Overview
![]() This chapter introduces the concepts of cryptography and covers the following topics:
This chapter introduces the concepts of cryptography and covers the following topics:
-
 Encryption, hashing, and digital signatures and how they provide confidentiality, integrity, and nonrepudiation
Encryption, hashing, and digital signatures and how they provide confidentiality, integrity, and nonrepudiation -
 Methods, algorithms, and purposes of symmetric encryption
Methods, algorithms, and purposes of symmetric encryption -
 Use and purpose of hashes and digital signatures in providing integrity and nonrepudiation
Use and purpose of hashes and digital signatures in providing integrity and nonrepudiation -
 Use and purpose of asymmetric encryption and Public Key Infrastructure (PKI)
Use and purpose of asymmetric encryption and Public Key Infrastructure (PKI)
![]() An IP Security (IPsec) virtual private network (VPN) is often used to connect branch offices, remote employees, and business partners to the resources of your company. It is a reliable way to maintain your company’s privacy while streamlining operations, reducing costs, and allowing flexible network administration. This chapter provides a primer on the theory of cryptography; describes the fundamental concepts, technologies, and terms used with VPNs; and describes how to configure an IPsec site-to-site VPN tunnel using both the command-line interface (CLI) and the Cisco Router and Security Device Manager (SDM).
An IP Security (IPsec) virtual private network (VPN) is often used to connect branch offices, remote employees, and business partners to the resources of your company. It is a reliable way to maintain your company’s privacy while streamlining operations, reducing costs, and allowing flexible network administration. This chapter provides a primer on the theory of cryptography; describes the fundamental concepts, technologies, and terms used with VPNs; and describes how to configure an IPsec site-to-site VPN tunnel using both the command-line interface (CLI) and the Cisco Router and Security Device Manager (SDM).
Examining Cryptographic Services
![]() Cryptographic services are the foundation for many security implementations, and provide confidentiality and integrity of data, when data might be exposed to untrusted parties. Understanding the basic functions of cryptography and how encryption and hashing provide confidentiality and integrity is important to creating a successful security policy. It is also important to understand the issues that are involved in key management.
Cryptographic services are the foundation for many security implementations, and provide confidentiality and integrity of data, when data might be exposed to untrusted parties. Understanding the basic functions of cryptography and how encryption and hashing provide confidentiality and integrity is important to creating a successful security policy. It is also important to understand the issues that are involved in key management.
 Cryptology Overview
Cryptology Overview
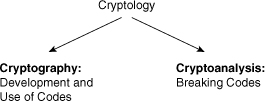
![]() Cryptology is the science of the making and breaking of secret codes. Cryptology is broken into two separate disciplines, as shown in Figure 4-1.
Cryptology is the science of the making and breaking of secret codes. Cryptology is broken into two separate disciplines, as shown in Figure 4-1.
![]() Cryptography is the development and use of codes, and cryptanalysis is the breaking of those codes. A symbiotic relationship exists between the two disciplines because each makes the other one better. National security organizations employ members of both disciplines and put them to work against each other.
Cryptography is the development and use of codes, and cryptanalysis is the breaking of those codes. A symbiotic relationship exists between the two disciplines because each makes the other one better. National security organizations employ members of both disciplines and put them to work against each other.
![]() In the past, there have been times when each discipline has been ahead of the other. For example, during the Hundred Years’ War between France and England, the cryptanalysts were ahead of the cryptographers. France believed that its cipher was unbreakable; however, the Englishmen were able to break it. Some historians believe that World War II largely turned on the fact that the winning side on both fronts was much more successful than the losing side at cracking the encryption of its adversary.
In the past, there have been times when each discipline has been ahead of the other. For example, during the Hundred Years’ War between France and England, the cryptanalysts were ahead of the cryptographers. France believed that its cipher was unbreakable; however, the Englishmen were able to break it. Some historians believe that World War II largely turned on the fact that the winning side on both fronts was much more successful than the losing side at cracking the encryption of its adversary.
![]() It is an ironic fact of cryptography that it is impossible to prove an algorithm secure. You can prove only that it is not vulnerable to known cryptanalytic attacks. If there are methods that have been developed but are unknown to the cryptanalysts, an algorithm might be able to be cracked. You can prove only invulnerability to known attacks, except for a brute-force attack.
It is an ironic fact of cryptography that it is impossible to prove an algorithm secure. You can prove only that it is not vulnerable to known cryptanalytic attacks. If there are methods that have been developed but are unknown to the cryptanalysts, an algorithm might be able to be cracked. You can prove only invulnerability to known attacks, except for a brute-force attack.
![]() All algorithms are vulnerable to brute force. If every possible key is tried, one of the keys has to work. Therefore, no algorithm is unbreakable. The best you can hope for are algorithms that are vulnerable only to brute-force attacks.
All algorithms are vulnerable to brute force. If every possible key is tried, one of the keys has to work. Therefore, no algorithm is unbreakable. The best you can hope for are algorithms that are vulnerable only to brute-force attacks.
| Note |
|
The History of Cryptography
![]() The history of cryptography starts in diplomatic circles thousands of years ago. Messengers from a king’s court would take encrypted messages to other courts. Occasionally, other courts not involved in the communication would attempt to steal any message sent to a kingdom they considered an adversary. Encryption was first used to prevent this information theft.
The history of cryptography starts in diplomatic circles thousands of years ago. Messengers from a king’s court would take encrypted messages to other courts. Occasionally, other courts not involved in the communication would attempt to steal any message sent to a kingdom they considered an adversary. Encryption was first used to prevent this information theft.
![]() Not long after, military commanders started using encryption to secure messages. The messengers had challenges in many ways greater than that of the diplomatic messenger because killing the messenger to get the message was common. With the stakes so high, military commanders resorted to encryption to secure their military communications.
Not long after, military commanders started using encryption to secure messages. The messengers had challenges in many ways greater than that of the diplomatic messenger because killing the messenger to get the message was common. With the stakes so high, military commanders resorted to encryption to secure their military communications.
![]() The cipher attributed to Julius Caesar was a simple substitution cipher that he used on the battlefield to quickly encrypt a message that could easily be decrypted by his commanders. Thomas Jefferson, the third president of the United States, was a man of many interests. Among his many inventions was an encryption system that he was believed to have used when serving as Secretary of State from 1790 to 1793.
The cipher attributed to Julius Caesar was a simple substitution cipher that he used on the battlefield to quickly encrypt a message that could easily be decrypted by his commanders. Thomas Jefferson, the third president of the United States, was a man of many interests. Among his many inventions was an encryption system that he was believed to have used when serving as Secretary of State from 1790 to 1793.
![]() Arthur Scherbius invented a machine in 1918 that served as a template for the machines that all the major participants in World War II used. He called the machine Enigma and sold it to Germany, estimating that if 1000 cryptanalysts tested 4 keys per minute, all day, every day, it would take 1.8 billion years to try them all.
Arthur Scherbius invented a machine in 1918 that served as a template for the machines that all the major participants in World War II used. He called the machine Enigma and sold it to Germany, estimating that if 1000 cryptanalysts tested 4 keys per minute, all day, every day, it would take 1.8 billion years to try them all.
![]() During World War II, the Germans and Allies had machines modeled after the Scherbius machine. These were the most sophisticated encryption devices ever developed, and in response to it, the British arguably invented the world’s first computer, the Colossus, to break the encryption that was used by the Enigma machine of Germany.
During World War II, the Germans and Allies had machines modeled after the Scherbius machine. These were the most sophisticated encryption devices ever developed, and in response to it, the British arguably invented the world’s first computer, the Colossus, to break the encryption that was used by the Enigma machine of Germany.
Ciphers
![]() A cipher is an algorithm for performing encryption and decryption; they are a series of well-defined steps that you can follow as a procedure. Substitution ciphers simply substitute one letter for another. In their simplest form, substitution ciphers retain the letter frequency of the original message.
A cipher is an algorithm for performing encryption and decryption; they are a series of well-defined steps that you can follow as a procedure. Substitution ciphers simply substitute one letter for another. In their simplest form, substitution ciphers retain the letter frequency of the original message.
![]() The cipher attributed to Julius Caesar is a simple substitution cipher. Every day has a different key, and that key is used to adjust the alphabet accordingly. For example, if today’s key is five, an A is moved five spaces, resulting in an encoded message uses F instead. A B is a G, a C is an H, and so forth. The next day the key might be eight, and the process begins again, with an A now being I, B is J, and so on.
The cipher attributed to Julius Caesar is a simple substitution cipher. Every day has a different key, and that key is used to adjust the alphabet accordingly. For example, if today’s key is five, an A is moved five spaces, resulting in an encoded message uses F instead. A B is a G, a C is an H, and so forth. The next day the key might be eight, and the process begins again, with an A now being I, B is J, and so on.
