 Introduction to Networks
Introduction to Networks
![]() In the 1960s and 1970s, before the PC was invented, a company would typically have only one central computer—a mainframe. Users connected to the mainframe through terminals on their desks. These terminals had no intelligence of their own—their only function was to display a text-based user interface provided by the mainframe. For this reason, they were usually called dumb terminals. The only network was the connection between the terminals and the mainframe.
In the 1960s and 1970s, before the PC was invented, a company would typically have only one central computer—a mainframe. Users connected to the mainframe through terminals on their desks. These terminals had no intelligence of their own—their only function was to display a text-based user interface provided by the mainframe. For this reason, they were usually called dumb terminals. The only network was the connection between the terminals and the mainframe.
![]() In 1981, the IBM PC was released—an event that changed the industry significantly. The PC had intelligence of its own, allowing users to do tasks on their desktops that previously required a mainframe. Networks were introduced to interconnect these distributed PCs.
In 1981, the IBM PC was released—an event that changed the industry significantly. The PC had intelligence of its own, allowing users to do tasks on their desktops that previously required a mainframe. Networks were introduced to interconnect these distributed PCs.
![]() The term network is used in many ways. For example, people network with one another, telephones are networked in the public telephone system, and data networks connect different computers. These uses of the term have a common thread: Networks make it possible for people or devices to communicate with each other.
The term network is used in many ways. For example, people network with one another, telephones are networked in the public telephone system, and data networks connect different computers. These uses of the term have a common thread: Networks make it possible for people or devices to communicate with each other.
![]() A data network is a network that allows computers to exchange data. The simplest data network is two PCs connected through a cable. However, most data networks connect many devices.
A data network is a network that allows computers to exchange data. The simplest data network is two PCs connected through a cable. However, most data networks connect many devices.
![]() An internetwork is a collection of individual networks connected by networking devices and that function as a single large network. The public Internet is the most common example—it is a single network that connects millions of computers. Internetworking refers to the industry and products that are involved in the design, implementation, and administration of internetworks.
An internetwork is a collection of individual networks connected by networking devices and that function as a single large network. The public Internet is the most common example—it is a single network that connects millions of computers. Internetworking refers to the industry and products that are involved in the design, implementation, and administration of internetworks.
![]() The first networks were LANs; they enabled multiple users in a relatively small geographic area to exchange files and messages and to access shared resources such as printers and disk storage. WANs were introduced to interconnect these LANs so that geographically dispersed users could also share information. The “LANs and WANs” section later in this chapter further describes these two types of networks.
The first networks were LANs; they enabled multiple users in a relatively small geographic area to exchange files and messages and to access shared resources such as printers and disk storage. WANs were introduced to interconnect these LANs so that geographically dispersed users could also share information. The “LANs and WANs” section later in this chapter further describes these two types of networks.
| Note |
|
Protocols and the OSI Model
![]() This section describes the OSI model and protocols used in internetworking. As an introduction, imagine that you are in Toronto and you want to send an e-mail to your friend in San Francisco. Successfully sending and receiving e-mail involves doing many things, including the following:
This section describes the OSI model and protocols used in internetworking. As an introduction, imagine that you are in Toronto and you want to send an e-mail to your friend in San Francisco. Successfully sending and receiving e-mail involves doing many things, including the following:
-
 You must type the message in your e-mail application.
You must type the message in your e-mail application. -
 You must address the message in your e-mail application.
You must address the message in your e-mail application. -
 You must click the Send button in your e-mail application to start sending the message.
You must click the Send button in your e-mail application to start sending the message. -
 You must use the correct type of connections and wires to connect your PC to your local network.
You must use the correct type of connections and wires to connect your PC to your local network. -
 Your PC must put the data on the wire.
Your PC must put the data on the wire. -
 Your PC must be able to connect to the Internet, and you must provide any necessary login information.
Your PC must be able to connect to the Internet, and you must provide any necessary login information. -
 Network devices must find the best path through the Internet so that the e-mail is received by the right person.
Network devices must find the best path through the Internet so that the e-mail is received by the right person.
![]() The following section introduces the OSI model, a model that describes all these communication functions and their relationships with each other.
