Summary
 In this chapter, you learned about security design principles with a focus on the following topics:
In this chapter, you learned about security design principles with a focus on the following topics:
-
 The need for network security, including business and legal requirements
The need for network security, including business and legal requirements
-
 The threats to network security, including reconnaissance, unauthorized access, and DoS
The threats to network security, including reconnaissance, unauthorized access, and DoS
-
 Security risks, including a breach of data confidentiality or integrity, and system and data availability interruptions
Security risks, including a breach of data confidentiality or integrity, and system and data availability interruptions
-
 Network security policies and process
Network security policies and process
-
 Calculating risk indices
Calculating risk indices
-
 The Cisco Self-Defending Network, including three critical elements: trust and identity management, threat defense, and secure connectivity
The Cisco Self-Defending Network, including three critical elements: trust and identity management, threat defense, and secure connectivity
-
 Security management
Security management
-
 How security is integrated in Cisco network devices
How security is integrated in Cisco network devices
-
 How security solutions are deployed in the Enterprise network
How security solutions are deployed in the Enterprise network
References
 For additional information, refer to the following resources:
For additional information, refer to the following resources:
-
 Cisco Systems, Inc., Security: Introduction, http://www.cisco.com/en/US/products/hw/vpndevc/index.html
Cisco Systems, Inc., Security: Introduction, http://www.cisco.com/en/US/products/hw/vpndevc/index.html
-
 Cisco Systems, Inc., Infrastructure Protection on Cisco IOS Software-Based Platforms, http://www.cisco.com/application/pdf/en/us/guest/products/ps1838/c1244/cdccont_0900aecd804ac831.pdf
Cisco Systems, Inc., Infrastructure Protection on Cisco IOS Software-Based Platforms, http://www.cisco.com/application/pdf/en/us/guest/products/ps1838/c1244/cdccont_0900aecd804ac831.pdf
-
 Cisco Systems, Inc., Security: Support Resources, http://www.cisco.com/en/US/products/hw/vpndevc/tsd_products_support_category_home.html
Cisco Systems, Inc., Security: Support Resources, http://www.cisco.com/en/US/products/hw/vpndevc/tsd_products_support_category_home.html
-
 Cisco Systems, Inc., Cisco Router and Security Device Manager: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
Cisco Systems, Inc., Cisco Router and Security Device Manager: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
