Configuring AAA on a Cisco Router Using the Local Database
![]() AAA is widely supported in Cisco IOS Software as an additional security service available for securing access to network devices and networks. One of the options you have when configuring your network to work with AAA is to use a local username and password database to provide security greater than a simple password. It is likely that smaller organizations will configure AAA to operate locally.
AAA is widely supported in Cisco IOS Software as an additional security service available for securing access to network devices and networks. One of the options you have when configuring your network to work with AAA is to use a local username and password database to provide security greater than a simple password. It is likely that smaller organizations will configure AAA to operate locally.
 Authentication, Authorization, and Accounting
Authentication, Authorization, and Accounting
![]() Access control is the way you control who is allowed access to the access server or router and which services they are allowed to use once they have access. AAA network security services provide the primary framework through which you set up access control on your router. AAA services provide a higher degree of scalability than the line-level and privileged EXEC authentication commands alone.
Access control is the way you control who is allowed access to the access server or router and which services they are allowed to use once they have access. AAA network security services provide the primary framework through which you set up access control on your router. AAA services provide a higher degree of scalability than the line-level and privileged EXEC authentication commands alone.
![]() Unauthorized access in campus, dialup, and Internet environments creates the potential for network intruders to gain access to sensitive network equipment and services. The Cisco AAA architecture enables systematic and scalable access security.
Unauthorized access in campus, dialup, and Internet environments creates the potential for network intruders to gain access to sensitive network equipment and services. The Cisco AAA architecture enables systematic and scalable access security.
![]() Network and administrative access security in the Cisco environment, whether it involves campus, dialup, or IPsec VPN access, is based on a modular architecture that has three functional components:
Network and administrative access security in the Cisco environment, whether it involves campus, dialup, or IPsec VPN access, is based on a modular architecture that has three functional components:
-
 Authentication: Authentication requires users and administrators to prove that they really are who they say they are. Authentication is established using a username and password, challenge and response, token cards, and other methods, such as “I am user student and my password validateme proves it.”
Authentication: Authentication requires users and administrators to prove that they really are who they say they are. Authentication is established using a username and password, challenge and response, token cards, and other methods, such as “I am user student and my password validateme proves it.” -
 Authorization: After authenticating the user and administrator, authorization services decide which resources the user and administrator are allowed to access and which operations the user and administrator are allowed to perform, such as “User student can access host serverXYZ using Telnet.”
Authorization: After authenticating the user and administrator, authorization services decide which resources the user and administrator are allowed to access and which operations the user and administrator are allowed to perform, such as “User student can access host serverXYZ using Telnet.” -
 Accounting and auditing: Accounting records what the users and administrators actually did, what they accessed, and for how long they accessed it. Accounting keeps track of how network resources are used, such as “User student accessed host serverXYZ using Telnet for 15 minutes.”
Accounting and auditing: Accounting records what the users and administrators actually did, what they accessed, and for how long they accessed it. Accounting keeps track of how network resources are used, such as “User student accessed host serverXYZ using Telnet for 15 minutes.”
 Introduction to AAA for Cisco Routers
Introduction to AAA for Cisco Routers
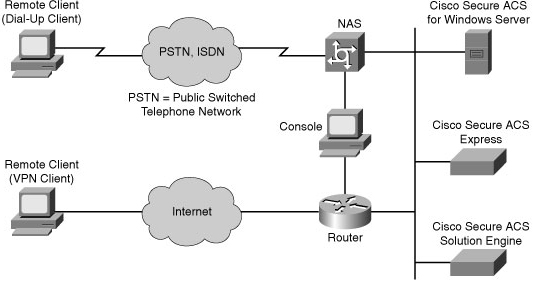
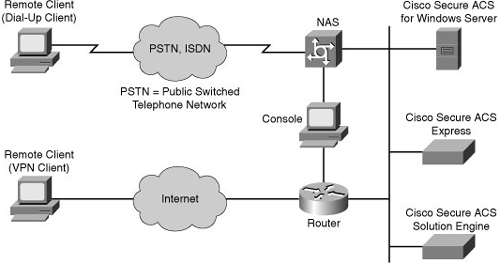
![]() Two examples of AAA implementation include authenticating remote users that are accessing the corporate LAN through dialup or Internet (IPsec VPN) connections as shown in Figure 2-9, and authenticating administrator access to the router console port, auxiliary port, and vty ports.
