Examining SAN Security
![]() Storage-area networks (SAN) offer a solution to the increasing costs of network and server downtime. Because the main purpose of everything in network security is to secure data, now that data is residing on a SAN, it is essential that you secure the SAN.
Storage-area networks (SAN) offer a solution to the increasing costs of network and server downtime. Because the main purpose of everything in network security is to secure data, now that data is residing on a SAN, it is essential that you secure the SAN.
 Defining SANs
Defining SANs
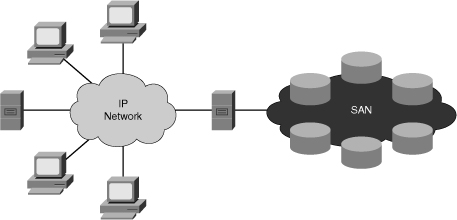
![]() A SAN is a specialized network, as shown in Figure 7-13, that enables fast, reliable access among servers and external storage resources. In a SAN, a storage device is not the exclusive property of any one server. Rather, storage devices are shared among all networked servers as peer resources. Just as you can use a LAN to connect clients to servers, you can use a SAN to connect servers to storage resources, servers to each other, and storage resources to storage resources.
A SAN is a specialized network, as shown in Figure 7-13, that enables fast, reliable access among servers and external storage resources. In a SAN, a storage device is not the exclusive property of any one server. Rather, storage devices are shared among all networked servers as peer resources. Just as you can use a LAN to connect clients to servers, you can use a SAN to connect servers to storage resources, servers to each other, and storage resources to storage resources.
![]() A SAN does not need to be a physically separate network; it can be a dedicated subnet that carries only business-critical I/O traffic between servers and storage devices. A SAN, for example, would not carry general-purpose traffic such as email or other end-user applications. It would be limited to I/O traffic, such as reading a file from a disk or writing a file to a disk.
A SAN does not need to be a physically separate network; it can be a dedicated subnet that carries only business-critical I/O traffic between servers and storage devices. A SAN, for example, would not carry general-purpose traffic such as email or other end-user applications. It would be limited to I/O traffic, such as reading a file from a disk or writing a file to a disk.
![]() By taking this type of network approach, you avoid the unacceptable compromise and performance reduction inherent in a single network for all applications.
By taking this type of network approach, you avoid the unacceptable compromise and performance reduction inherent in a single network for all applications.
![]() Network and server downtime cost companies large sums of money in business and productivity losses. At the same time, the amount of information to be managed and stored is increasing dramatically every year.
Network and server downtime cost companies large sums of money in business and productivity losses. At the same time, the amount of information to be managed and stored is increasing dramatically every year.
![]() SANs offer an answer to the increasing volume of data that must be stored in an enterprise network environment. They offer high-performance access without the burden of having to manage local attached storage. Implementation of a SAN enables users to offload storage traffic from the daily network operations and establish a direct connection between storage media and servers.
SANs offer an answer to the increasing volume of data that must be stored in an enterprise network environment. They offer high-performance access without the burden of having to manage local attached storage. Implementation of a SAN enables users to offload storage traffic from the daily network operations and establish a direct connection between storage media and servers.
 SAN Fundamentals
SAN Fundamentals
![]() SANs are evolving rapidly in the enterprise infrastructure to meet three primary business requirements:
SANs are evolving rapidly in the enterprise infrastructure to meet three primary business requirements:
-
 Reduce capital and operating expenses
Reduce capital and operating expenses -
 Increase agility to support changing business priorities, application requirements, and revenue growth
Increase agility to support changing business priorities, application requirements, and revenue growth -
 Improve long-distance replication, backup, and recovery to meet regulatory requirements and industry best practices
Improve long-distance replication, backup, and recovery to meet regulatory requirements and industry best practices
![]() Cisco can help IT managers meet these requirements with an enterprisewide approach to deploying scalable, highly available, and more easily administered SANs.
Cisco can help IT managers meet these requirements with an enterprisewide approach to deploying scalable, highly available, and more easily administered SANs.
![]() Cisco solutions for intelligent SANs are an integral part of an enterprise data center architecture and provide a better way to access, manage, and protect growing information resources across a consolidated Fibre Channel, Fibre Channel over IP (FCIP), Internet Small Computer Systems Interface (iSCSI), Gigabit Ethernet, or optical network.
Cisco solutions for intelligent SANs are an integral part of an enterprise data center architecture and provide a better way to access, manage, and protect growing information resources across a consolidated Fibre Channel, Fibre Channel over IP (FCIP), Internet Small Computer Systems Interface (iSCSI), Gigabit Ethernet, or optical network.
![]() Most of the major SAN transport technologies are based on the Small Computer Systems Interface (SCSI) communications model. In many ways, a SAN can be described as the merging of SCSI and networking. The SCSI command protocol is the de facto standard that is used extensively in high-performance storage applications. The command part of SCSI can be transported over a Fibre Channel SAN or encapsulated in an IP packet and carried across IP networks.
Most of the major SAN transport technologies are based on the Small Computer Systems Interface (SCSI) communications model. In many ways, a SAN can be described as the merging of SCSI and networking. The SCSI command protocol is the de facto standard that is used extensively in high-performance storage applications. The command part of SCSI can be transported over a Fibre Channel SAN or encapsulated in an IP packet and carried across IP networks.
![]() There are three major SAN transport technologies:
There are three major SAN transport technologies:
-
 Fibre Channel: This technology is the primary SAN transport for host-to-SAN connectivity. Traditionally, SANs have required a separate dedicated infrastructure to interconnect hosts and storage systems. The primary transport protocol for this interconnection has been Fibre Channel. Fibre Channel networks primarily provide a serial transport for the SCSI protocol.
Fibre Channel: This technology is the primary SAN transport for host-to-SAN connectivity. Traditionally, SANs have required a separate dedicated infrastructure to interconnect hosts and storage systems. The primary transport protocol for this interconnection has been Fibre Channel. Fibre Channel networks primarily provide a serial transport for the SCSI protocol. -
 iSCSI: This technology maps SCSI over TCP/IP and is another host-to-SAN connectivity model that is typically used in the LAN. The basic idea of iSCSI is to leverage an investment in existing IP networks to build and extend the SANs. This is accomplished by using the TCP/IP protocol to transport SCSI commands, data, and status between hosts or initiators and storage devices or targets, such as storage subsystems and tape devices.
iSCSI: This technology maps SCSI over TCP/IP and is another host-to-SAN connectivity model that is typically used in the LAN. The basic idea of iSCSI is to leverage an investment in existing IP networks to build and extend the SANs. This is accomplished by using the TCP/IP protocol to transport SCSI commands, data, and status between hosts or initiators and storage devices or targets, such as storage subsystems and tape devices. -
 FCIP: FCIP is a popular SAN-to-SAN connectivity model that is often used over the WAN or metropolitan-area network (MAN). SAN designers can use the open-standard FCIP protocol to break the distance barrier of current Fibre Channel solutions and enable interconnection of SAN islands over extended distances.
FCIP: FCIP is a popular SAN-to-SAN connectivity model that is often used over the WAN or metropolitan-area network (MAN). SAN designers can use the open-standard FCIP protocol to break the distance barrier of current Fibre Channel solutions and enable interconnection of SAN islands over extended distances.
![]() In computer storage, a logical unit number (LUN) is an address for an individual disk drive and, by extension, the disk device itself. The term is used in the SCSI protocol as a way to differentiate individual disk drives within a common SCSI target device, such as a disk array.