The following section introduces the OSI model, a model that describes all these communication functions and their relationships with each other.
 The OSI Model
The OSI Model
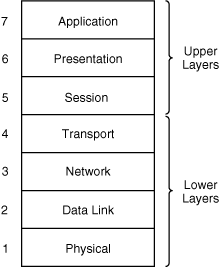
![]() The ISO standards committee created a list of all the network functions required for sending data (such as an e-mail) and divided them into seven categories. This model is known as the OSI seven-layer model. The OSI seven-layer model was released in 1984; it is illustrated in Figure 1-1.
The ISO standards committee created a list of all the network functions required for sending data (such as an e-mail) and divided them into seven categories. This model is known as the OSI seven-layer model. The OSI seven-layer model was released in 1984; it is illustrated in Figure 1-1.
| Note |
|
![]() As also shown in Figure 1-1, the seven layers can be thought of in two groups: the upper layers and the lower layers. The term upper layers often refers to Layers 5 through 7, and the term lower layers often refers to Layers 1 through 4, although this terminology is relative. The term upper layer also refers to any layer above another layer.
As also shown in Figure 1-1, the seven layers can be thought of in two groups: the upper layers and the lower layers. The term upper layers often refers to Layers 5 through 7, and the term lower layers often refers to Layers 1 through 4, although this terminology is relative. The term upper layer also refers to any layer above another layer.
![]() The upper layers are concerned with application issues—for example, the interface to the user and the format of the data. The lower layers are concerned with transport issues—for example, how the data traverses the network and the physical characteristics of that network.
The upper layers are concerned with application issues—for example, the interface to the user and the format of the data. The lower layers are concerned with transport issues—for example, how the data traverses the network and the physical characteristics of that network.
 Protocols
Protocols
![]() A protocol is a set of rules. The OSI model provides a framework for the communication protocols used between computers. Just as we need rules of the road—for example, so that we know that a red light means stop and a green light means go—computers also need to agree on a set of rules to successfully communicate. Two computers must use the same protocol to communicate. Computers that try to use different protocols would be analogous to speaking in Italian to someone who understands only English—it would not work.
A protocol is a set of rules. The OSI model provides a framework for the communication protocols used between computers. Just as we need rules of the road—for example, so that we know that a red light means stop and a green light means go—computers also need to agree on a set of rules to successfully communicate. Two computers must use the same protocol to communicate. Computers that try to use different protocols would be analogous to speaking in Italian to someone who understands only English—it would not work.
![]() Many different networking protocols are in use, in a variety of categories. For example, LAN and WAN protocols (at the lower two OSI layers) specify how communication is accomplished across various media types. Routed protocols (at Layer 3) specify the data’s format and how it is carried throughout a network, and routing protocols (some of which also operate at Layer 3) specify how routers communicate with one another to indicate the best paths through the network.
Many different networking protocols are in use, in a variety of categories. For example, LAN and WAN protocols (at the lower two OSI layers) specify how communication is accomplished across various media types. Routed protocols (at Layer 3) specify the data’s format and how it is carried throughout a network, and routing protocols (some of which also operate at Layer 3) specify how routers communicate with one another to indicate the best paths through the network.
![]() The most widely used network protocol suite today is the TCP/IP suite, named after two of the protocols within the suite. This network protocol suite is used in many places, including the backbone of the Internet and within organization’s networks. Novell’s NetWare, Apple Corporation’s AppleTalk, and IBM’s System Network Architecture are other examples of network protocol suites.
The most widely used network protocol suite today is the TCP/IP suite, named after two of the protocols within the suite. This network protocol suite is used in many places, including the backbone of the Internet and within organization’s networks. Novell’s NetWare, Apple Corporation’s AppleTalk, and IBM’s System Network Architecture are other examples of network protocol suites.
 The OSI Layers
The OSI Layers
![]() The following sections briefly describe each of the seven layers of the OSI model, starting at the lowest layer. Appendix C, “Open System Interconnection (OSI) Reference Model,” delves deeper into the details of the OSI model.
