Overview
![]() This chapter introduces the concept of perimeter security and covers the following topics:
This chapter introduces the concept of perimeter security and covers the following topics:
-
 Physical installation of and administrative access to Cisco routers
Physical installation of and administrative access to Cisco routers -
 Features and uses of Cisco Router and Security Device Manager (SDM)
Features and uses of Cisco Router and Security Device Manager (SDM) -
 Configuration of a Cisco router to perform authentication, authorization, accounting (AAA) authentication with a local database
Configuration of a Cisco router to perform authentication, authorization, accounting (AAA) authentication with a local database -
 Operation of external AAA sources such as RADIUS and TACACS+ servers, and configuration of a Cisco router to perform AAA
Operation of external AAA sources such as RADIUS and TACACS+ servers, and configuration of a Cisco router to perform AAA -
 Secure implementation of the management and reporting features of syslog, Simple Network Management Protocol (SNMP), Secure Shell (SSH), and Network Time Protocol (NTP)
Secure implementation of the management and reporting features of syslog, Simple Network Management Protocol (SNMP), Secure Shell (SSH), and Network Time Protocol (NTP) -
 Examination router configurations with the Security Audit feature of Cisco SDM and how to make the router and network more secure by using the One-Step Lockdown feature of Cisco SDM or the command auto secure
Examination router configurations with the Security Audit feature of Cisco SDM and how to make the router and network more secure by using the One-Step Lockdown feature of Cisco SDM or the command auto secure
![]() A network perimeter is the border between a private, locally managed network and the public network, such as the Internet. Therefore, traffic originating from the outside destined for the inside of a closed network must transit through the network perimeter.
A network perimeter is the border between a private, locally managed network and the public network, such as the Internet. Therefore, traffic originating from the outside destined for the inside of a closed network must transit through the network perimeter.
![]() In this chapter, you will learn how to apply security policies to the perimeter routers, which includes securing administrative access to the router. You will also be introduced to the Cisco Router and Security Device Manager.
In this chapter, you will learn how to apply security policies to the perimeter routers, which includes securing administrative access to the router. You will also be introduced to the Cisco Router and Security Device Manager.
Securing Administrative Access to Cisco Routers
![]() This section introduces how to secure Cisco routers using proven methods for physically securing the router and protecting the router administrative access.
This section introduces how to secure Cisco routers using proven methods for physically securing the router and protecting the router administrative access.
 General Router Security Guidelines
General Router Security Guidelines
![]() You should think about router security in terms of its physical security, the features and performance of the router operating system, the protection of the router configurations, and the elimination of potential abuse of unused ports and services through router hardening. The three main principles of router security are as follows:
You should think about router security in terms of its physical security, the features and performance of the router operating system, the protection of the router configurations, and the elimination of potential abuse of unused ports and services through router hardening. The three main principles of router security are as follows:
-
 To provide physical security for a router, take the following actions:
To provide physical security for a router, take the following actions:-
 Place the router in a locked room that is accessible only to authorized personnel, is free of electrostatic or magnetic interference, and has controls for temperature and humidity.
Place the router in a locked room that is accessible only to authorized personnel, is free of electrostatic or magnetic interference, and has controls for temperature and humidity. -
 Install an uninterruptible power supply (UPS) and keep spare components available. This reduces the possibility of a denial-of-service (DoS) attack from power loss.
Install an uninterruptible power supply (UPS) and keep spare components available. This reduces the possibility of a denial-of-service (DoS) attack from power loss. -
 Configure the router with the maximum amount of memory possible. The availability of memory can help protect the network from some DoS attacks, while supporting the widest range of security services.
Configure the router with the maximum amount of memory possible. The availability of memory can help protect the network from some DoS attacks, while supporting the widest range of security services. -
 Store physical devices that connect to the router in a secure place.
Store physical devices that connect to the router in a secure place.
-
-
 The security features in an operating system evolve over time; however, the latest version of an operating system might not be the most stable version available. To get the best security performance from your operating system, use the latest stable release that meets the feature requirements of your network. Also, keep a secure copy of the router operating system image and router configuration file as a backup.
The security features in an operating system evolve over time; however, the latest version of an operating system might not be the most stable version available. To get the best security performance from your operating system, use the latest stable release that meets the feature requirements of your network. Also, keep a secure copy of the router operating system image and router configuration file as a backup. -
 Similar to many computers, a router has many services that are enabled by default. Many of these services are unnecessary and can be used by an attacker to gather information or for exploitation. You should disable unnecessary services to harden your router configuration.
Similar to many computers, a router has many services that are enabled by default. Many of these services are unnecessary and can be used by an attacker to gather information or for exploitation. You should disable unnecessary services to harden your router configuration.
| Note |
|
![]() A router provides the capability to help secure the perimeter of a protected network. It is a device where you can implement security action that is based on the security policy of your organization.
A router provides the capability to help secure the perimeter of a protected network. It is a device where you can implement security action that is based on the security policy of your organization.
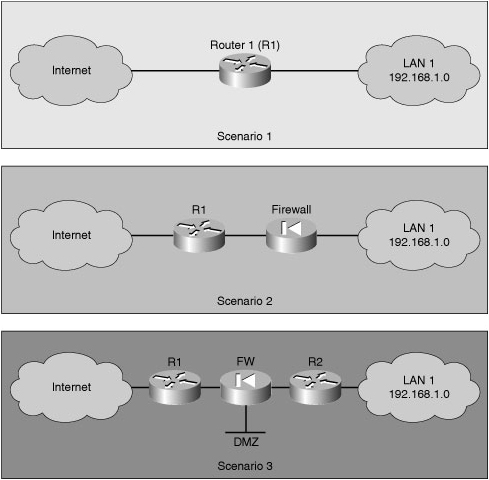
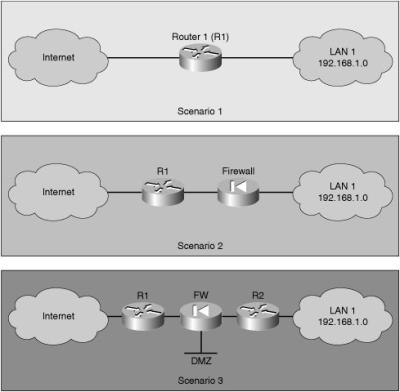
![]() To secure a network perimeter, you can deploy a router on its own. Scenario 1 of Figure 2-1 shows a typical topology where the router connects the private network to the Internet.
