Configuring AAA on a Cisco Router to Use Cisco Secure ACS
![]() Cisco Secure Access Control Server (ACS) for Windows provides a centralized identity networking solution and simplified user management experience across all Cisco devices and security management applications. This section covers what Cisco Secure ACS is and what you can use it for, the requirements for installing Cisco Secure ACS for Windows, and the Cisco Secure ACS installation procedure.
Cisco Secure Access Control Server (ACS) for Windows provides a centralized identity networking solution and simplified user management experience across all Cisco devices and security management applications. This section covers what Cisco Secure ACS is and what you can use it for, the requirements for installing Cisco Secure ACS for Windows, and the Cisco Secure ACS installation procedure.
 Cisco Secure ACS Overview
Cisco Secure ACS Overview
![]() Local implementations of AAA, explained in the previous section of this book, do not scale well. Most corporate environments have multiple Cisco routers and network access servers (NAS) with multiple router administrators and hundreds or thousands of users needing access to the corporate LAN. Maintaining local databases for each Cisco router and NAS for this size of network is not feasible.
Local implementations of AAA, explained in the previous section of this book, do not scale well. Most corporate environments have multiple Cisco routers and network access servers (NAS) with multiple router administrators and hundreds or thousands of users needing access to the corporate LAN. Maintaining local databases for each Cisco router and NAS for this size of network is not feasible.
![]() To solve this challenge, you can use one or more Cisco Secure ACS systems (servers or engines) to manage the entire user and administrative access needs for an entire corporate network using one or more databases. External AAA systems, such as the Cisco Secure ACS for Windows or Cisco Secure ACS Solution Engine, communicate with Cisco routers and NASs using the TACACS+ or RADIUS protocols to implement AAA functions. This allows you to make changes to user accounts and passwords in a centralized place (the ACS server), and have all the Cisco routers and NASs in your network access this information.
To solve this challenge, you can use one or more Cisco Secure ACS systems (servers or engines) to manage the entire user and administrative access needs for an entire corporate network using one or more databases. External AAA systems, such as the Cisco Secure ACS for Windows or Cisco Secure ACS Solution Engine, communicate with Cisco routers and NASs using the TACACS+ or RADIUS protocols to implement AAA functions. This allows you to make changes to user accounts and passwords in a centralized place (the ACS server), and have all the Cisco routers and NASs in your network access this information.
![]() Figure 2-14 shows the steps of the authentication and authorization process using an external Cisco Secure ACS system to provide AAA services to a network:
Figure 2-14 shows the steps of the authentication and authorization process using an external Cisco Secure ACS system to provide AAA services to a network:
|
|
|
|
|
|
|
|
|
|
|
|
![]() Cisco Secure ACS is a highly scalable, high-performance ACS that operates as a centralized RADIUS and TACACS+ server that provides the following features:
Cisco Secure ACS is a highly scalable, high-performance ACS that operates as a centralized RADIUS and TACACS+ server that provides the following features:
-
 Extends access security by combining authentication, user access, and administrator access with policy control within a centralized identity networking solution
Extends access security by combining authentication, user access, and administrator access with policy control within a centralized identity networking solution -
 Allows greater flexibility and mobility, increased security, and user-productivity gains
Allows greater flexibility and mobility, increased security, and user-productivity gains -
 Enforces a uniform security policy for all users regardless of how they access the network
Enforces a uniform security policy for all users regardless of how they access the network -
 Reduces the administrative and management burden involved in scaling user and network administrator access to the network
Reduces the administrative and management burden involved in scaling user and network administrator access to the network
![]() Cisco Secure ACS uses a central database, which allows it to centralize the control of all user privileges and distribute them to hundreds or thousands of access points throughout the network. Cisco Secure ACS provides detailed reporting and monitoring capabilities of user behavior, access connections, and device configuration changes. This feature has become extremely important for organizations trying to comply with Sarbanes-Oxley Act regulations. Cisco Secure ACS supports a broad variety of access connections, including wired and wireless LAN, dialup, broadband, content, storage, VoIP, firewalls, switches, and VPNs.
Cisco Secure ACS uses a central database, which allows it to centralize the control of all user privileges and distribute them to hundreds or thousands of access points throughout the network. Cisco Secure ACS provides detailed reporting and monitoring capabilities of user behavior, access connections, and device configuration changes. This feature has become extremely important for organizations trying to comply with Sarbanes-Oxley Act regulations. Cisco Secure ACS supports a broad variety of access connections, including wired and wireless LAN, dialup, broadband, content, storage, VoIP, firewalls, switches, and VPNs.
![]() You can leverage the Cisco Secure ACS framework to control administrator access and configuration for all the network devices in your network that support RADIUS and TACACS+. The following are some of the advanced features of Cisco Secure ACS:
You can leverage the Cisco Secure ACS framework to control administrator access and configuration for all the network devices in your network that support RADIUS and TACACS+. The following are some of the advanced features of Cisco Secure ACS:
-
 Automatic service monitoring
Automatic service monitoring -
 Database synchronization and importing of tools for large-scale deployments
Database synchronization and importing of tools for large-scale deployments -
 Lightweight Directory Access Protocol (LDAP) user authentication support
Lightweight Directory Access Protocol (LDAP) user authentication support -
 User and administrative access reporting
User and administrative access reporting -
 Restrictions to network access based on criteria such as the time of day and the day of week
Restrictions to network access based on criteria such as the time of day and the day of week -
 User and device group profiles
User and device group profiles -
 Token-based authentication
Token-based authentication
![]() Cisco Secure ACS is an important component of the Cisco Identity Based Networking Services (IBNS) architecture. Cisco IBNS is based on port-security standards such as IEEE 802.1x and Extensible Authentication Protocol (EAP), and extends security from the perimeter of the network to every connection point inside the LAN. You can deploy new policy control, such as per-user quotas, VLAN assignments, and ACLs within this new architecture, because of the extended capabilities of Cisco switches and wireless access points to query Cisco Secure ACS over the RADIUS protocol.
Cisco Secure ACS is an important component of the Cisco Identity Based Networking Services (IBNS) architecture. Cisco IBNS is based on port-security standards such as IEEE 802.1x and Extensible Authentication Protocol (EAP), and extends security from the perimeter of the network to every connection point inside the LAN. You can deploy new policy control, such as per-user quotas, VLAN assignments, and ACLs within this new architecture, because of the extended capabilities of Cisco switches and wireless access points to query Cisco Secure ACS over the RADIUS protocol.
![]() Cisco Secure ACS is also an important component of Cisco Network Admission Control (NAC). Cisco NAC is an industry initiative sponsored by Cisco that uses the network infrastructure to enforce security-policy compliance on all devices seeking to access network computing resources, thereby limiting damage from viruses and worms. With NAC, customers can choose to allow network access only to compliant and trusted endpoint devices (for instance, PCs, servers, and personal digital assistants [PDAs]) and can restrict the access of noncompliant devices. Cisco NAC is part of the Cisco Self-Defending Network initiative and is the foundation for enabling NAC on Layer 2 and Layer 3 networks. Future phases extend endpoint and network security interoperation to include dynamic incident-containment capabilities. This innovation enables compliant system elements to report misuse emanating from rogue or infected systems during an attack. Thus, infected systems can be dynamically quarantined from the rest of the network to significantly reduce virus, worm, and blended-threat propagation.
Cisco Secure ACS is also an important component of Cisco Network Admission Control (NAC). Cisco NAC is an industry initiative sponsored by Cisco that uses the network infrastructure to enforce security-policy compliance on all devices seeking to access network computing resources, thereby limiting damage from viruses and worms. With NAC, customers can choose to allow network access only to compliant and trusted endpoint devices (for instance, PCs, servers, and personal digital assistants [PDAs]) and can restrict the access of noncompliant devices. Cisco NAC is part of the Cisco Self-Defending Network initiative and is the foundation for enabling NAC on Layer 2 and Layer 3 networks. Future phases extend endpoint and network security interoperation to include dynamic incident-containment capabilities. This innovation enables compliant system elements to report misuse emanating from rogue or infected systems during an attack. Thus, infected systems can be dynamically quarantined from the rest of the network to significantly reduce virus, worm, and blended-threat propagation.
![]() Cisco Secure ACS is a powerful access control server with many high-performance and scalability features for any organization growing its WAN or LAN. The following lists the main benefits of Cisco Secure ACS:
Cisco Secure ACS is a powerful access control server with many high-performance and scalability features for any organization growing its WAN or LAN. The following lists the main benefits of Cisco Secure ACS:
-
 Ease of use: A web-based user interface simplifies and distributes the configuration for user profiles, group profiles, and Cisco Secure ACS configuration.
Ease of use: A web-based user interface simplifies and distributes the configuration for user profiles, group profiles, and Cisco Secure ACS configuration. -
 Scalability: Cisco Secure ACS is built to support large networked environments with support for redundant servers, remote databases, and database replication and backup services.
Scalability: Cisco Secure ACS is built to support large networked environments with support for redundant servers, remote databases, and database replication and backup services. -
 Extensibility: LDAP authentication forwarding supports the authentication of user profiles that are stored in directories from leading directory vendors, including Sun, Novell, and Microsoft.
Extensibility: LDAP authentication forwarding supports the authentication of user profiles that are stored in directories from leading directory vendors, including Sun, Novell, and Microsoft. -
 Management: Microsoft Windows Active Directory support consolidates Windows user name and password management and uses the Windows Performance Monitor for real-time statistics viewing.
Management: Microsoft Windows Active Directory support consolidates Windows user name and password management and uses the Windows Performance Monitor for real-time statistics viewing. -
 Administration: Different access levels for each Cisco Secure ACS administrator and the ability to group network devices together make it easier and more flexible to control the enforcement and changes of security policy administration over all of the devices in a network.
Administration: Different access levels for each Cisco Secure ACS administrator and the ability to group network devices together make it easier and more flexible to control the enforcement and changes of security policy administration over all of the devices in a network. -
 Product flexibility: Because Cisco IOS Software has embedded support for AAA, Cisco Secure ACS can be used across virtually any network access server that Cisco sells (the Cisco IOS Software release must support RADIUS or TACACS+). Cisco Secure ACS is available in three options: Cisco Secure ACS Solution Engine, Cisco Secure ACS Express, and Cisco Secure ACS for Windows.
Product flexibility: Because Cisco IOS Software has embedded support for AAA, Cisco Secure ACS can be used across virtually any network access server that Cisco sells (the Cisco IOS Software release must support RADIUS or TACACS+). Cisco Secure ACS is available in three options: Cisco Secure ACS Solution Engine, Cisco Secure ACS Express, and Cisco Secure ACS for Windows. -
 Integration: Tight coupling with Cisco IOS routers and VPN solutions provides features such as Multichassis Multilink PPP and Cisco IOS Software command authorization.
Integration: Tight coupling with Cisco IOS routers and VPN solutions provides features such as Multichassis Multilink PPP and Cisco IOS Software command authorization. -
 Third-party support: Cisco Secure ACS offers token server support for any one-time password (OTP) vendor that provides an RFC-compliant RADIUS interface, such as RSA, PassGo, Secure Computing, ActiveCard, Vasco, or CryptoCard.
Third-party support: Cisco Secure ACS offers token server support for any one-time password (OTP) vendor that provides an RFC-compliant RADIUS interface, such as RSA, PassGo, Secure Computing, ActiveCard, Vasco, or CryptoCard. -
 Control: Cisco Secure ACS provides dynamic quotas to restrict access based on the time of day, network use, number of logged sessions, and the day of the week.
Control: Cisco Secure ACS provides dynamic quotas to restrict access based on the time of day, network use, number of logged sessions, and the day of the week.
Cisco Secure ACS for Windows Requirements
![]() The Cisco Secure ACS server must meet certain minimum hardware, operating system, and third-party software requirements. In addition, if you are upgrading from an earlier version of Cisco Secure ACS, you should refer to the Cisco Secure ACS upgrade requirements at http://tinyurl.com/8optuc.
The Cisco Secure ACS server must meet certain minimum hardware, operating system, and third-party software requirements. In addition, if you are upgrading from an earlier version of Cisco Secure ACS, you should refer to the Cisco Secure ACS upgrade requirements at http://tinyurl.com/8optuc.
Hardware Requirements
![]() The server that will be running Cisco Secure ACS 4.2 must meet the following minimum hardware requirements:
The server that will be running Cisco Secure ACS 4.2 must meet the following minimum hardware requirements:
-
 Pentium IV processor that is 1.8 GHz or faster
Pentium IV processor that is 1.8 GHz or faster -
 1 GB of RAM
1 GB of RAM -
 At least 1 GB of free disk space; if you are running the database on the same computer, more disk space is required
At least 1 GB of free disk space; if you are running the database on the same computer, more disk space is required -
 Minimum graphics resolution of 256 colors at 800×600 pixels
Minimum graphics resolution of 256 colors at 800×600 pixels
Operating System Requirements
![]() Cisco Secure ACS 4.2 for Windows supports the English-language versions of the following Microsoft Windows operating systems:
Cisco Secure ACS 4.2 for Windows supports the English-language versions of the following Microsoft Windows operating systems:
-
 Windows 2000 Server, with Service Pack 4 installed
Windows 2000 Server, with Service Pack 4 installed -
 Windows 2000 Advanced Server, with the following conditions:
Windows 2000 Advanced Server, with the following conditions: Service Pack 4 installed
Service Pack 4 installed Without Microsoft clustering service installed
Without Microsoft clustering service installed Without other features specific to Windows 2000 Advanced Server enabled, such as Terminal Services.