The following sections briefly describe each of the seven layers of the OSI model, starting at the lowest layer. Appendix C, “Open System Interconnection (OSI) Reference Model,” delves deeper into the details of the OSI model.
Physical Layer—Layer 1
![]() The OSI physical layer defines specifications such as the electrical and mechanical conditions necessary for activating, maintaining, and deactivating the physical link between devices. Specifications include voltage levels, maximum cable lengths, connector types, and maximum data rates. The physical layer is concerned with the binary transmission of data. This binary data is represented as bits (which is short for binary digits). A bit has a single binary value, either 0 or 1.
The OSI physical layer defines specifications such as the electrical and mechanical conditions necessary for activating, maintaining, and deactivating the physical link between devices. Specifications include voltage levels, maximum cable lengths, connector types, and maximum data rates. The physical layer is concerned with the binary transmission of data. This binary data is represented as bits (which is short for binary digits). A bit has a single binary value, either 0 or 1.
Data Link Layer—Layer 2
![]() Layer 2, the data link layer, defines the format of data that is to be transmitted across the physical network. It indicates how the physical medium is accessed, including physical addressing, error handling, and flow control. The data link layer sends frames of data; different media have different types of frames.
Layer 2, the data link layer, defines the format of data that is to be transmitted across the physical network. It indicates how the physical medium is accessed, including physical addressing, error handling, and flow control. The data link layer sends frames of data; different media have different types of frames.
![]() For LANs, the Institute of Electrical and Electronics Engineers (IEEE) split Layer 2 into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC).
For LANs, the Institute of Electrical and Electronics Engineers (IEEE) split Layer 2 into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC).
![]() The LLC sublayer (defined by the IEEE 802.2 specification) allows multiple network layer (Layer 3) protocols to communicate over the same physical data link by allowing the Layer 3 protocol to be specified in the LLC portion of the frame.
The LLC sublayer (defined by the IEEE 802.2 specification) allows multiple network layer (Layer 3) protocols to communicate over the same physical data link by allowing the Layer 3 protocol to be specified in the LLC portion of the frame.
![]() Some examples of MAC sublayer protocols are IEEE 802.3 Ethernet and IEEE 802.5 Token Ring. The MAC sublayer specifies the physical MAC address that uniquely identifies a device on a network. Each frame that is sent specifies a destination MAC address; only the device with that MAC address should receive and process the frame. Each frame also includes the MAC address of the frame’s source.
Some examples of MAC sublayer protocols are IEEE 802.3 Ethernet and IEEE 802.5 Token Ring. The MAC sublayer specifies the physical MAC address that uniquely identifies a device on a network. Each frame that is sent specifies a destination MAC address; only the device with that MAC address should receive and process the frame. Each frame also includes the MAC address of the frame’s source.
| Note |
|
Network Layer—Layer 3
![]() The network layer is responsible for routing, which allows data to be properly forwarded across a logical internetwork (consisting of multiple physical networks). Logical network addresses (as opposed to physical MAC addresses) are specified at Layer 3. Layer 3 protocols include routed and routing protocols. The routing protocols determine the best path that should be used to forward the routed data through the internetwork to its destination.
The network layer is responsible for routing, which allows data to be properly forwarded across a logical internetwork (consisting of multiple physical networks). Logical network addresses (as opposed to physical MAC addresses) are specified at Layer 3. Layer 3 protocols include routed and routing protocols. The routing protocols determine the best path that should be used to forward the routed data through the internetwork to its destination.
![]() The network layer sends datagrams (or packets); different routed protocols have different types of datagrams.
The network layer sends datagrams (or packets); different routed protocols have different types of datagrams.
Transport Layer—Layer 4
![]() Layer 4, the transport layer, is concerned with end-to-end connections between the source and the destination. The transport layer provides network services to the upper layers.
Layer 4, the transport layer, is concerned with end-to-end connections between the source and the destination. The transport layer provides network services to the upper layers.
![]() Connection-oriented reliable transport establishes a logical connection and uses sequence numbers to ensure that all data is received at the destination. Connectionless best-effort transport just sends the data and relies on upper-layer error detection mechanisms to report and correct problems. Reliable transport has more overhead than best-effort transport.