![]() For example, if a message has 25 occurrences of the letter S, and S is replaced by the letter Q, there will 25 occurrences of the letter Q. If the message is long enough, it will be vulnerable to frequency analysis because it retains the frequency patterns found in the language. Because of this weakness, polyalphabetic ciphers were invented.
For example, if a message has 25 occurrences of the letter S, and S is replaced by the letter Q, there will 25 occurrences of the letter Q. If the message is long enough, it will be vulnerable to frequency analysis because it retains the frequency patterns found in the language. Because of this weakness, polyalphabetic ciphers were invented.
Vigenère Cipher
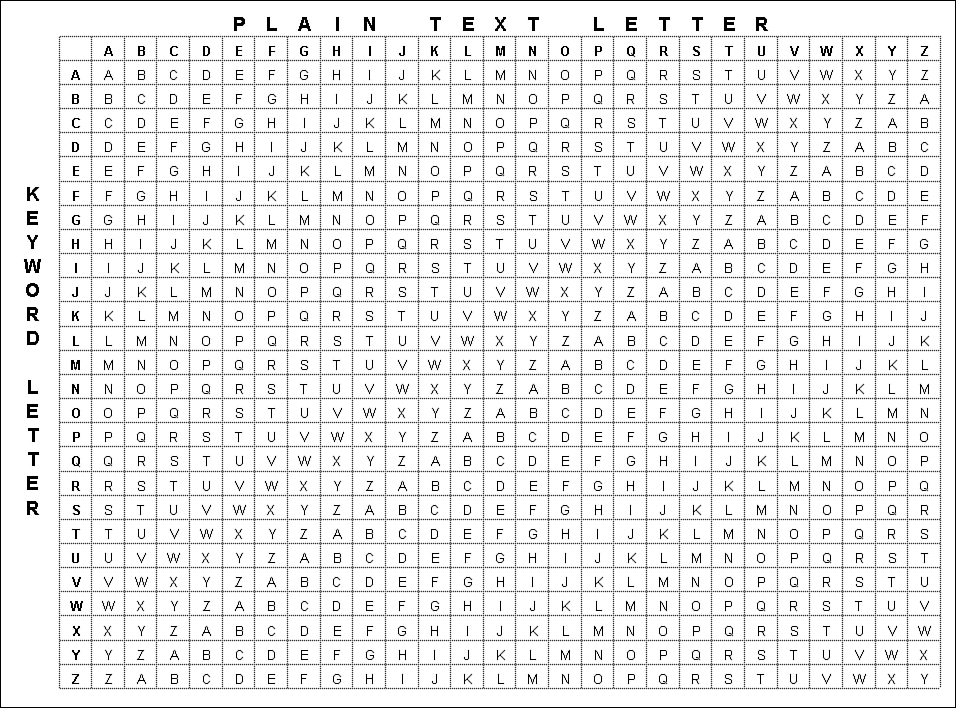
![]() The Vigenère cipher, shown in Figure 4-2, is a polyalphabetic cipher that encrypts text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution and therefore invulnerable to frequency analysis.
The Vigenère cipher, shown in Figure 4-2, is a polyalphabetic cipher that encrypts text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution and therefore invulnerable to frequency analysis.
![]() The method was originally described in 1553 in a book by Giovan Batista Belaso. Mistakenly, Blaise de Vigenère, a French cryptographer, has been attributed with its invention, hence its name.
The method was originally described in 1553 in a book by Giovan Batista Belaso. Mistakenly, Blaise de Vigenère, a French cryptographer, has been attributed with its invention, hence its name.
![]() To illustrate how it works, suppose that a key of SECRETKEY is used to encode ATTACK AT DAWN. The A is encoded by looking at the row starting with S for the letter in the A column. In this case, the A is replaced with S. Then you look for the row that begins with E for the letter T. This results in X as our second character. If you continue this encoding method, the message ATTACK AT DAWN is encrypted as SXVRGDKXBSAP.
To illustrate how it works, suppose that a key of SECRETKEY is used to encode ATTACK AT DAWN. The A is encoded by looking at the row starting with S for the letter in the A column. In this case, the A is replaced with S. Then you look for the row that begins with E for the letter T. This results in X as our second character. If you continue this encoding method, the message ATTACK AT DAWN is encrypted as SXVRGDKXBSAP.
| Note |
|
![]() In transposition ciphers, no letters are replaced, they are simply rearranged. An example of this type of cipher is taking the message THE PACKAGE IS DELIVERED and transposing it to read DEREVILEDSIEGAKCAPEHT. In this example, the key is to reverse the letters.
In transposition ciphers, no letters are replaced, they are simply rearranged. An example of this type of cipher is taking the message THE PACKAGE IS DELIVERED and transposing it to read DEREVILEDSIEGAKCAPEHT. In this example, the key is to reverse the letters.
![]() Another example of a transposition cipher is the rail fence cipher, shown in Figure 4-3. In this transposition, the words are spelled out as if they were a rail fence. The example in Figure 4-3 uses a key of three to illustrate how this could be done.
Another example of a transposition cipher is the rail fence cipher, shown in Figure 4-3. In this transposition, the words are spelled out as if they were a rail fence. The example in Figure 4-3 uses a key of three to illustrate how this could be done.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Figure 4-3: Rail Fence Cipher
![]() The message THE COVER IS BLOWN FLEE AT ONCE would be encoded as TOIOLTEHCVRSLWFEAOCEEBNEN using this method of transposition. Once again, no letters were changed; they were just rearranged.
The message THE COVER IS BLOWN FLEE AT ONCE would be encoded as TOIOLTEHCVRSLWFEAOCEEBNEN using this method of transposition. Once again, no letters were changed; they were just rearranged.
![]() The one-time pad was invented and patented by Gilbert Vernam in 1917 while working at AT&T. The primary design of the one-time pad was meant to overcome the weaknesses of using the Vigenère cipher. Vernam’s idea was a stream cipher that would apply the exclusive OR (XOR) operation to plaintext with a key, but still using the Vigenère cipher. Joseph Maubourgne, a captain in the U.S. Army Signal Corps, contributed the idea of using random data as a key. This combined idea is so significant that the National Security Agency (NSA) has called this patent “perhaps the most important in the history of cryptography.”
The one-time pad was invented and patented by Gilbert Vernam in 1917 while working at AT&T. The primary design of the one-time pad was meant to overcome the weaknesses of using the Vigenère cipher. Vernam’s idea was a stream cipher that would apply the exclusive OR (XOR) operation to plaintext with a key, but still using the Vigenère cipher. Joseph Maubourgne, a captain in the U.S. Army Signal Corps, contributed the idea of using random data as a key. This combined idea is so significant that the National Security Agency (NSA) has called this patent “perhaps the most important in the history of cryptography.”
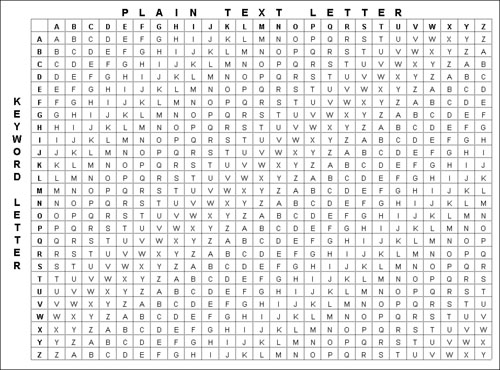
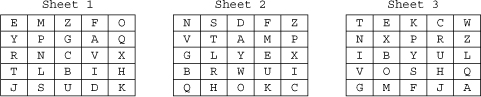
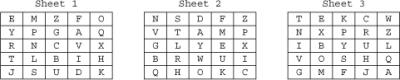
![]() Figure 4-4 shows three one-time pads used in conjunction with the Vigenère cipher.
Figure 4-4 shows three one-time pads used in conjunction with the Vigenère cipher.
