Cisco Self-Defending Networks
![]() In the past, threats from internal and external sources moved slowly and it was easy to defend against them. Now Internet worms spread across the world in a matter of minutes. Security systems, and the network itself, must react instantaneously. As the nature of threats to organizations continues to evolve, the defense posture taken by network administrators and managers must also evolve.
In the past, threats from internal and external sources moved slowly and it was easy to defend against them. Now Internet worms spread across the world in a matter of minutes. Security systems, and the network itself, must react instantaneously. As the nature of threats to organizations continues to evolve, the defense posture taken by network administrators and managers must also evolve.
![]() The Cisco Self-Defending Network strategy describes the Cisco vision for security systems and helps customers more effectively manage and mitigate the risks to their networked business systems and applications.
The Cisco Self-Defending Network strategy describes the Cisco vision for security systems and helps customers more effectively manage and mitigate the risks to their networked business systems and applications.
 Changing Threats and Challenges
Changing Threats and Challenges
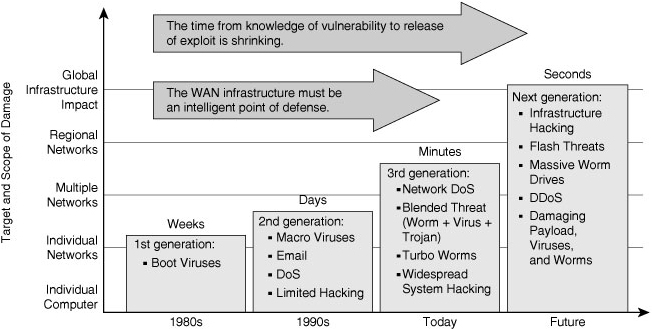
![]() Figure 1-24 shows how the threats that organizations face have evolved over the past few decades, and how the growth rate of vulnerabilities reported in operating systems and applications is rising. The number and variety of viruses and worms that have appeared over the past three years is daunting, and their rate of propagation is frightening. There have been unacceptable levels of business outages and expensive remediation projects that consume staff, time, and funds that were not originally budgeted for such tasks.
Figure 1-24 shows how the threats that organizations face have evolved over the past few decades, and how the growth rate of vulnerabilities reported in operating systems and applications is rising. The number and variety of viruses and worms that have appeared over the past three years is daunting, and their rate of propagation is frightening. There have been unacceptable levels of business outages and expensive remediation projects that consume staff, time, and funds that were not originally budgeted for such tasks.
![]() Figure 1-24 also shows that blended threats are evolving. A blended threat uses multiple means of propagation. These threats often have the characteristics of a virus; for example, they can attach themselves parasitically to email attachments. These threats self-replicate across a network with worm-like capability, and frequently search for and exploit a system or application vulnerability, or multiple vulnerabilities, to gain access to a host and deliver their payload. Some believe that blended threats might be evolving into “flash” threats that could exploit new, unknown vulnerabilities, and have the capability to propagate across the Internet in seconds, seriously affecting the Internet on a global scale.
Figure 1-24 also shows that blended threats are evolving. A blended threat uses multiple means of propagation. These threats often have the characteristics of a virus; for example, they can attach themselves parasitically to email attachments. These threats self-replicate across a network with worm-like capability, and frequently search for and exploit a system or application vulnerability, or multiple vulnerabilities, to gain access to a host and deliver their payload. Some believe that blended threats might be evolving into “flash” threats that could exploit new, unknown vulnerabilities, and have the capability to propagate across the Internet in seconds, seriously affecting the Internet on a global scale.
![]() Also, notice on Figure 1-24 that the trends are becoming regional and global in nature. Early attacks affected single systems or one organization’s network. In contrast, more recent attacks are affecting entire regions. For example, attacks have expanded from individual DoS attacks from a single attacker against a single target to large-scale DDoS attacks emanating from networks of compromised systems known as botnets.
Also, notice on Figure 1-24 that the trends are becoming regional and global in nature. Early attacks affected single systems or one organization’s network. In contrast, more recent attacks are affecting entire regions. For example, attacks have expanded from individual DoS attacks from a single attacker against a single target to large-scale DDoS attacks emanating from networks of compromised systems known as botnets.
![]() Threats are also becoming persistent. After an attack starts, attacks might appear in waves as infected systems join the network. Because infections are so complex and have so many end users (employees, vendors, and contractors), multiple types of endpoints (company desktop, home, and server), and multiple types of access (wired, wireless, VPN, and dialup), infections are difficult to eradicate.
Threats are also becoming persistent. After an attack starts, attacks might appear in waves as infected systems join the network. Because infections are so complex and have so many end users (employees, vendors, and contractors), multiple types of endpoints (company desktop, home, and server), and multiple types of access (wired, wireless, VPN, and dialup), infections are difficult to eradicate.
![]() Network-dependent enterprises constantly face security dilemmas in the typical business environment. You can no longer secure networks just by securing the network perimeter. Businesses have consolidated their data centers, converged internal networks, and embraced the Internet. Environments that were once self-contained and controlled are now open to partners through business-to-business extranets, retail outlet connections, and home-based employees. By extending the corporate network, the trust boundary has extended across untrusted intermediate networks and into uncontrolled environments.