Two examples of AAA implementation include authenticating remote users that are accessing the corporate LAN through dialup or Internet (IPsec VPN) connections as shown in Figure 2-9, and authenticating administrator access to the router console port, auxiliary port, and vty ports.
![]() Cisco networking products support AAA access control using a local usernames and passwords database or remote security server databases. A local security database is configured in the router for a small group of network users with the username xyz password strongpassword command or, preferably, the username xyz secret strongsecretpassword command. A remote security database is a separate server that provides AAA services for multiple network devices and a large number of network users by running RADIUS or TACACS+ protocols.
Cisco networking products support AAA access control using a local usernames and passwords database or remote security server databases. A local security database is configured in the router for a small group of network users with the username xyz password strongpassword command or, preferably, the username xyz secret strongsecretpassword command. A remote security database is a separate server that provides AAA services for multiple network devices and a large number of network users by running RADIUS or TACACS+ protocols.
![]() Cisco provides four ways to implement AAA services for Cisco routers:
Cisco provides four ways to implement AAA services for Cisco routers:
-
 Self-contained AAA: AAA services can be self-contained in the router or network access server (NAS) itself. This form of authentication is also known as local authentication.
Self-contained AAA: AAA services can be self-contained in the router or network access server (NAS) itself. This form of authentication is also known as local authentication. -
 Cisco Secure Access Control Server (ACS) for Microsoft Windows Server: AAA services on the router or NAS contact an external Cisco Secure ACS for Microsoft Windows system for user and administrator authentication.
Cisco Secure Access Control Server (ACS) for Microsoft Windows Server: AAA services on the router or NAS contact an external Cisco Secure ACS for Microsoft Windows system for user and administrator authentication. -
 Cisco Secure ACS Express: This is an entry-level RADIUS and TACACS+ AAA server appliance. AAA services on the router or NAS contact an external Cisco Secure ACS Express device for user and administrator authentication. Cisco ACS Express is available as a one rack unit (RU), security-hardened appliance with a preinstalled Cisco Secure ACS Express license. Cisco ACS Express supports a maximum of 50 AAA clients and 350 unique user logons in a 24-hour period.
Cisco Secure ACS Express: This is an entry-level RADIUS and TACACS+ AAA server appliance. AAA services on the router or NAS contact an external Cisco Secure ACS Express device for user and administrator authentication. Cisco ACS Express is available as a one rack unit (RU), security-hardened appliance with a preinstalled Cisco Secure ACS Express license. Cisco ACS Express supports a maximum of 50 AAA clients and 350 unique user logons in a 24-hour period. -
 Cisco Secure ACS Solution Engine: AAA services on the router or NAS contact an external Cisco Secure ACS Solution Engine for user and administrator authentication.
Cisco Secure ACS Solution Engine: AAA services on the router or NAS contact an external Cisco Secure ACS Solution Engine for user and administrator authentication.
 Using Local Services to Authenticate Router Access
Using Local Services to Authenticate Router Access
![]() If you have one or two NAS devices or routers that provide access to your network for a limited number of users, you can store username and password security information locally on the Cisco NAS devices or routers. This is referred to as local authentication on a local security database. The following are local authentication characteristics:
If you have one or two NAS devices or routers that provide access to your network for a limited number of users, you can store username and password security information locally on the Cisco NAS devices or routers. This is referred to as local authentication on a local security database. The following are local authentication characteristics:
-
 Used for small networks
Used for small networks -
 Stores usernames and passwords in the Cisco router or Cisco NAS
Stores usernames and passwords in the Cisco router or Cisco NAS -
 Users authenticate against the local security database in the Cisco router or Cisco NAS
Users authenticate against the local security database in the Cisco router or Cisco NAS -
 Does not require an external database
Does not require an external database
![]() The system administrator must populate the local security database by specifying username and password profiles for each user that might log in.