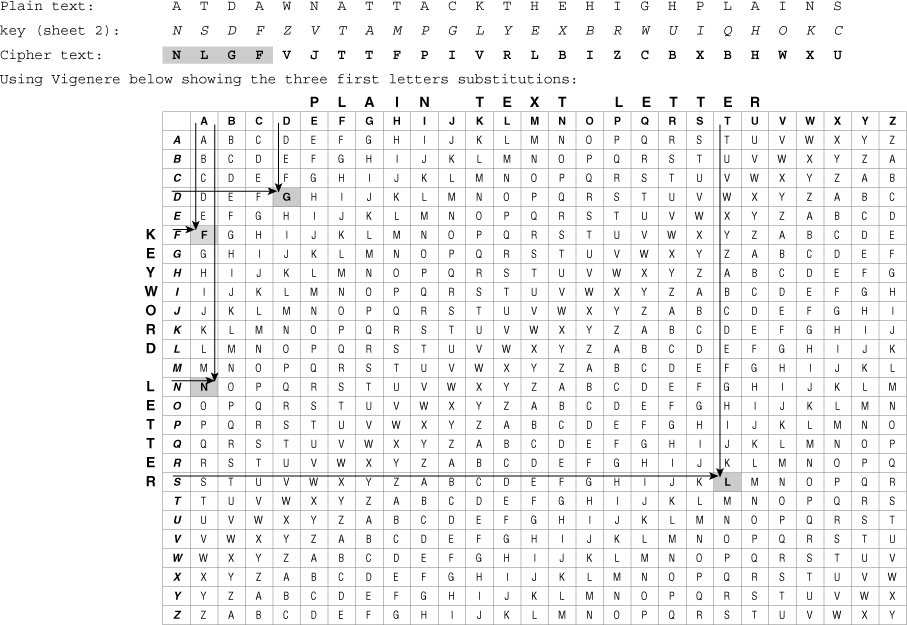
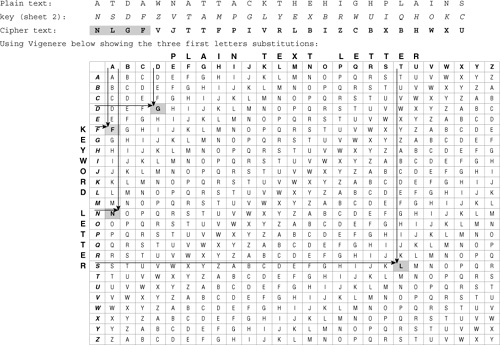
![]() In Figure 4-5, the plaintext “at dawn attack the high plains” is encrypted with Sheet 2 of the one-time pads, using the Vigenère cipher.
In Figure 4-5, the plaintext “at dawn attack the high plains” is encrypted with Sheet 2 of the one-time pads, using the Vigenère cipher.
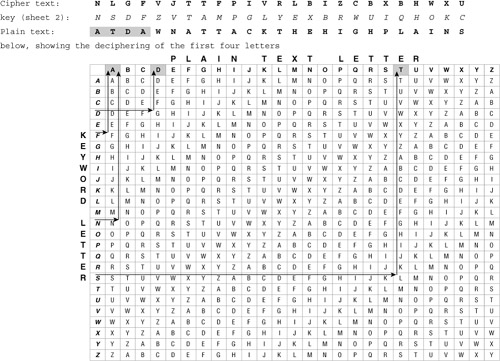
![]() In Figure 4-6, the ciphertext is unencrypted using Sheet 2 of the one-time pads.
In Figure 4-6, the ciphertext is unencrypted using Sheet 2 of the one-time pads.
![]() There are several difficulties inherent in using one-time pads in the real world. The first of these is the challenge of creating random data. Computers, because they have a mathematical foundation, are incapable of creating random data. In addition, if the key is used more than once, it is trivial to break. Key distribution is also challenging (for example, how do you distribute the pads?).
There are several difficulties inherent in using one-time pads in the real world. The first of these is the challenge of creating random data. Computers, because they have a mathematical foundation, are incapable of creating random data. In addition, if the key is used more than once, it is trivial to break. Key distribution is also challenging (for example, how do you distribute the pads?).
| Note |
|
The Process of Encryption
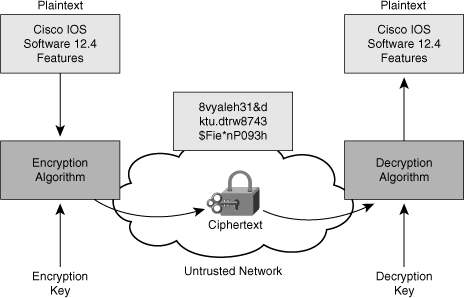
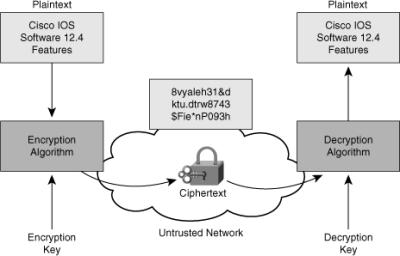
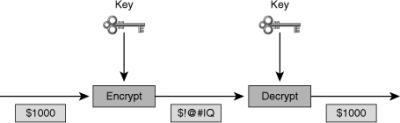
![]() Encryption is the process of disguising a message in such a way as to hide its original contents, as shown in Figure 4-7. With encryption, the plaintext readable message is converted to ciphertext, which is the unreadable, “disguised” message. Decryption reverses the process. The purpose of encryption is to guarantee confidentiality so that only authorized entities can read the original message.
Encryption is the process of disguising a message in such a way as to hide its original contents, as shown in Figure 4-7. With encryption, the plaintext readable message is converted to ciphertext, which is the unreadable, “disguised” message. Decryption reverses the process. The purpose of encryption is to guarantee confidentiality so that only authorized entities can read the original message.
![]() Old encryption algorithms, such as the Caesar cipher or the Enigma machine, were based on the secrecy of the algorithm to achieve confidentiality. With modern technology, where reverse engineering is often simple, public-domain algorithms are often used. With most modern algorithms, successful decryption requires knowledge of the appropriate cryptographic keys; that is, the security of encryption lies in the secrecy of the keys, not the algorithm.
Old encryption algorithms, such as the Caesar cipher or the Enigma machine, were based on the secrecy of the algorithm to achieve confidentiality. With modern technology, where reverse engineering is often simple, public-domain algorithms are often used. With most modern algorithms, successful decryption requires knowledge of the appropriate cryptographic keys; that is, the security of encryption lies in the secrecy of the keys, not the algorithm.
| Key Topic |
|
| Key Topic |
|
![]() Figure 4-9 illustrates an example of a simple computer version of a substitution cipher, where the word WOLFE is translated in ASCII. The key MAJOR is also translated in ASCII. The key is applied to the cleartext using in this example the logical operation XOR. The result is ciphertext. The result of applying the key using again the XOR operation is the deciphering of the cipher text to its original cleartext.
Figure 4-9 illustrates an example of a simple computer version of a substitution cipher, where the word WOLFE is translated in ASCII. The key MAJOR is also translated in ASCII. The key is applied to the cleartext using in this example the logical operation XOR. The result is ciphertext. The result of applying the key using again the XOR operation is the deciphering of the cipher text to its original cleartext.
|
| |
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Figure 4-9: Computer Version of a Substitution Cipher
![]() XOR is a type of logical disjunction on two operands that results in a value of true if only one of the operands has a value of true. In other words, for the result to be true (result of 1), the two operands must be different (one operand has to be 0 and the other operand must be 1). In mathematics, operands are the input values used on the operation. With the formula 4 * 5, 4 and 5 are operands, and * (multiplication) is the operation.
XOR is a type of logical disjunction on two operands that results in a value of true if only one of the operands has a value of true. In other words, for the result to be true (result of 1), the two operands must be different (one operand has to be 0 and the other operand must be 1). In mathematics, operands are the input values used on the operation. With the formula 4 * 5, 4 and 5 are operands, and * (multiplication) is the operation.
![]() Figure 4-9 is an example of both a substitution cipher and symmetrical encryption. Symmetrical encryption is discussed later in this chapter.
Figure 4-9 is an example of both a substitution cipher and symmetrical encryption. Symmetrical encryption is discussed later in this chapter.
![]() Encryption is usually used to provide confidentiality at an Open Systems Interconnection (OSI) layer, such as the following:
Encryption is usually used to provide confidentiality at an Open Systems Interconnection (OSI) layer, such as the following:
-
 Encrypt application layer data, such as secure email, secure database sessions (Oracle SQL*Net), and secure messaging (Lotus Notes sessions)
Encrypt application layer data, such as secure email, secure database sessions (Oracle SQL*Net), and secure messaging (Lotus Notes sessions) -
 Encrypt session layer data, using a protocol such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS)
Encrypt session layer data, using a protocol such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS) -
 Encrypt network layer data, using protocols such as those provided in the IPsec protocol suite
Encrypt network layer data, using protocols such as those provided in the IPsec protocol suite -
 Encrypt link layer data, using proprietary link-encrypting devices
Encrypt link layer data, using proprietary link-encrypting devices
Encryption Application Examples
![]() The IP Security (IPsec) protocols can provide this encryption functionality for all the packets routed over an untrusted network. The encrypting IPsec peer takes a packet with the plaintext payload, encrypts the payload into ciphertext, and forwards the packet to the untrusted network. Its IPsec partner receives the ciphertext payload packet and decrypts the payload into the original plaintext. The two IPsec peers share the same encryption and decryption algorithm and proper keys.
The IP Security (IPsec) protocols can provide this encryption functionality for all the packets routed over an untrusted network. The encrypting IPsec peer takes a packet with the plaintext payload, encrypts the payload into ciphertext, and forwards the packet to the untrusted network. Its IPsec partner receives the ciphertext payload packet and decrypts the payload into the original plaintext. The two IPsec peers share the same encryption and decryption algorithm and proper keys.
![]() The SSL protocol provides an encrypted channel on top of an existing TCP session. For example, HTTPS provides, among other services, confidentiality of the session between a web browser and a web server, using symmetric cryptography.