Without other features specific to Windows 2000 Advanced Server enabled, such as Terminal Services. -
 Windows Server 2003 Service Pack 1, Enterprise Edition or Standard Edition
Windows Server 2003 Service Pack 1, Enterprise Edition or Standard Edition -
 Windows Server 2003, R2, Standard Edition
Windows Server 2003, R2, Standard Edition -
 Windows Server 2003, Service Pack 2
Windows Server 2003, Service Pack 2 -
 Windows Server 2003, R2, Service Pack 2
Windows Server 2003, R2, Service Pack 2
| Note |
|
![]() You can apply the Windows service packs before or after installing Cisco Secure ACS. If you do not install a required service pack before installing Cisco Secure ACS, the Cisco Secure ACS installation program might warn you that the required service pack is not present. If you receive a service pack message, continue the installation, and then install the required service pack before starting user authentication with Cisco Secure ACS.
You can apply the Windows service packs before or after installing Cisco Secure ACS. If you do not install a required service pack before installing Cisco Secure ACS, the Cisco Secure ACS installation program might warn you that the required service pack is not present. If you receive a service pack message, continue the installation, and then install the required service pack before starting user authentication with Cisco Secure ACS.
Virtualization Compatibility
![]() Cisco has also tested ACS 4.2 on VMWare platform MWare ESX server 3.0.0.
Cisco has also tested ACS 4.2 on VMWare platform MWare ESX server 3.0.0.
| Note |
|
Cisco Secure ACS Solution Engine
![]() The Cisco Secure ACS Solution Engine, shown in Figure 2-15, is a one rack unit (RU), security-hardened appliance with a preinstalled Cisco Secure ACS license. The following lists the specifications of Cisco Secure ACS Solution Engine 4.2:
The Cisco Secure ACS Solution Engine, shown in Figure 2-15, is a one rack unit (RU), security-hardened appliance with a preinstalled Cisco Secure ACS license. The following lists the specifications of Cisco Secure ACS Solution Engine 4.2:
-
 CPU 3.4-GHz Intel Pentium 4, 800-MHz FSB, 2-MB cache
CPU 3.4-GHz Intel Pentium 4, 800-MHz FSB, 2-MB cache -
 1 GB of system memory
1 GB of system memory -
 80-GB Serial Advanced Technology Attachment (SATA) hard drive
80-GB Serial Advanced Technology Attachment (SATA) hard drive -
 Combination CD/DVD drive
Combination CD/DVD drive -
 One RS-232 serial port and three USB 2.0 I/O ports (one front, two rear)
One RS-232 serial port and three USB 2.0 I/O ports (one front, two rear)
![]() Compared to the Cisco Secure ACS for Windows product, the Cisco Secure ACS Solution Engine reduces the total cost of ownership by eliminating the need to install and maintain a Microsoft Windows server machine.
Compared to the Cisco Secure ACS for Windows product, the Cisco Secure ACS Solution Engine reduces the total cost of ownership by eliminating the need to install and maintain a Microsoft Windows server machine.
Cisco Secure ACS Express 5.0
![]() Cisco Secure ACS Express 5.0 is intended for commercial (fewer than 350 users), retail, and enterprise branch office deployments. The product offers a comprehensive yet simplified feature set, a cutting-edge user-friendly GUI, and an attractive price point that allows you to deploy this product in situations where Cisco Secure ACS for Windows or Cisco Secure ACS Solution Engine might not be suitable.
Cisco Secure ACS Express 5.0 is intended for commercial (fewer than 350 users), retail, and enterprise branch office deployments. The product offers a comprehensive yet simplified feature set, a cutting-edge user-friendly GUI, and an attractive price point that allows you to deploy this product in situations where Cisco Secure ACS for Windows or Cisco Secure ACS Solution Engine might not be suitable.
![]() Cisco Secure ACS Express 5.0 is available as a one RU, security-hardened appliance with a preinstalled Cisco Secure ACS Express license. Cisco Secure ACS Express 5.0 supports a maximum of 50 AAA clients and 350 unique user logins in a 24-hour period.
Cisco Secure ACS Express 5.0 is available as a one RU, security-hardened appliance with a preinstalled Cisco Secure ACS Express license. Cisco Secure ACS Express 5.0 supports a maximum of 50 AAA clients and 350 unique user logins in a 24-hour period.
![]() The following are some of the hardware specifications of Cisco Secure ACS Express 5.0:
The following are some of the hardware specifications of Cisco Secure ACS Express 5.0:
-
 CPU Intel 352 Celeron D
CPU Intel 352 Celeron D -
 1 GB of system memory
1 GB of system memory -
 250-GB hard drive, CD/DVD drive
250-GB hard drive, CD/DVD drive -
 2-10/100/1000 onboard Ethernet network interface cards (NIC)
2-10/100/1000 onboard Ethernet network interface cards (NIC) -
 One RS-232 serial port and three USB 2.0 I/O ports (one front, two rear)
One RS-232 serial port and three USB 2.0 I/O ports (one front, two rear) -
 1 PS/2 keyboard port and 1 PS/2 mouse port
1 PS/2 keyboard port and 1 PS/2 mouse port
| Note |
|
Cisco Secure ACS View 4.0
![]() Cisco Secure ACS View 4.0 is an advanced reporting and alert tool for multiple Cisco Secure ACS servers. Much like Cisco Monitoring, Analysis, and Response System (MARS), which takes an enterprise approach to logging, Cisco Secure ACS View 4.0 takes a similar approach to monitoring Cisco Secure ACS servers. It has a web-based interface and a significant number of preprogrammed reports which make it a powerful addition to a distributed enterprise that has widely distributed resources and Cisco Secure ACS servers.
Cisco Secure ACS View 4.0 is an advanced reporting and alert tool for multiple Cisco Secure ACS servers. Much like Cisco Monitoring, Analysis, and Response System (MARS), which takes an enterprise approach to logging, Cisco Secure ACS View 4.0 takes a similar approach to monitoring Cisco Secure ACS servers. It has a web-based interface and a significant number of preprogrammed reports which make it a powerful addition to a distributed enterprise that has widely distributed resources and Cisco Secure ACS servers.
 TACACS+ and RADIUS Protocols
TACACS+ and RADIUS Protocols
![]() The Cisco Secure ACS family of products supports both RADIUS and TACACS+ protocols, which are the two predominant AAA protocols that are used by Cisco security appliances, routers, and switches for implementing AAA.
The Cisco Secure ACS family of products supports both RADIUS and TACACS+ protocols, which are the two predominant AAA protocols that are used by Cisco security appliances, routers, and switches for implementing AAA.
![]() Cisco Secure ACS supports both TACACS+ and RADIUS:
Cisco Secure ACS supports both TACACS+ and RADIUS:
-
 TACACS+ remains more secure than RADIUS.
TACACS+ remains more secure than RADIUS. -
 RADIUS has a robust application programming interface and strong accounting.
RADIUS has a robust application programming interface and strong accounting.
TACACS+
![]() TACACS+ is a Cisco enhancement to the original TACACS protocol. Despite its name, TACACS+ is a protocol that was designed from the ground up and it is therefore incompatible with any earlier version of TACACS. TACACS+ has been submitted to the Internet Engineering Task Force (IETF) as a draft proposal.
TACACS+ is a Cisco enhancement to the original TACACS protocol. Despite its name, TACACS+ is a protocol that was designed from the ground up and it is therefore incompatible with any earlier version of TACACS. TACACS+ has been submitted to the Internet Engineering Task Force (IETF) as a draft proposal.
![]() TACACS+ provides separate message types for AAA services. Because TACACS+ separates authentication and authorization, it is possible to use TACACS+ authorization and accounting, while using another method of authentication.
TACACS+ provides separate message types for AAA services. Because TACACS+ separates authentication and authorization, it is possible to use TACACS+ authorization and accounting, while using another method of authentication.
![]() The extensions to the TACACS+ protocol provide more types of authentication requests and response codes than were in the original specification. TACACS+ offers multiprotocol support, such as IP and AppleTalk. Normal TACACS+ operation encrypts the entire body of the packet for more secure communications and uses TCP port 49.
The extensions to the TACACS+ protocol provide more types of authentication requests and response codes than were in the original specification. TACACS+ offers multiprotocol support, such as IP and AppleTalk. Normal TACACS+ operation encrypts the entire body of the packet for more secure communications and uses TCP port 49.
RADIUS
![]() RADIUS is an open IETF standard AAA protocol for applications such as network access or IP mobility that was developed by Livingston Enterprises. RADIUS works in both local and roaming situations and is commonly used for accounting purposes. RADIUS is currently defined by RFCs 2865, 2866, 2867, 2868, and many other related RFCs.
RADIUS is an open IETF standard AAA protocol for applications such as network access or IP mobility that was developed by Livingston Enterprises. RADIUS works in both local and roaming situations and is commonly used for accounting purposes. RADIUS is currently defined by RFCs 2865, 2866, 2867, 2868, and many other related RFCs.
![]() The RADIUS protocol hides the passwords during transmission between the NAS and RADIUS server, even with the PAP protocol, using a rather complex operation that involves Message Digest 5 (MD5) hashing and a shared secret. However, the rest of the packet is sent in plaintext.
The RADIUS protocol hides the passwords during transmission between the NAS and RADIUS server, even with the PAP protocol, using a rather complex operation that involves Message Digest 5 (MD5) hashing and a shared secret. However, the rest of the packet is sent in plaintext.
![]() RADIUS combines authentication and authorization as one process. Once users are authenticated, they are authorized, as well. RADIUS uses User Datagram Protocol (UDP) ports 1645 or 1812 for authentication and UDP ports 1646 or 1813 for accounting.
RADIUS combines authentication and authorization as one process. Once users are authenticated, they are authorized, as well. RADIUS uses User Datagram Protocol (UDP) ports 1645 or 1812 for authentication and UDP ports 1646 or 1813 for accounting.
![]() In addition, RADIUS is widely used by VoIP service providers. It is used to pass login credentials of a Session Initiation Protocol (SIP) endpoint (such as a broadband phone) to a SIP registrar using digest authentication, and then to a RADIUS server using RADIUS. RADIUS is also a common authentication protocol that is used by the 802.1x security standard.
In addition, RADIUS is widely used by VoIP service providers. It is used to pass login credentials of a Session Initiation Protocol (SIP) endpoint (such as a broadband phone) to a SIP registrar using digest authentication, and then to a RADIUS server using RADIUS. RADIUS is also a common authentication protocol that is used by the 802.1x security standard.
![]() The DIAMETER protocol is the planned replacement for RADIUS. DIAMETER is more secure than RADIUS because it uses Stream Control Transmission Protocol (SCTP) or TCP rather than UDP. It also provides for failover procedures, and offers a transition path for current RADIUS implementations.
The DIAMETER protocol is the planned replacement for RADIUS. DIAMETER is more secure than RADIUS because it uses Stream Control Transmission Protocol (SCTP) or TCP rather than UDP. It also provides for failover procedures, and offers a transition path for current RADIUS implementations.
Comparing TACACS+ and RADIUS
![]() There are several differences between TACACS+ and RADIUS, as shown in the following list. Table 2-11 summarizes these differences.
There are several differences between TACACS+ and RADIUS, as shown in the following list. Table 2-11 summarizes these differences.
|
|
| |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
-
 Functionality: TACACS+ separates AAA functions according to the AAA architecture, allowing modularity of the security server implementation. RADIUS combines authentication and authorization, but separates accounting, thus allowing less flexibility in implementation than TACACS+.
Functionality: TACACS+ separates AAA functions according to the AAA architecture, allowing modularity of the security server implementation. RADIUS combines authentication and authorization, but separates accounting, thus allowing less flexibility in implementation than TACACS+. -
 Standard: TACACS+ is a standard that is used mostly by Cisco customers. RADIUS is an open industry standard.
Standard: TACACS+ is a standard that is used mostly by Cisco customers. RADIUS is an open industry standard. -
 Transport protocol: TACACS+ uses TCP. RADIUS uses UDP, which was chosen for the simplification of client and server implementations; however, it makes the RADIUS protocol less robust and requires the server to implement reliability measures such as packet retransmission and timeouts.
Transport protocol: TACACS+ uses TCP. RADIUS uses UDP, which was chosen for the simplification of client and server implementations; however, it makes the RADIUS protocol less robust and requires the server to implement reliability measures such as packet retransmission and timeouts. -
 Challenge and response: TACACS+ supports bidirectional challenge and response as used in Challenge Handshake Authentication Protocol (CHAP) between two routers. RADIUS supports unidirectional challenge and response from the RADIUS security server to the RADIUS client.
Challenge and response: TACACS+ supports bidirectional challenge and response as used in Challenge Handshake Authentication Protocol (CHAP) between two routers. RADIUS supports unidirectional challenge and response from the RADIUS security server to the RADIUS client. -
 Protocol support: TACACS+ provides more complete dialup and WAN protocol support. RADIUS does not support AppleTalk Remote Access (ARA) access, NetBIOS Extended User Interface (NetBEUI), NetWare Access Server Interface (NASI), and X.25 Packet Assembler/Disassembler (PAD) connections.