-
 Cisco Systems, Inc., Cisco Adaptive Security Device Manager: Introduction, http://www.cisco.com/en/US/products/ps6121/index.html
Cisco Systems, Inc., Cisco Adaptive Security Device Manager: Introduction, http://www.cisco.com/en/US/products/ps6121/index.html
-
 Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
-
 Cisco Systems, Inc., CiscoWorks Management Center for Cisco Security Agents: Introduction, http://www.cisco.com/en/US/products/sw/cscowork/ps5212/index.html
Cisco Systems, Inc., CiscoWorks Management Center for Cisco Security Agents: Introduction, http://www.cisco.com/en/US/products/sw/cscowork/ps5212/index.html
-
 Cisco Systems, Inc., Cisco Secure Access Control Server for Windows: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2086/index.html
Cisco Systems, Inc., Cisco Secure Access Control Server for Windows: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2086/index.html
-
 Cisco Systems, Inc., Cisco Security Management Suite: Introduction, http://www.cisco.com/en/US/netsol/ns647/networking_solutions_sub_solution_home.html
Cisco Systems, Inc., Cisco Security Management Suite: Introduction, http://www.cisco.com/en/US/netsol/ns647/networking_solutions_sub_solution_home.html
-
 Cisco Systems, Inc., Cisco Security Manager: Introduction, http://www.cisco.com/en/US/products/ps6498/index.html
Cisco Systems, Inc., Cisco Security Manager: Introduction, http://www.cisco.com/en/US/products/ps6498/index.html
-
 Cisco Systems, Inc., Cisco Security Monitoring, Analysis and Response System: Introduction, http://www.cisco.com/en/US/products/ps6241/index.html
Cisco Systems, Inc., Cisco Security Monitoring, Analysis and Response System: Introduction, http://www.cisco.com/en/US/products/ps6241/index.html
-
 Cisco Systems, Inc., Cisco IOS Firewall: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps1018/index.html
Cisco Systems, Inc., Cisco IOS Firewall: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps1018/index.html
-
 Cisco Systems, Inc., Cisco IOS Intrusion Prevention System (IPS): Introduction, http://www.cisco.com/en/US/products/ps6634/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS Intrusion Prevention System (IPS): Introduction, http://www.cisco.com/en/US/products/ps6634/products_ios_protocol_group_home.html
-
 Cisco Systems, Inc., Cisco IOS IPsec: Introduction, http://www.cisco.com/en/US/products/ps6635/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS IPsec: Introduction, http://www.cisco.com/en/US/products/ps6635/products_ios_protocol_group_home.html
-
 Cisco Systems, Inc., Cisco IOS Trust and Identity: Introduction, http://www.cisco.com/en/US/products/ps6638/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS Trust and Identity: Introduction, http://www.cisco.com/en/US/products/ps6638/products_ios_protocol_group_home.html
