Network Devices
![]() The main devices that interconnect networks are hubs, switches, and routers, as described in the following sections.
The main devices that interconnect networks are hubs, switches, and routers, as described in the following sections.
| Note |
|
 Terminology: Domains, Bandwidth, Unicast, Broadcast, and Multicast
Terminology: Domains, Bandwidth, Unicast, Broadcast, and Multicast
![]() The following is some terminology related to the operation of network devices:
The following is some terminology related to the operation of network devices:
-
 A domain is a specific part of a network.
A domain is a specific part of a network. -
 Bandwidth is the amount of data that can be carried across a network in a given time period.
Bandwidth is the amount of data that can be carried across a network in a given time period. -
 Unicast data is data meant for a specific device.
Unicast data is data meant for a specific device. -
 Broadcast data is data meant for all devices; a special broadcast address indicates this.
Broadcast data is data meant for all devices; a special broadcast address indicates this. -
 Multicast data is data destined for a specific group of devices; again, a special address indicates this.
Multicast data is data destined for a specific group of devices; again, a special address indicates this. -
 A bandwidth domain, known as a collision domain for Ethernet LANs, includes all devices that share the same bandwidth.
A bandwidth domain, known as a collision domain for Ethernet LANs, includes all devices that share the same bandwidth. -
 A broadcast domain includes all devices that receive each others’ broadcasts (and multicasts).
A broadcast domain includes all devices that receive each others’ broadcasts (and multicasts).
![]() Devices in the same bandwidth domain are also in the same broadcast domain; however, devices in the same broadcast domain can be in different bandwidth domains.
Devices in the same bandwidth domain are also in the same broadcast domain; however, devices in the same broadcast domain can be in different bandwidth domains.
 Hubs
Hubs
![]() A typical Ethernet LAN uses unshielded twisted-pair (UTP) cables with RJ-45 connectors (which are slightly bigger than telephone RJ-11 connectors). Because these cables have only two ends, you need an intermediary device to connect more than two computers. That device is a hub.
A typical Ethernet LAN uses unshielded twisted-pair (UTP) cables with RJ-45 connectors (which are slightly bigger than telephone RJ-11 connectors). Because these cables have only two ends, you need an intermediary device to connect more than two computers. That device is a hub.
![]() A hub works at Layer 1 and connects multiple devices so that they are logically all on one LAN.
A hub works at Layer 1 and connects multiple devices so that they are logically all on one LAN.
![]() A hub has no intelligence—it sends all data received on any port to all the other ports. Consequently, devices connected through a hub receive everything that the other devices send, whether or not it was meant for them. This is analogous to being in a room with lots of people—if you speak, everyone can hear you. If more than one person speaks at a time, everyone just hears noise.
A hub has no intelligence—it sends all data received on any port to all the other ports. Consequently, devices connected through a hub receive everything that the other devices send, whether or not it was meant for them. This is analogous to being in a room with lots of people—if you speak, everyone can hear you. If more than one person speaks at a time, everyone just hears noise.
![]() All devices connected to a hub are in one collision domain and one broadcast domain.
All devices connected to a hub are in one collision domain and one broadcast domain.
| Note |
|
 Switches
Switches
![]() Just as having many people in a room trying to speak can result in nobody hearing anything intelligible, using hubs in anything but a small network is not efficient. To improve performance, LANs are usually divided into multiple smaller LANs interconnected by a Layer 2 LAN switch. The devices connected to a switch again appear as they are all on one LAN, but this time, multiple conversations between devices connected through the switch can happen simultaneously.
Just as having many people in a room trying to speak can result in nobody hearing anything intelligible, using hubs in anything but a small network is not efficient. To improve performance, LANs are usually divided into multiple smaller LANs interconnected by a Layer 2 LAN switch. The devices connected to a switch again appear as they are all on one LAN, but this time, multiple conversations between devices connected through the switch can happen simultaneously.
| Note |
|
![]() LAN switches are Layer 2 devices and have some intelligence—they send data to a port only if the data needs to go there. A device connected to a switch port does not receive any of the information addressed to devices on other ports. Therefore, the main advantage of using a switch instead of a hub is that the traffic received by a device is reduced because only frames addressed to a specific device are forwarded to the port on which that device is connected.
LAN switches are Layer 2 devices and have some intelligence—they send data to a port only if the data needs to go there. A device connected to a switch port does not receive any of the information addressed to devices on other ports. Therefore, the main advantage of using a switch instead of a hub is that the traffic received by a device is reduced because only frames addressed to a specific device are forwarded to the port on which that device is connected.
![]() Switches read the source and destination MAC addresses in the frames and therefore can keep track of who is where, and who is talking to whom, and send data only where it needs to go. However, if the switch receives a frame whose destination address indicates that it is a broadcast (information meant for everyone) or multicast (information meant for a group), by default it sends the frame out all ports (except for the one on which it was received).
Switches read the source and destination MAC addresses in the frames and therefore can keep track of who is where, and who is talking to whom, and send data only where it needs to go. However, if the switch receives a frame whose destination address indicates that it is a broadcast (information meant for everyone) or multicast (information meant for a group), by default it sends the frame out all ports (except for the one on which it was received).
![]() All devices connected to one switch port are in the same collision domain, but devices connected to different ports are in different collision domains. By default, all devices connected to a switch are in the same broadcast domain.
All devices connected to one switch port are in the same collision domain, but devices connected to different ports are in different collision domains. By default, all devices connected to a switch are in the same broadcast domain.
![]() Switches do not allow devices on different logical LANs to communicate with each other; this requires a router, as described in the next section.
Switches do not allow devices on different logical LANs to communicate with each other; this requires a router, as described in the next section.