Protocol support: TACACS+ provides more complete dialup and WAN protocol support. RADIUS does not support AppleTalk Remote Access (ARA) access, NetBIOS Extended User Interface (NetBEUI), NetWare Access Server Interface (NASI), and X.25 Packet Assembler/Disassembler (PAD) connections. -
 Confidentiality: TACACS+ encrypts the entire packet body of every packet. RADIUS encrypts only the password attribute portion of the Access-Request packet, which makes TACACS+ more secure.
Confidentiality: TACACS+ encrypts the entire packet body of every packet. RADIUS encrypts only the password attribute portion of the Access-Request packet, which makes TACACS+ more secure. -
 Customization: The flexibility that is provided in the TACACS+ protocol allows many things to be customized on a per-user basis or per-group basis, including which commands a user can execute on a router. RADIUS lacks this flexibility, and therefore many features that are possible with TACACS+ are not possible with RADIUS.
Customization: The flexibility that is provided in the TACACS+ protocol allows many things to be customized on a per-user basis or per-group basis, including which commands a user can execute on a router. RADIUS lacks this flexibility, and therefore many features that are possible with TACACS+ are not possible with RADIUS. -
 Accounting: TACACS+ accounting includes a limited number of information fields. RADIUS accounting can contain more information than TACAS+ accounting records, which is the key strength of RADIUS over TACACS+.
Accounting: TACACS+ accounting includes a limited number of information fields. RADIUS accounting can contain more information than TACAS+ accounting records, which is the key strength of RADIUS over TACACS+.
 Installing Cisco Secure ACS for Windows
Installing Cisco Secure ACS for Windows
![]() Before installing Cisco Secure ACS, it is important to prepare the server. You must consider third-party software requirements and the network and port requirements of the Cisco Secure ACS server and AAA devices.
Before installing Cisco Secure ACS, it is important to prepare the server. You must consider third-party software requirements and the network and port requirements of the Cisco Secure ACS server and AAA devices.
Third-Party Software Requirements
![]() Other than the software products that are described in the release notes, Cisco has not tested the interoperability of Cisco Secure ACS and other software products on the same computer. Cisco will only support interoperability issues with software products that are mentioned in the release notes. The most recent version of the Cisco Secure ACS release notes is posted on Cisco.com.
Other than the software products that are described in the release notes, Cisco has not tested the interoperability of Cisco Secure ACS and other software products on the same computer. Cisco will only support interoperability issues with software products that are mentioned in the release notes. The most recent version of the Cisco Secure ACS release notes is posted on Cisco.com.
Network and Port Requirements
![]() The network should meet the following requirements before you begin deploying Cisco Secure ACS:
The network should meet the following requirements before you begin deploying Cisco Secure ACS:
-
 For full TACACS+ and RADIUS support on Cisco IOS devices, AAA clients must run Cisco IOS Release 11.2 or later.
For full TACACS+ and RADIUS support on Cisco IOS devices, AAA clients must run Cisco IOS Release 11.2 or later. -
 Cisco devices that are not Cisco IOS AAA clients must be configured with TACACS+, RADIUS, or both.
Cisco devices that are not Cisco IOS AAA clients must be configured with TACACS+, RADIUS, or both. -
 Dial-in, VPN, or wireless clients must be able to connect to the applicable AAA clients.
Dial-in, VPN, or wireless clients must be able to connect to the applicable AAA clients. -
 The computer running Cisco Secure ACS must be able to reach all AAA clients using ping.
The computer running Cisco Secure ACS must be able to reach all AAA clients using ping. -
 Gateway devices between the Cisco Secure ACS and other network devices must permit communication over the ports that are needed to support the applicable feature or protocol.
Gateway devices between the Cisco Secure ACS and other network devices must permit communication over the ports that are needed to support the applicable feature or protocol. -
 A supported web browser must be installed on the computer running Cisco Secure ACS. For the most recent information about tested browsers, see the release notes for your Cisco Secure ACS product on Cisco.com.
A supported web browser must be installed on the computer running Cisco Secure ACS. For the most recent information about tested browsers, see the release notes for your Cisco Secure ACS product on Cisco.com. -
 All network cards in the computer running Cisco Secure ACS must be enabled. If there is a disabled network card on the computer running Cisco Secure ACS, installing Cisco Secure ACS may proceed slowly because of delays that are caused by the Microsoft CryptoAPI.
All network cards in the computer running Cisco Secure ACS must be enabled. If there is a disabled network card on the computer running Cisco Secure ACS, installing Cisco Secure ACS may proceed slowly because of delays that are caused by the Microsoft CryptoAPI.
 Configuring the Server
Configuring the Server
![]() After successfully installing Cisco Secure ACS, you must perform some initial configuration. The only way to configure a Cisco Secure ACS server is through an HTML interface, as shown in Figure 2-16. To access the Cisco Secure ACS HTML interface from the computer that is running Cisco Secure ACS, you can use the Cisco Secure icon labeled ACS Admin that appears on the desktop or you can enter the following URL into a supported web browser: http://127.0.0.1:2002.
After successfully installing Cisco Secure ACS, you must perform some initial configuration. The only way to configure a Cisco Secure ACS server is through an HTML interface, as shown in Figure 2-16. To access the Cisco Secure ACS HTML interface from the computer that is running Cisco Secure ACS, you can use the Cisco Secure icon labeled ACS Admin that appears on the desktop or you can enter the following URL into a supported web browser: http://127.0.0.1:2002.
| Note |
|
![]() The home page of Cisco Secure ACS is divided into frames. The buttons in the navigation bar represent a particular area or function that you can configure. When you click one of the buttons in the navigation bar, the window that opens enables you to access help on the right side of the window.
The home page of Cisco Secure ACS is divided into frames. The buttons in the navigation bar represent a particular area or function that you can configure. When you click one of the buttons in the navigation bar, the window that opens enables you to access help on the right side of the window.
![]() The following are the navigation buttons that are available in the navigation bar.
The following are the navigation buttons that are available in the navigation bar.
-
 User Setup: This option enables you to add a new user, search for an existing user, find users alphabetically or numerically, or simply list all users at once.
User Setup: This option enables you to add a new user, search for an existing user, find users alphabetically or numerically, or simply list all users at once. -
 Group Setup: This option enables you to configure any parameters that are common to a group of users. In this section, you can apply configuration from shared profile components and specific TACACS+ and RADIUS attributes.
Group Setup: This option enables you to configure any parameters that are common to a group of users. In this section, you can apply configuration from shared profile components and specific TACACS+ and RADIUS attributes. -
 Shared Profile Components: This option allows you to specify shell command authorization sets and Cisco PIX Firewall shell command authorization sets. By creating these command authorization sets, you can control the commands a user can execute on a device by applying the command authorization set to the user profile in the TACACS+ settings or at the group level.
Shared Profile Components: This option allows you to specify shell command authorization sets and Cisco PIX Firewall shell command authorization sets. By creating these command authorization sets, you can control the commands a user can execute on a device by applying the command authorization set to the user profile in the TACACS+ settings or at the group level. -
 Network Configuration: This option is where you add, delete, or modify settings for AAA clients.
Network Configuration: This option is where you add, delete, or modify settings for AAA clients. -
 System Configuration: Under this option, you will find many subconfiguration links:
System Configuration: Under this option, you will find many subconfiguration links:-
 Service Control: Allows you to start and stop the Cisco Secure ACS services.
Service Control: Allows you to start and stop the Cisco Secure ACS services. -
 Logging: Allows you to configure logging, such as failed attempts, and TACACS+ and RADIUS accounting.
Logging: Allows you to configure logging, such as failed attempts, and TACACS+ and RADIUS accounting. -
 Date Format Control: Allows you to change the format of the date that is displayed on reports.
Date Format Control: Allows you to change the format of the date that is displayed on reports. -
 Local Password Management: Allows you to set password length and password options. You can also configure options for remote password change and logging of password changes.
Local Password Management: Allows you to set password length and password options. You can also configure options for remote password change and logging of password changes. -
 ACS Backup: Allows you to schedule backups to be performed manually or automatically at specific times.
ACS Backup: Allows you to schedule backups to be performed manually or automatically at specific times. -
 ACS Service Management: Enables you to determine how often to test the availability of ACS authentication services.
ACS Service Management: Enables you to determine how often to test the availability of ACS authentication services.
-
-
 Interface Configuration: This option allows you to configure user-defined fields that are recorded in accounting logs, configure TACACS+ and RADIUS options, and control the display of options in the user interface. What options are available depends on whether you have selected TACACS+ or a form of RADIUS when you entered your AAA client.
Interface Configuration: This option allows you to configure user-defined fields that are recorded in accounting logs, configure TACACS+ and RADIUS options, and control the display of options in the user interface. What options are available depends on whether you have selected TACACS+ or a form of RADIUS when you entered your AAA client.Note  If you do not see RADIUS options here, you must add a AAA client that uses the RADIUS protocol. Interface Configuration is directly affected by the settings in Network Configuration.
If you do not see RADIUS options here, you must add a AAA client that uses the RADIUS protocol. Interface Configuration is directly affected by the settings in Network Configuration. -
 Administration Control: This option enables you to configure all aspects of Cisco Secure ACS for administrative access.
Administration Control: This option enables you to configure all aspects of Cisco Secure ACS for administrative access. -
 External User Databases: This option enables you to configure the unknown user policy, configure authorization privileges for unknown users, and configure external database types.
External User Databases: This option enables you to configure the unknown user policy, configure authorization privileges for unknown users, and configure external database types. -
 Posture Validation: Cisco Secure ACS supports the NAC initiative. NAC ensures that every endpoint conforms to the security policy before they are granted access to the network. The Posture Validation option enables you to configure NAC options.
Posture Validation: Cisco Secure ACS supports the NAC initiative. NAC ensures that every endpoint conforms to the security policy before they are granted access to the network. The Posture Validation option enables you to configure NAC options. -
 Network Access Profiles: This option enables you to classify access requests according to the IP address of a AAA client, membership in a network device group, protocol types, or other specific RADIUS attribute values sent by the network device through which the user connects. Cisco Secure ACS does not support network access profiles for TACACS+.
Network Access Profiles: This option enables you to classify access requests according to the IP address of a AAA client, membership in a network device group, protocol types, or other specific RADIUS attribute values sent by the network device through which the user connects. Cisco Secure ACS does not support network access profiles for TACACS+. -
 Reports and Activity: Cisco Secure ACS keeps track of a lot of information. Use this option to view the following logs that Cisco Secure ACS keeps:
Reports and Activity: Cisco Secure ACS keeps track of a lot of information. Use this option to view the following logs that Cisco Secure ACS keeps: TACACS+ accounting
TACACS+ accounting TACACS+ administration
TACACS+ administration RADIUS accounting
RADIUS accounting Passed authentications
Passed authentications Failed attempts
Failed attempts Logged-in users
Logged-in users Disabled accounts
Disabled accounts Cisco Secure ACS backup and restore
Cisco Secure ACS backup and restore Remote Database Management Source (RDBMS) synchronization
Remote Database Management Source (RDBMS) synchronization Database replication
Database replication Administration audit
Administration audit User password changes
User password changes Cisco Secure ACS service monitoring
Cisco Secure ACS service monitoring -
 Online Documentation: This button provides access to documentation for Cisco Secure ACS online at Cisco.com.
Online Documentation: This button provides access to documentation for Cisco Secure ACS online at Cisco.com.
Network Configuration
![]() Before configuring a router, switch, or firewall as a TACACS+ or RADIUS client, you must add the AAA client to the Cisco Secure ACS server and specify the IP address and encryption key, as shown in Figure 2-17. The Network Configuration page is where you add, delete, or modify settings for AAA clients.
Before configuring a router, switch, or firewall as a TACACS+ or RADIUS client, you must add the AAA client to the Cisco Secure ACS server and specify the IP address and encryption key, as shown in Figure 2-17. The Network Configuration page is where you add, delete, or modify settings for AAA clients.
![]() Follow these steps to create a AAA client:
Follow these steps to create a AAA client:
|
|
| |||
|
| ||||
|
|
| |||
|
|
| |||
|
|
| |||
|
|
| |||
|
|
| |||
|
|
|
Interface Configuration
![]() The options available from the Interface Configuration navigation button, shown in Figure 2-18, enable you to control the display of options in the user interface. The following configuration links are available when you click the Interface Configuration button; the specific options you see depend on whether you have added TACACS+ or RADIUS clients to the Cisco Secure ACS server:
The options available from the Interface Configuration navigation button, shown in Figure 2-18, enable you to control the display of options in the user interface. The following configuration links are available when you click the Interface Configuration button; the specific options you see depend on whether you have added TACACS+ or RADIUS clients to the Cisco Secure ACS server:
-
 TACACS+ (Cisco IOS)
TACACS+ (Cisco IOS) -
 RADIUS (Microsoft)
RADIUS (Microsoft) -
 RADIUS (Ascend)
RADIUS (Ascend) -
 RADIUS (IETF)
RADIUS (IETF) -
 RADIUS (Cisco IOS/PIX 6.0)
RADIUS (Cisco IOS/PIX 6.0) -
 Advanced Options
Advanced Options
| Note |
|
![]() The User Data Configuration link enables you to customize the fields that appear in the user setup and configuration windows. Here you can add fields such as phone number, work location, supervisor name, or any other pertinent information.
