Overview
![]() This chapter focuses on several additional aspects of network security—LAN, storage-area network (SAN), voice, and endpoints. This chapter emphasizes Layer 2 and host security to provide a much more comprehensive coverage of the important issues involved in securing an enterprise. Topics covered in this chapter include the following:
This chapter focuses on several additional aspects of network security—LAN, storage-area network (SAN), voice, and endpoints. This chapter emphasizes Layer 2 and host security to provide a much more comprehensive coverage of the important issues involved in securing an enterprise. Topics covered in this chapter include the following:
-
 Current endpoint protection methods, such as HIPS, integrity checkers, operating system protection, and the Cisco NAC Appliance
Current endpoint protection methods, such as HIPS, integrity checkers, operating system protection, and the Cisco NAC Appliance -
 Risks and countermeasures for SAN security
Risks and countermeasures for SAN security -
 Risks and countermeasures to IP telephony
Risks and countermeasures to IP telephony -
 Layer 2 attacks against network topologies and protocols
Layer 2 attacks against network topologies and protocols
![]() The term endpoint is used in a variety of ways in different contexts. For this chapter, an endpoint is considered an individual computer system or device that acts as a network client. Common endpoints are laptops, desktops, and personal computing devices, such as personal digital assistants (PDA). In addition, servers can be considered endpoints.
The term endpoint is used in a variety of ways in different contexts. For this chapter, an endpoint is considered an individual computer system or device that acts as a network client. Common endpoints are laptops, desktops, and personal computing devices, such as personal digital assistants (PDA). In addition, servers can be considered endpoints.
Examining Endpoint Security
![]() The Cisco strategy for addressing host security, and therefore network and enterprise security, is based on three broad elements:
The Cisco strategy for addressing host security, and therefore network and enterprise security, is based on three broad elements:
-
 Endpoint protection: New behavior-based technology is available with Cisco Security Agent that protects endpoints against threats that are posed by viruses, Trojan horses, and worms.
Endpoint protection: New behavior-based technology is available with Cisco Security Agent that protects endpoints against threats that are posed by viruses, Trojan horses, and worms. -
 Cisco Network Admission Control (NAC): The Cisco NAC solution ensures that every endpoint complies with network security policies before being granted access to the network. Cisco NAC provides access to compliant devices, and ensures that noncompliant devices are denied access, placed in quarantine, or given restricted access to resources.
Cisco Network Admission Control (NAC): The Cisco NAC solution ensures that every endpoint complies with network security policies before being granted access to the network. Cisco NAC provides access to compliant devices, and ensures that noncompliant devices are denied access, placed in quarantine, or given restricted access to resources. -
 Network infection containment: To address the newest attack methods that can compromise your network, containment focuses on automating key elements of the infection response process. The Cisco Self-Defending Network (SDN) elements of the Cisco NAC, Cisco Security Agent, and intrusion prevention system (IPS) provide this service.
Network infection containment: To address the newest attack methods that can compromise your network, containment focuses on automating key elements of the infection response process. The Cisco Self-Defending Network (SDN) elements of the Cisco NAC, Cisco Security Agent, and intrusion prevention system (IPS) provide this service.
![]() An endpoint security strategy is necessary because software has historically had weaknesses. Secure (trustworthy) software is designed to protect data and withstand attack attempts. Historically, “secure” software has been used only with the military and in critical commercial systems. Generally, this type of software is custom software.
An endpoint security strategy is necessary because software has historically had weaknesses. Secure (trustworthy) software is designed to protect data and withstand attack attempts. Historically, “secure” software has been used only with the military and in critical commercial systems. Generally, this type of software is custom software.
![]() You can make software more trusted by hardening it. Hardening is often done, but requires documentation of the internal software components, which is not commonly provided by vendors.
You can make software more trusted by hardening it. Hardening is often done, but requires documentation of the internal software components, which is not commonly provided by vendors.
![]() There are two main areas of focus for secure software:
There are two main areas of focus for secure software:
-
 Security of operating systems
Security of operating systems -
 Security of applications that run inside an operating system
Security of applications that run inside an operating system
 Operating System Vulnerabilities
Operating System Vulnerabilities
![]() Operating systems provide basic security services to applications:
Operating systems provide basic security services to applications:
-
 Trusted code and trusted path ensure that the integrity of the operating system code base is not violated, and provide the user with a way of using the system that bypasses any possible Trojan horse’s fake trusted path.
Trusted code and trusted path ensure that the integrity of the operating system code base is not violated, and provide the user with a way of using the system that bypasses any possible Trojan horse’s fake trusted path. Trusted code refers to the assurance that the operating system code is not compromised. An operating system might provide integrity checking of all running code by using Hashed Message Authentication Code (HMAC) or digital signatures. Also, integrity verification of add-on software might be necessary at installation. Digital signatures could be used here, too.
Trusted code refers to the assurance that the operating system code is not compromised. An operating system might provide integrity checking of all running code by using Hashed Message Authentication Code (HMAC) or digital signatures. Also, integrity verification of add-on software might be necessary at installation. Digital signatures could be used here, too. Trusted path refers to a facility that assures that the user is using a genuine system and not a Trojan horse. The trusted path mechanism guarantees that data entered by a user is protected from unauthorized programs. A prime example of a trusted path is the Ctrl-Alt-Del key sequence for logging in to Windows NT, Windows 2000, and Windows XP, which is called secure attention sequence. This sequence is guaranteed to take you to the genuine password prompt and thus bypasses fake logging prompt.
Trusted path refers to a facility that assures that the user is using a genuine system and not a Trojan horse. The trusted path mechanism guarantees that data entered by a user is protected from unauthorized programs. A prime example of a trusted path is the Ctrl-Alt-Del key sequence for logging in to Windows NT, Windows 2000, and Windows XP, which is called secure attention sequence. This sequence is guaranteed to take you to the genuine password prompt and thus bypasses fake logging prompt. -
 Privileged context of execution provides some identity authentication and certain privileges based on the identity of the user, such as the rights being set differently if you log as guest or as administrator on a Windows workstation.
Privileged context of execution provides some identity authentication and certain privileges based on the identity of the user, such as the rights being set differently if you log as guest or as administrator on a Windows workstation. -
 Process memory protection and isolation provides separation from other users and their data.
Process memory protection and isolation provides separation from other users and their data. -
 Access control to resources ensures confidentiality and integrity of data.
Access control to resources ensures confidentiality and integrity of data.
![]() An attacker can subvert all of these services. If either trusted code or a trusted path is not present or is compromised, the operating system and all applications can be easily subverted by hostile code. In addition, an operating system might be made more vulnerable if there is a need to provide support for legacy protocols.
An attacker can subvert all of these services. If either trusted code or a trusted path is not present or is compromised, the operating system and all applications can be easily subverted by hostile code. In addition, an operating system might be made more vulnerable if there is a need to provide support for legacy protocols.
![]() Modern operating systems provide each process with an identity and privileges. Privilege switching is possible during program operation or during a single logon session. For instance, UNIX has the suid (set-UID) facility, and Windows has the runas utility.
Modern operating systems provide each process with an identity and privileges. Privilege switching is possible during program operation or during a single logon session. For instance, UNIX has the suid (set-UID) facility, and Windows has the runas utility.
![]() The following techniques help protect an endpoint from operating system vulnerabilities:
The following techniques help protect an endpoint from operating system vulnerabilities:
-
 Least privilege concept: Ideally, to better protect the endpoint, the least privilege concept should be followed; a process should never be given more privilege than is necessary to perform a job. In real life, this concept is usually not honored, which is a source of many vulnerabilities.
Least privilege concept: Ideally, to better protect the endpoint, the least privilege concept should be followed; a process should never be given more privilege than is necessary to perform a job. In real life, this concept is usually not honored, which is a source of many vulnerabilities. -
 Isolation between processes: An operating system should provide isolation between processes. This isolation can be virtual or physical. For instance, memory protection can be done in hardware. Some trusted operating systems provide isolation via “logical execution compartments.” This logical execution compartment is best experienced nowadays when a program hangs and you can terminate only that one application. In the past, with older operating systems that were not enforcing process isolation, if one application was hanging, the operating system was also hanging.