Connection-oriented reliable transport establishes a logical connection and uses sequence numbers to ensure that all data is received at the destination. Connectionless best-effort transport just sends the data and relies on upper-layer error detection mechanisms to report and correct problems. Reliable transport has more overhead than best-effort transport.
![]() Multiplexing allows many applications to use the same physical connection. For example, data is tagged with a number that identifies the application from which it came. Both sides of the connection then can interpret the data in the same way.
Multiplexing allows many applications to use the same physical connection. For example, data is tagged with a number that identifies the application from which it came. Both sides of the connection then can interpret the data in the same way.
![]() The transport layer sends segments.
The transport layer sends segments.
Upper Layers—Layers 5 Through 7
![]() From the lower layers’ perspective, the three upper layers represent the data that must be transmitted from the source to the destination; the network typically neither knows nor cares about the contents of these layers. For completeness, the following briefly describes the functions of these layers:
From the lower layers’ perspective, the three upper layers represent the data that must be transmitted from the source to the destination; the network typically neither knows nor cares about the contents of these layers. For completeness, the following briefly describes the functions of these layers:
-
 The session layer, Layer 5, is responsible for establishing, maintaining, and terminating communication sessions between applications running on different hosts.
The session layer, Layer 5, is responsible for establishing, maintaining, and terminating communication sessions between applications running on different hosts. -
 The presentation layer, Layer 6, specifies the format, data structure, coding, compression, and other ways of representing the data to ensure that information sent from one host’s application layer can be read by the destination host.
The presentation layer, Layer 6, specifies the format, data structure, coding, compression, and other ways of representing the data to ensure that information sent from one host’s application layer can be read by the destination host. -
 Finally, the application layer, Layer 7, is the closest to the end user; it interacts directly with software applications that need to communicate over the network.
Finally, the application layer, Layer 7, is the closest to the end user; it interacts directly with software applications that need to communicate over the network.
 Communication Among OSI Layers
Communication Among OSI Layers
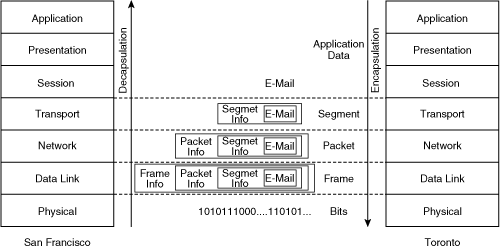
![]() This section describes how communication among the seven OSI layers is accomplished. When you send an e-mail from Toronto to your friend in San Francisco, you can think of your e-mail application sending a message to the e-mail application on your friend’s computer. In OSI model terms, information is exchanged between peer OSI layers—the application layer on your computer is communicating with the application layer on your friend’s computer. However, to accomplish this, the e-mail must go through all the other layers on your computer; for example, it must have the correct network layer address, be put in the correct frame type, and so on. The e-mail must then go over the network, and then go back through all the layers on your friend’s computer, until it finally arrives at your friend’s e-mail application.
This section describes how communication among the seven OSI layers is accomplished. When you send an e-mail from Toronto to your friend in San Francisco, you can think of your e-mail application sending a message to the e-mail application on your friend’s computer. In OSI model terms, information is exchanged between peer OSI layers—the application layer on your computer is communicating with the application layer on your friend’s computer. However, to accomplish this, the e-mail must go through all the other layers on your computer; for example, it must have the correct network layer address, be put in the correct frame type, and so on. The e-mail must then go over the network, and then go back through all the layers on your friend’s computer, until it finally arrives at your friend’s e-mail application.
![]() Control information from each layer is added to the e-mail data before it passes to lower layers; this control information is necessary to allow the data to go through the network properly. Thus, the data at each layer is encapsulated, or wrapped in, the information appropriate for that layer, including addressing and error checking. The right side of Figure 1-2 illustrates the following encapsulation process:
Control information from each layer is added to the e-mail data before it passes to lower layers; this control information is necessary to allow the data to go through the network properly. Thus, the data at each layer is encapsulated, or wrapped in, the information appropriate for that layer, including addressing and error checking. The right side of Figure 1-2 illustrates the following encapsulation process:
-
 At Layer 4, the e-mail is encapsulated in a segment.
