Services Within Modular Networks
![]() Businesses that operate large enterprise networks strive to create an enterprise-wide networked infrastructure and interactive services to serve as a solid foundation for business and collaborative applications. This section explores some of the interactive services with respect to the modules that form the Cisco Enterprise Architecture.
Businesses that operate large enterprise networks strive to create an enterprise-wide networked infrastructure and interactive services to serve as a solid foundation for business and collaborative applications. This section explores some of the interactive services with respect to the modules that form the Cisco Enterprise Architecture.
 Interactive Services
Interactive Services
![]() Since the inception of packet-based communications, networks have always offered a forwarding service. Forwarding is the fundamental activity within an internetwork. In IP, this forwarding service was built on the assumption that end nodes in the network were intelligent, and that the network core did not have intelligence. With advances in networking software and hardware, the network can offer an increasingly rich, intelligent set of mechanisms for forwarding information. Interactive services add intelligence to the network infrastructure, beyond simply moving a datagram between two points.
Since the inception of packet-based communications, networks have always offered a forwarding service. Forwarding is the fundamental activity within an internetwork. In IP, this forwarding service was built on the assumption that end nodes in the network were intelligent, and that the network core did not have intelligence. With advances in networking software and hardware, the network can offer an increasingly rich, intelligent set of mechanisms for forwarding information. Interactive services add intelligence to the network infrastructure, beyond simply moving a datagram between two points.
![]() For example, through intelligent network classification, the network distinguishes and identifies traffic based on application content and context. Advanced network services use the traffic classification to regulate performance, ensure security, facilitate delivery, and improve manageability.
For example, through intelligent network classification, the network distinguishes and identifies traffic based on application content and context. Advanced network services use the traffic classification to regulate performance, ensure security, facilitate delivery, and improve manageability.
![]() Network applications such as IP telephony support the entire enterprise network environment—from the teleworker to the campus to the data center. These applications are enabled by critical network services and provide a common set of capabilities to support the application’s networkwide requirements, including security, high availability, reliability, flexibility, responsiveness, and compliancy.
Network applications such as IP telephony support the entire enterprise network environment—from the teleworker to the campus to the data center. These applications are enabled by critical network services and provide a common set of capabilities to support the application’s networkwide requirements, including security, high availability, reliability, flexibility, responsiveness, and compliancy.
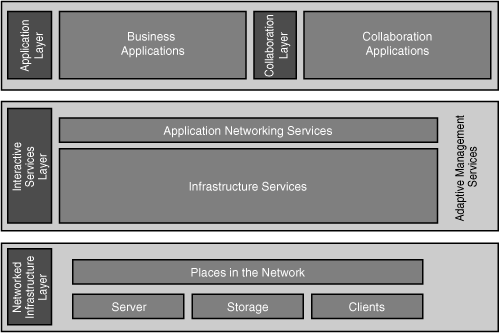
![]() Recall the layers of the Cisco SONA framework, illustrated in Figure 3-14. The SONA interactive services layer includes both application networking services and infrastructure services.
Recall the layers of the Cisco SONA framework, illustrated in Figure 3-14. The SONA interactive services layer includes both application networking services and infrastructure services.
![]() For example, the following infrastructure services (shown earlier in Figure 3-8) enhance classic network functions to support today’s applications environments by mapping the application’s requirements to the resources that they require from the network:
For example, the following infrastructure services (shown earlier in Figure 3-8) enhance classic network functions to support today’s applications environments by mapping the application’s requirements to the resources that they require from the network:
-
 Security services: Ensure that all aspects of the network are secure, from devices connecting to the network to secured transport to data theft prevention
Security services: Ensure that all aspects of the network are secure, from devices connecting to the network to secured transport to data theft prevention -
 Mobility services: Allow users to access network resources regardless of their physical location
Mobility services: Allow users to access network resources regardless of their physical location -
 Storage services: Provide distributed and virtual storage across the infrastructure
Storage services: Provide distributed and virtual storage across the infrastructure -
 Voice and collaboration services: Deliver the foundation by which voice can be carried across the network, such as security and high availability
Voice and collaboration services: Deliver the foundation by which voice can be carried across the network, such as security and high availability -
 Compute services: Connect and virtualize compute resources based on the application
Compute services: Connect and virtualize compute resources based on the application -
 Identity services: Map resources and policies to the user and device
Identity services: Map resources and policies to the user and device
![]() Examples of network services imbedded in the infrastructure services include the following:
Examples of network services imbedded in the infrastructure services include the following:
-
 Network management: Includes LAN management for advanced management of multilayer switches; routed WAN management for monitoring, traffic management, and access control to administer the routed infrastructure of multiservice networks; service management for managing and monitoring service level agreements (SLAs); and VPN security management for optimizing VPN performance and security administration.
Network management: Includes LAN management for advanced management of multilayer switches; routed WAN management for monitoring, traffic management, and access control to administer the routed infrastructure of multiservice networks; service management for managing and monitoring service level agreements (SLAs); and VPN security management for optimizing VPN performance and security administration. -
 High availability: Ensures end-to-end availability for services, clients, and sessions. Implementation includes reliable, fault-tolerant network devices to automatically identify and overcome failures, and resilient network technologies.
High availability: Ensures end-to-end availability for services, clients, and sessions. Implementation includes reliable, fault-tolerant network devices to automatically identify and overcome failures, and resilient network technologies. -
 QoS: Manages the delay, delay variation (jitter), bandwidth availability, and packet loss parameters of a network to meet the diverse needs of voice, video, and data applications. QoS features provide value-added functionality, such as network-based application recognition for classifying traffic on an application basis, Cisco IOS IP SLAs (previously called the service assurance agent) for end-to-end QoS measurements, Resource Reservation Protocol signaling for admission control and reservation of resources, and a variety of configurable queue insertion and servicing functions.
QoS: Manages the delay, delay variation (jitter), bandwidth availability, and packet loss parameters of a network to meet the diverse needs of voice, video, and data applications. QoS features provide value-added functionality, such as network-based application recognition for classifying traffic on an application basis, Cisco IOS IP SLAs (previously called the service assurance agent) for end-to-end QoS measurements, Resource Reservation Protocol signaling for admission control and reservation of resources, and a variety of configurable queue insertion and servicing functions. -
 IP multicasting: Provides bandwidth-conserving technology that reduces network traffic by delivering a single stream of information intended for many recipients through the transport network. Multicasting enables distribution of videoconferencing, corporate communications, distance learning, software, and other applications. Multicast packets are replicated only as necessary by Cisco routers enabled with Protocol Independent Multicast and other supporting multicast protocols that result in the most efficient delivery of data to multiple receivers.
IP multicasting: Provides bandwidth-conserving technology that reduces network traffic by delivering a single stream of information intended for many recipients through the transport network. Multicasting enables distribution of videoconferencing, corporate communications, distance learning, software, and other applications. Multicast packets are replicated only as necessary by Cisco routers enabled with Protocol Independent Multicast and other supporting multicast protocols that result in the most efficient delivery of data to multiple receivers.
![]() To support network applications efficiently, deploy the underlying infrastructure services in some or all modules of the enterprise network as required. These design elements can be replicated simply to other enterprise network modules as the network changes. As a result, modularization to small subsets of the overall network simplifies the network design and often reduces the network’s cost and complexity.
To support network applications efficiently, deploy the underlying infrastructure services in some or all modules of the enterprise network as required. These design elements can be replicated simply to other enterprise network modules as the network changes. As a result, modularization to small subsets of the overall network simplifies the network design and often reduces the network’s cost and complexity.
![]() The following sections explore some of the infrastructure services and application networking services. Network management services are described in the “Network Management Protocols and Features” section later in this chapter.
The following sections explore some of the infrastructure services and application networking services. Network management services are described in the “Network Management Protocols and Features” section later in this chapter.
