) network.
| Note |
|
![]() One of the main issues in WAN connections is selecting the appropriate physical WAN technology. The following sections discuss WAN technologies, starting with traditional WAN technologies.
One of the main issues in WAN connections is selecting the appropriate physical WAN technology. The following sections discuss WAN technologies, starting with traditional WAN technologies.
 Traditional WAN Technologies
Traditional WAN Technologies
![]() Traditional WAN technologies include the following:
Traditional WAN technologies include the following:
-
 Leased lines: Point-to-point connections indefinitely reserved for transmissions, rather than used only when transmission is required. The carrier establishes the connection either by dedicating a physical wire or by delegating a channel using frequency division multiplexing or time-division multiplexing (TDM). Leased-line connections usually use synchronous transmission.
Leased lines: Point-to-point connections indefinitely reserved for transmissions, rather than used only when transmission is required. The carrier establishes the connection either by dedicating a physical wire or by delegating a channel using frequency division multiplexing or time-division multiplexing (TDM). Leased-line connections usually use synchronous transmission. -
 Circuit-switched networks: A type of network that, for the duration of the connection, obtains and dedicates a physical path for a single connection between two network endpoints. Ordinary voice phone service over the PSTN is circuit-switched; the telephone company reserves a specific physical path to the number being called for the call’s duration. During that time, no one else can use the physical lines involved. Other circuit-switched examples include asynchronous serial transmission and ISDN.
Circuit-switched networks: A type of network that, for the duration of the connection, obtains and dedicates a physical path for a single connection between two network endpoints. Ordinary voice phone service over the PSTN is circuit-switched; the telephone company reserves a specific physical path to the number being called for the call’s duration. During that time, no one else can use the physical lines involved. Other circuit-switched examples include asynchronous serial transmission and ISDN. -
 Packet-switched and cell-switched networks: A carrier creates permanent virtual circuits (PVC) or switched virtual circuits (SVC) that deliver packets of data among customer sites. Users share common carrier resources and can use different paths through the WAN (for example, when congestion or delay is encountered). This allows the carrier to use its infrastructure more efficiently than it can with leased point-to-point links. Examples of packet-switched networks include X.25, Frame Relay, and Switched Multimegabit Data Service.
Packet-switched and cell-switched networks: A carrier creates permanent virtual circuits (PVC) or switched virtual circuits (SVC) that deliver packets of data among customer sites. Users share common carrier resources and can use different paths through the WAN (for example, when congestion or delay is encountered). This allows the carrier to use its infrastructure more efficiently than it can with leased point-to-point links. Examples of packet-switched networks include X.25, Frame Relay, and Switched Multimegabit Data Service.
![]() Leased lines and circuit-switched networks offer users dedicated bandwidth that other users cannot take. In contrast, packet-switched networks have traditionally offered more flexibility and used network bandwidth more efficiently than circuit-switched networks. Cell switching combines some aspects of circuit switching and packet switching to produce networks with low latency and high throughput.
Leased lines and circuit-switched networks offer users dedicated bandwidth that other users cannot take. In contrast, packet-switched networks have traditionally offered more flexibility and used network bandwidth more efficiently than circuit-switched networks. Cell switching combines some aspects of circuit switching and packet switching to produce networks with low latency and high throughput.
Packet-Switched Network Topologies
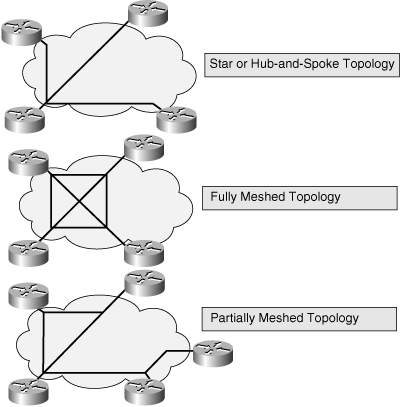
![]() As shown in Figure 5-2, packet-switched networks use three basic topologies: star, full mesh, and partial mesh.
As shown in Figure 5-2, packet-switched networks use three basic topologies: star, full mesh, and partial mesh.
Star Topology
![]() A star topology (also called a hub-and-spoke topology) features a single internetworking hub (for example, a central router) that provides access from remote networks into the core router. Communication between remote networks is possible only through the core router. The advantages of a star approach are simplified management and minimized tariff costs, which result from the low number of circuits. However, the disadvantages are significant, including the following:
A star topology (also called a hub-and-spoke topology) features a single internetworking hub (for example, a central router) that provides access from remote networks into the core router. Communication between remote networks is possible only through the core router. The advantages of a star approach are simplified management and minimized tariff costs, which result from the low number of circuits. However, the disadvantages are significant, including the following:
-
 The central router (the hub) is a single point of failure.
The central router (the hub) is a single point of failure. -
 The central router limits overall performance for access to centralized resources because all traffic intended for the centralized resources or for the other regional routers goes through this single device.
The central router limits overall performance for access to centralized resources because all traffic intended for the centralized resources or for the other regional routers goes through this single device. -
 The topology is not scalable.
The topology is not scalable.
Fully Meshed Topology
![]() In a fully meshed topology, each routing node on the periphery of a given packet-switching network has a direct path to every other node, providing any-to-any connectivity. The key rationale for creating a fully meshed environment is to provide a high level of redundancy; however, a fully meshed topology is not scalable to large packet-switched networks. Key issues include the following:
In a fully meshed topology, each routing node on the periphery of a given packet-switching network has a direct path to every other node, providing any-to-any connectivity. The key rationale for creating a fully meshed environment is to provide a high level of redundancy; however, a fully meshed topology is not scalable to large packet-switched networks. Key issues include the following:
-
 The large number of virtual circuits required—one for every connection between routers. The number of circuits required in a fully meshed topology is n(n–1)/2, where n is the number of routers.
The large number of virtual circuits required—one for every connection between routers. The number of circuits required in a fully meshed topology is n(n–1)/2, where n is the number of routers. -
 The problems associated with the requirement for large numbers of packet and broadcast replications.
The problems associated with the requirement for large numbers of packet and broadcast replications. -
 The configuration complexity of routers that must handle the absence of multicast support in nonbroadcast environments.
The configuration complexity of routers that must handle the absence of multicast support in nonbroadcast environments.
Partially Meshed Topology
![]() A partially meshed topology reduces, within a region, the number of routers that have direct connections to all other nodes within that region. Not all nodes are connected to all other nodes; for a nonmeshed node to communicate with another nonmeshed node, it must send traffic through one of the fully connected routers.
A partially meshed topology reduces, within a region, the number of routers that have direct connections to all other nodes within that region. Not all nodes are connected to all other nodes; for a nonmeshed node to communicate with another nonmeshed node, it must send traffic through one of the fully connected routers.