In computer storage, a logical unit number (LUN) is an address for an individual disk drive and, by extension, the disk device itself. The term is used in the SCSI protocol as a way to differentiate individual disk drives within a common SCSI target device, such as a disk array.
| Key Topic |
|
![]() LUN masking is an authorization process that makes a LUN available to some hosts and unavailable to others. LUN masking is implemented primarily at the host bus adapter (HBA) level. LUN masking that is implemented at this level is vulnerable to any attack that compromises the HBA, such as tampering with the HBA driver command in an attempt to eventually access the SAN.
LUN masking is an authorization process that makes a LUN available to some hosts and unavailable to others. LUN masking is implemented primarily at the host bus adapter (HBA) level. LUN masking that is implemented at this level is vulnerable to any attack that compromises the HBA, such as tampering with the HBA driver command in an attempt to eventually access the SAN.
![]() The security benefits of LUN masking are limited because with many HBAs it is possible to forge source addresses. LUN masking is mainly a way to protect against misbehaving servers corrupting disks that belong to other servers.
The security benefits of LUN masking are limited because with many HBAs it is possible to forge source addresses. LUN masking is mainly a way to protect against misbehaving servers corrupting disks that belong to other servers.
![]() For example, Windows servers that are attached to a SAN will sometimes corrupt non-Windows volumes by attempting to write Windows volume labels to them. By hiding the LUNs of the non-Windows volumes from the Windows server, this can be prevented, because the Windows server does not even realize the non-Windows volumes exist.
For example, Windows servers that are attached to a SAN will sometimes corrupt non-Windows volumes by attempting to write Windows volume labels to them. By hiding the LUNs of the non-Windows volumes from the Windows server, this can be prevented, because the Windows server does not even realize the non-Windows volumes exist.
| Note |
|
![]() A world wide name (WWN) is a 64-bit address that Fibre Channel networks use to uniquely identify each element in a Fibre Channel network.
A world wide name (WWN) is a 64-bit address that Fibre Channel networks use to uniquely identify each element in a Fibre Channel network.
![]() Zoning can use WWNs to assign security permissions. Zoning can also use name servers in the switches to either allow or block access to particular WWNs in the fabric.
Zoning can use WWNs to assign security permissions. Zoning can also use name servers in the switches to either allow or block access to particular WWNs in the fabric.
![]() The use of WWNs for security purposes is inherently unsecure because the WWN of a device is a user-configurable parameter. Zoning that uses WWNs is susceptible to unauthorized access, because the zone can be bypassed if an attacker is able to spoof the WWN of an authorized HBA. An HBA is an I/O adapter that sits between the bus of the host computer and the Fibre Channel loop, and manages the transfer of information between the two channels.
The use of WWNs for security purposes is inherently unsecure because the WWN of a device is a user-configurable parameter. Zoning that uses WWNs is susceptible to unauthorized access, because the zone can be bypassed if an attacker is able to spoof the WWN of an authorized HBA. An HBA is an I/O adapter that sits between the bus of the host computer and the Fibre Channel loop, and manages the transfer of information between the two channels.
![]() In storage networking, Fibre Channel zoning is the partitioning of a Fibre Channel fabric into smaller subsets. If a SAN contains several storage devices, one device should not necessarily be allowed to interact with all the other devices in the SAN.
In storage networking, Fibre Channel zoning is the partitioning of a Fibre Channel fabric into smaller subsets. If a SAN contains several storage devices, one device should not necessarily be allowed to interact with all the other devices in the SAN.
![]() Zoning is sometimes confused with LUN masking, because they seek the same objectives. However, zoning is implemented on fabric switches, whereas LUN masking is performed on endpoint devices. Zoning is also potentially more secure. Zone members “see” only other members of the zone. Devices can be members of more than one zone.
Zoning is sometimes confused with LUN masking, because they seek the same objectives. However, zoning is implemented on fabric switches, whereas LUN masking is performed on endpoint devices. Zoning is also potentially more secure. Zone members “see” only other members of the zone. Devices can be members of more than one zone.
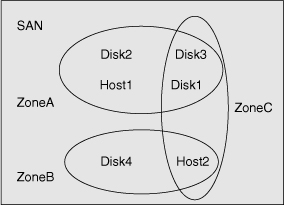
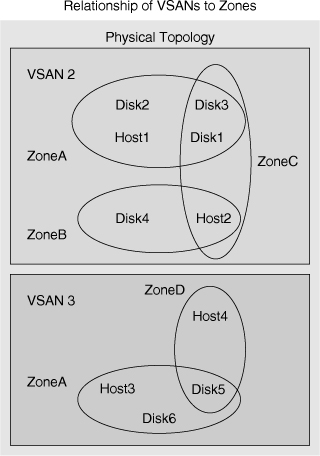
![]() In Figure 7-14, three zones have anywhere from two to four members per zone. All the members of ZoneC also belong to other zones. ZoneA has four members: Host1, Disk1, Disk2, and Disk3. ZoneB has two members: Host2 and Disk4. ZoneC has three members: Host2, Disk1, and Disk3. All the members of ZoneC belong to two zones.
In Figure 7-14, three zones have anywhere from two to four members per zone. All the members of ZoneC also belong to other zones. ZoneA has four members: Host1, Disk1, Disk2, and Disk3. ZoneB has two members: Host2 and Disk4. ZoneC has three members: Host2, Disk1, and Disk3. All the members of ZoneC belong to two zones.
| Note |
|
![]() A virtual storage-area network (VSAN) is a collection of ports from a set of connected Fibre Channel switches that form a virtual fabric. You can partition ports within a single switch into multiple VSANs. In addition, multiple switches can join any number of ports to form a single VSAN. In this manner, VSANs strongly resemble VLANs. Like VLANs, traffic is tagged with the VSAN ID as it crosses Inter-Switch Links.
A virtual storage-area network (VSAN) is a collection of ports from a set of connected Fibre Channel switches that form a virtual fabric. You can partition ports within a single switch into multiple VSANs. In addition, multiple switches can join any number of ports to form a single VSAN. In this manner, VSANs strongly resemble VLANs. Like VLANs, traffic is tagged with the VSAN ID as it crosses Inter-Switch Links.
| Note |
|
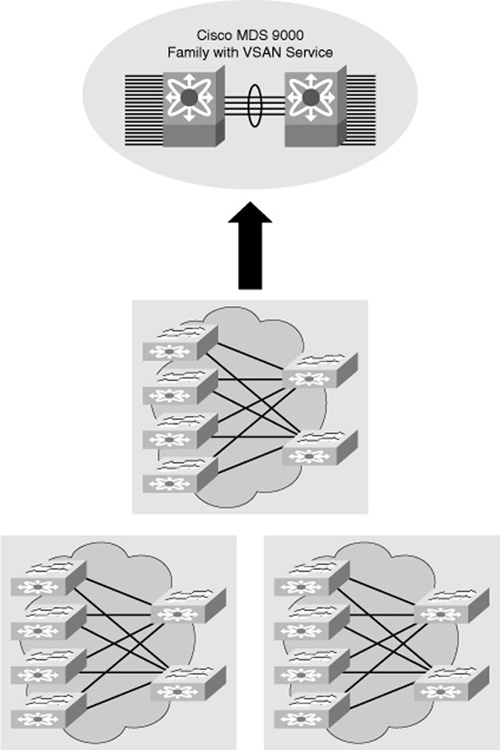
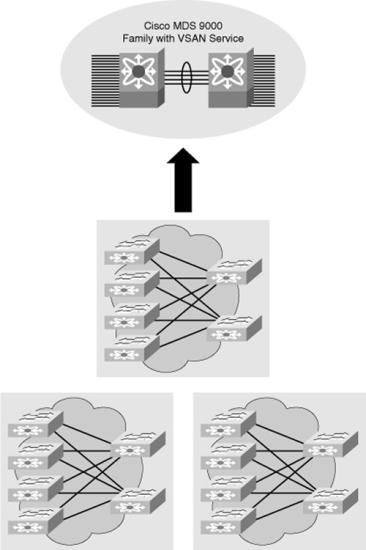
![]() As shown in Figure 7-15, physical SAN islands are virtualized onto common SAN infrastructure.