The SSL protocol provides an encrypted channel on top of an existing TCP session. For example, HTTPS provides, among other services, confidentiality of the session between a web browser and a web server, using symmetric cryptography.
![]() Both IPsec and SSL are used to set up a VPN. An IPsec VPN is application independent, and requires a specialized IP stack on the end system or in the packet path that includes IPsec. An SSL-based VPN supports only web-based applications, but the SSL software is included with all Internet browsers. Both SSL and IPsec are explained in more detail later in this book.
Both IPsec and SSL are used to set up a VPN. An IPsec VPN is application independent, and requires a specialized IP stack on the end system or in the packet path that includes IPsec. An SSL-based VPN supports only web-based applications, but the SSL software is included with all Internet browsers. Both SSL and IPsec are explained in more detail later in this book.
![]() In contrast to IPsec and SSL, Layer 2 encryption, also known as data-link encryption, encrypts the whole frame, including the physical address fields located in the header of the frame, and therefore can be used only on point-to-point links where no network switching or routing equipment is required for path decision.
In contrast to IPsec and SSL, Layer 2 encryption, also known as data-link encryption, encrypts the whole frame, including the physical address fields located in the header of the frame, and therefore can be used only on point-to-point links where no network switching or routing equipment is required for path decision.
| Note |
|
Cryptanalysis
![]() Cryptanalysis is the practice of breaking codes to obtain the meaning of encrypted data. An attacker who tries to break an algorithm or encrypted ciphertext might use one of the following attacks:
Cryptanalysis is the practice of breaking codes to obtain the meaning of encrypted data. An attacker who tries to break an algorithm or encrypted ciphertext might use one of the following attacks:
-
 Ciphertext-only attack
Ciphertext-only attack -
 Known-plaintext (the usual brute-force) attack
Known-plaintext (the usual brute-force) attack -
 Chosen-plaintext attack
Chosen-plaintext attack -
 Chosen-ciphertext attack
Chosen-ciphertext attack -
 Birthday attack
Birthday attack -
 Meet-in-the-middle attack
Meet-in-the-middle attack
![]() The sections that follow describe these attacks in greater detail.
The sections that follow describe these attacks in greater detail.
Brute-Force Attack
![]() In a brute-force attack, an attacker tries every possible key with the decryption algorithm, knowing that eventually one of them will work. All encryption algorithms are vulnerable to this attack. On average, a brute-force attack will succeed about 50 percent of the way through the keyspace. The objective of modern cryptographers is to have a sufficiently large keyspace so that it takes too much money and too much time to accomplish a brute-force attack.
In a brute-force attack, an attacker tries every possible key with the decryption algorithm, knowing that eventually one of them will work. All encryption algorithms are vulnerable to this attack. On average, a brute-force attack will succeed about 50 percent of the way through the keyspace. The objective of modern cryptographers is to have a sufficiently large keyspace so that it takes too much money and too much time to accomplish a brute-force attack.
| Note |
|
Ciphertext-Only Attack
![]() In a ciphertext-only attack, the attacker has the ciphertext of several messages, all of which have been encrypted using the same encryption algorithm, but the attacker has no knowledge of the underlying plaintext. The job of the attacker is to recover the ciphertext of as many messages as possible, or better yet, to deduce the key or keys used to encrypt the messages so as to decrypt other messages encrypted with the same keys. The attacker could use statistical analysis to achieve the result. Those attacks are no longer practical today because modern algorithms produce pseudorandom output that is resistant to statistical analysis.
In a ciphertext-only attack, the attacker has the ciphertext of several messages, all of which have been encrypted using the same encryption algorithm, but the attacker has no knowledge of the underlying plaintext. The job of the attacker is to recover the ciphertext of as many messages as possible, or better yet, to deduce the key or keys used to encrypt the messages so as to decrypt other messages encrypted with the same keys. The attacker could use statistical analysis to achieve the result. Those attacks are no longer practical today because modern algorithms produce pseudorandom output that is resistant to statistical analysis.
Known-Plaintext Attack
![]() In a known-plaintext attack, the attacker has access to the ciphertext of several messages, but also knows something about the plaintext underlying that ciphertext. With knowledge of the underlying protocol, file type, and some characteristic strings that might appear in the plaintext, the attacker uses a brute-force attack to try keys until decryption with the correct key produces a meaningful result. This attack may be the most practical attack, because attackers can usually assume the type and some features of the underlying plaintext, if they can only capture ciphertext. However, modern algorithms with enormous keyspaces make it unlikely for this attack to succeed, because on average an attacker would have to search through at least half of the keyspace to be successful.
In a known-plaintext attack, the attacker has access to the ciphertext of several messages, but also knows something about the plaintext underlying that ciphertext. With knowledge of the underlying protocol, file type, and some characteristic strings that might appear in the plaintext, the attacker uses a brute-force attack to try keys until decryption with the correct key produces a meaningful result. This attack may be the most practical attack, because attackers can usually assume the type and some features of the underlying plaintext, if they can only capture ciphertext. However, modern algorithms with enormous keyspaces make it unlikely for this attack to succeed, because on average an attacker would have to search through at least half of the keyspace to be successful.
| Note |
|
Chosen-Plaintext Attack
![]() In a chosen-plaintext attack, the attacker chooses what data the encryption device encrypts and observes the ciphertext output. A chosen-plaintext attack is more powerful than a known-plaintext attack because the attacker gets to choose the plaintext blocks to encrypt, allowing the attacker to choose plaintext that might yield more information about the key. This attack might not be very practical, because it is often difficult or impossible to capture both the ciphertext and plaintext, unless the trusted network has been broken into, and the attacker already has access to confidential information.
In a chosen-plaintext attack, the attacker chooses what data the encryption device encrypts and observes the ciphertext output. A chosen-plaintext attack is more powerful than a known-plaintext attack because the attacker gets to choose the plaintext blocks to encrypt, allowing the attacker to choose plaintext that might yield more information about the key. This attack might not be very practical, because it is often difficult or impossible to capture both the ciphertext and plaintext, unless the trusted network has been broken into, and the attacker already has access to confidential information.
Chosen-Ciphertext Attack
![]() In a chosen-ciphertext attack, the attacker can choose different ciphertexts to be decrypted and has access to the decrypted plaintext. With the pair, the attacker can search through the keyspace and determine which key decrypts the chosen ciphertext in the captured plaintext. For example, the attacker has access to a tamperproof encryption device with an embedded key. His job is to deduce the embedded key by sending data through the box. This attack is analogous to the chosen-plaintext attack. This attack might not be very practical, because it is often difficult or impossible to capture both the ciphertext and plaintext, unless the trusted network has been broken into, and the attacker already has access to confidential information.
In a chosen-ciphertext attack, the attacker can choose different ciphertexts to be decrypted and has access to the decrypted plaintext. With the pair, the attacker can search through the keyspace and determine which key decrypts the chosen ciphertext in the captured plaintext. For example, the attacker has access to a tamperproof encryption device with an embedded key. His job is to deduce the embedded key by sending data through the box. This attack is analogous to the chosen-plaintext attack. This attack might not be very practical, because it is often difficult or impossible to capture both the ciphertext and plaintext, unless the trusted network has been broken into, and the attacker already has access to confidential information.
Birthday Attack
![]() The birthday attack gets its name from the amazing statistical probability involved in two individuals having the same birthday. According to statisticians, the probability that 2 people in a group of 23 people share the same birthday is greater than 50 percent.
The birthday attack gets its name from the amazing statistical probability involved in two individuals having the same birthday. According to statisticians, the probability that 2 people in a group of 23 people share the same birthday is greater than 50 percent.
![]() This particular attack is a form of brute-force attack against hash functions. If some function, when supplied with a random input, returns one of k equally likely values, then by repeating the function with different inputs, the same output is expected after 1.2k1/2 number of times.
This particular attack is a form of brute-force attack against hash functions. If some function, when supplied with a random input, returns one of k equally likely values, then by repeating the function with different inputs, the same output is expected after 1.2k1/2 number of times.
| Tip |
|
Meet-in-the-Middle
![]() The meet-in-the-middle attack is a known-plaintext attack. Do not confuse this with the man-in-the-middle attack, which is discussed later. In a meet-in-the-middle attack, the attacker knows a portion of the plaintext and the corresponding ciphertext. The plaintext is encrypted with every possible key, and the results are stored. The ciphertext is then decrypted using every key until one of the results matches one of the stored values.
The meet-in-the-middle attack is a known-plaintext attack. Do not confuse this with the man-in-the-middle attack, which is discussed later. In a meet-in-the-middle attack, the attacker knows a portion of the plaintext and the corresponding ciphertext. The plaintext is encrypted with every possible key, and the results are stored. The ciphertext is then decrypted using every key until one of the results matches one of the stored values.