At Layer 4, the e-mail is encapsulated in a segment. -
 At Layer 3, this segment is encapsulated in a packet.
At Layer 3, this segment is encapsulated in a packet. -
 Finally, at Layer 1, the frame is sent out on the wire (or air, if wireless is used) in bits.
Finally, at Layer 1, the frame is sent out on the wire (or air, if wireless is used) in bits.
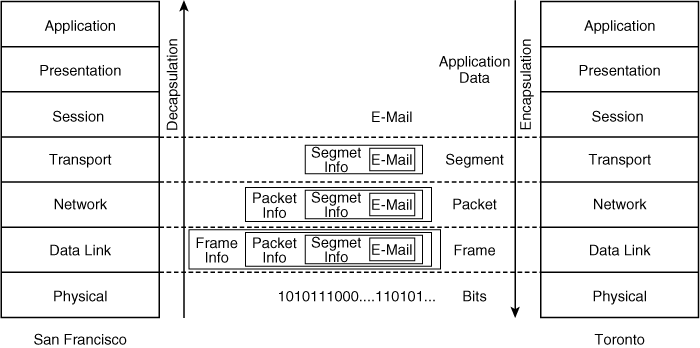
![]() The grouping of data used to exchange information at a particular OSI layer is known as a protocol data unit (PDU). Thus, the PDU at Layer 4 is a segment, at Layer 3 is a packet, and at Layer 2 is a frame.
The grouping of data used to exchange information at a particular OSI layer is known as a protocol data unit (PDU). Thus, the PDU at Layer 4 is a segment, at Layer 3 is a packet, and at Layer 2 is a frame.
![]() Notice how the overall size of the information increases as the data goes down through the lower layers. When data is received at the other end of the network, this additional information is analyzed and then removed as the data is passed to the higher layers toward the application layer. In other words, the data is unencapsulated, or unwrapped; this process is shown on the left side of Figure 1-2.
Notice how the overall size of the information increases as the data goes down through the lower layers. When data is received at the other end of the network, this additional information is analyzed and then removed as the data is passed to the higher layers toward the application layer. In other words, the data is unencapsulated, or unwrapped; this process is shown on the left side of Figure 1-2.
| Note |
|
| Note |
|
![]() At each layer, different protocols are available. For example, the packets sent by IP are different from those sent by IPX because different protocols (rules) must be followed. Both sides of peer layers that are communicating must support the same protocol.
At each layer, different protocols are available. For example, the packets sent by IP are different from those sent by IPX because different protocols (rules) must be followed. Both sides of peer layers that are communicating must support the same protocol.
LANs and WANs
![]() LANs were first used between PCs when users needed to connect with other PCs in the same building to share resources. A LAN is a high-speed, yet relatively inexpensive, network that allows connected computers to communicate. LANs have limited reach (hence the term local-area network), typically less than a few hundred meters, so they can connect only devices in the same room or building, or possibly within the same campus.
LANs were first used between PCs when users needed to connect with other PCs in the same building to share resources. A LAN is a high-speed, yet relatively inexpensive, network that allows connected computers to communicate. LANs have limited reach (hence the term local-area network), typically less than a few hundred meters, so they can connect only devices in the same room or building, or possibly within the same campus.
