Overview
This chapter reviews the purpose of VLANs and describes how VLAN implementation can simplify network management and troubleshooting, and can improve network performance. It reviews the end-to-end VLAN architecture where VLANs span switches and local VLANs connected via Layer 3 switching used in the Campus Enterprise Architecture. In addition to this, trunking and VLAN Trunking Protocol (VTP) that are also the significant features of deploying VLANs are discussed.
This chapter addresses how design considerations determine which VLANs span all the switches in a network and which VLANs remain local to a switch block. The configuration components of this chapter describe how individual switch ports can carry traffic for one or more VLANs, depending on their configuration as access or trunk ports. In addition, this chapter explains both why and how VLAN implementation occurs in an enterprise network.
In some scenarios, devices must belong to the same VLAN but still be prevented from communicating with one another. A specific feature, private VLANs, is useful for fine-tuning which devices can be reached by all VLAN members and which devices should be isolated. This chapter also describes how to use and configure private VLANs.
Finally, when several physical links connect the same devices, network designers can create a specific configuration to join those physical links in a common virtual connection using EtherChanneling. This chapter also explains the various possible technologies available to configure EtherChannel.
This chapter covers the following topics:
-
Given a large enterprise network, design, plan, and implement VLANs based on business and technical requirements and constraints.
-
Given a large enterprise network design, plan, implement and verify trunking based on business and technical requirements and constraints.
-
Design, plan, and implement and verify VTP based on business and technical requirements and constraints.
-
Plan, implement, and verify private VLANs.
-
Plan, implement, and verify EtherChannel in a Layer 2 topology based on business and technical requirements and constraints.
Implementing VLAN Technologies in a Campus Network
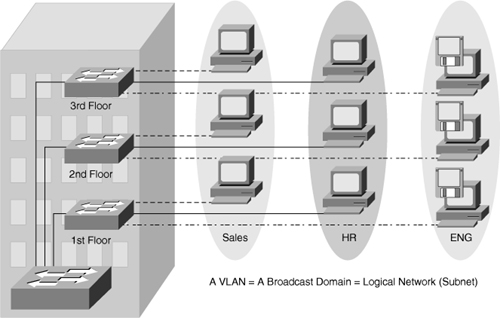
![]() A VLAN is a logical group of end devices with a common set of requirements independent of their physical location, as shown in Figure 2-1, in which sales, human resources, and engineering are three different VLANs spread across all three floors.
A VLAN is a logical group of end devices with a common set of requirements independent of their physical location, as shown in Figure 2-1, in which sales, human resources, and engineering are three different VLANs spread across all three floors.
![]() Although switches do not propagate Layer 2 broadcasts between VLANs, VLANs can exist anywhere in the switch network. Because a VLAN is a single broadcast domain, campus design best practices recommend mapping a VLAN generally to one IP subnet. To communicate between VLANs, packets need to pass through a router or Layer 3 device.
Although switches do not propagate Layer 2 broadcasts between VLANs, VLANs can exist anywhere in the switch network. Because a VLAN is a single broadcast domain, campus design best practices recommend mapping a VLAN generally to one IP subnet. To communicate between VLANs, packets need to pass through a router or Layer 3 device.
![]() Generally, a port carries traffic only for the single VLAN. For a VLAN to span multiple switches, Catalyst switches use trunks. A trunk carries traffic for multiple VLANs by using Inter-Switch Link (ISL) encapsulation or IEEE 802.1Q. This chapter discusses trunking in more detail in later sections. Because VLANs are an important aspect of any campus design, almost all Cisco devices support VLANs and trunking.
Generally, a port carries traffic only for the single VLAN. For a VLAN to span multiple switches, Catalyst switches use trunks. A trunk carries traffic for multiple VLANs by using Inter-Switch Link (ISL) encapsulation or IEEE 802.1Q. This chapter discusses trunking in more detail in later sections. Because VLANs are an important aspect of any campus design, almost all Cisco devices support VLANs and trunking.
| Note |
|
![]() When a network architect hands off a design, you need to create an implementation plan based on the knowledge of VLANs and trunks.