To secure a network perimeter, you can deploy a router on its own. Scenario 1 of Figure 2-1 shows a typical topology where the router connects the private network to the Internet.
![]() You can also use a router as part of a defense-in-depth approach, as shown in Scenario 2 of Figure 2-1. This approach is preferred to that of using only a router because it is more secure. The router acts as the first line of defense and, in such a deployment, is known as a screening router or perimeter router. It passes all the connections that are intended for the internal LAN to the firewall. The firewall provides additional access control by tracking the state of the connections. By default, the firewall denies the initiation of connections from the outside (untrusted) networks to the inside (trusted) network but allows the internal users to establish connections to the untrusted networks and permits the responses to come back through the firewall. It can also perform user authentication (authentication proxy), where users have to be authenticated before they can gain access to network resources.
You can also use a router as part of a defense-in-depth approach, as shown in Scenario 2 of Figure 2-1. This approach is preferred to that of using only a router because it is more secure. The router acts as the first line of defense and, in such a deployment, is known as a screening router or perimeter router. It passes all the connections that are intended for the internal LAN to the firewall. The firewall provides additional access control by tracking the state of the connections. By default, the firewall denies the initiation of connections from the outside (untrusted) networks to the inside (trusted) network but allows the internal users to establish connections to the untrusted networks and permits the responses to come back through the firewall. It can also perform user authentication (authentication proxy), where users have to be authenticated before they can gain access to network resources.
![]() Another approach, shown in Scenario 3 of Figure 2-1, is to offer an intermediate area, often called the demilitarized zone (DMZ). The DMZ, attached to the firewall, can be used for servers that must be accessible from the Internet or some other external network. The firewall, located between the routers, is set up to permit the required connections (for example, HTTP) from the outside (untrusted) networks to the public servers in the DMZ. The firewall serves as the primary protection for all devices on the DMZ. In this situation, the router provides some protection by filtering some traffic, but leaves the bulk of the protection to the firewall.
Another approach, shown in Scenario 3 of Figure 2-1, is to offer an intermediate area, often called the demilitarized zone (DMZ). The DMZ, attached to the firewall, can be used for servers that must be accessible from the Internet or some other external network. The firewall, located between the routers, is set up to permit the required connections (for example, HTTP) from the outside (untrusted) networks to the public servers in the DMZ. The firewall serves as the primary protection for all devices on the DMZ. In this situation, the router provides some protection by filtering some traffic, but leaves the bulk of the protection to the firewall.
| Note |
|
 Introduction to the Cisco Integrated Services Router Family
Introduction to the Cisco Integrated Services Router Family
![]() Cisco Integrated Services Routers (ISR) ship with the most comprehensive security services in the industry, intelligently embedding data, security, voice, and wireless in the platform portfolio for fast, scalable delivery of mission-critical business applications. The Cisco ISRs are an integral part of the Cisco Self-Defending Network. Engineered for delivering secure services, the Cisco ISRs offer a unique blend of both hardware-accelerated and software security features and offer solutions for the small office and teleworker and the branch office and small and medium-sized business (SMB).
Cisco Integrated Services Routers (ISR) ship with the most comprehensive security services in the industry, intelligently embedding data, security, voice, and wireless in the platform portfolio for fast, scalable delivery of mission-critical business applications. The Cisco ISRs are an integral part of the Cisco Self-Defending Network. Engineered for delivering secure services, the Cisco ISRs offer a unique blend of both hardware-accelerated and software security features and offer solutions for the small office and teleworker and the branch office and small and medium-sized business (SMB).
Cisco Integrated Services Routers Models
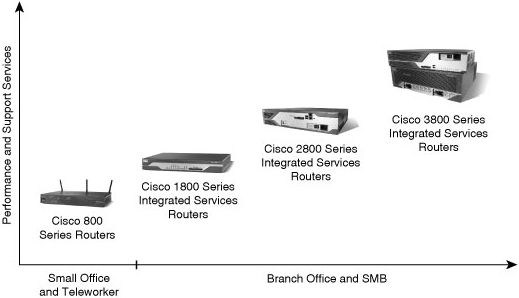
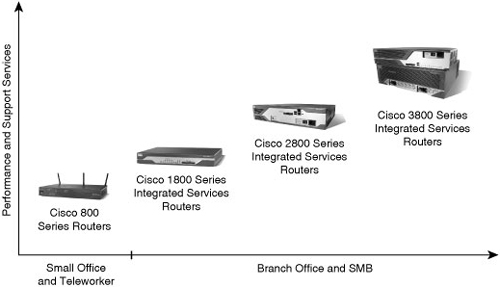
![]() Figure 2-2 shows Cisco ISRs and in which environment they are typically deployed.
Figure 2-2 shows Cisco ISRs and in which environment they are typically deployed.
![]() The Cisco ISR family consists of the following:
The Cisco ISR family consists of the following:
-
 Cisco 800 series routers: Extend to small offices and teleworkers, or to service providers to deploy as part of their managed network services, and deliver data, security, and wireless services concurrently and at broadband speeds, and offer built-in security. The Cisco 800 series also includes broadband routers that provide highly secure Internet access and corporate network connectivity to small remote offices and teleworkers.