-
 Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
-
 Cisco Systems, Inc., Cisco Integrated Services Routers—1800/2800/3800 Series, at-a-Glance, http://www.cisco.com/warp/public/765/tools/quickreference/isr.pdf
Cisco Systems, Inc., Cisco Integrated Services Routers—1800/2800/3800 Series, at-a-Glance, http://www.cisco.com/warp/public/765/tools/quickreference/isr.pdf
-
 Cisco Systems, Inc., Security Solutions for Large Enterprises, http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns413/networking_solutions_package.html
Cisco Systems, Inc., Security Solutions for Large Enterprises, http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns413/networking_solutions_package.html
-
 Cisco Systems, Inc., Cisco Security Center, http://tools.cisco.com/security/center/home.x
Cisco Systems, Inc., Cisco Security Center, http://tools.cisco.com/security/center/home.x
Case Study 10-1: ACMC Hospital Network Security Design
 This case study is a continuation of the ACMC Hospital case study introduced in Chapter 2, “Applying a Methodology to Network Design.”
This case study is a continuation of the ACMC Hospital case study introduced in Chapter 2, “Applying a Methodology to Network Design.”
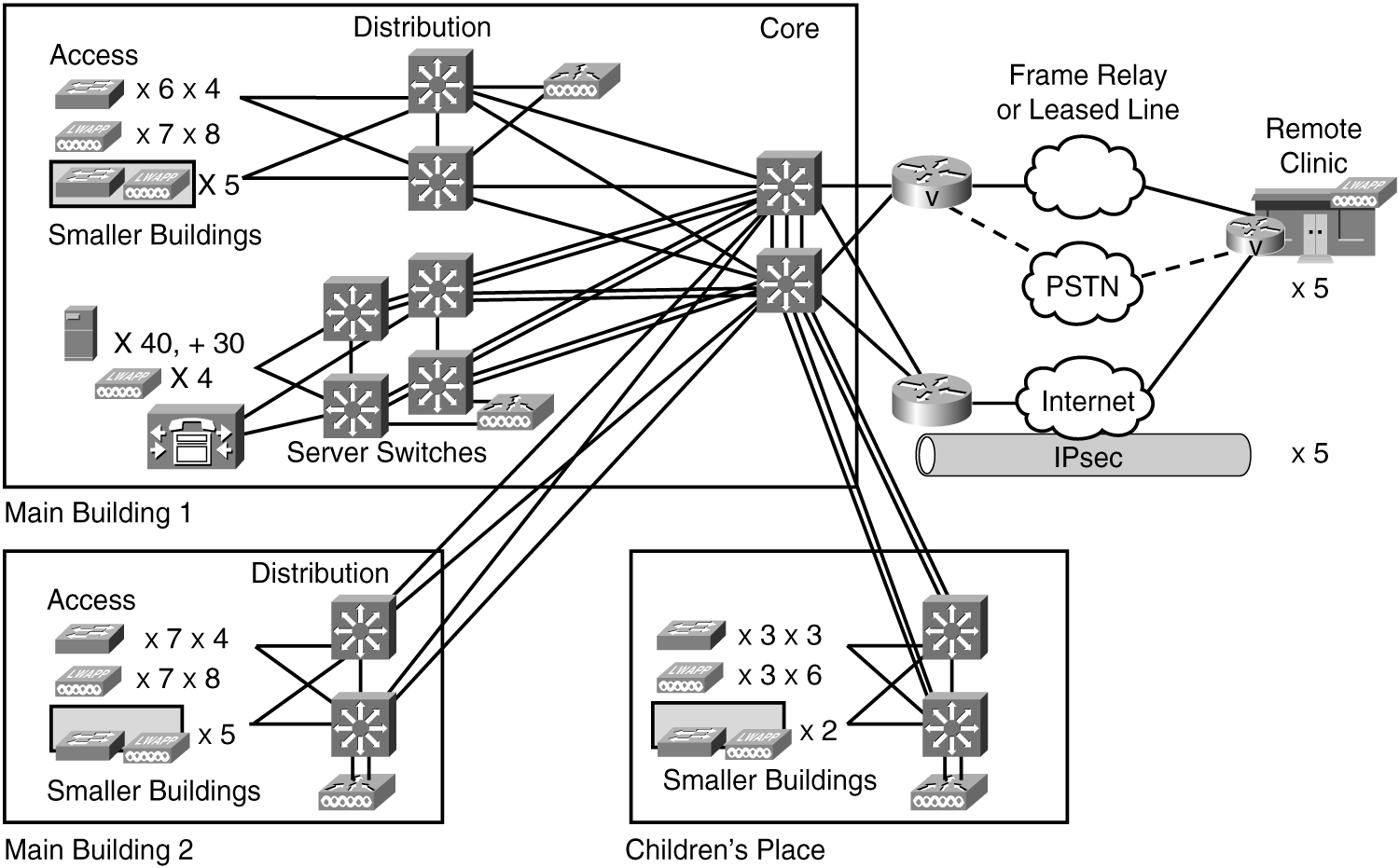
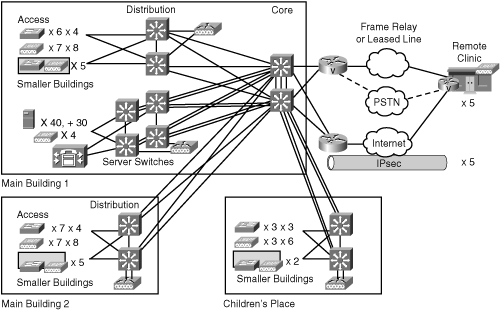
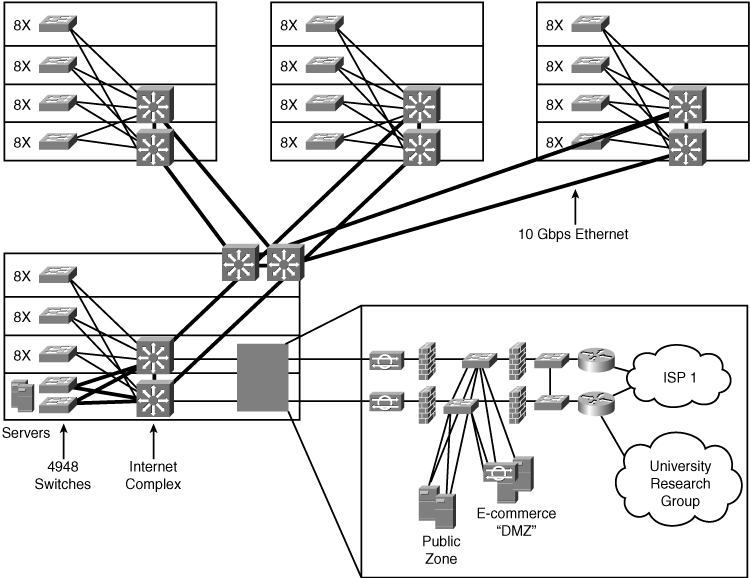
 In this case study, you create a high-level security design for the ACMC Hospital network. Figure 10-24 summarizes the design thus far.
In this case study, you create a high-level security design for the ACMC Hospital network. Figure 10-24 summarizes the design thus far.
 Case Study Questions
Case Study Questions
 Complete the following steps:
Complete the following steps:
|  Step 1 Step 1
|  Identify key business security requirements, risks, and threats about which ACMC should be concerned. Identify key business security requirements, risks, and threats about which ACMC should be concerned.
|
|  Step 2 Step 2
|  Design the Enterprise Edge modules for ACMC (E-commerce, Internet Connectivity, Remote Access and VPN, and WAN and MAN and Site-to-Site VPN). Determine how they should connect to the rest of the ACMC Hospital network. The design can use a consolidated approach in which devices are shared between modules. Design the Enterprise Edge modules for ACMC (E-commerce, Internet Connectivity, Remote Access and VPN, and WAN and MAN and Site-to-Site VPN). Determine how they should connect to the rest of the ACMC Hospital network. The design can use a consolidated approach in which devices are shared between modules.