Isolation between processes: An operating system should provide isolation between processes. This isolation can be virtual or physical. For instance, memory protection can be done in hardware. Some trusted operating systems provide isolation via “logical execution compartments.” This logical execution compartment is best experienced nowadays when a program hangs and you can terminate only that one application. In the past, with older operating systems that were not enforcing process isolation, if one application was hanging, the operating system was also hanging. -
 Reference monitor: A reference monitor is an access control concept that refers to a mechanism or process that mediates all access to objects. The reference monitor provides a central point for all policy decisions. A reference monitor typically implements auditing functions to keep track of access. In addition to the reference monitor that typically exits in an operating system, Cisco Security Agent functions essentially as a reference monitor.
Reference monitor: A reference monitor is an access control concept that refers to a mechanism or process that mediates all access to objects. The reference monitor provides a central point for all policy decisions. A reference monitor typically implements auditing functions to keep track of access. In addition to the reference monitor that typically exits in an operating system, Cisco Security Agent functions essentially as a reference monitor. -
 Small verifiable pieces of code: For all security functionality, the idea is to have small, easily verifiable pieces of software that are managed and monitored by a reference monitor.
Small verifiable pieces of code: For all security functionality, the idea is to have small, easily verifiable pieces of software that are managed and monitored by a reference monitor.
| Note |
|
 Application Vulnerabilities
Application Vulnerabilities
![]() Most attacks target applications, or the data they are protecting, or both. Attacks can be one of the following two types:
Most attacks target applications, or the data they are protecting, or both. Attacks can be one of the following two types:
-
 Direct: In a direct attack, the attacker fools the application into performing a task with the privileges of the application.
Direct: In a direct attack, the attacker fools the application into performing a task with the privileges of the application. -
 Indirect: In an indirect attack, the attacker first compromises another subsystem and attacks the application through the compromised subsystem (privilege escalation).
Indirect: In an indirect attack, the attacker first compromises another subsystem and attacks the application through the compromised subsystem (privilege escalation).
![]() The more privileges the application has, the more damage it can do to its sensitive data and the whole host system.
The more privileges the application has, the more damage it can do to its sensitive data and the whole host system.
| Note |
|
![]() The ultimate target of an attacker is often an application running on a host that processes sensitive data the attacker wants to obtain. When an attacker has the option of communicating directly with the application hosting sensitive data, the application must be suitably protected against this potential threat. Attackers seek to obtain permissions to read or write to sensitive data, thereby compromising confidentiality and integrity; they might want to cause a denial-of-service (DoS) attack in a specific application.
The ultimate target of an attacker is often an application running on a host that processes sensitive data the attacker wants to obtain. When an attacker has the option of communicating directly with the application hosting sensitive data, the application must be suitably protected against this potential threat. Attackers seek to obtain permissions to read or write to sensitive data, thereby compromising confidentiality and integrity; they might want to cause a denial-of-service (DoS) attack in a specific application.
![]() An attacker may attack an application directly by finding a flaw in the application and bypassing its access controls to obtain read or write access to sensitive data. The complexity of current applications makes such flaws common. In addition, secure development is too costly or not feasible for many businesses.
An attacker may attack an application directly by finding a flaw in the application and bypassing its access controls to obtain read or write access to sensitive data. The complexity of current applications makes such flaws common. In addition, secure development is too costly or not feasible for many businesses.
![]() In another scenario, an attacker gains access to sensitive data through a chain of compromises of other system components. For example, an attacker first obtains basic user-level access to the system on which the sensitive data resides. Then, by exploiting a flaw in any local application, the attacker attains system administration privileges (known as privilege escalation). Using these privileges, the attacker might be able to read or write to most objects on the system, including sensitive data of the target application.
In another scenario, an attacker gains access to sensitive data through a chain of compromises of other system components. For example, an attacker first obtains basic user-level access to the system on which the sensitive data resides. Then, by exploiting a flaw in any local application, the attacker attains system administration privileges (known as privilege escalation). Using these privileges, the attacker might be able to read or write to most objects on the system, including sensitive data of the target application.
 Buffer Overflows
Buffer Overflows
![]() An application must carefully verify user application input. The input might contain improperly formatted data, control sequences, or too much data.
An application must carefully verify user application input. The input might contain improperly formatted data, control sequences, or too much data.
![]() Buffer overflows are a common exploitation method that try to overwrite memory on an application stack by supplying too much data into an input buffer. Initially, it is not easy to discover how to initiate a buffer flow and use it to exploit a system, but once found, attackers can prepackage exploit code for widespread use by script kiddies who use easy-to-find and easy-to-use hacking tools.
Buffer overflows are a common exploitation method that try to overwrite memory on an application stack by supplying too much data into an input buffer. Initially, it is not easy to discover how to initiate a buffer flow and use it to exploit a system, but once found, attackers can prepackage exploit code for widespread use by script kiddies who use easy-to-find and easy-to-use hacking tools.
![]() A buffer overflow is an anomalous condition in which a program writes data beyond the allocated end of a buffer in memory. Buffer overflows usually arise from a bug and the improper use of languages such as C or C++ that are not memory safe. One consequence of the overflow is the overwriting of valid data.
A buffer overflow is an anomalous condition in which a program writes data beyond the allocated end of a buffer in memory. Buffer overflows usually arise from a bug and the improper use of languages such as C or C++ that are not memory safe. One consequence of the overflow is the overwriting of valid data.
![]() Buffer overflows are a commonly exploited computer security risk. Because program control data often sits in the memory areas adjacent to data buffers, executing a buffer overflow condition can make the computer execute arbitrary (and potentially malicious) code that is fed back to the program as data.
Buffer overflows are a commonly exploited computer security risk. Because program control data often sits in the memory areas adjacent to data buffers, executing a buffer overflow condition can make the computer execute arbitrary (and potentially malicious) code that is fed back to the program as data.
![]() A variant of a buffer overflow is a heap overflow. The heap is a stack that is dynamically allocated by the application at runtime and typically contains program data.
A variant of a buffer overflow is a heap overflow. The heap is a stack that is dynamically allocated by the application at runtime and typically contains program data.
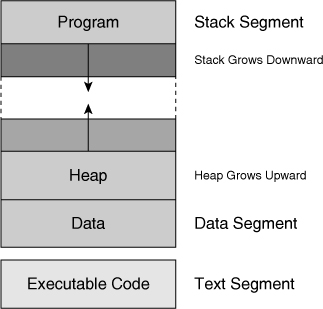
![]() Figure 7-1 shows a basic and generic representation of memory address space.
Figure 7-1 shows a basic and generic representation of memory address space.
| Note |
|
| Note |
|
![]() Buffer overflows are perhaps the most common method of application subversion on the Internet today.
Buffer overflows are perhaps the most common method of application subversion on the Internet today.
Basics of a Typical Buffer-Overflow Exploit
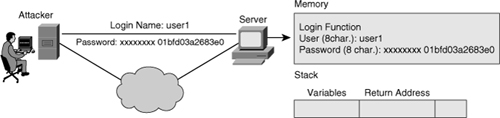
![]() An attacker tries to subvert a program function that reads input and calls a subroutine. The exploitable program function does not perform input length checks and allocates a fixed amount of memory for data, as shown in Figure 7-2.
An attacker tries to subvert a program function that reads input and calls a subroutine. The exploitable program function does not perform input length checks and allocates a fixed amount of memory for data, as shown in Figure 7-2.
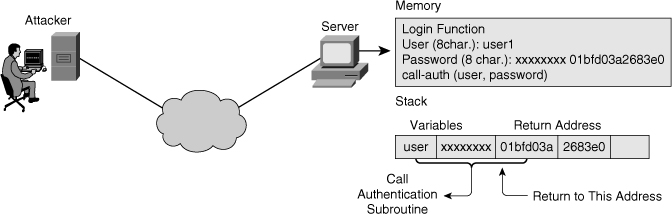
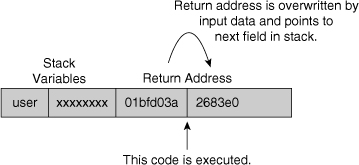
![]() When an application makes a subroutine call, it places all input parameters on the stack. To return from the subroutine, the return address is also placed on the stack by the calling function. An attacker can overwrite the return address by sending data that is longer than the fixed memory space on the stack that the application allocated, as shown in Figure 7-3.
