Securing the Cisco IOS Image and Configuration Files
![]() The Cisco IOS resilient configuration feature enables a router to secure and maintain a working copy of the running image and configuration so that those files can withstand malicious attempts to erase the contents of persistent storage (NVRAM and flash storage).
The Cisco IOS resilient configuration feature enables a router to secure and maintain a working copy of the running image and configuration so that those files can withstand malicious attempts to erase the contents of persistent storage (NVRAM and flash storage).
![]() A great challenge for network operators is the total downtime that is experienced after a router has been compromised and its operating software and configuration data are erased from its persistent storage. The operator must retrieve an archived copy (hopefully one is available) of the configuration and a working Cisco IOS image to restore the router. Recovery must then be performed for each affected router, adding to the total network downtime.
A great challenge for network operators is the total downtime that is experienced after a router has been compromised and its operating software and configuration data are erased from its persistent storage. The operator must retrieve an archived copy (hopefully one is available) of the configuration and a working Cisco IOS image to restore the router. Recovery must then be performed for each affected router, adding to the total network downtime.
![]() The Cisco IOS resilient configuration feature is intended to speed up the recovery process. This feature maintains a secure working copy of the router image and the startup configuration at all times. The user cannot remove these secure files. This set of Cisco IOS image and router running configuration files is referred to as the bootset.
The Cisco IOS resilient configuration feature is intended to speed up the recovery process. This feature maintains a secure working copy of the router image and the startup configuration at all times. The user cannot remove these secure files. This set of Cisco IOS image and router running configuration files is referred to as the bootset.
![]() The command sequence to save a primary bootset to a secure archive in persistent storage is as follows:
The command sequence to save a primary bootset to a secure archive in persistent storage is as follows:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Table 2-6 describes the key commands that are required to secure the Cisco IOS image and running configuration using the secure boot-image command:
Table 2-6 describes the key commands that are required to secure the Cisco IOS image and running configuration using the secure boot-image command:
R1(config)# secure boot-image
R1(config)# secure boot-config
|
|
|
|---|---|
|
|
|
|
|
|
![]() Secured files do not appear in the output of a dir command that is issued from an executive shell because the Cisco IOS file system prevents the secure files in a directory from being listed. ROM monitor mode does not have any such restriction and can list and boot secured files. Because the running image and running configuration archives are not visible in the output from the Cisco IOS command dir, use the show secure bootset command to verify the archive existence.
Secured files do not appear in the output of a dir command that is issued from an executive shell because the Cisco IOS file system prevents the secure files in a directory from being listed. ROM monitor mode does not have any such restriction and can list and boot secured files. Because the running image and running configuration archives are not visible in the output from the Cisco IOS command dir, use the show secure bootset command to verify the archive existence.
![]() Example 2-16 shows an example of the show secure bootset command output. This command is important to verify that the Cisco IOS image and configuration files have been properly backed up and secured.
Example 2-16 shows an example of the show secure bootset command output. This command is important to verify that the Cisco IOS image and configuration files have been properly backed up and secured.
R1# show secure bootset
IOS resilience router id FHK085031MD
IOS image resilience version 12.3 activated at 05:00:59 UTC Fri Feb 10 2006
Secure archive flash:c1841-advsecurityk9-mz.123-14.T1.bin type is image (elf) []
file size is 17533860 bytes, run size is 17699528 bytes
Runnable image, entry point 0x8000F000, run from ram
IOS configuration resilience version 12.3 activated at 05:01:02 UTC Fri Feb 10 2
006
Secure archive flash:.runcfg-20060210-050102.ar type is config
configuration archive size 4014 bytes
Configuring Enhanced Support for Virtual Logins
![]() The Cisco IOS login enhancements feature allows you to better secure your Cisco IOS devices when creating a virtual connection, such as Telnet, SSH, or HTTP. In addition, you can slow down dictionary attacks and thereby protect your router from a possible DoS attack.
The Cisco IOS login enhancements feature allows you to better secure your Cisco IOS devices when creating a virtual connection, such as Telnet, SSH, or HTTP. In addition, you can slow down dictionary attacks and thereby protect your router from a possible DoS attack.
![]() To better configure security when opening a virtual login connection, you should configure the login process with the following:
To better configure security when opening a virtual login connection, you should configure the login process with the following:
-
 Delays between successive login attempts
Delays between successive login attempts -
 Login shutdown if DoS attacks are suspected
Login shutdown if DoS attacks are suspected -
 Generation of system logging messages for login detection
Generation of system logging messages for login detection
 Delays Between Successive Login Attempts
Delays Between Successive Login Attempts
![]() A Cisco IOS device can accept virtual connections as fast as it can process these connections. Introducing a delay between login attempts helps to protect your router from a possible dictionary attack. You can enable delays in one of the following ways:
A Cisco IOS device can accept virtual connections as fast as it can process these connections. Introducing a delay between login attempts helps to protect your router from a possible dictionary attack. You can enable delays in one of the following ways:
-
 The login block-for command: You must enter this command before issuing the login delay command. However, if you enter only the login block-for command, a login delay of 1 second is automatically enforced.
The login block-for command: You must enter this command before issuing the login delay command. However, if you enter only the login block-for command, a login delay of 1 second is automatically enforced. -
 The login delay command: This command enables you to specify the number of seconds to delay between login attempts.