When a network architect hands off a design, you need to create an implementation plan based on the knowledge of VLANs and trunks.
![]() This section discusses in detail how to plan, implement, and verify VLAN technologies and address schemes to meet the given business and technical requirements and constraints. This ability includes being able to meet these objectives:
This section discusses in detail how to plan, implement, and verify VLAN technologies and address schemes to meet the given business and technical requirements and constraints. This ability includes being able to meet these objectives:
-
 Describe the different VLAN segmentation models.
Describe the different VLAN segmentation models. -
 Discuss VLAN implementation in a hierarchical network.
Discuss VLAN implementation in a hierarchical network. -
 Given an enterprise VLAN network design, describe the information needed to create an implementation plan and the choices that need to be made and analyze the consequences of those choices.
Given an enterprise VLAN network design, describe the information needed to create an implementation plan and the choices that need to be made and analyze the consequences of those choices. -
 Discuss best practices for VLAN implementation.
Discuss best practices for VLAN implementation. -
 Given an enterprise VLAN network design, configure, verify, and troubleshoot VLANs.
Given an enterprise VLAN network design, configure, verify, and troubleshoot VLANs.
 VLAN Segmentation Model
VLAN Segmentation Model
![]() Larger, flat networks generally consist of many end devices in which broadcasts and unknown unicast packets are flooded on all ports in the network One advantage of using VLANs is the capability to segment the Layer 2 broadcast domain. All devices in a VLAN are members of the same broadcast domain. If an end device transmits a Layer 2 broadcast, all other members of the VLAN receive the broadcast. Switches filter the broadcast from all the ports or devices that are not part of the same VLAN.
Larger, flat networks generally consist of many end devices in which broadcasts and unknown unicast packets are flooded on all ports in the network One advantage of using VLANs is the capability to segment the Layer 2 broadcast domain. All devices in a VLAN are members of the same broadcast domain. If an end device transmits a Layer 2 broadcast, all other members of the VLAN receive the broadcast. Switches filter the broadcast from all the ports or devices that are not part of the same VLAN.
![]() In a campus design, a network administrator can design a campus network with one of two models: end-to-end VLANs or local VLANs. Business and technical requirements, past experience, and political motivations can influence the design chosen. Choosing the right model initially can help create a solid foundation upon which to grow the business. Each model has its own advantages and disadvantages. When configuring a switch for an existing network, try to determine which model is used so that you can understand the logic behind each switch configuration and position in the infrastructure.
In a campus design, a network administrator can design a campus network with one of two models: end-to-end VLANs or local VLANs. Business and technical requirements, past experience, and political motivations can influence the design chosen. Choosing the right model initially can help create a solid foundation upon which to grow the business. Each model has its own advantages and disadvantages. When configuring a switch for an existing network, try to determine which model is used so that you can understand the logic behind each switch configuration and position in the infrastructure.
End-to-End VLAN
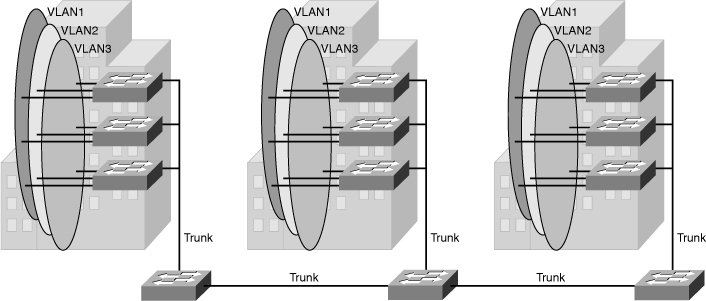
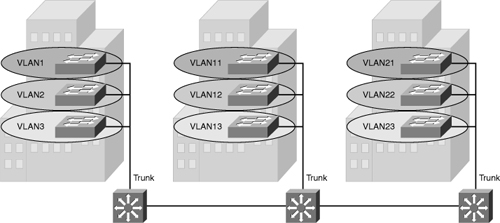
![]() The term end-to-end VLAN refers to a single VLAN that is associated with switch ports widely dispersed throughout an enterprise network on multiple switches. A Layer 2 switched campus network carries traffic for this VLAN throughout the network, as shown in Figure 2-2 where VLANs 1, 2 and 3 are spread across all three switches.