Cisco 800 series routers: Extend to small offices and teleworkers, or to service providers to deploy as part of their managed network services, and deliver data, security, and wireless services concurrently and at broadband speeds, and offer built-in security. The Cisco 800 series also includes broadband routers that provide highly secure Internet access and corporate network connectivity to small remote offices and teleworkers.Note  Cisco had another 800 series router, but that became end-of-life in 2002. For more information, refer to http://www.cisco.com/en/US/products/hw/routers/ps380/prod_eol_notices_list.html.
Cisco had another 800 series router, but that became end-of-life in 2002. For more information, refer to http://www.cisco.com/en/US/products/hw/routers/ps380/prod_eol_notices_list.html. -
 Cisco 1800 series routers: These fixed-configuration routers are designed for secure broadband, Metro Ethernet, and wireless connectivity. This series of routers helps businesses reduce costs by enabling them to deploy a single device that provides multiple services, such as integrated router with redundant link, LAN switch, firewall, virtual private network (VPN), intrusion prevention systems (IPS), wireless technology, and quality of service (QoS), which are commonly performed by separate devices. The Cisco 1861 router includes a modular high-speed WAN interface card (HWIC) slot.
Cisco 1800 series routers: These fixed-configuration routers are designed for secure broadband, Metro Ethernet, and wireless connectivity. This series of routers helps businesses reduce costs by enabling them to deploy a single device that provides multiple services, such as integrated router with redundant link, LAN switch, firewall, virtual private network (VPN), intrusion prevention systems (IPS), wireless technology, and quality of service (QoS), which are commonly performed by separate devices. The Cisco 1861 router includes a modular high-speed WAN interface card (HWIC) slot. -
 Cisco 2800 series routers: Designed to meet the expanding requirements of SMB offices and small to medium enterprise businesses in delivering secure, concurrent data, voice, and video services at wire-speed performance.
Cisco 2800 series routers: Designed to meet the expanding requirements of SMB offices and small to medium enterprise businesses in delivering secure, concurrent data, voice, and video services at wire-speed performance. -
 Cisco 3800 series routers: The architecture of these routers is designed to deliver the performance, availability, and reliability required for scaling mission-critical security, IP telephony, business video, network analysis, and web applications in the most demanding enterprise environments. Built for performance, the Cisco 3800 series ISRs deliver multiple secure, concurrent data, voice, and video services at wire-speed performance. The Cisco 3800 series ISR architecture builds on the powerful Cisco 3700 series Multiservice Access Routers.
Cisco 3800 series routers: The architecture of these routers is designed to deliver the performance, availability, and reliability required for scaling mission-critical security, IP telephony, business video, network analysis, and web applications in the most demanding enterprise environments. Built for performance, the Cisco 3800 series ISRs deliver multiple secure, concurrent data, voice, and video services at wire-speed performance. The Cisco 3800 series ISR architecture builds on the powerful Cisco 3700 series Multiservice Access Routers.
Cisco Integrated Services Router Features
![]() Cisco ISRs deliver additional options to enhance security in the network. Security-related features of the Cisco ISRs include the following:
Cisco ISRs deliver additional options to enhance security in the network. Security-related features of the Cisco ISRs include the following:
-
 Integrated security
Integrated security  The built-in, hardware-based encryption acceleration offloads the VPN processes to provide increased VPN throughput with minimal impact on the router CPU.
The built-in, hardware-based encryption acceleration offloads the VPN processes to provide increased VPN throughput with minimal impact on the router CPU. The Cisco ISR series provides a built-in VPN encryption acceleration for IP Security (IPsec) Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Advanced Encryption Standard (AES) 128-, 192-, and 256-bit key sizes. In addition, you can use an Advanced Integration Module (AIM) for VPN encryption.
The Cisco ISR series provides a built-in VPN encryption acceleration for IP Security (IPsec) Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Advanced Encryption Standard (AES) 128-, 192-, and 256-bit key sizes. In addition, you can use an Advanced Integration Module (AIM) for VPN encryption. The Cisco NAC Network Module for ISRs brings Cisco NAC Appliance Server capabilities to Cisco 2800 and 3800 Series Integrated Services Routers. By extending the Cisco NAC Appliance portfolio to smaller locations, the Cisco NAC Network Module enables network administrators to manage a single device in the branch office for data, voice, and security.
The Cisco NAC Network Module for ISRs brings Cisco NAC Appliance Server capabilities to Cisco 2800 and 3800 Series Integrated Services Routers. By extending the Cisco NAC Appliance portfolio to smaller locations, the Cisco NAC Network Module enables network administrators to manage a single device in the branch office for data, voice, and security. The Cisco IPS Network Module for Cisco routers includes innovative technologies that give users the confidence to take preventative actions on a broader range of threats. These technologies, including correlation and validation tools, greatly reduce the risk of dropping legitimate traffic.
The Cisco IPS Network Module for Cisco routers includes innovative technologies that give users the confidence to take preventative actions on a broader range of threats. These technologies, including correlation and validation tools, greatly reduce the risk of dropping legitimate traffic. The Cisco Intrusion Prevention System Advanced Integration Module (AIM-IPS) integrates and brings inline Cisco IPS functionality to Cisco 1841, 2811, 2821, 2851, and 3800 series routers.
The Cisco Intrusion Prevention System Advanced Integration Module (AIM-IPS) integrates and brings inline Cisco IPS functionality to Cisco 1841, 2811, 2821, 2851, and 3800 series routers. -
 Unified network services
Unified network services  Packet voice digital signal processing (DSP) modules (PVDM) provide conferencing, transcoding, and secure voice features. With Secure Real-Time Transport Protocol (SRTP), the whole voice payload is encrypted while the header is still in plaintext to support features such as QoS.
Packet voice digital signal processing (DSP) modules (PVDM) provide conferencing, transcoding, and secure voice features. With Secure Real-Time Transport Protocol (SRTP), the whole voice payload is encrypted while the header is still in plaintext to support features such as QoS. Media authentication and encryption in Cisco Survivable Remote Site Telephony (SRST) mode is supported beginning with the Cisco IOS Software Release 12.3(14)T and Cisco Unified CallManager Release 4.1.
