 Network Hierarchy
Network Hierarchy
![]() This section explains the hierarchical network model, which is composed of the access, distribution, and core layers. The functions generally associated with each of these layers are discussed, as is the most common approach to designing a hierarchical network.
This section explains the hierarchical network model, which is composed of the access, distribution, and core layers. The functions generally associated with each of these layers are discussed, as is the most common approach to designing a hierarchical network.
![]() Historically used in the design of enterprise local-area network and wide-area network data networks, this model works equally well within the functional modules of the Cisco Enterprise Architecture. These modules are discussed later in this chapter, in the section “Using a Modular Approach to Network Design.”
Historically used in the design of enterprise local-area network and wide-area network data networks, this model works equally well within the functional modules of the Cisco Enterprise Architecture. These modules are discussed later in this chapter, in the section “Using a Modular Approach to Network Design.”
 Hierarchical Network Model
Hierarchical Network Model
![]() The hierarchical network model provides a framework that network designers can use to help ensure that the network is flexible and easy to implement and troubleshoot.
The hierarchical network model provides a framework that network designers can use to help ensure that the network is flexible and easy to implement and troubleshoot.
Hierarchical Network Design Layers
![]() As shown in Figure 3-1, the hierarchical network design model consists of three layers:
As shown in Figure 3-1, the hierarchical network design model consists of three layers:
-
 The access layer provides local and remote workgroup or user access to the network.
The access layer provides local and remote workgroup or user access to the network. -
 The distribution layer provides policy-based connectivity.
The distribution layer provides policy-based connectivity. -
 The core (or backbone) layer provides high-speed transport to satisfy the connectivity and transport needs of the distribution layer devices.
The core (or backbone) layer provides high-speed transport to satisfy the connectivity and transport needs of the distribution layer devices.
![]() Each hierarchical layer focuses on specific functions, thereby allowing the network designer to choose the right systems and features based on their function within the model. This approach helps provide more accurate capacity planning and minimize total costs. Figure 3-2 illustrates a sample network showing the mapping to the hierarchical model’s three layers.
Each hierarchical layer focuses on specific functions, thereby allowing the network designer to choose the right systems and features based on their function within the model. This approach helps provide more accurate capacity planning and minimize total costs. Figure 3-2 illustrates a sample network showing the mapping to the hierarchical model’s three layers.
![]() You do not have to implement the hierarchical layers as distinct physical entities; they are defined to aid successful network design and to represent functionality that must exist within a network. The actual manner in which you implement the layers depends on the needs of the network you are designing. Each layer can be implemented in routers or switches, represented by physical media, or combined in a single device. A particular layer can be omitted, but hierarchy should be maintained for optimum performance. The following sections detail the functionality of the three layers and the devices used to implement them.
You do not have to implement the hierarchical layers as distinct physical entities; they are defined to aid successful network design and to represent functionality that must exist within a network. The actual manner in which you implement the layers depends on the needs of the network you are designing. Each layer can be implemented in routers or switches, represented by physical media, or combined in a single device. A particular layer can be omitted, but hierarchy should be maintained for optimum performance. The following sections detail the functionality of the three layers and the devices used to implement them.
 Access Layer Functionality
Access Layer Functionality
![]() This section describes the access layer functions and the interaction of the access layer with the distribution layer and local or remote users.
This section describes the access layer functions and the interaction of the access layer with the distribution layer and local or remote users.
The Role of the Access Layer
![]() The access layer is the concentration point at which clients access the network. Access layer devices control traffic by localizing service requests to the access media.
The access layer is the concentration point at which clients access the network. Access layer devices control traffic by localizing service requests to the access media.
![]() The purpose of the access layer is to grant user access to network resources. Following are the access layer’s characteristics:
The purpose of the access layer is to grant user access to network resources. Following are the access layer’s characteristics:
-
 In the campus environment, the access layer typically incorporates switched LAN devices with ports that provide connectivity for workstations and servers.
In the campus environment, the access layer typically incorporates switched LAN devices with ports that provide connectivity for workstations and servers. -
 In the WAN environment, the access layer for teleworkers or remote sites provides access to the corporate network across some wide-area technology, such as Frame Relay, Multiprotocol Label Switching (MPLS), Integrated Services Digital Network, leased lines, Digital Subscriber Line (DSL) over traditional telephone copper lines, or coaxial cable.
In the WAN environment, the access layer for teleworkers or remote sites provides access to the corporate network across some wide-area technology, such as Frame Relay, Multiprotocol Label Switching (MPLS), Integrated Services Digital Network, leased lines, Digital Subscriber Line (DSL) over traditional telephone copper lines, or coaxial cable. -
 So as not to compromise network integrity, access is granted only to authenticated users or devices (such as those with physical address or logical name authentication). For example, the devices at the access layer must detect whether a telecommuter who is dialing in is legitimate, yet they must require minimal authentication steps for the telecommuter.
So as not to compromise network integrity, access is granted only to authenticated users or devices (such as those with physical address or logical name authentication). For example, the devices at the access layer must detect whether a telecommuter who is dialing in is legitimate, yet they must require minimal authentication steps for the telecommuter.
Layer 2 and Multilayer Switching in the Access Layer
![]() Access can be provided to end users as part of either a Layer 2 (L2) switching environment or a multilayer switching environment.
Access can be provided to end users as part of either a Layer 2 (L2) switching environment or a multilayer switching environment.
| Note |
|
Using Layer 2 Switching in the Access Layer
![]() Access to local workstations and servers can be provided using shared or switched media LANs; VLANs may be used to segment the switched LANs. Each LAN or VLAN is a single broadcast domain.
Access to local workstations and servers can be provided using shared or switched media LANs; VLANs may be used to segment the switched LANs. Each LAN or VLAN is a single broadcast domain.
![]() The access layer aggregates end-user switched 10/100 ports and provides Fast Ethernet, Fast EtherChannel, and Gigabit Ethernet uplinks to the distribution layer to satisfy connectivity requirements and reduce the size of the broadcast domains. You can deploy multiple VLANs, each with its own IP subnet and its own instance of Spanning Tree Protocol (STP) providing alternative paths in case of failure. In this case, Layer 2 trunking (typically using the Institute for Electrical and Electronic Engineers [IEEE] 802.1Q trunking protocol) is used between the access layer switches and the distribution layer switches, with per-VLAN STP on each uplink for load balancing and redundancy, and with a distribution layer multilayer switch providing the inter-VLAN communication for the access layer.
The access layer aggregates end-user switched 10/100 ports and provides Fast Ethernet, Fast EtherChannel, and Gigabit Ethernet uplinks to the distribution layer to satisfy connectivity requirements and reduce the size of the broadcast domains. You can deploy multiple VLANs, each with its own IP subnet and its own instance of Spanning Tree Protocol (STP) providing alternative paths in case of failure. In this case, Layer 2 trunking (typically using the Institute for Electrical and Electronic Engineers [IEEE] 802.1Q trunking protocol) is used between the access layer switches and the distribution layer switches, with per-VLAN STP on each uplink for load balancing and redundancy, and with a distribution layer multilayer switch providing the inter-VLAN communication for the access layer.
| Note |
|
| Note |
|
![]() When RSTP cannot be implemented, Cisco IOS STP features such as UplinkFast, PortFast, and BackboneFast can be used to provide equivalent convergence improvements. These features are described as follows:
When RSTP cannot be implemented, Cisco IOS STP features such as UplinkFast, PortFast, and BackboneFast can be used to provide equivalent convergence improvements. These features are described as follows:
-
 UplinkFast: Enables faster failover on an access layer switch on which dual uplinks connect to the distribution layer. The failover time is reduced by unblocking the blocked uplink port on a switch immediately after root port failure, thereby transitioning it to the forwarding state immediately, without transitioning the port through the listening and learning states.
UplinkFast: Enables faster failover on an access layer switch on which dual uplinks connect to the distribution layer. The failover time is reduced by unblocking the blocked uplink port on a switch immediately after root port failure, thereby transitioning it to the forwarding state immediately, without transitioning the port through the listening and learning states. -
 BackboneFast: If a link fails on the way to the root switch but is not directly connected to the local switch, BackboneFast reduces the convergence time from 50 seconds to between 20 and 30 seconds.
BackboneFast: If a link fails on the way to the root switch but is not directly connected to the local switch, BackboneFast reduces the convergence time from 50 seconds to between 20 and 30 seconds. -
 PortFast: Enables switch ports connected to nonswitch devices (such as workstations) to immediately enter the spanning-tree forwarding state, thereby bypassing the listening and learning states, when they come up. Ports connected only to an end-user device do not have bridging loops, so it is safe to go directly to the forwarding state, significantly reducing the time it takes before the port is usable.
PortFast: Enables switch ports connected to nonswitch devices (such as workstations) to immediately enter the spanning-tree forwarding state, thereby bypassing the listening and learning states, when they come up. Ports connected only to an end-user device do not have bridging loops, so it is safe to go directly to the forwarding state, significantly reducing the time it takes before the port is usable.
| Note |
|
Using Multilayer Switching in the Access Layer
![]() The most common design for remote users is to use multilayer switches or routers. A multilayer switch, or router, is the boundary for broadcast domains and is necessary for communicating between broadcast domains (including VLANs). Access routers provide access to remote office environments using various wide-area technologies combined with multilayer features, such as route propagation, packet filtering, authentication, security, Quality of Service (QoS), and so on. These technologies allow the network to be optimized to satisfy a particular user’s needs. In a dialup connection environment, dial-on-demand routing (DDR) and static routing can be used to control costs.
The most common design for remote users is to use multilayer switches or routers. A multilayer switch, or router, is the boundary for broadcast domains and is necessary for communicating between broadcast domains (including VLANs). Access routers provide access to remote office environments using various wide-area technologies combined with multilayer features, such as route propagation, packet filtering, authentication, security, Quality of Service (QoS), and so on. These technologies allow the network to be optimized to satisfy a particular user’s needs. In a dialup connection environment, dial-on-demand routing (DDR) and static routing can be used to control costs.
Access Layer Example
![]() Figure 3-3 illustrates a sample network in which the campus access layer aggregates end users and provides uplinks to the distribution layer. The access layer switches are dual-attached to the distribution layer switches for high availability.