The system administrator must populate the local security database by specifying username and password profiles for each user that might log in.
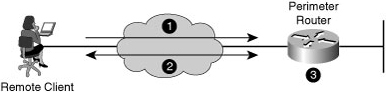
![]() Figure 2-10 shows how local authentication typically works.
Figure 2-10 shows how local authentication typically works.
-
 The router prompts the user for a username and password.
The router prompts the user for a username and password. -
 The router authenticates the username and password in the local database. The user is authorized to access the network based on information in the local database.
The router authenticates the username and password in the local database. The user is authorized to access the network based on information in the local database.
Authenticating Router Access
![]() You can use AAA to secure two different types of router access mode. The mode refers to the format of the packets that are requesting AAA services:
You can use AAA to secure two different types of router access mode. The mode refers to the format of the packets that are requesting AAA services:
-
 Character mode: A user is sending a request to establish an EXEC mode process with the router, for administrative purposes.
Character mode: A user is sending a request to establish an EXEC mode process with the router, for administrative purposes. -
 Packet mode: A user is sending a request to establish a connection through the router with a device on the network.
Packet mode: A user is sending a request to establish a connection through the router with a device on the network.
![]() With the exception of accounting commands, all the AAA commands apply to both character mode and packet mode.
With the exception of accounting commands, all the AAA commands apply to both character mode and packet mode.
![]() For a truly secure network, you must configure the router to secure administrative access and remote LAN network access using AAA services.
For a truly secure network, you must configure the router to secure administrative access and remote LAN network access using AAA services.
![]() Table 2-10 compares the router access modes, port types, and AAA command elements.
Table 2-10 compares the router access modes, port types, and AAA command elements.
|
|
|
|
|
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
Configuring Local Database Authentication Using AAA
![]() To configure AAA services to authenticate administrator access (character mode access) or network access (packet mode), follow these general steps:
To configure AAA services to authenticate administrator access (character mode access) or network access (packet mode), follow these general steps:
-
 Add usernames and passwords to the local router database for users who need administrative access to the router.
Add usernames and passwords to the local router database for users who need administrative access to the router. -
 Enable AAA globally on the router, or confirm that it is already enabled.
Enable AAA globally on the router, or confirm that it is already enabled. -
 Configure AAA/parameters on the router.
Configure AAA/parameters on the router. -
 Confirm and troubleshoot the AAA configuration.
Confirm and troubleshoot the AAA configuration.