Network-dependent enterprises constantly face security dilemmas in the typical business environment. You can no longer secure networks just by securing the network perimeter. Businesses have consolidated their data centers, converged internal networks, and embraced the Internet. Environments that were once self-contained and controlled are now open to partners through business-to-business extranets, retail outlet connections, and home-based employees. By extending the corporate network, the trust boundary has extended across untrusted intermediate networks and into uncontrolled environments.
![]() The growing list of devices that access networks poses more problems. Many devices do not comply with corporate policies. Network users often use compliant devices to access other uncontrolled networks before connecting into the corporate network. As a result, devices on these external networks can become conduits for attacks and related misuse. The following are some of the issues that concern network security experts:
The growing list of devices that access networks poses more problems. Many devices do not comply with corporate policies. Network users often use compliant devices to access other uncontrolled networks before connecting into the corporate network. As a result, devices on these external networks can become conduits for attacks and related misuse. The following are some of the issues that concern network security experts:
-
 Common application interfaces: The emergence of common application interfaces based on messaging protocols, such as Extensible Markup Language (XML) and SOAP, formally known as Simple Object Access Protocol, has increased e-commerce and corporate productivity. However, similar to most new technologies, these new message protocols have introduced an entirely new set of vulnerabilities and attack vectors that corporations need to protect. In the past, firewall policies would filter data carried across many network protocols. Now, single transport protocols, such as HTTP on TCP port 80, transport that data. As a result, much of the data that previously resided in packet headers now resides in the packet payload. This change creates significant processing challenges that make it easier for an attacker to evade classic network defenses.
Common application interfaces: The emergence of common application interfaces based on messaging protocols, such as Extensible Markup Language (XML) and SOAP, formally known as Simple Object Access Protocol, has increased e-commerce and corporate productivity. However, similar to most new technologies, these new message protocols have introduced an entirely new set of vulnerabilities and attack vectors that corporations need to protect. In the past, firewall policies would filter data carried across many network protocols. Now, single transport protocols, such as HTTP on TCP port 80, transport that data. As a result, much of the data that previously resided in packet headers now resides in the packet payload. This change creates significant processing challenges that make it easier for an attacker to evade classic network defenses. -
 Security hampering policy: To meet the data confidentiality and integrity requirements of corporations, more applications are using Secure Sockets Layer (SSL), Transport Layer Security (TLS), and HTTPS protocols to encrypt application-level traffic. This trend makes it much harder for IT departments to enforce corporate access policies at the network perimeter, because they cannot inspect the packet payloads of those encrypted flows. Many organizations mistakenly assume that if they comply with regulations, their infrastructure is more secure, which is frequently not the case. Following the law of unintended consequences, the very act of creating compliance can introduce new vulnerabilities. For example, worms and viruses can spread more effectively in a network supporting end-to-end VPNs because the intermediate nodes have no visibility into the traversing traffic. Such traffic can carry worms to sensitive corporate servers in a secure, encrypted packet. End-to-end VPNs can make it more difficult to remediate the problem and it can take longer to diagnose such an attack.
Security hampering policy: To meet the data confidentiality and integrity requirements of corporations, more applications are using Secure Sockets Layer (SSL), Transport Layer Security (TLS), and HTTPS protocols to encrypt application-level traffic. This trend makes it much harder for IT departments to enforce corporate access policies at the network perimeter, because they cannot inspect the packet payloads of those encrypted flows. Many organizations mistakenly assume that if they comply with regulations, their infrastructure is more secure, which is frequently not the case. Following the law of unintended consequences, the very act of creating compliance can introduce new vulnerabilities. For example, worms and viruses can spread more effectively in a network supporting end-to-end VPNs because the intermediate nodes have no visibility into the traversing traffic. Such traffic can carry worms to sensitive corporate servers in a secure, encrypted packet. End-to-end VPNs can make it more difficult to remediate the problem and it can take longer to diagnose such an attack. -
 Blurred perimeters: The wireless and mobile network within an enterprise now supports laptops, personal digital assistants (PDA), and mobile phones that have more than one network connection. These multihomed hosts are capable of establishing impromptu wireless networks to enable peer-to-peer communication. In addition, these devices effectively forward packets at the application level. As a result, network boundaries become much more ambiguous. To manage a secure system and maintain network availability, corporations must be able to extend a control point onto these mobile devices.
Blurred perimeters: The wireless and mobile network within an enterprise now supports laptops, personal digital assistants (PDA), and mobile phones that have more than one network connection. These multihomed hosts are capable of establishing impromptu wireless networks to enable peer-to-peer communication. In addition, these devices effectively forward packets at the application level. As a result, network boundaries become much more ambiguous. To manage a secure system and maintain network availability, corporations must be able to extend a control point onto these mobile devices.
![]() To illustrate the seriousness of network vulnerabilities, consider the effects of the SQL Slammer worm, first seen on January 25, 2003:
To illustrate the seriousness of network vulnerabilities, consider the effects of the SQL Slammer worm, first seen on January 25, 2003:
-
 Saturation point was reached within two hours of the start of infection.
Saturation point was reached within two hours of the start of infection. -
 Infections doubled every 8.5 seconds.
Infections doubled every 8.5 seconds. -
 SQL Slammer spread 100 times faster than Code Red.
SQL Slammer spread 100 times faster than Code Red. -
 At its peak, SQL Slammer scanned 55 million hosts per second.