The login delay command: This command enables you to specify the number of seconds to delay between login attempts. -
 The auto secure command: If you enable the AutoSecure feature, a login delay of 1 second is automatically enforced.
The auto secure command: If you enable the AutoSecure feature, a login delay of 1 second is automatically enforced.
 Login Shutdown if DoS Attacks Are Suspected
Login Shutdown if DoS Attacks Are Suspected
![]() If the configured number of connection attempts fails within a specified time period, the Cisco IOS device does not accept any additional connections for a period of time that is called the quiet period. Hosts that are permitted by a predefined access control list (ACL) are excluded from the quiet period.
If the configured number of connection attempts fails within a specified time period, the Cisco IOS device does not accept any additional connections for a period of time that is called the quiet period. Hosts that are permitted by a predefined access control list (ACL) are excluded from the quiet period.
![]() You can specify the number of failed connection attempts that trigger the quiet period using the command login block-for in global configuration mode. You can specify the predefined ACL that is excluded from the quiet period using the command login quiet-mode access-class command in global configuration mode.
You can specify the number of failed connection attempts that trigger the quiet period using the command login block-for in global configuration mode. You can specify the predefined ACL that is excluded from the quiet period using the command login quiet-mode access-class command in global configuration mode.
![]() This functionality is disabled by default, and it is not enabled if the AutoSecure feature is enabled.
This functionality is disabled by default, and it is not enabled if the AutoSecure feature is enabled.
 Generation of System Logging Messages for Login Detection
Generation of System Logging Messages for Login Detection
![]() After the router switches to and from quiet mode, logging messages are generated. Also, if they are configured, logging messages are generated upon every successful or failed login request.
After the router switches to and from quiet mode, logging messages are generated. Also, if they are configured, logging messages are generated upon every successful or failed login request.
| Note |
|
![]() You can use the command login on-success in global configuration mode to generate log messages for successful login requests. The login on-failure command generates logs for failed login requests.
You can use the command login on-success in global configuration mode to generate log messages for successful login requests. The login on-failure command generates logs for failed login requests.
![]() Logging messages for failed login attempts are automatically enabled when the auto secure command is issued, but are not automatically enabled for successful login attempts via the auto secure command.
Logging messages for failed login attempts are automatically enabled when the auto secure command is issued, but are not automatically enabled for successful login attempts via the auto secure command.
![]() All login enhancement features are disabled by default. You must issue the login block-for command, which enables default login functionality before using any other login commands. After you enable the login block-for command, the following defaults are enforced:
All login enhancement features are disabled by default. You must issue the login block-for command, which enables default login functionality before using any other login commands. After you enable the login block-for command, the following defaults are enforced:
-
 The default login delay is one second.
The default login delay is one second. -
 All login attempts made using Telnet, SSH, and HTTP are denied during the quiet period; that is, no ACLs are exempt from the login period until the login quiet-mode access-class command is issued.
All login attempts made using Telnet, SSH, and HTTP are denied during the quiet period; that is, no ACLs are exempt from the login period until the login quiet-mode access-class command is issued.
![]() Use the following command sequence to configure your Cisco IOS device for login parameters that help detect suspected DoS attacks and slow down dictionary attacks.
Use the following command sequence to configure your Cisco IOS device for login parameters that help detect suspected DoS attacks and slow down dictionary attacks.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() These commands are discussed in details in the next pages.
These commands are discussed in details in the next pages.
![]() Table 2-7 describes the commands required to set the parameters for the quiet period.
Table 2-7 describes the commands required to set the parameters for the quiet period.
|
|
|
|---|---|
|
|
|
|
|
|
![]() Example 2-17 shows a configuration that will disable login for 150 seconds if more than 2 login failures occur within 100 seconds. This will help provides DoS detection. Example 2-17 also shows configuration that invokes an ACL that is named myacl. If this command is not enabled, all login requests would be denied during quiet mode.
Example 2-17 shows a configuration that will disable login for 150 seconds if more than 2 login failures occur within 100 seconds. This will help provides DoS detection. Example 2-17 also shows configuration that invokes an ACL that is named myacl. If this command is not enabled, all login requests would be denied during quiet mode.
R1(config)# login block-for 150 attempts 2 within 100
R1(config)# login quiet-mode access-class myacl
![]() To enable a login delay, use the login delay seconds command. To log the successful and failed attempts to login, use the following commands:
To enable a login delay, use the login delay seconds command. To log the successful and failed attempts to login, use the following commands:
login on-failure log [every login]
login on-success log [every login]
![]() Then, use the show login command to verify that the login block-for command is issued. Example 2-18 shows that the router is configured to block login hosts for 100 seconds if more than 15 (16 or more) login requests fail within 100 seconds. Five login requests have already failed.
Then, use the show login command to verify that the login block-for command is issued. Example 2-18 shows that the router is configured to block login hosts for 100 seconds if more than 15 (16 or more) login requests fail within 100 seconds. Five login requests have already failed.
Router# show login
A default login delay of 1 second is applied.
No Quiet-Mode access list has been configured.
All successful login is logged and generate SNMP traps.
All failed login is logged and generate SNMP traps.
Router enabled to watch for login Attacks.
If more than 15 login failures occur in 100 seconds or less, logins will be
disabled for 100 seconds.