|
|  Step 3 Step 3
|  Design the security for remote clinics, using the Internet with VPN for backup access. Design the security for remote clinics, using the Internet with VPN for backup access.
|
|  Step 4 Step 4
|  Determine suitable IP subnetting for the Internet, DMZ, and VPN. Determine suitable IP subnetting for the Internet, DMZ, and VPN.
|
|  Step 5 Step 5
|  Which Cisco security products and features would you recommend in the Enterprise Campus and the data center or server switches? Which Cisco security products and features would you recommend in the Enterprise Campus and the data center or server switches?
|
|  Step 6 Step 6
|  Identify some of the other security considerations, products, and features that should be part of deployment and where they should be used. For example, how should you handle infrastructure protection? Identify some of the other security considerations, products, and features that should be part of deployment and where they should be used. For example, how should you handle infrastructure protection?
|
Case Study 10-2: ACMC Hospital Network—Connecting More Hospitals
 This case study is a continuation of ACMC Hospital Case Study 10-1.
This case study is a continuation of ACMC Hospital Case Study 10-1.
 In this case study, you expand the ACMC hospital network as it merges with two other hospitals. The government of the state in which ACMC operates wants to improve patient service by networking hospitals; the network will be called MedNet. The legislature hopes to leverage large-city medical expertise for telemedicine at smaller locations. Short-term TDM circuits are funded; MedNet will move to Metro Ethernet service after terms for provider construction and contract are agreed on. Clinics will be associated with and connected via county hospitals.
In this case study, you expand the ACMC hospital network as it merges with two other hospitals. The government of the state in which ACMC operates wants to improve patient service by networking hospitals; the network will be called MedNet. The legislature hopes to leverage large-city medical expertise for telemedicine at smaller locations. Short-term TDM circuits are funded; MedNet will move to Metro Ethernet service after terms for provider construction and contract are agreed on. Clinics will be associated with and connected via county hospitals.
 Case Study Questions
Case Study Questions
 Complete the following steps:
Complete the following steps:
|  Step 1 Step 1
|  Hospital Omega is a nearby hospital that has been having financial difficulties. It is facing large licensing and application development costs to bring its financial and other applications up to date. To cut costs and stabilize finances, Hospital Omega will merge with ACMC. All data services will move to the ACMC data center and gradually migrate to the modern applications that ACMC already has in place. The Hospital Omega network was deployed between seven and ten years ago, and in many cases, the equipment vendors no longer exist. The following are some details about Hospital Omega: Hospital Omega is a nearby hospital that has been having financial difficulties. It is facing large licensing and application development costs to bring its financial and other applications up to date. To cut costs and stabilize finances, Hospital Omega will merge with ACMC. All data services will move to the ACMC data center and gradually migrate to the modern applications that ACMC already has in place. The Hospital Omega network was deployed between seven and ten years ago, and in many cases, the equipment vendors no longer exist. The following are some details about Hospital Omega:
-
 Hospital Omega does not use DHCP. Hospital Omega does not use DHCP.
-
 Hospital Omega consists of one building of ten floors, with fewer than 250 computers per floor. Hospital Omega consists of one building of ten floors, with fewer than 250 computers per floor.
-
 Hospital Omega uses static routes. Hospital Omega uses static routes.
-
 The Hospital Omega network is flat and Layer 2 switched. The switching equipment is from a third-party vendor and is seven and ten years old. The Hospital Omega network is flat and Layer 2 switched. The switching equipment is from a third-party vendor and is seven and ten years old.
-
 The Hospital Omega network uses old copper and fiber cabling that was added by various people in a random manner over the years. For any given closet, about 50 percent of the cable (copper or fiber) goes to unknown locations and is of unknown quality. The Hospital Omega network uses old copper and fiber cabling that was added by various people in a random manner over the years. For any given closet, about 50 percent of the cable (copper or fiber) goes to unknown locations and is of unknown quality.
-
 Servers are scattered around the building in random closets near the department that originally installed them. Servers are scattered around the building in random closets near the department that originally installed them.
-
 Hospital Omega accesses the Internet via the University Research Group. Hospital Omega accesses the Internet via the University Research Group.