Encryption Algorithm Features
![]() The following are features that a good encryption algorithm provides:
The following are features that a good encryption algorithm provides:
-
 Resists cryptographic attacks
Resists cryptographic attacks -
 Supports variable and long key lengths and scalability
Supports variable and long key lengths and scalability -
 Creates an avalanche effect
Creates an avalanche effect -
 Does not have export or import restrictions
Does not have export or import restrictions
![]() A good cryptographic algorithm is designed in such a way that it resists common cryptographic attacks. The best way to break data protected by the algorithm is to try to decrypt the data using all the possible keys. The amount of time that such an attack needs depends on the number of possible keys, but is generally very, very long. With appropriately long keys, such attacks are usually considered unfeasible.
A good cryptographic algorithm is designed in such a way that it resists common cryptographic attacks. The best way to break data protected by the algorithm is to try to decrypt the data using all the possible keys. The amount of time that such an attack needs depends on the number of possible keys, but is generally very, very long. With appropriately long keys, such attacks are usually considered unfeasible.
![]() Variable-key lengths and scalability are also desirable attributes of a good encryption algorithm. The longer the encryption key, the longer it takes an attacker to break it. For example, a 16-bit key would mean that there are 65,536 possible keys, but a 56-bit key would mean there are 7.2 × 1016 possible keys. Scalability provides flexible key length and allows you to select the strength and speed of encryption that you need.
Variable-key lengths and scalability are also desirable attributes of a good encryption algorithm. The longer the encryption key, the longer it takes an attacker to break it. For example, a 16-bit key would mean that there are 65,536 possible keys, but a 56-bit key would mean there are 7.2 × 1016 possible keys. Scalability provides flexible key length and allows you to select the strength and speed of encryption that you need.
![]() When changing only a few bits of the plaintext message causes its ciphertext to change completely, this is known as an avalanche effect. The avalanche effect is a desired feature of an encryption algorithm because it allows very similar messages to be sent over an untrusted medium, with the encrypted (ciphertext) messages being completely different.
When changing only a few bits of the plaintext message causes its ciphertext to change completely, this is known as an avalanche effect. The avalanche effect is a desired feature of an encryption algorithm because it allows very similar messages to be sent over an untrusted medium, with the encrypted (ciphertext) messages being completely different.
![]() You must carefully consider export and import restrictions when you use encryption internationally. Some countries do not allow the export of encryption algorithms, or allow only the export of these algorithms with shorter keys, and some countries impose import restrictions on cryptographic algorithms.
You must carefully consider export and import restrictions when you use encryption internationally. Some countries do not allow the export of encryption algorithms, or allow only the export of these algorithms with shorter keys, and some countries impose import restrictions on cryptographic algorithms.
![]() In January 2000, the restrictions that the U.S. Department of Commerce placed on export regulations were dramatically relaxed. Currently, any cryptographic product is exportable under a license exception unless the end users are governments outside of the United States or are embargoed. Visit http://www.bis.doc.gov/encryption/default.htm for more information about the current U.S. Department of Commerce export regulations.
In January 2000, the restrictions that the U.S. Department of Commerce placed on export regulations were dramatically relaxed. Currently, any cryptographic product is exportable under a license exception unless the end users are governments outside of the United States or are embargoed. Visit http://www.bis.doc.gov/encryption/default.htm for more information about the current U.S. Department of Commerce export regulations.
 Symmetric and Asymmetric Encryption Algorithms
Symmetric and Asymmetric Encryption Algorithms
![]() An encryption algorithm, which is also called a cipher, is a mathematical function that is used to encrypt and decrypt data. Generally, there are two functions, one to encrypt and one to decrypt. If the security of an encryption system is based on the secrecy of the algorithm itself, the algorithm code must be heavily guarded. If the algorithm is revealed, every party that is involved must change the algorithm.
An encryption algorithm, which is also called a cipher, is a mathematical function that is used to encrypt and decrypt data. Generally, there are two functions, one to encrypt and one to decrypt. If the security of an encryption system is based on the secrecy of the algorithm itself, the algorithm code must be heavily guarded. If the algorithm is revealed, every party that is involved must change the algorithm.
![]() Modern cryptography takes a different approach: All algorithms are public, and cryptographic keys are used to ensure the secrecy of data. Cryptographic keys are sequences of bits that are input into an encryption algorithm together with the data to be encrypted. There are two classes of encryption algorithms, which differ in their use of keys:
Modern cryptography takes a different approach: All algorithms are public, and cryptographic keys are used to ensure the secrecy of data. Cryptographic keys are sequences of bits that are input into an encryption algorithm together with the data to be encrypted. There are two classes of encryption algorithms, which differ in their use of keys:
-
 Symmetric encryption algorithms: These use the same key to encrypt and decrypt data.
Symmetric encryption algorithms: These use the same key to encrypt and decrypt data. -
 Asymmetric encryption algorithms: These use different keys to encrypt and decrypt data.
Asymmetric encryption algorithms: These use different keys to encrypt and decrypt data.
| Key Topic |
|
Symmetric Encryption Algorithms
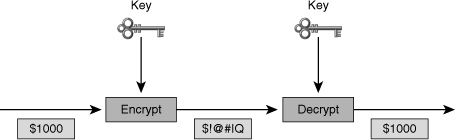
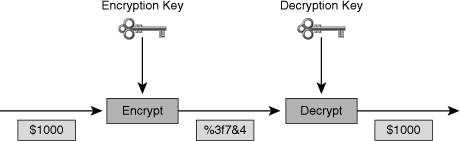
![]() Symmetric encryption algorithms are algorithms in which the encryption and decryption keys are the same, as shown in Figure 4-10. Therefore, the sender and the receiver must share the same secret key before communicating securely. The security of a symmetric algorithm rests in the secrecy of the symmetric key; by obtaining the key, anyone can encrypt and decrypt messages. Symmetric encryption is often called secret-key encryption. Symmetric, or secret-key, encryption is the more traditional form of cryptography. The typical key length range of symmetric encryption algorithms is 40 to 256 bits.
Symmetric encryption algorithms are algorithms in which the encryption and decryption keys are the same, as shown in Figure 4-10. Therefore, the sender and the receiver must share the same secret key before communicating securely. The security of a symmetric algorithm rests in the secrecy of the symmetric key; by obtaining the key, anyone can encrypt and decrypt messages. Symmetric encryption is often called secret-key encryption. Symmetric, or secret-key, encryption is the more traditional form of cryptography. The typical key length range of symmetric encryption algorithms is 40 to 256 bits.
![]() The following are well-known encryption algorithms that use symmetric keys:
The following are well-known encryption algorithms that use symmetric keys:
-
 DES: 56-bit keys
DES: 56-bit keys -
 Triple Data Encryption Standard (3DES): 112- and 168-bit keys
Triple Data Encryption Standard (3DES): 112- and 168-bit keys -
 AES: 128-, 192-, and 256-bit keys
AES: 128-, 192-, and 256-bit keys -
 International Data Encryption Algorithm (IDEA): 128-bit keys
International Data Encryption Algorithm (IDEA): 128-bit keys -
 The RC series (RC2, RC4, RC5, and RC6):
The RC series (RC2, RC4, RC5, and RC6): -
 Blowfish: 32- to 448-bit keys
Blowfish: 32- to 448-bit keys
![]() The most commonly used techniques in symmetric encryption cryptography are block ciphers, stream ciphers, and message authentication codes (MAC).
The most commonly used techniques in symmetric encryption cryptography are block ciphers, stream ciphers, and message authentication codes (MAC).
![]() Because symmetric algorithms are usually quite fast, they are often used for wire-speed encryption in data networks. Symmetric algorithms are based on simple mathematical operations and can easily be accelerated by hardware. Because of their speed, you can use symmetric algorithms for bulk encryption when data privacy is required (for example, to protect a VPN).
Because symmetric algorithms are usually quite fast, they are often used for wire-speed encryption in data networks. Symmetric algorithms are based on simple mathematical operations and can easily be accelerated by hardware. Because of their speed, you can use symmetric algorithms for bulk encryption when data privacy is required (for example, to protect a VPN).
![]() On the other hand, key management can be a challenge. The communicating parties must exchange the symmetric, secret key using a secure channel before any encryption can occur. Therefore, the security of any cryptographic system depends greatly on the security of the key exchange method.
On the other hand, key management can be a challenge. The communicating parties must exchange the symmetric, secret key using a secure channel before any encryption can occur. Therefore, the security of any cryptographic system depends greatly on the security of the key exchange method.
![]() Because of their speed, symmetric algorithms are frequently used for encryption services, with additional key management algorithms providing secure key exchange.
Because of their speed, symmetric algorithms are frequently used for encryption services, with additional key management algorithms providing secure key exchange.
Asymmetric Encryption Algorithms
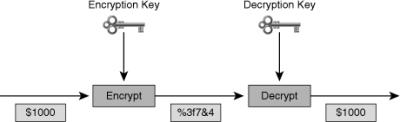
![]() Asymmetric algorithms, also sometimes called public-key algorithms, are designed in such a way that the key used for encryption differs from the key used for decryption, as shown in Figure 4-11.