At its peak, SQL Slammer scanned 55 million hosts per second. -
 The number of hosts infected was between 250,000 and 300,000.
The number of hosts infected was between 250,000 and 300,000. -
 Internet connectivity was affected worldwide.
Internet connectivity was affected worldwide.
![]() Source: Cooperative Association for Internet Data Analysis (CAIDA) and the University of California at San Diego.
Source: Cooperative Association for Internet Data Analysis (CAIDA) and the University of California at San Diego.
![]() SQL Slammer compromised 90 percent of vulnerable systems within the first 10 minutes, and doubled in size every 8.5 seconds. Within the first 3 minutes, it achieved its maximum scanning rate of more than 55 million scans per second.
SQL Slammer compromised 90 percent of vulnerable systems within the first 10 minutes, and doubled in size every 8.5 seconds. Within the first 3 minutes, it achieved its maximum scanning rate of more than 55 million scans per second.
 Building a Cisco Self-Defending Network
Building a Cisco Self-Defending Network
![]() A Cisco Self-Defending Network uses the network to identify, prevent, and adapt to threats. Unlike point-solution strategies, in which you purchase products individually without consideration for which products work best together, a network-based approach is a strategic approach that meets the current challenges and evolves your security capability to keep ahead of the curve.
A Cisco Self-Defending Network uses the network to identify, prevent, and adapt to threats. Unlike point-solution strategies, in which you purchase products individually without consideration for which products work best together, a network-based approach is a strategic approach that meets the current challenges and evolves your security capability to keep ahead of the curve.
![]() The following are key principles of a Cisco Self-Defending Network:
The following are key principles of a Cisco Self-Defending Network:
-
 Integrate security throughout the existing infrastructure. Security should be built in, not bolted on.
Integrate security throughout the existing infrastructure. Security should be built in, not bolted on. -
 There should be collaboration between security and the network so that they leverage off each other and work together.
There should be collaboration between security and the network so that they leverage off each other and work together. -
 The network should have the capability to intelligently evolve and adapt to emerging threats.
The network should have the capability to intelligently evolve and adapt to emerging threats.
![]() Cisco Self-Defending Network increases the value of your investment over time (contrary to point solutions, where the costs increase over time due to posture erosion, inconsistencies, and complexities).
Cisco Self-Defending Network increases the value of your investment over time (contrary to point solutions, where the costs increase over time due to posture erosion, inconsistencies, and complexities).
![]() A common infrastructure offers savings over time while supporting business transformations. A common infrastructure allows simplified management, which greatly reduces the evolution of gaps in controls that typically materialize over time. Management is more likely to be correctly and consistently performed when it is simplified, which allows the identification of gaps before they become disabling vulnerabilities in the posture.
A common infrastructure offers savings over time while supporting business transformations. A common infrastructure allows simplified management, which greatly reduces the evolution of gaps in controls that typically materialize over time. Management is more likely to be correctly and consistently performed when it is simplified, which allows the identification of gaps before they become disabling vulnerabilities in the posture.
![]() The process of assessing the environment, identifying gaps, applying changes, and ultimately auditing those controls becomes much more efficient when you have more consistent controls and visibility.
The process of assessing the environment, identifying gaps, applying changes, and ultimately auditing those controls becomes much more efficient when you have more consistent controls and visibility.
![]() An additional compelling argument for a Cisco Self-Defending Network design is the reality that introducing a common infrastructure falls within the scope of the other strategies for implementation. Specifically, each strategy is governed by product life cycle management. In spite of strategy differences, you can acquire the products that make up the infrastructure based on the traditional technology refresh cycles by which many IT organizations abide.
An additional compelling argument for a Cisco Self-Defending Network design is the reality that introducing a common infrastructure falls within the scope of the other strategies for implementation. Specifically, each strategy is governed by product life cycle management. In spite of strategy differences, you can acquire the products that make up the infrastructure based on the traditional technology refresh cycles by which many IT organizations abide.
![]() The Cisco Self-Defending Network approach is comprehensive and covers the following aspects of security using specific tools:
The Cisco Self-Defending Network approach is comprehensive and covers the following aspects of security using specific tools:
-
 Policy-based management through Cisco Security Manager.
Policy-based management through Cisco Security Manager. -
 Threat management through Cisco Security Monitoring, Analysis, and Response System (MARS).
Threat management through Cisco Security Monitoring, Analysis, and Response System (MARS). -
 Network security through Cisco IOS Software, Cisco ASAs, and Cisco IPS Sensor Software.
Network security through Cisco IOS Software, Cisco ASAs, and Cisco IPS Sensor Software. -
 Endpoint security through Cisco NAC appliances and Cisco Security Agent.
Endpoint security through Cisco NAC appliances and Cisco Security Agent.
![]() The following are additional benefits that result from this comprehensive, integrated approach:
The following are additional benefits that result from this comprehensive, integrated approach:
-
 360 degree-visibility and protection: Delivers comprehensive and proactive network defense
360 degree-visibility and protection: Delivers comprehensive and proactive network defense Infrastructurewide threat intelligence that is cost-effectively delivered across a variety of systems and devices.
Infrastructurewide threat intelligence that is cost-effectively delivered across a variety of systems and devices. Multivector threat identification captures policy violations, vulnerability exploits, and anomalous behavior.