 Routers
Routers
![]() A router goes one step further than a switch. It is a Layer 3 device that has much more intelligence than a hub or switch. By using logical Layer 3 addresses, routers allow devices on different LANs to communicate with each other and with distant devices—for example, those connected through the Internet or through a WAN. Examples of logical Layer 3 addresses include TCP/IP’s IP addresses and Novell’s IPX addresses.
A router goes one step further than a switch. It is a Layer 3 device that has much more intelligence than a hub or switch. By using logical Layer 3 addresses, routers allow devices on different LANs to communicate with each other and with distant devices—for example, those connected through the Internet or through a WAN. Examples of logical Layer 3 addresses include TCP/IP’s IP addresses and Novell’s IPX addresses.
![]() A device connected to a router does not receive any of the information meant just for devices on other ports, or broadcasts (destined for all networks) from devices on other ports.
A device connected to a router does not receive any of the information meant just for devices on other ports, or broadcasts (destined for all networks) from devices on other ports.
![]() The router reads the source and destination logical addresses in the packets and therefore keeps track of who is where, and who is talking to whom, and sends data only where it needs to go. It supports communication between LANs, but it blocks broadcasts (destined for all networks).
The router reads the source and destination logical addresses in the packets and therefore keeps track of who is where, and who is talking to whom, and sends data only where it needs to go. It supports communication between LANs, but it blocks broadcasts (destined for all networks).
![]() All devices connected to one router port are in the same collision domain, but devices connected to different ports are in different collision domains.
All devices connected to one router port are in the same collision domain, but devices connected to different ports are in different collision domains.
![]() All the devices connected to one router port are in the same broadcast domain, but devices connected to different ports are in different broadcast domains. Routers block broadcasts (destined for all networks) and multicasts by default; routers forward only unicast packets (destined for a specific device) and packets of a special type called directed broadcasts.
All the devices connected to one router port are in the same broadcast domain, but devices connected to different ports are in different broadcast domains. Routers block broadcasts (destined for all networks) and multicasts by default; routers forward only unicast packets (destined for a specific device) and packets of a special type called directed broadcasts.
| Note |
|
| Note |
|
![]() The fact that a router does not forward broadcasts (destined for all networks) is a significant difference between a router and a switch, and it helps control the amount of traffic on the network. For example, many protocols, such as IP, might use broadcasts for routing protocol advertisements, discovering servers, and so on. These broadcasts are a necessary part of local LAN traffic, but they are not required on other LANs and can even overwhelm slower WANs. Routers can generate broadcasts themselves if necessary (for example, to send a routing protocol advertisement), but do not pass on a received broadcast.
The fact that a router does not forward broadcasts (destined for all networks) is a significant difference between a router and a switch, and it helps control the amount of traffic on the network. For example, many protocols, such as IP, might use broadcasts for routing protocol advertisements, discovering servers, and so on. These broadcasts are a necessary part of local LAN traffic, but they are not required on other LANs and can even overwhelm slower WANs. Routers can generate broadcasts themselves if necessary (for example, to send a routing protocol advertisement), but do not pass on a received broadcast.
![]() Routing operation is discussed further in the “Routing” section, later in this chapter.
Routing operation is discussed further in the “Routing” section, later in this chapter.
Introduction to the TCP/IP Suite
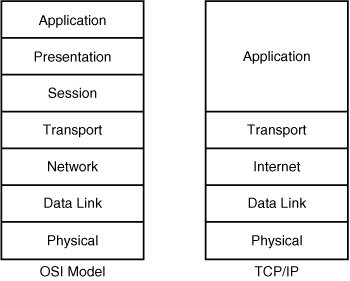
![]() As mentioned earlier, TCP/IP is the most widely used protocol suite. The relationship between the five layers of the TCP/IP protocol suite and the seven layers of the OSI model is illustrated in Figure 1-4.
As mentioned earlier, TCP/IP is the most widely used protocol suite. The relationship between the five layers of the TCP/IP protocol suite and the seven layers of the OSI model is illustrated in Figure 1-4.
![]() The five layers of the TCP/IP suite are the application layer, transport layer, Internet layer, data link layer, and physical layer.
The five layers of the TCP/IP suite are the application layer, transport layer, Internet layer, data link layer, and physical layer.
| Note |
|
![]() The TCP/IP application layer includes the functionality of the OSI application, presentation, and session layers. Applications defined in the TCP/IP suite include the following:
The TCP/IP application layer includes the functionality of the OSI application, presentation, and session layers. Applications defined in the TCP/IP suite include the following:
-
 FTP and Trivial File Transfer Protocol (TFTP): Transfer files between devices.
FTP and Trivial File Transfer Protocol (TFTP): Transfer files between devices. -
 SMTP and POP3: Provide e-mail services.
SMTP and POP3: Provide e-mail services. -
 HTTP: Transfers information to and from a World Wide Web server through web browser software.
HTTP: Transfers information to and from a World Wide Web server through web browser software. -
 Telnet: Emulates a terminal to connect to devices.
Telnet: Emulates a terminal to connect to devices. -
 Domain Name System (DNS): Translates network device names into network addresses and vice versa.
Domain Name System (DNS): Translates network device names into network addresses and vice versa. -
 Simple Network Management Protocol (SNMP): Used for network management, including setting threshold values and reporting network errors.
Simple Network Management Protocol (SNMP): Used for network management, including setting threshold values and reporting network errors. -
 Dynamic Host Configuration Protocol (DHCP): Assigns dynamic IP addressing information to devices as they require it.
Dynamic Host Configuration Protocol (DHCP): Assigns dynamic IP addressing information to devices as they require it.
![]() The transport layer and Internet layer protocols are detailed in the following sections.
The transport layer and Internet layer protocols are detailed in the following sections.