When an application makes a subroutine call, it places all input parameters on the stack. To return from the subroutine, the return address is also placed on the stack by the calling function. An attacker can overwrite the return address by sending data that is longer than the fixed memory space on the stack that the application allocated, as shown in Figure 7-3.
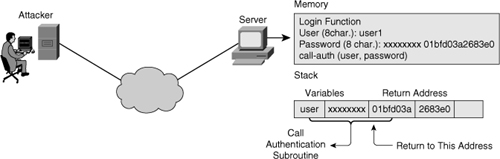
![]() Because of this overwrite, the application returns to an attacker-supplied address, pointing to the malicious code of the attacker, as shown in Figure 7-4. This code is also supplied as part of the overly long input. Arbitrary code can therefore be executed with the privileges of the application.
Because of this overwrite, the application returns to an attacker-supplied address, pointing to the malicious code of the attacker, as shown in Figure 7-4. This code is also supplied as part of the overly long input. Arbitrary code can therefore be executed with the privileges of the application.
Types of Buffer Overflows
![]() Buffer overflows are mostly used to root a system by executing arbitrary codes or to cause a DoS attack. Rooting a system is most easily accomplished with either remote root or local root buffer overflows. Remote root buffer overflows are the more dangerous of the two because if your system is vulnerable, an attacker can “own” it in a matter of seconds. The most dangerous worm attacks have exploited remote root buffer overflows.
Buffer overflows are mostly used to root a system by executing arbitrary codes or to cause a DoS attack. Rooting a system is most easily accomplished with either remote root or local root buffer overflows. Remote root buffer overflows are the more dangerous of the two because if your system is vulnerable, an attacker can “own” it in a matter of seconds. The most dangerous worm attacks have exploited remote root buffer overflows.
| Note |
|
| Note |
|
![]() Local root buffer overflows usually require some assistance in distributing the exploit in the form of a virus that is transported by email or possibly a Trojan horse–infected executable.
Local root buffer overflows usually require some assistance in distributing the exploit in the form of a virus that is transported by email or possibly a Trojan horse–infected executable.
| Note |
|
![]() Buffer overflows are usually the primary conduit through which viruses, worms, and Trojan horses do their damage. For example, the most serious worms, such as SQL Slammer and Code Red, exploit remote root buffer overflows. On the other hand, viruses tend to take advantage of local root buffer overflows. Increasingly, Trojan horses tend to resemble viruses by exploiting local root buffer overflows.
Buffer overflows are usually the primary conduit through which viruses, worms, and Trojan horses do their damage. For example, the most serious worms, such as SQL Slammer and Code Red, exploit remote root buffer overflows. On the other hand, viruses tend to take advantage of local root buffer overflows. Increasingly, Trojan horses tend to resemble viruses by exploiting local root buffer overflows.
Worms
![]() Worms are a particularly dangerous type of hostile code. They replicate themselves over networks by independently exploiting vulnerabilities. Worms usually do not require user participation and can spread extremely fast.
Worms are a particularly dangerous type of hostile code. They replicate themselves over networks by independently exploiting vulnerabilities. Worms usually do not require user participation and can spread extremely fast.
![]() Major components of a worm attack are
Major components of a worm attack are
-
 Vulnerability: A worm installs itself using an exploit vector (email attachment, Trojan horse, or remote root buffer overflow) on a vulnerable system.
Vulnerability: A worm installs itself using an exploit vector (email attachment, Trojan horse, or remote root buffer overflow) on a vulnerable system. -
 Payload: Once the device is infected with a worm, the attacker has access to the host, and it is usually a privileged access. Attackers can also use a local exploit to escalate their privilege level.
Payload: Once the device is infected with a worm, the attacker has access to the host, and it is usually a privileged access. Attackers can also use a local exploit to escalate their privilege level. -
 Propagation mechanism: After gaining access to a device, the worm replicates itself and chooses new targets.
Propagation mechanism: After gaining access to a device, the worm replicates itself and chooses new targets.
![]() Usually, worms are self-contained programs that attack a system attempting to exploit vulnerability. Upon successful exploitation, the worm copies itself from the attacking host to the newly exploited system and the cycle begins again.
Usually, worms are self-contained programs that attack a system attempting to exploit vulnerability. Upon successful exploitation, the worm copies itself from the attacking host to the newly exploited system and the cycle begins again.
Viruses
![]() Viruses are pieces of malicious code that piggyback on legitimate programs or content. They usually replicate by attaching themselves to other software. Viruses usually require end-user activation and can lay dormant for an extended period and then activate at a specific time or date. They can be destructive or harmless (benign). They can be programmed to mutate to avoid detection (polymorphism).
Viruses are pieces of malicious code that piggyback on legitimate programs or content. They usually replicate by attaching themselves to other software. Viruses usually require end-user activation and can lay dormant for an extended period and then activate at a specific time or date. They can be destructive or harmless (benign). They can be programmed to mutate to avoid detection (polymorphism).
![]() The virus code is attached to some executable by the creator (for example, a freeware game). Somehow, that executable circulates to other computers (for example, by USB flash drive or email attachment) or to a file downloaded from an FTP site. When a victim runs the infected executable, the virus is loaded into memory and can now infect other executables on that computer.
The virus code is attached to some executable by the creator (for example, a freeware game). Somehow, that executable circulates to other computers (for example, by USB flash drive or email attachment) or to a file downloaded from an FTP site. When a victim runs the infected executable, the virus is loaded into memory and can now infect other executables on that computer.
![]() A simple virus might install itself at the first line of code of the executable, such that starting the executable jumps right to the code for the virus. The virus might first check the disk for executables it has not yet infected and then infect them. Then, it might do any number of things ranging from harmless (displaying a picture to the screen) to subtly modifying files on the disk.
A simple virus might install itself at the first line of code of the executable, such that starting the executable jumps right to the code for the virus. The virus might first check the disk for executables it has not yet infected and then infect them. Then, it might do any number of things ranging from harmless (displaying a picture to the screen) to subtly modifying files on the disk.
Trojan Horses
![]() A Trojan horse is a program that appears to be normal and useful, but which contains hidden, malicious code that exploits the privileges of the user that runs it. Games are often trojanized in this manner. When running the game, the game works, but in the background, the Trojan horse has been installed on the victim system and continues running after the game has been closed.
A Trojan horse is a program that appears to be normal and useful, but which contains hidden, malicious code that exploits the privileges of the user that runs it. Games are often trojanized in this manner. When running the game, the game works, but in the background, the Trojan horse has been installed on the victim system and continues running after the game has been closed.
![]() The Trojan horse concept is flexible:
The Trojan horse concept is flexible:
-
 A Trojan horse might cause immediate damage.
A Trojan horse might cause immediate damage. -
 A Trojan horse might provide remote access to the system (a back door).
A Trojan horse might provide remote access to the system (a back door). -
 A Trojan horse might perform actions as instructed remotely, such as “send me the password file once per week.”
A Trojan horse might perform actions as instructed remotely, such as “send me the password file once per week.”
![]() Custom-written Trojan horses (for example, Trojan horses with a specific target) are hard to automatically detect.
Custom-written Trojan horses (for example, Trojan horses with a specific target) are hard to automatically detect.
| Tip |
|
Phases of a Generic Attacks
![]() The following is an explanation of the generic phases found in most attacks:
The following is an explanation of the generic phases found in most attacks:
-
 Probe phase: This phase identifies vulnerable targets. The goal of this phase is to find computers that can be subverted. Internet Control Message Protocol (ICMP) ping scans map networks, and scans and identifies operating systems and vulnerable software. Hackers can obtain passwords using social engineering, dictionary attack, brute-force attack, or network sniffing.
Probe phase: This phase identifies vulnerable targets. The goal of this phase is to find computers that can be subverted. Internet Control Message Protocol (ICMP) ping scans map networks, and scans and identifies operating systems and vulnerable software. Hackers can obtain passwords using social engineering, dictionary attack, brute-force attack, or network sniffing. -
 Penetrate phase: Exploit code is transferred to the vulnerable target in this phase. The goal of this phase is to get the target to execute the exploit code through an attack vector, such as a buffer overflow, ActiveX, or Common Gateway Interface (CGI) vulnerability, or an email virus.