The User Data Configuration link enables you to customize the fields that appear in the user setup and configuration windows. Here you can add fields such as phone number, work location, supervisor name, or any other pertinent information.
![]() The TACACS+ (Cisco IOS) link enables the administrator to configure TACACS+ settings and add new TACACS+ services. You can also configure advanced options that affect what you see in your user interface.
The TACACS+ (Cisco IOS) link enables the administrator to configure TACACS+ settings and add new TACACS+ services. You can also configure advanced options that affect what you see in your user interface.
Configuring Cisco Secure ACS for External Databases
![]() You can configure Cisco Secure ACS to forward authentication of users to one or more external user databases. Support for external user databases means that Cisco Secure ACS does not require you to create duplicate user entries in the Cisco Secure user database. In organizations in which a substantial user database already exists, Cisco Secure ACS can leverage the work already invested in building the database without any additional input. Figure 2-19 shows an example of Cisco Secure ACS External databases choices.
You can configure Cisco Secure ACS to forward authentication of users to one or more external user databases. Support for external user databases means that Cisco Secure ACS does not require you to create duplicate user entries in the Cisco Secure user database. In organizations in which a substantial user database already exists, Cisco Secure ACS can leverage the work already invested in building the database without any additional input. Figure 2-19 shows an example of Cisco Secure ACS External databases choices.
![]() For most database configurations, except for Windows databases, Cisco Secure ACS supports only one instance of a username and password. If you configure Cisco Secure ACS to use multiple user databases with common usernames stored in each, you must be careful with the database configurations; the first database to match the authentication credentials of the user is the only one that Cisco Secure ACS uses for that user.
For most database configurations, except for Windows databases, Cisco Secure ACS supports only one instance of a username and password. If you configure Cisco Secure ACS to use multiple user databases with common usernames stored in each, you must be careful with the database configurations; the first database to match the authentication credentials of the user is the only one that Cisco Secure ACS uses for that user.
| Note |
|
![]() Follow these steps, shown in Figure 2-19, to configure Cisco Secure ACS to use external databases:
Follow these steps, shown in Figure 2-19, to configure Cisco Secure ACS to use external databases:
Configuring a Windows Database as the External Database for Cisco Secure ACS
![]() The Windows external database configuration has more options than other external database configurations. Because Cisco Secure ACS is native to the Windows operating system, you can configure additional functionality using the Windows external database option, functionality that you cannot configure with other external database options.
The Windows external database configuration has more options than other external database configurations. Because Cisco Secure ACS is native to the Windows operating system, you can configure additional functionality using the Windows external database option, functionality that you cannot configure with other external database options.
|
|
|
|
|
|
| Note |
|
![]() Another option you can configure using the Windows external database is to map databases to domains. This option allows you to have the same username across different domains, all with different passwords.
Another option you can configure using the Windows external database is to map databases to domains. This option allows you to have the same username across different domains, all with different passwords.
Authenticating Users with the External Database
![]() After you have configured Cisco Secure ACS to communicate with an external user database, you can configure Cisco Secure ACS to authenticate users with the external user database in one of two ways:
After you have configured Cisco Secure ACS to communicate with an external user database, you can configure Cisco Secure ACS to authenticate users with the external user database in one of two ways:
-
 By specific user assignment: You can configure Cisco Secure ACS to authenticate specific users with an external user database.
By specific user assignment: You can configure Cisco Secure ACS to authenticate specific users with an external user database. -
 By unknown user policy: You can configure Cisco Secure ACS to use an external database to authenticate users not found in the Cisco Secure user database. This method does not require you to define users in the Cisco Secure user database.
By unknown user policy: You can configure Cisco Secure ACS to use an external database to authenticate users not found in the Cisco Secure user database. This method does not require you to define users in the Cisco Secure user database.
![]() Follow these steps to configure the unknown user policy in Cisco Secure ACS:
Follow these steps to configure the unknown user policy in Cisco Secure ACS:
|
|
| |||
|
|
| |||
|
|
| |||
|
|
| |||
|
|
| |||
|
|
|
![]() Figure 2-21 shows an example of an Unknown User Policy interface.
Figure 2-21 shows an example of an Unknown User Policy interface.
Group Setup
![]() After a user has been authenticated to an external database, the authorization that takes place is up to Cisco Secure ACS. This can complicate things because users authenticated by a Windows server might require different authorizations than users authenticated by the LDAP server.
After a user has been authenticated to an external database, the authorization that takes place is up to Cisco Secure ACS. This can complicate things because users authenticated by a Windows server might require different authorizations than users authenticated by the LDAP server.
![]() Because of this potential need for different authorizations, you should place users authenticated by the Windows server in one group and users authenticated by the LDAP server in another group. To do this, use database group mappings. Database group mappings enable you to map an authentication server, such as LDAP, Windows, ODBC, and so on, to a group that you have configured in Cisco Secure ACS. For some databases, a user can belong to only one group. For other databases, such as LDAP and Windows, support for group mapping by external database group membership is possible.
Because of this potential need for different authorizations, you should place users authenticated by the Windows server in one group and users authenticated by the LDAP server in another group. To do this, use database group mappings. Database group mappings enable you to map an authentication server, such as LDAP, Windows, ODBC, and so on, to a group that you have configured in Cisco Secure ACS. For some databases, a user can belong to only one group. For other databases, such as LDAP and Windows, support for group mapping by external database group membership is possible.
| Key Topic |
|
![]() One of the things you can configure in group setup is Per Group Command Authorization, which uses the Cisco Secure ACS to authorize which router commands the users that belong to a group can execute. In Figure 2-22, the group is permitted to execute any router commands except show running-config. This example is configured by doing the following:
One of the things you can configure in group setup is Per Group Command Authorization, which uses the Cisco Secure ACS to authorize which router commands the users that belong to a group can execute. In Figure 2-22, the group is permitted to execute any router commands except show running-config. This example is configured by doing the following:
|
|
|
|
|
|
|
|
|
| Note |
|
User Setup
![]() The configuration of user access is a critical task for configuring Cisco Secure ACS. Follow these steps to add a user account to the Cisco Secure ACS Server database:
The configuration of user access is a critical task for configuring Cisco Secure ACS. Follow these steps to add a user account to the Cisco Secure ACS Server database:
|
|
|
|
| |
|
|
|
|
|
|
| Note |
|
![]() Figure 2-23 shows how to accomplish user setup in Cisco Secure ACS.
Figure 2-23 shows how to accomplish user setup in Cisco Secure ACS.
 Configuring TACACS+ Support on a Cisco Router
Configuring TACACS+ Support on a Cisco Router
![]() The next step in configuring the router for TACACS+ support is to specify a list of available Cisco Secure ACS servers that will provide TACACS+ services for the router. Follow these steps to use Cisco SDM to add a TACACS+ server to the router:
The next step in configuring the router for TACACS+ support is to specify a list of available Cisco Secure ACS servers that will provide TACACS+ services for the router. Follow these steps to use Cisco SDM to add a TACACS+ server to the router:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The resulting CLI command that Cisco SDM will generate following the preceding steps is tacacs-server host 10.0.1.1 key secretkey.
The resulting CLI command that Cisco SDM will generate following the preceding steps is tacacs-server host 10.0.1.1 key secretkey.
Creating a AAA Login Authentication Policy
![]() After you enable AAA and configure the TACACS+ servers, you can configure the router to use the Cisco Secure ACS server to authenticate users logging in to the router. To configure the router to use the Cisco Secure ACS server for login authentication, you must create a user-defined authentication login method list or edit the default method list, and then apply this list to a router interface or line. The default method list is automatically applied to all interfaces and lines except those that have a user-defined method list explicitly applied. A user-defined method list overrides the default method list.
After you enable AAA and configure the TACACS+ servers, you can configure the router to use the Cisco Secure ACS server to authenticate users logging in to the router. To configure the router to use the Cisco Secure ACS server for login authentication, you must create a user-defined authentication login method list or edit the default method list, and then apply this list to a router interface or line. The default method list is automatically applied to all interfaces and lines except those that have a user-defined method list explicitly applied. A user-defined method list overrides the default method list.
| Note |
|
![]() Follow these steps to use Cisco SDM to configure a user-defined authentication login method list:
Follow these steps to use Cisco SDM to configure a user-defined authentication login method list:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The resulting CLI command that Cisco SDM generates is aaa authentication login TACACS_SERVER group tacacs+ enable.
The resulting CLI command that Cisco SDM generates is aaa authentication login TACACS_SERVER group tacacs+ enable.
Applying an Authentication Policy
![]() Once you create the authentication login method lists, you can apply the lists to lines and interfaces on the router.
Once you create the authentication login method lists, you can apply the lists to lines and interfaces on the router.
![]() Follow these steps to apply an authentication policy to a router line using Cisco SDM:
Follow these steps to apply an authentication policy to a router line using Cisco SDM:
|
|
|
|
|
|
|
|
|
![]() Example 2-27 shows the resulting CLI commands that Cisco SDM will generate in Figure 2-26.
Example 2-27 shows the resulting CLI commands that Cisco SDM will generate in Figure 2-26.
Router(config)# line vty 0 4
Router(config-line)# login authentication TACACS_SERVER
![]() You can also use the CLI to apply an authentication policy to lines or interfaces. Use the CLI command login authentication {default | list-name} in line configuration mode or interface configuration mode, where list-name is the name of the method list that was created and default is the default list.
You can also use the CLI to apply an authentication policy to lines or interfaces. Use the CLI command login authentication {default | list-name} in line configuration mode or interface configuration mode, where list-name is the name of the method list that was created and default is the default list.
Creating a AAA Exec Authorization Policy
![]() Because the TACACS+ protocol allows you to separate authentication from authorization, you can configure a router to restrict the user to be able to perform only certain functions after successful authentication. You can configure authorization for both character mode (exec authorization) and packet mode (network authorization).
Because the TACACS+ protocol allows you to separate authentication from authorization, you can configure a router to restrict the user to be able to perform only certain functions after successful authentication. You can configure authorization for both character mode (exec authorization) and packet mode (network authorization).
![]() To configure the router to use the Cisco Secure ACS server for authorization, you must create a user-defined authorization method list or edit the default authorization method list. The default authorization method list is automatically applied to all interfaces except those that have a user-defined authorization method list explicitly applied. A user-defined authorization method list overrides the default authorization method list.
To configure the router to use the Cisco Secure ACS server for authorization, you must create a user-defined authorization method list or edit the default authorization method list. The default authorization method list is automatically applied to all interfaces except those that have a user-defined authorization method list explicitly applied. A user-defined authorization method list overrides the default authorization method list.
| Tip |
|
![]() Follow these steps to use Cisco SDM to configure the default authorization method list for character mode (exec) access:
Follow these steps to use Cisco SDM to configure the default authorization method list for character mode (exec) access:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The resulting CLI command that Cisco SDM will generate is aaa authorization exec default group tacacs+.
The resulting CLI command that Cisco SDM will generate is aaa authorization exec default group tacacs+.
Creating a AAA Network Authorization Policy
![]() Follow these steps to use Cisco SDM to configure the default authorization method list for packet mode (network) access:
Follow these steps to use Cisco SDM to configure the default authorization method list for packet mode (network) access:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The resulting CLI command that Cisco SDM will generate is aaa authorization network default group tacacs+.
The resulting CLI command that Cisco SDM will generate is aaa authorization network default group tacacs+.
AAA Accounting Configuration
![]() Cisco Secure ACS serves as a central repository for accounting information, essentially tracking events that occur on the network. Each session that is established through Cisco Secure ACS can be fully accounted for, and stored on, the server. This stored information can be very helpful for management, security audits, capacity planning, and network-usage billing.
Cisco Secure ACS serves as a central repository for accounting information, essentially tracking events that occur on the network. Each session that is established through Cisco Secure ACS can be fully accounted for, and stored on, the server. This stored information can be very helpful for management, security audits, capacity planning, and network-usage billing.
![]() Like authentication and authorization method lists, method lists for accounting define the way accounting will be performed and the sequence in which these methods are performed. The default accounting method list is automatically applied to all interfaces except those that have a named accounting method list explicitly defined. A defined accounting method list overrides the default accounting method list.
Like authentication and authorization method lists, method lists for accounting define the way accounting will be performed and the sequence in which these methods are performed. The default accounting method list is automatically applied to all interfaces except those that have a named accounting method list explicitly defined. A defined accounting method list overrides the default accounting method list.
![]() AAA supports six different types of accounting: network, connection, exec, system, command, and resource.
AAA supports six different types of accounting: network, connection, exec, system, command, and resource.
![]() Currently, AAA accounting can be configured only via the CLI.
Currently, AAA accounting can be configured only via the CLI.
![]() To configure AAA accounting using named method lists, use the commands shown in Table 2-12 beginning in global configuration mode.
To configure AAA accounting using named method lists, use the commands shown in Table 2-12 beginning in global configuration mode.
|
|
|
|
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Named accounting method lists are specific to the indicated type of accounting. The aaa accounting parameters shown in Table 2-13 describes the types of accounting that can use named accounting method lists. The aaa accounting command enables you to specify how much information to record for accounting. Table 2-13 also describes the AAA accounting record types.