Asymmetric algorithms, also sometimes called public-key algorithms, are designed in such a way that the key used for encryption differs from the key used for decryption, as shown in Figure 4-11.
![]() The decryption key cannot, in any reasonable amount of time, be calculated from the encryption key and vice versa. The typical key length range for asymmetric algorithms is 512 to 4096 bits. You cannot directly compare the key length of asymmetric and symmetric algorithms because the underlying design of the two algorithm families differs greatly.
The decryption key cannot, in any reasonable amount of time, be calculated from the encryption key and vice versa. The typical key length range for asymmetric algorithms is 512 to 4096 bits. You cannot directly compare the key length of asymmetric and symmetric algorithms because the underlying design of the two algorithm families differs greatly.
| Note |
|
![]() The best-known asymmetric cryptographic algorithms are RSA, ElGamal, and elliptic curve algorithms.
The best-known asymmetric cryptographic algorithms are RSA, ElGamal, and elliptic curve algorithms.
| Note |
|
![]() Asymmetric algorithms can be up to 1000 times slower than symmetric algorithms. Their design is based on computational problems, such as factoring extremely large numbers or computing discrete logarithms of extremely large numbers. Because they lack speed, asymmetric algorithms are typically used in low-volume cryptographic mechanisms, such as digital signatures and key exchange. However, the key management of asymmetric algorithms tends to be simpler than that of symmetric algorithms, because usually one of the two encryption or decryption keys can be made public.
Asymmetric algorithms can be up to 1000 times slower than symmetric algorithms. Their design is based on computational problems, such as factoring extremely large numbers or computing discrete logarithms of extremely large numbers. Because they lack speed, asymmetric algorithms are typically used in low-volume cryptographic mechanisms, such as digital signatures and key exchange. However, the key management of asymmetric algorithms tends to be simpler than that of symmetric algorithms, because usually one of the two encryption or decryption keys can be made public.
| Key Topic |
|
 Block and Stream Ciphers
Block and Stream Ciphers
![]() Algorithms can operate in two modes:
Algorithms can operate in two modes:
-
 Block mode: The algorithm can work on only fixed chunks of data.
Block mode: The algorithm can work on only fixed chunks of data. -
 Stream mode: The algorithm can process data bit by bit.
Stream mode: The algorithm can process data bit by bit.
Block Ciphers
![]() Block ciphers transform a fixed-length block of plaintext into a block of ciphertext of the same length. Applying the reverse transformation to the ciphertext block, using the same secret key, results in decryption. Currently, the fixed length, also known as the block size, for many block ciphers is typically 128 bits. DES has a block size of 64 bits.
Block ciphers transform a fixed-length block of plaintext into a block of ciphertext of the same length. Applying the reverse transformation to the ciphertext block, using the same secret key, results in decryption. Currently, the fixed length, also known as the block size, for many block ciphers is typically 128 bits. DES has a block size of 64 bits.
| Note |
|
![]() Block ciphers usually result in output data that is larger than the input data because the ciphertext must be a multiple of the block size. To accomplish this, block algorithms take data one chunk at a time (for example, 8 bytes) and use padding to add artificial data (blanks) if there is less input data than one full block.
Block ciphers usually result in output data that is larger than the input data because the ciphertext must be a multiple of the block size. To accomplish this, block algorithms take data one chunk at a time (for example, 8 bytes) and use padding to add artificial data (blanks) if there is less input data than one full block.
![]() The following are common block ciphers:
The following are common block ciphers:
-
 DES and 3DES, running in Electronic Code Book (ECB) and Cipher Block Chaining (CBC) mode
DES and 3DES, running in Electronic Code Book (ECB) and Cipher Block Chaining (CBC) mode -
 AES
AES -
 IDEA
IDEA -
 Secure and Fast Encryption Routine (SAFER)
Secure and Fast Encryption Routine (SAFER) -
 Skipjack
Skipjack -
 Blowfish
Blowfish -
 RSA
RSA
Stream Ciphers
![]() Unlike block ciphers, stream ciphers operate on smaller units of plaintext, typically bits. With a stream cipher, the transformation of these smaller plaintext units varies, depending on when they are encountered during the encryption process. Stream ciphers can be much faster than block ciphers, and generally do not increase the message size, because they can encrypt an arbitrary number of bits.
Unlike block ciphers, stream ciphers operate on smaller units of plaintext, typically bits. With a stream cipher, the transformation of these smaller plaintext units varies, depending on when they are encountered during the encryption process. Stream ciphers can be much faster than block ciphers, and generally do not increase the message size, because they can encrypt an arbitrary number of bits.
![]() Common stream ciphers include the following:
Common stream ciphers include the following:
-
 DES and 3DES, running in output feedback (OFB) or cipher feedback (CFB) mode
DES and 3DES, running in output feedback (OFB) or cipher feedback (CFB) mode -
 RC4
RC4 -
 Software Encryption Algorithm (SEAL)
Software Encryption Algorithm (SEAL)
| Key Topic |
|
 Encryption Algorithm Selection
Encryption Algorithm Selection
![]() Choosing an encryption algorithm is one of the most important steps of building a cryptography-based solution. You should consider two main criteria when selecting an encryption algorithm for your organization:
Choosing an encryption algorithm is one of the most important steps of building a cryptography-based solution. You should consider two main criteria when selecting an encryption algorithm for your organization:
-
 Trust in the algorithm by the cryptographic community: Most new algorithms are broken quickly, so algorithms that have been resisting attacks for a number of years are preferred. Inventors and promoters often oversell the benefits of new algorithms. The truth is that there are few or no revolutions in cryptography.
Trust in the algorithm by the cryptographic community: Most new algorithms are broken quickly, so algorithms that have been resisting attacks for a number of years are preferred. Inventors and promoters often oversell the benefits of new algorithms. The truth is that there are few or no revolutions in cryptography. -
 Protection against brute-force attacks: If the algorithm is considered trusted, there is no shortcut to break it, and the attacker must search through the keyspace to guess the correct key. The algorithm must allow key lengths that satisfy the confidentiality requirements of an organization. For example, although DES is considered trustworthy, its key is shorter than 3DES or AES, and therefore could be easier to break than its more recent successors.
Protection against brute-force attacks: If the algorithm is considered trusted, there is no shortcut to break it, and the attacker must search through the keyspace to guess the correct key. The algorithm must allow key lengths that satisfy the confidentiality requirements of an organization. For example, although DES is considered trustworthy, its key is shorter than 3DES or AES, and therefore could be easier to break than its more recent successors.
![]() The following symmetric encryption algorithms are considered trustworthy:
The following symmetric encryption algorithms are considered trustworthy:
-
 DES
DES -
 3DES
3DES -
 IDEA
IDEA -
 RC4
RC4 -
 AES
AES
![]() Because of its short key length, DES is considered a good protocol to protect data for a short time. 3DES is a better choice when you want to protect data with an algorithm that is very trusted and has higher security strength.
Because of its short key length, DES is considered a good protocol to protect data for a short time. 3DES is a better choice when you want to protect data with an algorithm that is very trusted and has higher security strength.
![]() AES is a valid choice, being regarded as a good algorithm, although it is not proven to the degree that 3DES is. Because AES is more efficient, you can use AES in high-throughput, low-latency environments, especially when 3DES cannot handle the throughput or latency requirements. In time, AES is expected to gain more and more trust, when more time has passed and more attacks have been attempted against it.
AES is a valid choice, being regarded as a good algorithm, although it is not proven to the degree that 3DES is. Because AES is more efficient, you can use AES in high-throughput, low-latency environments, especially when 3DES cannot handle the throughput or latency requirements. In time, AES is expected to gain more and more trust, when more time has passed and more attacks have been attempted against it.
![]() RSA and Diffie-Hellman (DH) are considered trustworthy for confidentiality.
RSA and Diffie-Hellman (DH) are considered trustworthy for confidentiality.
![]() Other algorithms, such as elliptical curve cryptography (ECC), are generally considered immature in cryptographic terms.
Other algorithms, such as elliptical curve cryptography (ECC), are generally considered immature in cryptographic terms.
![]() For symmetric algorithms, each bit in a key doubles the difficulty of finding the key. But with asymmetric algorithms, such as RSA, each additional bit only nominally increases the difficulty of factoring the composite number that is used by the algorithm. Therefore, symmetrical and asymmetrical keys compare as follow:
For symmetric algorithms, each bit in a key doubles the difficulty of finding the key. But with asymmetric algorithms, such as RSA, each additional bit only nominally increases the difficulty of factoring the composite number that is used by the algorithm. Therefore, symmetrical and asymmetrical keys compare as follow:
-
 An 80-bit symmetric key is considered equal to a 1024-bit key using the RSA algorithm.