Configuring User Accounts Using Cisco SDM
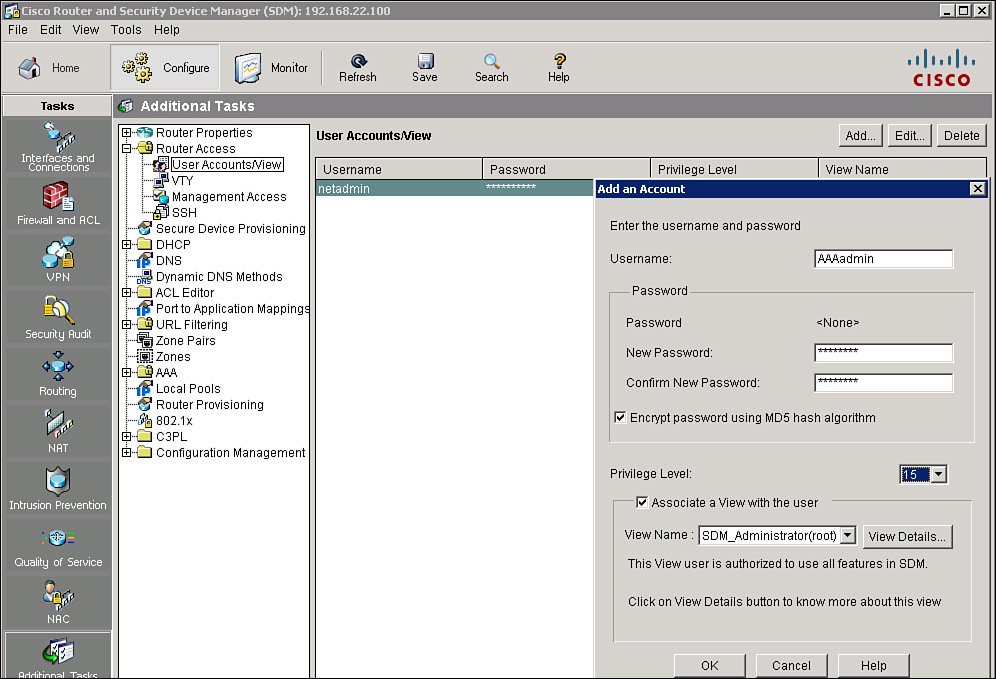
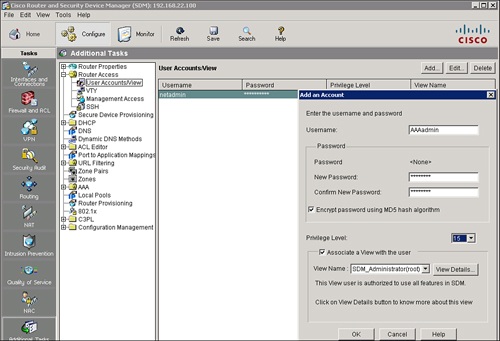
![]() The first step to configure AAA services for local authentication is to create users. Figure 2-11 shows the steps to use with Cisco SDM to create a user account in the local router database:
The first step to configure AAA services for local authentication is to create users. Figure 2-11 shows the steps to use with Cisco SDM to create a user account in the local router database:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Cisco SDM will generate the following CLI command:
Cisco SDM will generate the following CLI command:
 username AAAadmin privilege 15 secret 5 $1$f16u$uKOO6J/UnojZ0bCEzgnQi1 view root
username AAAadmin privilege 15 secret 5 $1$f16u$uKOO6J/UnojZ0bCEzgnQi1 view rootEnabling and Disabling AAA Using Cisco SDM
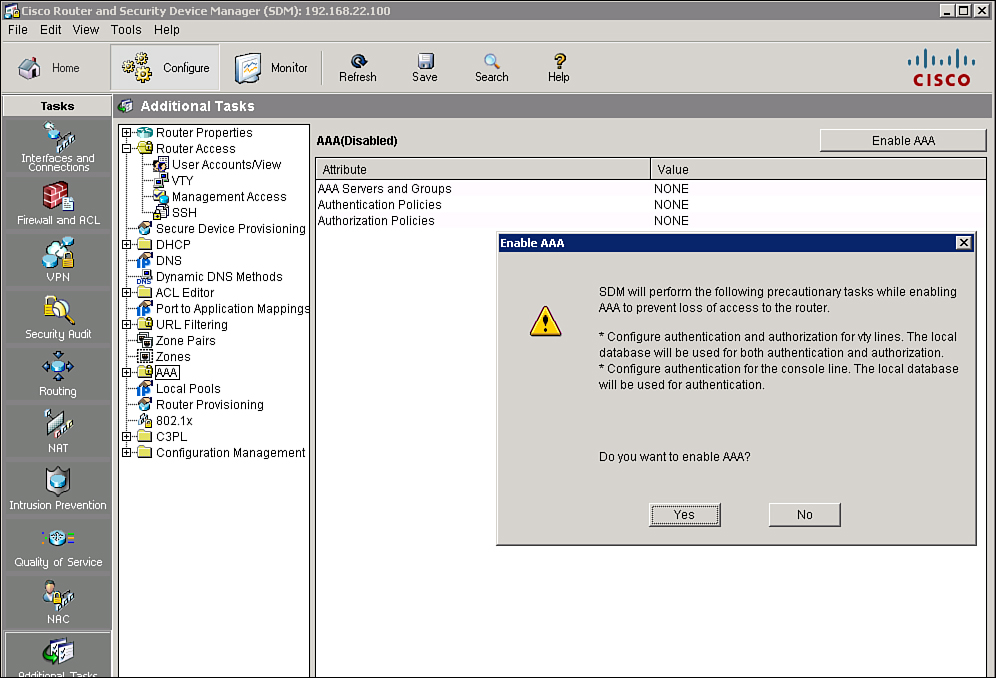
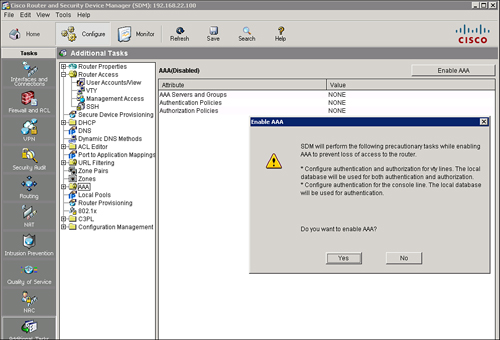
![]() The next step in configuring AAA is to make sure AAA is enabled. To verify the AAA configuration and to enable or disable AAA, choose Configure > Additional Tasks > AAA, as shown in Figure 2-12. AAA is enabled by default in Cisco SDM. If you click Disable, Cisco SDM displays a message telling you that it will make configuration changes to ensure that the router can be accessed after AAA is disabled. Disabling AAA will prevent you from configuring your router as an Easy VPN server, and will prevent you from associating user accounts with CLI views.
The next step in configuring AAA is to make sure AAA is enabled. To verify the AAA configuration and to enable or disable AAA, choose Configure > Additional Tasks > AAA, as shown in Figure 2-12. AAA is enabled by default in Cisco SDM. If you click Disable, Cisco SDM displays a message telling you that it will make configuration changes to ensure that the router can be accessed after AAA is disabled. Disabling AAA will prevent you from configuring your router as an Easy VPN server, and will prevent you from associating user accounts with CLI views.