Named accounting method lists are specific to the indicated type of accounting. The aaa accounting parameters shown in Table 2-13 describes the types of accounting that can use named accounting method lists. The aaa accounting command enables you to specify how much information to record for accounting. Table 2-13 also describes the AAA accounting record types.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|
AAA Configuration for TACACS+ Example
![]() Example 2-28 shows the resulting running configuration of a router that has been configured for TACACS+ services using Cisco SDM and CLI commands.
Example 2-28 shows the resulting running configuration of a router that has been configured for TACACS+ services using Cisco SDM and CLI commands.
aaa new-model
!
aaa authentication login TACACS_SERVER tacacs+ local
aaa authorization exec tacacs+
aaa authorization network tacacs+
aaa accounting exec start-stop tacacs+
aaa accounting network start-stop tacacs+
aaa accounting commands 15 default stop-only group tacacs+
!
!
tacacs-server host 10.0.1.11
tacacs-server key ciscosecure
!
line vty 0 4
login authentication TACACS_SERVER
![]() The following is an explanation of the commands displayed in Example 2-28:
The following is an explanation of the commands displayed in Example 2-28:
-
 aaa new-model: Enables AAA
aaa new-model: Enables AAA -
 aaa authentication login TACACS_SERVER tacacs+ local: Defines a AAA login policy entitled TACACS_SERVER that uses TACACS+ as the first authentication method and the local database as a second method if TACACS+ is unavailable
aaa authentication login TACACS_SERVER tacacs+ local: Defines a AAA login policy entitled TACACS_SERVER that uses TACACS+ as the first authentication method and the local database as a second method if TACACS+ is unavailable -
 aaa authorization exec tacacs+: Defines a AAA authorization policy that utilizes TACACS+ for access to an EXEC prompt
aaa authorization exec tacacs+: Defines a AAA authorization policy that utilizes TACACS+ for access to an EXEC prompt -
 aaa authorization network tacacs+: Defines a AAA authorization policy that utilizes TACACS+ for network access
aaa authorization network tacacs+: Defines a AAA authorization policy that utilizes TACACS+ for network access -
 aaa accounting exec start-stop tacacs+: Defines a AAA accounting policy that utilizes TACACS+ for logging both start and stop records for user EXEC terminal sessions
aaa accounting exec start-stop tacacs+: Defines a AAA accounting policy that utilizes TACACS+ for logging both start and stop records for user EXEC terminal sessions -
 aaa accounting network start-stop tacacs+: Defines a AAA accounting policy that utilizes TACACS+ for logging both start and stop records for all network-related service requests