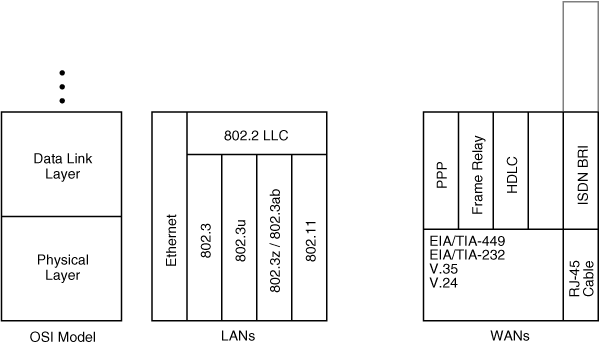
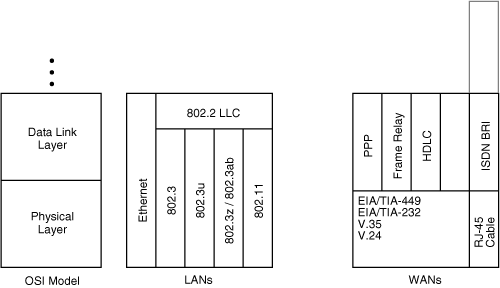
![]() A LAN is an always-on connection—in other words, you don’t have to dial up or otherwise connect to it when you want to send some data. LANs also usually belong to the organization in which they are deployed, so no incremental cost is typically associated with sending data. A variety of LAN technologies are available, some of which are shown in the center of Figure 1-3 and briefly described here:
A LAN is an always-on connection—in other words, you don’t have to dial up or otherwise connect to it when you want to send some data. LANs also usually belong to the organization in which they are deployed, so no incremental cost is typically associated with sending data. A variety of LAN technologies are available, some of which are shown in the center of Figure 1-3 and briefly described here:
-
 Ethernet and IEEE 802.3, running at 10 megabits per second (Mbps), use a carrier sense multiple access collision detect (CSMA/CD) technology. When a CSMA/CD device has data to send, it listens to see whether any of the other devices on the wire (multiple access) are transmitting (carrier sense). If no other device is transmitting, this device starts to send its data, listening all the time in case another device erroneously starts to send data (collision detect).
Ethernet and IEEE 802.3, running at 10 megabits per second (Mbps), use a carrier sense multiple access collision detect (CSMA/CD) technology. When a CSMA/CD device has data to send, it listens to see whether any of the other devices on the wire (multiple access) are transmitting (carrier sense). If no other device is transmitting, this device starts to send its data, listening all the time in case another device erroneously starts to send data (collision detect). -
 Fast Ethernet (at 100 Mbps), covered by the IEEE 802.3u specification, also uses the CSMA/CD technology.
Fast Ethernet (at 100 Mbps), covered by the IEEE 802.3u specification, also uses the CSMA/CD technology. -
 Gigabit Ethernet (running at 1 gigabit per second [Gbps]) is covered by the IEEE 802.3z and 802.3ab specifications and uses the CSMA/CD technology.
Gigabit Ethernet (running at 1 gigabit per second [Gbps]) is covered by the IEEE 802.3z and 802.3ab specifications and uses the CSMA/CD technology. -
 Wireless LAN (WLAN) standards, defined by the IEEE 802.11 specifications, are capable of speeds up to 54 Mbps under the 802.11g specification. (A new standard, 802.11n, planned to be ratified in 2007, will be capable of higher speeds.) WLANs use a carrier sense multiple access collision avoidance (CSMA/CA) mechanism (versus the CSMA/CD mechanism used by the wired Ethernet standards).
Wireless LAN (WLAN) standards, defined by the IEEE 802.11 specifications, are capable of speeds up to 54 Mbps under the 802.11g specification. (A new standard, 802.11n, planned to be ratified in 2007, will be capable of higher speeds.) WLANs use a carrier sense multiple access collision avoidance (CSMA/CA) mechanism (versus the CSMA/CD mechanism used by the wired Ethernet standards).
![]() WANs interconnect devices that are usually connected to LANs and are located over a relatively broad geographic area (hence the term wide-area network). Compared to a LAN, a typical WAN is slower, requires a connection request when you want to send data, and usually belongs to another organization (called a service provider). You pay the service provider a fee (known as a tariff) for the use of the WAN; this fee could be a fixed monthly amount, or it could be variable based on usage and distance.
WANs interconnect devices that are usually connected to LANs and are located over a relatively broad geographic area (hence the term wide-area network). Compared to a LAN, a typical WAN is slower, requires a connection request when you want to send data, and usually belongs to another organization (called a service provider). You pay the service provider a fee (known as a tariff) for the use of the WAN; this fee could be a fixed monthly amount, or it could be variable based on usage and distance.
