Other Types of Firewalls
![]() Over the years, variations of standards stateful firewalls have emerged. Some examples of those variations, which provide additional or restrictive features, are deep packet inspection (DPI) firewalls and Layer 2 firewalls.
Over the years, variations of standards stateful firewalls have emerged. Some examples of those variations, which provide additional or restrictive features, are deep packet inspection (DPI) firewalls and Layer 2 firewalls.
![]() Application inspection firewalls ensure the security of applications and services. Some applications require special handling by the firewall application inspection function. Applications that require special application inspection functions are those that embed IP addressing information in the user data packet or that open secondary channels on dynamically assigned ports.
Application inspection firewalls ensure the security of applications and services. Some applications require special handling by the firewall application inspection function. Applications that require special application inspection functions are those that embed IP addressing information in the user data packet or that open secondary channels on dynamically assigned ports.
![]() The application inspection function works with NAT to help identify the location of the embedded addressing information. This arrangement allows NAT to translate embedded addresses and to update any checksum or other fields that are affected by the translation.
The application inspection function works with NAT to help identify the location of the embedded addressing information. This arrangement allows NAT to translate embedded addresses and to update any checksum or other fields that are affected by the translation.
![]() The application inspection function also monitors sessions to determine the port numbers for secondary channels. Many protocols open secondary TCP or UDP ports. The initial session on a well-known port negotiates dynamically assigned port numbers. The application inspection function monitors these sessions, identifies the dynamic port assignments, and permits data exchange on these ports for the duration of the specific session.
The application inspection function also monitors sessions to determine the port numbers for secondary channels. Many protocols open secondary TCP or UDP ports. The initial session on a well-known port negotiates dynamically assigned port numbers. The application inspection function monitors these sessions, identifies the dynamic port assignments, and permits data exchange on these ports for the duration of the specific session.
![]() An application inspection firewall behaves in different ways according to each layer:
An application inspection firewall behaves in different ways according to each layer:
-
 Transport layer mechanism: From a transport layer perspective, the application inspection firewall acts like a stateful firewall by examining information in the headers of Layer 3 packets and Layer 4 segments. For example, the application inspection firewall looks at the TCP header for SYN, RST, ACK, FIN, and other control codes to determine the state of the connection.
Transport layer mechanism: From a transport layer perspective, the application inspection firewall acts like a stateful firewall by examining information in the headers of Layer 3 packets and Layer 4 segments. For example, the application inspection firewall looks at the TCP header for SYN, RST, ACK, FIN, and other control codes to determine the state of the connection. -
 Session layer mechanism: From a session layer perspective, the application inspection firewall checks the conformity of commands within a known protocol. For example, when the application inspection firewall checks the SMTP message type, it allows only acceptable message types on Layer 5 (such as, DATA, HELO, MAIL, NOOP, QUIT, RCPT, RSET). In addition, the application inspection firewall checks whether the command attributes that are used (for example, length of a message type) conform to the internal rules. These rules often trust the RFC of a specific protocol.
Session layer mechanism: From a session layer perspective, the application inspection firewall checks the conformity of commands within a known protocol. For example, when the application inspection firewall checks the SMTP message type, it allows only acceptable message types on Layer 5 (such as, DATA, HELO, MAIL, NOOP, QUIT, RCPT, RSET). In addition, the application inspection firewall checks whether the command attributes that are used (for example, length of a message type) conform to the internal rules. These rules often trust the RFC of a specific protocol. -
 Application layer mechanism: From an application layer perspective, the application inspection firewall protocol is rarely supported. Sometimes application layer firewalls provide protocol support for HTTP, and the application inspection firewall can determine whether the content is really an HTML website or a tunneled application, such as Kazaa Media Desktop or eDonkey. In the case of a tunneled application, the application inspection firewall would block the content or terminate the connection. Future development will provide application inspection support for more protocols on an application inspection firewall.
Application layer mechanism: From an application layer perspective, the application inspection firewall protocol is rarely supported. Sometimes application layer firewalls provide protocol support for HTTP, and the application inspection firewall can determine whether the content is really an HTML website or a tunneled application, such as Kazaa Media Desktop or eDonkey. In the case of a tunneled application, the application inspection firewall would block the content or terminate the connection. Future development will provide application inspection support for more protocols on an application inspection firewall.