Media authentication and encryption in Cisco Survivable Remote Site Telephony (SRST) mode is supported beginning with the Cisco IOS Software Release 12.3(14)T and Cisco Unified CallManager Release 4.1. -
 Mobility
Mobility  There are Cisco HWICs that provide access point functionality as an integrated secure 802.11 access point for modular Cisco ISRs.
There are Cisco HWICs that provide access point functionality as an integrated secure 802.11 access point for modular Cisco ISRs. The third-generation (3G) wireless HWICs offer a compelling alternative to traditional wired backup solutions by using terrestrial cellular technology.
The third-generation (3G) wireless HWICs offer a compelling alternative to traditional wired backup solutions by using terrestrial cellular technology. -
 Application intelligence
Application intelligence  The Cisco Wide Area Application Services (WAAS) network module is a powerful application-acceleration and WAN-optimization solution that accelerates the performance of any TCP-based application that is delivered across a WAN. Cisco WAAS allows customers to consolidate costly branch servers and storage into data centers and deploy new applications centrally while still offering near-LAN performance for remote users.
The Cisco Wide Area Application Services (WAAS) network module is a powerful application-acceleration and WAN-optimization solution that accelerates the performance of any TCP-based application that is delivered across a WAN. Cisco WAAS allows customers to consolidate costly branch servers and storage into data centers and deploy new applications centrally while still offering near-LAN performance for remote users. Performance routing improves application performance by enabling a performance-aware infrastructure that selects the best path across the network.
Performance routing improves application performance by enabling a performance-aware infrastructure that selects the best path across the network. -
 Universal Serial Bus (USB) port
Universal Serial Bus (USB) port  As of Cisco IOS Software Release 12.3(14)T, the USB eToken and USB flash support are available. The USB eToken feature provides secure configuration distribution and allows users to store VPN credentials for deployment. The USB flash feature allows users to store images and configurations using USB flash memory.
As of Cisco IOS Software Release 12.3(14)T, the USB eToken and USB flash support are available. The USB eToken feature provides secure configuration distribution and allows users to store VPN credentials for deployment. The USB flash feature allows users to store images and configurations using USB flash memory.
| Note |
|
 Configuring Secure Administration Access
Configuring Secure Administration Access
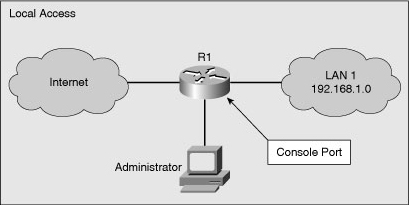
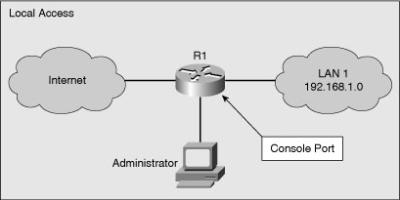
![]() Local access to a router, shown in Figure 2-3, usually involves a direct connection to a console port on the Cisco router using a PC or a laptop computer running terminal emulation software.
Local access to a router, shown in Figure 2-3, usually involves a direct connection to a console port on the Cisco router using a PC or a laptop computer running terminal emulation software.
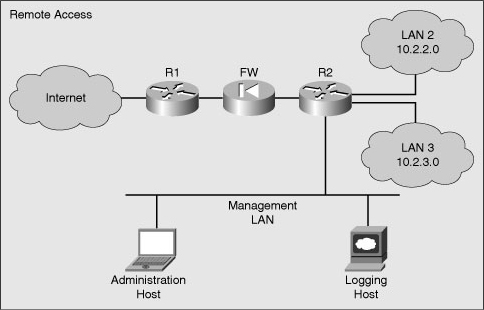
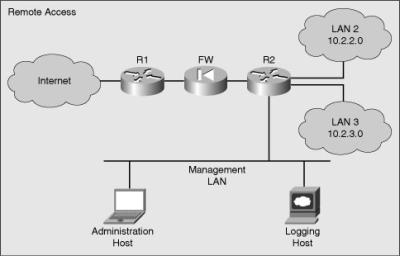
![]() Remote access typically involves allowing Telnet, Secure Shell (SSH), HTTP, HTTPS, or Simple Network Management Protocol (SNMP) connections to the router from a computer on the same subnet or different subnet. Figure 2-4 shows the topologies associated with both types of access.
Remote access typically involves allowing Telnet, Secure Shell (SSH), HTTP, HTTPS, or Simple Network Management Protocol (SNMP) connections to the router from a computer on the same subnet or different subnet. Figure 2-4 shows the topologies associated with both types of access.
![]() It is preferable to allow only local access to the router because some remote-access protocols, such as Telnet, send the data, including usernames and passwords, to the router in plaintext. If an attacker can collect network traffic while an administrator is logged in remotely to a router, the attacker can capture passwords or router configuration information.
It is preferable to allow only local access to the router because some remote-access protocols, such as Telnet, send the data, including usernames and passwords, to the router in plaintext. If an attacker can collect network traffic while an administrator is logged in remotely to a router, the attacker can capture passwords or router configuration information.
![]() If remote access is required, it is recommended that you apply one of the following options:
If remote access is required, it is recommended that you apply one of the following options:
-
 Establish a dedicated management network. The management network should include only identified administration hosts and connections to a dedicated interface on the router.
Establish a dedicated management network. The management network should include only identified administration hosts and connections to a dedicated interface on the router. -
 Encrypt all the traffic between the administrator computer and the router.
Encrypt all the traffic between the administrator computer and the router.
![]() In either case, you can configure a packet filter to allow only the identified administration hosts and preferred protocols to access the router. For example, permit only SSH requests from the IP address of the administration host to initiate a connection to the routers in the network.