 Security Services in a Modular Network Design
Security Services in a Modular Network Design
![]() Without a full understanding of the threats involved, network security deployments tend to be incorrectly configured, too focused on security devices, or lacking appropriate threat response options.
Without a full understanding of the threats involved, network security deployments tend to be incorrectly configured, too focused on security devices, or lacking appropriate threat response options.
![]() Security both in the Enterprise Campus (internal security) and at the Enterprise Edge (from external threats) is important. An enterprise should include several layers of protection so that a breach at one layer or in one network module does not mean that other layers or modules are also compromised; Cisco calls deploying layered security defense-in-depth.
Security both in the Enterprise Campus (internal security) and at the Enterprise Edge (from external threats) is important. An enterprise should include several layers of protection so that a breach at one layer or in one network module does not mean that other layers or modules are also compromised; Cisco calls deploying layered security defense-in-depth.
Internal Security
![]() Strongly protecting the internal Enterprise Campus by including security functions in each individual element is important for the following reasons:
Strongly protecting the internal Enterprise Campus by including security functions in each individual element is important for the following reasons:
-
 If the security established at the Enterprise Edge fails, an unprotected Enterprise Campus is vulnerable. Deploying several layers of security increases the protection of the Enterprise Campus, where the most strategic assets usually reside.
If the security established at the Enterprise Edge fails, an unprotected Enterprise Campus is vulnerable. Deploying several layers of security increases the protection of the Enterprise Campus, where the most strategic assets usually reside. -
 Relying on physical security is not enough. For example, as a visitor to the organization, a potential attacker could gain physical access to devices in the Enterprise Campus.
Relying on physical security is not enough. For example, as a visitor to the organization, a potential attacker could gain physical access to devices in the Enterprise Campus. -
 Often external access does not stop at the Enterprise Edge; some applications require at least indirect access to the Enterprise Campus resources. Strong security must protect access to these resources.
Often external access does not stop at the Enterprise Edge; some applications require at least indirect access to the Enterprise Campus resources. Strong security must protect access to these resources.
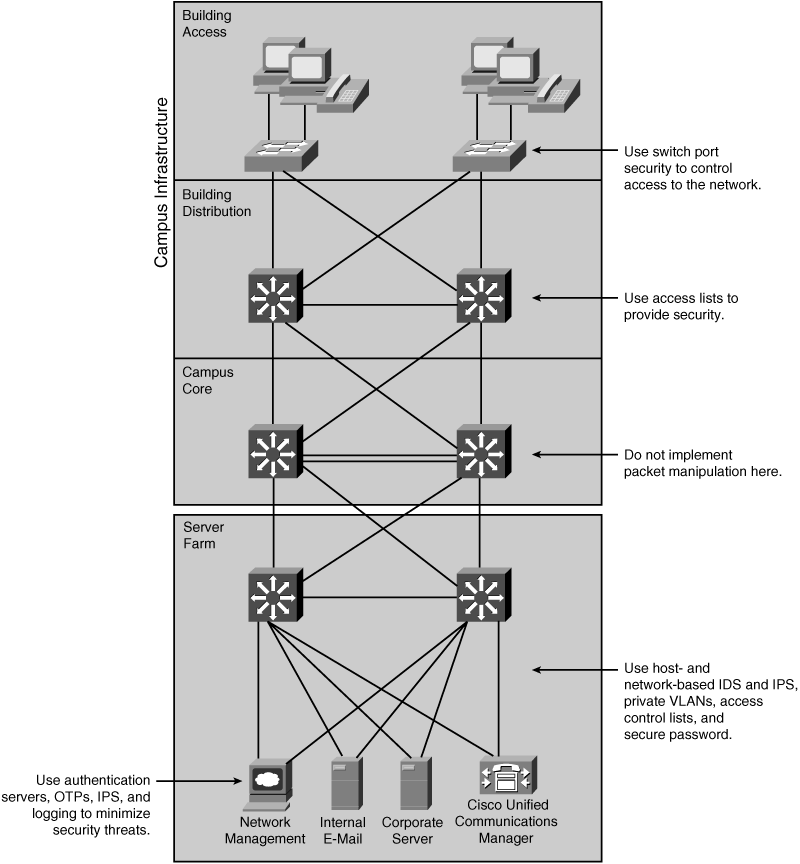
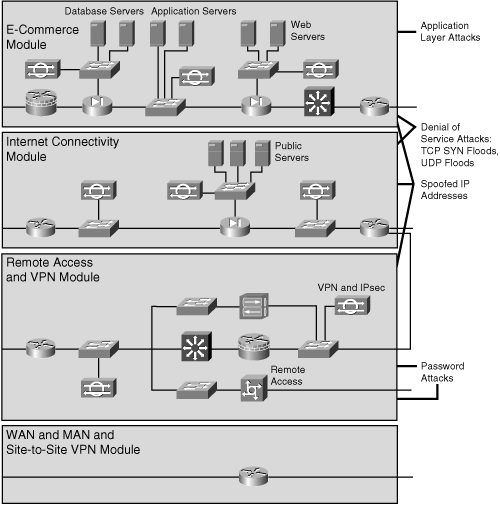
![]() Figure 3-15 shows how internal security can be designed into the Cisco Enterprise Architecture.
Figure 3-15 shows how internal security can be designed into the Cisco Enterprise Architecture.
![]() The following are some recommended security practices in each module:
The following are some recommended security practices in each module:
-
 At the Building Access layer, access is controlled at the port level using the data link layer information. Some examples are filtering based on media access control addresses and IEEE 802.1X port authentication.
At the Building Access layer, access is controlled at the port level using the data link layer information. Some examples are filtering based on media access control addresses and IEEE 802.1X port authentication. -
 The Building Distribution layer performs filtering to keep unnecessary traffic from the Campus Core. This packet filtering can be considered a security function because it does prevent some undesired access to other modules. Given that switches in the Building Distribution layer are typically multilayer switches (and are therefore Layer 3–aware), this is the first place on the data path in which filtering based on network layer information can be performed.
The Building Distribution layer performs filtering to keep unnecessary traffic from the Campus Core. This packet filtering can be considered a security function because it does prevent some undesired access to other modules. Given that switches in the Building Distribution layer are typically multilayer switches (and are therefore Layer 3–aware), this is the first place on the data path in which filtering based on network layer information can be performed. -
 The Campus Core layer is a high-speed switching backbone and should be designed to switch packets as quickly as possible; it should not perform any security functions, because doing so would slow down the switching of packets.
The Campus Core layer is a high-speed switching backbone and should be designed to switch packets as quickly as possible; it should not perform any security functions, because doing so would slow down the switching of packets. -
 The Server Farm module’s primary goal is to provide application services to end users and devices. Enterprises often overlook the Server Farm module from a security perspective. Given the high degree of access that most employees have to these servers, they often become the primary goal of internally originated attacks. Simply relying on effective passwords does not provide a comprehensive attack mitigation strategy. Using host-based and network-based IPSs and IDSs, private VLANs, and access control provides a much more comprehensive attack response. For example, onboard IDS within the Server Farm’s multilayer switches inspects traffic flows.
The Server Farm module’s primary goal is to provide application services to end users and devices. Enterprises often overlook the Server Farm module from a security perspective. Given the high degree of access that most employees have to these servers, they often become the primary goal of internally originated attacks. Simply relying on effective passwords does not provide a comprehensive attack mitigation strategy. Using host-based and network-based IPSs and IDSs, private VLANs, and access control provides a much more comprehensive attack response. For example, onboard IDS within the Server Farm’s multilayer switches inspects traffic flows.Note  Private VLANs provide Layer 2 isolation between ports within the same broadcast domain.