![]() In the CLI, use the global configuration command aaa new-model to enable AAA. Use the no form of this command to disable AAA.
In the CLI, use the global configuration command aaa new-model to enable AAA. Use the no form of this command to disable AAA.
Configuring AAA Authentication Using Cisco SDM
![]() A method list is a sequential list of authentication methods to query to authenticate a user. Method lists enable you to designate one or more security protocols to be used for authentication, thus ensuring a backup system for authentication in case the initial method fails.
A method list is a sequential list of authentication methods to query to authenticate a user. Method lists enable you to designate one or more security protocols to be used for authentication, thus ensuring a backup system for authentication in case the initial method fails.
![]() When you first enable AAA, there is a default method list named default, which is automatically applied to all interfaces and lines, but which has no authentication methods defined. To configure AAA authentication, you must first either define a list of authentication methods for the default method, or configure your own named method lists and apply them to interfaces or lines. For flexibility, you can apply different method lists to different interfaces and lines. If an interface or line has a nondefault method list applied to it, that method overrides the default method list.
When you first enable AAA, there is a default method list named default, which is automatically applied to all interfaces and lines, but which has no authentication methods defined. To configure AAA authentication, you must first either define a list of authentication methods for the default method, or configure your own named method lists and apply them to interfaces or lines. For flexibility, you can apply different method lists to different interfaces and lines. If an interface or line has a nondefault method list applied to it, that method overrides the default method list.