![]() There are many forms of partially meshed topologies. In general, partially meshed approaches provide the best balance for regional topologies in terms of the number of virtual circuits, redundancy, and performance.
There are many forms of partially meshed topologies. In general, partially meshed approaches provide the best balance for regional topologies in terms of the number of virtual circuits, redundancy, and performance.
 WAN Transport Technologies
WAN Transport Technologies
![]() Table 5-1 compares various WAN technologies, based on the main factors that influence technology selection. This table provides typical baseline characteristics to help you compare the performance and features offered by different technologies. Often, the offerings of the service provider limit your technology decisions.
Table 5-1 compares various WAN technologies, based on the main factors that influence technology selection. This table provides typical baseline characteristics to help you compare the performance and features offered by different technologies. Often, the offerings of the service provider limit your technology decisions.
| Note |
|
|
|
|
|
|
|
|
|
|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||||||
![]() These technologies are introduced in the following sections.
These technologies are introduced in the following sections.
TDM (Leased Lines)
![]() The base channel bandwidth is 64 kilobits per second (kbps), also known as digital signal level 0 (DS0). 64 kbps is the bandwidth required for an uncompressed digitized phone conversation.
The base channel bandwidth is 64 kilobits per second (kbps), also known as digital signal level 0 (DS0). 64 kbps is the bandwidth required for an uncompressed digitized phone conversation.
![]() For example, a North American T1 circuit is made up of 24 channels, each at 64 kbps, resulting in a bandwidth of 1.544 megabits per second (Mbps). A T3 circuit has 672 channels and runs at 44.736 Mbps. Corresponding European standards are the E1 standard, supporting 30 channels at 2.048 Mbps, and the E3 standard, supporting 480 channels at 34.368 Mbps.
For example, a North American T1 circuit is made up of 24 channels, each at 64 kbps, resulting in a bandwidth of 1.544 megabits per second (Mbps). A T3 circuit has 672 channels and runs at 44.736 Mbps. Corresponding European standards are the E1 standard, supporting 30 channels at 2.048 Mbps, and the E3 standard, supporting 480 channels at 34.368 Mbps.
![]() A carrier establishes a connection in a TDM network by dedicating a channel for a specific connection. In contrast, packet-switched networks traditionally offer the service provider more flexibility and use network bandwidth more efficiently than TDM networks because the network resources are shared dynamically and subscribers are charged on the basis of their network use.
A carrier establishes a connection in a TDM network by dedicating a channel for a specific connection. In contrast, packet-switched networks traditionally offer the service provider more flexibility and use network bandwidth more efficiently than TDM networks because the network resources are shared dynamically and subscribers are charged on the basis of their network use.
ISDN
![]() ISDN is a system of digital phone connections that has been available as a communications standard since 1984. This system allows voice and data to be transmitted simultaneously across the world using end-to-end digital connectivity.
ISDN is a system of digital phone connections that has been available as a communications standard since 1984. This system allows voice and data to be transmitted simultaneously across the world using end-to-end digital connectivity.
![]() However, because the industry is moving toward using broadband technologies—such as Digital Subscriber Line (DSL), cable, and public wireless—to IP security (IPsec) VPNs, ISDN presents an effective solution only for remote-user applications where broadband technologies are not available.
However, because the industry is moving toward using broadband technologies—such as Digital Subscriber Line (DSL), cable, and public wireless—to IP security (IPsec) VPNs, ISDN presents an effective solution only for remote-user applications where broadband technologies are not available.
| Note |
|
Frame Relay
![]() Frame Relay is an example of a packet-switched technology for connecting devices on a WAN that has been deployed since the late 1980s. Frame Relay is an industry-standard networking protocol that handles multiple virtual circuits (VC) using a derivation of High-Level Data Link Control (HDLC) encapsulation between connected devices.
Frame Relay is an example of a packet-switched technology for connecting devices on a WAN that has been deployed since the late 1980s. Frame Relay is an industry-standard networking protocol that handles multiple virtual circuits (VC) using a derivation of High-Level Data Link Control (HDLC) encapsulation between connected devices.
Asynchronous Transfer Mode
![]() Each ATM cell can be processed asynchronously (relative to other related cells), queued, and multiplexed over the transmission path. ATM provides support for multiple Quality of Service (QoS) classes to meet delay and loss requirements.
Each ATM cell can be processed asynchronously (relative to other related cells), queued, and multiplexed over the transmission path. ATM provides support for multiple Quality of Service (QoS) classes to meet delay and loss requirements.
MPLS
![]() MPLS is an Internet Engineering Task Force (IETF) standard architecture that combines the advantages of Layer 3 routing with the benefits of Layer 2 switching.
MPLS is an Internet Engineering Task Force (IETF) standard architecture that combines the advantages of Layer 3 routing with the benefits of Layer 2 switching.
![]() This process results in a faster, more scalable, and more flexible WAN solution. The MPLS standards evolved from the efforts of many companies, including Cisco’s tag-switching technology.
This process results in a faster, more scalable, and more flexible WAN solution. The MPLS standards evolved from the efforts of many companies, including Cisco’s tag-switching technology.
![]() MPLS enables scalable VPNs, end-to-end QoS, and other IP services that allow efficient utilization of existing networks with simpler configuration and management and quicker fault correction.
MPLS enables scalable VPNs, end-to-end QoS, and other IP services that allow efficient utilization of existing networks with simpler configuration and management and quicker fault correction.
MPLS Operation
![]() MPLS is a connection-oriented technology whose operation is based on a label attached to each packet as it enters the MPLS network. A label identifies a flow of packets (for example, voice traffic between two nodes), also called a Forwarding Equivalence Class (FEC). An FEC is a grouping of packets; packets belonging to the same FEC receive the same treatment in the network. The FEC can be determined by various parameters, including source or destination IP address or port numbers, IP protocol, IP precedence, or Layer 2 circuit identifier. Therefore, the FEC can define the flow’s QoS requirements. In addition, appropriate queuing and discard policies can be applied for FECs.
MPLS is a connection-oriented technology whose operation is based on a label attached to each packet as it enters the MPLS network. A label identifies a flow of packets (for example, voice traffic between two nodes), also called a Forwarding Equivalence Class (FEC). An FEC is a grouping of packets; packets belonging to the same FEC receive the same treatment in the network. The FEC can be determined by various parameters, including source or destination IP address or port numbers, IP protocol, IP precedence, or Layer 2 circuit identifier. Therefore, the FEC can define the flow’s QoS requirements. In addition, appropriate queuing and discard policies can be applied for FECs.
![]() The MPLS network nodes, called Label-Switched Routers (LSR), use the label to determine the packet’s next hop. The LSRs do not need to examine the packet’s IP header; rather, they forward it based on the label.