Multivector threat identification captures policy violations, vulnerability exploits, and anomalous behavior. -
 Simplified control: Streamlines policy and management across the network
Simplified control: Streamlines policy and management across the network Networkwide policy management.
Networkwide policy management. Infrastructurewide implementation across a variety of systems and devices.
Infrastructurewide implementation across a variety of systems and devices. -
 Proactive business protection: Ensures the operations of the enterprise
Proactive business protection: Ensures the operations of the enterprise Unparalleled collaboration and correlation across systems, endpoints, and management enables adaptive response to real-time threats.
Unparalleled collaboration and correlation across systems, endpoints, and management enables adaptive response to real-time threats. Key element of the Cisco Self-Defending Network strategy.
Key element of the Cisco Self-Defending Network strategy.
![]() This enhanced threat control and containment solution portfolio delivers comprehensive threat protection across the entire infrastructure, ensuring business continuity and strengthening the Self-Defending Network vision.
This enhanced threat control and containment solution portfolio delivers comprehensive threat protection across the entire infrastructure, ensuring business continuity and strengthening the Self-Defending Network vision.
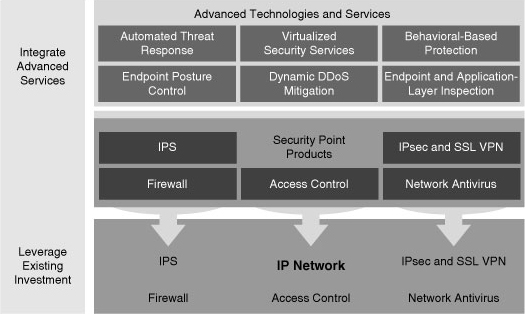
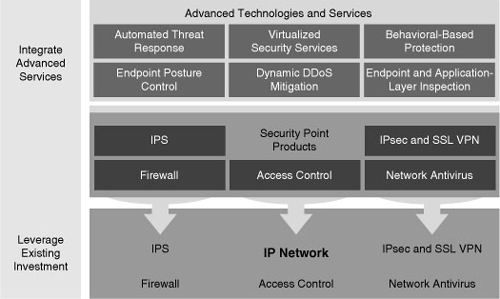
![]() A Cisco Self-Defending Network starts with a secure network platform, as shown in Figure 1-25, which is a strong, secure, flexible base from which you build your own Cisco Self-Defending Network solution.
A Cisco Self-Defending Network starts with a secure network platform, as shown in Figure 1-25, which is a strong, secure, flexible base from which you build your own Cisco Self-Defending Network solution.
![]() With security integrated into the very fabric of the network, security becomes an integral and fundamental network feature. The next step, as shown in Figure 1-25, is to layer advanced technologies and security services, where and when you need them, on to this platform. The following are solutions for advanced technologies and security services:
With security integrated into the very fabric of the network, security becomes an integral and fundamental network feature. The next step, as shown in Figure 1-25, is to layer advanced technologies and security services, where and when you need them, on to this platform. The following are solutions for advanced technologies and security services:
-
 Threat control and containment: Keep your employees productive against a challenging and ever-changing threat landscape.
Threat control and containment: Keep your employees productive against a challenging and ever-changing threat landscape. -
 Secure communications: Ensure the confidentiality and privacy of all of your sensitive communications, whether it is data communication, voice communication, or wireless communication.
Secure communications: Ensure the confidentiality and privacy of all of your sensitive communications, whether it is data communication, voice communication, or wireless communication. -
 Tools for operational control and policy management: Add a suite of tools that comprise a framework for operational control and policy management that span your security end to end.
Tools for operational control and policy management: Add a suite of tools that comprise a framework for operational control and policy management that span your security end to end.
![]() Whether you are a large enterprise or commercial customer, these solution components comprise a complete Cisco Self-Defending Network.
Whether you are a large enterprise or commercial customer, these solution components comprise a complete Cisco Self-Defending Network.
Threat Control and Containment
![]() The Cisco Threat Control and Containment solution offers comprehensive protection for your network through networkwide visibility, simplified policy control, and proactive system protection.
The Cisco Threat Control and Containment solution offers comprehensive protection for your network through networkwide visibility, simplified policy control, and proactive system protection.
![]() The Cisco Threat Control and Containment solution is part of the Cisco Self-Defending Network, which protects the network, servers, endpoints, and information. The Cisco Threat Control and Containment solution regulates network access, isolates infected systems, prevents intrusions, and protects critical business assets. It counteracts malicious traffic such as worms, viruses, and malware before they affect your business, by using centralized policy, configuration, and threat event management.
The Cisco Threat Control and Containment solution is part of the Cisco Self-Defending Network, which protects the network, servers, endpoints, and information. The Cisco Threat Control and Containment solution regulates network access, isolates infected systems, prevents intrusions, and protects critical business assets. It counteracts malicious traffic such as worms, viruses, and malware before they affect your business, by using centralized policy, configuration, and threat event management.
![]() The Cisco Threat Control and Containment Solution contains three elements:
The Cisco Threat Control and Containment Solution contains three elements:
-
 Threat control for endpoints: This element defends against threats most commonly introduced by Internet use, such as viruses, spyware, and other malicious content that may lead to data loss and degrade productivity.