![]() Cisco IOS Software uses the first method listed to authenticate users. If that method fails to respond, the Cisco IOS Software selects the next authentication method listed in the method list. This process continues until there is successful communication with a listed authentication method or until all methods defined in the method list have been exhausted.
Cisco IOS Software uses the first method listed to authenticate users. If that method fails to respond, the Cisco IOS Software selects the next authentication method listed in the method list. This process continues until there is successful communication with a listed authentication method or until all methods defined in the method list have been exhausted.
![]() It is important to note that the Cisco IOS Software attempts authentication with the next listed authentication method only when there is no response from the previous method. If authentication fails at any point in this cycle (meaning that the security server or local username database responds by denying the user access), the authentication process stops and no other authentication methods are attempted.
It is important to note that the Cisco IOS Software attempts authentication with the next listed authentication method only when there is no response from the previous method. If authentication fails at any point in this cycle (meaning that the security server or local username database responds by denying the user access), the authentication process stops and no other authentication methods are attempted.
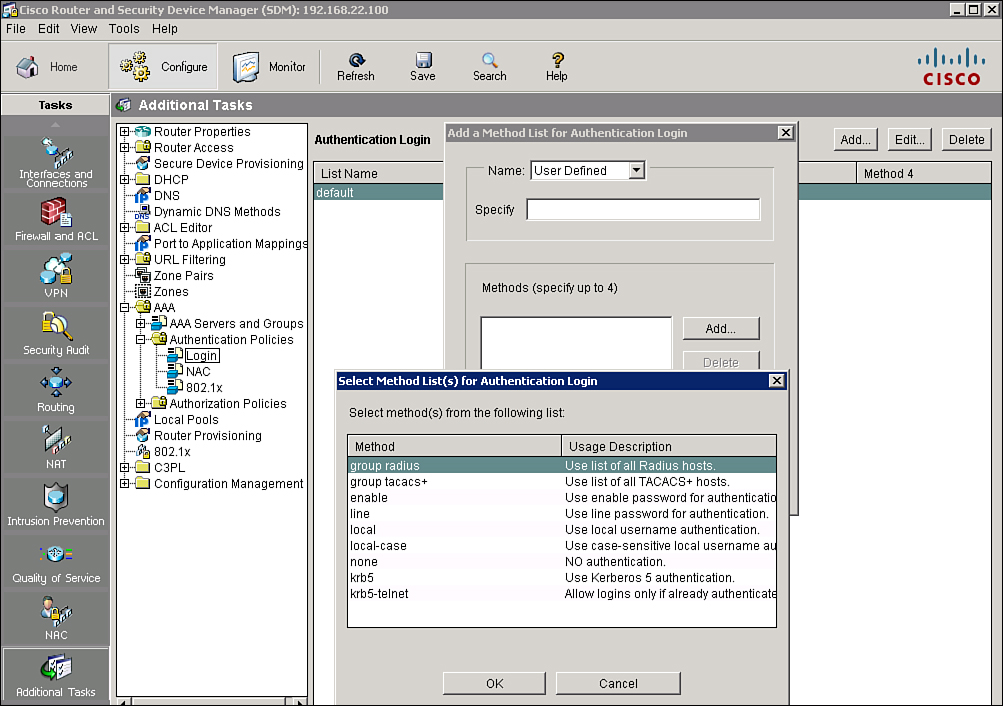
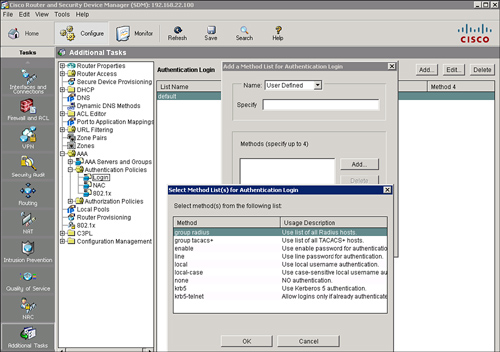
![]() Follow these steps, shown in Figure 2-13, to configure the default method list for login authentication using the local database:
Follow these steps, shown in Figure 2-13, to configure the default method list for login authentication using the local database:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The Cisco SDM will generate the following CLI command:
The Cisco SDM will generate the following CLI command:
aaa authentication login default local
| Note |
|
Additional AAA CLI Commands
![]() To further secure administrative access to the router, you can specify the maximum number of failed AAA login attempts that can occur before an account is locked out. Currently, you can configure this option only from the CLI.