The MPLS network nodes, called Label-Switched Routers (LSR), use the label to determine the packet’s next hop. The LSRs do not need to examine the packet’s IP header; rather, they forward it based on the label.
![]() After a path has been established, packets destined for the same endpoint with the same requirements can be forwarded based on these labels without a routing decision at every hop.
After a path has been established, packets destined for the same endpoint with the same requirements can be forwarded based on these labels without a routing decision at every hop.
![]() Labels usually correspond to Layer 3 destination addresses, which makes MPLS equivalent to destination-based routing.
Labels usually correspond to Layer 3 destination addresses, which makes MPLS equivalent to destination-based routing.
![]() A Label-Switched Path (LSP) must be defined for each FEC before packets can be sent. It is important to note that labels are locally significant to each MPLS node only; therefore, the nodes must communicate what label to use for each FEC. One of two protocols is used for this communication: the Label Distribution Protocol or an enhanced version of the Resource Reservation Protocol. An interior routing protocol, such as Open Shortest Path First (OSPF) or Enhanced Interior Gateway Routing Protocol (EIGRP), is also used within the MPLS network to exchange routing information.
A Label-Switched Path (LSP) must be defined for each FEC before packets can be sent. It is important to note that labels are locally significant to each MPLS node only; therefore, the nodes must communicate what label to use for each FEC. One of two protocols is used for this communication: the Label Distribution Protocol or an enhanced version of the Resource Reservation Protocol. An interior routing protocol, such as Open Shortest Path First (OSPF) or Enhanced Interior Gateway Routing Protocol (EIGRP), is also used within the MPLS network to exchange routing information.
![]() A unique feature of MPLS is its capability to perform label stacking, in which multiple labels can be carried in a packet. The top label, which is the last one in, is always processed first. Label stacking enables multiple LSPs to be aggregated, thereby creating tunnels through multiple levels of an MPLS network.
A unique feature of MPLS is its capability to perform label stacking, in which multiple labels can be carried in a packet. The top label, which is the last one in, is always processed first. Label stacking enables multiple LSPs to be aggregated, thereby creating tunnels through multiple levels of an MPLS network.
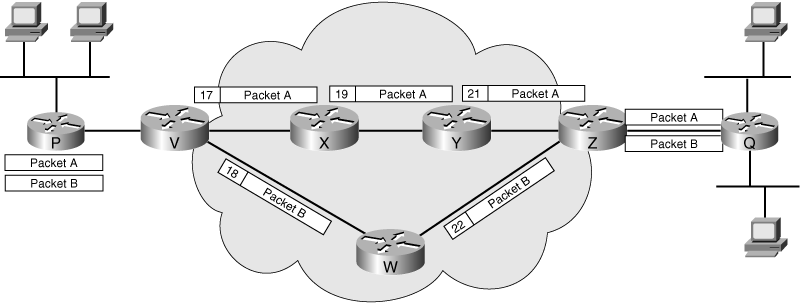
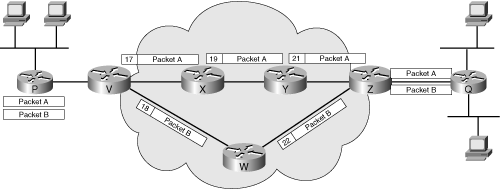
![]() An MPLS label is a 32-bit field placed between a packet’s data link layer header and its IP header. Figure 5-3 illustrates the flow of two packets through an MPLS network.
An MPLS label is a 32-bit field placed between a packet’s data link layer header and its IP header. Figure 5-3 illustrates the flow of two packets through an MPLS network.
| Note |
|
![]() In Figure 5-3, each of the MPLS nodes has previously communicated the labels it uses for each of the defined FECs to its neighboring nodes. Packet A and Packet B represent different flows; for example, Packet A might be from an FTP session, whereas Packet B is from a voice conversation. Without MPLS, these packets would take the same route through the network.
In Figure 5-3, each of the MPLS nodes has previously communicated the labels it uses for each of the defined FECs to its neighboring nodes. Packet A and Packet B represent different flows; for example, Packet A might be from an FTP session, whereas Packet B is from a voice conversation. Without MPLS, these packets would take the same route through the network.
![]() For Packets A and B, Router V is the ingress edge LSR—that is, the point at which the packets enter the network. Router V examines each packet and determines the appropriate FEC. Packet A is assigned label 17 and is sent to Router X; Packet B is assigned label 18 and is sent to Router W. As each LSR receives a labeled packet, it removes the label, locates the label in its table, applies the appropriate outgoing label, and forwards the packet to the next LSR in the LSP. When the packets reach Router Z (the egress edge LSR, or the point at which the packets leave the MPLS network), Router Z removes the label and forwards the packets appropriately, based on its IP routing table.
For Packets A and B, Router V is the ingress edge LSR—that is, the point at which the packets enter the network. Router V examines each packet and determines the appropriate FEC. Packet A is assigned label 17 and is sent to Router X; Packet B is assigned label 18 and is sent to Router W. As each LSR receives a labeled packet, it removes the label, locates the label in its table, applies the appropriate outgoing label, and forwards the packet to the next LSR in the LSP. When the packets reach Router Z (the egress edge LSR, or the point at which the packets leave the MPLS network), Router Z removes the label and forwards the packets appropriately, based on its IP routing table.
MPLS Services
![]() The following are some of the most common services provided by MPLS:
The following are some of the most common services provided by MPLS:
-
 Traffic engineering: MPLS allows traffic to be directed through a specific path, which might be different from the least-cost path determined by the IP routing protocol. This ability to define routes and resource utilization is known as traffic engineering.
Traffic engineering: MPLS allows traffic to be directed through a specific path, which might be different from the least-cost path determined by the IP routing protocol. This ability to define routes and resource utilization is known as traffic engineering. -
 QoS support: MPLS creates a connection-oriented network for IP traffic, thereby providing the foundation for QoS traffic controls. For example, it might provide guaranteed bandwidth to specific traffic between two locations.
QoS support: MPLS creates a connection-oriented network for IP traffic, thereby providing the foundation for QoS traffic controls. For example, it might provide guaranteed bandwidth to specific traffic between two locations. -
 Fast reroute (FRR): Because FRR allows extremely quick recovery from node or link failure, it prevents applications from timing out and losing data.
Fast reroute (FRR): Because FRR allows extremely quick recovery from node or link failure, it prevents applications from timing out and losing data. -
 MPLS VPNs: MPLS VPNs are much easier to deploy than traditional VPNs. They scale easily with increasing numbers of routes and customers and provide the same level of privacy as Layer 2 technologies. MPLS VPNs can also support nonunique IP addresses in various locations; for example, two organizations that use the 10.0.0.0 private address space can be supported simultaneously. MPLS VPNs are described in the later “Peer-to-Peer VPNs” section.