Threat control for endpoints: This element defends against threats most commonly introduced by Internet use, such as viruses, spyware, and other malicious content that may lead to data loss and degrade productivity. Cisco products that provide threat control for endpoints include the Cisco Security Agent for Desktops, Cisco ASA 5500 series (Content Security Edition), Cisco Integrated Services Routers, Cisco IPS, and Cisco NAC appliances.
Cisco products that provide threat control for endpoints include the Cisco Security Agent for Desktops, Cisco ASA 5500 series (Content Security Edition), Cisco Integrated Services Routers, Cisco IPS, and Cisco NAC appliances. -
 Threat control for infrastructure: This element safeguards your server and application infrastructure against attacks and intrusions. It also defends against internal and external attempts to penetrate or attack servers and information resources through application and operating system vulnerabilities.
Threat control for infrastructure: This element safeguards your server and application infrastructure against attacks and intrusions. It also defends against internal and external attempts to penetrate or attack servers and information resources through application and operating system vulnerabilities. Products that provide threat control for the infrastructure include the Cisco Security Agent for Servers, Cisco IPS, Cisco firewall solutions including the Cisco ASA 5500 series and Cisco Catalyst 6500 series Firewall Services Module, Cisco ACE (Application Control Engine) Module, Cisco AVS Application Velocity System, XML security, Cisco Security MARS, and Cisco Security Manager.
Products that provide threat control for the infrastructure include the Cisco Security Agent for Servers, Cisco IPS, Cisco firewall solutions including the Cisco ASA 5500 series and Cisco Catalyst 6500 series Firewall Services Module, Cisco ACE (Application Control Engine) Module, Cisco AVS Application Velocity System, XML security, Cisco Security MARS, and Cisco Security Manager. -
 Threat control for email: This element protects your business productivity, resource availability, and confidential information by stopping email-initiated threats. Cisco provides solutions to protect from threats contained in email, such as the Content Security and Control Security Services Module used in the Cisco ASA firewall and the IronPort appliance.
Threat control for email: This element protects your business productivity, resource availability, and confidential information by stopping email-initiated threats. Cisco provides solutions to protect from threats contained in email, such as the Content Security and Control Security Services Module used in the Cisco ASA firewall and the IronPort appliance.
Secure Communications
![]() Ensuring the privacy and integrity of all information is vital to your business. You can achieve this through the use of IPsec and SSL VPNs. As your company uses the flexibility and cost-effectiveness of the Internet to extend its network to branch offices, telecommuters, customers, and partners, security is paramount. You must create a manageable, cost-effective communications infrastructure that will do the following:
Ensuring the privacy and integrity of all information is vital to your business. You can achieve this through the use of IPsec and SSL VPNs. As your company uses the flexibility and cost-effectiveness of the Internet to extend its network to branch offices, telecommuters, customers, and partners, security is paramount. You must create a manageable, cost-effective communications infrastructure that will do the following:
-
 Improve productivity
Improve productivity -
 Enable new business applications
Enable new business applications -
 Help you comply with information privacy regulations
Help you comply with information privacy regulations -
 Enhance business efficiency
Enhance business efficiency
![]() The Cisco Secure Communications solution is a set of products and security life cycle services that are an essential element of the Cisco Self-Defending Network. By incorporating capabilities that secure the network, the endpoints, and the applications and messages, this systems-based approach delivers comprehensive security of your communications. The solution has two major elements:
The Cisco Secure Communications solution is a set of products and security life cycle services that are an essential element of the Cisco Self-Defending Network. By incorporating capabilities that secure the network, the endpoints, and the applications and messages, this systems-based approach delivers comprehensive security of your communications. The solution has two major elements:
-
 Secure communications for remote access: This element provides highly secure, customizable access to corporate networks and applications by establishing an encrypted tunnel across the Internet.
Secure communications for remote access: This element provides highly secure, customizable access to corporate networks and applications by establishing an encrypted tunnel across the Internet. -
 Secure communications for site-to-site connections: This element provides an Internet-based WAN infrastructure for connecting branch offices, home offices, or the sites of business partners to all or portions of your network.
Secure communications for site-to-site connections: This element provides an Internet-based WAN infrastructure for connecting branch offices, home offices, or the sites of business partners to all or portions of your network.
| Tip |
|
Operational Control and Policy Management
![]() Cisco network management systems help you automate, simplify, and integrate your network to reduce operational costs and improve productivity. Built to complement the popular CiscoWorks products, the tools within the network management systems provide innovative ways to centrally manage your network to achieve critical functions such as availability, responsiveness, resilience, and security in a consistent way.
Cisco network management systems help you automate, simplify, and integrate your network to reduce operational costs and improve productivity. Built to complement the popular CiscoWorks products, the tools within the network management systems provide innovative ways to centrally manage your network to achieve critical functions such as availability, responsiveness, resilience, and security in a consistent way.
![]() These network management systems also help reduce the troubleshooting and planning time associated with the introduction of new services such as voice, wireless, and security management. Solutions-focused tools streamline network management systems, including the management of devices, configurations, users, and services.
These network management systems also help reduce the troubleshooting and planning time associated with the introduction of new services such as voice, wireless, and security management. Solutions-focused tools streamline network management systems, including the management of devices, configurations, users, and services.