![]() The data link and physical layers can support a wide variety of LANs and WANs (including those discussed in the “LANs and WANs” section, earlier in this chapter). A data link layer protocol related to the TCP/IP suite is described in the later “TCP/IP-Related Data Link Layer Protocol” section.
The data link and physical layers can support a wide variety of LANs and WANs (including those discussed in the “LANs and WANs” section, earlier in this chapter). A data link layer protocol related to the TCP/IP suite is described in the later “TCP/IP-Related Data Link Layer Protocol” section.
 TCP/IP Transport Layer Protocols
TCP/IP Transport Layer Protocols
![]() The TCP/IP transport layer includes the following two protocols:
The TCP/IP transport layer includes the following two protocols:
-
 Transmission Control Protocol (TCP): Provides connection-oriented, end-to-end reliable transmission. Before sending any data, TCP on the source device establishes a connection with TCP on the destination device, ensuring that both sides are synchronized. Data is acknowledged; any data not received properly is retransmitted. FTP is an example of an application that uses TCP to guarantee that the data sent from one device to another is received successfully.
Transmission Control Protocol (TCP): Provides connection-oriented, end-to-end reliable transmission. Before sending any data, TCP on the source device establishes a connection with TCP on the destination device, ensuring that both sides are synchronized. Data is acknowledged; any data not received properly is retransmitted. FTP is an example of an application that uses TCP to guarantee that the data sent from one device to another is received successfully. -
 User Datagram Protocol (UDP): Provides connectionless, best-effort unacknowledged data transmission. In other words, UDP does not ensure that all the segments arrive at the destination undamaged. UDP does not have the overhead of TCP related to establishing the connection and acknowledging the data. However, this means that upper-layer protocols or the user must determine whether all the data arrived successfully, and retransmit if necessary. TFTP is an example of an application that uses UDP. When all the segments have arrived at the destination, TFTP computes the file check sequence and reports the results to the user. If an error occurs, the user must send the entire file again.
User Datagram Protocol (UDP): Provides connectionless, best-effort unacknowledged data transmission. In other words, UDP does not ensure that all the segments arrive at the destination undamaged. UDP does not have the overhead of TCP related to establishing the connection and acknowledging the data. However, this means that upper-layer protocols or the user must determine whether all the data arrived successfully, and retransmit if necessary. TFTP is an example of an application that uses UDP. When all the segments have arrived at the destination, TFTP computes the file check sequence and reports the results to the user. If an error occurs, the user must send the entire file again.
| Note |
|
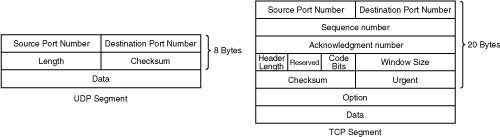
![]() TCP and UDP, being at the transport layer, send segments. Figure 1-5 illustrates the fields in a UDP segment and in a TCP segment.
TCP and UDP, being at the transport layer, send segments. Figure 1-5 illustrates the fields in a UDP segment and in a TCP segment.
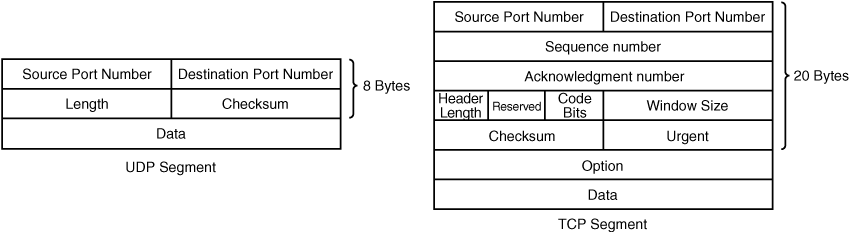
![]() The UDP segment fields are as follows:
The UDP segment fields are as follows:
-
 Source and destination port numbers (16 bits each): Identify the upper-layer protocol (the application) in the sending and receiving devices.
Source and destination port numbers (16 bits each): Identify the upper-layer protocol (the application) in the sending and receiving devices. -
 Length (16 bits): The total number of 32-bit words in the header and the data.
Length (16 bits): The total number of 32-bit words in the header and the data. -
 Checksum (16 bits): The checksum of the header and data fields, used to ensure that the segment is received correctly.
Checksum (16 bits): The checksum of the header and data fields, used to ensure that the segment is received correctly. -
 Data (variable length): The upper-layer data (the application data).
Data (variable length): The upper-layer data (the application data).
![]() The TCP segment fields are as follows:
The TCP segment fields are as follows:
-
 Source and destination port numbers (16 bits each): Identify the upper-layer protocol (the application) in the sending and receiving hosts.
Source and destination port numbers (16 bits each): Identify the upper-layer protocol (the application) in the sending and receiving hosts. -
 Sequence and acknowledgment numbers (32 bits each): Ensure the correct order of the received data and that the data reached the destination.
Sequence and acknowledgment numbers (32 bits each): Ensure the correct order of the received data and that the data reached the destination. -
 Header length (4 bits): The number of 32-bit words in the header.
Header length (4 bits): The number of 32-bit words in the header. -
 Reserved (6 bits): For future use, set to 0.
Reserved (6 bits): For future use, set to 0. -
 Code bits (6 bits): Indicates different types of segments. For example, the SYN (synchronize) bit is used for setting up a session, the ACK (acknowledge) bit is used for acknowledging a segment, and the FIN (finish) bit is used for closing a session.
Code bits (6 bits): Indicates different types of segments. For example, the SYN (synchronize) bit is used for setting up a session, the ACK (acknowledge) bit is used for acknowledging a segment, and the FIN (finish) bit is used for closing a session. -
 Window size (16 bits): The number of octets that the receiving device is willing to accept before it must send an acknowledgment.