Figure 3-3 illustrates a sample network in which the campus access layer aggregates end users and provides uplinks to the distribution layer. The access layer switches are dual-attached to the distribution layer switches for high availability.
![]() The access layer can support convergence, high availability, security, QoS, and IP multicast. Some services found at the access layer include establishing a QoS trust boundary, broadcast suppression, and Internet Group Management Protocol (IGMP) snooping.
The access layer can support convergence, high availability, security, QoS, and IP multicast. Some services found at the access layer include establishing a QoS trust boundary, broadcast suppression, and Internet Group Management Protocol (IGMP) snooping.
 Distribution Layer Functionality
Distribution Layer Functionality
![]() This section describes distribution layer functions and the interaction of the distribution layer with the core and access layers.
This section describes distribution layer functions and the interaction of the distribution layer with the core and access layers.
The Role of the Distribution Layer
![]() The distribution layer represents both a separation between the access and core layers and a connection point between the diverse access sites and the core layer. The distribution layer determines department or workgroup access and provides policy-based connectivity.
The distribution layer represents both a separation between the access and core layers and a connection point between the diverse access sites and the core layer. The distribution layer determines department or workgroup access and provides policy-based connectivity.
![]() Following are the characteristics of the distribution layer:
Following are the characteristics of the distribution layer:
-
 Distribution layer devices control access to resources that are available at the core layer and must therefore use bandwidth efficiently.
Distribution layer devices control access to resources that are available at the core layer and must therefore use bandwidth efficiently. -
 In a campus environment, the distribution layer aggregates wiring closet bandwidth by concentrating multiple low-speed access links into a high-speed core link and using switches to segment workgroups and isolate network problems to prevent them from affecting the core layer.
In a campus environment, the distribution layer aggregates wiring closet bandwidth by concentrating multiple low-speed access links into a high-speed core link and using switches to segment workgroups and isolate network problems to prevent them from affecting the core layer. -
 Similarly, in a WAN environment, the distribution layer aggregates WAN connections at the edge of the campus and provides policy-based connectivity.
Similarly, in a WAN environment, the distribution layer aggregates WAN connections at the edge of the campus and provides policy-based connectivity. -
 This layer provides redundant connections for access devices. Redundant connections also provide the opportunity to load-balance between devices.
This layer provides redundant connections for access devices. Redundant connections also provide the opportunity to load-balance between devices. -
 The distribution layer represents a routing boundary between the access and core layers and is where routing and packet manipulation are performed.
The distribution layer represents a routing boundary between the access and core layers and is where routing and packet manipulation are performed. -
 The distribution layer allows the core layer to connect diverse sites while maintaining high performance. To maintain good performance in the core, the distribution layer can redistribute between bandwidth-intensive access-layer routing protocols and optimized core routing protocols. Route filtering is also implemented at the distribution layer.
The distribution layer allows the core layer to connect diverse sites while maintaining high performance. To maintain good performance in the core, the distribution layer can redistribute between bandwidth-intensive access-layer routing protocols and optimized core routing protocols. Route filtering is also implemented at the distribution layer. -
 The distribution layer can summarize routes from the access layer to improve routing protocol performance. For some networks, the distribution layer offers a default route to access-layer routers and runs dynamic routing protocols only when communicating with core routers.
The distribution layer can summarize routes from the access layer to improve routing protocol performance. For some networks, the distribution layer offers a default route to access-layer routers and runs dynamic routing protocols only when communicating with core routers. -
 The distribution layer connects network services to the access layer and implements policies for QoS, security, traffic loading, and routing. For example, the distribution layer addresses different protocols’ QoS needs by implementing policy-based traffic control to isolate backbone and local environments. Policy-based traffic control prioritizes traffic to ensure the best performance for the most time-critical and time-dependent applications.
The distribution layer connects network services to the access layer and implements policies for QoS, security, traffic loading, and routing. For example, the distribution layer addresses different protocols’ QoS needs by implementing policy-based traffic control to isolate backbone and local environments. Policy-based traffic control prioritizes traffic to ensure the best performance for the most time-critical and time-dependent applications. -
 The distribution layer is often the layer that terminates access layer VLANs (broadcast domains); however, this can also be done at the access layer.
The distribution layer is often the layer that terminates access layer VLANs (broadcast domains); however, this can also be done at the access layer. -
 This layer provides any media transitions (for example, between Ethernet and ATM) that must occur.
This layer provides any media transitions (for example, between Ethernet and ATM) that must occur.
Distribution Layer Example
![]() Figure 3-4 shows a sample network with various features of the distribution layer highlighted.
Figure 3-4 shows a sample network with various features of the distribution layer highlighted.
![]() Following are the characteristics of the distribution layer in the routed campus network shown in Figure 3-4:
Following are the characteristics of the distribution layer in the routed campus network shown in Figure 3-4:
-
 Multilayer switching is used toward the access layer (and, in this case, within the access layer).
Multilayer switching is used toward the access layer (and, in this case, within the access layer). -
 Multilayer switching is performed in the distribution layer and extended toward the core layer.
Multilayer switching is performed in the distribution layer and extended toward the core layer. -
 The distribution layer performs two-way route redistribution to exchange the routes between the Routing Information Protocol version 2 (RIPv2) and Enhanced Interior Gateway Routing Protocol (EIGRP) routing processes.
The distribution layer performs two-way route redistribution to exchange the routes between the Routing Information Protocol version 2 (RIPv2) and Enhanced Interior Gateway Routing Protocol (EIGRP) routing processes. -
 Route filtering is configured on the interfaces toward the access layer.
Route filtering is configured on the interfaces toward the access layer. -
 Route summarization is configured on the interfaces toward the core layer.
Route summarization is configured on the interfaces toward the core layer. -
 The distribution layer contains highly redundant connectivity, both toward the access layer and toward the core layer.
The distribution layer contains highly redundant connectivity, both toward the access layer and toward the core layer.
 Core Layer Functionality
Core Layer Functionality
![]() This section describes core layer functions and the interaction of the core layer with the distribution layer.
This section describes core layer functions and the interaction of the core layer with the distribution layer.
The Role of the Core Layer
![]() The function of the core layer is to provide fast and efficient data transport. Characteristics of the core layer include the following:
The function of the core layer is to provide fast and efficient data transport. Characteristics of the core layer include the following:
-
 The core layer is a high-speed backbone that should be designed to switch packets as quickly as possible to optimize communication transport within the network.
The core layer is a high-speed backbone that should be designed to switch packets as quickly as possible to optimize communication transport within the network. -
 Because the core is critical for connectivity, core layer devices are expected to provide a high level of availability and reliability. A fault-tolerant network design ensures that failures do not have a major impact on network connectivity. The core must be able to accommodate failures by rerouting traffic and responding quickly to changes in network topology. The core must provide a high level of redundancy. A full mesh is strongly suggested, and at least a well-connected partial mesh with multiple paths from each device is required.
Because the core is critical for connectivity, core layer devices are expected to provide a high level of availability and reliability. A fault-tolerant network design ensures that failures do not have a major impact on network connectivity. The core must be able to accommodate failures by rerouting traffic and responding quickly to changes in network topology. The core must provide a high level of redundancy. A full mesh is strongly suggested, and at least a well-connected partial mesh with multiple paths from each device is required. -
 The core layer should not perform any packet manipulation, such as checking access lists or filtering, which would slow down the switching of packets.
The core layer should not perform any packet manipulation, such as checking access lists or filtering, which would slow down the switching of packets. -
 The core layer must be manageable.
The core layer must be manageable. -
 The core devices must be able to implement scalable protocols and technologies, and provide alternative paths and load balancing.
The core devices must be able to implement scalable protocols and technologies, and provide alternative paths and load balancing.
Switching in the Core Layer
![]() Layer 2 switching or multilayer switching (routing) can be used in the core layer. Because core devices are responsible for accommodating failures by rerouting traffic and responding quickly to network topology changes, and because performance for routing in the core with a multilayer switch incurs no cost, most implementations have multilayer switching in the core layer. The core layer can then more readily implement scalable protocols and technologies, and provide alternate paths and load balancing.
Layer 2 switching or multilayer switching (routing) can be used in the core layer. Because core devices are responsible for accommodating failures by rerouting traffic and responding quickly to network topology changes, and because performance for routing in the core with a multilayer switch incurs no cost, most implementations have multilayer switching in the core layer. The core layer can then more readily implement scalable protocols and technologies, and provide alternate paths and load balancing.
![]() Figure 3-5 shows an example of Layer 2 switching in the campus core.
Figure 3-5 shows an example of Layer 2 switching in the campus core.
![]() In Figure 3-5, a typical packet between access sites follows these steps:
In Figure 3-5, a typical packet between access sites follows these steps:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Figure 3-6 shows an example of multilayer switching in the campus core.
Figure 3-6 shows an example of multilayer switching in the campus core.
![]() In Figure 3-6, a typical packet between access sites follows these steps:
In Figure 3-6, a typical packet between access sites follows these steps:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 Hierarchical Routing in the WAN
Hierarchical Routing in the WAN
![]() Figure 3-7 shows an example of hierarchical routing in the WAN portion of a network.
Figure 3-7 shows an example of hierarchical routing in the WAN portion of a network.
![]() In Figure 3-7, a typical packet between access sites follows these steps:
In Figure 3-7, a typical packet between access sites follows these steps:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Using a Modular Approach to Network Design
![]() This section expands on the Cisco Service-Oriented Network Architecture (SONA) framework described in Chapter 2 and explores the six modules of the Cisco Enterprise Architecture, with an emphasis on the network infrastructure design considerations.
This section expands on the Cisco Service-Oriented Network Architecture (SONA) framework described in Chapter 2 and explores the six modules of the Cisco Enterprise Architecture, with an emphasis on the network infrastructure design considerations.
| Note |
|
![]() The modularity built into the architecture allows flexibility in network design and facilitates implementation and troubleshooting. Before the details of the architecture itself are introduced, an overview of the evolution of enterprise networks is provided.
The modularity built into the architecture allows flexibility in network design and facilitates implementation and troubleshooting. Before the details of the architecture itself are introduced, an overview of the evolution of enterprise networks is provided.