In either case, you can configure a packet filter to allow only the identified administration hosts and preferred protocols to access the router. For example, permit only SSH requests from the IP address of the administration host to initiate a connection to the routers in the network.
| Note |
|
Configuring the Router Passwords
![]() Configuring secure administrative access is an extremely important security task. If an unauthorized person were to gain administrative access to a router, the person could alter routing parameters, disable routing functions, discover and gain access to other systems in the network, or simply erase the startup configuration file and reload the router.
Configuring secure administrative access is an extremely important security task. If an unauthorized person were to gain administrative access to a router, the person could alter routing parameters, disable routing functions, discover and gain access to other systems in the network, or simply erase the startup configuration file and reload the router.
![]() Strong passwords and similar secrets, such as SNMP community strings, are the primary defense against unauthorized access to your router. The first step to secure Cisco router administrative access is to configure secure system passwords. The best way to handle most passwords is to maintain them on a TACACS+ or RADIUS authentication server such as the Cisco Secure Access Control Server (ACS). However, routers can have locally configured passwords for privileged access and can have other password information in their configuration files. This section focuses only on configuring local passwords.
Strong passwords and similar secrets, such as SNMP community strings, are the primary defense against unauthorized access to your router. The first step to secure Cisco router administrative access is to configure secure system passwords. The best way to handle most passwords is to maintain them on a TACACS+ or RADIUS authentication server such as the Cisco Secure Access Control Server (ACS). However, routers can have locally configured passwords for privileged access and can have other password information in their configuration files. This section focuses only on configuring local passwords.
![]() To gain access to the router and configure passwords, connect to the router using a console. A console is a terminal connected to a router console port. The terminal can be a dumb terminal or a PC with terminal emulation software, such as Microsoft HyperTerminal.
To gain access to the router and configure passwords, connect to the router using a console. A console is a terminal connected to a router console port. The terminal can be a dumb terminal or a PC with terminal emulation software, such as Microsoft HyperTerminal.
| Key Topic |
|
![]() When creating passwords for Cisco routers, always keep the following rules in mind:
When creating passwords for Cisco routers, always keep the following rules in mind:
-
 Establish a minimum of 10 characters for a password.
Establish a minimum of 10 characters for a password. -
 Passwords can include the following:
Passwords can include the following:-
 Any alphanumeric character
Any alphanumeric character -
 A mix of uppercase and lowercase characters
A mix of uppercase and lowercase characters -
 Symbols and spaces
Symbols and spaces
-
-
 Passwords should not use dictionary words.
Passwords should not use dictionary words. -
 Password-leading spaces are ignored, but no spaces after the first character are ignored.
Password-leading spaces are ignored, but no spaces after the first character are ignored. -
 Decide when and how often the passwords should be changed.
Decide when and how often the passwords should be changed.
![]() You might want to add your own rules to this list to make your passwords even safer, such as insisting that passwords be a sequence of alternating letters, numbers, and a symbol, for instance.
You might want to add your own rules to this list to make your passwords even safer, such as insisting that passwords be a sequence of alternating letters, numbers, and a symbol, for instance.
![]() You can secure a router by using a password to restrict access. Using a password and assigning privilege levels is a simple way to provide terminal access control in a network. A password can be established on individual lines, such as the console, and to the privileged EXEC mode. Passwords are case sensitive.
You can secure a router by using a password to restrict access. Using a password and assigning privilege levels is a simple way to provide terminal access control in a network. A password can be established on individual lines, such as the console, and to the privileged EXEC mode. Passwords are case sensitive.
![]() By default, the console port does not require a password for console administrative access; however, you should always configure a console port line-level password. As shown in Example 2-1, you can use the line console 0 command followed by the login and password subcommands to require login and establish a login password on the console line.
By default, the console port does not require a password for console administrative access; however, you should always configure a console port line-level password. As shown in Example 2-1, you can use the line console 0 command followed by the login and password subcommands to require login and establish a login password on the console line.
R1(config)# line console 0
R1(config-line)# login
R1(config-line)# password M3rcury$09
![]() By default, Cisco routers support up to five simultaneous vty (Telnet) sessions. On the router, the vty ports are numbered from 0 through 4. As shown in Example 2-2, you can use the line vty 0 4 command followed by the login and password subcommands to require login and establish a login password on incoming Telnet sessions.
By default, Cisco routers support up to five simultaneous vty (Telnet) sessions. On the router, the vty ports are numbered from 0 through 4. As shown in Example 2-2, you can use the line vty 0 4 command followed by the login and password subcommands to require login and establish a login password on incoming Telnet sessions.
R1(config)# line vty 0 4
R1(config-line)# login
R1(config-line)# password V3nus$2009
![]() The enable secret password global command restricts access to the privileged EXEC mode. As shown in Example 2-3, you can use the enable secret global configuration command to configure the enable secret password. The enable secret password is always hashed inside the router configuration using a Message Digest 5 (MD5) hashing algorithm; it never appears in cleartext.
The enable secret password global command restricts access to the privileged EXEC mode. As shown in Example 2-3, you can use the enable secret global configuration command to configure the enable secret password. The enable secret password is always hashed inside the router configuration using a Message Digest 5 (MD5) hashing algorithm; it never appears in cleartext.
R1(config)# enable secret M1lkyway$09
![]() The enable password is also used to enter enable mode, but it is from earlier versions of Cisco IOS Software. By default, the enable password is not encrypted in the router configuration. The enable password global configuration command was kept for backward compatibility in case you downgrade the router to a version of Cisco IOS Software that does not support the enable secret password command. If both an enable password and an enable secret password are configured, the enable password is ignored. Example 2-4 demonstrates use of the enable password command.