Router presently in Watch-Mode, will remain in Watch-Mode for 95 seconds.
Present login failure count 5.
![]() Example 2-19 is an output from the show login command to verify that the router is in quiet mode. This output shows that the login block-for command was configured to block login hosts for 100 seconds if more than 2 (3 or more) login requests fail within 100 seconds.
Example 2-19 is an output from the show login command to verify that the router is in quiet mode. This output shows that the login block-for command was configured to block login hosts for 100 seconds if more than 2 (3 or more) login requests fail within 100 seconds.
Router# show login
A default login delay of 1 second is applied.
No Quiet-Mode access list has been configured.
All successful login is logged and generate SNMP traps.
All failed login is logged and generate SNMP traps.
Router enabled to watch for login Attacks.
If more than 2 login failures occur in 100 seconds or less, logins will be
disabled for 100 seconds.
Router presently in Quiet-Mode, will remain in Quiet-Mode for 93 seconds.
Denying logins from all sources.
![]() Example 2-20 displays output from the show login failures command indicating all failed login attempts on the router.
Example 2-20 displays output from the show login failures command indicating all failed login attempts on the router.
Router# show login failures
Information about login failures with the device
Username Source IPAddr lPort Count TimeStamp
try1 10.1.1.1 23 1 21:52:49 UTC Sun Mar 9 2003
try2 10.1.1.2 23 1 21:52:52 UTC Sun Mar 9 2003
 Configuring Banner Messages
Configuring Banner Messages
![]() You should use banner messages to warn would-be intruders that they are not welcome on your network. Banners are very important, especially from a legal perspective.
You should use banner messages to warn would-be intruders that they are not welcome on your network. Banners are very important, especially from a legal perspective.
![]() Choosing what to place in your banner messages is important and should be reviewed by legal counsel before placing them on your routers. Intruders could have an argument in court cases if they were to argue that they have encountered a warning banner mentioning “Welcome to this site” or the like. All banners should rather warn that the access is strictly reserved to authorized personnel.
Choosing what to place in your banner messages is important and should be reviewed by legal counsel before placing them on your routers. Intruders could have an argument in court cases if they were to argue that they have encountered a warning banner mentioning “Welcome to this site” or the like. All banners should rather warn that the access is strictly reserved to authorized personnel.
![]() Banners are disabled by default, and you must explicitly enable them. Use the banner command from global configuration mode to specify appropriate messages.
Banners are disabled by default, and you must explicitly enable them. Use the banner command from global configuration mode to specify appropriate messages.
![]() Table 2-8 describes the parameters for the banner command, the syntax for which is as follows:
Table 2-8 describes the parameters for the banner command, the syntax for which is as follows:
banner {exec | incoming | login | motd | slip-ppp} d message d
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The following is a list of valid tokens for use within the message section of the banner command:
The following is a list of valid tokens for use within the message section of the banner command:
-
 $(hostname): Displays the hostname for the router
$(hostname): Displays the hostname for the router -
 $(domain): Displays the domain name for the router
$(domain): Displays the domain name for the router -
 $(line): Displays the vty or tty (asynchronous) line number
$(line): Displays the vty or tty (asynchronous) line number -
 $(line-desc): Displays the description that is attached to the line
$(line-desc): Displays the description that is attached to the line
![]() You can also use the Cisco SDM to configure banner messages.
You can also use the Cisco SDM to configure banner messages.
![]() Example 2-21 shows the configuration of a MOTD banner.
Example 2-21 shows the configuration of a MOTD banner.
R1(config)# banner motd %
WARNING: You are connected to $(hostname) on the Cisco Systems, Incorporated
network.
Unauthorized access and use of this network will be vigorously prosecuted. %
 Introducing Cisco SDM
Introducing Cisco SDM
![]() Cisco Router and Security Device Manager (SDM) is an intuitive, web-based tool that enables you to easily and reliably deploy and manage the services on Cisco IOS routers. Cisco SDM simplifies router and security configuration through smart wizards, which help users quickly and easily deploy, configure, and monitor Cisco routers without requiring knowledge of the Cisco IOS Software CLI.
Cisco Router and Security Device Manager (SDM) is an intuitive, web-based tool that enables you to easily and reliably deploy and manage the services on Cisco IOS routers. Cisco SDM simplifies router and security configuration through smart wizards, which help users quickly and easily deploy, configure, and monitor Cisco routers without requiring knowledge of the Cisco IOS Software CLI.
![]() Cisco SDM offers users the following benefits:
Cisco SDM offers users the following benefits:
-
 Smart wizards in Cisco SDM have built-in intelligence about recommended Cisco IOS configurations for different use scenarios.
Smart wizards in Cisco SDM have built-in intelligence about recommended Cisco IOS configurations for different use scenarios. -
 Cisco SDM can recommend an optimum security configuration for a router that is based on the detection of such areas as LAN and WAN connections, ACLs, Network Address Translation (NAT), IP Security (IPsec) policies, and firewall rules.
Cisco SDM can recommend an optimum security configuration for a router that is based on the detection of such areas as LAN and WAN connections, ACLs, Network Address Translation (NAT), IP Security (IPsec) policies, and firewall rules. -
 Cisco SDM includes features such as WAN and virtual private network (VPN) troubleshooting, router security audit, and one-step lockdown that leverage the integration of routing, WAN access, and security technology.