 Evolution of Enterprise Networks
Evolution of Enterprise Networks
![]() You do not have to go far back in history to find a time when networks were primarily used for file and print services. These networks were isolated LANs that were built throughout the enterprise organization. As organizations interconnected, these isolated LANs and their functions grew from file and print services to include critical applications; the critical nature and complexity of the enterprise networks also grew.
You do not have to go far back in history to find a time when networks were primarily used for file and print services. These networks were isolated LANs that were built throughout the enterprise organization. As organizations interconnected, these isolated LANs and their functions grew from file and print services to include critical applications; the critical nature and complexity of the enterprise networks also grew.
![]() As discussed in the previous section, Cisco introduced the hierarchical model to divide the enterprise network design (separately for both campus and WAN networks) into the access, distribution, and core layers. This solution has several weaknesses, especially for large networks, which are difficult to implement, manage, and, particularly, troubleshoot. Networks became complex, and it was difficult to evaluate a network solution end-to-end through the network. The hierarchical model does not scale well to these large networks.
As discussed in the previous section, Cisco introduced the hierarchical model to divide the enterprise network design (separately for both campus and WAN networks) into the access, distribution, and core layers. This solution has several weaknesses, especially for large networks, which are difficult to implement, manage, and, particularly, troubleshoot. Networks became complex, and it was difficult to evaluate a network solution end-to-end through the network. The hierarchical model does not scale well to these large networks.
![]() An efficient method of solving and scaling a complex task is to break it into smaller, more specialized tasks. Networks can easily be broken down smaller because they have natural physical, logical, and functional boundaries. If they are sufficiently large to require additional design or operational separation, these specialized functional modules can then be designed hierarchically with the access, distribution, and core layers.
An efficient method of solving and scaling a complex task is to break it into smaller, more specialized tasks. Networks can easily be broken down smaller because they have natural physical, logical, and functional boundaries. If they are sufficiently large to require additional design or operational separation, these specialized functional modules can then be designed hierarchically with the access, distribution, and core layers.
![]() The Cisco Enterprise Architecture does just that: It reduces the enterprise network into further physical, logical, and functional boundaries, to scale the hierarchical model. Now, rather than designing networks using only the hierarchical model, networks can be designed using this Cisco Enterprise Architecture, with hierarchy (access, distribution, and core) included in the various modules, as required.
The Cisco Enterprise Architecture does just that: It reduces the enterprise network into further physical, logical, and functional boundaries, to scale the hierarchical model. Now, rather than designing networks using only the hierarchical model, networks can be designed using this Cisco Enterprise Architecture, with hierarchy (access, distribution, and core) included in the various modules, as required.
![]() Designing with this Cisco Enterprise Architecture is not much different from what is already used in practice; it formalizes current practice. There have always been separate hierarchies for the campus (with access, distribution, and core) and for the WAN (the remote office was the access layer, the regional office provided the distribution layer, and the headquarters was the core). The hierarchies tied together at the campus backbone. The Cisco Enterprise Architecture extends the concept of hierarchy from the original two modules: Campus and WAN.
Designing with this Cisco Enterprise Architecture is not much different from what is already used in practice; it formalizes current practice. There have always been separate hierarchies for the campus (with access, distribution, and core) and for the WAN (the remote office was the access layer, the regional office provided the distribution layer, and the headquarters was the core). The hierarchies tied together at the campus backbone. The Cisco Enterprise Architecture extends the concept of hierarchy from the original two modules: Campus and WAN.
 Cisco SONA Framework
Cisco SONA Framework
![]() As illustrated in Figure 3-8, the Cisco SONA provides an enterprise-wide framework that integrates the entire network—campus, data center, enterprise edge, WAN, branches, and teleworkers—offering staff secure access to the tools, processes, and services they require.
As illustrated in Figure 3-8, the Cisco SONA provides an enterprise-wide framework that integrates the entire network—campus, data center, enterprise edge, WAN, branches, and teleworkers—offering staff secure access to the tools, processes, and services they require.
![]() The modules of the Cisco Enterprise Architecture represent focused views of each of the places in the network described in the SONA framework. Each module has a distinct network infrastructure and distinct services; network applications extend between the modules.
The modules of the Cisco Enterprise Architecture represent focused views of each of the places in the network described in the SONA framework. Each module has a distinct network infrastructure and distinct services; network applications extend between the modules.
 Functional Areas of the Cisco Enterprise Architecture
Functional Areas of the Cisco Enterprise Architecture
![]() At the first layer of modularity in the Cisco Enterprise Architecture, the entire network is divided into functional components—functional areas that contain network modules—while still maintaining the hierarchical concept of the core-distribution-access layers within the network modules as needed.
At the first layer of modularity in the Cisco Enterprise Architecture, the entire network is divided into functional components—functional areas that contain network modules—while still maintaining the hierarchical concept of the core-distribution-access layers within the network modules as needed.
| Note |
|
![]() The Cisco Enterprise Architecture comprises the following six major functional areas (also called modules):
The Cisco Enterprise Architecture comprises the following six major functional areas (also called modules):
-
 Enterprise Campus
Enterprise Campus -
 Enterprise Edge
Enterprise Edge -
 Service Provider
Service Provider -
 Enterprise Branch
Enterprise Branch -
 Enterprise Data Center
Enterprise Data Center -
 Enterprise Teleworker
Enterprise Teleworker
| Note |
|
![]() Figure 3-9 illustrates the modules within the Cisco Enterprise Architecture.
Figure 3-9 illustrates the modules within the Cisco Enterprise Architecture.
| Note |
|
![]() The Cisco Enterprise Campus Architecture combines a core infrastructure of intelligent switching and routing with tightly integrated productivity-enhancing technologies, including Cisco Unified Communications, mobility, and advanced security. The architecture provides the enterprise with high availability through a resilient multilayer design, redundant hardware and software features, and automatic procedures for reconfiguring network paths when failures occur. IP multicast capabilities provide optimized bandwidth consumption, and QoS features ensure that real-time traffic (such as voice, video, or critical data) is not dropped or delayed. Integrated security protects against and mitigates the impact of worms, viruses, and other attacks on the network, including at the switch port level. For example, the Cisco enterprise-wide architecture extends support for security standards, such as the IEEE 802.1X port-based network access control standard and the Extensible Authentication Protocol. It also provides the flexibility to add Internet Protocol Security (IPsec) and MPLS virtual private networks (VPN), identity and access management, and VLANs to compartmentalize access. These features help improve performance and security while decreasing costs.
The Cisco Enterprise Campus Architecture combines a core infrastructure of intelligent switching and routing with tightly integrated productivity-enhancing technologies, including Cisco Unified Communications, mobility, and advanced security. The architecture provides the enterprise with high availability through a resilient multilayer design, redundant hardware and software features, and automatic procedures for reconfiguring network paths when failures occur. IP multicast capabilities provide optimized bandwidth consumption, and QoS features ensure that real-time traffic (such as voice, video, or critical data) is not dropped or delayed. Integrated security protects against and mitigates the impact of worms, viruses, and other attacks on the network, including at the switch port level. For example, the Cisco enterprise-wide architecture extends support for security standards, such as the IEEE 802.1X port-based network access control standard and the Extensible Authentication Protocol. It also provides the flexibility to add Internet Protocol Security (IPsec) and MPLS virtual private networks (VPN), identity and access management, and VLANs to compartmentalize access. These features help improve performance and security while decreasing costs.
![]() The Cisco Enterprise Edge Architecture offers connectivity to voice, video, and data services outside the enterprise. This module enables the enterprise to use Internet and partner resources, and provide resources for its customers. QoS, service levels, and security are the main issues in the Enterprise Edge.
The Cisco Enterprise Edge Architecture offers connectivity to voice, video, and data services outside the enterprise. This module enables the enterprise to use Internet and partner resources, and provide resources for its customers. QoS, service levels, and security are the main issues in the Enterprise Edge.
![]() The Cisco Enterprise WAN and MAN and Site-to-Site VPN module is part of the Enterprise Edge. It offers the convergence of voice, video, and data services over a single Cisco Unified Communications network, which enables the enterprise to span large geographic areas in a cost-effective manner. QoS, granular service levels, and comprehensive encryption options help ensure the secure delivery of high-quality corporate voice, video, and data resources to all corporate sites, enabling staff to work productively and efficiently wherever they are located. Security is provided with multiservice VPNs (both IPsec and MPLS) over Layer 2 or Layer 3 WANs, hub-and-spoke, or full-mesh topologies.
The Cisco Enterprise WAN and MAN and Site-to-Site VPN module is part of the Enterprise Edge. It offers the convergence of voice, video, and data services over a single Cisco Unified Communications network, which enables the enterprise to span large geographic areas in a cost-effective manner. QoS, granular service levels, and comprehensive encryption options help ensure the secure delivery of high-quality corporate voice, video, and data resources to all corporate sites, enabling staff to work productively and efficiently wherever they are located. Security is provided with multiservice VPNs (both IPsec and MPLS) over Layer 2 or Layer 3 WANs, hub-and-spoke, or full-mesh topologies.
![]() The Cisco Enterprise Data Center Architecture is a cohesive, adaptive network architecture that supports requirements for consolidation, business continuance, and security while enabling emerging service-oriented architectures, virtualization, and on-demand computing. Staff, suppliers, and customers can be provided with secure access to applications and resources, simplifying and streamlining management and significantly reducing overhead. Redundant data centers provide backup using synchronous and asynchronous data and application replication. The network and devices offer server and application load balancing to maximize performance. This architecture allows the enterprise to scale without major changes to the infrastructure. This module can be located either at the campus as a server farm or at a remote facility.
The Cisco Enterprise Data Center Architecture is a cohesive, adaptive network architecture that supports requirements for consolidation, business continuance, and security while enabling emerging service-oriented architectures, virtualization, and on-demand computing. Staff, suppliers, and customers can be provided with secure access to applications and resources, simplifying and streamlining management and significantly reducing overhead. Redundant data centers provide backup using synchronous and asynchronous data and application replication. The network and devices offer server and application load balancing to maximize performance. This architecture allows the enterprise to scale without major changes to the infrastructure. This module can be located either at the campus as a server farm or at a remote facility.