Window size (16 bits): The number of octets that the receiving device is willing to accept before it must send an acknowledgment.Note  An octet is 8 bits of data.
An octet is 8 bits of data. -
 Checksum (16 bits): The checksum of the header and data fields, used to ensure that the segment is received correctly.
Checksum (16 bits): The checksum of the header and data fields, used to ensure that the segment is received correctly. -
 Urgent (16 bits): Indicates the end of urgent data.
Urgent (16 bits): Indicates the end of urgent data. -
 Option (0 or 32 bits): Only one option is currently defined: the maximum TCP segment size.
Option (0 or 32 bits): Only one option is currently defined: the maximum TCP segment size. -
 Data (variable): The upper-layer data (the application data).
Data (variable): The upper-layer data (the application data).
![]() Notice that the UDP header is much smaller than the TCP header. UDP does not need the sequencing, acknowledgment, or windowing fields, because it does not establish and maintain connections.
Notice that the UDP header is much smaller than the TCP header. UDP does not need the sequencing, acknowledgment, or windowing fields, because it does not establish and maintain connections.
![]() Port number operation, which is the same for both TCP and UDP, is described in the next section. Following that section, the operation of sequence and acknowledgment numbers and windowing are described; these are crucial to understanding TCP operation.
Port number operation, which is the same for both TCP and UDP, is described in the next section. Following that section, the operation of sequence and acknowledgment numbers and windowing are described; these are crucial to understanding TCP operation.
Port Numbers
![]() Well-known, or standardized, port numbers are assigned to applications so that different implementations of the TCP/IP protocol suite can interoperate. Well-known port numbers are numbers up to 1023; examples include the following:
Well-known, or standardized, port numbers are assigned to applications so that different implementations of the TCP/IP protocol suite can interoperate. Well-known port numbers are numbers up to 1023; examples include the following:
-
 FTP: TCP port 20 (data) and port 21 (control)
FTP: TCP port 20 (data) and port 21 (control) -
 TFTP: UDP port 69
TFTP: UDP port 69 -
 SMTP: TCP port 25
SMTP: TCP port 25 -
 POP3: TCP port 110
POP3: TCP port 110 -
 HTTP: TCP port 80
HTTP: TCP port 80 -
 Telnet: TCP port 23
Telnet: TCP port 23 -
 DNS: TCP and UDP port 53
DNS: TCP and UDP port 53 -
 SNMP: UDP port 161
SNMP: UDP port 161
![]() Port numbers from 1024 through 49151 are called registered port numbers; these are registered for use by other applications. The dynamic ports numbers are those from 49152 through 65535; these can be dynamically assigned by hosts as source port numbers when they create and end sessions.
Port numbers from 1024 through 49151 are called registered port numbers; these are registered for use by other applications. The dynamic ports numbers are those from 49152 through 65535; these can be dynamically assigned by hosts as source port numbers when they create and end sessions.
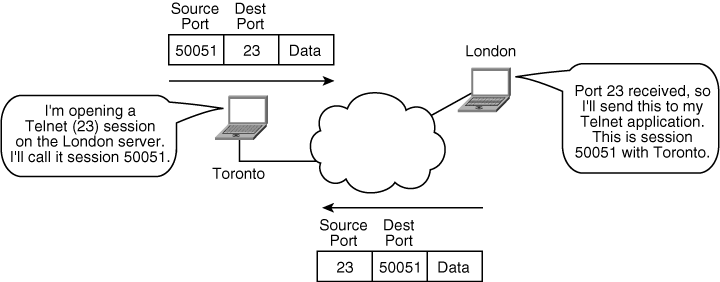
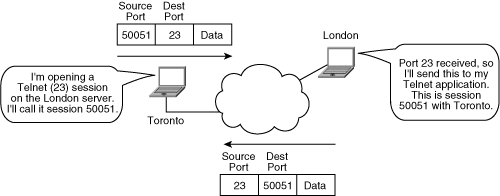
![]() For example, Figure 1-6 illustrates a device in Toronto that is opening a Telnet session (TCP port 23) with a device in London. Note that the source port from Toronto is 50051. Toronto records this Telnet session with London as port 50051 to distinguish it from any other Telnet sessions it might have running (because simultaneous multiple Telnet sessions can be running on a device). The London device receives port number 23 and therefore knows that this is a Telnet session. In its reply, it uses a destination port of 50051, which Toronto knows is the Telnet session it opened with London.
For example, Figure 1-6 illustrates a device in Toronto that is opening a Telnet session (TCP port 23) with a device in London. Note that the source port from Toronto is 50051. Toronto records this Telnet session with London as port 50051 to distinguish it from any other Telnet sessions it might have running (because simultaneous multiple Telnet sessions can be running on a device). The London device receives port number 23 and therefore knows that this is a Telnet session. In its reply, it uses a destination port of 50051, which Toronto knows is the Telnet session it opened with London.
TCP Sequencing, Acknowledgment, and Windowing
![]() To illustrate TCP operation, this section follows a TCP session as it is established, data is sent, and the session is closed.
To illustrate TCP operation, this section follows a TCP session as it is established, data is sent, and the session is closed.
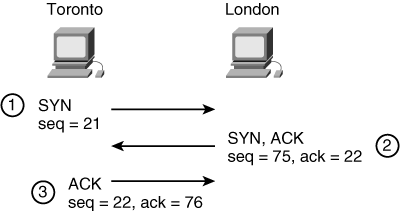
![]() The TCP three-way handshake is shown in Figure 1-7.
The TCP three-way handshake is shown in Figure 1-7.
![]() In this example, a user in Toronto wants to establish a TCP session with a device in London to start a Telnet session. The first step in the handshake involves the initiator, Toronto, sending a segment with the SYN bit set—this indicates that it wants to start a session and synchronize with London. This segment also includes the initial sequence number that Toronto is using—21 in this example.