To further secure administrative access to the router, you can specify the maximum number of failed AAA login attempts that can occur before an account is locked out. Currently, you can configure this option only from the CLI.
![]() To specify the maximum number of unsuccessful authentication attempts before a user is locked out, use the aaa local authentication attempts max-fail command in global configuration mode. To remove the number of unsuccessful attempts that was set, use the no form of this command. The complete syntax for this command is as follows:
To specify the maximum number of unsuccessful authentication attempts before a user is locked out, use the aaa local authentication attempts max-fail command in global configuration mode. To remove the number of unsuccessful attempts that was set, use the no form of this command. The complete syntax for this command is as follows:
aaa local authentication attempts max-fail number-of-unsuccessful-attempts
![]() To display a list of all locked-out users, use the show aaa local user lockout command in privileged EXEC mode.
To display a list of all locked-out users, use the show aaa local user lockout command in privileged EXEC mode.
![]() Example 2-23 shows that user1 is locked out.
Example 2-23 shows that user1 is locked out.
R1# show aaa local user lockout
Local-user Lock time
user1 04:28:49 UTC Sat Dec 15 2007
![]() Use the clear aaa local user lockout command in privileged EXEC mode to unlock a locked-out user. The complete syntax for this command is clear aaa local user lockout {username username | all}. To specify a single user to unlock, specify the username using the username parameter. To unlock all the users, use the all keyword. You might also consider using the clear aaa local user fail-attempts username username or the clear aaa local user fail-attempts all commands for cases in which you need to clear already logged unsuccessful attempts after the user configuration was changed.
Use the clear aaa local user lockout command in privileged EXEC mode to unlock a locked-out user. The complete syntax for this command is clear aaa local user lockout {username username | all}. To specify a single user to unlock, specify the username using the username parameter. To unlock all the users, use the all keyword. You might also consider using the clear aaa local user fail-attempts username username or the clear aaa local user fail-attempts all commands for cases in which you need to clear already logged unsuccessful attempts after the user configuration was changed.
| Note |
|
![]() When a user logs in to a Cisco router and uses AAA, a unique ID is assigned to the session. Throughout the life of the session, various attributes that are related to the session are collected and stored internally within the AAA database. These attributes can include the IP address of the user, the protocol that is used to access the router (such as PPP or SLIP), the speed of the connection, and the number of packets or bytes that are received or transmitted.
When a user logs in to a Cisco router and uses AAA, a unique ID is assigned to the session. Throughout the life of the session, various attributes that are related to the session are collected and stored internally within the AAA database. These attributes can include the IP address of the user, the protocol that is used to access the router (such as PPP or SLIP), the speed of the connection, and the number of packets or bytes that are received or transmitted.
![]() To display the attributes that are collected for a AAA session, use the show aaa user {all | unique id} command in privileged EXEC mode.
To display the attributes that are collected for a AAA session, use the show aaa user {all | unique id} command in privileged EXEC mode.
| Note |
|
![]() As shown in Example 2-24, you can use the show aaa sessions command to show the unique ID of a session.
As shown in Example 2-24, you can use the show aaa sessions command to show the unique ID of a session.