![]() The Cisco Enterprise Branch Architecture allows enterprises to extend head-office applications and services (such as security, Cisco Unified Communications, and advanced application performance) to thousands of remote locations and users or to a small group of branches. Cisco integrates security, switching, network analysis, caching, and converged voice and video services into a series of integrated services routers (ISR) in the branch so that the enterprises can deploy new services without buying new routers. This architecture provides secure access to voice, mission-critical data, and video applications—anywhere, anytime. Advanced routing, VPNs, redundant WAN links, application content caching, and local IP telephony call processing features are available with high levels of resilience for all the branch offices. An optimized network leverages the WAN and LAN to reduce traffic and save bandwidth and operational expenses. The enterprise can easily support branch offices with the capability to centrally configure, monitor, and manage devices located at remote sites, including tools, such as Cisco AutoQoS and the Cisco Router and Security Device Manager graphical user interface QoS wizard, which proactively resolve congestion and bandwidth issues before they affect network performance.
The Cisco Enterprise Branch Architecture allows enterprises to extend head-office applications and services (such as security, Cisco Unified Communications, and advanced application performance) to thousands of remote locations and users or to a small group of branches. Cisco integrates security, switching, network analysis, caching, and converged voice and video services into a series of integrated services routers (ISR) in the branch so that the enterprises can deploy new services without buying new routers. This architecture provides secure access to voice, mission-critical data, and video applications—anywhere, anytime. Advanced routing, VPNs, redundant WAN links, application content caching, and local IP telephony call processing features are available with high levels of resilience for all the branch offices. An optimized network leverages the WAN and LAN to reduce traffic and save bandwidth and operational expenses. The enterprise can easily support branch offices with the capability to centrally configure, monitor, and manage devices located at remote sites, including tools, such as Cisco AutoQoS and the Cisco Router and Security Device Manager graphical user interface QoS wizard, which proactively resolve congestion and bandwidth issues before they affect network performance.
![]() The Cisco Enterprise Teleworker Architecture allows enterprises to securely deliver voice and data services to remote small or home offices (known as small office, home office [SOHO]) over a standard broadband access service, providing a business-resiliency solution for the enterprise and a flexible work environment for employees. Centralized management minimizes the IT support costs, and robust integrated security mitigates the unique security challenges of this environment. Integrated security and identity-based networking services enable the enterprise to extend campus security policies to the teleworker. Staff can securely log in to the network over an always-on VPN and gain access to authorized applications and services from a single cost-effective platform. Productivity can be further enhanced by adding an IP phone, thereby providing cost-effective access to a centralized IP communications system with voice and unified messaging services.
The Cisco Enterprise Teleworker Architecture allows enterprises to securely deliver voice and data services to remote small or home offices (known as small office, home office [SOHO]) over a standard broadband access service, providing a business-resiliency solution for the enterprise and a flexible work environment for employees. Centralized management minimizes the IT support costs, and robust integrated security mitigates the unique security challenges of this environment. Integrated security and identity-based networking services enable the enterprise to extend campus security policies to the teleworker. Staff can securely log in to the network over an always-on VPN and gain access to authorized applications and services from a single cost-effective platform. Productivity can be further enhanced by adding an IP phone, thereby providing cost-effective access to a centralized IP communications system with voice and unified messaging services.
| Note |
|
![]() This architecture allows network designers to focus on only a selected module and its functions. Designers can describe each network application and service on a per-module basis and validate each as part of the complete enterprise network design. Modules can be added to achieve scalability if necessary; for example, an organization can add more Enterprise Campus modules if it has more than one campus.
This architecture allows network designers to focus on only a selected module and its functions. Designers can describe each network application and service on a per-module basis and validate each as part of the complete enterprise network design. Modules can be added to achieve scalability if necessary; for example, an organization can add more Enterprise Campus modules if it has more than one campus.
 Guidelines for Creating an Enterprise Network
Guidelines for Creating an Enterprise Network
![]() When creating an Enterprise network, divide the network into appropriate areas, where the Enterprise Campus includes all devices and connections within the main Campus location; the Enterprise Edge covers all communications with remote locations and the Internet from the perspective of the Enterprise Campus; and the remote modules include the remote branches, teleworkers, and the remote data center. Define clear boundaries between each of the areas.
When creating an Enterprise network, divide the network into appropriate areas, where the Enterprise Campus includes all devices and connections within the main Campus location; the Enterprise Edge covers all communications with remote locations and the Internet from the perspective of the Enterprise Campus; and the remote modules include the remote branches, teleworkers, and the remote data center. Define clear boundaries between each of the areas.
| Note |
|
![]() Figure 3-10 shows an example of dividing a network into an Enterprise Campus area, an Enterprise Edge area, and some remote areas.
Figure 3-10 shows an example of dividing a network into an Enterprise Campus area, an Enterprise Edge area, and some remote areas.
![]() The following sections provide additional details about each of the functional areas and their modules.
The following sections provide additional details about each of the functional areas and their modules.
 Enterprise Campus Modules
Enterprise Campus Modules
![]() This section introduces the Enterprise Campus functional area and describes the purpose of each module therein. It also discusses connections with other modules.
This section introduces the Enterprise Campus functional area and describes the purpose of each module therein. It also discusses connections with other modules.
![]() An enterprise campus site is a large site that is often the corporate headquarters or a major office. Regional offices, SOHOs, and mobile workers might have to connect to the central campus for data and information. As illustrated in Figure 3-11, the Enterprise Campus functional area includes the Campus Infrastructure module and, typically, a Server Farm module.
An enterprise campus site is a large site that is often the corporate headquarters or a major office. Regional offices, SOHOs, and mobile workers might have to connect to the central campus for data and information. As illustrated in Figure 3-11, the Enterprise Campus functional area includes the Campus Infrastructure module and, typically, a Server Farm module.
Campus Infrastructure Module
![]() The Campus Infrastructure design consists of several buildings connected across a Campus Core. The Campus Infrastructure module connects devices within a campus to the Server Farm and Enterprise Edge modules. A single building in a Campus Infrastructure design contains a Building Access layer and a Building Distribution layer. When more buildings are added to the Campus Infrastructure, a backbone or Campus Core layer is added between buildings. The Campus Infrastructure module includes three layers:
The Campus Infrastructure design consists of several buildings connected across a Campus Core. The Campus Infrastructure module connects devices within a campus to the Server Farm and Enterprise Edge modules. A single building in a Campus Infrastructure design contains a Building Access layer and a Building Distribution layer. When more buildings are added to the Campus Infrastructure, a backbone or Campus Core layer is added between buildings. The Campus Infrastructure module includes three layers:
| Note |
|
Building Access Layer
![]() The Building Access layer, located within a campus building, aggregates end users from different workgroups and provides uplinks to the Building Distribution layer. It contains end-user devices such as workstations, Cisco IP phones, and networked printers, connected to Layer 2 access switches; VLANs and STP might also be supported. The Building Access layer provides important services, such as broadcast suppression, protocol filtering, network access, IP multicast, and QoS. For high availability, the access switches are dual-attached to the distribution layer switches. The Building Access layer might also provide Power over Ethernet (PoE) and auxiliary VLANs to support voice services.
The Building Access layer, located within a campus building, aggregates end users from different workgroups and provides uplinks to the Building Distribution layer. It contains end-user devices such as workstations, Cisco IP phones, and networked printers, connected to Layer 2 access switches; VLANs and STP might also be supported. The Building Access layer provides important services, such as broadcast suppression, protocol filtering, network access, IP multicast, and QoS. For high availability, the access switches are dual-attached to the distribution layer switches. The Building Access layer might also provide Power over Ethernet (PoE) and auxiliary VLANs to support voice services.
Building Distribution Layer
![]() The Building Distribution layer aggregates the wiring closets within a building and provides connectivity to the Campus Core layer. It provides aggregation of the access layer networks using multilayer switching. The Building Distribution layer performs routing, QoS, and access control. Requests for data flow into the multilayer switches and onward into the Campus Core layer; responses follow the reverse path. Redundancy and load balancing with the Building Access and Campus Core layer are recommended. For example, in Figure 3-11, the Building Distribution layer has two equal-cost paths into the Campus Core layer, providing fast failure recovery because each distribution switch maintains two equal-cost paths in its routing table to every destination network. If one connection to the Campus Core layer fails, all routes immediately switch over to the remaining path.
The Building Distribution layer aggregates the wiring closets within a building and provides connectivity to the Campus Core layer. It provides aggregation of the access layer networks using multilayer switching. The Building Distribution layer performs routing, QoS, and access control. Requests for data flow into the multilayer switches and onward into the Campus Core layer; responses follow the reverse path. Redundancy and load balancing with the Building Access and Campus Core layer are recommended. For example, in Figure 3-11, the Building Distribution layer has two equal-cost paths into the Campus Core layer, providing fast failure recovery because each distribution switch maintains two equal-cost paths in its routing table to every destination network. If one connection to the Campus Core layer fails, all routes immediately switch over to the remaining path.
Campus Core Layer
![]() The Campus Core layer is the core layer of the Campus Infrastructure module. Within the Enterprise Campus functional area, this high-performance, switched backbone connects the buildings and various parts of the campus. Specifically, this layer interconnects the Building Distribution layer with the Server Farm and the Enterprise Edge modules.
The Campus Core layer is the core layer of the Campus Infrastructure module. Within the Enterprise Campus functional area, this high-performance, switched backbone connects the buildings and various parts of the campus. Specifically, this layer interconnects the Building Distribution layer with the Server Farm and the Enterprise Edge modules.
![]() The Campus Core layer of the Campus Infrastructure module provides redundant and fast-converging connectivity between buildings and with the Server Farm and Enterprise Edge modules. It routes and switches traffic as quickly as possible from one module to another. This module usually uses multilayer switches for high-throughput functions with added routing, QoS, and security features.
The Campus Core layer of the Campus Infrastructure module provides redundant and fast-converging connectivity between buildings and with the Server Farm and Enterprise Edge modules. It routes and switches traffic as quickly as possible from one module to another. This module usually uses multilayer switches for high-throughput functions with added routing, QoS, and security features.
Server Farm Module
![]() A high-capacity, centralized server farm module provides users with internal server resources. In addition, it typically supports network management services for the enterprise, including monitoring, logging, and troubleshooting, and other common management features from end to end.