In this example, a user in Toronto wants to establish a TCP session with a device in London to start a Telnet session. The first step in the handshake involves the initiator, Toronto, sending a segment with the SYN bit set—this indicates that it wants to start a session and synchronize with London. This segment also includes the initial sequence number that Toronto is using—21 in this example.
![]() Assuming that the device in London is willing to establish the session, it returns a segment that also has the SYN bit set. In addition, this segment has the ACK bit set because London is acknowledging that it successfully received a segment from Toronto. The acknowledgment number is set to 22, indicating that London is now expecting to receive segment 22 and therefore that it successfully received number 21. This is known as an expectational acknowledgment. The new segment includes the initial sequence number that London is using—75 in this example.
Assuming that the device in London is willing to establish the session, it returns a segment that also has the SYN bit set. In addition, this segment has the ACK bit set because London is acknowledging that it successfully received a segment from Toronto. The acknowledgment number is set to 22, indicating that London is now expecting to receive segment 22 and therefore that it successfully received number 21. This is known as an expectational acknowledgment. The new segment includes the initial sequence number that London is using—75 in this example.
![]() Finally, Toronto replies with an acknowledgment segment, sequence number 22 (as London is expecting), and acknowledgment number 76, indicating that it is now expecting number 76 and therefore has successfully received number 75. The session is now established, and data can be exchanged between Toronto and London.
Finally, Toronto replies with an acknowledgment segment, sequence number 22 (as London is expecting), and acknowledgment number 76, indicating that it is now expecting number 76 and therefore has successfully received number 75. The session is now established, and data can be exchanged between Toronto and London.
| Note |
|
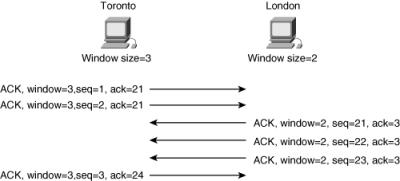
![]() The window size field in the segment controls the flow of the session. It indicates how many octets a device is willing to accept before it must send an acknowledgment. Because each host can have different flow restrictions (for example, one host might be very busy and therefore require that a smaller amount of data be sent at one time), each side of the session can have different window sizes, as illustrated in Figure 1-8.
The window size field in the segment controls the flow of the session. It indicates how many octets a device is willing to accept before it must send an acknowledgment. Because each host can have different flow restrictions (for example, one host might be very busy and therefore require that a smaller amount of data be sent at one time), each side of the session can have different window sizes, as illustrated in Figure 1-8.
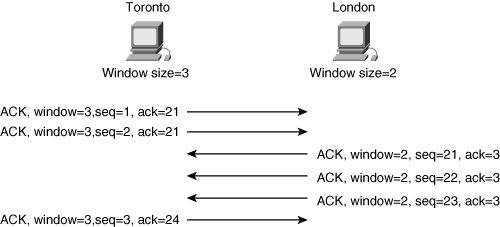
![]() In this example, the window size on Toronto is set to 3, and on London it is set to 2. When Toronto sends data to London, it can send 2 octets before it must wait for an acknowledgment. When London sends data to Toronto, it can send 3 octets before it must wait for an acknowledgment.
In this example, the window size on Toronto is set to 3, and on London it is set to 2. When Toronto sends data to London, it can send 2 octets before it must wait for an acknowledgment. When London sends data to Toronto, it can send 3 octets before it must wait for an acknowledgment.
| Note |
|
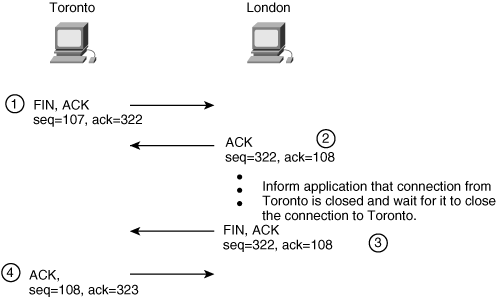
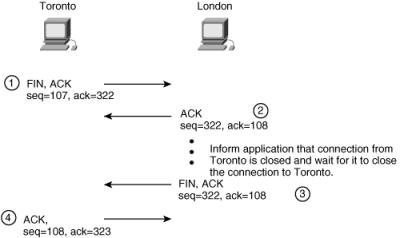
![]() After all the data for the session is sent, the session can be closed. The process is similar to how it was established, using a handshake. In this case, four steps are used, as illustrated in Figure 1-9.
After all the data for the session is sent, the session can be closed. The process is similar to how it was established, using a handshake. In this case, four steps are used, as illustrated in Figure 1-9.
![]() In this example, Toronto wants to close its Telnet session with London. The first step in the handshake involves Toronto sending a segment with the FIN bit set, indicating that it wants to finish the session. This segment also includes the sequence number that Toronto is currently using—107 in this example.
In this example, Toronto wants to close its Telnet session with London. The first step in the handshake involves Toronto sending a segment with the FIN bit set, indicating that it wants to finish the session. This segment also includes the sequence number that Toronto is currently using—107 in this example.
![]() London immediately acknowledges the request. This segment has the ACK bit set with the acknowledgment number set to 108, indicating that London successfully received number 107. This segment includes the sequence number that London is currently using—322 in this example. London then informs its Telnet application that half of the session, the connection from Toronto, is now closed.
London immediately acknowledges the request. This segment has the ACK bit set with the acknowledgment number set to 108, indicating that London successfully received number 107. This segment includes the sequence number that London is currently using—322 in this example. London then informs its Telnet application that half of the session, the connection from Toronto, is now closed.
![]() When the application on the London device requests that the other half of the connection (to Toronto) be closed, London sends a new segment with the FIN bit set, indicating that it wants to close the session.