Penetrate phase: Exploit code is transferred to the vulnerable target in this phase. The goal of this phase is to get the target to execute the exploit code through an attack vector, such as a buffer overflow, ActiveX, or Common Gateway Interface (CGI) vulnerability, or an email virus. -
 Persist phase: After the attack is successfully launched in memory, its code tries to persist on the target system. The goal of this phase is to ensure that the attacker code is running and available to the attacker even if the system reboots. This ability is achieved by modifying system files, making Registry changes, and installing new code.
Persist phase: After the attack is successfully launched in memory, its code tries to persist on the target system. The goal of this phase is to ensure that the attacker code is running and available to the attacker even if the system reboots. This ability is achieved by modifying system files, making Registry changes, and installing new code. -
 Propagate phase: Next, the attacker attempts to extend the attack to other targets. This phase looks for vulnerable neighboring machines. Propagation vectors include emailing copies of the attack to other systems and uploading files to other systems using file shares or FTP services, active web connections, and file transfers through Internet Relay Chat (IRC).
Propagate phase: Next, the attacker attempts to extend the attack to other targets. This phase looks for vulnerable neighboring machines. Propagation vectors include emailing copies of the attack to other systems and uploading files to other systems using file shares or FTP services, active web connections, and file transfers through Internet Relay Chat (IRC). -
 Paralyze phase: During this phase, actual damage is done to the system. Files can be erased, systems can crash, information can be stolen, and distributed DoS (DDoS) attacks can be launched.
Paralyze phase: During this phase, actual damage is done to the system. Files can be erased, systems can crash, information can be stolen, and distributed DoS (DDoS) attacks can be launched.
Notable Worm and Virus Attacks
![]() Table 7-1 lists a cross-reference of worm and virus attacks over the past 20 years, with some of the differences in how they accomplished the various phases of attack used by hackers. Note how often similar methods are used.
Table 7-1 lists a cross-reference of worm and virus attacks over the past 20 years, with some of the differences in how they accomplished the various phases of attack used by hackers. Note how often similar methods are used.
|
|
|
|
|
|
|
|
| |
|---|---|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 IronPort
IronPort
![]() Cisco IronPort security appliances, shown in Figure 7-5, protect enterprises against Internet threats, with a focus on email and web security products, which are two of the main sources of endpoint threats.
Cisco IronPort security appliances, shown in Figure 7-5, protect enterprises against Internet threats, with a focus on email and web security products, which are two of the main sources of endpoint threats.
![]() The following are the three major security appliance products that IronPort offers:
The following are the three major security appliance products that IronPort offers:
-
 IronPort C-series: Email security appliances
IronPort C-series: Email security appliances -
 IronPort S-series: Web security appliance
IronPort S-series: Web security appliance -
 IronPort M-series: Security management appliance
IronPort M-series: Security management appliance
IronPort SenderBase
![]() At the heart of IronPort’s success is IronPort SenderBase (http://www.senderbase.org). SenderBase is the first and largest email traffic monitoring service. SenderBase collects data from more than 100,000 Internet service providers (ISP), universities, and corporations around the world. SenderBase measures more than 120 different parameters for any email server on the Internet. This massive database receives more than five billion queries per day, with real-time data streaming in from every continent, from both small and large network providers. SenderBase has the most accurate view of the sending patterns of any given mail sender because of the size of the database, and conversely the database has remained the largest in the world because of the accuracy of the data. IronPort licenses SenderBase data to the open-source community and other institutions that are participating in the fight against spam.
At the heart of IronPort’s success is IronPort SenderBase (http://www.senderbase.org). SenderBase is the first and largest email traffic monitoring service. SenderBase collects data from more than 100,000 Internet service providers (ISP), universities, and corporations around the world. SenderBase measures more than 120 different parameters for any email server on the Internet. This massive database receives more than five billion queries per day, with real-time data streaming in from every continent, from both small and large network providers. SenderBase has the most accurate view of the sending patterns of any given mail sender because of the size of the database, and conversely the database has remained the largest in the world because of the accuracy of the data. IronPort licenses SenderBase data to the open-source community and other institutions that are participating in the fight against spam.
IronPort C-Series: Email Security Appliances
![]() The IronPort C-series email security appliances are in production at 8 of the 10 largest ISPs and more than 20 percent of the largest enterprises in the world. These systems have a demonstrated record of unparalleled security and reliability. The same code base that powers the largest customers of IronPort is available in all the IronPort email security appliances, to protect the email systems of enterprises of all sizes. By reducing the downtime associated with spam, viruses, and a wide variety of other threats, these products enable the administration of corporate mail systems and reduce the burden on technical staff. IronPort email security appliances support and protect your email systems—not only from the threats of today, but also from those certain to evolve in the future.
The IronPort C-series email security appliances are in production at 8 of the 10 largest ISPs and more than 20 percent of the largest enterprises in the world. These systems have a demonstrated record of unparalleled security and reliability. The same code base that powers the largest customers of IronPort is available in all the IronPort email security appliances, to protect the email systems of enterprises of all sizes. By reducing the downtime associated with spam, viruses, and a wide variety of other threats, these products enable the administration of corporate mail systems and reduce the burden on technical staff. IronPort email security appliances support and protect your email systems—not only from the threats of today, but also from those certain to evolve in the future.
![]() The C-series is an all-inclusive Mail Transfer Agent (MTA) that provides the following services:
The C-series is an all-inclusive Mail Transfer Agent (MTA) that provides the following services:
-
 Antispam
Antispam -
 Antivirus
Antivirus -
 Policy enforcement
Policy enforcement -
 Mail routing
Mail routing
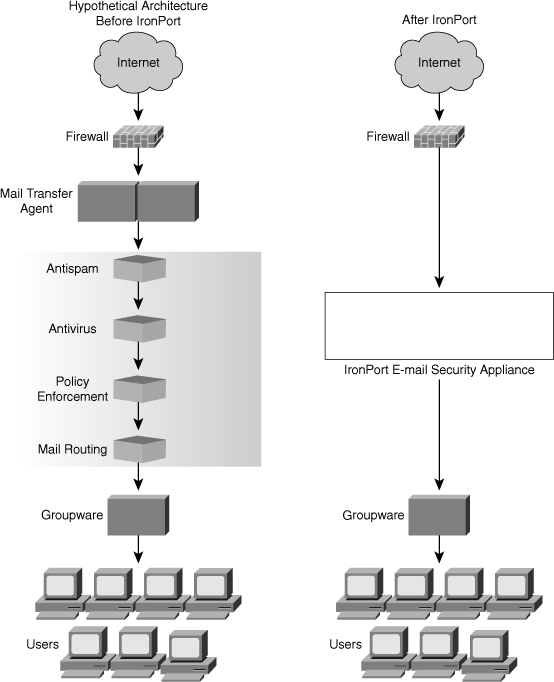
![]() Figure 7-6 shows a before and after network topology using IronPort C-series.
Figure 7-6 shows a before and after network topology using IronPort C-series.
| Note |
|
IronPort S-Series: Web Security Appliances
![]() The IronPort S-series is the fastest web security appliance in the industry. Spyware has quickly evolved to become one of the most significant corporate security issues. More than 80 percent of corporate PCs are infected with spyware, yet less than 10 percent of corporations have deployed perimeter spyware defenses. The speed, variety, and maliciousness of spyware and web-based malware attacks have highlighted the importance of a robust, secure platform to protect the enterprise network perimeter from such threats. The IronPort S-series appliances combine a high-performance security platform with the exclusive Web Reputation technology of IronPort and the breakthrough Dynamic Vectoring and Streaming (DVS) engine of IronPort, a new scanning technology that enables signature-based spyware filtering. Robust management and reporting tools deliver ease of administration and complete visibility into threat-related activity.