As shown in Figure 7-15, physical SAN islands are virtualized onto common SAN infrastructure.
![]() VSANs were originally invented by Cisco, but they have now been adopted as an ANSI standard.
VSANs were originally invented by Cisco, but they have now been adopted as an ANSI standard.
 SAN Security Scope
SAN Security Scope
![]() Three areas that you should protect to secure SANs are the SAN fabric, the hosts, and the actual disks. To provide this security, it is important to focus on six areas:
Three areas that you should protect to secure SANs are the SAN fabric, the hosts, and the actual disks. To provide this security, it is important to focus on six areas:
-
 SAN management access: Secure the management services used to administer the SAN.
SAN management access: Secure the management services used to administer the SAN. -
 Fabric access: Secure access to the fabric from devices.
Fabric access: Secure access to the fabric from devices. -
 Target access: Secure access to targets and LUNs.
Target access: Secure access to targets and LUNs. -
 SAN protocol: Secure the protocols used in switch-to-switch communications.
SAN protocol: Secure the protocols used in switch-to-switch communications. -
 IP storage access: Secure FCIP and iSCSI.
IP storage access: Secure FCIP and iSCSI. -
 Data integrity and secrecy: Encrypt data as it crosses networks and encrypt data that is stored on disks.
Data integrity and secrecy: Encrypt data as it crosses networks and encrypt data that is stored on disks.
SAN Management Access Security
![]() Security for SAN management focuses on protecting against the following:
Security for SAN management focuses on protecting against the following:
-
 Disruption of switch processing: The disruption of switch processing can be accomplished with a DoS attack, which causes excessive load on the CPU and thus causes it to be unable to react to fabric events.
Disruption of switch processing: The disruption of switch processing can be accomplished with a DoS attack, which causes excessive load on the CPU and thus causes it to be unable to react to fabric events. -
 Compromise of fabric: Compromised fabric stability is caused by changed configurations, lost configurations, or both that could result in changes to the configured services or ports.
Compromise of fabric: Compromised fabric stability is caused by changed configurations, lost configurations, or both that could result in changes to the configured services or ports. -
 Compromise of data integrity and confidentiality: Data compromise is the breaching of the actual data, either compromising integrity or confidentiality.
Compromise of data integrity and confidentiality: Data compromise is the breaching of the actual data, either compromising integrity or confidentiality.
![]() Many of the fabric and target access security features, explained next, are just as relevant to SAN protocol security as they are to fabric and target access security. In addition to these, switches should include additional SAN protocol security functions such as a capability to reject disruptive fabric-reconfiguration requests from rogue misconfigured or new unconfigured switches being attached to an existing fabric.
Many of the fabric and target access security features, explained next, are just as relevant to SAN protocol security as they are to fabric and target access security. In addition to these, switches should include additional SAN protocol security functions such as a capability to reject disruptive fabric-reconfiguration requests from rogue misconfigured or new unconfigured switches being attached to an existing fabric.
SAN Fabric and Target Access Security
![]() Security for fabric access and target access should focus on three main things:
Security for fabric access and target access should focus on three main things:
-
 Application data integrity: If unauthorized access is gained to application data, integrity and confidentiality have both been breached. It is conceivable that there will also be availability concerns if the data is corrupted or deleted.
Application data integrity: If unauthorized access is gained to application data, integrity and confidentiality have both been breached. It is conceivable that there will also be availability concerns if the data is corrupted or deleted. -
 LUN integrity: If the LUN is compromised, either accidentally or intentionally, data can be lost and availability can be threatened.
LUN integrity: If the LUN is compromised, either accidentally or intentionally, data can be lost and availability can be threatened. -
 Application performance: Application performance security should focus on unnecessary I/O or fabric events that affect availability.
Application performance: Application performance security should focus on unnecessary I/O or fabric events that affect availability.
![]() VSANs and zones are complementary technologies that work well together as a security control in a SAN. The first step in configuring these complimentary protocols is to associate the physical ports with a VSAN, much like associating switch ports with VLANs, and then you logically divide the VSANs into zones.
VSANs and zones are complementary technologies that work well together as a security control in a SAN. The first step in configuring these complimentary protocols is to associate the physical ports with a VSAN, much like associating switch ports with VLANs, and then you logically divide the VSANs into zones.
![]() There are two main methods of zoning:
There are two main methods of zoning:
-
 Soft zoning: Restricts only the fabric name services, showing a device only an allowed subset of devices. Therefore, when a server looks at the content of the fabric, it will see only the devices it is allowed to see. However, any server can still attempt to contact other devices on the network based on their address.
Soft zoning: Restricts only the fabric name services, showing a device only an allowed subset of devices. Therefore, when a server looks at the content of the fabric, it will see only the devices it is allowed to see. However, any server can still attempt to contact other devices on the network based on their address. -
 Hard zoning: In contrast to soft zoning, this method actually restricts communication across a fabric. This zoning is more commonly used because it is more secure.
Hard zoning: In contrast to soft zoning, this method actually restricts communication across a fabric. This zoning is more commonly used because it is more secure.
![]() In Figure 7-16, there are two VSANs, each with multiple zones. Disks and hosts are dedicated to VSANs, although both hosts and disks can belong to multiple zones within a single VSAN. However, disks and hosts cannot span VSANs.
In Figure 7-16, there are two VSANs, each with multiple zones. Disks and hosts are dedicated to VSANs, although both hosts and disks can belong to multiple zones within a single VSAN. However, disks and hosts cannot span VSANs.
IP Storage and Transmission Security
![]() To secure data transmission and data storage, a number of techniques are used. iSCSI leverages many strategies common to IP networking. For example, IP access control lists (ACL) are analogous to Fibre Channel zones, VLANs are similar to VSANs, and IEEE 802.1X port security resembles Fibre Channel port security.
To secure data transmission and data storage, a number of techniques are used. iSCSI leverages many strategies common to IP networking. For example, IP access control lists (ACL) are analogous to Fibre Channel zones, VLANs are similar to VSANs, and IEEE 802.1X port security resembles Fibre Channel port security.
![]() For data transmission security, a number of encryption and authentication protocols are supported, such as Diffie-Hellman Challenge Handshake Authentication Protocol (DH-CHAP), Fibre Channel Authentication Protocol (FCAP), Fibre Channel Password Authentication Protocol (FCPAP), Encapsulating Security Payload (ESP), and Fibre Channel Security Protocol (FC-SP).
For data transmission security, a number of encryption and authentication protocols are supported, such as Diffie-Hellman Challenge Handshake Authentication Protocol (DH-CHAP), Fibre Channel Authentication Protocol (FCAP), Fibre Channel Password Authentication Protocol (FCPAP), Encapsulating Security Payload (ESP), and Fibre Channel Security Protocol (FC-SP).
![]() FCIP security leverages many IP Security (IPsec) features in Cisco IOS-based routers:
FCIP security leverages many IP Security (IPsec) features in Cisco IOS-based routers:
-
 IPsec for security over public carriers
IPsec for security over public carriers -
 High-speed encryption services in specialized hardware
High-speed encryption services in specialized hardware -
 Firewall filtering
Firewall filtering
Examining Voice Security
![]() This section examines the business drivers for VoIP, the required components, and the service issues. This section also examines the security implications of VoIP on IP networks.
This section examines the business drivers for VoIP, the required components, and the service issues. This section also examines the security implications of VoIP on IP networks.