aaa accounting network start-stop tacacs+: Defines a AAA accounting policy that utilizes TACACS+ for logging both start and stop records for all network-related service requests -
 aaa accounting commands 15 default stop-only group tacacs+: Defines a default commands accounting method list, where accounting services are provided by a TACACS+ security server, set for privilege level 15 commands with a stop-only restriction
aaa accounting commands 15 default stop-only group tacacs+: Defines a default commands accounting method list, where accounting services are provided by a TACACS+ security server, set for privilege level 15 commands with a stop-only restriction -
 tacacs-server host 10.0.1.11: Configures the IP address of the TACACS+ server
tacacs-server host 10.0.1.11: Configures the IP address of the TACACS+ server -
 tacacs-server key ciscosecure: Configures an encryption key of ciscosecure to be used when communicating with the TACACS+ server
tacacs-server key ciscosecure: Configures an encryption key of ciscosecure to be used when communicating with the TACACS+ server -
 line vty 0 4: Enters line configuration mode for vty 0 through vty 4
line vty 0 4: Enters line configuration mode for vty 0 through vty 4 -
 login authentication TACACS_SERVER: Applies the AAA authentication policy named TACACS_SERVER to all five vty lines
login authentication TACACS_SERVER: Applies the AAA authentication policy named TACACS_SERVER to all five vty lines
 Troubleshooting TACACS+
Troubleshooting TACACS+
![]() Use the debug aaa authentication command in privileged EXEC mode to get a high-level view of login activity. When the TACACS+ protocol is used on the router, you can also use the debug tacacs command for more detailed debugging information. To disable debugging output, use the no form of this command.
Use the debug aaa authentication command in privileged EXEC mode to get a high-level view of login activity. When the TACACS+ protocol is used on the router, you can also use the debug tacacs command for more detailed debugging information. To disable debugging output, use the no form of this command.
![]() Example 2-29 provides sample output from the debug aaa authentication command for a TACACS+ login attempt that was successful. The information indicates that TACACS+ is the authentication method that was used.
Example 2-29 provides sample output from the debug aaa authentication command for a TACACS+ login attempt that was successful. The information indicates that TACACS+ is the authentication method that was used.
Router# debug aaa authentication
14:01:17: AAA/AUTHEN (567936829): Method=TACACS+
14:01:17: TAC+: send AUTHEN/CONT packet
14:01:17: TAC+ (567936829): received authen response status = PASS
14:01:17: AAA/AUTHEN (567936829): status = PASS
The following is sample output from the debug tacacs command for a TACACS+ login