R1# show aaa sessions
Total sessions since last reload: 4
Session Id: 1
Unique Id: 175
User Name: tecteam
IP Address: 10.30.30.2
Idle Time: 0
CT Call Handle: 0
Confirming and Troubleshooting the AAA Configuration
![]() To configure AAA services to authenticate administrator access (character mode access) or network access (packet mode), follow these general steps:
To configure AAA services to authenticate administrator access (character mode access) or network access (packet mode), follow these general steps:
-
 Add usernames and passwords to the local router database for users that need administrative access to the router.
Add usernames and passwords to the local router database for users that need administrative access to the router. -
 Enable AAA globally on the router, or confirm that it is already enabled.
Enable AAA globally on the router, or confirm that it is already enabled. -
 Configure AAA/parameters on the router.
Configure AAA/parameters on the router. -
 Confirm and troubleshoot the AAA configuration.
Confirm and troubleshoot the AAA configuration.
![]() Example 2-25 shows an example of what the running configuration would look like after configuring AAA for local authentication using Cisco SDM and the CLI.
Example 2-25 shows an example of what the running configuration would look like after configuring AAA for local authentication using Cisco SDM and the CLI.
aaa new-model
aaa local authentication attempts max-fail 10
!
!
aaa authentication login default local
enable secret 5 $1$x1EE$33AXd2VTVvhbWL0A37tQ3.
enable password 7 15141905172924
!
username admin1 password 7 14161606050A7B7974786B
username admin2 secret 5 $1$ErWl$b5rDNK7Y5RHkxX/Ks7Hr00
username AAAadmin privilege 15 view root secret 5 $1$0GGC$1Y.WBhh7UQso8cJSkvv2N0
!
![]() To display information on AAA authentication, use the debug aaa authentication command in privileged EXEC command mode, as shown in Example 2-26. Use the no debug aaa authentication form of the command to disable this debug mode. Example 2-26 shows the debug output for a successful AAA authentication using a local database.
To display information on AAA authentication, use the debug aaa authentication command in privileged EXEC command mode, as shown in Example 2-26. Use the no debug aaa authentication form of the command to disable this debug mode. Example 2-26 shows the debug output for a successful AAA authentication using a local database.
R1# debug aaa authentication
113123: Feb 4 10:11:19.305 CST: AAA/MEMORY: create_user (0x619C4940) user=''
ruser='' port='tty1' rem_addr='async/81560' authen_type=ASCII service=LOGIN priv=1
113124: Feb 4 10:11:19.305 CST: AAA/AUTHEN/START (2784097690): port='tty1' list=''
action=LOGIN service=LOGIN
113125: Feb 4 10:11:19.305 CST: AAA/AUTHEN/START (2784097690): using "default" list
113126: Feb 4 10:11:19.305 CST: AAA/AUTHEN/START (2784097690): Method=LOCAL
113127: Feb 4 10:11:19.305 CST: AAA/AUTHEN (2784097690): status = GETUSER
113128: Feb 4 10:11:26.305 CST: AAA/AUTHEN/CONT (2784097690): continue_login
(user='(undef)')
113129: Feb 4 10:11:26.305 CST: AAA/AUTHEN (2784097690): status = GETUSER
113130: Feb 4 10:11:26.305 CST: AAA/AUTHEN/CONT (2784097690): Method=LOCAL
113131: Feb 4 10:11:26.305 CST: AAA/AUTHEN (2784097690): status = GETPASS
113132: Feb 4 10:11:28.145 CST: AAA/AUTHEN/CONT (2784097690): continue_login
(user='diallocal')
113133: Feb 4 10:11:28.145 CST: AAA/AUTHEN (2784097690): status = GETPASS
113134: Feb 4 10:11:28.145 CST: AAA/AUTHEN/CONT (2784097690): Method=LOCAL
113135: Feb 4 10:11:28.145 CST: AAA/AUTHEN (2784097690): status = PASS

0 comments
Post a Comment