 VoIP Fundamentals
VoIP Fundamentals
![]() VoIP is the transmission of voice traffic over IP-based networks. IP was originally designed for data networking, but its success in data networking has led to its adaptation to voice traffic.
VoIP is the transmission of voice traffic over IP-based networks. IP was originally designed for data networking, but its success in data networking has led to its adaptation to voice traffic.
![]() VoIP has become popular largely because of the cost savings it provides compared with traditional telephone networks. On traditional telephone networks, most people pay a flat monthly fee for local telephone calls and a per-minute charge for long-distance calls. VoIP calls are placed using the Internet, with most Internet connections being charged a flat monthly fee. Using the Internet connection for both data traffic and voice calls can allow consumers to get rid of one monthly bill. For international calls, the monetary savings can be enormous.
VoIP has become popular largely because of the cost savings it provides compared with traditional telephone networks. On traditional telephone networks, most people pay a flat monthly fee for local telephone calls and a per-minute charge for long-distance calls. VoIP calls are placed using the Internet, with most Internet connections being charged a flat monthly fee. Using the Internet connection for both data traffic and voice calls can allow consumers to get rid of one monthly bill. For international calls, the monetary savings can be enormous.
| Note |
|
![]() The business advantages that drive implementations of VoIP networks have changed over time. Starting with simple media convergence, these advantages have evolved to include the convergence of call-switching intelligence and the total user experience.
The business advantages that drive implementations of VoIP networks have changed over time. Starting with simple media convergence, these advantages have evolved to include the convergence of call-switching intelligence and the total user experience.
![]() Originally, return on investment (ROI) calculations centered on toll-bypass and converged-network savings. Although these savings are still relevant today, advances in voice technologies allow organizations and service providers to differentiate their product offerings by providing advanced features.
Originally, return on investment (ROI) calculations centered on toll-bypass and converged-network savings. Although these savings are still relevant today, advances in voice technologies allow organizations and service providers to differentiate their product offerings by providing advanced features.
![]() The following are some of the VoIP business drivers:
The following are some of the VoIP business drivers:
-
 Cost savings: Traditional time-division multiplexing (TDM), which is used in the public switched telephone network (PSTN) environment, dedicates 64 kb/s of bandwidth per voice channel. This approach results in bandwidth being wasted when there is no voice to transmit. VoIP shares bandwidth with multiple logical connections, which allows a more efficient utilization of bandwidth, thereby reducing bandwidth requirements. A substantial amount of equipment is needed to combine 64-kb/s channels into high-speed links for transport across the network. Packet telephony statistically multiplexes voice traffic alongside data traffic. This consolidation results in substantial savings on capital equipment and operations costs.
Cost savings: Traditional time-division multiplexing (TDM), which is used in the public switched telephone network (PSTN) environment, dedicates 64 kb/s of bandwidth per voice channel. This approach results in bandwidth being wasted when there is no voice to transmit. VoIP shares bandwidth with multiple logical connections, which allows a more efficient utilization of bandwidth, thereby reducing bandwidth requirements. A substantial amount of equipment is needed to combine 64-kb/s channels into high-speed links for transport across the network. Packet telephony statistically multiplexes voice traffic alongside data traffic. This consolidation results in substantial savings on capital equipment and operations costs. -
 Flexibility: The sophisticated functionality of IP networks allows organizations to be flexible in the types of applications and services that they provide to their customers and users. Service providers can easily segment customers. This segmentation helps service providers provide different applications, custom services, and rates depending on the traffic volume needs of the customer and other factors.
Flexibility: The sophisticated functionality of IP networks allows organizations to be flexible in the types of applications and services that they provide to their customers and users. Service providers can easily segment customers. This segmentation helps service providers provide different applications, custom services, and rates depending on the traffic volume needs of the customer and other factors. -
 Advanced features: The following are some examples of the advanced features that current VoIP applications provide.
Advanced features: The following are some examples of the advanced features that current VoIP applications provide.-
 Advanced call routing: When multiple paths exist to connect a call to its destination, certain paths may be preferred based on cost, distance, quality, partner handoffs, traffic load, or other considerations. Least-cost routing and time-of-day routing are two examples of advanced call routing that can be implemented to determine the best possible route for each call.
Advanced call routing: When multiple paths exist to connect a call to its destination, certain paths may be preferred based on cost, distance, quality, partner handoffs, traffic load, or other considerations. Least-cost routing and time-of-day routing are two examples of advanced call routing that can be implemented to determine the best possible route for each call. -
 Unified messaging: Unified messaging improves communications and boosts productivity. It delivers this advantage by providing a single-user interface to messages that have been delivered over a variety of mediums. For example, users can read their email, hear their voice mail, and view fax messages by accessing a single inbox.
Unified messaging: Unified messaging improves communications and boosts productivity. It delivers this advantage by providing a single-user interface to messages that have been delivered over a variety of mediums. For example, users can read their email, hear their voice mail, and view fax messages by accessing a single inbox. -
 Integrated information systems: Organizations are using VoIP to affect business process transformation. Centralized call control, geographically dispersed virtual contact centers, and access to resources and self-help tools are examples of VoIP technology that have enabled organizations to draw from a broad range of resources to service customers.
Integrated information systems: Organizations are using VoIP to affect business process transformation. Centralized call control, geographically dispersed virtual contact centers, and access to resources and self-help tools are examples of VoIP technology that have enabled organizations to draw from a broad range of resources to service customers. -
 Long-distance toll bypass: Long-distance toll bypass is an attractive solution for organizations that place a significant number of calls between sites that are charged long-distance fees. In this case, it might be more cost-effective to use VoIP to place those calls across the IP network. If the IP WAN becomes congested, the calls can overflow into the PSTN, ensuring that there is no degradation in voice quality.
Long-distance toll bypass: Long-distance toll bypass is an attractive solution for organizations that place a significant number of calls between sites that are charged long-distance fees. In this case, it might be more cost-effective to use VoIP to place those calls across the IP network. If the IP WAN becomes congested, the calls can overflow into the PSTN, ensuring that there is no degradation in voice quality. -
 Encryption: Security mechanisms in the IP network enable the administrator to ensure that IP conversations are secure. Encryption of sensitive signaling header fields and message bodies protects the packet in case of unauthorized packet interception.
Encryption: Security mechanisms in the IP network enable the administrator to ensure that IP conversations are secure. Encryption of sensitive signaling header fields and message bodies protects the packet in case of unauthorized packet interception. -
 Customer relationship: The capability to provide customer support through multiple mediums, such as telephone, chat, and email, builds solid customer satisfaction and loyalty. A pervasive IP network allows organizations to provide contact center agents with consolidated and up-to-date customer records along with the related customer communication. Access to this information allows quick problem solving, which in turn, builds strong customer relationships.
Customer relationship: The capability to provide customer support through multiple mediums, such as telephone, chat, and email, builds solid customer satisfaction and loyalty. A pervasive IP network allows organizations to provide contact center agents with consolidated and up-to-date customer records along with the related customer communication. Access to this information allows quick problem solving, which in turn, builds strong customer relationships.
-
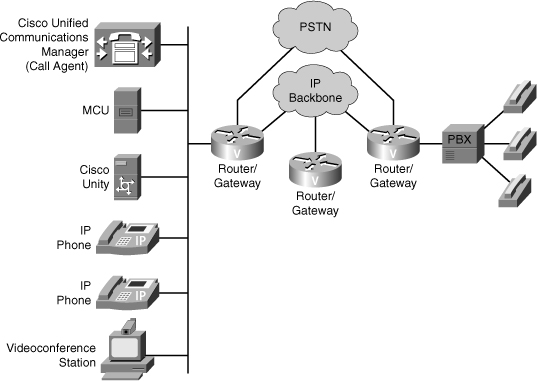
![]() Figure 7-17 shows the basic components of a packet voice network:
Figure 7-17 shows the basic components of a packet voice network:
-
 IP phones: IP phones provide IP voice to the desktop.