Private VLANs provide Layer 2 isolation between ports within the same broadcast domain. -
 The Server Farm module typically includes network management systems to securely manage all devices and hosts within the enterprise architecture. For example, syslog provides important information on security violations and configuration changes by logging security-related events (authentication and so on). An authentication, authorization, and accounting (AAA) security server also works with a one-time password (OTP) server to provide a high level of security to all local and remote users. AAA and OTP authentication reduces the likelihood of a successful password attack.
The Server Farm module typically includes network management systems to securely manage all devices and hosts within the enterprise architecture. For example, syslog provides important information on security violations and configuration changes by logging security-related events (authentication and so on). An authentication, authorization, and accounting (AAA) security server also works with a one-time password (OTP) server to provide a high level of security to all local and remote users. AAA and OTP authentication reduces the likelihood of a successful password attack.
External Threats
![]() When designing security in an enterprise network, the Enterprise Edge is the first line of defense at which potential outside attacks can be stopped. The Enterprise Edge is like a wall with small doors and strong guards that efficiently control any access. The following four attack methods are commonly used in attempts to compromise the integrity of the enterprise network from the outside:
When designing security in an enterprise network, the Enterprise Edge is the first line of defense at which potential outside attacks can be stopped. The Enterprise Edge is like a wall with small doors and strong guards that efficiently control any access. The following four attack methods are commonly used in attempts to compromise the integrity of the enterprise network from the outside:
-
 IP spoofing: An IP spoofing attack occurs when a hacker uses a trusted computer to launch an attack from inside or outside the network. The hacker uses either an IP address that is in the range of a network’s trusted IP addresses or a trusted external IP address that provides access to specified resources on the network. IP spoofing attacks often lead to other types of attacks. For example, a hacker might launch a denial of service (DoS) attack using spoofed source addresses to hide his identity.
IP spoofing: An IP spoofing attack occurs when a hacker uses a trusted computer to launch an attack from inside or outside the network. The hacker uses either an IP address that is in the range of a network’s trusted IP addresses or a trusted external IP address that provides access to specified resources on the network. IP spoofing attacks often lead to other types of attacks. For example, a hacker might launch a denial of service (DoS) attack using spoofed source addresses to hide his identity. -
 Password attacks: Using a packet sniffer to determine usernames and passwords is a simple password attack; however, the term password attack usually refers to repeated brute-force attempts to identify username and password information. Trojan horse programs are another method that can be used to determine this information. A hacker might also use IP spoofing as a first step in a system attack by violating a trust relationship based on source IP addresses. First, however, the system would have to be configured to bypass password authentication so that only a username is required.
Password attacks: Using a packet sniffer to determine usernames and passwords is a simple password attack; however, the term password attack usually refers to repeated brute-force attempts to identify username and password information. Trojan horse programs are another method that can be used to determine this information. A hacker might also use IP spoofing as a first step in a system attack by violating a trust relationship based on source IP addresses. First, however, the system would have to be configured to bypass password authentication so that only a username is required. -
 DoS attacks: DoS attacks focus on making a service unavailable for normal use and are typically accomplished by exhausting some resource limitation on the network or within an operating system or application.
DoS attacks: DoS attacks focus on making a service unavailable for normal use and are typically accomplished by exhausting some resource limitation on the network or within an operating system or application. -
 Application layer attacks: Application layer attacks typically exploit well-known weaknesses in common software programs to gain access to a computer.
Application layer attacks: Application layer attacks typically exploit well-known weaknesses in common software programs to gain access to a computer.
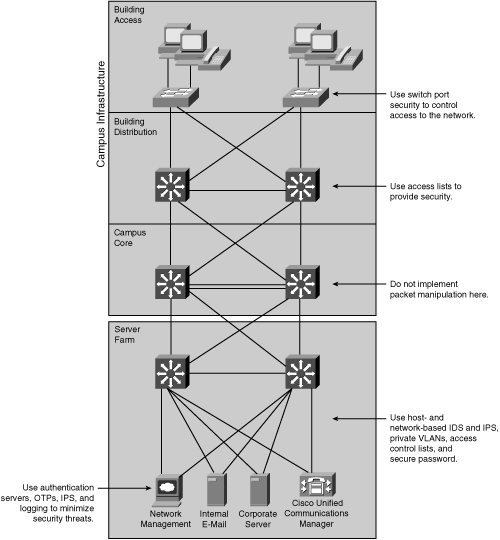
![]() Figure 3-16 shows these four attack methods and how they relate to the Enterprise Edge modules.
Figure 3-16 shows these four attack methods and how they relate to the Enterprise Edge modules.
![]() Because of the complexity of network applications, access control must be extremely granular and flexible yet still provide strong security. Tight borders between outside and inside cannot be defined, because interactions are continuously taking place between the Enterprise Edge and Enterprise Campus. The ease of use of the network applications and resources must be balanced against the security measures imposed on the network users.
Because of the complexity of network applications, access control must be extremely granular and flexible yet still provide strong security. Tight borders between outside and inside cannot be defined, because interactions are continuously taking place between the Enterprise Edge and Enterprise Campus. The ease of use of the network applications and resources must be balanced against the security measures imposed on the network users.
| Note |
|
 High-Availability Services in a Modular Network Design
High-Availability Services in a Modular Network Design
![]() Most enterprise networks carry mission-critical information. Organizations that run such networks are usually interested in protecting the integrity of that information. Along with security, these organizations expect the internetworking platforms to offer a sufficient level of resilience.
Most enterprise networks carry mission-critical information. Organizations that run such networks are usually interested in protecting the integrity of that information. Along with security, these organizations expect the internetworking platforms to offer a sufficient level of resilience.
![]() This section introduces another network infrastructure service: high availability. To ensure adequate connectivity for mission-critical applications, high availability is an essential component of an enterprise environment.
This section introduces another network infrastructure service: high availability. To ensure adequate connectivity for mission-critical applications, high availability is an essential component of an enterprise environment.
Designing High Availability into a Network
![]() Redundant network designs duplicate network links and devices, eliminating single points of failure on the network. The goal is to duplicate components whose failure could disable critical applications.
Redundant network designs duplicate network links and devices, eliminating single points of failure on the network. The goal is to duplicate components whose failure could disable critical applications.
![]() Because redundancy is expensive to deploy and maintain, redundant topologies should be implemented with care. Redundancy adds complexity to the network topology and to network addressing and routing. The level of redundancy should meet the organization’s availability and affordability requirements.
Because redundancy is expensive to deploy and maintain, redundant topologies should be implemented with care. Redundancy adds complexity to the network topology and to network addressing and routing. The level of redundancy should meet the organization’s availability and affordability requirements.
![]() Critical applications, systems, internetworking devices, and links must be identified. Analyze the risk tolerance and the consequences of not implementing redundancy, and ensure that you consider the trade-offs of redundancy versus cost and simplicity versus complexity. Duplicate any component whose failure could disable critical applications.
Critical applications, systems, internetworking devices, and links must be identified. Analyze the risk tolerance and the consequences of not implementing redundancy, and ensure that you consider the trade-offs of redundancy versus cost and simplicity versus complexity. Duplicate any component whose failure could disable critical applications.
![]() Redundancy is not provided by simply duplicating all links. Unless all devices are completely fault-tolerant, redundant links should terminate at different devices; otherwise, devices that are not fault-tolerant become single points of failure.
Redundancy is not provided by simply duplicating all links. Unless all devices are completely fault-tolerant, redundant links should terminate at different devices; otherwise, devices that are not fault-tolerant become single points of failure.