MPLS VPNs: MPLS VPNs are much easier to deploy than traditional VPNs. They scale easily with increasing numbers of routes and customers and provide the same level of privacy as Layer 2 technologies. MPLS VPNs can also support nonunique IP addresses in various locations; for example, two organizations that use the 10.0.0.0 private address space can be supported simultaneously. MPLS VPNs are described in the later “Peer-to-Peer VPNs” section. -
 Multiprotocol support: MPLS can be used in an ATM network, a Frame Relay network, or a pure IP-based Internet. MPLS can be used to carry many kinds of traffic, including IP packets, and native ATM, SONET, and Ethernet frames.
Multiprotocol support: MPLS can be used in an ATM network, a Frame Relay network, or a pure IP-based Internet. MPLS can be used to carry many kinds of traffic, including IP packets, and native ATM, SONET, and Ethernet frames.
![]() The key for the designer of an MPLS WAN is to minimize routing decisions and maximize MPLS switching use.
The key for the designer of an MPLS WAN is to minimize routing decisions and maximize MPLS switching use.
Metro Ethernet
![]() Service providers offer Metro Ethernet services to deliver converged voice, video, and data networking. Metro Ethernet provides a data-optimized connectivity solution for the MAN and WAN based on Ethernet technology widely deployed within the enterprise LAN. It also supports high-performance networks in the metropolitan area, meeting the increasing need for faster data speeds and more stringent QoS requirements.
Service providers offer Metro Ethernet services to deliver converged voice, video, and data networking. Metro Ethernet provides a data-optimized connectivity solution for the MAN and WAN based on Ethernet technology widely deployed within the enterprise LAN. It also supports high-performance networks in the metropolitan area, meeting the increasing need for faster data speeds and more stringent QoS requirements.
![]() Where traditional TDM access is rigid, complex, and costly to provision, Metro Ethernet services provide scalable bandwidth in flexible increments, simplified management, and faster and lower-cost provisioning. This simple, easy-to-use technology appeals to customers who are already using Ethernet on their LANs.
Where traditional TDM access is rigid, complex, and costly to provision, Metro Ethernet services provide scalable bandwidth in flexible increments, simplified management, and faster and lower-cost provisioning. This simple, easy-to-use technology appeals to customers who are already using Ethernet on their LANs.
DSL Technologies
![]() DSL delivers high bandwidth over traditional telephone copper lines. It works by way of two modems at either end of the wire. Like dialup, cable, wireless, and T1, DSL is a transmission technology that enables SPs to deliver a wide variety of services to their customers. These can include premium, high-speed Internet and intranet access, voice, VPNs, videoconferencing, and video on demand.
DSL delivers high bandwidth over traditional telephone copper lines. It works by way of two modems at either end of the wire. Like dialup, cable, wireless, and T1, DSL is a transmission technology that enables SPs to deliver a wide variety of services to their customers. These can include premium, high-speed Internet and intranet access, voice, VPNs, videoconferencing, and video on demand.
Basic DSL Implementations
![]() The term xDSL covers a variety of similar forms of DSL. The two basic DSL categories are Asymmetric DSL (ADSL) and Symmetric DSL (SDSL). ADSL can be used only over short distances (typically less than 2 km).
The term xDSL covers a variety of similar forms of DSL. The two basic DSL categories are Asymmetric DSL (ADSL) and Symmetric DSL (SDSL). ADSL can be used only over short distances (typically less than 2 km).
![]() With ADSL, traffic moves upstream and downstream at different speeds. For example, data that travels from the Internet to the end-user computer (downstream) could be moving at 1.5 Mbps, while data traveling from the end-user computer to the Internet (upstream) could be traveling at 384 kbps. ADSL can also be provisioned for symmetric operation, making it a viable residential and home office solution.
With ADSL, traffic moves upstream and downstream at different speeds. For example, data that travels from the Internet to the end-user computer (downstream) could be moving at 1.5 Mbps, while data traveling from the end-user computer to the Internet (upstream) could be traveling at 384 kbps. ADSL can also be provisioned for symmetric operation, making it a viable residential and home office solution.
![]() The use of a single twisted pair limits the operating range of SDSL to 10,000 feet (3048.8 meters). Unlike ADSL, SDSL does not allow concurrent PSTN telephony services on the same line. SDSL is a viable business solution and an excellent choice for running applications such as web and e-mail servers.
The use of a single twisted pair limits the operating range of SDSL to 10,000 feet (3048.8 meters). Unlike ADSL, SDSL does not allow concurrent PSTN telephony services on the same line. SDSL is a viable business solution and an excellent choice for running applications such as web and e-mail servers.
| Note |
|
ADSL Architecture and Design
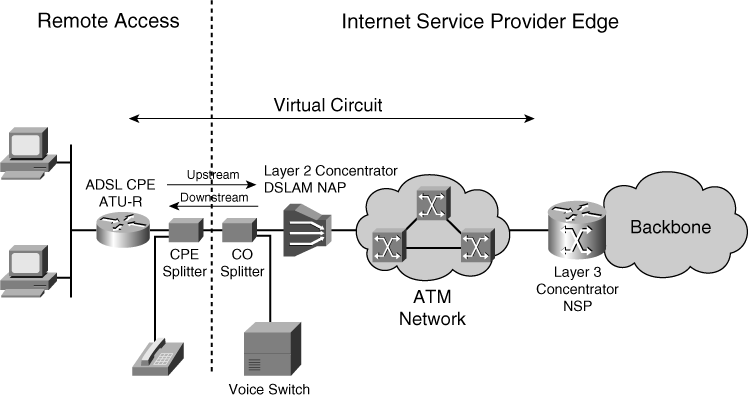
![]() Figure 5-4 illustrates a typical ADSL service architecture. The network consists of Customer Premises Equipment (CPE), the Network Access Provider (NAP), and the Network Service Provider (NSP), as follows:
Figure 5-4 illustrates a typical ADSL service architecture. The network consists of Customer Premises Equipment (CPE), the Network Access Provider (NAP), and the Network Service Provider (NSP), as follows:
-
 CPE refers to an end-user workstation, such as a PC, together with an ADSL modem or an ADSL transceiver unit remote terminal (ATU-R).
CPE refers to an end-user workstation, such as a PC, together with an ADSL modem or an ADSL transceiver unit remote terminal (ATU-R). -
 The NAP provides ADSL line termination by using DSL access multiplexers (DSLAM).
The NAP provides ADSL line termination by using DSL access multiplexers (DSLAM). -
 The DSLAM forwards traffic to the NSP, the local access concentrator, which is used for Layer 3 termination.
The DSLAM forwards traffic to the NSP, the local access concentrator, which is used for Layer 3 termination.