IP phones: IP phones provide IP voice to the desktop. -
 Gatekeeper: (Not shown in Figure 7-17.) The gatekeeper, also known as a Cisco Multimedia Conference Manager (MCM), provides Call Admission Control (CAC), bandwidth control and management, and address translation.
Gatekeeper: (Not shown in Figure 7-17.) The gatekeeper, also known as a Cisco Multimedia Conference Manager (MCM), provides Call Admission Control (CAC), bandwidth control and management, and address translation. -
 Gateway: The gateway provides translation between VoIP and non-VoIP networks, such as the PSTN. Gateways also provide physical access for local analog and digital voice devices, such as telephones, fax machines, key sets, and PBXs.
Gateway: The gateway provides translation between VoIP and non-VoIP networks, such as the PSTN. Gateways also provide physical access for local analog and digital voice devices, such as telephones, fax machines, key sets, and PBXs. -
 Multipoint control unit (MCU): The multipoint control unit provides real-time connectivity for participants in multiple locations to attend the same videoconference or meeting.
Multipoint control unit (MCU): The multipoint control unit provides real-time connectivity for participants in multiple locations to attend the same videoconference or meeting. -
 Call agent: The call agent provides call control for IP phones, CAC, bandwidth control and management, and address translation. Cisco Unified Communications Managers and Cisco Unified Communications Manager Business Edition both function as the call agents.
Call agent: The call agent provides call control for IP phones, CAC, bandwidth control and management, and address translation. Cisco Unified Communications Managers and Cisco Unified Communications Manager Business Edition both function as the call agents. -
 Application servers: Application servers provide services such as voice mail and unified messaging (which is provided by Cisco Unity).
Application servers: Application servers provide services such as voice mail and unified messaging (which is provided by Cisco Unity). -
 Videoconference station: The videoconference station provides access for end-user participation in videoconferencing. The videoconference station contains a video-capture device for video input and a microphone for audio input. The user can view video streams and hear the audio that originates at a remote user station.
Videoconference station: The videoconference station provides access for end-user participation in videoconferencing. The videoconference station contains a video-capture device for video input and a microphone for audio input. The user can view video streams and hear the audio that originates at a remote user station.
![]() Other components, such as software voice applications, interactive voice response (IVR) systems, and softphones, provide additional services to meet the needs of enterprise sites.
Other components, such as software voice applications, interactive voice response (IVR) systems, and softphones, provide additional services to meet the needs of enterprise sites.
![]() The following are some of the major VoIP protocols:
The following are some of the major VoIP protocols:
-
 H.323: This is an ITU standard protocol for interactive conferencing. H.323 was originally designed for multimedia in a connectionless environment, such as a LAN. H.323, is an umbrella of standards that define all aspects of synchronized voice, video, and data transmission. H.323 defines end-to-end call signaling.
H.323: This is an ITU standard protocol for interactive conferencing. H.323 was originally designed for multimedia in a connectionless environment, such as a LAN. H.323, is an umbrella of standards that define all aspects of synchronized voice, video, and data transmission. H.323 defines end-to-end call signaling. -
 Media Gateway Control Protocol (MGCP): This is a method for PSTN gateway control or thin device control. Specified in RFC 2705, MGCP defines a protocol to control VoIP gateways that are connected to external call control devices, referred to as call agents. MGCP provides the signaling capability for less-expensive edge devices, such as gateways, that may not have implemented a full voice-signaling protocol such as H.323. For example, any time an event such as off hook occurs at the voice port of a gateway, the voice port reports that event to the call agent. The call agent then signals that device to provide a service, such as dial-tone signaling. The call agent controls the gateway.
Media Gateway Control Protocol (MGCP): This is a method for PSTN gateway control or thin device control. Specified in RFC 2705, MGCP defines a protocol to control VoIP gateways that are connected to external call control devices, referred to as call agents. MGCP provides the signaling capability for less-expensive edge devices, such as gateways, that may not have implemented a full voice-signaling protocol such as H.323. For example, any time an event such as off hook occurs at the voice port of a gateway, the voice port reports that event to the call agent. The call agent then signals that device to provide a service, such as dial-tone signaling. The call agent controls the gateway. -
 H.248: This is a joint IETF and ITU standard that is based on the original MGCP standard. The H.248 protocol, also known as Megaco, defines a single gateway control approach that works with multiple gateway applications, including PSTN gateways, ATM interfaces, analog-like and telephone interfaces, IVR servers, and others. The Megaco protocol provides full call control intelligence and implements call-level features such as transfer, conference, call forward, and hold. The basic operation of the Megaco protocol is similar in nature to MGCP; however, the Megaco protocol provides more flexibility by interfacing with a wider variety of applications and gateways.
H.248: This is a joint IETF and ITU standard that is based on the original MGCP standard. The H.248 protocol, also known as Megaco, defines a single gateway control approach that works with multiple gateway applications, including PSTN gateways, ATM interfaces, analog-like and telephone interfaces, IVR servers, and others. The Megaco protocol provides full call control intelligence and implements call-level features such as transfer, conference, call forward, and hold. The basic operation of the Megaco protocol is similar in nature to MGCP; however, the Megaco protocol provides more flexibility by interfacing with a wider variety of applications and gateways. -
 Session Initiation Protocol (SIP): SIP is a detailed protocol that specifies the commands and responses to set up and tear down calls. SIP also details features such as security, proxy, and transport (TCP or User Datagram Protocol [UDP]) services. SIP and its partner protocols, Session Announcement Protocol (SAP) and Session Description Protocol (SDP), provide announcements and information about multicast sessions to users on a network. SIP defines end-to-end call signaling between devices. SIP is a text-based protocol that borrows many elements of HTTP, using the same transaction request and response model, and similar header and response codes. It also adopts a modified form of the URL addressing scheme that is used within email that is based on Simple Mail Transfer Protocol (SMTP).
Session Initiation Protocol (SIP): SIP is a detailed protocol that specifies the commands and responses to set up and tear down calls. SIP also details features such as security, proxy, and transport (TCP or User Datagram Protocol [UDP]) services. SIP and its partner protocols, Session Announcement Protocol (SAP) and Session Description Protocol (SDP), provide announcements and information about multicast sessions to users on a network. SIP defines end-to-end call signaling between devices. SIP is a text-based protocol that borrows many elements of HTTP, using the same transaction request and response model, and similar header and response codes. It also adopts a modified form of the URL addressing scheme that is used within email that is based on Simple Mail Transfer Protocol (SMTP). -
 Real-Time Transport Protocol (RTP): RTP is an IETF standard media-streaming protocol. RTP carries the voice payload across the network. RTP provides sequence numbers and time stamps for the orderly processing of voice packets.
Real-Time Transport Protocol (RTP): RTP is an IETF standard media-streaming protocol. RTP carries the voice payload across the network. RTP provides sequence numbers and time stamps for the orderly processing of voice packets. -
 RTP Control Protocol (RTCP): RTCP provides out-of-band control information for an RTP flow. Every RTP flow has a corresponding RTCP flow that reports statistics on the call. RTCP is used for quality of service (QoS) reporting.
RTP Control Protocol (RTCP): RTCP provides out-of-band control information for an RTP flow. Every RTP flow has a corresponding RTCP flow that reports statistics on the call. RTCP is used for quality of service (QoS) reporting. -
 Secure Real-Time Protocol (SRTP): SRTP provides encryption, message authentication and integrity, and replay protection to the RTP data in both unicast and multicast applications that a VoIP device transmits. This eliminates the need to use IPsec to encrypt VoIP streams.