The term end-to-end VLAN refers to a single VLAN that is associated with switch ports widely dispersed throughout an enterprise network on multiple switches. A Layer 2 switched campus network carries traffic for this VLAN throughout the network, as shown in Figure 2-2 where VLANs 1, 2 and 3 are spread across all three switches.
![]() If more than one VLAN in a network is operating in the end-to-end mode, special links (Layer 2 trunks) are required between switches to carry the traffic of all the different VLANs.
If more than one VLAN in a network is operating in the end-to-end mode, special links (Layer 2 trunks) are required between switches to carry the traffic of all the different VLANs.
![]() An end-to-end VLAN model has the following characteristics:
An end-to-end VLAN model has the following characteristics:
-
 Each VLAN is dispersed geographically throughout the network.
Each VLAN is dispersed geographically throughout the network. -
 Users are grouped into each VLAN regardless of the physical location.
Users are grouped into each VLAN regardless of the physical location. -
 As a user moves throughout a campus, the VLAN membership of that user remains the same, regardless of the physical switch to which this user attaches.
As a user moves throughout a campus, the VLAN membership of that user remains the same, regardless of the physical switch to which this user attaches. -
 Users are typically associated with a given VLAN for network management reasons. This is why they are kept in the same VLAN, therefore the same group, as they move through the campus.
Users are typically associated with a given VLAN for network management reasons. This is why they are kept in the same VLAN, therefore the same group, as they move through the campus. -
 All devices on a given VLAN typically have addresses on the same IP subnet.
All devices on a given VLAN typically have addresses on the same IP subnet.
Local VLAN
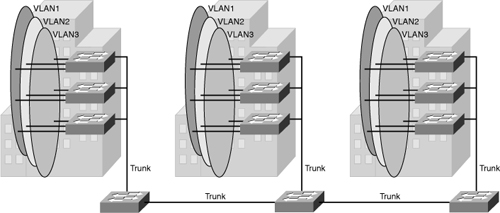
![]() The Campus Enterprise Architecture is based on the local VLAN model. In a local VLAN model, all users of a set of geographically common switches are grouped into a single VLAN, regardless of the organizational function of those users. Local VLANs are generally confined to a wiring closet, as shown in Figure 2-3, that VLANs are local to one access switch and trunking to the distribution switch. If users move from one location to another in the campus, their connection changes to the new VLAN at the new physical location.
The Campus Enterprise Architecture is based on the local VLAN model. In a local VLAN model, all users of a set of geographically common switches are grouped into a single VLAN, regardless of the organizational function of those users. Local VLANs are generally confined to a wiring closet, as shown in Figure 2-3, that VLANs are local to one access switch and trunking to the distribution switch. If users move from one location to another in the campus, their connection changes to the new VLAN at the new physical location.
![]() In the local VLAN model, Layer 2 switching is implemented at the access level and routing is implemented at the distribution and core level, as shown in Figure 2-3, to enable users to maintain access to the resources they need.
In the local VLAN model, Layer 2 switching is implemented at the access level and routing is implemented at the distribution and core level, as shown in Figure 2-3, to enable users to maintain access to the resources they need.
![]() The following are some local VLAN characteristics and user guidelines:
The following are some local VLAN characteristics and user guidelines:
-
 The network administrator should create local VLANs with physical boundaries in mind rather than the job functions of the users on the end devices.
The network administrator should create local VLANs with physical boundaries in mind rather than the job functions of the users on the end devices. -
 Generally, local VLANs exist between the access and distribution levels.
Generally, local VLANs exist between the access and distribution levels. -
 Traffic from a local VLAN is routed at the distribution and core levels to reach destinations on other networks.
Traffic from a local VLAN is routed at the distribution and core levels to reach destinations on other networks. -
 Configure the VTP mode in transparent mode because VLANs on a given access switch should not be advertised to all other switches in the network, nor do they need to be manually created in any other switch’s VLAN database.