When the application on the London device requests that the other half of the connection (to Toronto) be closed, London sends a new segment with the FIN bit set, indicating that it wants to close the session.
![]() Finally, Toronto replies with an acknowledgment segment with acknowledgment number 323 (indicating that it has successfully received number 322). The session is now closed in both directions.
Finally, Toronto replies with an acknowledgment segment with acknowledgment number 323 (indicating that it has successfully received number 322). The session is now closed in both directions.
 TCP/IP Internet Layer Protocols
TCP/IP Internet Layer Protocols
![]() The TCP/IP Internet layer corresponds to the OSI network layer and includes the IP-routed protocol, as well as a protocol for message and error reporting.
The TCP/IP Internet layer corresponds to the OSI network layer and includes the IP-routed protocol, as well as a protocol for message and error reporting.
Protocols
![]() The protocols at this layer include the following:
The protocols at this layer include the following:
-
 IP: Provides connectionless, best-effort delivery of datagrams through the network. A unique IP address—a logical address—is assigned to each interface of each device in the network. IP and IP addresses are introduced later in this chapter and are described in more detail in Appendix B, “IPv4 Supplement.”
IP: Provides connectionless, best-effort delivery of datagrams through the network. A unique IP address—a logical address—is assigned to each interface of each device in the network. IP and IP addresses are introduced later in this chapter and are described in more detail in Appendix B, “IPv4 Supplement.”Note  Two versions of IP currently exist: IP version 4 (IPv4) and the emerging IP version 6 (IPv6). In this book, the term IP refers to IPv4. IPv6 is introduced in Chapter 6, “Designing IP Addressing in the Network.”
Two versions of IP currently exist: IP version 4 (IPv4) and the emerging IP version 6 (IPv6). In this book, the term IP refers to IPv4. IPv6 is introduced in Chapter 6, “Designing IP Addressing in the Network.” -
 Internet Control Message Protocol (ICMP): Sends messages and error reports through the network. For example, the ping application included in most TCP/IP protocol suites sends an ICMP echo message to a destination, which then replies with an ICMP echo reply message. Ping provides confirmation that the destination can be reached and gives a measure of how long packets are taking to travel between the source and destination.
Internet Control Message Protocol (ICMP): Sends messages and error reports through the network. For example, the ping application included in most TCP/IP protocol suites sends an ICMP echo message to a destination, which then replies with an ICMP echo reply message. Ping provides confirmation that the destination can be reached and gives a measure of how long packets are taking to travel between the source and destination.
| Note |
|
| Note |
|
IP Datagrams
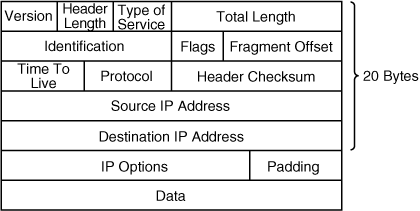
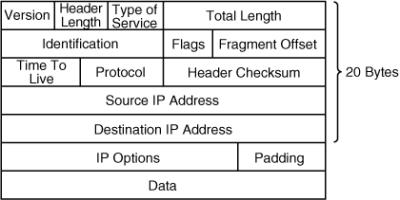
![]() Figure 1-10 illustrates the fields of an IP datagram.
Figure 1-10 illustrates the fields of an IP datagram.
![]() The IP datagram fields are as follows:
The IP datagram fields are as follows:
-
 Version (4 bits): Identifies the IP version—in this case, version 4.
Version (4 bits): Identifies the IP version—in this case, version 4. -
 Header length (4 bits): The number of 32-bit words in the header (including the options).
Header length (4 bits): The number of 32-bit words in the header (including the options). -
 Type of service (ToS) (8 bits): Specifies how the datagram should be handled within the network. These bits mark traffic for a specific quality of service (QoS), which is further described in Chapter 4.
Type of service (ToS) (8 bits): Specifies how the datagram should be handled within the network. These bits mark traffic for a specific quality of service (QoS), which is further described in Chapter 4. -
 Total length (16 bits): The total number of octets in the header and data fields.
Total length (16 bits): The total number of octets in the header and data fields. -
 Identification (16 bits), flags (3 bits), and fragment offset (13 bits): Handle cases where a large datagram must be fragmented—split into multiple packets—to go through a network that cannot handle datagrams of that size.
Identification (16 bits), flags (3 bits), and fragment offset (13 bits): Handle cases where a large datagram must be fragmented—split into multiple packets—to go through a network that cannot handle datagrams of that size. -
 Time to Live (TTL) (8 bits): Ensures that datagrams do not loop endlessly in the network; this field must be decremented by 1 by each router that the datagram passes through.
Time to Live (TTL) (8 bits): Ensures that datagrams do not loop endlessly in the network; this field must be decremented by 1 by each router that the datagram passes through. -
 Protocol (8 bits): Indicates the upper-layer (Layer 4, the transport layer) protocol that the data is for. Therefore, this field might indicate the type of segment that the datagram is carrying, similar to how the port number field in the UDP and TCP segments indicates the type of application that the segment is carrying. A protocol number of 6 means that the datagram is carrying a TCP segment, whereas a protocol number of 17 means that the datagram is carrying a UDP segment. The protocol may have other values, such as a value indicating that traffic from a specific routing protocol is being carried inside the datagram.
Protocol (8 bits): Indicates the upper-layer (Layer 4, the transport layer) protocol that the data is for. Therefore, this field might indicate the type of segment that the datagram is carrying, similar to how the port number field in the UDP and TCP segments indicates the type of application that the segment is carrying. A protocol number of 6 means that the datagram is carrying a TCP segment, whereas a protocol number of 17 means that the datagram is carrying a UDP segment. The protocol may have other values, such as a value indicating that traffic from a specific routing protocol is being carried inside the datagram. -
 Header checksum (16 bits): Ensures that the header is received correctly.