Secure Real-Time Protocol (SRTP): SRTP provides encryption, message authentication and integrity, and replay protection to the RTP data in both unicast and multicast applications that a VoIP device transmits. This eliminates the need to use IPsec to encrypt VoIP streams. -
 Skinny Client Control Protocol (SCCP): SCCP is a Cisco proprietary protocol used between Cisco Unified Communications Manager and Cisco IP phones. Some other vendors are beginning to support SCCP. With the SCCP architecture, the vast majority of the H.323 processing power resides in an H.323 proxy known as the Cisco Unified Communications Manager. The end stations (IP phones) run what is called the skinny client, which consumes less processing overhead. The skinny client communicates with the Cisco Unified Communications Manager using connection-oriented (TCP/IP-based) communication to establish a call with another H.323-compliant end station. Once the Cisco Unified Communications Manager has established the call, the two H.323 end stations use connectionless (UDP/IP-based) communication for audio transmissions.
Skinny Client Control Protocol (SCCP): SCCP is a Cisco proprietary protocol used between Cisco Unified Communications Manager and Cisco IP phones. Some other vendors are beginning to support SCCP. With the SCCP architecture, the vast majority of the H.323 processing power resides in an H.323 proxy known as the Cisco Unified Communications Manager. The end stations (IP phones) run what is called the skinny client, which consumes less processing overhead. The skinny client communicates with the Cisco Unified Communications Manager using connection-oriented (TCP/IP-based) communication to establish a call with another H.323-compliant end station. Once the Cisco Unified Communications Manager has established the call, the two H.323 end stations use connectionless (UDP/IP-based) communication for audio transmissions.
![]() Table 7-5 provides a summary of the major VoIP protocols.
Table 7-5 provides a summary of the major VoIP protocols.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|
 Voice Security Threats
Voice Security Threats
![]() The following are some of the common threats to VoIP networks:
The following are some of the common threats to VoIP networks:
-
 Unauthorized access to voice resources: Hackers can tamper with voice systems, user identities, and telephone configurations, and intercept voice-mail messages. They could also do toll fraud. If hackers gain access to the voice-mail system, they can change the voice-mail greeting, which will have a negative impact on the image and reputation of the company. A hacker who gains access to the PBX or voice gateway can shut down voice ports or change voice-routing parameters, affecting voice access into and through the network.
Unauthorized access to voice resources: Hackers can tamper with voice systems, user identities, and telephone configurations, and intercept voice-mail messages. They could also do toll fraud. If hackers gain access to the voice-mail system, they can change the voice-mail greeting, which will have a negative impact on the image and reputation of the company. A hacker who gains access to the PBX or voice gateway can shut down voice ports or change voice-routing parameters, affecting voice access into and through the network. -
 Compromise of network resources: The goal of a secure network is to ensure that applications, processes, and users can reliably and securely interoperate using the shared network resources. Because the shared network infrastructure carries voice and data, securing access to the network infrastructure is critical to securing voice functions. Because IP voice systems are installed on a data network, they are potential targets for hackers who previously targeted only PCs, servers, and data applications. Hackers are aided in their search for vulnerabilities in IP voice systems by the open and well-known standards and protocols that are used by IP networks.
Compromise of network resources: The goal of a secure network is to ensure that applications, processes, and users can reliably and securely interoperate using the shared network resources. Because the shared network infrastructure carries voice and data, securing access to the network infrastructure is critical to securing voice functions. Because IP voice systems are installed on a data network, they are potential targets for hackers who previously targeted only PCs, servers, and data applications. Hackers are aided in their search for vulnerabilities in IP voice systems by the open and well-known standards and protocols that are used by IP networks. -
 DoS attacks: DoS attacks are defined as the malicious attacking or overloading of call-processing equipment to deny access to services by legitimate users. Most DoS attacks fall into one of three categories:
DoS attacks: DoS attacks are defined as the malicious attacking or overloading of call-processing equipment to deny access to services by legitimate users. Most DoS attacks fall into one of three categories:-
 Network resource overload: This type of attack involves overloading a network resource that is required for proper functioning of a service. The network resource is most often bandwidth. The DoS attack uses up all available bandwidth, causing authorized users to be unable to access the required services.
Network resource overload: This type of attack involves overloading a network resource that is required for proper functioning of a service. The network resource is most often bandwidth. The DoS attack uses up all available bandwidth, causing authorized users to be unable to access the required services. -
 Host resource starvation: This type of attack involves using up critical host resources. When use of these resources is maximized by the DoS attack, the server can no longer respond to legitimate service requests.
Host resource starvation: This type of attack involves using up critical host resources. When use of these resources is maximized by the DoS attack, the server can no longer respond to legitimate service requests. -
 Out-of-bounds attack: This type of attack involves using illegal packet structure and unexpected data, which can cause the operating system of the remote system to crash. One example of this type of attack may be to use illegal combinations of TCP flags. Most TCP/IP stacks are developed to respond to appropriate use: They are not developed for anomalies. When the stack receives illegal data, it may not know how to handle the packet and may cause a system crash.
Out-of-bounds attack: This type of attack involves using illegal packet structure and unexpected data, which can cause the operating system of the remote system to crash. One example of this type of attack may be to use illegal combinations of TCP flags. Most TCP/IP stacks are developed to respond to appropriate use: They are not developed for anomalies. When the stack receives illegal data, it may not know how to handle the packet and may cause a system crash.
-
-
 Eavesdropping: Eavesdropping involves the unauthorized interception of voice packets or RTP media streams. Eavesdropping exposes confidential or proprietary information that is obtained by intercepting and reassembling packets in a voice stream. Numerous tools are used by hackers to eavesdrop.
Eavesdropping: Eavesdropping involves the unauthorized interception of voice packets or RTP media streams. Eavesdropping exposes confidential or proprietary information that is obtained by intercepting and reassembling packets in a voice stream. Numerous tools are used by hackers to eavesdrop.
Spam over IP Telephony
![]() Spam over IP Telephony (SPIT) also referred to VoIP spam, is unsolicited and unwanted bulk messages broadcast over VoIP to the end users of an enterprise network. In addition to being annoying and having the potential to significantly affect the availability and productivity of the endpoints, high-volume bulk calls that are routed over IP can be difficult to trace and have the capacity for fraud, unauthorized use, and privacy violations.
Spam over IP Telephony (SPIT) also referred to VoIP spam, is unsolicited and unwanted bulk messages broadcast over VoIP to the end users of an enterprise network. In addition to being annoying and having the potential to significantly affect the availability and productivity of the endpoints, high-volume bulk calls that are routed over IP can be difficult to trace and have the capacity for fraud, unauthorized use, and privacy violations.
![]() Up to now, there have not been a great many instances of VoIP spam, but there is great potential for it to become a major problem. SPIT could be generated in a similar way to email spam with botnets, targeting millions of VoIP users from compromised machines.
Up to now, there have not been a great many instances of VoIP spam, but there is great potential for it to become a major problem. SPIT could be generated in a similar way to email spam with botnets, targeting millions of VoIP users from compromised machines.
![]() Spam has been a problem for years, and unsolicited commercial and malicious email spam now makes up the majority of email worldwide. In Europe in 2006, according to analysts Radicati, 16 billion spam messages were sent each day, representing 62 percent of all European email messages, and this figure is expected to increase to 37 billion spam emails a day by 2010. There is a concern in some circles that VoIP will suffer the same fate as email, and IP telephony would then become unusable.