![]() The following types of redundancy may be used in the modules of an enterprise:
The following types of redundancy may be used in the modules of an enterprise:
-
 Device redundancy, including card and port redundancy
Device redundancy, including card and port redundancy -
 Redundant physical connections to critical workstations and servers
Redundant physical connections to critical workstations and servers -
 Route redundancy
Route redundancy -
 Link redundancy
Link redundancy -
 Power redundancy, including redundant power supplies integral to the network devices and redundant power to the building’s physical plant
Power redundancy, including redundant power supplies integral to the network devices and redundant power to the building’s physical plant
High Availability in the Server Farm
![]() Improving the reliability of critical workstations and servers usually depends on the hardware and operating system software in use. Some common ways of connecting include the following:
Improving the reliability of critical workstations and servers usually depends on the hardware and operating system software in use. Some common ways of connecting include the following:
-
 Single attachment: When a workstation or server has traffic to send to a station that is not local, it must know the address of a router on its network segment. If that router fails, the workstation or server needs a mechanism to discover an alternative router. If the workstation or server has a single attachment, it needs a Layer 3 mechanism to dynamically find an alternative router; therefore, the single-attachment method is not recommended. The available mechanisms include Address Resolution Protocol (ARP), Router Discovery Protocol (RDP), routing protocols (such as Routing Information Protocol [RIP]), Hot Standby Router Protocol (HSRP), Gateway Load Balancing Protocol (GLBP), and Virtual Router Redundancy Protocol (VRRP). These router discovery methods are described in the “Router Discovery” sidebar on the next page.
Single attachment: When a workstation or server has traffic to send to a station that is not local, it must know the address of a router on its network segment. If that router fails, the workstation or server needs a mechanism to discover an alternative router. If the workstation or server has a single attachment, it needs a Layer 3 mechanism to dynamically find an alternative router; therefore, the single-attachment method is not recommended. The available mechanisms include Address Resolution Protocol (ARP), Router Discovery Protocol (RDP), routing protocols (such as Routing Information Protocol [RIP]), Hot Standby Router Protocol (HSRP), Gateway Load Balancing Protocol (GLBP), and Virtual Router Redundancy Protocol (VRRP). These router discovery methods are described in the “Router Discovery” sidebar on the next page. -
 Attachment through a redundant transceiver: Physical redundancy with a redundant transceiver attachment is suitable in environments where the workstation hardware or software does not support redundant attachment options.
Attachment through a redundant transceiver: Physical redundancy with a redundant transceiver attachment is suitable in environments where the workstation hardware or software does not support redundant attachment options. -
 Attachment through redundant network interface cards (NIC): Some environments (for example, most UNIX servers) support a redundant attachment through dual NICs (primary and backup); the device driver represents this attachment as a single interface to the operating system.
Attachment through redundant network interface cards (NIC): Some environments (for example, most UNIX servers) support a redundant attachment through dual NICs (primary and backup); the device driver represents this attachment as a single interface to the operating system. -
 Fast EtherChannel or Gigabit EtherChannel port bundles: Fast EtherChannel and Gigabit EtherChannel port bundles group multiple Fast or Gigabit Ethernet ports into a single logical transmission path between a switch and a router, host, or another switch. STP treats this EtherChannel as one logical link. The switch distributes frames across the ports in an EtherChannel. This load balancing was originally done based only on MAC addresses; however, newer implementations can also load-balance based on IP addresses or Layer 4 port numbers. Source, destination, or source and destination addresses or port numbers can be used. If a port within an EtherChannel fails, traffic previously carried over the failed port reverts to the remaining ports within the EtherChannel.
Fast EtherChannel or Gigabit EtherChannel port bundles: Fast EtherChannel and Gigabit EtherChannel port bundles group multiple Fast or Gigabit Ethernet ports into a single logical transmission path between a switch and a router, host, or another switch. STP treats this EtherChannel as one logical link. The switch distributes frames across the ports in an EtherChannel. This load balancing was originally done based only on MAC addresses; however, newer implementations can also load-balance based on IP addresses or Layer 4 port numbers. Source, destination, or source and destination addresses or port numbers can be used. If a port within an EtherChannel fails, traffic previously carried over the failed port reverts to the remaining ports within the EtherChannel.
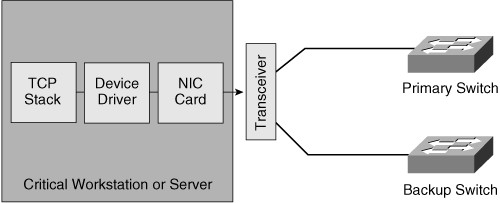
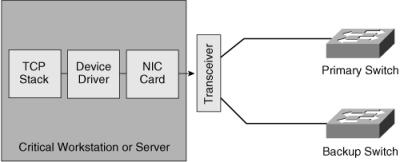
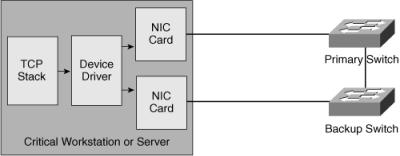
![]() Figure 3-17 shows a server-to-switch connection implemented with a redundant transceiver.
Figure 3-17 shows a server-to-switch connection implemented with a redundant transceiver.
![]() The redundant transceiver has two uplink ports that are usually connected to two access switches. The transceiver activates the backup port after it detects a link failure (carrier loss) on the primary port. The redundant transceiver can detect only physical layer failures; it cannot detect failures inside the switch or failures beyond the first switch. This type of redundancy is most often implemented on servers.
The redundant transceiver has two uplink ports that are usually connected to two access switches. The transceiver activates the backup port after it detects a link failure (carrier loss) on the primary port. The redundant transceiver can detect only physical layer failures; it cannot detect failures inside the switch or failures beyond the first switch. This type of redundancy is most often implemented on servers.
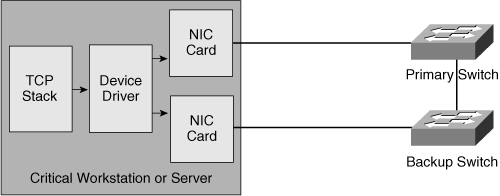
![]() In Figure 3-18, the installation of an additional interface card in the server provides redundancy.
In Figure 3-18, the installation of an additional interface card in the server provides redundancy.
![]() In this case, the device driver presents the configured NIC cards as a single interface (one IP address) to the operating system. If the primary link dies, the backup card activates. The two NICs might use a common MAC address, or they might use two distinct MAC addresses and send gratuitous ARP messages to provide proper IP-to-MAC address mapping on the switches when the backup interface card activates. With a redundant NIC, a VLAN shared between the two access switches is required to support the single IP address on the two server links.
In this case, the device driver presents the configured NIC cards as a single interface (one IP address) to the operating system. If the primary link dies, the backup card activates. The two NICs might use a common MAC address, or they might use two distinct MAC addresses and send gratuitous ARP messages to provide proper IP-to-MAC address mapping on the switches when the backup interface card activates. With a redundant NIC, a VLAN shared between the two access switches is required to support the single IP address on the two server links.
| Note |
|
Designing Route Redundancy
![]() Redundant routes have two purposes:
Redundant routes have two purposes:
-
 To minimize the effect of link failures
To minimize the effect of link failures -
 To minimize the effect of an internetworking device failure
To minimize the effect of an internetworking device failure
![]() Redundant routes might also be used for load balancing when all routes are up.
Redundant routes might also be used for load balancing when all routes are up.
![]() Possible ways to make the connection redundant include the following:
Possible ways to make the connection redundant include the following:
-
 Parallel physical links between switches and routers
Parallel physical links between switches and routers -
 Backup LAN and WAN links (for example, DDR backup for a leased line)
Backup LAN and WAN links (for example, DDR backup for a leased line)
![]() The following are possible ways to make the network redundant:
The following are possible ways to make the network redundant:
-
 A full mesh to provide complete redundancy and good performance
A full mesh to provide complete redundancy and good performance -
 A partial mesh, which is less expensive and more scalable
A partial mesh, which is less expensive and more scalable
![]() The common approach when designing route redundancy is to implement partial redundancy by using a partial mesh instead of a full mesh and backup links to the alternative device. This protects only the most vital parts of the network, such as the links between the layers and concentration devices.