Configure the VTP mode in transparent mode because VLANs on a given access switch should not be advertised to all other switches in the network, nor do they need to be manually created in any other switch’s VLAN database. -
 A network that consists entirely of local VLANs can benefit from increased convergence times offered via routing protocols, instead of a spanning tree for Layer 2 networks. It is usually recommended to have one to three VLANs per access layer switches.
A network that consists entirely of local VLANs can benefit from increased convergence times offered via routing protocols, instead of a spanning tree for Layer 2 networks. It is usually recommended to have one to three VLANs per access layer switches.
Comparison of End-to-End VLANs and Local VLANs
![]() This subsection describes the benefits and drawbacks of local VLANs versus end-to-end VLANs.
This subsection describes the benefits and drawbacks of local VLANs versus end-to-end VLANs.
![]() Because a VLAN usually represents a Layer 3 segment, each end-to-end VLAN enables a single Layer 3 segment to be dispersed geographically throughout the network. The following could be some of the reasons for implementing the end-to-end design:
Because a VLAN usually represents a Layer 3 segment, each end-to-end VLAN enables a single Layer 3 segment to be dispersed geographically throughout the network. The following could be some of the reasons for implementing the end-to-end design:
-
 Grouping users: Users can be grouped on a common IP segment, even though they are geographically dispersed. Recently the trend has been moving toward virtualization. Solutions such as VMWARE need end-to-end VLANs to be spread across segments of the campus.
Grouping users: Users can be grouped on a common IP segment, even though they are geographically dispersed. Recently the trend has been moving toward virtualization. Solutions such as VMWARE need end-to-end VLANs to be spread across segments of the campus. -
 Security: A VLAN can contain resources that should not be accessible to all users on the network, or there might be a reason to confine certain traffic to a particular VLAN.
Security: A VLAN can contain resources that should not be accessible to all users on the network, or there might be a reason to confine certain traffic to a particular VLAN. -
 Applying quality of service (QoS): Traffic can be a higher or lower access priority to network resources from a given VLAN.
Applying quality of service (QoS): Traffic can be a higher or lower access priority to network resources from a given VLAN. -
 Routing avoidance: If much of the VLAN user traffic is destined for devices on that same VLAN, and routing to those devices is not desirable, users can access resources on their VLAN without their traffic being routed off the VLAN, even though the traffic might traverse multiple switches.
Routing avoidance: If much of the VLAN user traffic is destined for devices on that same VLAN, and routing to those devices is not desirable, users can access resources on their VLAN without their traffic being routed off the VLAN, even though the traffic might traverse multiple switches. -
 Special purpose VLAN: Sometimes a VLAN is provisioned to carry a single type of traffic that must be dispersed throughout the campus (for example, multicast, voice, or visitor VLANs).
Special purpose VLAN: Sometimes a VLAN is provisioned to carry a single type of traffic that must be dispersed throughout the campus (for example, multicast, voice, or visitor VLANs). -
 Poor design: For no clear purpose, users are placed in VLANs that span the campus or even span WANs. Sometimes when a network is already configured and running, organizations are hesitant to improve the design because of downtime or other political reasons.
Poor design: For no clear purpose, users are placed in VLANs that span the campus or even span WANs. Sometimes when a network is already configured and running, organizations are hesitant to improve the design because of downtime or other political reasons.
![]() Following are some items that the network admin should consider when implementing end-to-end VLANs:
Following are some items that the network admin should consider when implementing end-to-end VLANs:
-
 Switch ports are provisioned for each user and associated with a given VLAN. Because users on an end-to-end VLAN can be anywhere in the network, all switches must be aware of that VLAN. This means that all switches carrying traffic for end-to-end VLANs are required to have those specific VLANs defined in each switch’s VLAN database.
Switch ports are provisioned for each user and associated with a given VLAN. Because users on an end-to-end VLAN can be anywhere in the network, all switches must be aware of that VLAN. This means that all switches carrying traffic for end-to-end VLANs are required to have those specific VLANs defined in each switch’s VLAN database. -
 Also, flooded traffic for the VLAN is, by default, passed to every switch even if it does not currently have any active ports in the particular end-to-end VLAN.