Spam has been a problem for years, and unsolicited commercial and malicious email spam now makes up the majority of email worldwide. In Europe in 2006, according to analysts Radicati, 16 billion spam messages were sent each day, representing 62 percent of all European email messages, and this figure is expected to increase to 37 billion spam emails a day by 2010. There is a concern in some circles that VoIP will suffer the same fate as email, and IP telephony would then become unusable.
![]() Another concern about SPIT is that email antispam methods will not work. The real-time nature of voice calls will make dealing with SPIT much more challenging than email spam. New methods are going to have to be invented to address SPIT problems.
Another concern about SPIT is that email antispam methods will not work. The real-time nature of voice calls will make dealing with SPIT much more challenging than email spam. New methods are going to have to be invented to address SPIT problems.
| Note |
|
![]() An example of SPIT would be marketing or malicious phone calls made on a regular basis. The calls are infrequent enough, so they bypass any thresholds, but are frequent enough to affect employee productivity.
An example of SPIT would be marketing or malicious phone calls made on a regular basis. The calls are infrequent enough, so they bypass any thresholds, but are frequent enough to affect employee productivity.
Fraud
![]() Two common types of fraud in VoIP networks are vishing and fraud.
Two common types of fraud in VoIP networks are vishing and fraud.
![]() Vishing (voice phishing) uses telephony to glean information, such as account details, directly from users. One of the first reported cases of vishing affected PayPal. Victims first received an email pretending to come from PayPal asking them to verify their credit card details over the phone. Those who called the number were then asked to enter their credit card number using the keypad. Once the credit card number had been entered, the perpetrators of this fraud were free to steal money from the account of their victims.
Vishing (voice phishing) uses telephony to glean information, such as account details, directly from users. One of the first reported cases of vishing affected PayPal. Victims first received an email pretending to come from PayPal asking them to verify their credit card details over the phone. Those who called the number were then asked to enter their credit card number using the keypad. Once the credit card number had been entered, the perpetrators of this fraud were free to steal money from the account of their victims.
![]() Scams such as this are not just a danger for VoIP users, but the lower cost of making voice calls will make them much more popular than with standard phone systems. Users still trust the telephone more than the web, and by using spamming techniques, attackers can call thousands of people for very little cost every day.
Scams such as this are not just a danger for VoIP users, but the lower cost of making voice calls will make them much more popular than with standard phone systems. Users still trust the telephone more than the web, and by using spamming techniques, attackers can call thousands of people for very little cost every day.
![]() Toll fraud is the theft of long-distance telephone service by unauthorized access to a PSTN trunk (an “outside line”) on a PBX or voice-mail system. Toll fraud is a multibillion-dollar illegal industry, and all organizations are vulnerable. Theft can also be defined as the use of the telephony system, by both authorized and unauthorized users, to use voice network resources to access unauthorized numbers, such as premium-rate numbers.
Toll fraud is the theft of long-distance telephone service by unauthorized access to a PSTN trunk (an “outside line”) on a PBX or voice-mail system. Toll fraud is a multibillion-dollar illegal industry, and all organizations are vulnerable. Theft can also be defined as the use of the telephony system, by both authorized and unauthorized users, to use voice network resources to access unauthorized numbers, such as premium-rate numbers.
![]() This fraud is not new and PBXs have always been vulnerable. The difference is that few people could hack into PBXs, compared to the numbers of people actively breaking into IP systems.
This fraud is not new and PBXs have always been vulnerable. The difference is that few people could hack into PBXs, compared to the numbers of people actively breaking into IP systems.
![]() To protect against such fraud, it is important to use features that exist in Cisco Unified Communications Manager, such as dial-plan filters, partitions, or forced authorization codes (FAC), to control phone calls.
To protect against such fraud, it is important to use features that exist in Cisco Unified Communications Manager, such as dial-plan filters, partitions, or forced authorization codes (FAC), to control phone calls.
SIP Vulnerabilities
![]() The increasing adoption of SIP for VoIP is expected to open up a completely new front in the security war. SIP is a protocol that offers little inherent security. Some of its characteristics also leave it vulnerable to hackers, such as using text for encoding and SIP extensions that can create security holes.
The increasing adoption of SIP for VoIP is expected to open up a completely new front in the security war. SIP is a protocol that offers little inherent security. Some of its characteristics also leave it vulnerable to hackers, such as using text for encoding and SIP extensions that can create security holes.
![]() Examples of hacks for SIP include registration hijacking, which allows a hacker to intercept incoming calls and reroute them; message tampering, which allows a hacker to modify data packets traveling between SIP addresses; and session teardown, which allows a hacker to terminate calls or carry out a VoIP-targeted DoS attack by flooding the system with shutdown requests.
Examples of hacks for SIP include registration hijacking, which allows a hacker to intercept incoming calls and reroute them; message tampering, which allows a hacker to modify data packets traveling between SIP addresses; and session teardown, which allows a hacker to terminate calls or carry out a VoIP-targeted DoS attack by flooding the system with shutdown requests.
 Defending Against VoIP Hacking
Defending Against VoIP Hacking
![]() Many IP security solutions can be implemented only on Layer 3 (IP) devices. Because of protocol architecture, the MAC layer (Layer 2) offers little or no inherent security. Understanding and establishing broadcast domains is one of the fundamental precepts in designing secure IP networks. Many simple, yet dangerous attacks can be launched if the attacking device resides within the same broadcast domain as the target system. For this reason, IP phones, VoIP gateways, and network management workstations should always be on their own subnet, separate from the rest of the data network and from each other.
Many IP security solutions can be implemented only on Layer 3 (IP) devices. Because of protocol architecture, the MAC layer (Layer 2) offers little or no inherent security. Understanding and establishing broadcast domains is one of the fundamental precepts in designing secure IP networks. Many simple, yet dangerous attacks can be launched if the attacking device resides within the same broadcast domain as the target system. For this reason, IP phones, VoIP gateways, and network management workstations should always be on their own subnet, separate from the rest of the data network and from each other.
Protect IP Telephony with Voice VLAN
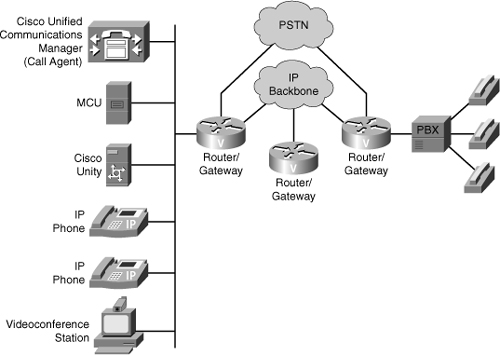
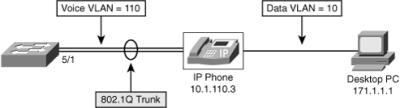
![]() To ensure communications privacy and integrity, voice media streams must be protected from eavesdropping and tampering. Data-networking technologies, such as VLANs, can segment voice traffic from data traffic, enabling you to prevent access to the voice VLAN from the data VLAN. Using separate VLANs for voice and data, as shown in Figure 7-18, prevents any attacker or attacking application from snooping or capturing other VLAN traffic as it traverses the physical wire. Also, by making sure that each device connects to the network using a switched infrastructure, you can render packet-sniffing tools less effective for capturing user traffic.
To ensure communications privacy and integrity, voice media streams must be protected from eavesdropping and tampering. Data-networking technologies, such as VLANs, can segment voice traffic from data traffic, enabling you to prevent access to the voice VLAN from the data VLAN. Using separate VLANs for voice and data, as shown in Figure 7-18, prevents any attacker or attacking application from snooping or capturing other VLAN traffic as it traverses the physical wire. Also, by making sure that each device connects to the network using a switched infrastructure, you can render packet-sniffing tools less effective for capturing user traffic.