Cisco SDM includes features such as WAN and virtual private network (VPN) troubleshooting, router security audit, and one-step lockdown that leverage the integration of routing, WAN access, and security technology. -
 For novices, Cisco SDM helps users that have limited CLI knowledge and security expertise to configure basic network security implementations. For experts, Cisco SDM has power tools that improve productivity.
For novices, Cisco SDM helps users that have limited CLI knowledge and security expertise to configure basic network security implementations. For experts, Cisco SDM has power tools that improve productivity. -
 As a device manager, Cisco SDM manages one device at a time.
As a device manager, Cisco SDM manages one device at a time. -
 Cisco SDM supports Cisco IOS Software Release 12.2(11)T6 or later.
Cisco SDM supports Cisco IOS Software Release 12.2(11)T6 or later. -
 Cisco SDM has no impact on router DRAM or CPU.
Cisco SDM has no impact on router DRAM or CPU. -
 Cisco SDM works in conjunction with other management tools and the CLI over Telnet.
Cisco SDM works in conjunction with other management tools and the CLI over Telnet.
![]() Refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide for details on supported platforms and Cisco IOS Software requirements.
Refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide for details on supported platforms and Cisco IOS Software requirements.
| Note |
|
 Supporting Cisco SDM and Cisco SDM Express
Supporting Cisco SDM and Cisco SDM Express
![]() Cisco SDM is a web-based tool that is supported on Microsoft Windows-based PC platforms. Refer to the Cisco Router and Security Device Manager Quick Start Guide at http://tinyurl.com/5n2rb7 for details on the operating systems and web browsers that Cisco SDM supports.
Cisco SDM is a web-based tool that is supported on Microsoft Windows-based PC platforms. Refer to the Cisco Router and Security Device Manager Quick Start Guide at http://tinyurl.com/5n2rb7 for details on the operating systems and web browsers that Cisco SDM supports.
![]() Cisco SDM is factory installed on some router models. If it is not installed on your router, it will either be available on a CD-ROM that is included with new routers or you can download it from Cisco.com. The install options allow you to install Cisco SDM Express, Cisco SDM, or both.
Cisco SDM is factory installed on some router models. If it is not installed on your router, it will either be available on a CD-ROM that is included with new routers or you can download it from Cisco.com. The install options allow you to install Cisco SDM Express, Cisco SDM, or both.
| Note |
|
| Note |
|
![]() If the router is an existing router and is not configured with the Cisco SDM default configuration, you must configure the following services on the router for Cisco SDM to access the router properly:
If the router is an existing router and is not configured with the Cisco SDM default configuration, you must configure the following services on the router for Cisco SDM to access the router properly:
-
 Set up a username and password that has privilege level 15:
Set up a username and password that has privilege level 15: username name privilege 15 secret password
username name privilege 15 secret password -
 Enable the HTTP server:
Enable the HTTP server: ip http server
ip http server
ip http authentication local
ip http secure-server (for enabling HTTPS access to Cisco SDM)
ip http timeout-policy idle 600 life 86400 request 1000 -
 Define the protocol to use to connect to the Telnet and Secure Shell (SSH) vty lines:
Define the protocol to use to connect to the Telnet and Secure Shell (SSH) vty lines: line con 0
line con 0
login local
line vty 0 4
privilege level 15
login local
transport input telnet ssh
line vty 5 15
privilege level 15
login local
transport input telnet ssh
| Note |
|
![]() When you want to run Cisco SDM from your router, for Cisco SDM Version 2.2a and later, the following files must be loaded on the router flash memory:
When you want to run Cisco SDM from your router, for Cisco SDM Version 2.2a and later, the following files must be loaded on the router flash memory:
-
 sdmconfig-modelxxx.cfg, where modelxxx is the model number of the router (this is, the manufacture default configuration file for the router)
sdmconfig-modelxxx.cfg, where modelxxx is the model number of the router (this is, the manufacture default configuration file for the router) -
 sdm.tar
sdm.tar -
 es.tar (for Cisco SDM Express and optional once Cisco SDM is installed)
es.tar (for Cisco SDM Express and optional once Cisco SDM is installed) -
 common.tar
common.tar -
 home.shtml
home.shtml -
 home.tar
home.tar
![]() The file wlanui.tar is required if there are wireless interfaces to manage. Example 2-22 shows the content of the flash of a Cisco 2800 router.
The file wlanui.tar is required if there are wireless interfaces to manage. Example 2-22 shows the content of the flash of a Cisco 2800 router.
router# show flash
-#- –length– ––-date/time––– path
1 19312988 Dec 13 2005 01:23:50 +00:00 c2800nm-advsecurityk9-mz.124-5.bin
2 3317 Feb 8 2006 00:00:30 +00:00 startup.config
3 1646 Feb 8 2006 18:31:50 +00:00 sdmconfig-2811.cfg
4 4049920 Feb 8 2006 18:32:32 +00:00 sdm.tar
5 812544 Feb 8 2006 18:32:56 +00:00 es.tar
6 1007616 Feb 8 2006 18:33:14 +00:00 common.tar
7 1038 Feb 8 2006 18:33:24 +00:00 home.shtml
8 113152 Feb 8 2006 18:33:42 +00:00 home.tar
 Launching Cisco SDM Express
Launching Cisco SDM Express
![]() On a new router, you can access Cisco SDM Express from your PC web browser by going to http://10.10.10.1. The factory default router configuration file that comes with Cisco SDM configures the router Ethernet IP address to 10.10.10.1.