An 80-bit symmetric key is considered equal to a 1024-bit key using the RSA algorithm. -
 A 112-bit symmetric key is considered equal to a 2048-bit key using the RSA algorithm.
A 112-bit symmetric key is considered equal to a 2048-bit key using the RSA algorithm. -
 A 128-bit symmetric key is considered equal to a 3072-bit key using the RSA algorithm.
A 128-bit symmetric key is considered equal to a 3072-bit key using the RSA algorithm.
![]() For more information about the comparison of the key strengths of symmetric algorithms to RSA, refer to http://www.rsasecurity.com/rsalabs/node.asp?id=2004.
For more information about the comparison of the key strengths of symmetric algorithms to RSA, refer to http://www.rsasecurity.com/rsalabs/node.asp?id=2004.
 Cryptographic Hashes
Cryptographic Hashes
![]() Hashing is a mechanism used for data integrity assurance. Hashing is based on a one-way mathematical function. Functions hash (digest) data into a fixed-length digest (fingerprint). Hashes are functions that are relatively easy to compute, but significantly harder to reverse. Grinding coffee is a good example of a one-way function: It is easy to grind coffee beans, but it is almost impossible to put all the tiny pieces back together to rebuild the original beans.
Hashing is a mechanism used for data integrity assurance. Hashing is based on a one-way mathematical function. Functions hash (digest) data into a fixed-length digest (fingerprint). Hashes are functions that are relatively easy to compute, but significantly harder to reverse. Grinding coffee is a good example of a one-way function: It is easy to grind coffee beans, but it is almost impossible to put all the tiny pieces back together to rebuild the original beans.
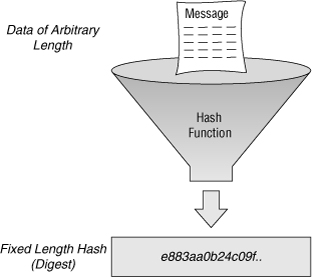
![]() Figure 4-12 illustrates how hashing is performed. Data of arbitrary length is input into the hash function, and the result of the hash function is the fixed-length hash, known as either the digest or fingerprint. Hashing is similar to the calculation of cyclic redundancy check (CRC) checksums, but it is much stronger cryptographically. That is, given a CRC value, it is easy to generate data with the same CRC. However, with hash functions, it is computationally infeasible for an attacker to have two different sets of data that would come up with the same fingerprint.
Figure 4-12 illustrates how hashing is performed. Data of arbitrary length is input into the hash function, and the result of the hash function is the fixed-length hash, known as either the digest or fingerprint. Hashing is similar to the calculation of cyclic redundancy check (CRC) checksums, but it is much stronger cryptographically. That is, given a CRC value, it is easy to generate data with the same CRC. However, with hash functions, it is computationally infeasible for an attacker to have two different sets of data that would come up with the same fingerprint.
| Key Topic |
|
| Note |
|
 Key Management
Key Management
![]() Key management is often considered the most difficult part of designing a cryptosystem. Many cryptosystems have failed because of mistakes in their key management, and all modern cryptographic algorithms require the services of key management procedures. In practice, most attacks on cryptographic systems will be aimed at the key management level, rather than at the cryptographic algorithm itself.
Key management is often considered the most difficult part of designing a cryptosystem. Many cryptosystems have failed because of mistakes in their key management, and all modern cryptographic algorithms require the services of key management procedures. In practice, most attacks on cryptographic systems will be aimed at the key management level, rather than at the cryptographic algorithm itself.
Key Management Components
![]() Key management consists of the following components:
Key management consists of the following components:
-
 Key generation: In a modern cryptographic system, key generation is usually automated and not left to the end user. The use of good random number generators is needed to ensure that all keys are likely to be equally generated so that the attacker cannot predict which keys are more likely to be used.
Key generation: In a modern cryptographic system, key generation is usually automated and not left to the end user. The use of good random number generators is needed to ensure that all keys are likely to be equally generated so that the attacker cannot predict which keys are more likely to be used. -
 Key verification: Almost all cryptographic algorithms have some weak keys that should not be used, and with the help of key verification procedures, you can regenerate these keys if they occur.
Key verification: Almost all cryptographic algorithms have some weak keys that should not be used, and with the help of key verification procedures, you can regenerate these keys if they occur. -
 Key storage: On a modern multiuser operating system that uses cryptography, a key can be stored in memory. This presents a possible problem when that memory is swapped to the disk, because a Trojan horse program, installed on the PC of a user, could then have access to the private keys of that user. A possible solution is to store the key on a USB stick and require a password to unlock that key.
Key storage: On a modern multiuser operating system that uses cryptography, a key can be stored in memory. This presents a possible problem when that memory is swapped to the disk, because a Trojan horse program, installed on the PC of a user, could then have access to the private keys of that user. A possible solution is to store the key on a USB stick and require a password to unlock that key. -
 Key exchange: The key management procedures should also provide a secure key exchange mechanism, which allows secure agreement on the keying material with the other party, probably over an untrusted medium.
Key exchange: The key management procedures should also provide a secure key exchange mechanism, which allows secure agreement on the keying material with the other party, probably over an untrusted medium. -
 Key revocation and destruction: Key revocation notifies all the interested parties that a certain key has been compromised and should no longer be used. Key destruction erases old keys in such a manner that malicious attackers cannot recover them.
Key revocation and destruction: Key revocation notifies all the interested parties that a certain key has been compromised and should no longer be used. Key destruction erases old keys in such a manner that malicious attackers cannot recover them.
| Key Topic |
|
Keyspaces
![]() The keyspace of an algorithm is the set of all possible key values. A key that has n bits produces a keyspace that has 2n possible key values. By adding one bit to the key, you effectively double the keyspace. For example, DES with its 56-bit keys has a keyspace of more than 72,000,000,000,000,000 (256) possible keys, but by adding 1 bit to the key length, the keyspace doubles, and an attacker needs twice the amount of time to search the keyspace.
The keyspace of an algorithm is the set of all possible key values. A key that has n bits produces a keyspace that has 2n possible key values. By adding one bit to the key, you effectively double the keyspace. For example, DES with its 56-bit keys has a keyspace of more than 72,000,000,000,000,000 (256) possible keys, but by adding 1 bit to the key length, the keyspace doubles, and an attacker needs twice the amount of time to search the keyspace.
![]() As previously mentioned, almost every algorithm has some weak keys in its keyspace that enable an attacker to break the encryption via a shortcut. Weak keys show regularities in encryption or poor encryption. For instance, DES has four keys for which encryption is the same as decryption. This means that if one of these weak keys is encrypted twice, the original plaintext is recovered.
As previously mentioned, almost every algorithm has some weak keys in its keyspace that enable an attacker to break the encryption via a shortcut. Weak keys show regularities in encryption or poor encryption. For instance, DES has four keys for which encryption is the same as decryption. This means that if one of these weak keys is encrypted twice, the original plaintext is recovered.
![]() The weak keys of DES are those that produce 16 identical subkeys. This occurs when the key bits are
The weak keys of DES are those that produce 16 identical subkeys. This occurs when the key bits are
-
 Alternating 1s + 0s (0101010101010101)
Alternating 1s + 0s (0101010101010101) -
 E0E0E0E0F1F1F1F1
E0E0E0E0F1F1F1F1 -
 1F1F1F1F0E0E0E0E
1F1F1F1F0E0E0E0E
![]() It is unlikely that such keys would be chosen, but implementations should still verify all keys and prevent weak keys from being used. With manual key generation, you must take special care to avoid defining weak keys.
It is unlikely that such keys would be chosen, but implementations should still verify all keys and prevent weak keys from being used. With manual key generation, you must take special care to avoid defining weak keys.
Key Length Issues
![]() If the cryptographic system is trustworthy, the only way to break it is with a brute-force attack. A brute-force attack is a search through the entire keyspace, trying all the possible keys, to find a key that decrypts the data. If the keyspace is large enough, the search should require an enormous amount of time, making such an exhaustive effort unfeasible. On average, an attacker has to search through half of the keyspace before the correct key is found. The time that is needed to accomplish this search depends on the computer power available to the attacker. However, current key lengths can easily make any attempt insignificant, because it would take many millions or billions of years to complete the search when a sufficiently long key is used.
If the cryptographic system is trustworthy, the only way to break it is with a brute-force attack. A brute-force attack is a search through the entire keyspace, trying all the possible keys, to find a key that decrypts the data. If the keyspace is large enough, the search should require an enormous amount of time, making such an exhaustive effort unfeasible. On average, an attacker has to search through half of the keyspace before the correct key is found. The time that is needed to accomplish this search depends on the computer power available to the attacker. However, current key lengths can easily make any attempt insignificant, because it would take many millions or billions of years to complete the search when a sufficiently long key is used.
![]() With modern algorithms that are trusted, the strength of protection depends solely on the length of the key. Choose the key length so that it protects data confidentiality or integrity for an adequate period of time. Data that is more sensitive and needs to be kept secret longer must use longer keys.