Header checksum (16 bits): Ensures that the header is received correctly. -
 Source and destination IP addresses (32 bits each): Logical IP addresses assigned to the source and destination of the datagram, respectively. IP addresses are introduced later in this chapter, in the “Addressing” section.
Source and destination IP addresses (32 bits each): Logical IP addresses assigned to the source and destination of the datagram, respectively. IP addresses are introduced later in this chapter, in the “Addressing” section. -
 IP options and padding (variable length; 0 or a multiple of 32 bits): Used for network testing and debugging.
IP options and padding (variable length; 0 or a multiple of 32 bits): Used for network testing and debugging. -
 Data (variable): The upper-layer (transport layer) data.
Data (variable): The upper-layer (transport layer) data.
 TCP/IP-Related Data Link Layer Protocol
TCP/IP-Related Data Link Layer Protocol
![]() The TCP/IP data link layer corresponds to the OSI data link layer. It includes the Address Resolution Protocol (ARP) to request the MAC address (the data link layer physical address) for a given IP address. The returned MAC address is used as the destination address in the frames that encapsulate the packets of data being routed to the destination IP address.
The TCP/IP data link layer corresponds to the OSI data link layer. It includes the Address Resolution Protocol (ARP) to request the MAC address (the data link layer physical address) for a given IP address. The returned MAC address is used as the destination address in the frames that encapsulate the packets of data being routed to the destination IP address.
Routing
![]() This section examines how routers work and introduces routing tables and routing protocols. Routers work at the OSI model network layer. The main functions of a router are first to determine the best path that each packet should take to get to its destination and second to send the packet on its way. Sending the packet out the appropriate interface, along the best path, is also called switching the packet because the packet is encapsulated in a new frame, with the appropriate framing information.
This section examines how routers work and introduces routing tables and routing protocols. Routers work at the OSI model network layer. The main functions of a router are first to determine the best path that each packet should take to get to its destination and second to send the packet on its way. Sending the packet out the appropriate interface, along the best path, is also called switching the packet because the packet is encapsulated in a new frame, with the appropriate framing information.
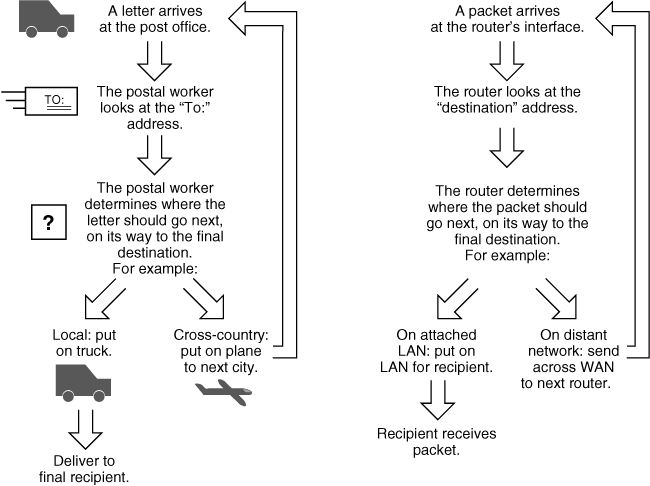
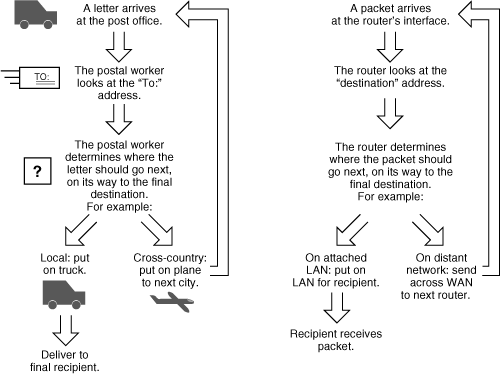
![]() Therefore, a router’s job is much like that of a worker at a post office. The postal worker looks at the address label on the letter (the network layer address on the packet), determines which way the letter (the packet) should be sent, and then sends it. The comparison between the post office and a router is illustrated in Figure 1-11.
Therefore, a router’s job is much like that of a worker at a post office. The postal worker looks at the address label on the letter (the network layer address on the packet), determines which way the letter (the packet) should be sent, and then sends it. The comparison between the post office and a router is illustrated in Figure 1-11.
 Routers Work at the Lower Three OSI Layers
Routers Work at the Lower Three OSI Layers
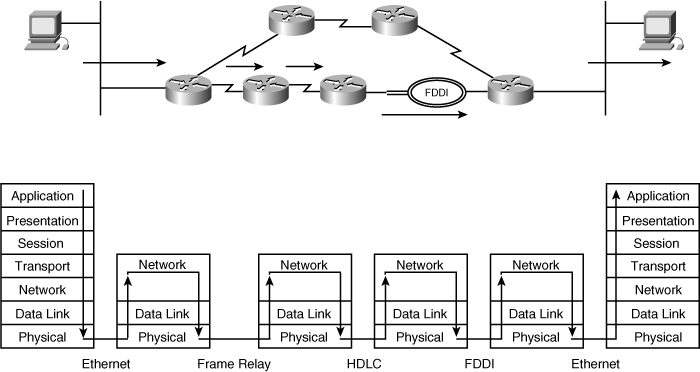
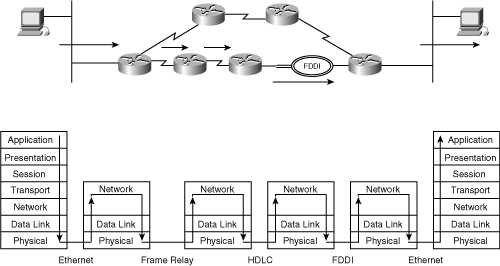
![]() The router doesn’t care what is in the higher layers—what kind of data is in the packet. The router is just responsible for sending the packet the correct way. The router does have to be concerned with the data link and physical layers, though, because it might have to receive and send data on different media. For example, a packet received on an Ethernet LAN might have to be sent out on a Frame Relay WAN, requiring the router to know how to communicate on both these types of media. In terms of layers, therefore, a router unencapsulates received data up to the network layer and then encapsulates the data again into the appropriate frame and bit types. This process is illustrated in Figure 1-12, where the PC on the left is sending data to the PC on the right. The routers have determined that the path marked with the arrows is the best path between the PCs.