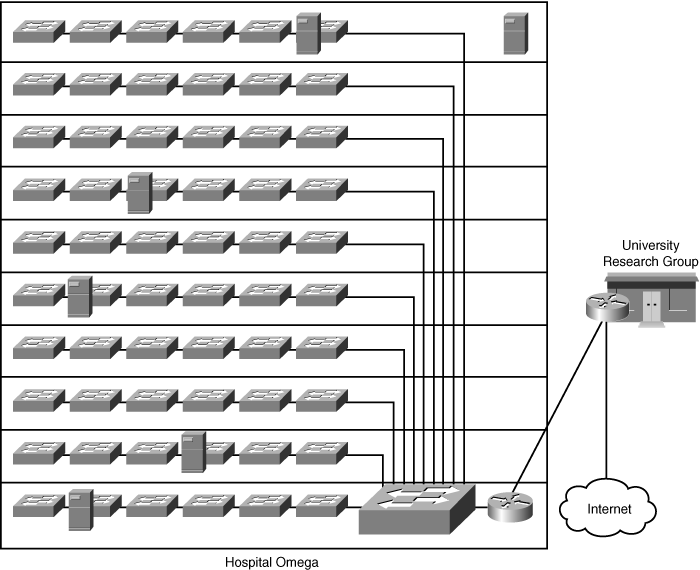
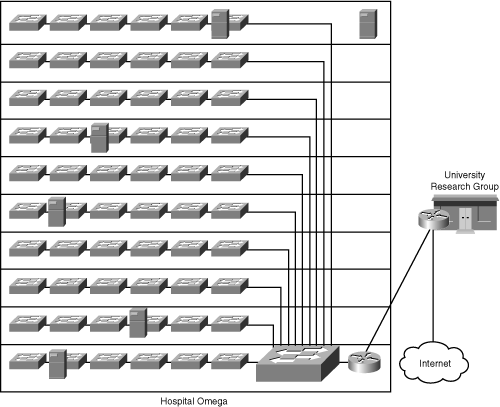
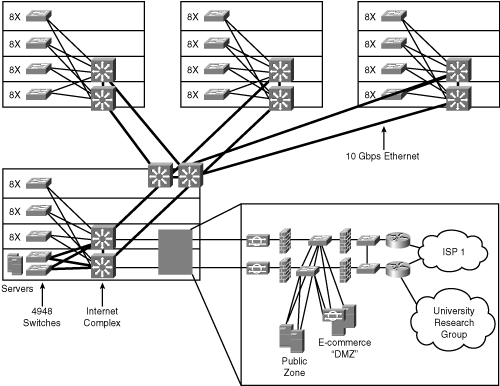
 Figure 10-25 shows the Hospital Omega network. Figure 10-25 shows the Hospital Omega network.
 The CIO wants a design to modernize the Hospital Omega network and allow robust access to the ACMC data center. Identify any issues you have with this merger and what design you would propose to the CIO. The CIO wants a design to modernize the Hospital Omega network and allow robust access to the ACMC data center. Identify any issues you have with this merger and what design you would propose to the CIO.
|
|  Step 2 Step 2
|  What is the key security issue for the Hospital Omega network? How could this issue be resolved? What is the key security issue for the Hospital Omega network? How could this issue be resolved?
|
|  Step 3 Step 3
|  Hospital Beta is another nearby hospital. ACMC and Hospital Beta overlap in several areas of medical expertise and feel that pooling talent and facilities should lead to better depth of medical expertise and better patient care. Sharing financial and other applications should also reduce overhead costs. The following are some details about Hospital Beta: Hospital Beta is another nearby hospital. ACMC and Hospital Beta overlap in several areas of medical expertise and feel that pooling talent and facilities should lead to better depth of medical expertise and better patient care. Sharing financial and other applications should also reduce overhead costs. The following are some details about Hospital Beta:
-
 Hospital Beta uses DHCP. Hospital Beta uses DHCP.
-
 Hospital Beta consists of four buildings, each with four large floors (with fewer than 250 Ethernet users and ports each). Each floor uses eight 24-port Cisco Catalyst 3560 switches in intermediate distribution frame closets, with dual uplinks to the distribution layer switches. The data center and Internet complex is on one floor of one of the four buildings. Hospital Beta consists of four buildings, each with four large floors (with fewer than 250 Ethernet users and ports each). Each floor uses eight 24-port Cisco Catalyst 3560 switches in intermediate distribution frame closets, with dual uplinks to the distribution layer switches. The data center and Internet complex is on one floor of one of the four buildings.