![]() An ADSL circuit connects an ADSL modem on each end of a twisted-pair telephone line. This creates three information channels:
An ADSL circuit connects an ADSL modem on each end of a twisted-pair telephone line. This creates three information channels:
-
 Medium-speed downstream channel
Medium-speed downstream channel -
 Low-speed upstream channel
Low-speed upstream channel -
 Basic telephone service channel
Basic telephone service channel
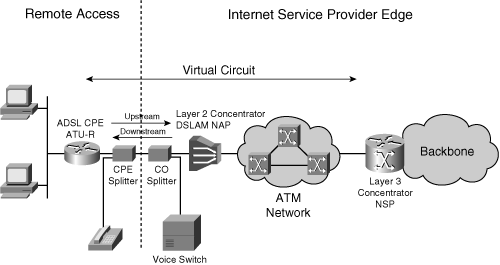
![]() Filters, or splitters, split off the basic telephone service channel from the digital modem, guaranteeing uninterrupted basic telephone service even if ADSL fails. Figure 5-5 illustrates a typical ADSL network, including (from left to right) customer workstations and PCs on a LAN, CPE (ADSL routers), a DSLAM on an ATM transport network, an NSP concentrator, and both packet and ATM core networks. Two very popular point-to-point protocol (PPP) implementations exist in ADSL designs: PPP over ATM (PPPoA) and PPP over Ethernet (PPPoE).
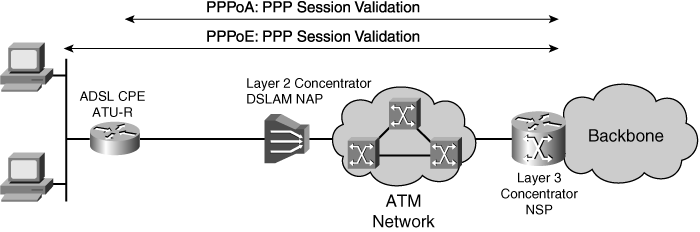
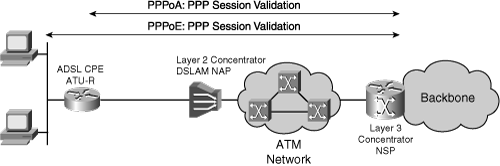
Filters, or splitters, split off the basic telephone service channel from the digital modem, guaranteeing uninterrupted basic telephone service even if ADSL fails. Figure 5-5 illustrates a typical ADSL network, including (from left to right) customer workstations and PCs on a LAN, CPE (ADSL routers), a DSLAM on an ATM transport network, an NSP concentrator, and both packet and ATM core networks. Two very popular point-to-point protocol (PPP) implementations exist in ADSL designs: PPP over ATM (PPPoA) and PPP over Ethernet (PPPoE).
![]() In the PPPoA architecture, the CPE acts as an Ethernet-to-WAN router, and the PPP session is established between the CPE and the Layer 3 access concentrator (the NSP). A PPPoA implementation involves configuring the CPE with PPP authentication information (login and password).
In the PPPoA architecture, the CPE acts as an Ethernet-to-WAN router, and the PPP session is established between the CPE and the Layer 3 access concentrator (the NSP). A PPPoA implementation involves configuring the CPE with PPP authentication information (login and password).
![]() In the PPPoE architecture, the CPE acts as an Ethernet-to-WAN bridge, and the PPP session is established between the end user’s PC or PPPoE router and the Layer 3 access concentrator (the NSP). The client initiates a PPP session by encapsulating PPP frames into an Ethernet frame and then bridging the frame (over ATM/DSL) to the gateway router (the NSP). From this point, the PPP sessions are established, authenticated, and addressed. The client receives its IP address using PPP negotiation from the termination point (the NSP).
In the PPPoE architecture, the CPE acts as an Ethernet-to-WAN bridge, and the PPP session is established between the end user’s PC or PPPoE router and the Layer 3 access concentrator (the NSP). The client initiates a PPP session by encapsulating PPP frames into an Ethernet frame and then bridging the frame (over ATM/DSL) to the gateway router (the NSP). From this point, the PPP sessions are established, authenticated, and addressed. The client receives its IP address using PPP negotiation from the termination point (the NSP).
Long Reach Ethernet Technology
![]() LRE technology allows Ethernet LAN transmissions to coexist with POTS, ISDN, or advanced PBX signaling services over the same pair of ordinary copper wires. LRE technology uses coding and digital modulation techniques from the DSL world in conjunction with Ethernet, the most popular LAN protocol.
LRE technology allows Ethernet LAN transmissions to coexist with POTS, ISDN, or advanced PBX signaling services over the same pair of ordinary copper wires. LRE technology uses coding and digital modulation techniques from the DSL world in conjunction with Ethernet, the most popular LAN protocol.
![]() An LRE system provides a point-to-point transmission that can deliver a symmetrical, full-duplex, raw data rate of up to 15 Mbps over distances of up to 1 mile (1.6 km). The channel’s speed decreases with distance.
An LRE system provides a point-to-point transmission that can deliver a symmetrical, full-duplex, raw data rate of up to 15 Mbps over distances of up to 1 mile (1.6 km). The channel’s speed decreases with distance.
Cable Technology
![]() This technology is a good option for environments where cable television is widely deployed. Cable service providers support both residential and commercial customers.
This technology is a good option for environments where cable television is widely deployed. Cable service providers support both residential and commercial customers.
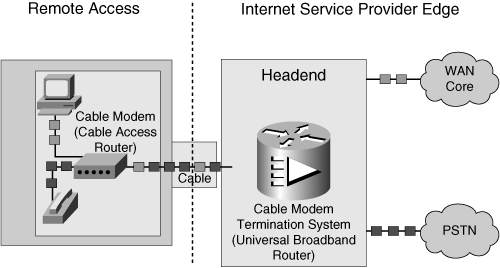
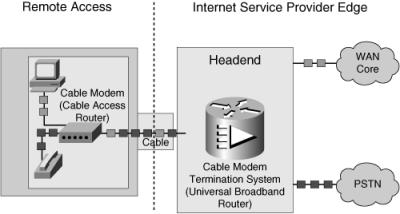
![]() Figure 5-6 illustrates some of the components used to transmit data and voice on a cable network. The Universal Broadband Router (uBR), also referred to as the Cable Modem Termination System (CMTS), provides high-speed data connectivity and is deployed at the cable company’s headend. The uBR forwards data upstream to connect with either the PSTN or the Internet. The cable modem, also referred to as the cable access router, at the customer location offers support for transmission of voice, modem, and fax calls over the TCP/IP cable network.
Figure 5-6 illustrates some of the components used to transmit data and voice on a cable network. The Universal Broadband Router (uBR), also referred to as the Cable Modem Termination System (CMTS), provides high-speed data connectivity and is deployed at the cable company’s headend. The uBR forwards data upstream to connect with either the PSTN or the Internet. The cable modem, also referred to as the cable access router, at the customer location offers support for transmission of voice, modem, and fax calls over the TCP/IP cable network.