The common approach when designing route redundancy is to implement partial redundancy by using a partial mesh instead of a full mesh and backup links to the alternative device. This protects only the most vital parts of the network, such as the links between the layers and concentration devices.
![]() A full-mesh design forms any-to-any connectivity and is ideal for connecting a reasonably small number of devices. However, as the network topology grows, the number of links required to maintain a full mesh increases exponentially. (The number of links in a full mesh is n(n–1)/2, where n is the number of routers.) As the number of router peers increases, the bandwidth and CPU resources devoted to processing routing updates and service requests also increase.
A full-mesh design forms any-to-any connectivity and is ideal for connecting a reasonably small number of devices. However, as the network topology grows, the number of links required to maintain a full mesh increases exponentially. (The number of links in a full mesh is n(n–1)/2, where n is the number of routers.) As the number of router peers increases, the bandwidth and CPU resources devoted to processing routing updates and service requests also increase.
![]() A partial-mesh network is similar to the full-mesh network with some of its connections removed. A partial-mesh backbone might be appropriate for a campus network in which traffic predominantly goes into one centralized Server Farm module.
A partial-mesh network is similar to the full-mesh network with some of its connections removed. A partial-mesh backbone might be appropriate for a campus network in which traffic predominantly goes into one centralized Server Farm module.
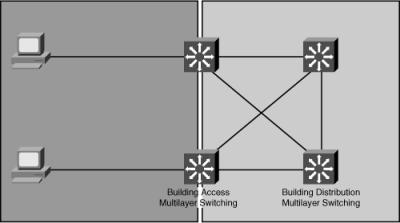
![]() Figure 3-19 illustrates an example of route redundancy in a campus. In this example, the access layer switches are fully meshed with the distribution layer switches. If a link or distribution switch fails, an access layer switch can still communicate with the distribution layer. The multilayer switches select the primary and backup paths between the access and distribution layers based on the link’s metric as computed by the routing protocol algorithm in use. The best path is placed in the forwarding table, and, in the case of equal-cost paths, load sharing takes place.
Figure 3-19 illustrates an example of route redundancy in a campus. In this example, the access layer switches are fully meshed with the distribution layer switches. If a link or distribution switch fails, an access layer switch can still communicate with the distribution layer. The multilayer switches select the primary and backup paths between the access and distribution layers based on the link’s metric as computed by the routing protocol algorithm in use. The best path is placed in the forwarding table, and, in the case of equal-cost paths, load sharing takes place.
| Note |
|
Designing Link Redundancy
![]() It is often necessary to provision redundant media in locations where mission-critical application traffic travels. In Layer 2–switched networks, redundant links are permitted as long as STP is running. STP guarantees one, and only one, active path within a broadcast domain, avoiding problems such as broadcast storms (when a broadcast continuously loops). The redundant path automatically activates when the active path goes down.
It is often necessary to provision redundant media in locations where mission-critical application traffic travels. In Layer 2–switched networks, redundant links are permitted as long as STP is running. STP guarantees one, and only one, active path within a broadcast domain, avoiding problems such as broadcast storms (when a broadcast continuously loops). The redundant path automatically activates when the active path goes down.
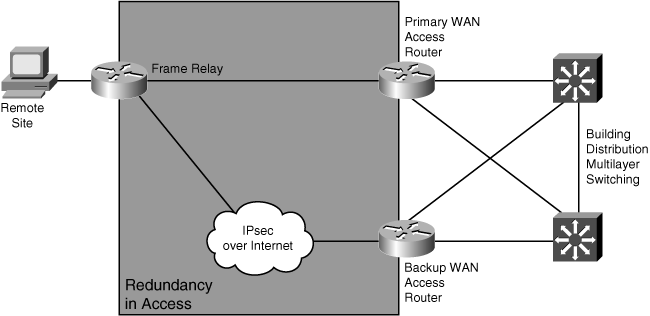
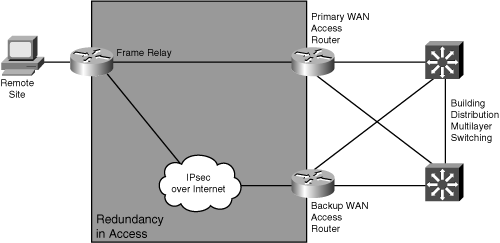
![]() Because WAN links are often critical pieces of the internetwork, redundant media are often deployed in WAN environments. As is the case in Figure 3-20, where a Frame Relay circuit is used in parallel with a backup IPsec connection over the Internet, backup links can use different technologies. It is important that the backup provide sufficient capacity to meet the critical requirements if the primary route fails.
Because WAN links are often critical pieces of the internetwork, redundant media are often deployed in WAN environments. As is the case in Figure 3-20, where a Frame Relay circuit is used in parallel with a backup IPsec connection over the Internet, backup links can use different technologies. It is important that the backup provide sufficient capacity to meet the critical requirements if the primary route fails.
![]() Backup links can be always-on or become active when a primary link goes down or becomes congested.
Backup links can be always-on or become active when a primary link goes down or becomes congested.
 Voice Services in a Modular Network Design
Voice Services in a Modular Network Design
![]() To ensure successful implementation of voice applications, network designers must consider the enterprise services and infrastructure, and its configuration. For example, to support VoIP, the underlying IP infrastructure must be functioning and robust. In other words, don’t even think of adding voice to a network experiencing other problems such as congestion or network failures.
To ensure successful implementation of voice applications, network designers must consider the enterprise services and infrastructure, and its configuration. For example, to support VoIP, the underlying IP infrastructure must be functioning and robust. In other words, don’t even think of adding voice to a network experiencing other problems such as congestion or network failures.
Two Voice Implementations
![]() Voice transport is a general term that can be divided into the following two implementations:
Voice transport is a general term that can be divided into the following two implementations:
-
 VoIP: VoIP uses voice-enabled routers to convert analog voice into IP packets or packetized digital voice channels and route those packets between corresponding locations. Users do not often notice that VoIP is implemented in the network—they use their traditional phones, which are connected to a PBX. However, the PBX is not connected to the PSTN or to another PBX, but to a voice-enabled router that is an entry point to VoIP. Voice-enabled routers can also terminate IP phones using Session Initiation Protocol for call control and signaling.
VoIP: VoIP uses voice-enabled routers to convert analog voice into IP packets or packetized digital voice channels and route those packets between corresponding locations. Users do not often notice that VoIP is implemented in the network—they use their traditional phones, which are connected to a PBX. However, the PBX is not connected to the PSTN or to another PBX, but to a voice-enabled router that is an entry point to VoIP. Voice-enabled routers can also terminate IP phones using Session Initiation Protocol for call control and signaling. -
 IP telephony: For IP telephony, traditional phones are replaced with IP phones. A server for call control and signaling, such as a Cisco Unified Communications Manager, is also used. The IP phone itself performs voice-to-IP conversion, and no voice-enabled routers are required within the enterprise network. However, if a connection to the PSTN is required, a voice-enabled router or other gateway in the Enterprise Edge is added where calls are forwarded to the PSTN.
IP telephony: For IP telephony, traditional phones are replaced with IP phones. A server for call control and signaling, such as a Cisco Unified Communications Manager, is also used. The IP phone itself performs voice-to-IP conversion, and no voice-enabled routers are required within the enterprise network. However, if a connection to the PSTN is required, a voice-enabled router or other gateway in the Enterprise Edge is added where calls are forwarded to the PSTN.Note  Earlier names for the Cisco Unified Communications Manager include Cisco CallManager and Cisco Unified CallManager.