-
 Each building uses two Cisco Catalyst 6506 switches at the distribution layer. The switches are dual-homed via single-mode fiber at 10 Gbps to the core switches. Each building uses two Cisco Catalyst 6506 switches at the distribution layer. The switches are dual-homed via single-mode fiber at 10 Gbps to the core switches.
-
 The two Cisco Catalyst 6506 core switches are interconnected with 10-Gbps links and have dual connections to two Cisco Catalyst 4948 switches for the servers. The two Cisco Catalyst 6506 core switches are interconnected with 10-Gbps links and have dual connections to two Cisco Catalyst 4948 switches for the servers.
-
 The campus network is based on high-speed Layer 3 Cisco switches. The campus network is based on high-speed Layer 3 Cisco switches.
-
 Wireless is supported using Cisco WLAN controllers (WLC). Wireless is supported using Cisco WLAN controllers (WLC).
-
 The hospital has a DMZ, dual firewalls in each of two layers, IPS monitoring for the DMZ, and so forth. The hospital has a DMZ, dual firewalls in each of two layers, IPS monitoring for the DMZ, and so forth.
-
 Cisco IP telephony is in place. Cisco IP telephony is in place.
-
 Hospital Beta has a connection to the University Research Group. Hospital Beta has a connection to the University Research Group.
 Figure 10-26 shows the Hospital Beta network. Figure 10-26 shows the Hospital Beta network.
 The CIO wants a design to standardize the Hospital Beta network and allow robust access to the ACMC data center. Identify any issues you have with this merger and what design you would propose to the CIO. The CIO wants a design to standardize the Hospital Beta network and allow robust access to the ACMC data center. Identify any issues you have with this merger and what design you would propose to the CIO.
|
|  Step 4 Step 4
|  The CIO wants to consolidate servers in the ACMC data center. What issues need to be examined before proceeding with such a migration? The CIO wants to consolidate servers in the ACMC data center. What issues need to be examined before proceeding with such a migration?
|
|  Step 5 Step 5
|  Suppose that inexpensive Metro Ethernet is available between ACMC and Hospital Beta. How does this change your answer to the question in the previous step? Suppose that inexpensive Metro Ethernet is available between ACMC and Hospital Beta. How does this change your answer to the question in the previous step?
|
|  Step 6 Step 6
|  Hospital Beta already has deployed a Cisco Unified Communications Manager, IP phones, voice gateways, and so forth. Should the Cisco Unified Communications Manager and Cisco Unity servers be moved to the ACMC data center? Why or why not? If not, how should they interact with a Cisco Unified Communications Manager on the ACMC campus? Hospital Beta already has deployed a Cisco Unified Communications Manager, IP phones, voice gateways, and so forth. Should the Cisco Unified Communications Manager and Cisco Unity servers be moved to the ACMC data center? Why or why not? If not, how should they interact with a Cisco Unified Communications Manager on the ACMC campus?
|
|  Step 7 Step 7
|  Should the WLCs at Hospital Beta be moved to the ACMC campus? Should the WLCs at Hospital Beta be moved to the ACMC campus?
|
|  Step 8 Step 8
|  Hospital Omega uses static routes on its one Internet router. Hospital Beta uses the Intermediate System-to-Intermediate System (IS-IS) routing protocol. Make a recommendation for overall routing protocol and routing design for the merged networks. Hospital Omega uses static routes on its one Internet router. Hospital Beta uses the Intermediate System-to-Intermediate System (IS-IS) routing protocol. Make a recommendation for overall routing protocol and routing design for the merged networks.
|
|  Step 9 Step 9
|  The CIO at ACMC is concerned about HIPAA compliance and general security. She and you agree on running all Internet connectivity through ACMC and Hospital Beta. Assume that firewalls, firewall rules, DMZs, and properly configured IPsec VPN access are all in place. What additional steps can be taken to improve security in the combined ACMC-Omega-Beta network? The CIO at ACMC is concerned about HIPAA compliance and general security. She and you agree on running all Internet connectivity through ACMC and Hospital Beta. Assume that firewalls, firewall rules, DMZs, and properly configured IPsec VPN access are all in place. What additional steps can be taken to improve security in the combined ACMC-Omega-Beta network?