![]() Cable modems are installed at the customer premises to support small businesses, branch offices, and corporate telecommuters.
Cable modems are installed at the customer premises to support small businesses, branch offices, and corporate telecommuters.
![]() The uBR is designed to be installed at a cable operator’s headend facility or distribution hub and to function as the CMTS for subscriber-end devices.
The uBR is designed to be installed at a cable operator’s headend facility or distribution hub and to function as the CMTS for subscriber-end devices.
![]() The Data over Cable Service Interface Specification (DOCSIS) Radio Frequency (RF) Interface Specification defines the interface between the cable modem and the CMTS, and the data-over-cable procedures that the equipment must support.
The Data over Cable Service Interface Specification (DOCSIS) Radio Frequency (RF) Interface Specification defines the interface between the cable modem and the CMTS, and the data-over-cable procedures that the equipment must support.
Upstream and Downstream Data Flow
![]() A data service is delivered to a subscriber through channels in a coaxial or optical fiber cable to a cable modem installed externally or internally to a subscriber’s computer or television set. One television channel is used for upstream signals from the cable modem to the CMTS, and another channel is used for downstream signals from the CMTS to the cable modem.
A data service is delivered to a subscriber through channels in a coaxial or optical fiber cable to a cable modem installed externally or internally to a subscriber’s computer or television set. One television channel is used for upstream signals from the cable modem to the CMTS, and another channel is used for downstream signals from the CMTS to the cable modem.
![]() When a CMTS receives signals from a cable modem, it converts these signals into IP packets that are then sent to an IP router for transmission across the Internet. When a CMTS sends signals to a cable modem, it modulates the downstream signals for transmission across the cable, or across the optical fiber and cable, to the cable modem. All cable modems can communicate with the CMTS, but not with other cable modems on the line.
When a CMTS receives signals from a cable modem, it converts these signals into IP packets that are then sent to an IP router for transmission across the Internet. When a CMTS sends signals to a cable modem, it modulates the downstream signals for transmission across the cable, or across the optical fiber and cable, to the cable modem. All cable modems can communicate with the CMTS, but not with other cable modems on the line.
![]() The actual bandwidth for Internet service over a cable TV line is shared 27 Mbps on the download path to the subscriber, with about 2.5 Mbps of shared bandwidth for interactive responses in the other direction.
The actual bandwidth for Internet service over a cable TV line is shared 27 Mbps on the download path to the subscriber, with about 2.5 Mbps of shared bandwidth for interactive responses in the other direction.
CATV Transmission
![]() Before converting to their respective channel assignments in the downstream frequency domain, signals from broadcasters and satellite services are descrambled. Video signals are converted from optical signals to electrical signals and then are amplified and forwarded downstream over coaxial cable for distribution to the cable operator’s customers.
Before converting to their respective channel assignments in the downstream frequency domain, signals from broadcasters and satellite services are descrambled. Video signals are converted from optical signals to electrical signals and then are amplified and forwarded downstream over coaxial cable for distribution to the cable operator’s customers.
Wireless Technologies
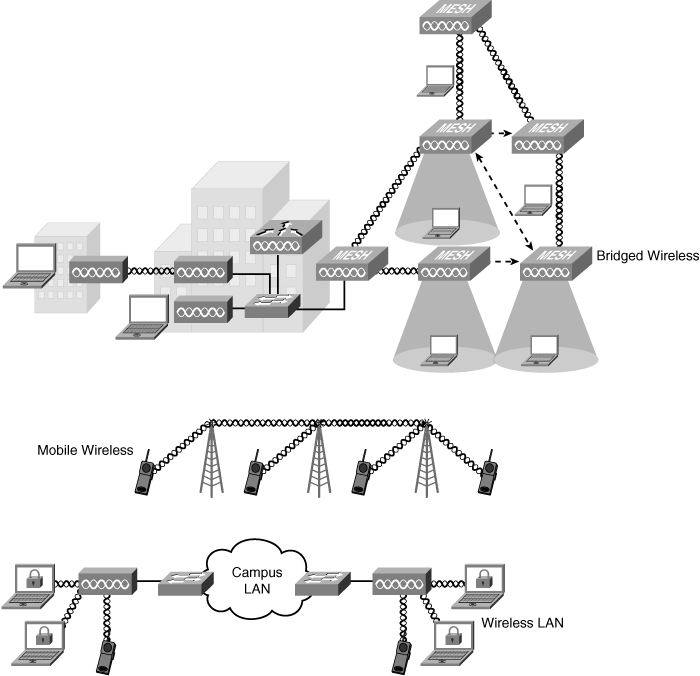
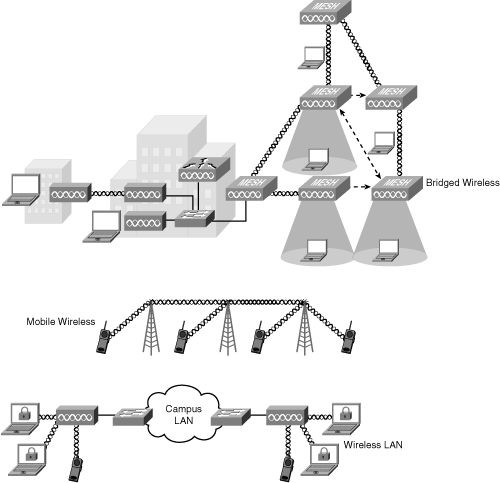
![]() Common examples of wireless equipment include cellular phones and pagers, global positioning systems, cordless computer peripherals, satellite television, and wireless LANs (WLAN). As shown in Figure 5-7, wireless implementations include the following:
Common examples of wireless equipment include cellular phones and pagers, global positioning systems, cordless computer peripherals, satellite television, and wireless LANs (WLAN). As shown in Figure 5-7, wireless implementations include the following:
-
 Bridged wireless: Designed to connect two or more networks, typically located in different buildings, at high data rates for data-intensive, line-of-sight applications. A series of wireless bridges or routers connect discrete, distant sites into a single LAN, interconnecting hard-to-wire sites, noncontiguous floors, satellite offices, school or corporate campus settings, temporary networks, and warehouses.