The router doesn’t care what is in the higher layers—what kind of data is in the packet. The router is just responsible for sending the packet the correct way. The router does have to be concerned with the data link and physical layers, though, because it might have to receive and send data on different media. For example, a packet received on an Ethernet LAN might have to be sent out on a Frame Relay WAN, requiring the router to know how to communicate on both these types of media. In terms of layers, therefore, a router unencapsulates received data up to the network layer and then encapsulates the data again into the appropriate frame and bit types. This process is illustrated in Figure 1-12, where the PC on the left is sending data to the PC on the right. The routers have determined that the path marked with the arrows is the best path between the PCs.
![]() In this figure, notice that only the two PCs care about the upper layers, whereas all the routers in the path concern themselves with only the lower three layers.
In this figure, notice that only the two PCs care about the upper layers, whereas all the routers in the path concern themselves with only the lower three layers.
 Routing Tables
Routing Tables
![]() To determine the best path on which to send a packet, a router must know where the packet’s destination network is.
To determine the best path on which to send a packet, a router must know where the packet’s destination network is.
![]() However routes are learned, routers keep the best path (or multiple best paths) to each destination in a routing table. A routing table contains a list of all the networks that a router knows how to reach. For each network, the routing table typically contains the following items:
However routes are learned, routers keep the best path (or multiple best paths) to each destination in a routing table. A routing table contains a list of all the networks that a router knows how to reach. For each network, the routing table typically contains the following items:
-
 How the route to the network was learned (for example, statically or by using a routing protocol).
How the route to the network was learned (for example, statically or by using a routing protocol). -
 The network address of the router from which the route to the network was learned (if applicable).
The network address of the router from which the route to the network was learned (if applicable). -
 The interface (port) on the router through which the network can be reached.
The interface (port) on the router through which the network can be reached. -
 The metric of the route. The metric is a measurement, such as the number of other routers that the path goes through, that routing protocols use when determining the best path.
The metric of the route. The metric is a measurement, such as the number of other routers that the path goes through, that routing protocols use when determining the best path.
| Note |
|
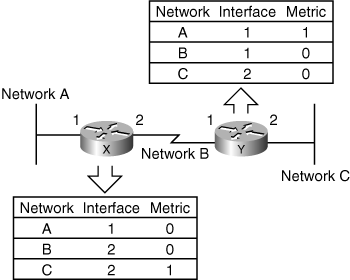
![]() For example, in the network shown in Figure 1-13, the metric used is hops—the number of other routers between this router and the destination network. Both routers know about all three networks. Router X, on the left, knows about networks A and B because it is connected to them (hence the metric of 0) and knows about network C from Router Y (hence the metric of 1). Router Y, on the right, knows about networks B and C because it is connected to them (hence the metric of 0) and knows about network A from Router X (hence the metric of 1).
For example, in the network shown in Figure 1-13, the metric used is hops—the number of other routers between this router and the destination network. Both routers know about all three networks. Router X, on the left, knows about networks A and B because it is connected to them (hence the metric of 0) and knows about network C from Router Y (hence the metric of 1). Router Y, on the right, knows about networks B and C because it is connected to them (hence the metric of 0) and knows about network A from Router X (hence the metric of 1).
 Routing Protocols
Routing Protocols
![]() Routers use routing protocols to exchange routing information. Routing protocols allow routers to learn from other routers the networks that are available so that data can be sent in the correct direction. Remember that two routers communicating with each other must use the same routing protocol or they can’t understand each other.
Routers use routing protocols to exchange routing information. Routing protocols allow routers to learn from other routers the networks that are available so that data can be sent in the correct direction. Remember that two routers communicating with each other must use the same routing protocol or they can’t understand each other.
![]() The TCP/IP protocol suite includes the following routing protocols:
The TCP/IP protocol suite includes the following routing protocols:
-
 Routing Information Protocol (RIP), versions 1 and 2 (RIPv1 and RIPv2)
Routing Information Protocol (RIP), versions 1 and 2 (RIPv1 and RIPv2) -
 Enhanced Interior Gateway Routing Protocol (EIGRP)
Enhanced Interior Gateway Routing Protocol (EIGRP) -
 Open Shortest Path First (OSPF)
Open Shortest Path First (OSPF) -
 Integrated Intermediate System-to-Intermediate System (IS-IS)
Integrated Intermediate System-to-Intermediate System (IS-IS) -
 Border Gateway Protocol (BGP) Version 4 (BGP-4)
Border Gateway Protocol (BGP) Version 4 (BGP-4)
| Note |
|
![]() The previous sections introduced the basics of routing and how routers learn about the available networks so that data can be sent along the correct path. Routers look at the packet’s destination address to determine where the packet is going so that they can then select the best route to get the packet there. The following section discusses these addresses.
The previous sections introduced the basics of routing and how routers learn about the available networks so that data can be sent along the correct path. Routers look at the packet’s destination address to determine where the packet is going so that they can then select the best route to get the packet there. The following section discusses these addresses.

0 comments
Post a Comment