The IronPort S-series is the fastest web security appliance in the industry. Spyware has quickly evolved to become one of the most significant corporate security issues. More than 80 percent of corporate PCs are infected with spyware, yet less than 10 percent of corporations have deployed perimeter spyware defenses. The speed, variety, and maliciousness of spyware and web-based malware attacks have highlighted the importance of a robust, secure platform to protect the enterprise network perimeter from such threats. The IronPort S-series appliances combine a high-performance security platform with the exclusive Web Reputation technology of IronPort and the breakthrough Dynamic Vectoring and Streaming (DVS) engine of IronPort, a new scanning technology that enables signature-based spyware filtering. Robust management and reporting tools deliver ease of administration and complete visibility into threat-related activity.
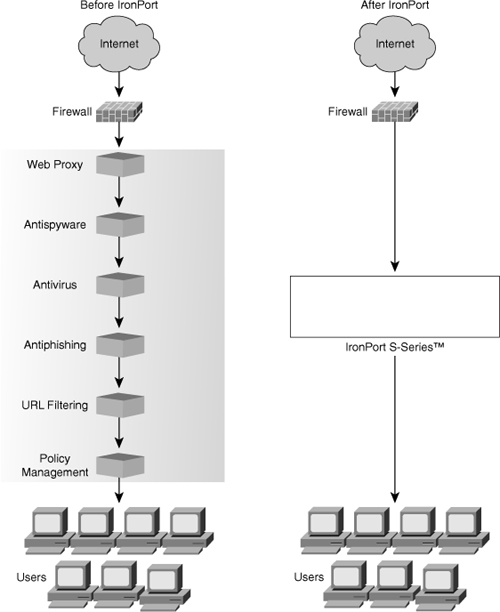
![]() Figure 7-7 shows a before and after network topology using IronPort S-series.
Figure 7-7 shows a before and after network topology using IronPort S-series.
| Note |
|
 Cisco NAC Products
Cisco NAC Products
![]() The purpose of Cisco Network Access Control (NAC) is to allow only authorized and compliant systems (whether managed or unmanaged) to access the network and to enforce network security policy. In this way, Cisco NAC helps maintain network stability. NAC provides four key features:
The purpose of Cisco Network Access Control (NAC) is to allow only authorized and compliant systems (whether managed or unmanaged) to access the network and to enforce network security policy. In this way, Cisco NAC helps maintain network stability. NAC provides four key features:
-
 Authentication and authorization
Authentication and authorization -
 Posture assessment (evaluating an incoming device against the policies of the network)
Posture assessment (evaluating an incoming device against the policies of the network) -
 Quarantining of noncompliant systems
Quarantining of noncompliant systems -
 Remediation of noncompliant systems
Remediation of noncompliant systems
![]() Cisco NAC products come in these general categories:
Cisco NAC products come in these general categories:
-
 NAC framework: The NAC framework uses the existing Cisco network infrastructure and third-party software to enforce security policy compliance on all endpoints. The NAC framework is a system that is suited for high-performance network environments with diverse endpoints. These environments require a consistent LAN, WAN, wireless, extranet, and remote-access solution that integrates into the existing security and patch software, tools, and processes. Different devices in the network, not necessarily one device, can provide the four key features of NAC.
NAC framework: The NAC framework uses the existing Cisco network infrastructure and third-party software to enforce security policy compliance on all endpoints. The NAC framework is a system that is suited for high-performance network environments with diverse endpoints. These environments require a consistent LAN, WAN, wireless, extranet, and remote-access solution that integrates into the existing security and patch software, tools, and processes. Different devices in the network, not necessarily one device, can provide the four key features of NAC. -
 Cisco NAC Appliance: The Cisco NAC Appliance solution condenses the four key NAC functions into an appliance form and provides a turnkey solution to control network access. This solution is a natural fit for medium-scale networks that require a self-contained, turnkey solution. Cisco NAC Appliance is especially ideal for organizations that need simplified and integrated tracking of operating system and antivirus patches and vulnerability updates. Cisco NAC Appliance does not require a Cisco network.
Cisco NAC Appliance: The Cisco NAC Appliance solution condenses the four key NAC functions into an appliance form and provides a turnkey solution to control network access. This solution is a natural fit for medium-scale networks that require a self-contained, turnkey solution. Cisco NAC Appliance is especially ideal for organizations that need simplified and integrated tracking of operating system and antivirus patches and vulnerability updates. Cisco NAC Appliance does not require a Cisco network.
![]() Table 7-2 summarizes the differences between NAC framework and Cisco NAC Appliance.
Table 7-2 summarizes the differences between NAC framework and Cisco NAC Appliance.
|
|
|
|---|---|
|
|
|
|
|
|
NAC Framework
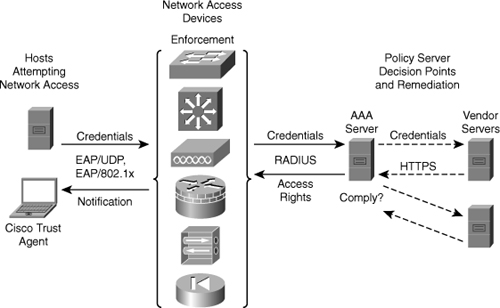
![]() Figure 7-8 displays components of a NAC framework that is used to provide compliance-based access control. NAC functions, including authentication, authorization, and accounting (AAA), scanning, and remediation, are performed by other Cisco products, such as a Cisco Secure Access Control Server (ACS), or partner products such as TrendMicro.
Figure 7-8 displays components of a NAC framework that is used to provide compliance-based access control. NAC functions, including authentication, authorization, and accounting (AAA), scanning, and remediation, are performed by other Cisco products, such as a Cisco Secure Access Control Server (ACS), or partner products such as TrendMicro.
![]() QualysGuard, released by Qualys, a Cisco partner, can automatically audit hosts to determine their security position.
QualysGuard, released by Qualys, a Cisco partner, can automatically audit hosts to determine their security position.
![]() The goal of both the NAC framework and the Cisco NAC Appliance is to admit on to the network only those hosts that are authenticated and have had their security posture examined and approved. The net result of such a thorough examination before allowing connectivity is a tremendous reduction in total cost of ownership (TCO) because only known, secure machines are allowed to connect. Therefore, laptops that have been on the road for weeks and have possibly been infected or were unable to receive current security updates cannot connect into the network and unleash a DoS attack.
The goal of both the NAC framework and the Cisco NAC Appliance is to admit on to the network only those hosts that are authenticated and have had their security posture examined and approved. The net result of such a thorough examination before allowing connectivity is a tremendous reduction in total cost of ownership (TCO) because only known, secure machines are allowed to connect. Therefore, laptops that have been on the road for weeks and have possibly been infected or were unable to receive current security updates cannot connect into the network and unleash a DoS attack.
![]() In Figure 7-8, the network devices function as the enforcement layer. They force the clients to authenticate and then query a RADIUS server for authentication and authorization. The RADIUS server can query other devices, such as a TrendMicro antivirus server, and reply to the network enforcers. If everything is up to standard, the host is identified and admitted to the network.
In Figure 7-8, the network devices function as the enforcement layer. They force the clients to authenticate and then query a RADIUS server for authentication and authorization. The RADIUS server can query other devices, such as a TrendMicro antivirus server, and reply to the network enforcers. If everything is up to standard, the host is identified and admitted to the network.
Cisco NAC Appliance: Components
![]() The Cisco NAC Appliance consolidates all the functions of the NAC framework into a single network appliance fulfilling all the same roles. The following are the major components of the Cisco NAC Appliance and the tasks they accomplish:
The Cisco NAC Appliance consolidates all the functions of the NAC framework into a single network appliance fulfilling all the same roles. The following are the major components of the Cisco NAC Appliance and the tasks they accomplish:
-
 Cisco NAC Appliance Server (NAS): Cisco NAS is a device that is used to perform network access control. This security enforcement device is implemented at the network level. It can be implemented in-band or out-of-band, in Layers 2 or Layer 3, as a virtual gateway or as a real IP gateway, and it can be deployed centrally or around the globe. The Cisco NAS performs device compliance checks as users attempt to access the network.