Bridged wireless: Designed to connect two or more networks, typically located in different buildings, at high data rates for data-intensive, line-of-sight applications. A series of wireless bridges or routers connect discrete, distant sites into a single LAN, interconnecting hard-to-wire sites, noncontiguous floors, satellite offices, school or corporate campus settings, temporary networks, and warehouses. -
 Mobile wireless: Includes cellular voice and data applications. Wireless technology usage increased with the introduction of digital services on wireless. Second- and third-generation mobile phones offer better connectivity and higher speeds. Mobile wireless technologies include the following:
Mobile wireless: Includes cellular voice and data applications. Wireless technology usage increased with the introduction of digital services on wireless. Second- and third-generation mobile phones offer better connectivity and higher speeds. Mobile wireless technologies include the following:-
 Global System for Mobile (GSM): GSM is a digital mobile radio standard that uses time division multiple access (TDMA) technology. It allows eight simultaneous calls on the same frequency, in three different bands: 900, 1800, and 1900 MHz. The transfer data rate is 9.6 kbps. One of the unique benefits of the GSM service is its international roaming capability, a result of roaming agreements established among the various operators.
Global System for Mobile (GSM): GSM is a digital mobile radio standard that uses time division multiple access (TDMA) technology. It allows eight simultaneous calls on the same frequency, in three different bands: 900, 1800, and 1900 MHz. The transfer data rate is 9.6 kbps. One of the unique benefits of the GSM service is its international roaming capability, a result of roaming agreements established among the various operators. -
 General Packet Radio Service (GPRS): GPRS extends the capability of GSM and supports intermittent and bursty data transfer. Speeds offered to the client are in the range of ISDN speeds (64 kbps to 128 kbps).
General Packet Radio Service (GPRS): GPRS extends the capability of GSM and supports intermittent and bursty data transfer. Speeds offered to the client are in the range of ISDN speeds (64 kbps to 128 kbps). -
 Universal Mobile Telephone Service (UMTS): UTMS is a so-called third-generation (3G) broadband, packet-based transmission of text, digitized voice, video, and multimedia at data rates up to 2 Mbps. UMTS offers a consistent set of services to mobile computer and phone users, regardless of their location in the world.
Universal Mobile Telephone Service (UMTS): UTMS is a so-called third-generation (3G) broadband, packet-based transmission of text, digitized voice, video, and multimedia at data rates up to 2 Mbps. UMTS offers a consistent set of services to mobile computer and phone users, regardless of their location in the world. -
 Code Division Multiple Access (CDMA): CDMA is a spread-spectrum technology that assigns a code to each conversation; individual conversations are encoded in a pseudo-random digital sequence.
Code Division Multiple Access (CDMA): CDMA is a spread-spectrum technology that assigns a code to each conversation; individual conversations are encoded in a pseudo-random digital sequence.
-
-
 WLAN: Developed because of demand for LAN connections over the air and often used for intrabuilding communication. WLAN technology can replace a traditional wired network or extend its reach and capabilities. WLANs cover a growing range of applications, such as guest access and voice, and support services, such as advanced security and location of wireless devices.
WLAN: Developed because of demand for LAN connections over the air and often used for intrabuilding communication. WLAN technology can replace a traditional wired network or extend its reach and capabilities. WLANs cover a growing range of applications, such as guest access and voice, and support services, such as advanced security and location of wireless devices. The IEEE 802.11g standard supports speeds of up to 54 Mbps in the 2.4-GHz band.
The IEEE 802.11g standard supports speeds of up to 54 Mbps in the 2.4-GHz band. The IEEE 802.11b standard supports speeds of up to 11 Mbps in the 2.4-GHz band.
The IEEE 802.11b standard supports speeds of up to 11 Mbps in the 2.4-GHz band. The IEEE 802.11a standard supports speeds of up to 54 Mbps in the 5-GHz band.
The IEEE 802.11a standard supports speeds of up to 54 Mbps in the 5-GHz band.
| Note |
|
Synchronous Optical Network and Synchronous Digital Hierarchy
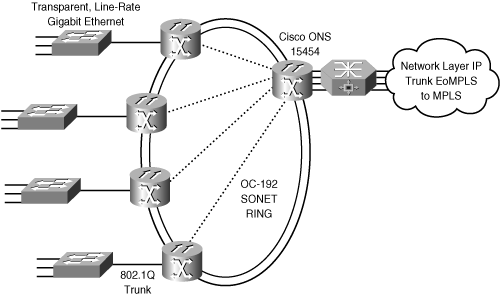
![]() Synchronous Optical Network/Synchronous Digital Hierarchy (SONET/SDH) is a circuit-based bandwidth-efficient technology. SONET/SDH establishes high-speed circuits using TDM frames in ring topologies over an optical infrastructure, as illustrated in Figure 5-8. It results in guaranteed bandwidth, regardless of actual usage. Common bit rates are 155 Mbps and 622 Mbps, with a current maximum of 10 Gigabits per second (Gbps).
Synchronous Optical Network/Synchronous Digital Hierarchy (SONET/SDH) is a circuit-based bandwidth-efficient technology. SONET/SDH establishes high-speed circuits using TDM frames in ring topologies over an optical infrastructure, as illustrated in Figure 5-8. It results in guaranteed bandwidth, regardless of actual usage. Common bit rates are 155 Mbps and 622 Mbps, with a current maximum of 10 Gigabits per second (Gbps).
![]() SONET/SDH rings support two IP encapsulations for user interfaces: ATM, and Packet over SONET/SDH (POS), which sends native IP packets directly over SONET/SDH frames. SONET/SDH rings provide major innovations for transport and have important capabilities, such as proactive performance monitoring and automatic recovery (self-healing) via an automatic protection switching mechanism. These capabilities increase their reliability to cope with system faults. Failure of a single SONET/SDH link or a network element does not lead to failure of the entire network.
SONET/SDH rings support two IP encapsulations for user interfaces: ATM, and Packet over SONET/SDH (POS), which sends native IP packets directly over SONET/SDH frames. SONET/SDH rings provide major innovations for transport and have important capabilities, such as proactive performance monitoring and automatic recovery (self-healing) via an automatic protection switching mechanism. These capabilities increase their reliability to cope with system faults. Failure of a single SONET/SDH link or a network element does not lead to failure of the entire network.
![]() Optical carrier (OC) rates are the digital hierarchies of the SONET standard, supporting the following speeds:
Optical carrier (OC) rates are the digital hierarchies of the SONET standard, supporting the following speeds:
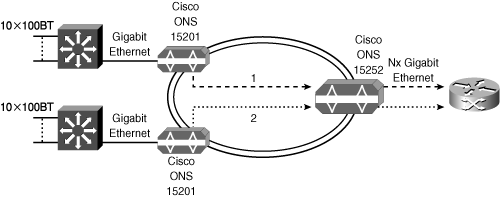
Dense Wavelength Division Multiplexing
![]() Dense Wavelength Division Multiplexing (DWDM), illustrated in Figure 5-9, increases bandwidth on an optical medium.
Dense Wavelength Division Multiplexing (DWDM), illustrated in Figure 5-9, increases bandwidth on an optical medium.