Earlier names for the Cisco Unified Communications Manager include Cisco CallManager and Cisco Unified CallManager.
![]() Both implementations require properly designed networks. Using a modular approach in a voice transport design is especially important because of the voice sensitivity to delay and the complexity of troubleshooting voice networks. All Cisco Enterprise Architecture modules are involved in voice transport design.
Both implementations require properly designed networks. Using a modular approach in a voice transport design is especially important because of the voice sensitivity to delay and the complexity of troubleshooting voice networks. All Cisco Enterprise Architecture modules are involved in voice transport design.
IP Telephony Components
![]() An IP telephony network contains four main voice-specific components:
An IP telephony network contains four main voice-specific components:
-
 IP phones: IP phones are used to place calls in an IP telephony network. They perform voice-to-IP (and vice versa) coding and compression using special hardware. IP phones offer services such as user directory lookups and Internet access. The phones are active network devices that require power to operate; power is supplied through the LAN connection using PoE or with an external power supply.
IP phones: IP phones are used to place calls in an IP telephony network. They perform voice-to-IP (and vice versa) coding and compression using special hardware. IP phones offer services such as user directory lookups and Internet access. The phones are active network devices that require power to operate; power is supplied through the LAN connection using PoE or with an external power supply. -
 Switches with inline power: Switches with inline power (PoE) enable the modular wiring closet infrastructure to provide centralized power for Cisco IP telephony networks. These switches are similar to traditional switches, with an added option to provide power to the LAN ports where IP phones are connected. The switches also perform some basic QoS tasks, such as packet classification, which is required for prioritizing voice through the network.
Switches with inline power: Switches with inline power (PoE) enable the modular wiring closet infrastructure to provide centralized power for Cisco IP telephony networks. These switches are similar to traditional switches, with an added option to provide power to the LAN ports where IP phones are connected. The switches also perform some basic QoS tasks, such as packet classification, which is required for prioritizing voice through the network. -
 Call-processing manager: The call-processing manager, such as a Cisco Unified Communications Manager, provides central call control and configuration management for IP phones. It provides the core functionality to initialize IP telephony devices and to perform call setup and call routing throughout the network. Cisco Unified Communications Manager can be clustered to provide a distributed, scalable, and highly available IP telephony model. Adding more servers to a cluster of servers provides more capacity to the system.
Call-processing manager: The call-processing manager, such as a Cisco Unified Communications Manager, provides central call control and configuration management for IP phones. It provides the core functionality to initialize IP telephony devices and to perform call setup and call routing throughout the network. Cisco Unified Communications Manager can be clustered to provide a distributed, scalable, and highly available IP telephony model. Adding more servers to a cluster of servers provides more capacity to the system. -
 Voice gateway: Voice gateways, also called voice-enabled routers or voice-enabled switches, provide voice services such as voice-to-IP coding and compression, PSTN access, IP packet routing, backup call processing, and voice services. Backup call processing allows voice gateways to take over call processing in case the primary call-processing manager fails. Voice gateways typically support a subset of the call-processing functionality supported by the Cisco Unified Communications Manager.
Voice gateway: Voice gateways, also called voice-enabled routers or voice-enabled switches, provide voice services such as voice-to-IP coding and compression, PSTN access, IP packet routing, backup call processing, and voice services. Backup call processing allows voice gateways to take over call processing in case the primary call-processing manager fails. Voice gateways typically support a subset of the call-processing functionality supported by the Cisco Unified Communications Manager.
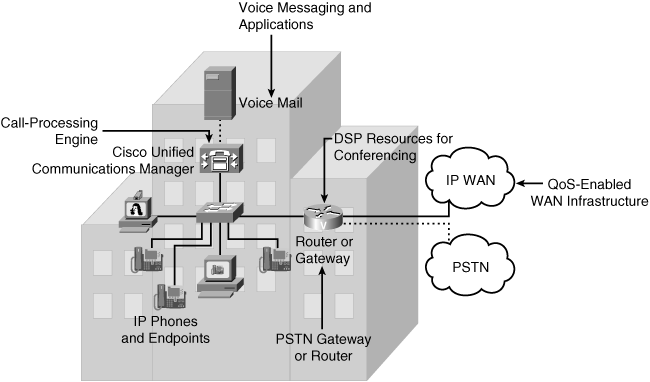
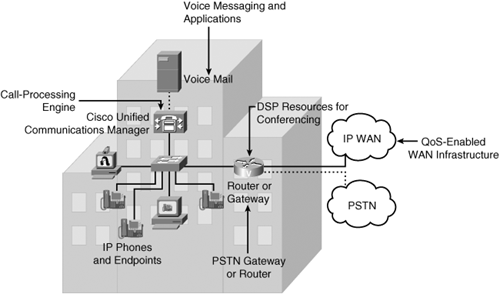
![]() Other components of an IP telephony network include a robust IP network, voice messaging and applications, and digital signal processor resources to process voice functions in hardware, which is much faster than doing it in software. These components are located throughout the enterprise network, as illustrated in Figure 3-21.
Other components of an IP telephony network include a robust IP network, voice messaging and applications, and digital signal processor resources to process voice functions in hardware, which is much faster than doing it in software. These components are located throughout the enterprise network, as illustrated in Figure 3-21.
Modular Approach in Voice Network Design
![]() Implementing voice requires deploying delay-sensitive services from end to end in all enterprise network modules. Use the modular approach to simplify design, implementation, and especially troubleshooting. Voice implementation requires some modifications to the existing enterprise network infrastructure in terms of performance, capacity, and availability because it is an end-to-end solution. For example, clients (IP phones) are located in the Building Access layer, and the call-processing manager is located in the Server Farm module; therefore, all modules in the enterprise network are involved in voice processing and must be adequately considered. Voice affects the various modules of the network as follows:
Implementing voice requires deploying delay-sensitive services from end to end in all enterprise network modules. Use the modular approach to simplify design, implementation, and especially troubleshooting. Voice implementation requires some modifications to the existing enterprise network infrastructure in terms of performance, capacity, and availability because it is an end-to-end solution. For example, clients (IP phones) are located in the Building Access layer, and the call-processing manager is located in the Server Farm module; therefore, all modules in the enterprise network are involved in voice processing and must be adequately considered. Voice affects the various modules of the network as follows:
-
 Building Access layer: IP phones and end-user computers are attached to Layer 2 switches here. Switches provide power to the IP phones and provide QoS packet classification and marking, which is essential for proper voice packet manipulation through the network.
Building Access layer: IP phones and end-user computers are attached to Layer 2 switches here. Switches provide power to the IP phones and provide QoS packet classification and marking, which is essential for proper voice packet manipulation through the network. -
 Building Distribution layer: This layer performs packet reclassifications if the Building Access layer is unable to classify packets or is not within the trusted boundary. It aggregates Building Access layer switches (wiring closets) and provides redundant uplinks to the Campus Core layer.
Building Distribution layer: This layer performs packet reclassifications if the Building Access layer is unable to classify packets or is not within the trusted boundary. It aggregates Building Access layer switches (wiring closets) and provides redundant uplinks to the Campus Core layer. -
 Campus Core layer: The Campus Core layer forms the network’s core. All enterprise network modules are attached to it; therefore, virtually all traffic between application servers and clients traverses the Campus Core. With the advent of wire-speed multilayer gigabit switching devices, LAN backbones have migrated to switched gigabit architectures that combine all the benefits of routing with wire-speed packet forwarding.
Campus Core layer: The Campus Core layer forms the network’s core. All enterprise network modules are attached to it; therefore, virtually all traffic between application servers and clients traverses the Campus Core. With the advent of wire-speed multilayer gigabit switching devices, LAN backbones have migrated to switched gigabit architectures that combine all the benefits of routing with wire-speed packet forwarding. -
 Server Farm module: This module includes multilayer switches with redundant connections to redundant Cisco Unified Communications Managers, which are essential for providing high availability and reliability.