Cisco NAC Appliance Server (NAS): Cisco NAS is a device that is used to perform network access control. This security enforcement device is implemented at the network level. It can be implemented in-band or out-of-band, in Layers 2 or Layer 3, as a virtual gateway or as a real IP gateway, and it can be deployed centrally or around the globe. The Cisco NAS performs device compliance checks as users attempt to access the network. -
 Cisco NAC Appliance Manager (NAM): Cisco NAM is a centralized administrative interface that is used by technical support personnel. The Cisco NAM provides a web-based interface for creating security policies and managing online users. It can also act as an authentication proxy to authentication servers on the back end. Administrators can use it to establish user roles, compliance checks, and remediation requirements. The Cisco NAM communicates with, and manages, the Cisco NAS, which is the enforcement component of the Cisco NAC Appliance.
Cisco NAC Appliance Manager (NAM): Cisco NAM is a centralized administrative interface that is used by technical support personnel. The Cisco NAM provides a web-based interface for creating security policies and managing online users. It can also act as an authentication proxy to authentication servers on the back end. Administrators can use it to establish user roles, compliance checks, and remediation requirements. The Cisco NAM communicates with, and manages, the Cisco NAS, which is the enforcement component of the Cisco NAC Appliance. -
 Cisco NAC Appliance Agent (NAA): Cisco NAA is client software that facilitates network admission. This lightweight, read-only agent runs on an endpoint machine. It performs a deep inspection of the security profile of a local machine by analyzing Registry settings, services, and files. Through this inspection, it can determine whether a device has a required hotfix; and can then run the correct antivirus software version and other security software, such as Cisco Security Agents. For unmanaged assets, the Cisco NAA can be downloaded as needed.
Cisco NAC Appliance Agent (NAA): Cisco NAA is client software that facilitates network admission. This lightweight, read-only agent runs on an endpoint machine. It performs a deep inspection of the security profile of a local machine by analyzing Registry settings, services, and files. Through this inspection, it can determine whether a device has a required hotfix; and can then run the correct antivirus software version and other security software, such as Cisco Security Agents. For unmanaged assets, the Cisco NAA can be downloaded as needed. -
 Ruleset updates: Automatic updates are used to keep the security level high by always providing the latest virus updates, software patches, and so on, for quarantined hosts.
Ruleset updates: Automatic updates are used to keep the security level high by always providing the latest virus updates, software patches, and so on, for quarantined hosts.
![]() The Cisco NAC Appliance extends NAC to all network access methods, including access through LANs, remote-access gateways, and wireless access points. The Cisco NAC Appliance also supports posture assessment for guest users.
The Cisco NAC Appliance extends NAC to all network access methods, including access through LANs, remote-access gateways, and wireless access points. The Cisco NAC Appliance also supports posture assessment for guest users.
![]() Cisco NAC Appliance provides the following benefits:
Cisco NAC Appliance provides the following benefits:
-
 It recognizes users, their devices, and their roles in the network. This occurs at the point of authentication, before malicious code can cause damage.
It recognizes users, their devices, and their roles in the network. This occurs at the point of authentication, before malicious code can cause damage. -
 It evaluates whether machines are compliant with security policies. Security policies can include specific antivirus or antispyware software, operating system updates, or patches. The Cisco NAC Appliance supports policies that vary by user type, device type, or operating system.
It evaluates whether machines are compliant with security policies. Security policies can include specific antivirus or antispyware software, operating system updates, or patches. The Cisco NAC Appliance supports policies that vary by user type, device type, or operating system. -
 It enforces security policies by blocking and isolating noncompliant machines. A network administrator will be advised of the noncompliance and will proceed to repair the host.
It enforces security policies by blocking and isolating noncompliant machines. A network administrator will be advised of the noncompliance and will proceed to repair the host.
![]() Noncompliant machines are redirected into a quarantine area, where remediation occurs at the discretion of the administrator.
Noncompliant machines are redirected into a quarantine area, where remediation occurs at the discretion of the administrator.
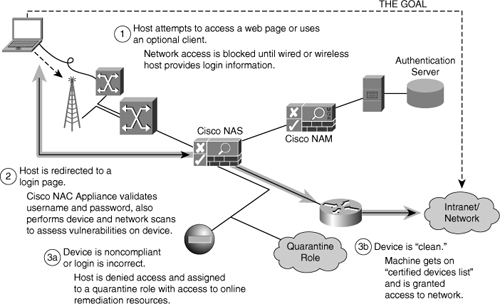
![]() Figure 7-9 illustrates the Cisco NAC Appliance process:
Figure 7-9 illustrates the Cisco NAC Appliance process:
-
 The user attempts to access a network resource.
The user attempts to access a network resource. -
 The user is redirected to a login page.
The user is redirected to a login page. -
 The host is authenticated and optionally scanned for posture compliance.
The host is authenticated and optionally scanned for posture compliance.-
 If not compliant, the host is quarantined to a VLAN where the host can be patched and become compliant.
If not compliant, the host is quarantined to a VLAN where the host can be patched and become compliant. -
 If compliant, the host is granted access to the network.
If compliant, the host is granted access to the network.
-
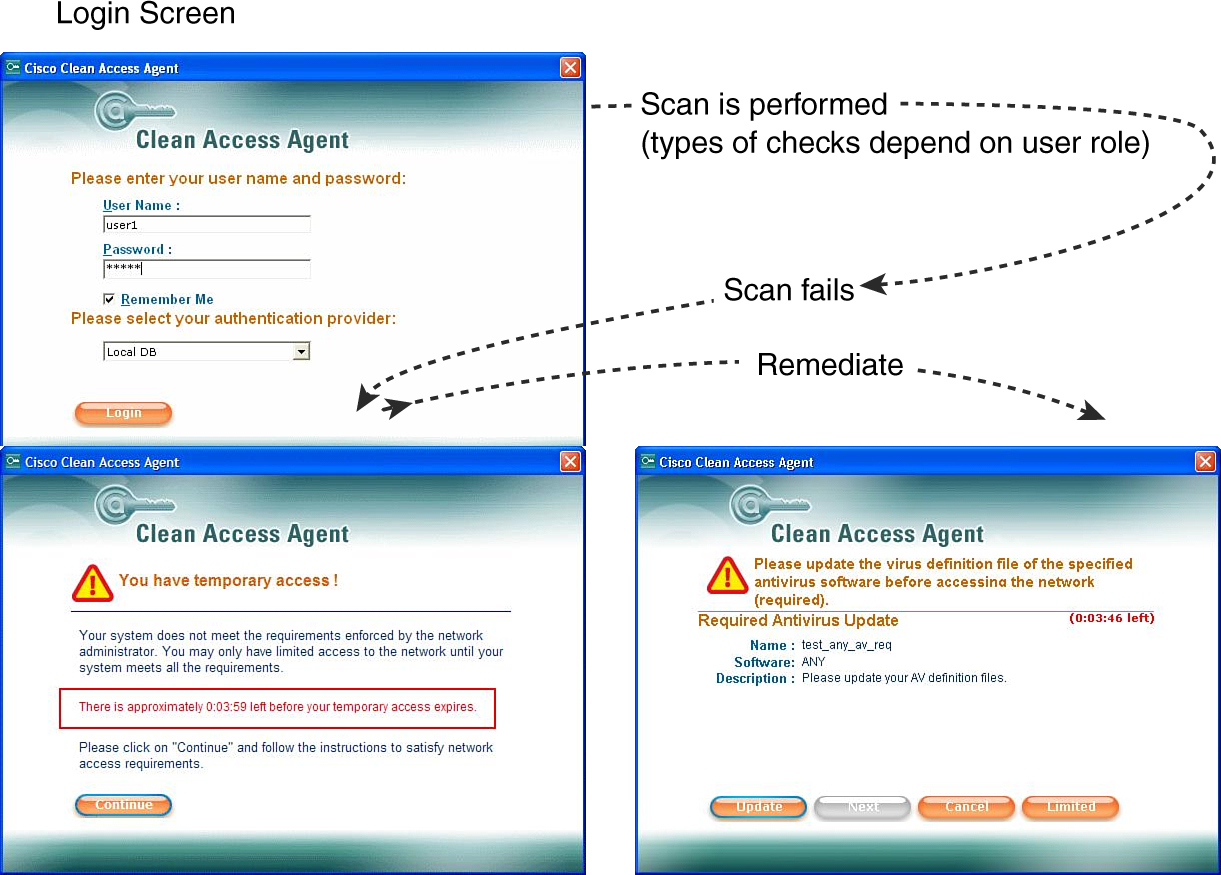
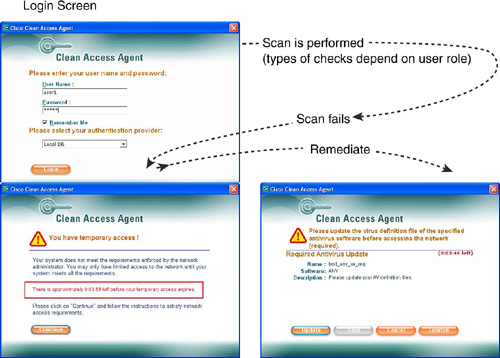
![]() The Cisco NAA is the software interface that users sees when they interact with the Cisco NAC Appliance. Figure 7-10 shows the three windows that a user sees.