On a new router, you can access Cisco SDM Express from your PC web browser by going to http://10.10.10.1. The factory default router configuration file that comes with Cisco SDM configures the router Ethernet IP address to 10.10.10.1.
![]() If the proper files are loaded on the router flash memory, when you access the router for the first time, the Cisco SDM Express wizard appears. Just enter the required information, noting that some fields provide a default value.
If the proper files are loaded on the router flash memory, when you access the router for the first time, the Cisco SDM Express wizard appears. Just enter the required information, noting that some fields provide a default value.
![]() When you launch Cisco SDM from the router, Cisco SDM checks the router configuration. If certain features are not configured, Cisco SDM Express launches instead. For example, when Cisco SDM sees the default configuration file on the router (sdmconfig-modelxxx.cfg, where modelxxx is the model number of the device), Cisco SDM Express is launched.
When you launch Cisco SDM from the router, Cisco SDM checks the router configuration. If certain features are not configured, Cisco SDM Express launches instead. For example, when Cisco SDM sees the default configuration file on the router (sdmconfig-modelxxx.cfg, where modelxxx is the model number of the device), Cisco SDM Express is launched.
![]() After you have completed the initial router configuration with Cisco SDM Express, the Cisco SDM Express Wizard is not presented again. If you need to make changes, you can edit the configurations using the full Cisco SDM tool.
After you have completed the initial router configuration with Cisco SDM Express, the Cisco SDM Express Wizard is not presented again. If you need to make changes, you can edit the configurations using the full Cisco SDM tool.
![]() You can find details about Cisco SDM Express in the Cisco SDM Express 2.4 User’s Guide at http://tinyurl.com/47w5rk.
You can find details about Cisco SDM Express in the Cisco SDM Express 2.4 User’s Guide at http://tinyurl.com/47w5rk.
 Launching Cisco SDM
Launching Cisco SDM
![]() SDM can run either as an application installed on your PC or from the router’s flash through your PC’s browser.
SDM can run either as an application installed on your PC or from the router’s flash through your PC’s browser.
![]() To launch Cisco SDM from an administrator PC, choose Start > Programs (All Programs) > Cisco Systems > Cisco SDM > Cisco SDM. Next, provide the IP address of the LAN interface on the router, as configured previously with the Cisco SDM Express Wizard, in the SDM Launcher window.
To launch Cisco SDM from an administrator PC, choose Start > Programs (All Programs) > Cisco Systems > Cisco SDM > Cisco SDM. Next, provide the IP address of the LAN interface on the router, as configured previously with the Cisco SDM Express Wizard, in the SDM Launcher window.
![]() To launch Cisco SDM from the router flash memory, open an HTTP or HTTPS connection to the IP address of the Ethernet interface on the router. Follow the prompts, including entering your administrator credentials (username and password), to reach the Cisco SDM home page. Table 2-9 shows the browser requirements to run SDM.
To launch Cisco SDM from the router flash memory, open an HTTP or HTTPS connection to the IP address of the Ethernet interface on the router. Follow the prompts, including entering your administrator credentials (username and password), to reach the Cisco SDM home page. Table 2-9 shows the browser requirements to run SDM.
|
|
|
|---|---|
|
|
|
|
| |
|
| |
|
|
|
|
|
 Navigating the Cisco SDM Interface
Navigating the Cisco SDM Interface
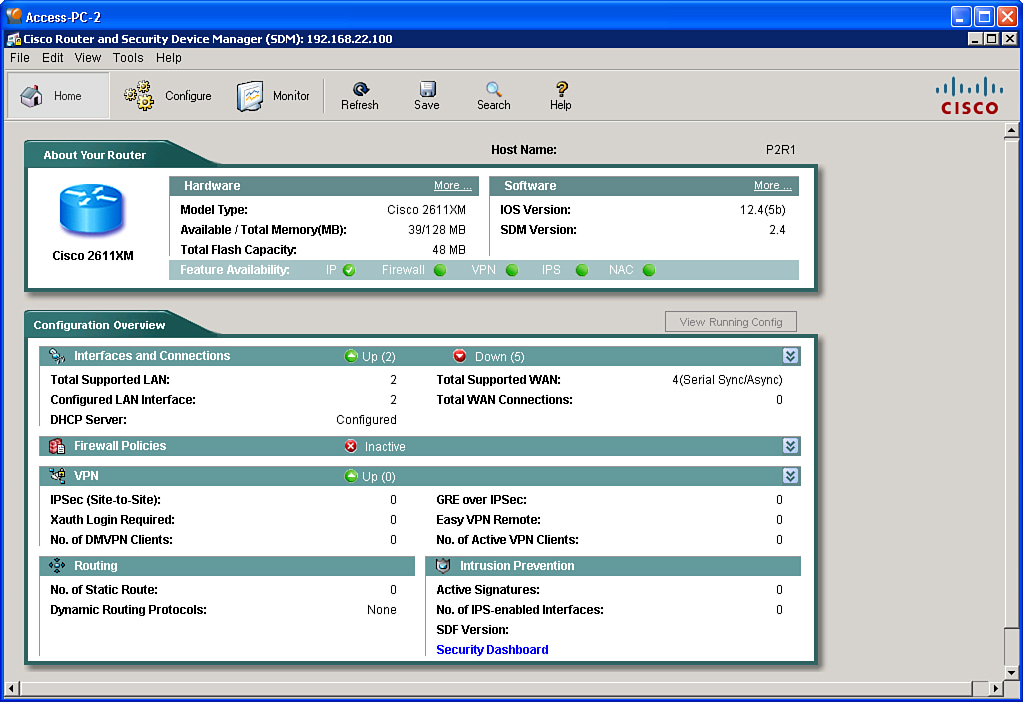
![]() The home page, shown in Figure 2-5, appears each time you successfully log in to Cisco SDM.