|
|  Step 10 Step 10
|  Hospital Omega is paying a large amount per phone for Centrex service. The CIO urgently wants to cut costs by moving to IP phones for Hospital Omega. The return on investment for doing this indicates that it would pay for itself in less than a year. The CIO has asked you for technical comments on doing this; what do you tell her? Hospital Omega is paying a large amount per phone for Centrex service. The CIO urgently wants to cut costs by moving to IP phones for Hospital Omega. The return on investment for doing this indicates that it would pay for itself in less than a year. The CIO has asked you for technical comments on doing this; what do you tell her?
|
|  Step 11 Step 11
|  ACMC has been assigned address block 10.1.0.0 /16. Could ACMC re-address within 10.1.0.0 /16? Assuming that it could, provide a revised addressing scheme that includes appropriate addressing for Hospital Beta and Hospital Omega. What are the summarized routes that each hospital should be advertising to the others? ACMC has been assigned address block 10.1.0.0 /16. Could ACMC re-address within 10.1.0.0 /16? Assuming that it could, provide a revised addressing scheme that includes appropriate addressing for Hospital Beta and Hospital Omega. What are the summarized routes that each hospital should be advertising to the others?
|
![]() In this chapter, you learned about security design principles with a focus on the following topics:
In this chapter, you learned about security design principles with a focus on the following topics: The need for network security, including business and legal requirements
The need for network security, including business and legal requirements The threats to network security, including reconnaissance, unauthorized access, and DoS
The threats to network security, including reconnaissance, unauthorized access, and DoS Security risks, including a breach of data confidentiality or integrity, and system and data availability interruptions
Security risks, including a breach of data confidentiality or integrity, and system and data availability interruptions Network security policies and process
Network security policies and process Calculating risk indices
Calculating risk indices The Cisco Self-Defending Network, including three critical elements: trust and identity management, threat defense, and secure connectivity
The Cisco Self-Defending Network, including three critical elements: trust and identity management, threat defense, and secure connectivity Security management
Security management How security is integrated in Cisco network devices
How security is integrated in Cisco network devices How security solutions are deployed in the Enterprise network
How security solutions are deployed in the Enterprise network![]() For additional information, refer to the following resources:
For additional information, refer to the following resources: Cisco Systems, Inc., Security: Introduction, http://www.cisco.com/en/US/products/hw/vpndevc/index.html
Cisco Systems, Inc., Security: Introduction, http://www.cisco.com/en/US/products/hw/vpndevc/index.html  Cisco Systems, Inc., Infrastructure Protection on Cisco IOS Software-Based Platforms, http://www.cisco.com/application/pdf/en/us/guest/products/ps1838/c1244/cdccont_0900aecd804ac831.pdf
Cisco Systems, Inc., Infrastructure Protection on Cisco IOS Software-Based Platforms, http://www.cisco.com/application/pdf/en/us/guest/products/ps1838/c1244/cdccont_0900aecd804ac831.pdf  Cisco Systems, Inc., Security: Support Resources, http://www.cisco.com/en/US/products/hw/vpndevc/tsd_products_support_category_home.html
Cisco Systems, Inc., Security: Support Resources, http://www.cisco.com/en/US/products/hw/vpndevc/tsd_products_support_category_home.html  Cisco Systems, Inc., Cisco Router and Security Device Manager: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
Cisco Systems, Inc., Cisco Router and Security Device Manager: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html  Cisco Systems, Inc., Cisco Adaptive Security Device Manager: Introduction, http://www.cisco.com/en/US/products/ps6121/index.html
Cisco Systems, Inc., Cisco Adaptive Security Device Manager: Introduction, http://www.cisco.com/en/US/products/ps6121/index.html  Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html  Cisco Systems, Inc., CiscoWorks Management Center for Cisco Security Agents: Introduction, http://www.cisco.com/en/US/products/sw/cscowork/ps5212/index.html
Cisco Systems, Inc., CiscoWorks Management Center for Cisco Security Agents: Introduction, http://www.cisco.com/en/US/products/sw/cscowork/ps5212/index.html  Cisco Systems, Inc., Cisco Secure Access Control Server for Windows: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2086/index.html