A high-capacity, centralized server farm module provides users with internal server resources. In addition, it typically supports network management services for the enterprise, including monitoring, logging, and troubleshooting, and other common management features from end to end.
![]() The Server Farm module typically contains internal e-mail and other corporate servers that provide internal users with application, file, print, e-mail, and Domain Name System (DNS) services. As shown in Figure 3-11, because access to these servers is vital, as a best practice, they are typically connected to two different switches to enable full redundancy or load sharing. Moreover, the Server Farm module switches are cross-connected with the Campus Core layer switches, thereby enabling high reliability and availability of all servers in the Server Farm module.
The Server Farm module typically contains internal e-mail and other corporate servers that provide internal users with application, file, print, e-mail, and Domain Name System (DNS) services. As shown in Figure 3-11, because access to these servers is vital, as a best practice, they are typically connected to two different switches to enable full redundancy or load sharing. Moreover, the Server Farm module switches are cross-connected with the Campus Core layer switches, thereby enabling high reliability and availability of all servers in the Server Farm module.
![]() The network management system performs system logging, network monitoring, and general configuration management functions. For management purposes, an out-of-band network connection (a network on which no production traffic travels) to all network components is recommended. For locations where an out-of-band network is impossible (because of geographic or system-related issues), the network management system uses the production network.
The network management system performs system logging, network monitoring, and general configuration management functions. For management purposes, an out-of-band network connection (a network on which no production traffic travels) to all network components is recommended. For locations where an out-of-band network is impossible (because of geographic or system-related issues), the network management system uses the production network.
![]() Network management can provide configuration management for nearly all devices in the network, using a combination of the following two technologies:
Network management can provide configuration management for nearly all devices in the network, using a combination of the following two technologies:
-
 Cisco IOS routers can act as terminal servers to provide a dedicated management network segment to the console ports on the Cisco devices throughout the enterprise by using a reverse-Telnet function.
Cisco IOS routers can act as terminal servers to provide a dedicated management network segment to the console ports on the Cisco devices throughout the enterprise by using a reverse-Telnet function. -
 More extensive management features (software changes, content updates, log and alarm aggregation, and Simple Network Management Protocol [SNMP] management) can be provided through the dedicated out-of-band management network segment.
More extensive management features (software changes, content updates, log and alarm aggregation, and Simple Network Management Protocol [SNMP] management) can be provided through the dedicated out-of-band management network segment.
| Note |
|
Enterprise Campus Guidelines
![]() Follow these guidelines for creating the modules within an Enterprise Campus functional area:
Follow these guidelines for creating the modules within an Enterprise Campus functional area:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 Enterprise Edge Modules
Enterprise Edge Modules
![]() This section describes the components of the Enterprise Edge and explains the importance of each module. The Enterprise Edge infrastructure modules aggregate the connectivity from the various elements outside the campus—using various services and WAN technologies as needed, typically provisioned from service providers—and route the traffic into the Campus Core layer. The Enterprise Edge modules perform security functions when enterprise resources connect across public networks and the Internet. As shown in Figure 3-12 and in the following list, the Enterprise Edge functional area is composed of four main modules:
This section describes the components of the Enterprise Edge and explains the importance of each module. The Enterprise Edge infrastructure modules aggregate the connectivity from the various elements outside the campus—using various services and WAN technologies as needed, typically provisioned from service providers—and route the traffic into the Campus Core layer. The Enterprise Edge modules perform security functions when enterprise resources connect across public networks and the Internet. As shown in Figure 3-12 and in the following list, the Enterprise Edge functional area is composed of four main modules:
-
 E-commerce module: The E-commerce module includes the devices and services necessary for an organization to provide e-commerce applications.
E-commerce module: The E-commerce module includes the devices and services necessary for an organization to provide e-commerce applications. -
 Internet Connectivity module: The Internet Connectivity module provides enterprise users with Internet access.
Internet Connectivity module: The Internet Connectivity module provides enterprise users with Internet access. -
 Remote Access and VPN module: This module terminates VPN traffic and dial-in connections from external users.
Remote Access and VPN module: This module terminates VPN traffic and dial-in connections from external users. -
 WAN and MAN and Site-to-Site VPN module: This module provides connectivity between remote sites and the central site over various WAN technologies.
WAN and MAN and Site-to-Site VPN module: This module provides connectivity between remote sites and the central site over various WAN technologies.
![]() These modules connect to the Campus Core directly or through an optional Edge Distribution module. The optional Edge Distribution module aggregates the connectivity from the various elements at the enterprise edge and routes the traffic into the Campus Core layer. In addition, the Edge Distribution module acts as a boundary between the Enterprise Campus and the Enterprise Edge and is the last line of defense against external attacks; its structure is similar to that of the Building Distribution layer.
These modules connect to the Campus Core directly or through an optional Edge Distribution module. The optional Edge Distribution module aggregates the connectivity from the various elements at the enterprise edge and routes the traffic into the Campus Core layer. In addition, the Edge Distribution module acts as a boundary between the Enterprise Campus and the Enterprise Edge and is the last line of defense against external attacks; its structure is similar to that of the Building Distribution layer.
![]() The following sections detail each of the four main Enterprise Edge modules.
The following sections detail each of the four main Enterprise Edge modules.
E-commerce Module
![]() The E-commerce module enables enterprises to successfully deploy e-commerce applications and take advantage of the opportunities the Internet provides. The majority of traffic is initiated external to the enterprise. All e-commerce transactions pass through a series of intelligent services that provide scalability, security, and high availability within the overall e-commerce network design. To build a successful e-commerce solution, the following network devices might be included:
The E-commerce module enables enterprises to successfully deploy e-commerce applications and take advantage of the opportunities the Internet provides. The majority of traffic is initiated external to the enterprise. All e-commerce transactions pass through a series of intelligent services that provide scalability, security, and high availability within the overall e-commerce network design. To build a successful e-commerce solution, the following network devices might be included:
-
 Web servers: Act as the primary user interface for e-commerce navigation
Web servers: Act as the primary user interface for e-commerce navigation -
 Application servers: Host the various applications
Application servers: Host the various applications -
 Database servers: Contain the application and transaction information that is the heart of the e-commerce business implementation
Database servers: Contain the application and transaction information that is the heart of the e-commerce business implementation -
 Firewalls or firewall routers: Govern communication and provide security between the system’s various users
Firewalls or firewall routers: Govern communication and provide security between the system’s various users -
 Network Intrusion Detection System/Network Intrusion Protection System (NIDS/NIPS) appliances: Monitor key network segments in the module to detect and respond to attacks against the network
Network Intrusion Detection System/Network Intrusion Protection System (NIDS/NIPS) appliances: Monitor key network segments in the module to detect and respond to attacks against the network -
 Multilayer switch with Intrusion Detection System/Intrusion Protection System (IDS/IPS) modules: Provide traffic transport and integrated security monitoring
Multilayer switch with Intrusion Detection System/Intrusion Protection System (IDS/IPS) modules: Provide traffic transport and integrated security monitoring -
 Host-Based Intrusion Protection Systems: Deployed on sensitive core application servers and on dedicated appliances to provide real-time reporting and prevention of attacks as an extra layer of defense
Host-Based Intrusion Protection Systems: Deployed on sensitive core application servers and on dedicated appliances to provide real-time reporting and prevention of attacks as an extra layer of defense
Internet Connectivity Module
![]() The Internet Connectivity module provides internal users with connectivity to Internet services, such as HTTP, FTP, Simple Mail Transfer Protocol (SMTP), and DNS. This module also provides Internet users with access to information published on an enterprise’s public servers, such as HTTP and FTP servers. Internet session initiation is typically from inside the enterprise toward the Internet. Additionally, this module accepts VPN traffic from remote users and remote sites and forwards it to the Remote Access and VPN module, where VPN termination takes place. The Internet Connectivity module is not designed to serve e-commerce applications. Major components used in the Internet Connectivity module include the following:
The Internet Connectivity module provides internal users with connectivity to Internet services, such as HTTP, FTP, Simple Mail Transfer Protocol (SMTP), and DNS. This module also provides Internet users with access to information published on an enterprise’s public servers, such as HTTP and FTP servers. Internet session initiation is typically from inside the enterprise toward the Internet. Additionally, this module accepts VPN traffic from remote users and remote sites and forwards it to the Remote Access and VPN module, where VPN termination takes place. The Internet Connectivity module is not designed to serve e-commerce applications. Major components used in the Internet Connectivity module include the following:
-
 SMTP mail servers: Act as a relay between the Internet and the intranet mail servers.
SMTP mail servers: Act as a relay between the Internet and the intranet mail servers. -
 DNS servers: Serve as the authoritative external DNS server for the enterprise and relay internal DNS requests to the Internet.
DNS servers: Serve as the authoritative external DNS server for the enterprise and relay internal DNS requests to the Internet. -
 Public servers (for example, FTP and HTTP): Provide public information about the organization. Each server on the public services segment contains host-based intrusion detection systems (HIDS) to monitor against any rogue activity at the operating system level and in common server applications including HTTP, FTP, and SMTP.
Public servers (for example, FTP and HTTP): Provide public information about the organization. Each server on the public services segment contains host-based intrusion detection systems (HIDS) to monitor against any rogue activity at the operating system level and in common server applications including HTTP, FTP, and SMTP. -
 Firewalls or firewall routers: Provide network-level protection of resources, provide stateful filtering of traffic, and forward VPN traffic from remote sites and users for termination.
Firewalls or firewall routers: Provide network-level protection of resources, provide stateful filtering of traffic, and forward VPN traffic from remote sites and users for termination. -
 Edge routers: Provide basic filtering and multilayer connectivity to the Internet.
Edge routers: Provide basic filtering and multilayer connectivity to the Internet.