![]() The benefits of the different Cisco network management systems include the following:
The benefits of the different Cisco network management systems include the following:
-
 Increase speed and accuracy of policy deployment
Increase speed and accuracy of policy deployment -
 Gain visibility to monitor end-to-end security
Gain visibility to monitor end-to-end security -
 Respond to threats more rapidly
Respond to threats more rapidly -
 Enforce corporate policy compliance
Enforce corporate policy compliance -
 Enable proper workflow management
Enable proper workflow management
Cisco Security Management Suite
![]() The Cisco Security Management Suite is a framework of products and technologies designed for scalable policy administration and enforcement for the Cisco Self-Defending Network. This integrated solution can simplify and automate the tasks associated with security management operations, including configuration, monitoring, analysis, and response. There are two main components of the Cisco Security Management Suite: Cisco Security Manager and Cisco Security MARS.
The Cisco Security Management Suite is a framework of products and technologies designed for scalable policy administration and enforcement for the Cisco Self-Defending Network. This integrated solution can simplify and automate the tasks associated with security management operations, including configuration, monitoring, analysis, and response. There are two main components of the Cisco Security Management Suite: Cisco Security Manager and Cisco Security MARS.
Cisco Security Manager
![]() Cisco Security Manager is a powerful but easy-to-use solution that enables you to centrally provision all aspects of device configurations and security policies for the Cisco family of security products. The solution is effective for managing even small networks consisting of fewer than 10 devices, but also scales to efficiently manage large-scale networks composed of thousands of devices. Scalability is achieved through intelligent policy-based management techniques that can simplify administration. Cisco Security Manager features include the following:
Cisco Security Manager is a powerful but easy-to-use solution that enables you to centrally provision all aspects of device configurations and security policies for the Cisco family of security products. The solution is effective for managing even small networks consisting of fewer than 10 devices, but also scales to efficiently manage large-scale networks composed of thousands of devices. Scalability is achieved through intelligent policy-based management techniques that can simplify administration. Cisco Security Manager features include the following:
-
 It enables administrators to effectively manage configuration for Cisco IPS 4200 series sensors, the Cisco ASA Advanced Inspection and Prevention Security Services Module (AIP-SSM), the Cisco Catalyst 6500 Series Intrusion Detection System Services Module 2 (IDSM-2), the Cisco IDS Network Module, the Cisco IPS AIM, and Cisco IOS IPS.
It enables administrators to effectively manage configuration for Cisco IPS 4200 series sensors, the Cisco ASA Advanced Inspection and Prevention Security Services Module (AIP-SSM), the Cisco Catalyst 6500 Series Intrusion Detection System Services Module 2 (IDSM-2), the Cisco IDS Network Module, the Cisco IPS AIM, and Cisco IOS IPS. -
 It responds faster to threats by enabling you to define and assign new security policies to thousands of devices in a few simple steps.
It responds faster to threats by enabling you to define and assign new security policies to thousands of devices in a few simple steps. -
 It has a rich graphical user interface that provides superior ease of use.
It has a rich graphical user interface that provides superior ease of use. -
 Multiple views provide flexible methods to manage devices and policies, including the ability to manage the security network visually on a topology map.
Multiple views provide flexible methods to manage devices and policies, including the ability to manage the security network visually on a topology map. -
 It contains extensive animated help for the new user, which reduces the learning time.
It contains extensive animated help for the new user, which reduces the learning time. -
 It enables you to centrally specify which policies are shared and automatically inherited by new devices to ensure corporate policies are implemented consistently, while providing optional flexibility.
It enables you to centrally specify which policies are shared and automatically inherited by new devices to ensure corporate policies are implemented consistently, while providing optional flexibility. -
 It integrates with Cisco Secure Access Control Server (ACS) to provide granular roll-based access control to devices and management functions.
It integrates with Cisco Secure Access Control Server (ACS) to provide granular roll-based access control to devices and management functions. -
 It integrates with Cisco Security MARS to correlate events with the associated firewall rules to help make quicker decisions and increase network uptime.
It integrates with Cisco Security MARS to correlate events with the associated firewall rules to help make quicker decisions and increase network uptime. -
 It enables you to assign specific tasks to each administrator during the deployment of a policy, with formal change control and tracking, and allows the security and network operations staff to work together as a single team with effective coordination.
It enables you to assign specific tasks to each administrator during the deployment of a policy, with formal change control and tracking, and allows the security and network operations staff to work together as a single team with effective coordination.
Cisco Security MARS
![]() Cisco Security MARS provides security monitoring for network security devices and host applications made by Cisco and other providers. Cisco Security MARS offers these benefits:
Cisco Security MARS provides security monitoring for network security devices and host applications made by Cisco and other providers. Cisco Security MARS offers these benefits:
-
 Greatly reduces false positives by providing an end-to-end view of the network
Greatly reduces false positives by providing an end-to-end view of the network -
 Defines the most effective mitigation responses by understanding the configuration and topology of your environment
Defines the most effective mitigation responses by understanding the configuration and topology of your environment -
 Promotes awareness of environmental anomalies with network behavior analysis using NetFlow
Promotes awareness of environmental anomalies with network behavior analysis using NetFlow -
 Provides quick and easy access to audit compliance reports with more than 150 ready-to-use customizable reports
Provides quick and easy access to audit compliance reports with more than 150 ready-to-use customizable reports -
 Makes precise recommendations for threat removal, including the ability to visualize the attack path and identify the source of the threat with detailed topological graphs that simplify security response at Layer 2 and above
Makes precise recommendations for threat removal, including the ability to visualize the attack path and identify the source of the threat with detailed topological graphs that simplify security response at Layer 2 and above
| Tip |
|
 Cisco Integrated Security Portfolio
Cisco Integrated Security Portfolio
![]() A truly secure network requires multiple products and technologies that collaborate seamlessly across platforms and integrate tightly with the network infrastructure, as shown in Figure 1-26. No single product or technology can secure a network.