The enable password is also used to enter enable mode, but it is from earlier versions of Cisco IOS Software. By default, the enable password is not encrypted in the router configuration. The enable password global configuration command was kept for backward compatibility in case you downgrade the router to a version of Cisco IOS Software that does not support the enable secret password command. If both an enable password and an enable secret password are configured, the enable password is ignored. Example 2-4 demonstrates use of the enable password command.
R1(config)# enable password earth
![]() If you forget the enable secret password, you have no alternative but to replace it using the Cisco router password recovery procedure specific to your Cisco equipment, which you can find in Cisco Document ID 6130 at http://www.cisco.com/en/US/products/sw/iosswrel/ps1831/products_tech_note09186a00801746e6.shtml.
If you forget the enable secret password, you have no alternative but to replace it using the Cisco router password recovery procedure specific to your Cisco equipment, which you can find in Cisco Document ID 6130 at http://www.cisco.com/en/US/products/sw/iosswrel/ps1831/products_tech_note09186a00801746e6.shtml.
![]() With the exception of the enable secret password, all Cisco router passwords are stored in plaintext by default within the router configuration. You can view these passwords with the show running-config command. Sniffers can also see these passwords if your TFTP server configuration files traverse an unsecured intranet or Internet connection. If an intruder gains access to the TFTP server where the router configuration files are stored, the intruder is able to obtain these passwords.
With the exception of the enable secret password, all Cisco router passwords are stored in plaintext by default within the router configuration. You can view these passwords with the show running-config command. Sniffers can also see these passwords if your TFTP server configuration files traverse an unsecured intranet or Internet connection. If an intruder gains access to the TFTP server where the router configuration files are stored, the intruder is able to obtain these passwords.
![]() As a safeguard against this possible exploit, the service password-encryption command encrypts all the passwords (except the previously hashed enable secret password) in the router configuration file, and will encrypt any passwords you set after entering this command until you turn the command off with the no form of the command. This method, which uses the Vigeneàre method explained in Chapter 4, “Fundamentals of Cryptography,” is not as safe as MD5, which is used with the enable secret command, but prevents casual discovery of the router line-level passwords. Example 2-5 shows how to configure the service password-encryption command. To remove the service password-encryption command, use no service password-encryption.
As a safeguard against this possible exploit, the service password-encryption command encrypts all the passwords (except the previously hashed enable secret password) in the router configuration file, and will encrypt any passwords you set after entering this command until you turn the command off with the no form of the command. This method, which uses the Vigeneàre method explained in Chapter 4, “Fundamentals of Cryptography,” is not as safe as MD5, which is used with the enable secret command, but prevents casual discovery of the router line-level passwords. Example 2-5 shows how to configure the service password-encryption command. To remove the service password-encryption command, use no service password-encryption.
![]() Also by default, Cisco router auxiliary ports do not require a password for remote administrative access. Administrators sometimes use this port to remotely configure and monitor the router using a dialup modem connection. To combat this vulnerability, you can use the line aux 0 command followed by the login and password subcommands to require login and establish a login password on an incoming auxiliary line.
Also by default, Cisco router auxiliary ports do not require a password for remote administrative access. Administrators sometimes use this port to remotely configure and monitor the router using a dialup modem connection. To combat this vulnerability, you can use the line aux 0 command followed by the login and password subcommands to require login and establish a login password on an incoming auxiliary line.
| Note |
|
R1(config)#service password-encryption
Setting Timeouts for Router Lines
![]() By default, an administrative interface stays active (and logged in) for 10 minutes after the last session activity. After that, the interface times out and logs out of the session. It is recommended that you fine-tune these timers to limit the amount of time to within a two- or three-minute maximum.
By default, an administrative interface stays active (and logged in) for 10 minutes after the last session activity. After that, the interface times out and logs out of the session. It is recommended that you fine-tune these timers to limit the amount of time to within a two- or three-minute maximum.
![]() You can adjust these timers using the exec-timeout command in line configuration mode for each of the line types that are used.
You can adjust these timers using the exec-timeout command in line configuration mode for each of the line types that are used.
![]() The syntax for this command is exec-timeout minutes [seconds]. Table 2-1 explains the variables.
The syntax for this command is exec-timeout minutes [seconds]. Table 2-1 explains the variables.
|
|
|
|---|---|
|
|
|
|
|
|
![]() Example 2-6 shows how to configure the console and auxiliary port timeouts for three and a half minutes.
Example 2-6 shows how to configure the console and auxiliary port timeouts for three and a half minutes.
R1(config)# line console 0
R1(config-line)# exec-timeout 3 30
R1(config-line)# exit
R1(config)# line aux 0
R1(config-line)# exec-timeout 3 30
R1(config)# line vty 0 4
R1(config-line)# exec-timeout 3 30
![]() You can also use the Cisco Router and Security Device Manager (SDM), introduced later in this chapter, to configure the exec-timeout for the vty lines.
You can also use the Cisco Router and Security Device Manager (SDM), introduced later in this chapter, to configure the exec-timeout for the vty lines.
Configuring the Minimum Length for Router Passwords
![]() Cisco IOS Software Release 12.3(1) and later allows you to set the minimum character length for all router passwords using the security passwords global configuration command. This command provides enhanced security access to the router by allowing you to specify a minimum password length (0 to 16 characters); this eliminates common passwords that are short and prevalent on most networks, such as lab and cisco. Example 2-7 demonstrates the security passwords command set for a minimum of 10 characters.
Cisco IOS Software Release 12.3(1) and later allows you to set the minimum character length for all router passwords using the security passwords global configuration command. This command provides enhanced security access to the router by allowing you to specify a minimum password length (0 to 16 characters); this eliminates common passwords that are short and prevalent on most networks, such as lab and cisco. Example 2-7 demonstrates the security passwords command set for a minimum of 10 characters.
R1(config)# security passwords min-length 10
![]() This command affects user passwords, enable passwords and enable secret passwords, and line passwords that are created after the command is executed. Existing router passwords remain unaffected.