![]() There are several advantages of an application inspection firewall:
There are several advantages of an application inspection firewall:
-
 Application inspection firewalls are aware of the state of Layer 4 and Layer 5 connections. For example, the application inspection firewall knows that a Layer 5 SMTP MAIL FROM command always follows a HELO command.
Application inspection firewalls are aware of the state of Layer 4 and Layer 5 connections. For example, the application inspection firewall knows that a Layer 5 SMTP MAIL FROM command always follows a HELO command. -
 Application inspection firewalls check the conformity of application commands at Layer 5.
Application inspection firewalls check the conformity of application commands at Layer 5. -
 Application inspection firewalls have the capability to check and affect Layer 7.
Application inspection firewalls have the capability to check and affect Layer 7. -
 Application inspection firewalls can prevent more kinds of attacks than stateful firewalls can. For example, application inspection firewalls can stop an attacker from trying to set up a virtual private network (VPN) tunnel (triggered from inside the network) through an application firewall by way of tunneled HTTP requests.
Application inspection firewalls can prevent more kinds of attacks than stateful firewalls can. For example, application inspection firewalls can stop an attacker from trying to set up a virtual private network (VPN) tunnel (triggered from inside the network) through an application firewall by way of tunneled HTTP requests.
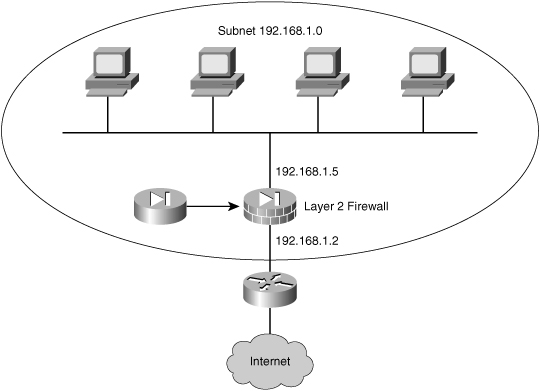
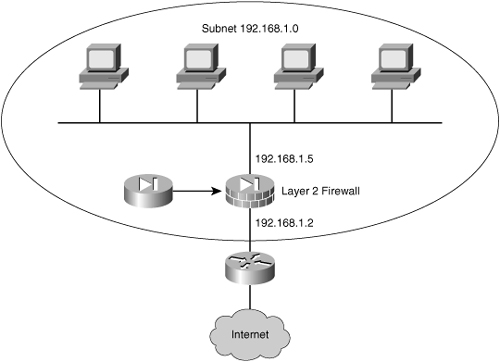
![]() Cisco PIX and Cisco ASA Adaptive Security Appliance Software Version 7.0 and Cisco Firewall Services Module Version 2.2 debut the capability to deploy a security appliance in a secure bridging mode as a Layer 2 device to provide rich Layer 2 through 7 security services for the protected network. This capability enables businesses to deploy security appliances into existing network environments without the need to readdress the network. Although the security appliance can be invisible to devices on both sides of a protected network, as shown in Figure 3-9, administrators can use an exposed IP address to manage the appliance.
Cisco PIX and Cisco ASA Adaptive Security Appliance Software Version 7.0 and Cisco Firewall Services Module Version 2.2 debut the capability to deploy a security appliance in a secure bridging mode as a Layer 2 device to provide rich Layer 2 through 7 security services for the protected network. This capability enables businesses to deploy security appliances into existing network environments without the need to readdress the network. Although the security appliance can be invisible to devices on both sides of a protected network, as shown in Figure 3-9, administrators can use an exposed IP address to manage the appliance.
| Note |
|
| Tip |
|
Cisco Family of Firewalls
![]() Cisco offers firewalls on different platforms:
Cisco offers firewalls on different platforms:
![]() The sections that follow describe these platforms in greater detail.
The sections that follow describe these platforms in greater detail.