A truly secure network requires multiple products and technologies that collaborate seamlessly across platforms and integrate tightly with the network infrastructure, as shown in Figure 1-26. No single product or technology can secure a network.
![]() Cisco offers the broadest portfolio of integrated security products in the industry. No other vendor has such a diversity of platforms. Benefits of a comprehensive Cisco architecture include the following:
Cisco offers the broadest portfolio of integrated security products in the industry. No other vendor has such a diversity of platforms. Benefits of a comprehensive Cisco architecture include the following:
-
 Increase speed and accuracy of policy deployment
Increase speed and accuracy of policy deployment -
 Gain visibility to monitor end-to-end security
Gain visibility to monitor end-to-end security -
 Respond to threats more rapidly
Respond to threats more rapidly -
 Enforce corporate policy compliance
Enforce corporate policy compliance -
 Enable proper workflow management
Enable proper workflow management
![]() The Cisco portfolio is designed to meet the requirements and diverse deployment models of any network and any environment. The following are some of these products:
The Cisco portfolio is designed to meet the requirements and diverse deployment models of any network and any environment. The following are some of these products:
-
 Cisco IOS platforms with integrated IPS, VPN, and stateful firewall to support secure IP connectivity
Cisco IOS platforms with integrated IPS, VPN, and stateful firewall to support secure IP connectivity -
 Cisco ASA 5500 series appliances with integrated VPN to ensure perimeter security, access control, and IPS
Cisco ASA 5500 series appliances with integrated VPN to ensure perimeter security, access control, and IPS -
 Cisco PIX 500 series security appliances with integrated VPN to ensure perimeter security and access control
Cisco PIX 500 series security appliances with integrated VPN to ensure perimeter security and access control -
 Appliance-based network IDS and IPS and integrated network IDS and IPS for Cisco IOS routers, Cisco PIX security appliances, and Cisco ASAs
Appliance-based network IDS and IPS and integrated network IDS and IPS for Cisco IOS routers, Cisco PIX security appliances, and Cisco ASAs -
 Cisco Security Agent endpoint protection software, which protects servers and desktops from the damaging effects of known and unknown threats
Cisco Security Agent endpoint protection software, which protects servers and desktops from the damaging effects of known and unknown threats -
 Cisco Secure ACS, which ensures that users have the proper authority to access corporate resources
Cisco Secure ACS, which ensures that users have the proper authority to access corporate resources -
 Security modules for Cisco Catalyst 6500 series switches and Cisco 7600 series routers that provide security throughout the data center
Security modules for Cisco Catalyst 6500 series switches and Cisco 7600 series routers that provide security throughout the data center -
 Security management products, including Cisco Security Manager, Cisco Security MARS, Cisco Router and Security Device Manager (SDM), and other GUI-based device managers
Security management products, including Cisco Security Manager, Cisco Security MARS, Cisco Router and Security Device Manager (SDM), and other GUI-based device managers
![]() Most customers will not adopt all the components of the Cisco Self-Defending Network at one time, because it can be difficult to overhaul all the required subsystems simultaneously without disrupting the integrity of the IT services. Some customers might hesitate to turn over security controls to an automated system until they are confident that the system will operate dependably. The Cisco Self-Defending Network initiative deals with these concerns by first providing products that you can usefully deploy independently of one another and then by offering solutions that can link these products together as confidence builds in each product and subsystem. This initiative has proven to be a successful approach based on a combination of product development, product acquisition, systems development, and partnering.
Most customers will not adopt all the components of the Cisco Self-Defending Network at one time, because it can be difficult to overhaul all the required subsystems simultaneously without disrupting the integrity of the IT services. Some customers might hesitate to turn over security controls to an automated system until they are confident that the system will operate dependably. The Cisco Self-Defending Network initiative deals with these concerns by first providing products that you can usefully deploy independently of one another and then by offering solutions that can link these products together as confidence builds in each product and subsystem. This initiative has proven to be a successful approach based on a combination of product development, product acquisition, systems development, and partnering.
Summary
![]() To have a comprehensive security solution, it is important to cover all aspects of the operation of an organization. Comprehensive security requires suitable reliance on technical, physical, and administrative controls; implementing defense in depth; and developing an all-inclusive security policy. You will also be required to demonstrate forward thinking, taking into consideration the threats of tomorrow.
To have a comprehensive security solution, it is important to cover all aspects of the operation of an organization. Comprehensive security requires suitable reliance on technical, physical, and administrative controls; implementing defense in depth; and developing an all-inclusive security policy. You will also be required to demonstrate forward thinking, taking into consideration the threats of tomorrow.
![]() In this chapter you have learned that
In this chapter you have learned that
-
 To provide a comprehensive security solution, it is essential that there be a combination of technical, physical, and administrative controls in place.