![]() DWDM is a crucial component of optical networks. It maximizes the use of installed fiber cable and allows new services to be provisioned efficiently over existing infrastructure. Flexible add and drop modules allow individual channels to be dropped and inserted along a route. An open architecture system allows the connection of a variety of devices, including SONET terminals, ATM switches, and IP routers. DWDM is also used inside the SONET/SDH ring.
DWDM is a crucial component of optical networks. It maximizes the use of installed fiber cable and allows new services to be provisioned efficiently over existing infrastructure. Flexible add and drop modules allow individual channels to be dropped and inserted along a route. An open architecture system allows the connection of a variety of devices, including SONET terminals, ATM switches, and IP routers. DWDM is also used inside the SONET/SDH ring.
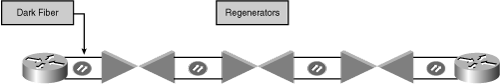
Dark Fiber
![]() Dark fiber use is illustrated in Figure 5-10. The framing for the dark fiber is provided by the company’s devices and does not have to be SONET/SDH. As a result, the dark-fiber connection eliminates the need for SONET/SDH multiplexers, which are required in SONET/SDH rings. The edge devices connect directly over the site-to-site dark fiber using a Layer 2 encapsulation such as Gigabit Ethernet. When such connectivity is used to transmit data over significantly long distances, regenerators or DWDM concentrators are inserted into the link to maintain signal integrity and provide appropriate jitter control.
Dark fiber use is illustrated in Figure 5-10. The framing for the dark fiber is provided by the company’s devices and does not have to be SONET/SDH. As a result, the dark-fiber connection eliminates the need for SONET/SDH multiplexers, which are required in SONET/SDH rings. The edge devices connect directly over the site-to-site dark fiber using a Layer 2 encapsulation such as Gigabit Ethernet. When such connectivity is used to transmit data over significantly long distances, regenerators or DWDM concentrators are inserted into the link to maintain signal integrity and provide appropriate jitter control.
![]() Depending on the carrier and location, dark fiber might be available for sale on the wholesale market for both metro and wide-area links at prices previously associated with leased-line rental.
Depending on the carrier and location, dark fiber might be available for sale on the wholesale market for both metro and wide-area links at prices previously associated with leased-line rental.
 WAN Transport Technology Pricing and Contract Considerations
WAN Transport Technology Pricing and Contract Considerations
![]() This section discusses pricing and contract considerations for WAN technologies.
This section discusses pricing and contract considerations for WAN technologies.
| Note |
|
![]() Historically, WAN transport costs include an access circuit charge and, for TDM, a distance-sensitive rate. Some carriers have dropped or reduced distance-based factors as TDM circuits have become a commodity.
Historically, WAN transport costs include an access circuit charge and, for TDM, a distance-sensitive rate. Some carriers have dropped or reduced distance-based factors as TDM circuits have become a commodity.
![]() A service provider might need 60 days or more to provision access circuits. The higher the bandwidth, the more lead time it might take to install.
A service provider might need 60 days or more to provision access circuits. The higher the bandwidth, the more lead time it might take to install.
![]() Metro Ethernet might not be available everywhere, and the lead times could be long. Construction and associated fees might be required when provisioning the fiber access.
Metro Ethernet might not be available everywhere, and the lead times could be long. Construction and associated fees might be required when provisioning the fiber access.
![]() For Frame Relay and ATM, typical charges include a combination of an access circuit charge (per-PVC) and possibly per-bandwidth (committed information rate [CIR] or minimum information rate [MIR]) charges. Some carriers have simplified these rates by charging based on the access circuit and then setting CIR or MIR to half that speed; this technique allows bursts to two times the guaranteed rate.
For Frame Relay and ATM, typical charges include a combination of an access circuit charge (per-PVC) and possibly per-bandwidth (committed information rate [CIR] or minimum information rate [MIR]) charges. Some carriers have simplified these rates by charging based on the access circuit and then setting CIR or MIR to half that speed; this technique allows bursts to two times the guaranteed rate.
![]() Frame Relay might be generally available up to T3 speeds. However, in some cases, the trunks between Frame Relay switches is T3 speed and the service providers do not want to offer T3 access circuits because all the bandwidth would be utilized.
Frame Relay might be generally available up to T3 speeds. However, in some cases, the trunks between Frame Relay switches is T3 speed and the service providers do not want to offer T3 access circuits because all the bandwidth would be utilized.
![]() For MPLS VPNs, pricing generally is set to compete with Frame Relay and ATM. Some providers encourage customers to move to MPLS VPN by offering lower prices than for Frame Relay and ATM. Other service providers price MPLS VPNs somewhat higher than Frame Relay or ATM because they include a routing service.
For MPLS VPNs, pricing generally is set to compete with Frame Relay and ATM. Some providers encourage customers to move to MPLS VPN by offering lower prices than for Frame Relay and ATM. Other service providers price MPLS VPNs somewhat higher than Frame Relay or ATM because they include a routing service.
![]() Tariffed commercial services typically are available at published rates and are subject to certain restrictions. Some carriers are moving toward unpublished rates, allowing more flexibility in options and charges.
Tariffed commercial services typically are available at published rates and are subject to certain restrictions. Some carriers are moving toward unpublished rates, allowing more flexibility in options and charges.
![]() In general, the time needed to contract a WAN circuit in a standard carrier package is on the order of one month or so. If you choose to negotiate an SLA, expect six months or more of discussions with the service provider, and include your legal department. You might not be able to influence many changes in the SLA unless you represent a very large customer.
In general, the time needed to contract a WAN circuit in a standard carrier package is on the order of one month or so. If you choose to negotiate an SLA, expect six months or more of discussions with the service provider, and include your legal department. You might not be able to influence many changes in the SLA unless you represent a very large customer.
![]() Contract periods are usually in the range of one to five years. Because the telecommunications industry is changing quickly, enterprises generally do not want to get locked into a long-term contract. Escape clauses in case of merger or poor performance might help mitigate the business risks of long-term contracts.
Contract periods are usually in the range of one to five years. Because the telecommunications industry is changing quickly, enterprises generally do not want to get locked into a long-term contract. Escape clauses in case of merger or poor performance might help mitigate the business risks of long-term contracts.
![]() For dark fiber, contract periods are generally for 20 years. One option to consider is the right of nonreversion, meaning that no matter what happens to the provider, the fiber is yours to use for the full 20 years, protecting the enterprise in case of a service provider merger, bankruptcy, and so on. The process and responsibility to repair the fiber when necessary should also be defined in the contract.
For dark fiber, contract periods are generally for 20 years. One option to consider is the right of nonreversion, meaning that no matter what happens to the provider, the fiber is yours to use for the full 20 years, protecting the enterprise in case of a service provider merger, bankruptcy, and so on. The process and responsibility to repair the fiber when necessary should also be defined in the contract.


0 comments
Post a Comment