 Cisco IOS Firewalls
Cisco IOS Firewalls
![]() A Cisco IOS Firewall is a specialized Cisco IOS feature that runs on Cisco routers. It is an enterprise-class firewall product that is rich with features for small and medium-sized businesses (SMB) and enterprise branch offices. The following are some of the main features of a Cisco IOS Firewall:
A Cisco IOS Firewall is a specialized Cisco IOS feature that runs on Cisco routers. It is an enterprise-class firewall product that is rich with features for small and medium-sized businesses (SMB) and enterprise branch offices. The following are some of the main features of a Cisco IOS Firewall:
-
 Zone-based policy framework for intuitive policy management
Zone-based policy framework for intuitive policy management -
 Application firewalling for web, email, and other traffic
Application firewalling for web, email, and other traffic -
 Instant messenger and peer-to-peer application filtering
Instant messenger and peer-to-peer application filtering -
 VoIP protocol firewalling
VoIP protocol firewalling -
 Virtual routing and forwarding (VRF) firewalling
Virtual routing and forwarding (VRF) firewalling -
 Wireless integration
Wireless integration -
 Stateful failover
Stateful failover -
 Local URL whitelist and blacklist support
Local URL whitelist and blacklist support
![]() Another important feature of Cisco IOS Firewalls, deployed on specific models, is the assurance of its security standard known as FIPS 140.
Another important feature of Cisco IOS Firewalls, deployed on specific models, is the assurance of its security standard known as FIPS 140.
![]() The Federal Information Processing Standard (FIPS) 140 is a U.S. government and Canadian government standard that specifies security requirements for cryptographic modules. FIPS 140 has four levels of assurance. Level 1 is the lowest level, and Level 4 is the most stringent. Each level builds upon the one below it, so a Level 2 certification means that a product meets the requirements for both Level 1 and Level 2.
The Federal Information Processing Standard (FIPS) 140 is a U.S. government and Canadian government standard that specifies security requirements for cryptographic modules. FIPS 140 has four levels of assurance. Level 1 is the lowest level, and Level 4 is the most stringent. Each level builds upon the one below it, so a Level 2 certification means that a product meets the requirements for both Level 1 and Level 2.
| Note |
|
![]() Another benefit of Cisco security platforms is their conformance to Common Criteria.
Another benefit of Cisco security platforms is their conformance to Common Criteria.
![]() The Common Criteria is an international standard for evaluating IT security. It was developed by a consortium of countries to replace a number of existing country-specific security assessment processes, and was intended to establish a single standard for international use. Currently, the Common Criteria is officially recognized by 14 countries, and evaluations can be conducted by any certified Common Criteria laboratory in a member country. To maintain the independent nature of the Common Criteria, evaluation results from a certified lab are submitted to the Common Criteria organization of the corresponding country for independent validation. This independent validation process, which distinguishes Common Criteria from some commercial certifications, ensures that the evaluation process is consistent across labs, and that it cannot be influenced by financial motives.
The Common Criteria is an international standard for evaluating IT security. It was developed by a consortium of countries to replace a number of existing country-specific security assessment processes, and was intended to establish a single standard for international use. Currently, the Common Criteria is officially recognized by 14 countries, and evaluations can be conducted by any certified Common Criteria laboratory in a member country. To maintain the independent nature of the Common Criteria, evaluation results from a certified lab are submitted to the Common Criteria organization of the corresponding country for independent validation. This independent validation process, which distinguishes Common Criteria from some commercial certifications, ensures that the evaluation process is consistent across labs, and that it cannot be influenced by financial motives.
![]() Table 3-1 illustrates for which security certifications the routers in the Cisco router family qualify.
Table 3-1 illustrates for which security certifications the routers in the Cisco router family qualify.