To provide a comprehensive security solution, it is essential that there be a combination of technical, physical, and administrative controls in place. -
 Defense in depth is a philosophy used to provide layered security to a system by using multiple security mechanisms.
Defense in depth is a philosophy used to provide layered security to a system by using multiple security mechanisms. -
 Operations security is concerned with the controls used to protect hardware, software, and media on a day-to-day basis.
Operations security is concerned with the controls used to protect hardware, software, and media on a day-to-day basis. -
 A security policy is a set of objectives for the company, rules of behavior for users and administrators, and requirements for system and management that collectively ensure the security of network and computer systems in an organization.
A security policy is a set of objectives for the company, rules of behavior for users and administrators, and requirements for system and management that collectively ensure the security of network and computer systems in an organization. -
 Changing threats and challenges demand a new approach to network security, one that is quickly adaptable, such as the Cisco Self-Defending Network.
Changing threats and challenges demand a new approach to network security, one that is quickly adaptable, such as the Cisco Self-Defending Network.
 References
References
![]() For additional information, refer to these resources:
For additional information, refer to these resources:
-
 Richardson, R. 2007 CSI Computer Crime and Security Survey, http://i.cmpnet.com/v2.gocsi.com/pdf/CSISurvey2007.pdf
Richardson, R. 2007 CSI Computer Crime and Security Survey, http://i.cmpnet.com/v2.gocsi.com/pdf/CSISurvey2007.pdf -
 Harris, S. CISSP All-in-One Exam Guide, Third Edition (McGraw Hill Osborne, 2005)
Harris, S. CISSP All-in-One Exam Guide, Third Edition (McGraw Hill Osborne, 2005) -
 The Jargon File, http://www.catb.org/~esr/jargon/html/index.html
The Jargon File, http://www.catb.org/~esr/jargon/html/index.html -
 McClure, S., Scambray, J., and Kurtz, G. Hacking Exposed, Fifth Edition (McGraw-Hill/Osborne, 2005)
McClure, S., Scambray, J., and Kurtz, G. Hacking Exposed, Fifth Edition (McGraw-Hill/Osborne, 2005) -
 SecurityFocus, http://www.securityfocus.com/
SecurityFocus, http://www.securityfocus.com/ -
 Verio, http://www.whois.net/
Verio, http://www.whois.net/ -
 Uwhois, Universal WHOIS, http://www.uwhois.com/
Uwhois, Universal WHOIS, http://www.uwhois.com/ -
 Insecure.org, http://www.insecure.org/nmap/
Insecure.org, http://www.insecure.org/nmap/ -
 Giacobbi, G. The GNU Netcat Project, http://netcat.sourceforge.net/
Giacobbi, G. The GNU Netcat Project, http://netcat.sourceforge.net/ -
 Security-Solutions.net, http://www.security-solutions.net/download/index.html
Security-Solutions.net, http://www.security-solutions.net/download/index.html -
 Microsoft Corporation. Windows 2000 Resource Kit Tools for Administrative Tasks. http://support.microsoft.com/kb/927229
Microsoft Corporation. Windows 2000 Resource Kit Tools for Administrative Tasks. http://support.microsoft.com/kb/927229 -
 SomarSoft Utilities, http://www.somarsoft.com/
SomarSoft Utilities, http://www.somarsoft.com/ -
 Microsoft Corporation. Windows Server 2003 SP1 Platform SDK Web Install, http://tinyurl.com/cew8e
Microsoft Corporation. Windows Server 2003 SP1 Platform SDK Web Install, http://tinyurl.com/cew8e -
 Kabay, M. E. Salami Fraud, http://www.networkworld.com/newsletters/sec/2002/01467137.html
Kabay, M. E. Salami Fraud, http://www.networkworld.com/newsletters/sec/2002/01467137.html -
 NIST Publication 800-64 Rev. A. Security Considerations in the Information System Development Life Cycle
NIST Publication 800-64 Rev. A. Security Considerations in the Information System Development Life Cycle -
 NIST Publication 800-42. Guideline on Network Security Testing
NIST Publication 800-42. Guideline on Network Security Testing -
 Tripwire, Inc., http://www.tripwire.com
Tripwire, Inc., http://www.tripwire.com -
 GFI Security & Messaging Software, http://www.gfi.com
GFI Security & Messaging Software, http://www.gfi.com -
 Tenable Network Security, http://www.nessus.org/download
Tenable Network Security, http://www.nessus.org/download -
 Wood, C. Information Security Policies Made Easy, Version 10 (Information Shield, 2005)
Wood, C. Information Security Policies Made Easy, Version 10 (Information Shield, 2005) -
 NIST Publication 800-29 Rev A. NIST Engineering Principles for Information Technology Security
NIST Publication 800-29 Rev A. NIST Engineering Principles for Information Technology Security -
 Cisco Systems, Inc. Security: Reduce IT Risk, http://www.cisco.com/go/sdn
Cisco Systems, Inc. Security: Reduce IT Risk, http://www.cisco.com/go/sdn -
 Wikipedia Foundation, Inc. Attack Tree, http://en.wikipedia.org/wiki/Attack_tree
Wikipedia Foundation, Inc. Attack Tree, http://en.wikipedia.org/wiki/Attack_tree




0 comments
Post a Comment