This command affects user passwords, enable passwords and enable secret passwords, and line passwords that are created after the command is executed. Existing router passwords remain unaffected.
![]() It is highly recommended that you set your minimum password length to at least 10 characters. Never use a length of zero.
It is highly recommended that you set your minimum password length to at least 10 characters. Never use a length of zero.
![]() After the security passwords command has been enabled, any attempt to create a new password that is less than the specified length fails and results in an error message similar to this message:
After the security passwords command has been enabled, any attempt to create a new password that is less than the specified length fails and results in an error message similar to this message:
-
 Password too short - must be at least 10 characters. Password configuration failed.
Password too short - must be at least 10 characters. Password configuration failed.
Enhanced Username Password Security
![]() Cisco routers can maintain a list of usernames and passwords for performing local login authentication.
Cisco routers can maintain a list of usernames and passwords for performing local login authentication.
![]() Starting with Cisco IOS Software Release 12.0(18)S, system administrators can choose to use an MD5 hashing mechanism to encrypt a user password. MD5 hashing of passwords is a much better algorithm than the standard type 7 found in the service password-encryption command. The added layer of MD5 protection is useful in environments in which the password crosses the network or is stored on a TFTP server.
Starting with Cisco IOS Software Release 12.0(18)S, system administrators can choose to use an MD5 hashing mechanism to encrypt a user password. MD5 hashing of passwords is a much better algorithm than the standard type 7 found in the service password-encryption command. The added layer of MD5 protection is useful in environments in which the password crosses the network or is stored on a TFTP server.
![]() MD5 hashing of a Cisco IOS user password is accomplished with the username secret command in global configuration mode. Administrators can choose to enter a plaintext password for MD5 hashing by the router (option 0), or they can enter a previously encrypted MD5 secret (option 5). The syntax for the username secret command is as follows:
MD5 hashing of a Cisco IOS user password is accomplished with the username secret command in global configuration mode. Administrators can choose to enter a plaintext password for MD5 hashing by the router (option 0), or they can enter a previously encrypted MD5 secret (option 5). The syntax for the username secret command is as follows:
username name secret {[0] password | 5 encrypted-secret}
![]() Table 2-2 shows the parameters of the username secret command.
Table 2-2 shows the parameters of the username secret command.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Example 2-8 shows an example of the username secret command.
Example 2-8 shows an example of the username secret command.
R1(config)# username SecAdmin secret 0 Curium2008
R1(config)# username SecAdmin secret 5 $1$feb0$a104Qd9UZ./Ak00KTggPD0
Securing ROM Monitor
![]() By default, Cisco IOS routers allow a break sequence during startup that forces the router into ROM monitor mode. Once the router is in ROM monitor mode, anyone can choose to enter a new secret password using the well-known Cisco password recovery procedure. This procedure, if performed correctly, leaves the router configuration intact. This scenario presents a potential security breach because anyone who gains physical access to the router console port can enter ROM monitor, reset the enable secret password, and discover the router configuration.
By default, Cisco IOS routers allow a break sequence during startup that forces the router into ROM monitor mode. Once the router is in ROM monitor mode, anyone can choose to enter a new secret password using the well-known Cisco password recovery procedure. This procedure, if performed correctly, leaves the router configuration intact. This scenario presents a potential security breach because anyone who gains physical access to the router console port can enter ROM monitor, reset the enable secret password, and discover the router configuration.
![]() You can mitigate this potential security breach by using the no service password-recovery global configuration command, as shown in Example 2-9. The no service password-recovery command is a hidden Cisco IOS command and has no arguments or keywords.
You can mitigate this potential security breach by using the no service password-recovery global configuration command, as shown in Example 2-9. The no service password-recovery command is a hidden Cisco IOS command and has no arguments or keywords.
R1(config)# no service password-recovery
WARNING:
Executing this command will disable password recovery mechanism. Do not execute
this command without another plan for password recovery.
Are you sure you want to continue? [yes/no]: yes
R1(config)#
| Caution |
|
![]() When the no service password-recovery command is executed, the router boot sequence will look similar to the output shown in Example 2-10.
When the no service password-recovery command is executed, the router boot sequence will look similar to the output shown in Example 2-10.
System Bootstrap, Version 11.3(2)XA4, RELEASE SOFTWARE (fc1)
Copyright (c) 1999 by cisco Systems, Inc.
C2600 platform with 65536 Kbytes of main memory
PASSWORD RECOVERY FUNCTIONALITY IS DISABLED
program load complete, entry point: 0x80008000, size: 0xed9ee4
![]() Also, after the no service password-recovery command is executed, the show running-config command displays the no service password-recovery statement, as shown in Example 2-11.
Also, after the no service password-recovery command is executed, the show running-config command displays the no service password-recovery statement, as shown in Example 2-11.
Router# show running-config
!
version 12.0
service tcp-keepalives-in
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
service password-encryption
no service password-recovery
!
hostname Boston
| Note |
|
 Configuring Multiple Privilege Levels
Configuring Multiple Privilege Levels
![]() Cisco routers enable you to configure various privilege levels for your administrators. You can configure different passwords to control which administrators have access to the various privilege levels. Configuring various privilege levels is especially useful in a help desk environment where you want certain administrators to be able to configure and monitor every part of the router (level 15), while you want other administrators to only monitor, and not configure, the router (customized levels 2 to 14). There are 16 privilege levels, 0 to 15; level 0 is reserved for the user-level access privileges, levels 1 to 14 are levels you can customize, and level 15 is reserved for enable mode privileges.
Cisco routers enable you to configure various privilege levels for your administrators. You can configure different passwords to control which administrators have access to the various privilege levels. Configuring various privilege levels is especially useful in a help desk environment where you want certain administrators to be able to configure and monitor every part of the router (level 15), while you want other administrators to only monitor, and not configure, the router (customized levels 2 to 14). There are 16 privilege levels, 0 to 15; level 0 is reserved for the user-level access privileges, levels 1 to 14 are levels you can customize, and level 15 is reserved for enable mode privileges.