|
|
| ||
|---|---|---|---|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||
| Note |
|
 Cisco PIX 500 Series Security Appliances
Cisco PIX 500 Series Security Appliances
![]() The Cisco PIX 500 series Security Appliance delivers robust user and application policy enforcement, multivector attack protection, and secure connectivity services in cost-effective, easy-to-deploy solutions. These purpose-built appliances provide multiple integrated security and networking services:
The Cisco PIX 500 series Security Appliance delivers robust user and application policy enforcement, multivector attack protection, and secure connectivity services in cost-effective, easy-to-deploy solutions. These purpose-built appliances provide multiple integrated security and networking services:
-
 Advanced application-aware firewall services
Advanced application-aware firewall services -
 Market-leading VoIP and multimedia security
Market-leading VoIP and multimedia security -
 Robust site-to-site and remote-access IPsec VPN connectivity
Robust site-to-site and remote-access IPsec VPN connectivity -
 Award-winning resiliency
Award-winning resiliency -
 Intelligent networking services
Intelligent networking services -
 Flexible management solutions
Flexible management solutions
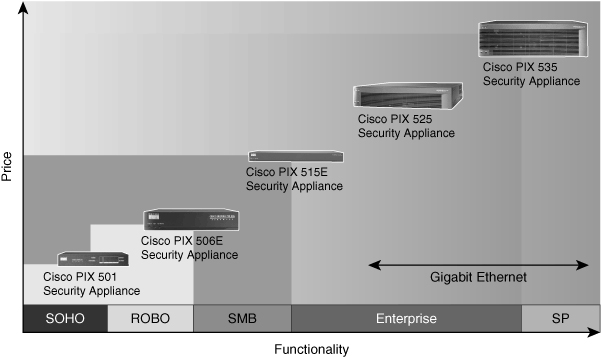
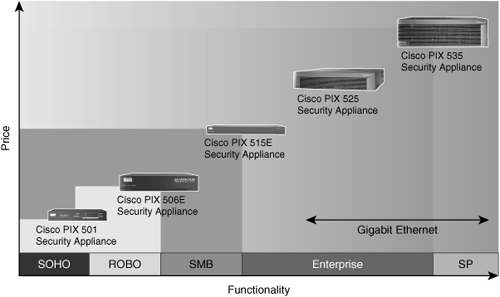
![]() The Cisco PIX 500 series Security Appliances scale to meet a range of requirements and network sizes. The Cisco PIX 500 series Security Appliances currently consists of five models: the PIX 501, 506E, 515E, 525, and 535. Figure 3-10 provides a visual reference of the PIX 500 family of products.
The Cisco PIX 500 series Security Appliances scale to meet a range of requirements and network sizes. The Cisco PIX 500 series Security Appliances currently consists of five models: the PIX 501, 506E, 515E, 525, and 535. Figure 3-10 provides a visual reference of the PIX 500 family of products.
| Note |
|
| Note |
|
 Cisco ASA 5500 Series Adaptive Security Appliances
Cisco ASA 5500 Series Adaptive Security Appliances
![]() Cisco ASA 5500 series Adaptive Security Appliances are easy-to-deploy solutions that integrate world-class firewall, Cisco Unified Communications (voice and video) security, Secure Sockets Layer (SSL) and IPsec VPN, IPS, and content security services in a flexible, modular product family. Designed as a key component of the Cisco Self-Defending Network, the ASA 5500 series appliances provide intelligent threat defense and secure communications services that stop attacks before they affect business continuity. Designed to protect networks of all sizes, the ASA 5500 series appliances enable organizations to lower their overall deployment and operations costs while delivering comprehensive multilayer security.
Cisco ASA 5500 series Adaptive Security Appliances are easy-to-deploy solutions that integrate world-class firewall, Cisco Unified Communications (voice and video) security, Secure Sockets Layer (SSL) and IPsec VPN, IPS, and content security services in a flexible, modular product family. Designed as a key component of the Cisco Self-Defending Network, the ASA 5500 series appliances provide intelligent threat defense and secure communications services that stop attacks before they affect business continuity. Designed to protect networks of all sizes, the ASA 5500 series appliances enable organizations to lower their overall deployment and operations costs while delivering comprehensive multilayer security.
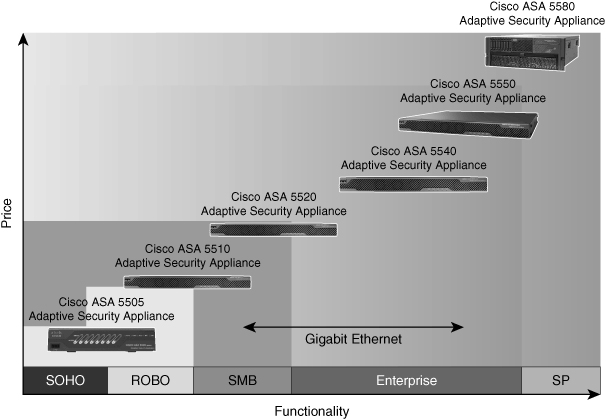
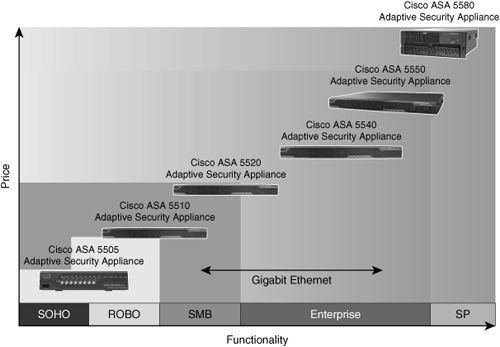
![]() The Cisco ASA scales to meet a range of requirements and network sizes, as shown in Figure 3-11. The Cisco ASA 5500 series appliances currently consist of five models: the Cisco ASA 5505, 5510, 5520, 5540, and 5550.