The home page, shown in Figure 2-5, appears each time you successfully log in to Cisco SDM.
![]() Navigating the Cisco SDM user interface on the home page is done through the toolbar. Two of the modes on the toolbar, Configure mode and Monitor mode, are also used to navigate the interface. To select a mode, click the corresponding button in the toolbar. For each mode, a task panel is available that shows the wizard options available for that mode.
Navigating the Cisco SDM user interface on the home page is done through the toolbar. Two of the modes on the toolbar, Configure mode and Monitor mode, are also used to navigate the interface. To select a mode, click the corresponding button in the toolbar. For each mode, a task panel is available that shows the wizard options available for that mode.
![]() Configure mode provides wizards for the novice. Figure 2-6 shows the Configure mode task bar. More experienced users are able to perform tasks in any order and without the wizards. Monitor mode allows you to view the current status of the router.
Configure mode provides wizards for the novice. Figure 2-6 shows the Configure mode task bar. More experienced users are able to perform tasks in any order and without the wizards. Monitor mode allows you to view the current status of the router.
![]() Upon SDM startup, it synchronizes with the router running configuration. Subsequent commands applied using the CLI are not automatically reflected in SDM. In this case, you can use the Refresh button to resynchronize the router running configuration with Cisco SDM.
Upon SDM startup, it synchronizes with the router running configuration. Subsequent commands applied using the CLI are not automatically reflected in SDM. In this case, you can use the Refresh button to resynchronize the router running configuration with Cisco SDM.
![]() Click the Save button to save the running configuration to the startup configuration on the router.
Click the Save button to save the running configuration to the startup configuration on the router.
 Cisco SDM Wizards in Configure Mode
Cisco SDM Wizards in Configure Mode
![]() When you access a wizard, a dialog box appears if there is a new configuration that is not yet reflected in Cisco SDM. The dialog box states that you must perform a Refresh or Deliver before entering wizard mode. If you click Refresh, the running configuration of the router is reloaded into Cisco SDM. If you click Deliver, any work done in Cisco SDM is copied to the running configuration of the router. Click either the Refresh or Deliver button to perform the required function.
When you access a wizard, a dialog box appears if there is a new configuration that is not yet reflected in Cisco SDM. The dialog box states that you must perform a Refresh or Deliver before entering wizard mode. If you click Refresh, the running configuration of the router is reloaded into Cisco SDM. If you click Deliver, any work done in Cisco SDM is copied to the running configuration of the router. Click either the Refresh or Deliver button to perform the required function.
![]() When the requested page appears, such as the Configure mode page, the wizards display on the left. In general, the following are functions that are available from the wizards in Configure mode:
When the requested page appears, such as the Configure mode page, the wizards display on the left. In general, the following are functions that are available from the wizards in Configure mode:
-
 The Interfaces and Connections window displays the router interfaces and connections. The window also enables you to add, edit, and delete connections and to enable or disable the following types of connections:
The Interfaces and Connections window displays the router interfaces and connections. The window also enables you to add, edit, and delete connections and to enable or disable the following types of connections: The LAN Wizard configures the LAN interfaces and DHCP.
The LAN Wizard configures the LAN interfaces and DHCP. The WAN Wizard configures PPP, Frame Relay, and High-Level Data Link Control (HDLC) WAN interfaces.
The WAN Wizard configures PPP, Frame Relay, and High-Level Data Link Control (HDLC) WAN interfaces. -
 Firewall and ACL provide two wizards: a basic firewall wizard with inside and outside interfaces, and an advanced firewall wizard with inside, outside, and DMZ interfaces.
Firewall and ACL provide two wizards: a basic firewall wizard with inside and outside interfaces, and an advanced firewall wizard with inside, outside, and DMZ interfaces. -
 For VPN, there are four wizards: IPsec VPN (site-to-site VPN), Cisco Easy VPN Remote, Cisco Easy VPN Server, and Dynamic Multipoint VPN (DMVPN).
For VPN, there are four wizards: IPsec VPN (site-to-site VPN), Cisco Easy VPN Remote, Cisco Easy VPN Server, and Dynamic Multipoint VPN (DMVPN). -
 The Security Audit task contains two wizards: the Router Security Audit and a One-Step Lockdown Wizard.