Server Farm module: This module includes multilayer switches with redundant connections to redundant Cisco Unified Communications Managers, which are essential for providing high availability and reliability. -
 Enterprise Edge: The Enterprise Edge extends IP telephony from the Enterprise Campus to remote locations via WANs, the PSTN, and the Internet.
Enterprise Edge: The Enterprise Edge extends IP telephony from the Enterprise Campus to remote locations via WANs, the PSTN, and the Internet.
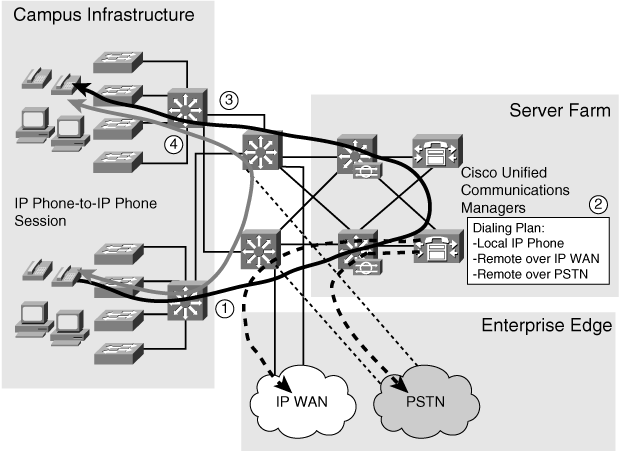
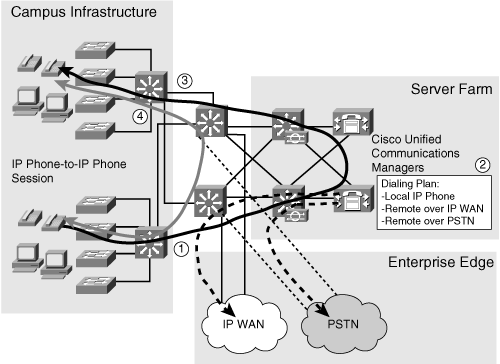
![]() Figure 3-22 shows the voice network solution in the Cisco Enterprise Architecture. It illustrates how a call is initiated on an IP phone, how the call setup goes through the Cisco Unified Communications Manager, and how the end-to-end session between two IP phones is established. Note that Cisco Unified Communications Manager is involved in only the call setup.
Figure 3-22 shows the voice network solution in the Cisco Enterprise Architecture. It illustrates how a call is initiated on an IP phone, how the call setup goes through the Cisco Unified Communications Manager, and how the end-to-end session between two IP phones is established. Note that Cisco Unified Communications Manager is involved in only the call setup.
![]() Calls destined for remote locations traverse the Enterprise Edge through the WAN and MAN and Site-to-Site VPN module or through the Remote Access and VPN module. Calls destined for public phone numbers on the PSTN are routed over the Enterprise Edge through the Remote Access and VPN module. Calls between IP phones traverse the Building Access, Building Distribution, and Campus Core layers, and the Server Farm module. Although call setup uses all these modules, speech employs only the Building Access, Building Distribution, and, in some cases, the Campus Core layers.
Calls destined for remote locations traverse the Enterprise Edge through the WAN and MAN and Site-to-Site VPN module or through the Remote Access and VPN module. Calls destined for public phone numbers on the PSTN are routed over the Enterprise Edge through the Remote Access and VPN module. Calls between IP phones traverse the Building Access, Building Distribution, and Campus Core layers, and the Server Farm module. Although call setup uses all these modules, speech employs only the Building Access, Building Distribution, and, in some cases, the Campus Core layers.
Evaluating the Existing Data Infrastructure for Voice Design
![]() When designing IP telephony, designers must document and evaluate the existing data infrastructure in each enterprise module to help determine upgrade requirements. Items to consider include the following:
When designing IP telephony, designers must document and evaluate the existing data infrastructure in each enterprise module to help determine upgrade requirements. Items to consider include the following:
-
 Performance: Enhanced infrastructure for additional bandwidth, consistent performance, or higher availability, if required, might be necessary for the converging environment. Performance evaluation includes analyzing network maps, device inventory information, and network baseline information. Links and devices such as those with high peak or busy-hour use might have to be upgraded to provide sufficient capacity for the additional voice traffic. Devices with high CPU use, high backplane use, high memory use, queuing drops, or buffer misses might have to be upgraded.
Performance: Enhanced infrastructure for additional bandwidth, consistent performance, or higher availability, if required, might be necessary for the converging environment. Performance evaluation includes analyzing network maps, device inventory information, and network baseline information. Links and devices such as those with high peak or busy-hour use might have to be upgraded to provide sufficient capacity for the additional voice traffic. Devices with high CPU use, high backplane use, high memory use, queuing drops, or buffer misses might have to be upgraded. -
 Availability: Redundancy in all network modules should be reviewed to ensure that the network can meet the recommended IP telephony availability goals with the current or new network design.
Availability: Redundancy in all network modules should be reviewed to ensure that the network can meet the recommended IP telephony availability goals with the current or new network design. -
 Features: Examine the router and switch characteristics—including the chassis, module, and software version—to determine the IP telephony feature capabilities in the existing environment.
Features: Examine the router and switch characteristics—including the chassis, module, and software version—to determine the IP telephony feature capabilities in the existing environment. -
 Capacity: Evaluate the overall network capacity and the impact of IP telephony on a module-by-module basis to ensure that the network meets capacity requirements and that there is no adverse impact on the existing network and application requirements.
Capacity: Evaluate the overall network capacity and the impact of IP telephony on a module-by-module basis to ensure that the network meets capacity requirements and that there is no adverse impact on the existing network and application requirements. -
 Power: Assess the power requirements of the new network infrastructure, ensuring that the additional devices will not oversubscribe existing power. Consider taking advantage of PoE capabilities in devices.
Power: Assess the power requirements of the new network infrastructure, ensuring that the additional devices will not oversubscribe existing power. Consider taking advantage of PoE capabilities in devices.
| Note |
|
 Wireless Services in a Modular Network
Wireless Services in a Modular Network
![]() A wireless LAN (WLAN) supports mobile clients connecting to the enterprise network. The mobile clients do not have a physical connection to the network because WLANs replace the Layer 1 traditional wired network (usually Category 5 cable) with radio frequency (RF) transmissions through the air. WLANs are for local networks, either in-building, line-of-sight outdoor bridging applications, or a combination of both.
A wireless LAN (WLAN) supports mobile clients connecting to the enterprise network. The mobile clients do not have a physical connection to the network because WLANs replace the Layer 1 traditional wired network (usually Category 5 cable) with radio frequency (RF) transmissions through the air. WLANs are for local networks, either in-building, line-of-sight outdoor bridging applications, or a combination of both.
![]() In a wireless network, many issues can arise to prevent the RF signal from reaching all parts of the facility, including multipath distortion, hidden node problems, interference from other wireless sources, and near/far issues. A site survey helps find the regions where these issues occur by defining the contours of RF coverage in a particular facility, discovering regions where multipath distortion can occur, areas where RF interference is high, and finding solutions to eliminate such issues.
In a wireless network, many issues can arise to prevent the RF signal from reaching all parts of the facility, including multipath distortion, hidden node problems, interference from other wireless sources, and near/far issues. A site survey helps find the regions where these issues occur by defining the contours of RF coverage in a particular facility, discovering regions where multipath distortion can occur, areas where RF interference is high, and finding solutions to eliminate such issues.
![]() Privacy and security issues must also be considered in a wireless network. Because WLANs are typically connected to the wired network, all the modules within the enterprise infrastructure must be considered to ensure the success of a wireless deployment.