Remote Access and VPN Module
![]() The Remote Access and VPN module terminates remote access traffic and VPN traffic that the Internet Connectivity Module forwards from remote users and remote sites. It also uses the Internet Connectivity module to initiate VPN connections to remote sites. Furthermore, the module terminates dial-in connections received through the public switched telephone network (PSTN) and, after successful authentication, grants dial-in users access to the network. Major components used in the Remote Access and VPN module include the following:
The Remote Access and VPN module terminates remote access traffic and VPN traffic that the Internet Connectivity Module forwards from remote users and remote sites. It also uses the Internet Connectivity module to initiate VPN connections to remote sites. Furthermore, the module terminates dial-in connections received through the public switched telephone network (PSTN) and, after successful authentication, grants dial-in users access to the network. Major components used in the Remote Access and VPN module include the following:
-
 Dial-in access concentrators: Terminate dial-in connections and authenticate individual users
Dial-in access concentrators: Terminate dial-in connections and authenticate individual users -
 Cisco Adaptive Security Appliances (ASA): Terminate IPsec tunnels, authenticate individual remote users, and provide firewall and intrusion prevention services
Cisco Adaptive Security Appliances (ASA): Terminate IPsec tunnels, authenticate individual remote users, and provide firewall and intrusion prevention services -
 Firewalls: Provide network-level protection of resources and stateful filtering of traffic, provide differentiated security for remote access users, authenticate trusted remote sites, and provide connectivity using IPsec tunnels
Firewalls: Provide network-level protection of resources and stateful filtering of traffic, provide differentiated security for remote access users, authenticate trusted remote sites, and provide connectivity using IPsec tunnels -
 NIDS appliances: Provide Layer 4 to Layer 7 monitoring of key network segments in the module
NIDS appliances: Provide Layer 4 to Layer 7 monitoring of key network segments in the module
WAN and MAN and Site-to-Site VPN Module
![]() The WAN and MAN and Site-to-Site VPN module uses various WAN technologies, including site-to-site VPNs, to route traffic between remote sites and the central site. In addition to traditional media (such as leased lines) and circuit-switched data-link technologies (such as Frame Relay and ATM), this module can use more recent WAN physical layer technologies, including Synchronous Optical Network/Synchronous Digital Hierarchy (SDH), cable, DSL, MPLS, Metro Ethernet, wireless, and service provider VPNs. This module incorporates all Cisco devices that support these WAN technologies, and routing, access control, and QoS mechanisms. Although security is not as critical when all links are owned by the enterprise, it should be considered in the network design.
The WAN and MAN and Site-to-Site VPN module uses various WAN technologies, including site-to-site VPNs, to route traffic between remote sites and the central site. In addition to traditional media (such as leased lines) and circuit-switched data-link technologies (such as Frame Relay and ATM), this module can use more recent WAN physical layer technologies, including Synchronous Optical Network/Synchronous Digital Hierarchy (SDH), cable, DSL, MPLS, Metro Ethernet, wireless, and service provider VPNs. This module incorporates all Cisco devices that support these WAN technologies, and routing, access control, and QoS mechanisms. Although security is not as critical when all links are owned by the enterprise, it should be considered in the network design.
Enterprise Edge Guidelines
![]() Follow these guidelines for creating the modules within the Enterprise Edge functional area:
Follow these guidelines for creating the modules within the Enterprise Edge functional area:
|
|
|
|
|
|
|
|
|
|
|
|
 Service Provider Modules
Service Provider Modules
![]() Figure 3-13 shows the modules within the Service Provider functional area. The enterprise itself does not implement these modules; however, they are necessary to enable communication with other networks, using a variety of WAN technologies, and with Internet service providers (ISP). The modules within the Service Provider functional area are as follows:
Figure 3-13 shows the modules within the Service Provider functional area. The enterprise itself does not implement these modules; however, they are necessary to enable communication with other networks, using a variety of WAN technologies, and with Internet service providers (ISP). The modules within the Service Provider functional area are as follows:
![]() The following sections describe each of these modules.
The following sections describe each of these modules.
Internet Service Provider Module
![]() The Internet Service Provider module represents enterprise IP connectivity to an ISP network for basic access to the Internet or for enabling Enterprise Edge services, such as those in the E-commerce, Remote Access and VPN, and Internet Connectivity modules. Enterprises can connect to two or more ISPs to provide redundant connections to the Internet. The physical connection between the ISP and the enterprise can use any of the WAN technologies.
The Internet Service Provider module represents enterprise IP connectivity to an ISP network for basic access to the Internet or for enabling Enterprise Edge services, such as those in the E-commerce, Remote Access and VPN, and Internet Connectivity modules. Enterprises can connect to two or more ISPs to provide redundant connections to the Internet. The physical connection between the ISP and the enterprise can use any of the WAN technologies.
PSTN Module
![]() The PSTN module represents the dialup infrastructure for accessing the enterprise network using ISDN, analog, and wireless telephony (cellular) technologies. Enterprises can also use this infrastructure to back up existing WAN links; WAN backup connections are generally established on demand and torn down after an idle timeout.
The PSTN module represents the dialup infrastructure for accessing the enterprise network using ISDN, analog, and wireless telephony (cellular) technologies. Enterprises can also use this infrastructure to back up existing WAN links; WAN backup connections are generally established on demand and torn down after an idle timeout.
Frame Relay/ATM Module
![]() Traditional Frame Relay and ATM are still used; however, despite the module’s name, it also represents many modern technologies. The technologies in this module include the following:
Traditional Frame Relay and ATM are still used; however, despite the module’s name, it also represents many modern technologies. The technologies in this module include the following:
-
 Frame Relay is a connection-oriented, packet-switching technology designed to efficiently transmit data traffic at data rates of up to those used by E3 and T3 connections. Its capability to connect multiple remote sites across a single physical connection reduces the number of point-to-point physical connections required to link sites.
Frame Relay is a connection-oriented, packet-switching technology designed to efficiently transmit data traffic at data rates of up to those used by E3 and T3 connections. Its capability to connect multiple remote sites across a single physical connection reduces the number of point-to-point physical connections required to link sites.Note  E3 is a European standard with a bandwidth of 34.368 megabits per second (Mbps). T3 is a North American standard with a bandwidth of 44.736 Mbps.
E3 is a European standard with a bandwidth of 34.368 megabits per second (Mbps). T3 is a North American standard with a bandwidth of 44.736 Mbps. -
 ATM is a higher-speed alternative to Frame Relay. It is a high-performance, cell-oriented, switching and multiplexing technology for carrying different types of traffic.
ATM is a higher-speed alternative to Frame Relay. It is a high-performance, cell-oriented, switching and multiplexing technology for carrying different types of traffic. -
 Leased lines provide the simplest permanent point-to-point connection between two remote locations. The carrier (service provider) reserves point-to-point links for the customer’s private use. Because the connection does not carry anyone else’s communications, the carrier can ensure a given level of quality. The fee for the connection is typically a fixed monthly rate.
Leased lines provide the simplest permanent point-to-point connection between two remote locations. The carrier (service provider) reserves point-to-point links for the customer’s private use. Because the connection does not carry anyone else’s communications, the carrier can ensure a given level of quality. The fee for the connection is typically a fixed monthly rate. -
 SONET/SDH are standards for transmission over optical networks. Europe uses SDH, whereas North America uses SONET.
SONET/SDH are standards for transmission over optical networks. Europe uses SDH, whereas North America uses SONET. -
 Cable technology uses existing coaxial cable TV cables. Coupled with cable modems, this technology provides much greater bandwidth than telephone lines and can be used to achieve extremely fast access to the Internet or enterprise network.
Cable technology uses existing coaxial cable TV cables. Coupled with cable modems, this technology provides much greater bandwidth than telephone lines and can be used to achieve extremely fast access to the Internet or enterprise network. -
 DSL uses existing twisted-pair telephone lines to transport high-bandwidth data, such as voice, data, and video. DSL is sometimes referred to as last-mile technology because it is used only for connections from a telephone switching station (at a service provider) to a home or office, not between switching stations. DSL is used by telecommuters to access enterprise networks; however, more and more companies are migrating from traditional Frame Relay to DSL technology using VPNs because of its cost efficiency.
DSL uses existing twisted-pair telephone lines to transport high-bandwidth data, such as voice, data, and video. DSL is sometimes referred to as last-mile technology because it is used only for connections from a telephone switching station (at a service provider) to a home or office, not between switching stations. DSL is used by telecommuters to access enterprise networks; however, more and more companies are migrating from traditional Frame Relay to DSL technology using VPNs because of its cost efficiency. -
 Wireless bridging technology interconnects remote LANs using point-to-point signal transmissions that go through the air over a terrestrial radio or microwave platform, rather than through copper or fiber cables. Wireless bridging requires neither satellite feeds nor local phone service. One of the advantages of bridged wireless is its capability to connect users in remote areas without having to install new cables. However, this technology is limited to shorter distances, and weather conditions can degrade its performance.
Wireless bridging technology interconnects remote LANs using point-to-point signal transmissions that go through the air over a terrestrial radio or microwave platform, rather than through copper or fiber cables. Wireless bridging requires neither satellite feeds nor local phone service. One of the advantages of bridged wireless is its capability to connect users in remote areas without having to install new cables. However, this technology is limited to shorter distances, and weather conditions can degrade its performance. -
 MPLS combines the advantages of multilayer routing with the benefits of Layer 2 switching. With MPLS, labels are assigned to each packet at the edge of the network. Rather than examining the IP packet header information, MPLS nodes use this label to determine how to process the data, resulting in a faster, more scalable, and more flexible WAN solution.
MPLS combines the advantages of multilayer routing with the benefits of Layer 2 switching. With MPLS, labels are assigned to each packet at the edge of the network. Rather than examining the IP packet header information, MPLS nodes use this label to determine how to process the data, resulting in a faster, more scalable, and more flexible WAN solution.
| Note |
|
 Remote Enterprise Modules
Remote Enterprise Modules
![]() The three modules supporting remote enterprise locations are the Enterprise Branch, the Enterprise Data Center, and the Enterprise Teleworker.
The three modules supporting remote enterprise locations are the Enterprise Branch, the Enterprise Data Center, and the Enterprise Teleworker.
Enterprise Branch Module
![]() The Enterprise Branch module extends the enterprise by providing each location with a resilient network architecture with integrated security, Cisco Unified Communications, and wireless mobility.
The Enterprise Branch module extends the enterprise by providing each location with a resilient network architecture with integrated security, Cisco Unified Communications, and wireless mobility.