Cisco Systems, Inc., Cisco Secure Access Control Server for Windows: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2086/index.html  Cisco Systems, Inc., Cisco Security Management Suite: Introduction, http://www.cisco.com/en/US/netsol/ns647/networking_solutions_sub_solution_home.html
Cisco Systems, Inc., Cisco Security Management Suite: Introduction, http://www.cisco.com/en/US/netsol/ns647/networking_solutions_sub_solution_home.html  Cisco Systems, Inc., Cisco Security Manager: Introduction, http://www.cisco.com/en/US/products/ps6498/index.html
Cisco Systems, Inc., Cisco Security Manager: Introduction, http://www.cisco.com/en/US/products/ps6498/index.html  Cisco Systems, Inc., Cisco Security Monitoring, Analysis and Response System: Introduction, http://www.cisco.com/en/US/products/ps6241/index.html
Cisco Systems, Inc., Cisco Security Monitoring, Analysis and Response System: Introduction, http://www.cisco.com/en/US/products/ps6241/index.html  Cisco Systems, Inc., Cisco IOS Firewall: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps1018/index.html
Cisco Systems, Inc., Cisco IOS Firewall: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps1018/index.html  Cisco Systems, Inc., Cisco IOS Intrusion Prevention System (IPS): Introduction, http://www.cisco.com/en/US/products/ps6634/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS Intrusion Prevention System (IPS): Introduction, http://www.cisco.com/en/US/products/ps6634/products_ios_protocol_group_home.html  Cisco Systems, Inc., Cisco IOS IPsec: Introduction, http://www.cisco.com/en/US/products/ps6635/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS IPsec: Introduction, http://www.cisco.com/en/US/products/ps6635/products_ios_protocol_group_home.html  Cisco Systems, Inc., Cisco IOS Trust and Identity: Introduction, http://www.cisco.com/en/US/products/ps6638/products_ios_protocol_group_home.html
Cisco Systems, Inc., Cisco IOS Trust and Identity: Introduction, http://www.cisco.com/en/US/products/ps6638/products_ios_protocol_group_home.html  Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html
Cisco Systems, Inc., Cisco Intrusion Prevention System: Introduction, http://www.cisco.com/en/US/products/sw/secursw/ps2113/index.html  Cisco Systems, Inc., Cisco Integrated Services Routers—1800/2800/3800 Series, at-a-Glance, http://www.cisco.com/warp/public/765/tools/quickreference/isr.pdf
Cisco Systems, Inc., Cisco Integrated Services Routers—1800/2800/3800 Series, at-a-Glance, http://www.cisco.com/warp/public/765/tools/quickreference/isr.pdf  Cisco Systems, Inc., Security Solutions for Large Enterprises, http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns413/networking_solutions_package.html
Cisco Systems, Inc., Security Solutions for Large Enterprises, http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns413/networking_solutions_package.html  Cisco Systems, Inc., Cisco Security Center, http://tools.cisco.com/security/center/home.x
Cisco Systems, Inc., Cisco Security Center, http://tools.cisco.com/security/center/home.x ![]() This case study is a continuation of the ACMC Hospital case study introduced in Chapter 2, “Applying a Methodology to Network Design.”
This case study is a continuation of the ACMC Hospital case study introduced in Chapter 2, “Applying a Methodology to Network Design.” ![]() In this case study, you create a high-level security design for the ACMC Hospital network. Figure 10-24 summarizes the design thus far.
In this case study, you create a high-level security design for the ACMC Hospital network. Figure 10-24 summarizes the design thus far. Case Study Questions
Case Study Questions![]() This case study is a continuation of ACMC Hospital Case Study 10-1.
This case study is a continuation of ACMC Hospital Case Study 10-1. ![]() In this case study, you expand the ACMC hospital network as it merges with two other hospitals. The government of the state in which ACMC operates wants to improve patient service by networking hospitals; the network will be called MedNet. The legislature hopes to leverage large-city medical expertise for telemedicine at smaller locations. Short-term TDM circuits are funded; MedNet will move to Metro Ethernet service after terms for provider construction and contract are agreed on. Clinics will be associated with and connected via county hospitals.
In this case study, you expand the ACMC hospital network as it merges with two other hospitals. The government of the state in which ACMC operates wants to improve patient service by networking hospitals; the network will be called MedNet. The legislature hopes to leverage large-city medical expertise for telemedicine at smaller locations. Short-term TDM circuits are funded; MedNet will move to Metro Ethernet service after terms for provider construction and contract are agreed on. Clinics will be associated with and connected via county hospitals. Case Study Questions
Case Study Questions![]() Complete the following steps:
Complete the following steps:
0 comments
Post a Comment