Privacy and security issues must also be considered in a wireless network. Because WLANs are typically connected to the wired network, all the modules within the enterprise infrastructure must be considered to ensure the success of a wireless deployment.
Centralized WLAN Components
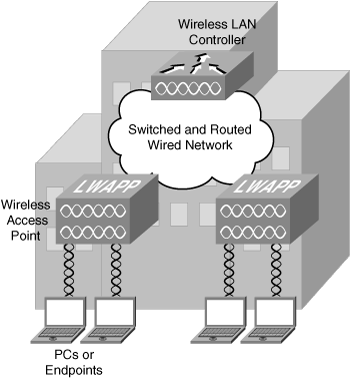
![]() As illustrated in Figure 3-23, the four main components in a centralized WLAN deployment are as follows:
As illustrated in Figure 3-23, the four main components in a centralized WLAN deployment are as follows:
-
 End-user devices: A PC or other end-user device in the access layer uses a wireless NIC to connect to an access point (AP) using radio waves.
End-user devices: A PC or other end-user device in the access layer uses a wireless NIC to connect to an access point (AP) using radio waves. -
 Wireless APs: APs, typically in the access layer, are shared devices that function similar to a hub. Cisco APs can be either lightweight or autonomous.
Wireless APs: APs, typically in the access layer, are shared devices that function similar to a hub. Cisco APs can be either lightweight or autonomous. Lightweight APs are used in centralized WLAN deployments. A lightweight AP receives control and configuration from a WLAN controller (WLC) with which it is associated, providing a centralized point of management and reducing the security concern of a stolen AP. An autonomous AP has a local configuration and requires local management, which might make consistent configurations difficult and add to the cost of network management.
Lightweight APs are used in centralized WLAN deployments. A lightweight AP receives control and configuration from a WLAN controller (WLC) with which it is associated, providing a centralized point of management and reducing the security concern of a stolen AP. An autonomous AP has a local configuration and requires local management, which might make consistent configurations difficult and add to the cost of network management. -
 WLC: A WLC provides management and support for wireless services such as roaming. The WLC is typically in the core layer of an enterprise network.
WLC: A WLC provides management and support for wireless services such as roaming. The WLC is typically in the core layer of an enterprise network. -
 Existing switched and routed wired network: The wireless APs connect to the wired enterprise network.
Existing switched and routed wired network: The wireless APs connect to the wired enterprise network.
| Note |
|
 Application Networking Services in a Modular Network Design
Application Networking Services in a Modular Network Design
![]() Traditional networks handled static web pages, e-mail, and routine client/server traffic. Today, enterprise networks must handle more sophisticated types of network applications that include voice and video. Examples include voice transport, videoconferencing, online training, and audio and video broadcasts. Applications place increasing demands on IT infrastructures as they evolve into highly visible services that represent the face of the business to internal and external audiences.
Traditional networks handled static web pages, e-mail, and routine client/server traffic. Today, enterprise networks must handle more sophisticated types of network applications that include voice and video. Examples include voice transport, videoconferencing, online training, and audio and video broadcasts. Applications place increasing demands on IT infrastructures as they evolve into highly visible services that represent the face of the business to internal and external audiences.
![]() The large amount and variety of data requires that the modern network be application-aware—in other words, be aware of the content carried across it to optimally handle that content. It is no longer enough simply to add more bandwidth as needs grow. Networks have had to become smarter. A new role is emerging for the network as a provider of application infrastructure services that extend the value of applications, either by improving delivery of content to users and other applications or by offloading infrastructure functions that today burden development and operations teams. Application Networking Services (ANS) provide this intelligence.
The large amount and variety of data requires that the modern network be application-aware—in other words, be aware of the content carried across it to optimally handle that content. It is no longer enough simply to add more bandwidth as needs grow. Networks have had to become smarter. A new role is emerging for the network as a provider of application infrastructure services that extend the value of applications, either by improving delivery of content to users and other applications or by offloading infrastructure functions that today burden development and operations teams. Application Networking Services (ANS) provide this intelligence.
ANS Examples
![]() Table 3-1 illustrates some sample application deployment issues that many IT managers face today and how ANS resolves these issues.
Table 3-1 illustrates some sample application deployment issues that many IT managers face today and how ANS resolves these issues.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
ANS Components
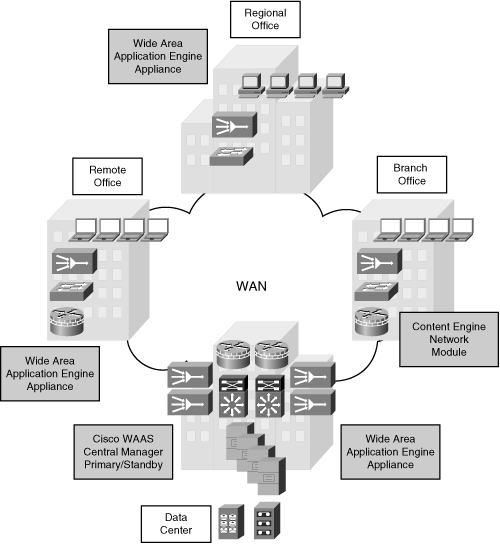
![]() Figure 3-24 illustrates an example of ANS deployed in offices connected over a WAN, providing LAN-like performance to users in the branch, regional, and remote offices. ANS components are deployed symmetrically in the data center and the distant offices. The ANS components in this example are as follows:
Figure 3-24 illustrates an example of ANS deployed in offices connected over a WAN, providing LAN-like performance to users in the branch, regional, and remote offices. ANS components are deployed symmetrically in the data center and the distant offices. The ANS components in this example are as follows:
-
 Cisco Wide Area Application Services (WAAS) software: Cisco WAAS software gives remote offices LAN-like access to centrally hosted applications, servers, storage, and multimedia.
Cisco Wide Area Application Services (WAAS) software: Cisco WAAS software gives remote offices LAN-like access to centrally hosted applications, servers, storage, and multimedia. -
 Cisco Wide Area Application Engine (WAE) appliance: Cisco WAE appliances provide high-performance global LAN-like access to enterprise applications and data. WAEs use either WAAS or Application and Content Networking System [ACNS] software. WAEs help consolidate storage, servers, and so forth in the corporate data center, with only low-cost, easy-to-maintain network appliances in distant offices.
Cisco Wide Area Application Engine (WAE) appliance: Cisco WAE appliances provide high-performance global LAN-like access to enterprise applications and data. WAEs use either WAAS or Application and Content Networking System [ACNS] software. WAEs help consolidate storage, servers, and so forth in the corporate data center, with only low-cost, easy-to-maintain network appliances in distant offices. Each Cisco WAE device can be managed using the embedded command-line interface, the device Web GUI, or the Cisco WAAS Central Manager GUI. The Cisco WAAS Central Manager runs on Cisco WAE appliances and can be configured for high availability by deploying a pair of Cisco WAEs as central managers. The two central manager WAEs automatically share configuration and monitoring data.
Each Cisco WAE device can be managed using the embedded command-line interface, the device Web GUI, or the Cisco WAAS Central Manager GUI. The Cisco WAAS Central Manager runs on Cisco WAE appliances and can be configured for high availability by deploying a pair of Cisco WAEs as central managers. The two central manager WAEs automatically share configuration and monitoring data. -
 Cisco 2600/3600/3700 Series Content Engine Module: Content Engine Modules can be deployed in the data center or branch offices to optimize WAN bandwidth, accelerate deployment of mission-critical web applications, add web content security, and deliver live and on-demand business video.
Cisco 2600/3600/3700 Series Content Engine Module: Content Engine Modules can be deployed in the data center or branch offices to optimize WAN bandwidth, accelerate deployment of mission-critical web applications, add web content security, and deliver live and on-demand business video.
| Note |
|

0 comments
Post a Comment