![]() To assign privileges to levels 2 to 14, use the privilege command from global configuration mode:
To assign privileges to levels 2 to 14, use the privilege command from global configuration mode:
privilege mode {level level command | reset command}
![]() Table 2-3 describes the parameters for this command and Example 2-12 demonstrates usage.
Table 2-3 describes the parameters for this command and Example 2-12 demonstrates usage.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
R1(config)# privilege exec level 2 ping
R1(config)# enable secret level 2 Cariboo2008
![]() To assign a password to the custom privilege level, use the command enable secret level level password in global configuration mode.
To assign a password to the custom privilege level, use the command enable secret level level password in global configuration mode.
![]() To enter a custom privilege level, use the command enable level and enter the password that was assigned to the custom privilege level.
To enter a custom privilege level, use the command enable level and enter the password that was assigned to the custom privilege level.
![]() Example 2-12 sets the ping command to require privilege level 2 or above access and establishes Cariboo2008 as the secret password for privilege level 2. When you enter the enable 2 command, as shown in Example 2-13, the router prompts you for the enable secret password for privilege level 2.
Example 2-12 sets the ping command to require privilege level 2 or above access and establishes Cariboo2008 as the secret password for privilege level 2. When you enter the enable 2 command, as shown in Example 2-13, the router prompts you for the enable secret password for privilege level 2.
![]() Use the show privilege command to display the current privilege level, as shown in Example 2-13.
Use the show privilege command to display the current privilege level, as shown in Example 2-13.
R1> enable 2
Password: Cariboo2008
R1#show privilege
Current privilege level is 2
 Configuring Role-Based Command-Line Interface Access
Configuring Role-Based Command-Line Interface Access
![]() The role-based command-line interface (CLI) access feature allows you to create different “views” of router configurations for different users. Views define which commands are accepted from different users and what configuration information is visible to them. With role-based CLI access, you can exercise better control over Cisco networking devices.
The role-based command-line interface (CLI) access feature allows you to create different “views” of router configurations for different users. Views define which commands are accepted from different users and what configuration information is visible to them. With role-based CLI access, you can exercise better control over Cisco networking devices.
| Note |
|
![]() The steps used to configure and confirm a view are as follows:
The steps used to configure and confirm a view are as follows:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The last two steps allow you to preview the views that you have configured. The next few pages discuss these commands in detail.
The last two steps allow you to preview the views that you have configured. The next few pages discuss these commands in detail.
![]() The key commands specific to configuring views for role-based CLI are shown a little later in this section in Example 2-14. When a system is in “root view,” it has all the access privileges as a user who has level 15 privileges. To configure any view for the system, you must be in the root view.
The key commands specific to configuring views for role-based CLI are shown a little later in this section in Example 2-14. When a system is in “root view,” it has all the access privileges as a user who has level 15 privileges. To configure any view for the system, you must be in the root view.
![]() The difference between a user who has level 15 privileges and a root view user is that a root view user can configure a new view and add or remove commands from the view.
The difference between a user who has level 15 privileges and a root view user is that a root view user can configure a new view and add or remove commands from the view.
![]() To access the root view, use first the enable view command and the parser view command:
To access the root view, use first the enable view command and the parser view command:
R1> enable view
R1# configure terminal
R1(config)# parser view view-name
![]() Table 2-4 shows the commands and parameters used to access and modify the root view.
Table 2-4 shows the commands and parameters used to access and modify the root view.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Next, you must assign the allowed commands to the selected view. Use the commands command in view configuration mode to assign the allowed commands. The syntax for this command is as follows:
Next, you must assign the allowed commands to the selected view. Use the commands command in view configuration mode to assign the allowed commands. The syntax for this command is as follows:
R1(config-view)# commands parser-mode {include | include-exclusive | exclude}
[all] [interface interface-name | command]
![]() Table 2-5 shows the parameters used with the commands command.
Table 2-5 shows the parameters used with the commands command.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Example 2-14 displays a complete configuration of a new view, called NetOps.
Example 2-14 displays a complete configuration of a new view, called NetOps.
R1> enable view
Password:
R1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# parser view NetOps
R1(config-view)# secret 0 hardtocrackpw
R1(config-view)# commands exec include ping
R1(config-view)# commands exec include all show
R1(config-view)# commands exec include telnet
R1(config-view)# commands exec include traceroute
R1(config-view)# commands exec include write
R1(config-view)# commands exec include configure
R1(config-view)# commands configure include access-list
R1(config-view)# commands configure include all interface
R1(config-view)# commands configure include all ip
![]() To verify a view, use the enable view command. Enter the name of the view that you want to verify and provide the password to log in to the view. After you are in the view, use the question mark (?) command to verify that the commands available in the view are correct. Example 2-15 shows the commands only accessible from the NetOps view at the privilege mode and at the configuration mode.
To verify a view, use the enable view command. Enter the name of the view that you want to verify and provide the password to log in to the view. After you are in the view, use the question mark (?) command to verify that the commands available in the view are correct. Example 2-15 shows the commands only accessible from the NetOps view at the privilege mode and at the configuration mode.
R1# enable view NetOps
Password: hardtocrackpw
R1#
Jan 3 13:45:03.887: %PARSER-6-VIEW_SWITCH: successfully set to view 'NetOps'.
R1#?
Exec commands:
configure Enter configuration mode
enable Turn on privileged commands
exit Exit from the EXEC
ping Send echo messages
show Show running system information
telnet Open a telnet connection
traceroute Trace route to destination
write Write running configuration to memory, network, or terminal
R1# configure terminal
R1(config)#?
Configure commands:
access-list Add an access list entry
do To run exec commands in config mode
exit Exit from configure mode
interface Select an interface to configure
ip Global IP configuration subcommands

0 comments
Post a Comment