attempt that was successful, as indicated by the status PASS:
Router# debug tacacs
14:00:09: TAC+: Opening TCP/IP connection to 192.168.60.15 using source
10.116.0.79
14:00:09: TAC+: Sending TCP/IP packet number 383258052-1 to 192.168.60.15
(AUTHEN/START)
14:00:09: TAC+: Receiving TCP/IP packet number 383258052-2 from 192.168.60.15
14:00:09: TAC+ (383258052): received authen response status = GETUSER
14:00:10: TAC+: send AUTHEN/CONT packet
14:00:10: TAC+: Sending TCP/IP packet number 383258052-3 to 192.168.60.15
(AUTHEN/CONT)
14:00:10: TAC+: Receiving TCP/IP packet number 383258052-4 from 192.168.60.15
14:00:10: TAC+ (383258052): received authen response status = GETPASS
14:00:14: TAC+: send AUTHEN/CONT packet
14:00:14: TAC+: Sending TCP/IP packet number 383258052-5 to 192.168.60.15
(AUTHEN/CONT)
14:00:14: TAC+: Receiving TCP/IP packet number 383258052-6 from 192.168.60.15
14:00:14: TAC+ (383258052): received authen response status = PASS
14:00:14: TAC+: Closing TCP/IP connection to 192.168.60.15
![]() Example 2-30 shows sample output from the debug tacacs command for a TACACS+ login attempt that was unsuccessful, as indicated by the status FAIL.
Example 2-30 shows sample output from the debug tacacs command for a TACACS+ login attempt that was unsuccessful, as indicated by the status FAIL.
Router# debug tacacs
13:53:35: TAC+: Opening TCP/IP connection to 192.168.60.15 using source
192.48.0.79
13:53:35: TAC+: Sending TCP/IP packet number 416942312-1 to 192.168.60.15
(AUTHEN/START)
13:53:35: TAC+: Receiving TCP/IP packet number 416942312-2 from 192.168.60.15
13:53:35: TAC+ (416942312): received authen response status = GETUSER
13:53:37: TAC+: send AUTHEN/CONT packet
13:53:37: TAC+: Sending TCP/IP packet number 416942312-3 to 192.168.60.15
(AUTHEN/CONT)
13:53:37: TAC+: Receiving TCP/IP packet number 416942312-4 from 192.168.60.15
13:53:37: TAC+ (416942312): received authen response status = GETPASS
13:53:38: TAC+: send AUTHEN/CONT packet
13:53:38: TAC+: Sending TCP/IP packet number 416942312-5 to 192.168.60.15
(AUTHEN/CONT)
13:53:38: TAC+: Receiving TCP/IP packet number 416942312-6 from 192.168.60.15
13:53:38: TAC+ (416942312): received authen response status = FAIL
13:53:40: TAC+: Closing TCP/IP connection to 192.168.60.15
![]() To display information from the TACACS+ helper process, use the debug tacacs events command in privileged EXEC mode. To disable debugging output, use the no form of this command.
To display information from the TACACS+ helper process, use the debug tacacs events command in privileged EXEC mode. To disable debugging output, use the no form of this command.
| Note |
|
![]() Example 2-31 shows sample output from the debug tacacs events command. The example shows the opening and closing of a TCP connection to a TACACS+ server, the bytes read and written over the connection, and the TCP status of the connection:
Example 2-31 shows sample output from the debug tacacs events command. The example shows the opening and closing of a TCP connection to a TACACS+ server, the bytes read and written over the connection, and the TCP status of the connection:
Router# debug tacacs events
%LINK-3-UPDOWN: Interface Async2, changed state to up
00:03:16: TAC+: Opening TCP/IP to 192.168.58.104/1049 timeout=15
00:03:16: TAC+: Opened TCP/IP handle 0x48A87C to 192.168.58.104/1049
00:03:16: TAC+: periodic timer started
00:03:16: TAC+: 192.168.58.104 req=3BD868 id=-1242409656 ver=193 handle=0x48A87C
(ESTAB)
expire=14 AUTHEN/START/SENDAUTH/CHAP queued
00:03:17: TAC+: 192.168.58.104 ESTAB 3BD868 wrote 46 of 46 bytes
00:03:22: TAC+: 192.168.58.104 CLOSEWAIT read=12 wanted=12 alloc=12 got=12
00:03:22: TAC+: 192.168.58.104 CLOSEWAIT read=61 wanted=61 alloc=61 got=49
00:03:22: TAC+: 192.168.58.104 received 61 byte reply for 3BD868
00:03:22: TAC+: req=3BD868 id=-1242409656 ver=193 handle=0x48A87C (CLOSEWAIT)
expire=9
AUTHEN/START/SENDAUTH/CHAP processed
00:03:22: TAC+: periodic timer stopped (queue empty)
00:03:22: TAC+: Closing TCP/IP 0x48A87C connection to 192.168.58.104/1049
00:03:22: TAC+: Opening TCP/IP to 192.168.58.104/1049 timeout=15
00:03:22: TAC+: Opened TCP/IP handle 0x489F08 to 192.168.58.104/1049
00:03:22: TAC+: periodic timer started
00:03:22: TAC+: 192.168.58.104 req=3BD868 id=299214410 ver=192 handle=0x489F08
(ESTAB)
expire=14 AUTHEN/START/SENDPASS/CHAP queued
00:03:23: TAC+: 192.168.58.104 ESTAB 3BD868 wrote 41 of 41 bytes
00:03:23: TAC+: 192.168.58.104 CLOSEWAIT read=12 wanted=12 alloc=12 got=12
00:03:23: TAC+: 192.168.58.104 CLOSEWAIT read=21 wanted=21 alloc=21 got=9
00:03:23: TAC+: 192.168.58.104 received 21 byte reply for 3BD868
00:03:23: TAC+: req=3BD868 id=299214410 ver=192 handle=0x489F08 (CLOSEWAIT)
expire=13
AUTHEN/START/SENDPASS/CHAP processed
00:03:23: TAC+: periodic timer stopped (queue empty)
| Note |
|

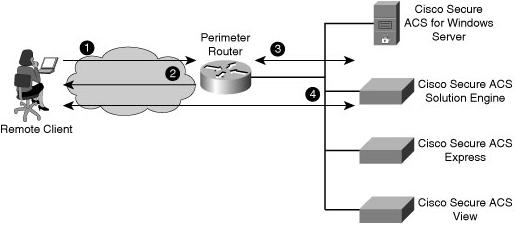
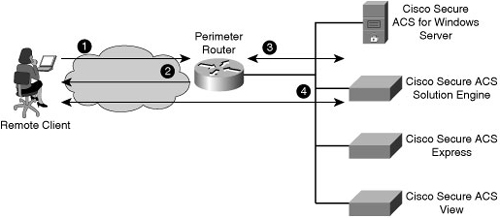


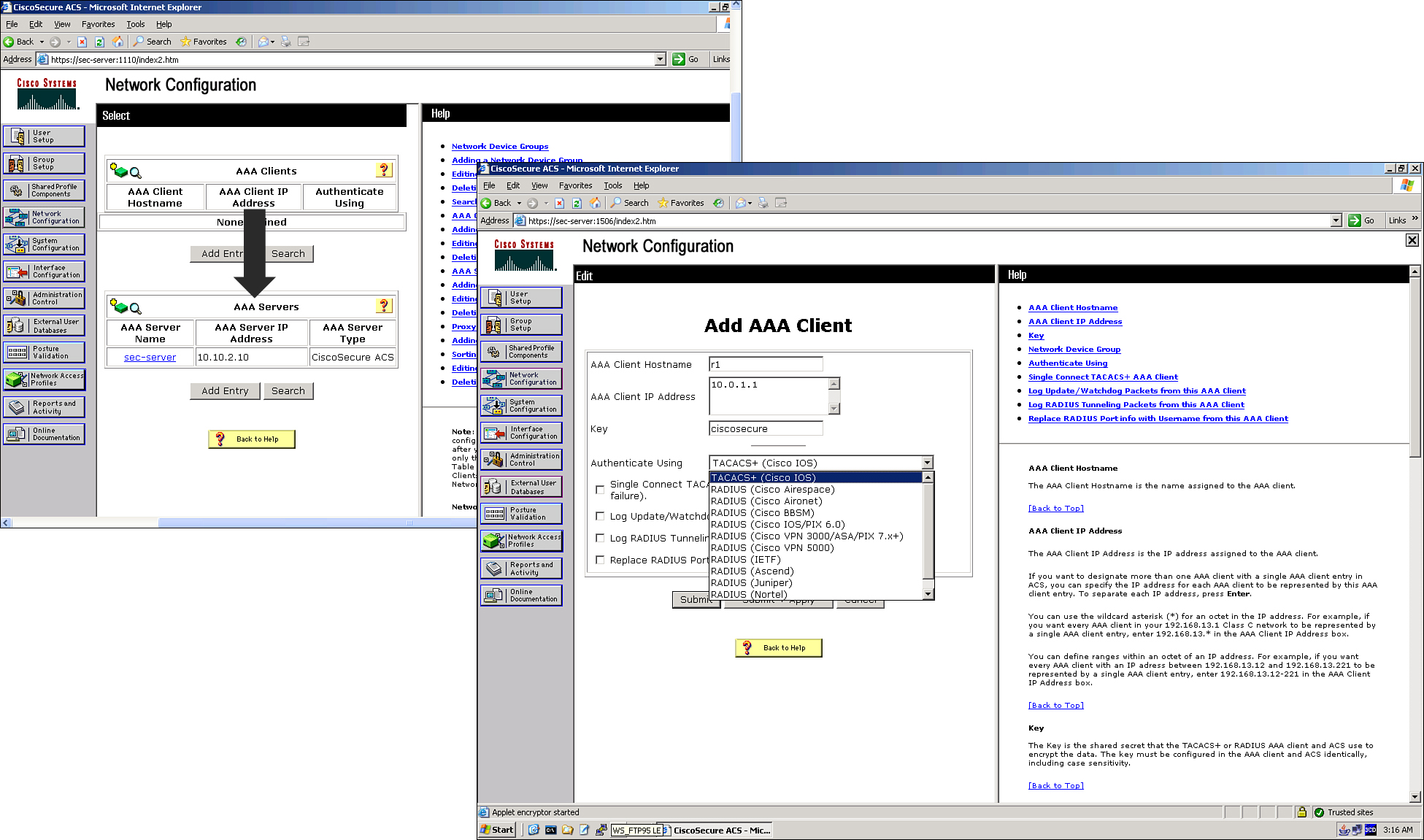
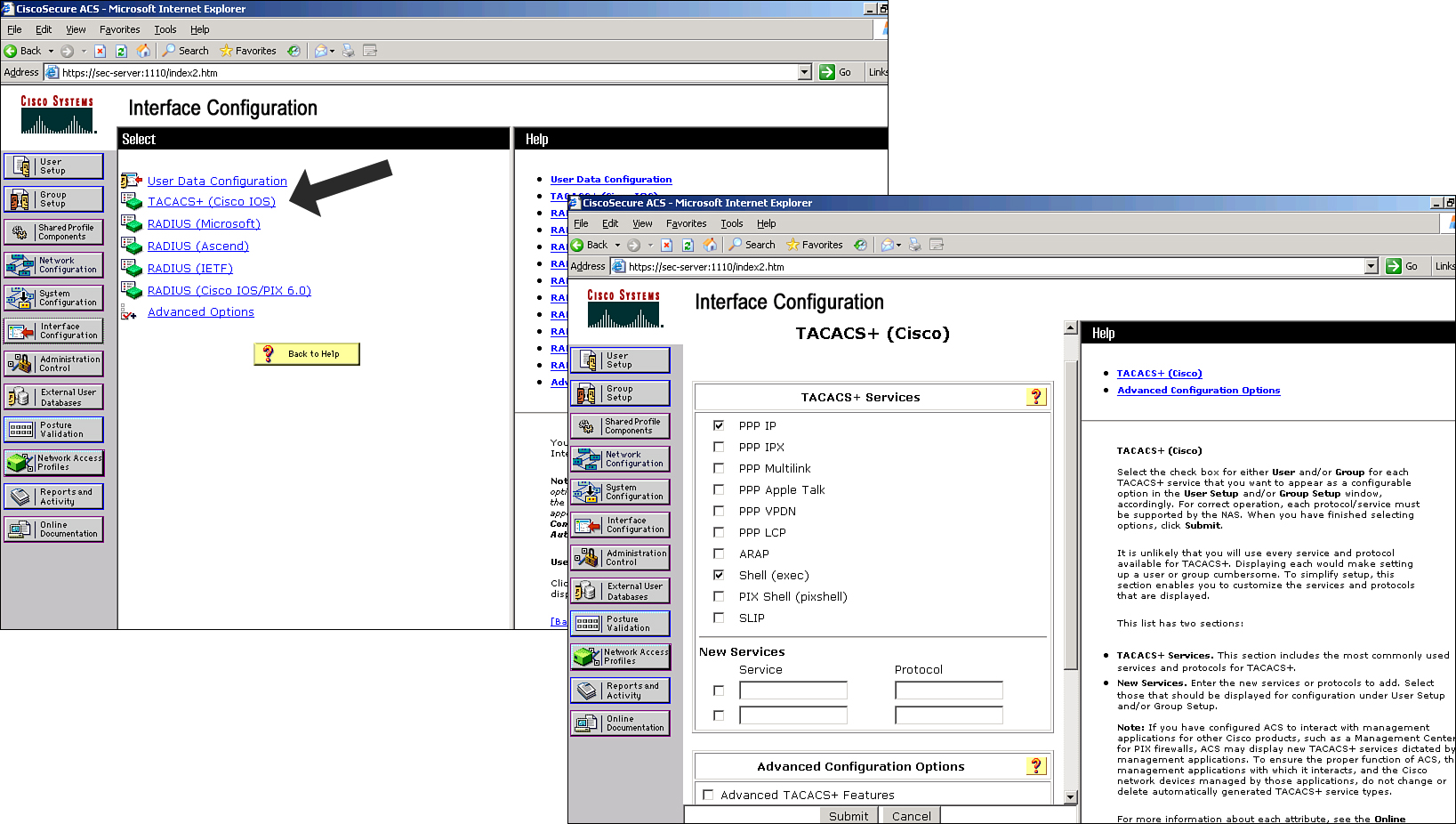
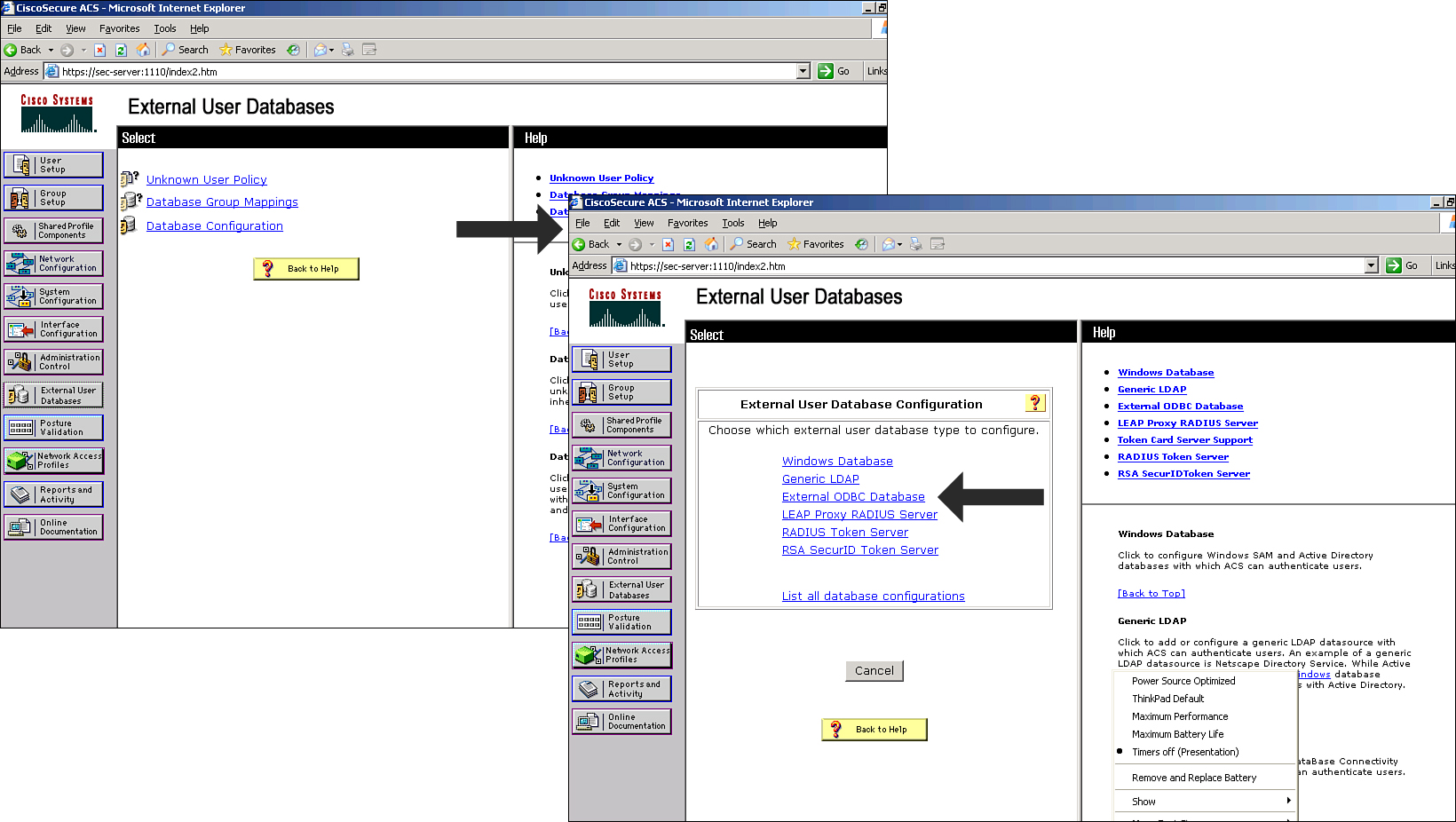
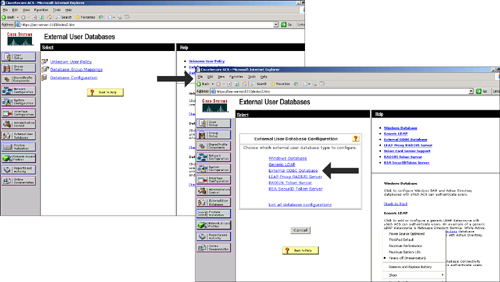
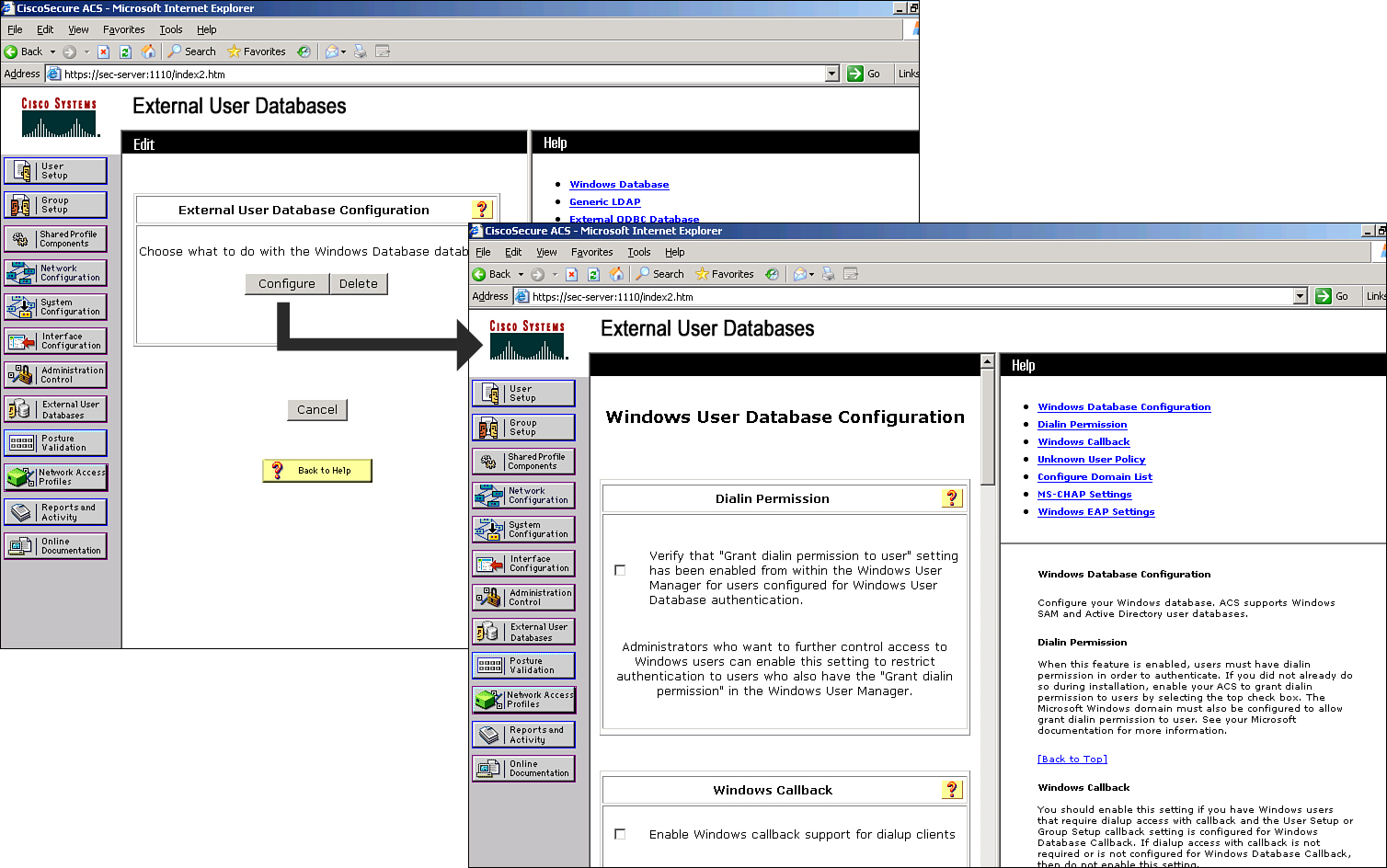
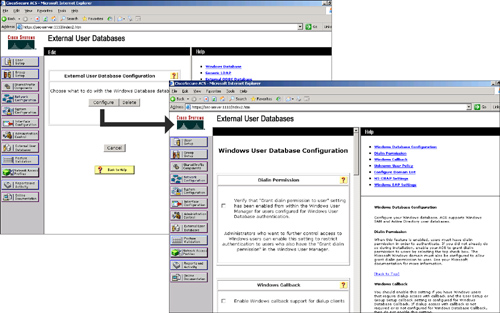
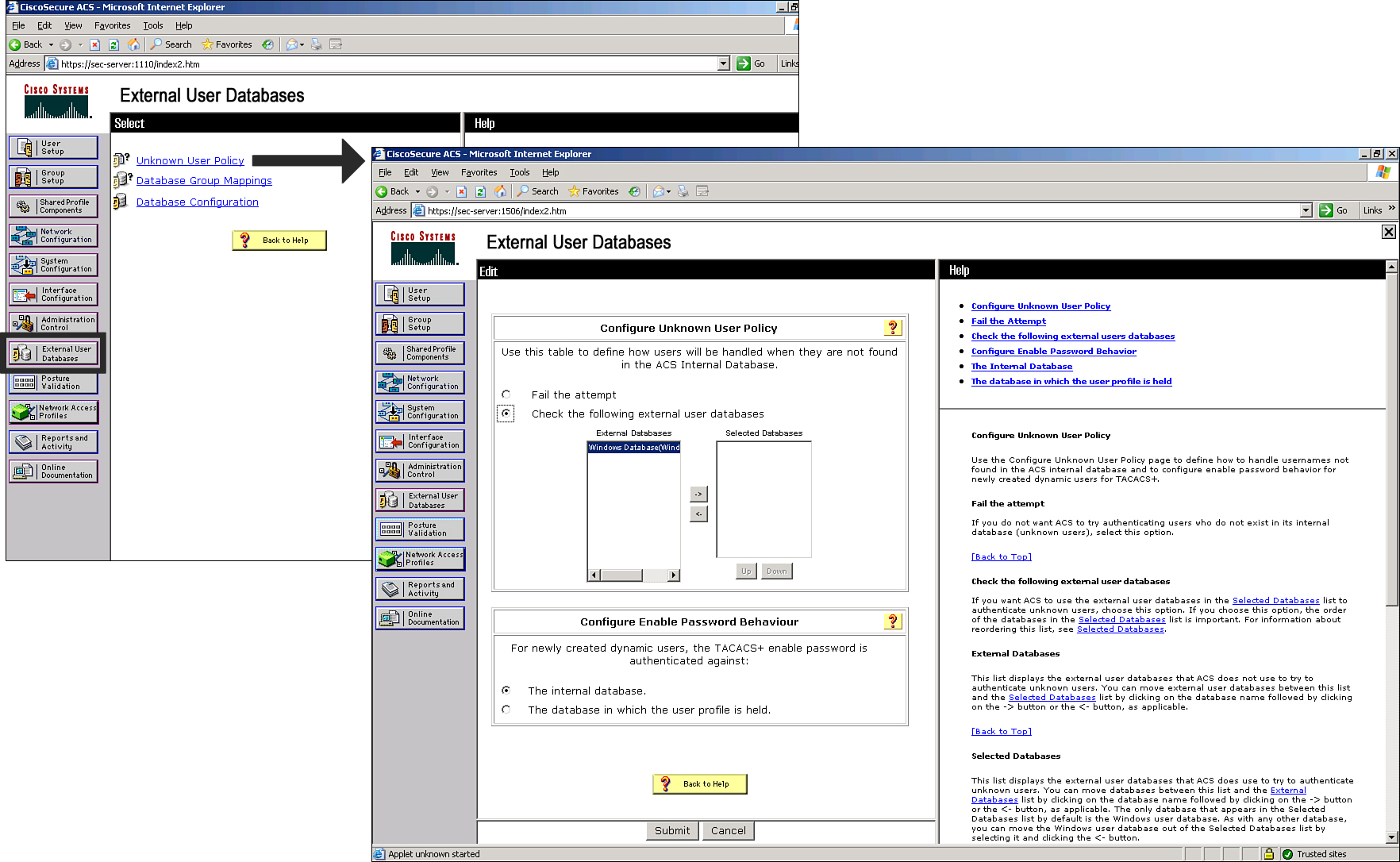
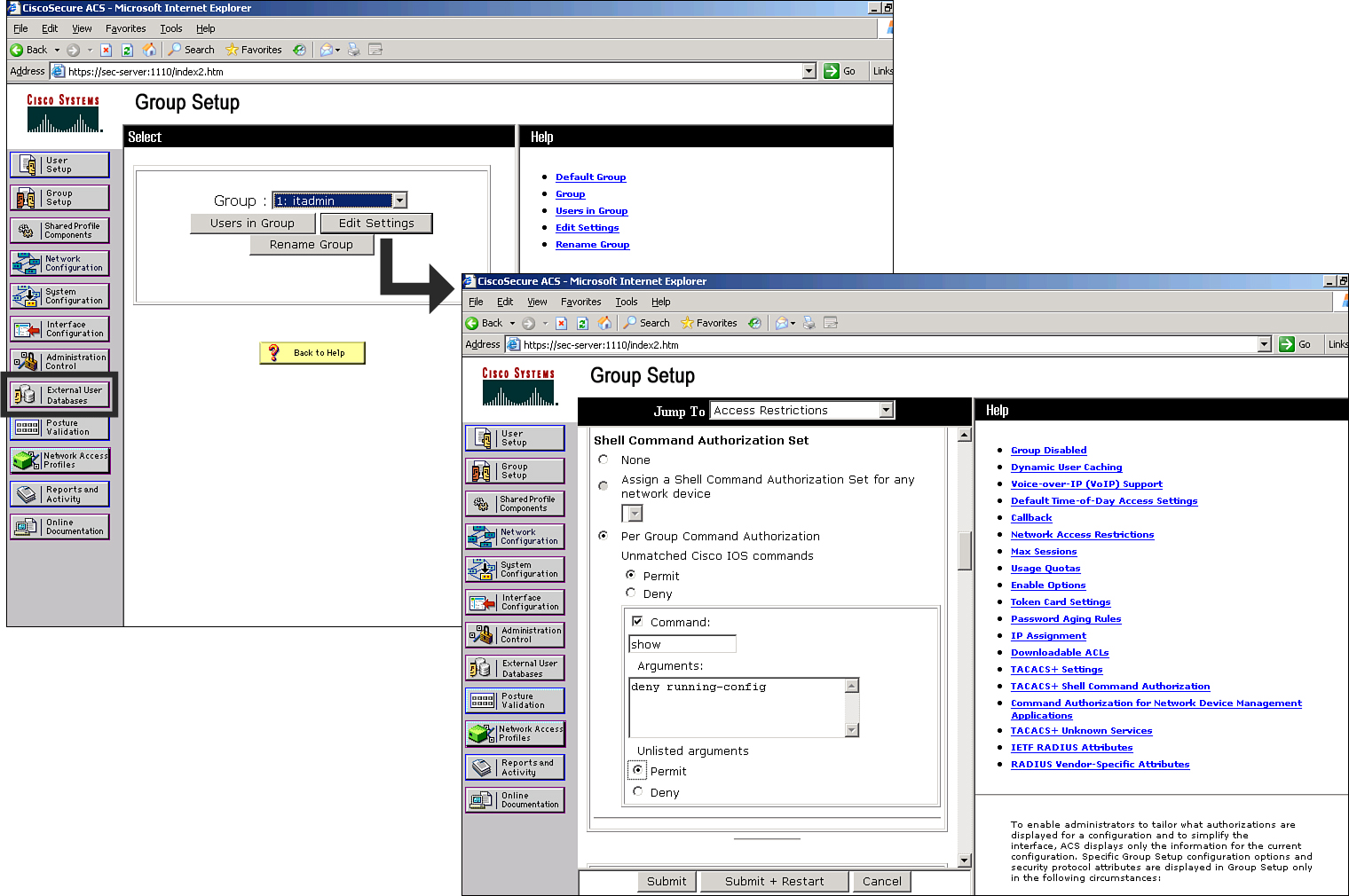
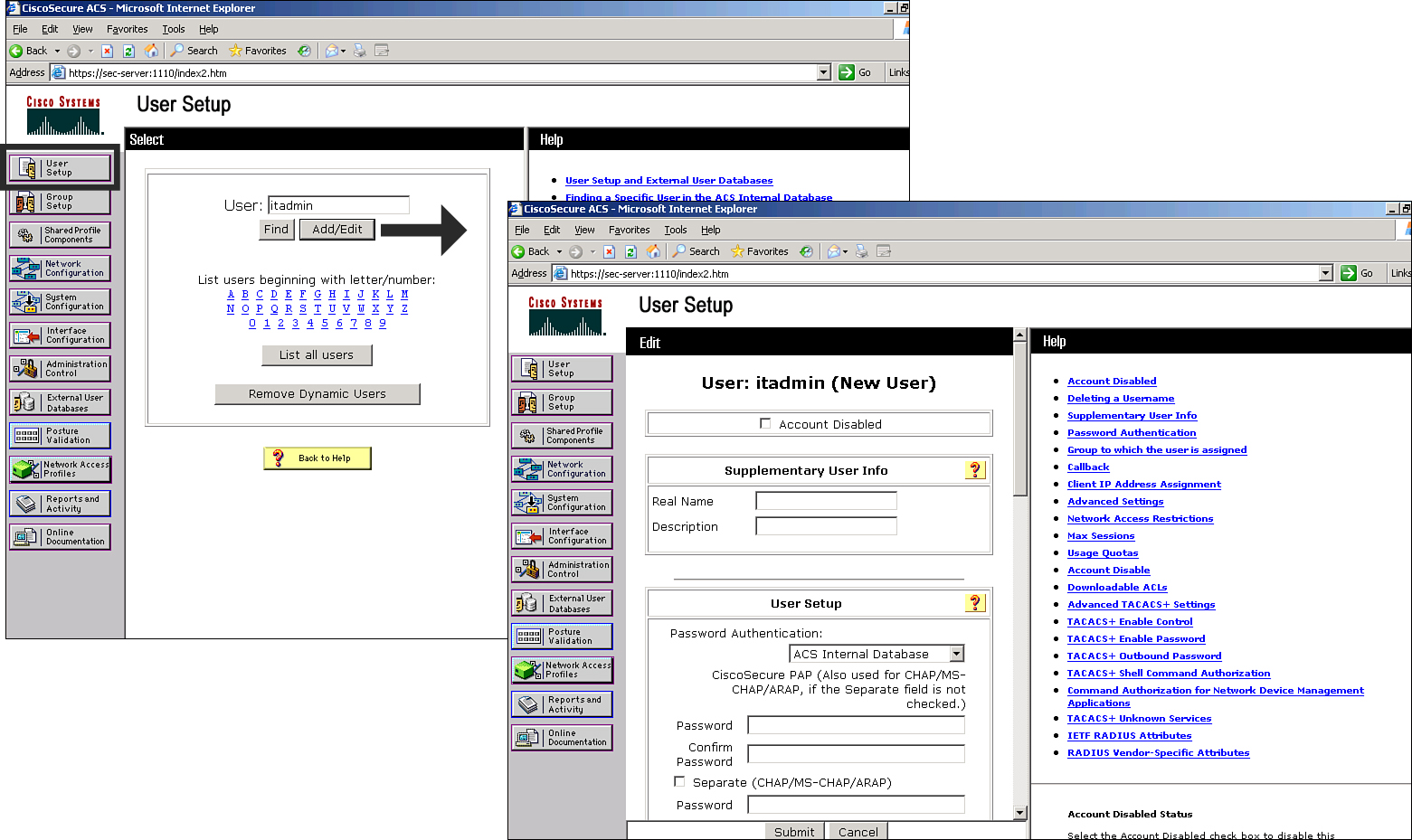
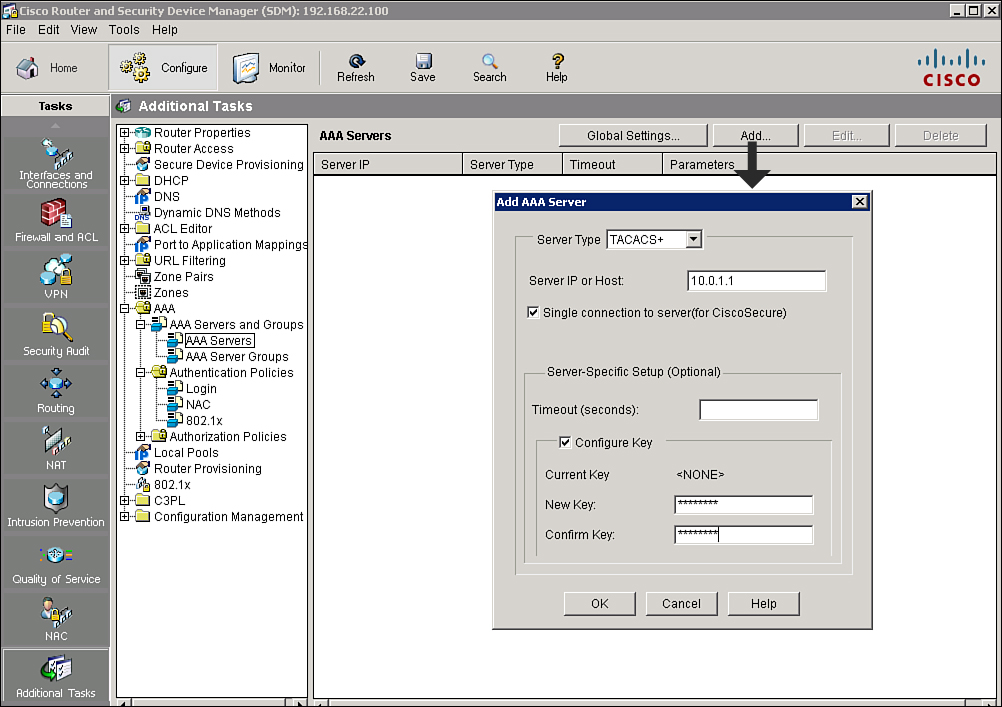
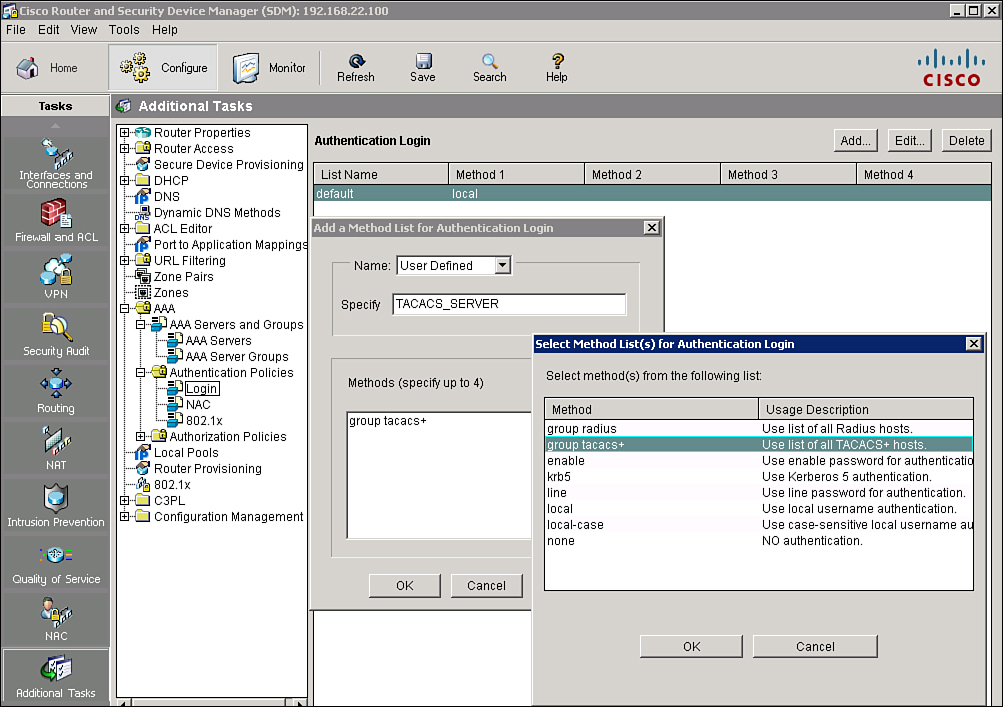
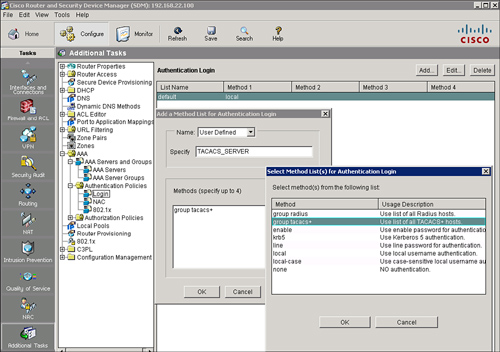
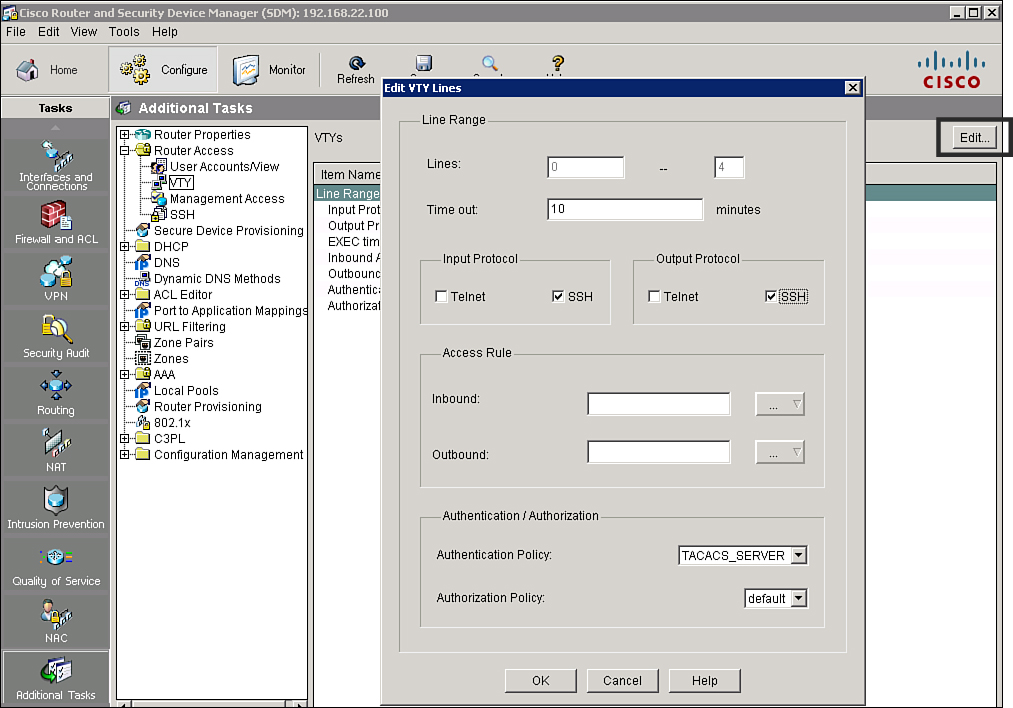
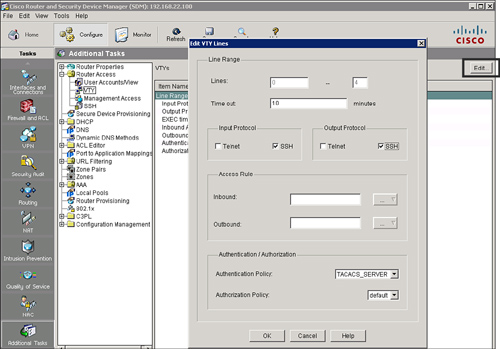
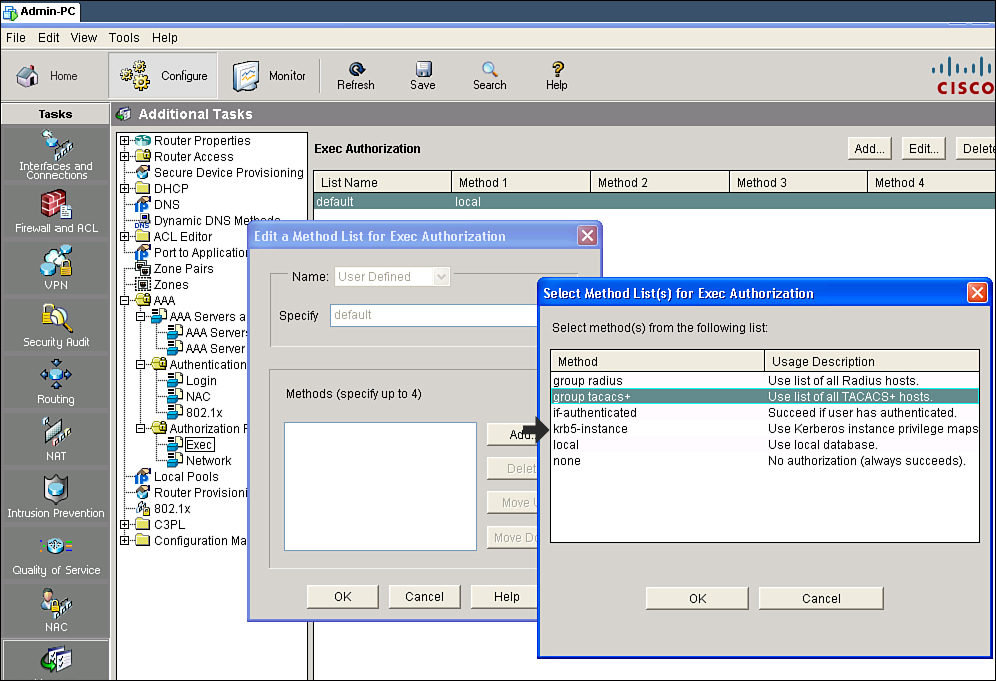
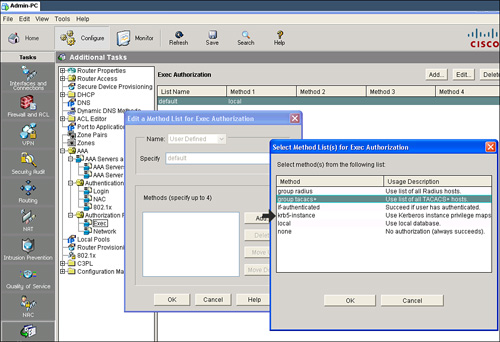
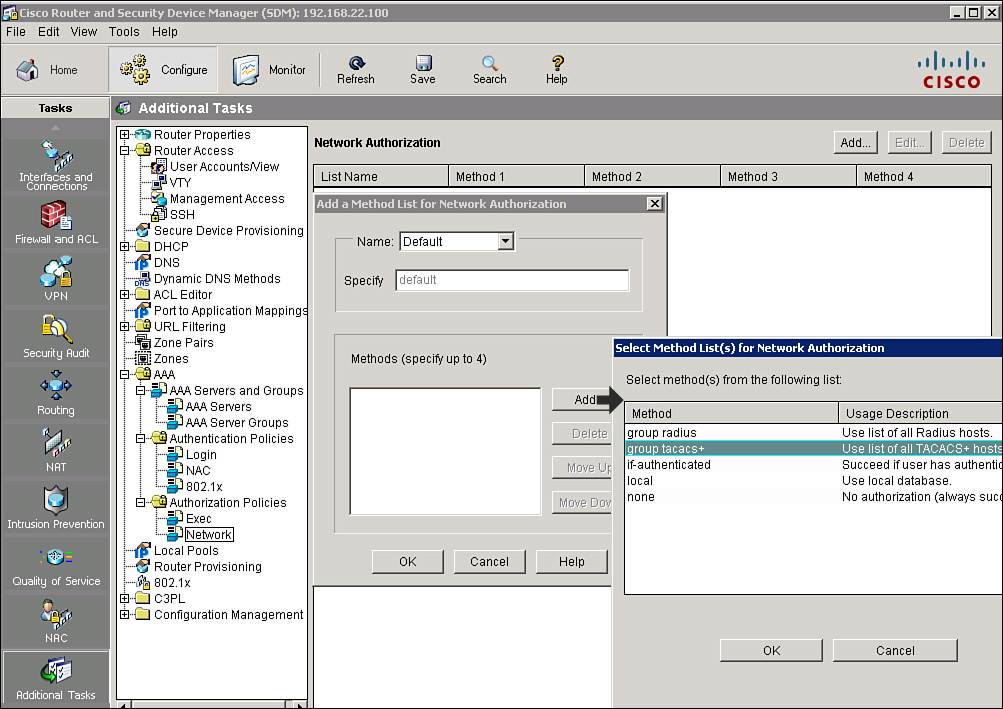
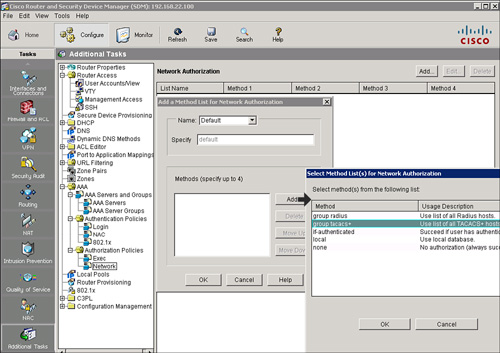
0 comments
Post a Comment