With modern algorithms that are trusted, the strength of protection depends solely on the length of the key. Choose the key length so that it protects data confidentiality or integrity for an adequate period of time. Data that is more sensitive and needs to be kept secret longer must use longer keys.
![]() The funding of the attacker should also affect your choice of key length. When you assess the risk of someone breaking the encryption algorithm, you must estimate the resources of the attacker and how long you must protect the data. For example, if the attacker has $1 million of funding, and the data must be protected for one year, classic DES is not a good choice because it can be broken by a $1 million machine in a couple of minutes. However, it would take an attacker some million years or more to crack 168-bit 3DES or 128-bit RC4, which makes either of these key length choices more than adequate.
The funding of the attacker should also affect your choice of key length. When you assess the risk of someone breaking the encryption algorithm, you must estimate the resources of the attacker and how long you must protect the data. For example, if the attacker has $1 million of funding, and the data must be protected for one year, classic DES is not a good choice because it can be broken by a $1 million machine in a couple of minutes. However, it would take an attacker some million years or more to crack 168-bit 3DES or 128-bit RC4, which makes either of these key length choices more than adequate.
![]() Performance is another issue that can influence the choice of key length. You must find a good balance between the speed and protection strength of an algorithm, because some algorithms, such as RSA, run slower with larger key sizes. Strive for adequate protection, while enabling unhindered communication over untrusted networks.
Performance is another issue that can influence the choice of key length. You must find a good balance between the speed and protection strength of an algorithm, because some algorithms, such as RSA, run slower with larger key sizes. Strive for adequate protection, while enabling unhindered communication over untrusted networks.
![]() Because of the rapid advances in technology and cryptanalytic methods, the key size needed for a particular application is constantly increasing. Go to the National Institute of Standards and Technology (NIST) website at http://www.keylength.com/en/4/ to see updated key length recommendations.
Because of the rapid advances in technology and cryptanalytic methods, the key size needed for a particular application is constantly increasing. Go to the National Institute of Standards and Technology (NIST) website at http://www.keylength.com/en/4/ to see updated key length recommendations.
Example of the Impact of Key Length
![]() Part of the strength of the RSA algorithm is the difficulty of factoring large numbers. If a 1024-bit number is hard to factor, then a 2048-bit number is going to be even harder to factor. Even with the fastest computers available today, it would take many lifetimes to factor a 1024-bit number that is a factor of two 512-bit prime numbers. Of course, this advantage is lost if an easy way to factor large numbers is found. However, cryptographers consider this possibility unlikely, and the rule “the longer the key, the better” is valid, except for possible performance reasons.
Part of the strength of the RSA algorithm is the difficulty of factoring large numbers. If a 1024-bit number is hard to factor, then a 2048-bit number is going to be even harder to factor. Even with the fastest computers available today, it would take many lifetimes to factor a 1024-bit number that is a factor of two 512-bit prime numbers. Of course, this advantage is lost if an easy way to factor large numbers is found. However, cryptographers consider this possibility unlikely, and the rule “the longer the key, the better” is valid, except for possible performance reasons.
![]() As of 2005, the best known attack on 3DES required around 232 known plaintexts, 2113 steps, 290 single DES encryptions, and 288 memory operations. This is not currently practical. If the attacker seeks to discover any one of many cryptographic keys, there is a memory-efficient attack that will discover one of 228 keys, given a handful of chosen plaintexts per key and around 284 encryption operations. This attack is highly parallelizable and verges on the practical, given billion-dollar budgets and years to mount the attack, although the circumstances in which it would be useful are limited.
As of 2005, the best known attack on 3DES required around 232 known plaintexts, 2113 steps, 290 single DES encryptions, and 288 memory operations. This is not currently practical. If the attacker seeks to discover any one of many cryptographic keys, there is a memory-efficient attack that will discover one of 228 keys, given a handful of chosen plaintexts per key and around 284 encryption operations. This attack is highly parallelizable and verges on the practical, given billion-dollar budgets and years to mount the attack, although the circumstances in which it would be useful are limited.
 Introducing SSL VPNs
Introducing SSL VPNs
![]() Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide secure communications on the Internet for such things as web browsing, email, Internet faxing, instant messaging, and other data transfers. SSL and TLS have some slight differences, but the protocol remains largely the same. Originally developed by Netscape, SSL has been universally accepted on the World Wide Web.
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide secure communications on the Internet for such things as web browsing, email, Internet faxing, instant messaging, and other data transfers. SSL and TLS have some slight differences, but the protocol remains largely the same. Originally developed by Netscape, SSL has been universally accepted on the World Wide Web.
![]() The SSL and TLS protocols support the use of a variety of different cryptographic algorithms, or ciphers, for use in operations such as authentication between the server and client, transmitting certificates, and establishing session keys. Symmetric algorithms are used for bulk encryption, asymmetric algorithms are used for authentication and the exchange of keys, and hashing is used as part of the authentication process.
The SSL and TLS protocols support the use of a variety of different cryptographic algorithms, or ciphers, for use in operations such as authentication between the server and client, transmitting certificates, and establishing session keys. Symmetric algorithms are used for bulk encryption, asymmetric algorithms are used for authentication and the exchange of keys, and hashing is used as part of the authentication process.
| Note |
|
![]() SSL-based VPNs provide remote-access connectivity from almost any Internet-enabled location using a standard web browser and its native SSL encryption. They do not require any special-purpose client software to be preinstalled on the system. Therefore, SSL-based VPNs are capable of “anywhere” connectivity from company-managed desktops and non-company-managed desktops, such as employee-owned PCs, contractor or business partner desktops, and Internet kiosks. All the software required for application access across the SSL VPN connection is dynamically downloaded as needed, minimizing the maintenance of desktop software.
SSL-based VPNs provide remote-access connectivity from almost any Internet-enabled location using a standard web browser and its native SSL encryption. They do not require any special-purpose client software to be preinstalled on the system. Therefore, SSL-based VPNs are capable of “anywhere” connectivity from company-managed desktops and non-company-managed desktops, such as employee-owned PCs, contractor or business partner desktops, and Internet kiosks. All the software required for application access across the SSL VPN connection is dynamically downloaded as needed, minimizing the maintenance of desktop software.
![]() SSL VPNs and IPsec VPNs are complementary technologies that you can deploy together to better address the unique access requirements of diverse user communities. Both offer access to virtually any network application or resource. SSL VPNs offer additional features such as easy connectivity from desktops outside your company’s management, little or no desktop software maintenance, and user-customized web portals upon login.
SSL VPNs and IPsec VPNs are complementary technologies that you can deploy together to better address the unique access requirements of diverse user communities. Both offer access to virtually any network application or resource. SSL VPNs offer additional features such as easy connectivity from desktops outside your company’s management, little or no desktop software maintenance, and user-customized web portals upon login.
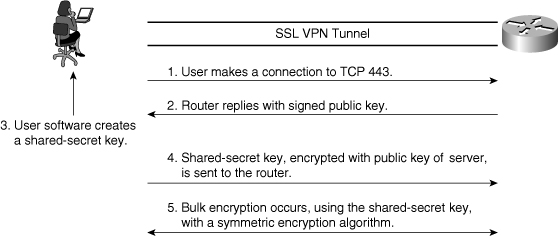
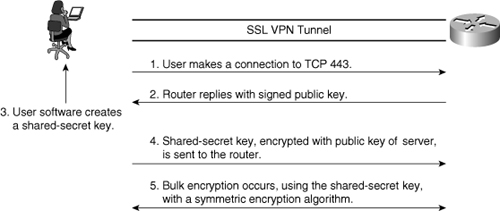
![]() Figure 4-13 gives a simplified explanation of the key steps in establishing an SSL session:
Figure 4-13 gives a simplified explanation of the key steps in establishing an SSL session:
| Note |
|

7 comments
electronic signatures
Excellent guide. This article is well written and a complete guide to learn all about cryptography technique. I am highly impressed with this detail and would like to appreciate you for the efforts that you have used in writing it.
well done,
i must say encryption means a lot in day to day life to keep our communication safe and secure. There is an app "The EnKryptonite application" and it transform your daily life into a secured one. It protects you wherever and whenever you communicate. Download from:
App store & Google Play
Thank you sharing the information keep updating Data Science online Course
Enjoyed reading the article above, really explains everything in detail, the article is very interesting and effective. Thank you and good luck for the upcoming articles.
Digital Marketing Training in Chennai
Digital Marketing Course in Chennai
Great Blog I Have Read Your Blog It Is Very Useful For Me Thank you for posting and sharing such great information.can you help me in finding out more detail on Fundamentals of Cryptography.
This post is so helpfull and informative.Keep updating with more information...
Scope Of Cyber Security
Careers In Cyber Security
we specialize in creating dynamic, responsive, and user-friendly WordPress websites with our custom WordPress Development Services
Post a Comment