The Security Audit task contains two wizards: the Router Security Audit and a One-Step Lockdown Wizard. -
 The Routing window displays the configured static routes and the configuration of the routing protocols. From this window, you can configure the Routing Information Protocol (RIP), Open Shortest Path First (OSPF), or Enhanced Interior Gateway Routing Protocol (EIGRP) routing protocol parameters, review the routes, add new static routes, edit existing static routes, and delete static routes.
The Routing window displays the configured static routes and the configuration of the routing protocols. From this window, you can configure the Routing Information Protocol (RIP), Open Shortest Path First (OSPF), or Enhanced Interior Gateway Routing Protocol (EIGRP) routing protocol parameters, review the routes, add new static routes, edit existing static routes, and delete static routes. -
 The NAT window enables you to view NAT rules, view address pools, and set translation timeouts. From this window, you can also designate interfaces as inside or outside interfaces.
The NAT window enables you to view NAT rules, view address pools, and set translation timeouts. From this window, you can also designate interfaces as inside or outside interfaces. -
 Starting with Cisco IOS Software Release 12.3(8)T, the Intrusion Prevention window allows you to enable or disable Cisco IOS Intrusion Prevention System (IPS) features on any interface in the router. If a Cisco Intrusion Detection System (IDS) Access Router Network Module (Cisco IDS Network Module) is installed in the router, this window displays basic status information for the module. If the Cisco IDS Network Module has been configured, you can also start the Cisco IDS Device Manager (IDM) software on the Cisco IDS Network Module and select the router interfaces that you want the Cisco IDS Network Module to monitor from this window.
Starting with Cisco IOS Software Release 12.3(8)T, the Intrusion Prevention window allows you to enable or disable Cisco IOS Intrusion Prevention System (IPS) features on any interface in the router. If a Cisco Intrusion Detection System (IDS) Access Router Network Module (Cisco IDS Network Module) is installed in the router, this window displays basic status information for the module. If the Cisco IDS Network Module has been configured, you can also start the Cisco IDS Device Manager (IDM) software on the Cisco IDS Network Module and select the router interfaces that you want the Cisco IDS Network Module to monitor from this window.Note  If Cisco SDM detects that the Cisco IDS Network Module has not been configured, it prompts you to open a session to the network module so that you can configure it. You can use Telnet or SSH for this session.
If Cisco SDM detects that the Cisco IDS Network Module has not been configured, it prompts you to open a session to the network module so that you can configure it. You can use Telnet or SSH for this session. -
 The Quality of Service window allows you to configure QoS rules and policies for your router.
The Quality of Service window allows you to configure QoS rules and policies for your router. -
 The NAC window is used to protect data networks from computer viruses by assessing the health of client workstations, ensuring that they receive the latest available virus signature updates, and controlling their access to the network.
The NAC window is used to protect data networks from computer viruses by assessing the health of client workstations, ensuring that they receive the latest available virus signature updates, and controlling their access to the network.
![]() When you finish using a wizard, all the changes are automatically delivered to the router using generated CLI commands. You can choose whether to copy the running configuration to the startup configuration file.
When you finish using a wizard, all the changes are automatically delivered to the router using generated CLI commands. You can choose whether to copy the running configuration to the startup configuration file.
![]() For additional details on these tasks, refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide.
For additional details on these tasks, refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide.
Configure Mode: Advanced Configuration
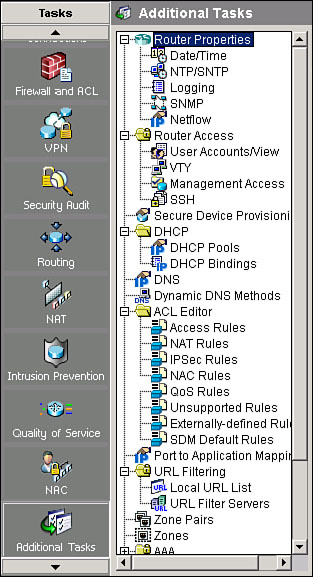
![]() At the bottom of the Cisco SDM configuration task bar is an Additional Tasks option, shown in Figure 2-7. This option allows you to configure many advanced options for the router, such as router properties, router access, DHCP settings, Domain Name System (DNS) and Dynamic DNS (DDNS) settings, ACLs, AAA configuration, router provisioning, and IEEE 802.1x. Click Additional Tasks to enter this mode and configure one of these options. You can perform tasks in any order, and you can always see existing configurations.
At the bottom of the Cisco SDM configuration task bar is an Additional Tasks option, shown in Figure 2-7. This option allows you to configure many advanced options for the router, such as router properties, router access, DHCP settings, Domain Name System (DNS) and Dynamic DNS (DDNS) settings, ACLs, AAA configuration, router provisioning, and IEEE 802.1x. Click Additional Tasks to enter this mode and configure one of these options. You can perform tasks in any order, and you can always see existing configurations.
![]() You can choose Additional Tasks > Router Properties to define the overall attributes of the router, such as the router name, domain name, password, SNMP status, DNS server address, user accounts, router log attributes, vty settings, SSH settings, and other router access security settings.
You can choose Additional Tasks > Router Properties to define the overall attributes of the router, such as the router name, domain name, password, SNMP status, DNS server address, user accounts, router log attributes, vty settings, SSH settings, and other router access security settings.
![]() After you click Additional Tasks, you can use the Router Access window to create and manage security policies to access and manage the router. You can create, edit, and delete role-based user access accounts and set up management access policies to limit the Telnet, SNMP, or Cisco SDM access to the router from specific hosts or networks.