![]() Using voice VLANs to logically segment voice and data traffic is an industrywide accepted best practice. As much as possible, devices that are identified as voice devices should be restricted to dedicated voice VLANs. This approach ensures that they can communicate only with other voice resources. More important, voice traffic is kept away from the general data network, where it could be more easily intercepted or tampered with. In addition, having a voice specific VLAN makes it easier to apply VLAN access control lists (VACL) to protect voice traffic.
Using voice VLANs to logically segment voice and data traffic is an industrywide accepted best practice. As much as possible, devices that are identified as voice devices should be restricted to dedicated voice VLANs. This approach ensures that they can communicate only with other voice resources. More important, voice traffic is kept away from the general data network, where it could be more easily intercepted or tampered with. In addition, having a voice specific VLAN makes it easier to apply VLAN access control lists (VACL) to protect voice traffic.
![]() By understanding the protocols used between devices in the VoIP network, you can implement affective ACLs on the voice VLANs. IP phones send only RTP traffic to each other; they never have a reason to send TCP or Internet Control Message Protocol (ICMP) traffic to each other. IP phones do send a few TCP and UDP protocols to communicate with servers. You can stop many of the IP phone attacks by using ACLs on the voice VLANs to watch for deviations from these principles.
By understanding the protocols used between devices in the VoIP network, you can implement affective ACLs on the voice VLANs. IP phones send only RTP traffic to each other; they never have a reason to send TCP or Internet Control Message Protocol (ICMP) traffic to each other. IP phones do send a few TCP and UDP protocols to communicate with servers. You can stop many of the IP phone attacks by using ACLs on the voice VLANs to watch for deviations from these principles.
![]() Firewalls inspect packets and match them against configured rules. It is difficult to specify ahead of time which ports will be used in a voice call because the ports are dynamically negotiated during call setup.
Firewalls inspect packets and match them against configured rules. It is difficult to specify ahead of time which ports will be used in a voice call because the ports are dynamically negotiated during call setup.
Protect IP Telephony with Firewalls
![]() Cisco ASA Appliances inspect voice protocols to ensure that SIP, SCCP, H.323, and MGCP requests conform to voice standards. Cisco ASA Appliances can also provide the following capabilities to help protect voice traffic:
Cisco ASA Appliances inspect voice protocols to ensure that SIP, SCCP, H.323, and MGCP requests conform to voice standards. Cisco ASA Appliances can also provide the following capabilities to help protect voice traffic:
-
 Inspect protocols to ensure SIP, SCCP, H.232 and MGCP requests conform to standards
Inspect protocols to ensure SIP, SCCP, H.232 and MGCP requests conform to standards -
 Prevent inappropriate SIP methods from being sent to Cisco Unified Communications Manager
Prevent inappropriate SIP methods from being sent to Cisco Unified Communications Manager -
 Rate limit SIP requests
Rate limit SIP requests -
 Enforce the policy of calls according to whitelists, blacklists, caller/called party and SIP uniform resource identifier
Enforce the policy of calls according to whitelists, blacklists, caller/called party and SIP uniform resource identifier -
 Dynamically open ports for Cisco applications
Dynamically open ports for Cisco applications -
 Enable inspection of encrypted phone calls
Enable inspection of encrypted phone calls
![]() Cisco IOS firewalls can also provide security unified communication.
Cisco IOS firewalls can also provide security unified communication.
Protect IP Telephony with VPNs
![]() VPNs are widely used to provide secure connections to the corporate network. The connections can originate from a branch office, a small office, home office (SOHO), a telecommuter, or a roaming user. Then IPsec can be used for authentication and confidentiality services. To facilitate performance, it is recommended that VPN tunnels terminate inside of a firewall, as shown in Figure 7-19. You can then use the firewall to inspect and protect the plaintext protocols.
VPNs are widely used to provide secure connections to the corporate network. The connections can originate from a branch office, a small office, home office (SOHO), a telecommuter, or a roaming user. Then IPsec can be used for authentication and confidentiality services. To facilitate performance, it is recommended that VPN tunnels terminate inside of a firewall, as shown in Figure 7-19. You can then use the firewall to inspect and protect the plaintext protocols.
![]() Frequently asked questions about voice over VPN generally deal with overhead and delay, which have an impact on the QoS for the call.
Frequently asked questions about voice over VPN generally deal with overhead and delay, which have an impact on the QoS for the call.
| Note |
|
![]() Voice communications do not work when even a modest amount of latency is present. Because secure VPNs encrypt data, they can create a throughput bottleneck when they process packets through their encryption algorithm. The problem usually gets worse as security increases.
Voice communications do not work when even a modest amount of latency is present. Because secure VPNs encrypt data, they can create a throughput bottleneck when they process packets through their encryption algorithm. The problem usually gets worse as security increases.
![]() VoIP and either Advanced Encryption Standard (AES), Data Encryption Standard (DES), or Triple DES (3DES) encryptions are fully compatible with each other as long as the VPN delivers the necessary throughput. Internationally, corporations can run into other factors. The U.S. Department of Commerce places restrictions on the export of certain encryption technology. Usually, DES is exportable, whereas 3DES and AES are not, but regulations take numerous forms, from total export exclusions that are applied to certain countries, to allowing 3DES export to specific industries and users. Corporations with VPNs that extend outside the United States should find out whether their VPN provider has exportable products and how export regulations affect networks built with those products.
VoIP and either Advanced Encryption Standard (AES), Data Encryption Standard (DES), or Triple DES (3DES) encryptions are fully compatible with each other as long as the VPN delivers the necessary throughput. Internationally, corporations can run into other factors. The U.S. Department of Commerce places restrictions on the export of certain encryption technology. Usually, DES is exportable, whereas 3DES and AES are not, but regulations take numerous forms, from total export exclusions that are applied to certain countries, to allowing 3DES export to specific industries and users. Corporations with VPNs that extend outside the United States should find out whether their VPN provider has exportable products and how export regulations affect networks built with those products.
| Note |
|
Protect IP Telephony Endpoints and Servers
![]() Signed firmware and configuration files are among the defenses that are built in to Cisco IP telephony products. You can also harden the IP phones by disabling specific features and functions that could be used to compromise the phone. Things you should think about disabling on the Cisco IP phone, especially those located in public areas such as office lobbies, airport gates, and so on, include the PC port, settings button, speakerphone, and web access.
Signed firmware and configuration files are among the defenses that are built in to Cisco IP telephony products. You can also harden the IP phones by disabling specific features and functions that could be used to compromise the phone. Things you should think about disabling on the Cisco IP phone, especially those located in public areas such as office lobbies, airport gates, and so on, include the PC port, settings button, speakerphone, and web access.
![]() When securing your voice traffic, do not forget to secure the voice application servers. The current version of Cisco Unified Communications Manager is a hardened appliance that disables unnecessary services, disables default usernames, allows only signed images to be installed, has Cisco Security Agent installed, and supports secure management protocols.
When securing your voice traffic, do not forget to secure the voice application servers. The current version of Cisco Unified Communications Manager is a hardened appliance that disables unnecessary services, disables default usernames, allows only signed images to be installed, has Cisco Security Agent installed, and supports secure management protocols.
![]() By combining the transport security provided by secure LANs, firewalls, and VPNs with the application and host security features available with the Cisco Unified Communications Manager and Cisco IP phones, it is possible to have a highly secure IP telephony environment.
By combining the transport security provided by secure LANs, firewalls, and VPNs with the application and host security features available with the Cisco Unified Communications Manager and Cisco IP phones, it is possible to have a highly secure IP telephony environment.

0 comments
Post a Comment