![]() Just as you find many types of LANs, many types of WANs are also available, some of which are illustrated on the right side of Figure 1-3. Like LANs, WANs function at the lower two layers of the OSI model. A few, such as ISDN, also function at Layer 3. The service you use depends on many factors, including what is available where you are and, of course, the cost of the service. Some of the common WAN technologies include the following:
Just as you find many types of LANs, many types of WANs are also available, some of which are illustrated on the right side of Figure 1-3. Like LANs, WANs function at the lower two layers of the OSI model. A few, such as ISDN, also function at Layer 3. The service you use depends on many factors, including what is available where you are and, of course, the cost of the service. Some of the common WAN technologies include the following:
-
 Packet-switched network: A network that shares the service provider’s facilities. The service provider creates permanent virtual circuits and switched virtual circuits that deliver data between subscribers’ sites. Frame Relay is an example of a packet-switched network.
Packet-switched network: A network that shares the service provider’s facilities. The service provider creates permanent virtual circuits and switched virtual circuits that deliver data between subscribers’ sites. Frame Relay is an example of a packet-switched network. -
 Leased line: A point-to-point connection reserved for transmission. Common data link layer protocols used in this case are PPP and High-Level Data Link Control (HDLC).
Leased line: A point-to-point connection reserved for transmission. Common data link layer protocols used in this case are PPP and High-Level Data Link Control (HDLC). -
 Circuit-switched network: A physical path reserved for the duration of the connection between two points. ISDN Basic Rate Interface (BRI) is an example of this type of network.
Circuit-switched network: A physical path reserved for the duration of the connection between two points. ISDN Basic Rate Interface (BRI) is an example of this type of network.
![]() Two other technologies, digital subscriber line (DSL) and cable, connect residential and business premises to service providers’ premises:
Two other technologies, digital subscriber line (DSL) and cable, connect residential and business premises to service providers’ premises:
-
 DSL: Uses unused bandwidth on traditional copper telephone lines to deliver traffic at higher speeds than traditional modems allow. The most common DSL implementation is asymmetric DSL (ADSL). It is called asymmetric because the download speed is faster than the upload speed, reflecting the needs of most users and more efficiently using the available bandwidth on standard two-wire telephone lines. ADSL allows regular telephone traffic to simultaneously share the line with high-speed data traffic so that only one telephone line is required to support both high-speed Internet and normal telephone services.
DSL: Uses unused bandwidth on traditional copper telephone lines to deliver traffic at higher speeds than traditional modems allow. The most common DSL implementation is asymmetric DSL (ADSL). It is called asymmetric because the download speed is faster than the upload speed, reflecting the needs of most users and more efficiently using the available bandwidth on standard two-wire telephone lines. ADSL allows regular telephone traffic to simultaneously share the line with high-speed data traffic so that only one telephone line is required to support both high-speed Internet and normal telephone services. -
 Cable: Uses unused bandwidth on cable television networks to deliver data at higher speeds than traditional modems allow.
Cable: Uses unused bandwidth on cable television networks to deliver data at higher speeds than traditional modems allow.
| Note |
|

4 comments
Hi!
Awesome post, really useful!
Have you heard about Publish Green? You’ve probably seen our Ebooks all over the place. We’re the leading free Ebooks for the world. We’ve just launched our website TCP/IP Networking Fundamentals Pdf where we give away the best free Ebook resources out there. We’d be stoked if you could add us to this list.
Keep sharing With us
instagram takipçi satın al
instagram takipçi satın al
takipçi satın al
takipçi satın al
instagram takipçi satın al
takipçi satın al
instagram takipçi satın al
MMORPG
İNSTAGRAM TAKİPÇİ SATİN AL
tiktok jeton hilesi
TİKTOK JETON HİLESİ
Sac Ekim Antalya
ınstagram takipci
İnstagram Takipçi Satın Al
Mt2 Pvp Serverler
instagram takipci
maltepe mitsubishi klima servisi
ümraniye vestel klima servisi
kartal arçelik klima servisi
ümraniye arçelik klima servisi
beykoz samsung klima servisi
üsküdar daikin klima servisi
pendik toshiba klima servisi
pendik beko klima servisi
tuzla lg klima servisi
Post a Comment