![]() A branch office generally accommodates employees who have a compelling reason to be located away from the central site, such as a regional sales office. A branch office is sometimes called a remote site, remote office, or sales office. Branch office users must be able to connect to the central site to access company information. Therefore, they benefit from high-speed Internet access, VPN connectivity to corporate intranets, telecommuting capabilities for work-at-home employees, videoconferencing, and economical PSTN-quality voice and fax calls over managed IP networks. The Enterprise Branch module typically uses a simplified version of the Campus Infrastructure module design.
A branch office generally accommodates employees who have a compelling reason to be located away from the central site, such as a regional sales office. A branch office is sometimes called a remote site, remote office, or sales office. Branch office users must be able to connect to the central site to access company information. Therefore, they benefit from high-speed Internet access, VPN connectivity to corporate intranets, telecommuting capabilities for work-at-home employees, videoconferencing, and economical PSTN-quality voice and fax calls over managed IP networks. The Enterprise Branch module typically uses a simplified version of the Campus Infrastructure module design.
Enterprise Data Center Module
![]() The Enterprise Data Center module has an architecture that is similar to the campus Server Farm module discussed earlier. The Enterprise Data Center network architecture allows the network to evolve into a platform that enhances the application, server, and storage solutions and equips organizations to manage increased security, cost, and regulatory requirements while providing the ability to respond quickly to changing business environments. The Enterprise Data Center module may include the following components:
The Enterprise Data Center module has an architecture that is similar to the campus Server Farm module discussed earlier. The Enterprise Data Center network architecture allows the network to evolve into a platform that enhances the application, server, and storage solutions and equips organizations to manage increased security, cost, and regulatory requirements while providing the ability to respond quickly to changing business environments. The Enterprise Data Center module may include the following components:
-
 At the networked infrastructure layer: Gigabit Ethernet, 10-Gigabit Ethernet, or InfiniBand connections, with storage switching and optical transport devices
At the networked infrastructure layer: Gigabit Ethernet, 10-Gigabit Ethernet, or InfiniBand connections, with storage switching and optical transport devicesNote  InfiniBand is a high-speed switched fabric mesh technology.
InfiniBand is a high-speed switched fabric mesh technology. -
 At the interactive services layer: Services include storage fabric services, computer services, security services, and application optimization services
At the interactive services layer: Services include storage fabric services, computer services, security services, and application optimization services -
 At the management layer: Tools include Fabric Manager (for element and network management) and Cisco VFrame (for server and service provisioning)
At the management layer: Tools include Fabric Manager (for element and network management) and Cisco VFrame (for server and service provisioning)
![]() The remote Enterprise Data Center module also needs highly available WAN connectivity with business continuance capabilities to integrate it with the rest of the Cisco Enterprise Architecture. The Server Farm module in the campus can leverage the WAN connectivity of the campus core, but the remote Enterprise Data Center must implement its own WAN connectivity.
The remote Enterprise Data Center module also needs highly available WAN connectivity with business continuance capabilities to integrate it with the rest of the Cisco Enterprise Architecture. The Server Farm module in the campus can leverage the WAN connectivity of the campus core, but the remote Enterprise Data Center must implement its own WAN connectivity.