The Cisco NAA is the software interface that users sees when they interact with the Cisco NAC Appliance. Figure 7-10 shows the three windows that a user sees.
-
 The first window the user sees is the initial logon window, where the user enters the username and password, and the system is scanned for compliance.
The first window the user sees is the initial logon window, where the user enters the username and password, and the system is scanned for compliance. -
 If the scan fails, the user is granted temporary access and will see the You Have Temporary Access window.
If the scan fails, the user is granted temporary access and will see the You Have Temporary Access window. -
 If remediation is available, the Please Download and Install the Required Software window is presented, inviting the user to install the necessary software to become compliant.
If remediation is available, the Please Download and Install the Required Software window is presented, inviting the user to install the necessary software to become compliant.
 Cisco Security Agent
Cisco Security Agent
![]() Cisco Security Agent, a host intrusion prevention system (HIPS) product, is software that provides endpoint security by providing threat protection capabilities for server, desktop, and point-of-service computing systems. Because a single management console can support up to 100,000 agents, it is a highly scalable solution.
Cisco Security Agent, a host intrusion prevention system (HIPS) product, is software that provides endpoint security by providing threat protection capabilities for server, desktop, and point-of-service computing systems. Because a single management console can support up to 100,000 agents, it is a highly scalable solution.
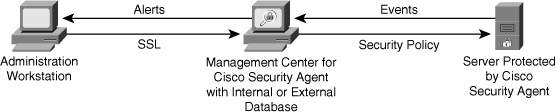
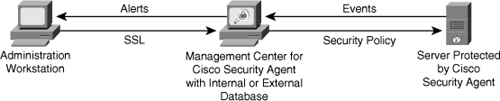
![]() The Cisco Security Agent architecture model consists of two components, as shown in Figure 7-11:
The Cisco Security Agent architecture model consists of two components, as shown in Figure 7-11:
-
 Management Center for Cisco Security Agents: Management Center for Cisco Security Agent enables you to divide network hosts into groups by function and security requirements, and then configure security policies for those groups. Management Center for Cisco Security Agent can maintain a log of security violations and send alerts by email or pager.
Management Center for Cisco Security Agents: Management Center for Cisco Security Agent enables you to divide network hosts into groups by function and security requirements, and then configure security policies for those groups. Management Center for Cisco Security Agent can maintain a log of security violations and send alerts by email or pager. -
 Cisco Security Agent: The Cisco Security Agent component is installed on the host system and continuously monitors local system activity and analyzes the operations of that system. Cisco Security Agent takes proactive action to block attempted malicious activity and polls the Management Center for Cisco Security Agent at configurable intervals for policy updates. Obviously, the Management Center should also run CSA.
Cisco Security Agent: The Cisco Security Agent component is installed on the host system and continuously monitors local system activity and analyzes the operations of that system. Cisco Security Agent takes proactive action to block attempted malicious activity and polls the Management Center for Cisco Security Agent at configurable intervals for policy updates. Obviously, the Management Center should also run CSA.
| Tip |
|
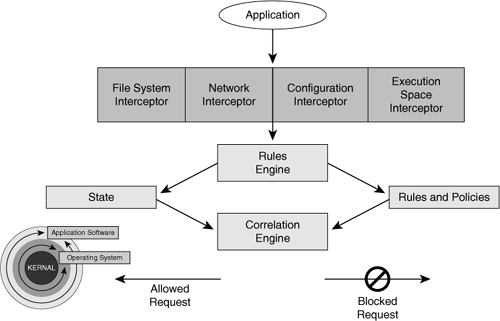
![]() When an application needs access to system resources, it makes an operating system call to the kernel. Cisco Security Agent intercepts these operating system calls and compares them with the cached security policy, as shown in Figure 7-12. If the request does not violate the policy, it is passed to the kernel for execution.
When an application needs access to system resources, it makes an operating system call to the kernel. Cisco Security Agent intercepts these operating system calls and compares them with the cached security policy, as shown in Figure 7-12. If the request does not violate the policy, it is passed to the kernel for execution.
![]() If the request violates the security policy, Cisco Security Agent blocks the request and takes the following actions:
If the request violates the security policy, Cisco Security Agent blocks the request and takes the following actions:
-
 An appropriate error message is passed back to the application.
An appropriate error message is passed back to the application. -
 An alert is generated and sent to the Management Center for Cisco Security Agent.
An alert is generated and sent to the Management Center for Cisco Security Agent.
![]() Cisco Security Agent correlates this particular operating system call with the other calls made by that application or process, and correlates these events to detect malicious activity.
Cisco Security Agent correlates this particular operating system call with the other calls made by that application or process, and correlates these events to detect malicious activity.
![]() Cisco Security Agent provides protection through the deployment of four interceptors:
Cisco Security Agent provides protection through the deployment of four interceptors:
-
 File system interceptor: All file read or write requests are intercepted and allowed, or denied, based on the security policy.
File system interceptor: All file read or write requests are intercepted and allowed, or denied, based on the security policy. -
 Network interceptor: Network driver interface specification (NDIS) changes are controlled and network connections are cleared through the security policy. The number of network connections that are allowed within a specified time can also be limited to prevent DoS attacks.
Network interceptor: Network driver interface specification (NDIS) changes are controlled and network connections are cleared through the security policy. The number of network connections that are allowed within a specified time can also be limited to prevent DoS attacks. -
 Configuration interceptor: Read/write requests to the Registry in Windows or to rc configuration files on UNIX are intercepted. This interception occurs because modification of the operating system configuration can have serious consequences. Therefore, Cisco Security Agent tightly controls read/write requests to the Registry.
Configuration interceptor: Read/write requests to the Registry in Windows or to rc configuration files on UNIX are intercepted. This interception occurs because modification of the operating system configuration can have serious consequences. Therefore, Cisco Security Agent tightly controls read/write requests to the Registry. -
 Execution space interceptor: This interceptor maintains the integrity of the dynamic runtime environment of each application by detecting and blocking write requests to memory that is not owned by the requesting application. Attempts by one application to inject code, such as a shared library or dynamic link library (DLL) into another are also detected and blocked. The interceptor also detects buffer-overflow attacks. This results in maintaining the integrity of dynamic resources, such as the file system and configuration of web services. In addition, the integrity of highly dynamic resources, such as memory and network I/O, is preserved.
Execution space interceptor: This interceptor maintains the integrity of the dynamic runtime environment of each application by detecting and blocking write requests to memory that is not owned by the requesting application. Attempts by one application to inject code, such as a shared library or dynamic link library (DLL) into another are also detected and blocked. The interceptor also detects buffer-overflow attacks. This results in maintaining the integrity of dynamic resources, such as the file system and configuration of web services. In addition, the integrity of highly dynamic resources, such as memory and network I/O, is preserved.
Cisco Security Agent Interceptors
![]() By intercepting communication between applications and the underlying system, Cisco Security Agent combines the functionality of the following traditional security approaches:
By intercepting communication between applications and the underlying system, Cisco Security Agent combines the functionality of the following traditional security approaches:
-
 Distributed firewall: The network interceptor performs the functions of a host firewall.
Distributed firewall: The network interceptor performs the functions of a host firewall. -
 HIPS: The network interceptor teams with the execution space interceptor to provide the alerting capability of a HIPS, with the proactive enforcement of a security policy.
HIPS: The network interceptor teams with the execution space interceptor to provide the alerting capability of a HIPS, with the proactive enforcement of a security policy. -
 Application sandbox: An application sandbox is an execution space in which you can run suspect programs with less-than-normal access to system resources. This security service is provided by a combination of file system, configuration, and execution space interceptors.