After you click Additional Tasks, you can use the Router Access window to create and manage security policies to access and manage the router. You can create, edit, and delete role-based user access accounts and set up management access policies to limit the Telnet, SNMP, or Cisco SDM access to the router from specific hosts or networks.
![]() For additional details on the features and functions available from the Additional Tasks windows, refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide.
For additional details on the features and functions available from the Additional Tasks windows, refer to the Cisco Router and Security Device Manager Version 2.4 User’s Guide.
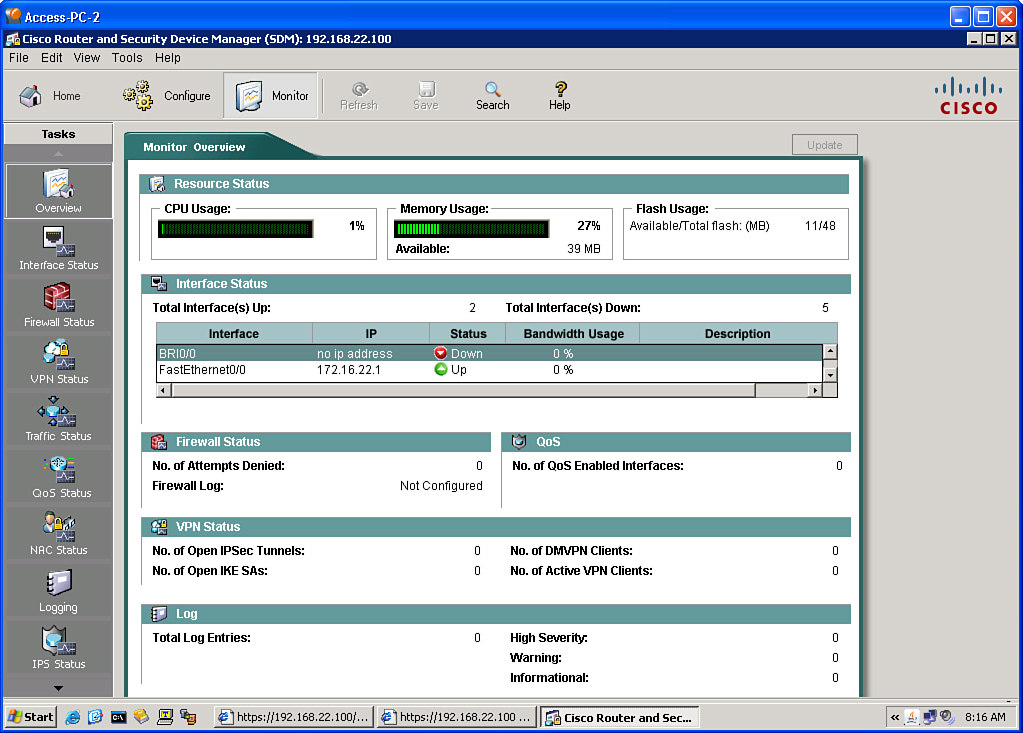
Monitor Mode
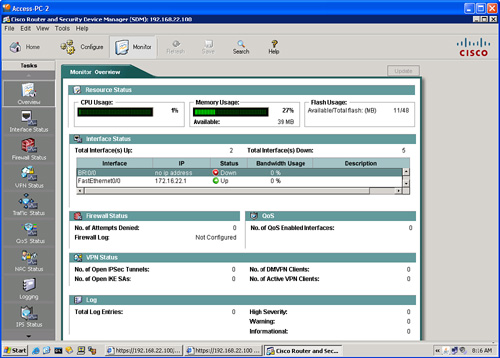
![]() From Monitor mode, you can view information about your router, including the router interfaces, firewalls, and any active VPN connections. You can also view any messages in the router event log. Figure 2-8 shows Monitor mode.
From Monitor mode, you can view information about your router, including the router interfaces, firewalls, and any active VPN connections. You can also view any messages in the router event log. Figure 2-8 shows Monitor mode.
![]() The monitor function includes the following information:
The monitor function includes the following information:
-
 The Monitor Overview window provides the router status, including a list of the error log entries.
The Monitor Overview window provides the router status, including a list of the error log entries. -
 Interface Status is used to select the interface and conditions to monitor (for example, packets and errors and whether you want to monitor them in or out).
Interface Status is used to select the interface and conditions to monitor (for example, packets and errors and whether you want to monitor them in or out). -
 Firewall Status displays a log with the number of entry attempts that the firewall denied.
Firewall Status displays a log with the number of entry attempts that the firewall denied. -
 VPN Status displays statistics about active VPN connections.
VPN Status displays statistics about active VPN connections. -
 QoS displays QoS policy information on the interfaces.
QoS displays QoS policy information on the interfaces. -
 NAC Status (not shown in Figure 2-8) displays information such as the number of active Network Admission Control (NAC) sessions on the routers.
NAC Status (not shown in Figure 2-8) displays information such as the number of active Network Admission Control (NAC) sessions on the routers. -
 Log contains the event log categorized by severity level, such as a UNIX syslog service.
Log contains the event log categorized by severity level, such as a UNIX syslog service.




0 comments
Post a Comment