Enterprise Teleworker Module
![]() The Enterprise Teleworker module provides people in geographically dispersed locations, such as home offices or hotels, with highly secure access to central-site applications and network services.
The Enterprise Teleworker module provides people in geographically dispersed locations, such as home offices or hotels, with highly secure access to central-site applications and network services.
![]() The Enterprise Teleworker module supports a small office with one to several employees or the home office of a telecommuter. Telecommuters might also be mobile users—people who need access while traveling or who do not work at a fixed company site.
The Enterprise Teleworker module supports a small office with one to several employees or the home office of a telecommuter. Telecommuters might also be mobile users—people who need access while traveling or who do not work at a fixed company site.
![]() Depending on the amount of use and the WAN services available, telecommuters working from home tend to use broadband or dialup services. Mobile users tend to access the company network using a broadband Internet service and the VPN client software on their laptops or via an asynchronous dialup connection through the telephone company. Telecommuters working from home might also use a VPN tunnel gateway router for encrypted data and voice traffic to and from the company intranet. These solutions provide simple and safe access for teleworkers to the corporate network site, according to the needs of the users at the sites.
Depending on the amount of use and the WAN services available, telecommuters working from home tend to use broadband or dialup services. Mobile users tend to access the company network using a broadband Internet service and the VPN client software on their laptops or via an asynchronous dialup connection through the telephone company. Telecommuters working from home might also use a VPN tunnel gateway router for encrypted data and voice traffic to and from the company intranet. These solutions provide simple and safe access for teleworkers to the corporate network site, according to the needs of the users at the sites.
![]() The Cisco Teleworker solution provides an easy-to-deploy, centrally managed solution that addresses both the workers’ mobility needs and the enterprise’s needs for lower operational costs, security, productivity, business resiliency, and business responsiveness. Small ISRs form the backbone of the Enterprise Teleworker architecture. An optional IP phone can be provided to take advantage of a centralized Cisco Unified Communications system.
The Cisco Teleworker solution provides an easy-to-deploy, centrally managed solution that addresses both the workers’ mobility needs and the enterprise’s needs for lower operational costs, security, productivity, business resiliency, and business responsiveness. Small ISRs form the backbone of the Enterprise Teleworker architecture. An optional IP phone can be provided to take advantage of a centralized Cisco Unified Communications system.

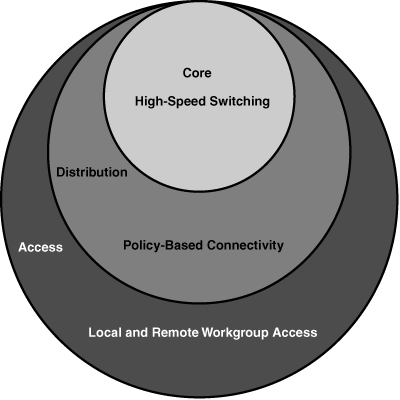
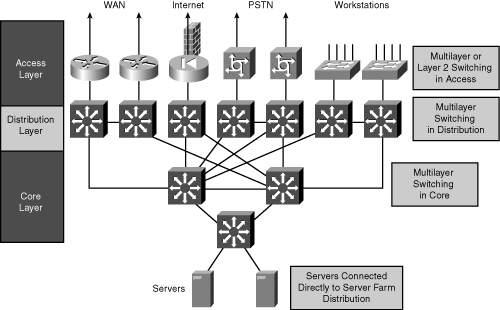
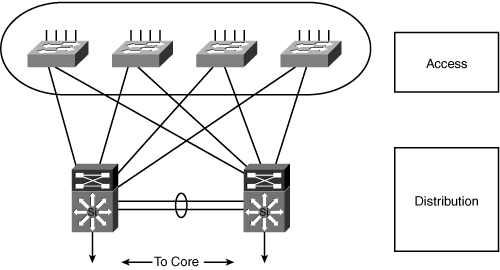
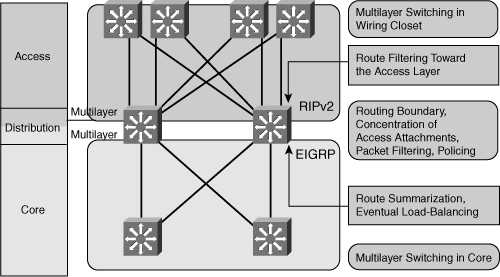
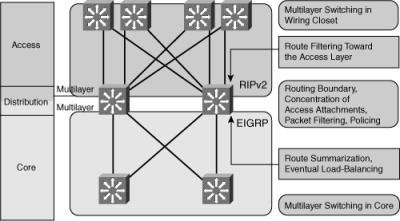
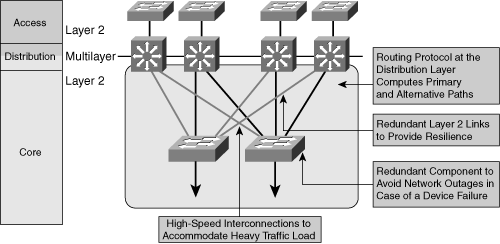
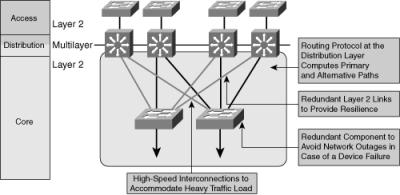
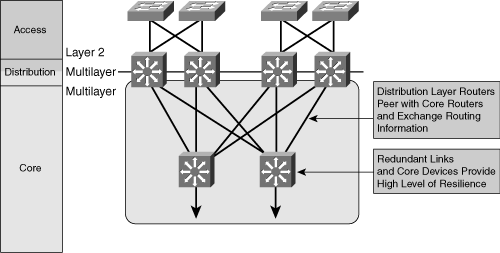
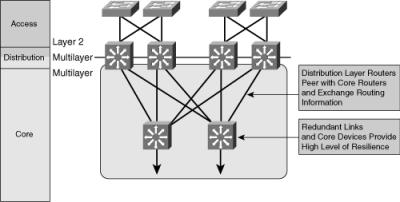
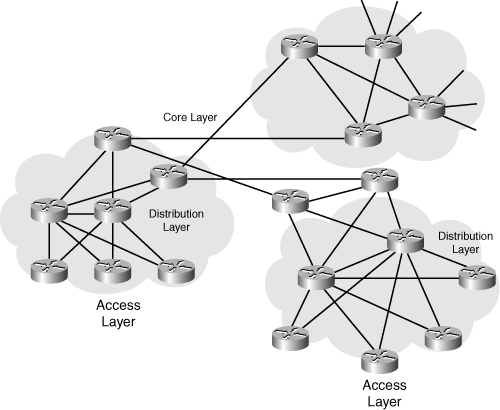
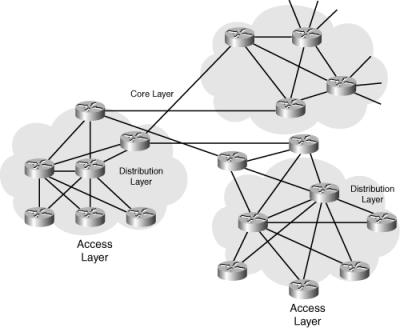
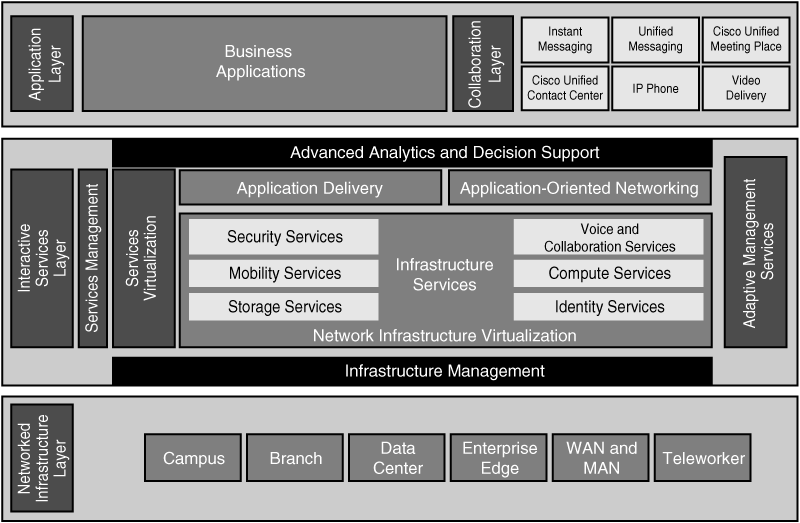
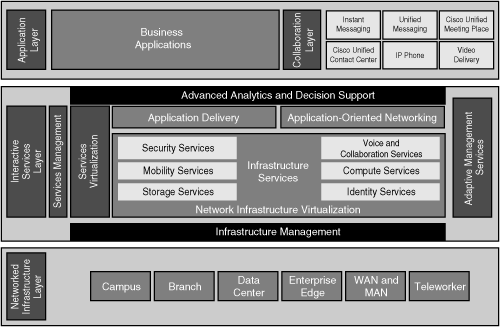
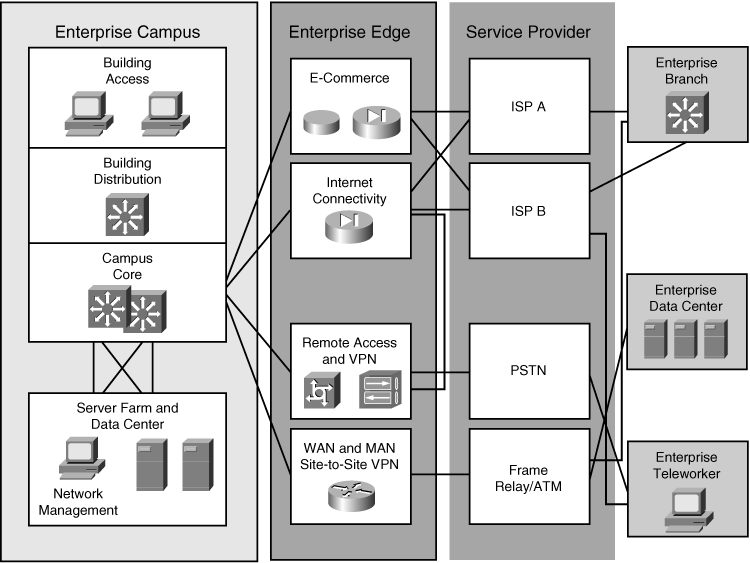
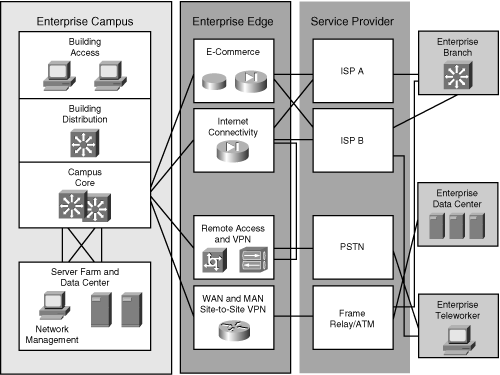
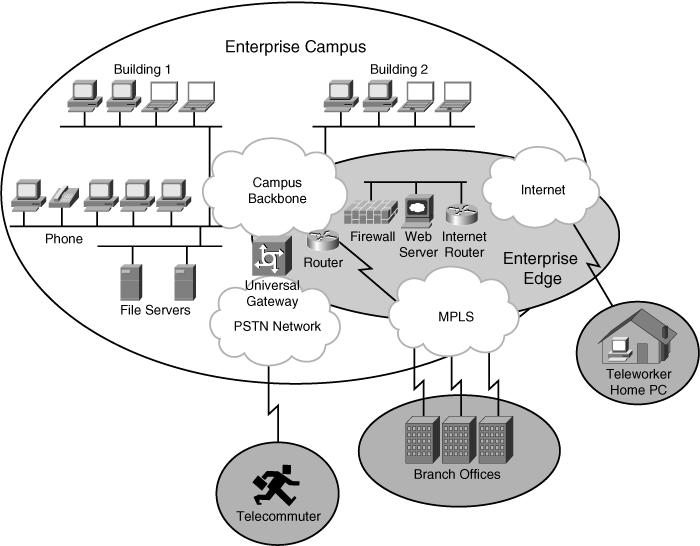
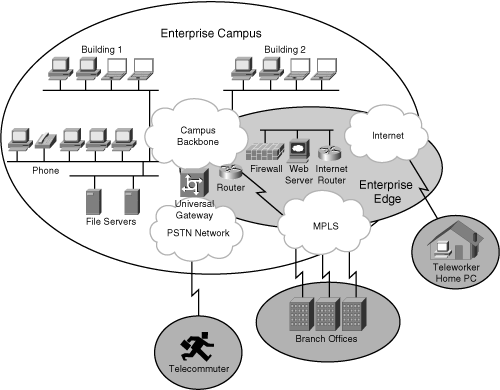
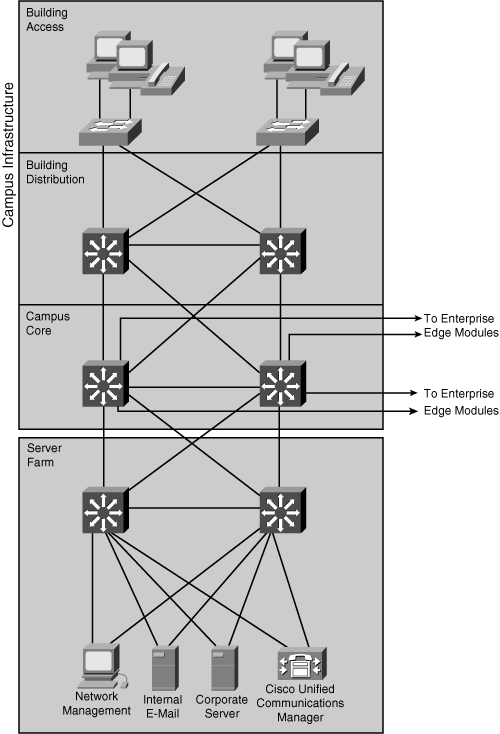
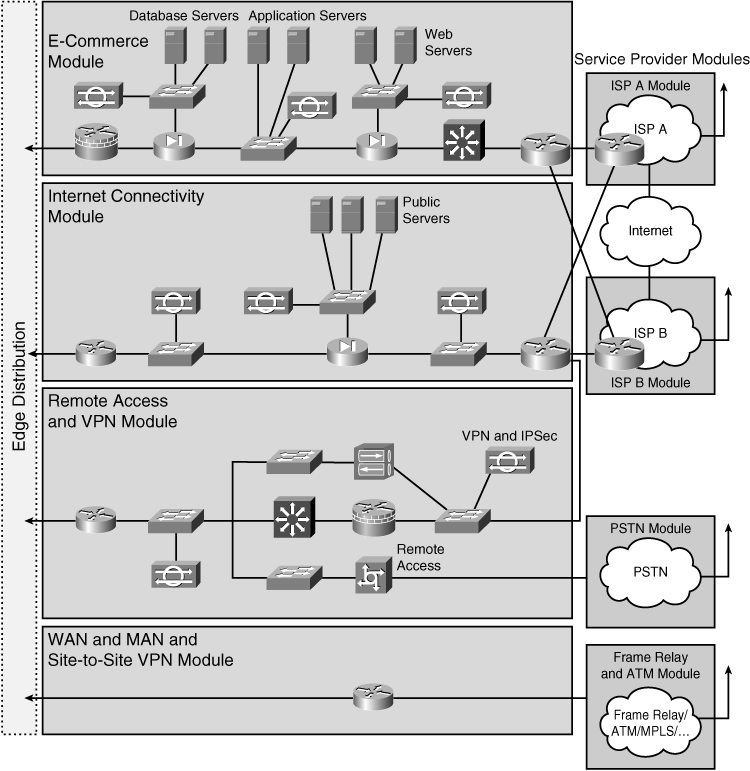
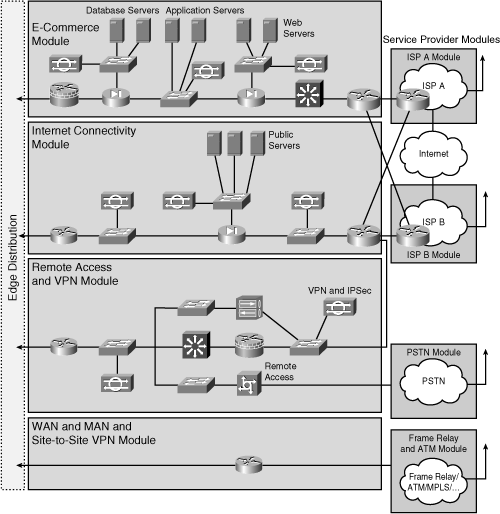
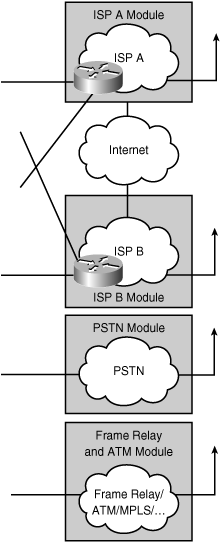
0 comments
Post a Comment