Application sandbox: An application sandbox is an execution space in which you can run suspect programs with less-than-normal access to system resources. This security service is provided by a combination of file system, configuration, and execution space interceptors. -
 Network worm prevention: The network and execution space interceptors provide worm prevention without a need for updates.
Network worm prevention: The network and execution space interceptors provide worm prevention without a need for updates. -
 File-integrity monitor: The file system and the configuration interceptors act as a file-integrity monitor.
File-integrity monitor: The file system and the configuration interceptors act as a file-integrity monitor.
![]() Table 7-3 summarizes the Cisco Security Agent interceptors.
Table 7-3 summarizes the Cisco Security Agent interceptors.
|
|
|
|
|
|
|---|---|---|---|---|
|
|
| |||
|
|
|
| ||
|
|
|
| ||
|
|
|
|
![]() The default policies on Cisco Security Agent implement all of these security features. Customers can easily create or change policies; however, the default policies instantly provide all of these protections.
The default policies on Cisco Security Agent implement all of these security features. Customers can easily create or change policies; however, the default policies instantly provide all of these protections.
Cisco Security Agent Attack Response
![]() Malicious attacks come in thousands of varieties, and new attacks are constantly being devised to exploit newly discovered vulnerabilities.
Malicious attacks come in thousands of varieties, and new attacks are constantly being devised to exploit newly discovered vulnerabilities.
![]() An analysis of the logical progression of an attack helps illustrate how almost every attack intends to gain control of core mechanisms in the target system. Table 7-4 provides an overview of the different phases of attacks. Significant differences exist between the attack mechanisms used in the probe and penetrate phases compared to the attack mechanisms used in the persist phase.
An analysis of the logical progression of an attack helps illustrate how almost every attack intends to gain control of core mechanisms in the target system. Table 7-4 provides an overview of the different phases of attacks. Significant differences exist between the attack mechanisms used in the probe and penetrate phases compared to the attack mechanisms used in the persist phase.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The first two stages change continuously, with new vulnerabilities being discovered and custom exploits being created almost every day. Combating attacks at the probe and penetrate phases requires constant updating of malicious IPS signatures and firewall defenses as these attacks evolve. Attacks at these early phases also lend themselves to evasion techniques, such as Unicode encoding of web strings or overlapping packet fragments. The mutability of attacks at the penetrate stage requires a significant amount of interpretation, because false alarms that require time-consuming review by a security administrator can be generated.
The first two stages change continuously, with new vulnerabilities being discovered and custom exploits being created almost every day. Combating attacks at the probe and penetrate phases requires constant updating of malicious IPS signatures and firewall defenses as these attacks evolve. Attacks at these early phases also lend themselves to evasion techniques, such as Unicode encoding of web strings or overlapping packet fragments. The mutability of attacks at the penetrate stage requires a significant amount of interpretation, because false alarms that require time-consuming review by a security administrator can be generated.
![]() In contrast, attack mechanisms in the persist phase and the later phases are comparatively stable. The malicious activities of an attacker are limited, and an attack involves making a system call to the kernel to access the system resources. The malicious code can attempt to modify the operating system, modify files, create or alter network connections, or violate the memory space of active processes. The list of potential attacks on system resources has remained stable. These attacks use different vectors to access the target systems.
In contrast, attack mechanisms in the persist phase and the later phases are comparatively stable. The malicious activities of an attacker are limited, and an attack involves making a system call to the kernel to access the system resources. The malicious code can attempt to modify the operating system, modify files, create or alter network connections, or violate the memory space of active processes. The list of potential attacks on system resources has remained stable. These attacks use different vectors to access the target systems.
![]() Because consistently identifying attacks in their early phases is nearly impossible, Cisco Security Agent focuses on providing proactive security by controlling access to system resources. This approach avoids the need for updating defenses to keep up with the latest attack and protects hosts from a new attack. For example, the Nimda and Slammer worms caused millions of dollars of damage to enterprises on the first day of their appearance, before updates were available; but Cisco Security Agent stopped these attacks by identifying their malicious behavior without any updates.
Because consistently identifying attacks in their early phases is nearly impossible, Cisco Security Agent focuses on providing proactive security by controlling access to system resources. This approach avoids the need for updating defenses to keep up with the latest attack and protects hosts from a new attack. For example, the Nimda and Slammer worms caused millions of dollars of damage to enterprises on the first day of their appearance, before updates were available; but Cisco Security Agent stopped these attacks by identifying their malicious behavior without any updates.
 Endpoint Security Best Practices
Endpoint Security Best Practices
![]() Trusted operating systems exist, but are expensive and can be cumbersome to support. Their appropriate use would be for critical servers or workstations. Although there has been some progress in the past 10 years, the default configuration of a typical modern operating system is still quite untrustworthy. Operating system hardening should be considered mandatory for use in sensitive environments. A hardened system resists an attacker when alternate paths to sensitive data are attempted.
Trusted operating systems exist, but are expensive and can be cumbersome to support. Their appropriate use would be for critical servers or workstations. Although there has been some progress in the past 10 years, the default configuration of a typical modern operating system is still quite untrustworthy. Operating system hardening should be considered mandatory for use in sensitive environments. A hardened system resists an attacker when alternate paths to sensitive data are attempted.
![]() Network access controls (firewalls) should be used to limit the exposure of hosts. You should allow only necessary traffic to reach sensitive machines.
Network access controls (firewalls) should be used to limit the exposure of hosts. You should allow only necessary traffic to reach sensitive machines.
![]() Security add-ons, such as integrity checkers, IPSs, and host firewalls, are recommended for systems that perform important services.
Security add-ons, such as integrity checkers, IPSs, and host firewalls, are recommended for systems that perform important services.
![]() Design applications with security in mind from the start:
Design applications with security in mind from the start:
-
 Apply the least privilege principle.
Apply the least privilege principle. -
 Use modularization and multiple tiers of application functionality, spread over multiple servers.
Use modularization and multiple tiers of application functionality, spread over multiple servers.
![]() To manage host and application risks, use multiple protection methods together to form a multilayered security system. A multilayered security system does not rely on a single security mechanism to perform a function, because that mechanism might be compromised. Instead, different security mechanisms provide a similar protection function and back each other up. This applies universally to any security system and is considered good practice in a security design.
To manage host and application risks, use multiple protection methods together to form a multilayered security system. A multilayered security system does not rely on a single security mechanism to perform a function, because that mechanism might be compromised. Instead, different security mechanisms provide a similar protection function and back each other up. This applies universally to any security system and is considered good practice in a security design.
![]() The following are application protection methods:
The following are application protection methods:
-
 Application access controls (enforcing least privilege) coupled with secure programming is the most significant cornerstones of application security. Secure development is typically expensive and slow. With the creation of safer high-level languages and the awareness of developers to security issues in programming, many current systems can provide high levels of application security. Most stock software still in use today by many businesses is vulnerable to simple attacks to defeat its security.
Application access controls (enforcing least privilege) coupled with secure programming is the most significant cornerstones of application security. Secure development is typically expensive and slow. With the creation of safer high-level languages and the awareness of developers to security issues in programming, many current systems can provide high levels of application security. Most stock software still in use today by many businesses is vulnerable to simple attacks to defeat its security. -
 Cryptography, if used properly, can provide confidentiality, integrity, and authenticity guarantees for data. Cryptographic methods often protect data when it is outside the control of the application, such as when the data on the disk drives is encrypted and can only be read by the application. More commonly, all data between the client and the server is encrypted, providing confidentiality over an unsafe network.
Cryptography, if used properly, can provide confidentiality, integrity, and authenticity guarantees for data. Cryptographic methods often protect data when it is outside the control of the application, such as when the data on the disk drives is encrypted and can only be read by the application. More commonly, all data between the client and the server is encrypted, providing confidentiality over an unsafe network. -
 Do not trust data from outside sources, and always perform strict input validation.
Do not trust data from outside sources, and always perform strict input validation. -
 Assume that users of the application may be malicious (which is not always the case).
Assume that users of the application may be malicious (which is not always the case).


0 comments
Post a Comment