The Cisco ASA scales to meet a range of requirements and network sizes, as shown in Figure 3-11. The Cisco ASA 5500 series appliances currently consist of five models: the Cisco ASA 5505, 5510, 5520, 5540, and 5550.
| Note |
|
 Cisco Firewall Services Module
Cisco Firewall Services Module
![]() The Cisco Firewall Services Module (FWSM) is a high-speed, integrated firewall module (commonly called a “blade”) for Cisco Catalyst 6500 switches and Cisco 7600 series routers and provides the fastest firewall data rates in the industry. Up to four FWSMs can be installed in a single switch chassis. Based on Cisco PIX Firewall technology, the Cisco FWSM offers large enterprises and service providers unmatched security, reliability, and performance.
The Cisco Firewall Services Module (FWSM) is a high-speed, integrated firewall module (commonly called a “blade”) for Cisco Catalyst 6500 switches and Cisco 7600 series routers and provides the fastest firewall data rates in the industry. Up to four FWSMs can be installed in a single switch chassis. Based on Cisco PIX Firewall technology, the Cisco FWSM offers large enterprises and service providers unmatched security, reliability, and performance.
Developing an Effective Firewall Policy
![]() Best practice documents are a composite effort of security practitioners. This partial list is designed to be generic and serve only as a starting point for your own firewall security policy:
Best practice documents are a composite effort of security practitioners. This partial list is designed to be generic and serve only as a starting point for your own firewall security policy:
-
 Position firewalls at key security boundaries.
Position firewalls at key security boundaries. -
 Firewalls are the primary security device, but it is unwise to rely exclusively on a firewall for security.
Firewalls are the primary security device, but it is unwise to rely exclusively on a firewall for security. -
 Deny all traffic by default and permit only services that are needed.
Deny all traffic by default and permit only services that are needed. -
 Ensure that physical access to the firewall is controlled.
Ensure that physical access to the firewall is controlled. -
 Regularly monitor firewall logs. Cisco Security Monitoring, Analysis, and Response System (MARS) is especially useful in monitoring firewall logs.
Regularly monitor firewall logs. Cisco Security Monitoring, Analysis, and Response System (MARS) is especially useful in monitoring firewall logs. -
 Practice change management for firewall configuration changes.
Practice change management for firewall configuration changes. -
 Remember that firewalls primarily protect from technical attacks originating from the outside. Inside attacks tend to be nontechnical in nature, such as accidentally deleting a mission-critical data, or accidentally unplugging a device, thus creating a DoS attack, albeit an unintentional one.
Remember that firewalls primarily protect from technical attacks originating from the outside. Inside attacks tend to be nontechnical in nature, such as accidentally deleting a mission-critical data, or accidentally unplugging a device, thus creating a DoS attack, albeit an unintentional one.
| Tip |
|
 Creating Static Packet Filters Using ACLs
Creating Static Packet Filters Using ACLs
![]() Cisco provides basic traffic filtering capabilities with ACLs. You can configure ACLs for all routed network protocols to filter packets as the packets pass through a router or security appliance. There are many reasons to configure ACLs. For example, you can use ACLs to restrict the contents of routing updates or to provide traffic flow control. One of the most important reasons to configure ACLs is to provide security for your network.
Cisco provides basic traffic filtering capabilities with ACLs. You can configure ACLs for all routed network protocols to filter packets as the packets pass through a router or security appliance. There are many reasons to configure ACLs. For example, you can use ACLs to restrict the contents of routing updates or to provide traffic flow control. One of the most important reasons to configure ACLs is to provide security for your network.
![]() This section outlines the types of ACLs available and provides guidelines that help create ACLs to provide network security.
This section outlines the types of ACLs available and provides guidelines that help create ACLs to provide network security.

0 comments
Post a Comment