Also, flooded traffic for the VLAN is, by default, passed to every switch even if it does not currently have any active ports in the particular end-to-end VLAN. -
 Finally, troubleshooting devices on a campus with end-to-end VLANs can be challenging because the traffic for a single VLAN can traverse multiple switches in a large area of the campus, and that can easily cause potential spanning-tree problems.
Finally, troubleshooting devices on a campus with end-to-end VLANs can be challenging because the traffic for a single VLAN can traverse multiple switches in a large area of the campus, and that can easily cause potential spanning-tree problems.
Mapping VLANs to a Hierarchical Network
![]() In the past, network designers have attempted to implement the 80/20 rule when designing networks. The rule was based on the observation that, in general, 80 percent of the traffic on a network segment was passed between local devices, and only 20 percent of the traffic was destined for remote network segments. Therefore, network architecture used to prefer end-to-end VLANs. To avoid the complications of end-to-end VLANs, designers now consolidate servers in central locations on the network and provide access to external resources, such as the Internet, through one or two paths on the network because the bulk of traffic now traverses a number of segments. Therefore, the paradigm now is closer to a 20/80 proportion, in which the greater flow of traffic leaves the local segment, so local VLANs have become more efficient.
In the past, network designers have attempted to implement the 80/20 rule when designing networks. The rule was based on the observation that, in general, 80 percent of the traffic on a network segment was passed between local devices, and only 20 percent of the traffic was destined for remote network segments. Therefore, network architecture used to prefer end-to-end VLANs. To avoid the complications of end-to-end VLANs, designers now consolidate servers in central locations on the network and provide access to external resources, such as the Internet, through one or two paths on the network because the bulk of traffic now traverses a number of segments. Therefore, the paradigm now is closer to a 20/80 proportion, in which the greater flow of traffic leaves the local segment, so local VLANs have become more efficient.
![]() In addition, the concept of end-to-end VLANs was attractive when IP address configuration was a manually administered and burdensome process; therefore, anything that reduced this burden as users moved between networks was an improvement. However, given the ubiquity of DHCP, the process of configuring an IP address at each desktop is no longer a significant issue. As a result, there are few benefits to extending a VLAN throughout an enterprise; for example, if there are some clustering and other requirements.
In addition, the concept of end-to-end VLANs was attractive when IP address configuration was a manually administered and burdensome process; therefore, anything that reduced this burden as users moved between networks was an improvement. However, given the ubiquity of DHCP, the process of configuring an IP address at each desktop is no longer a significant issue. As a result, there are few benefits to extending a VLAN throughout an enterprise; for example, if there are some clustering and other requirements.
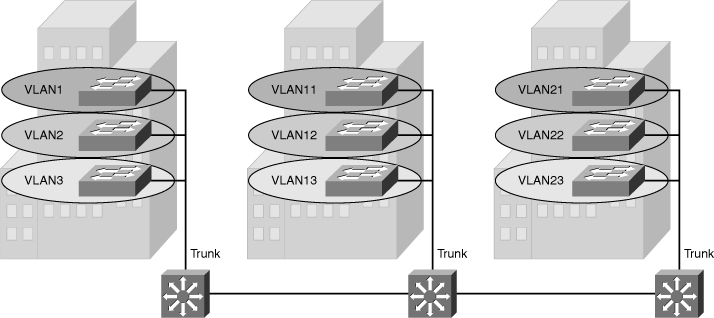
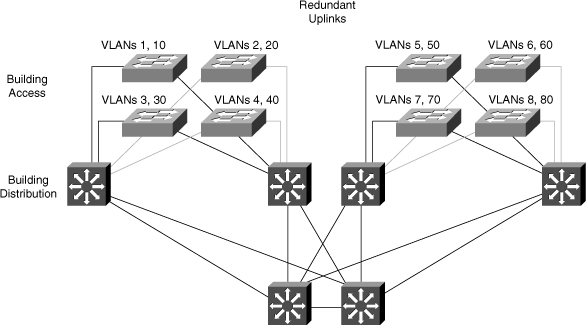
![]() Local VLANs are part of the enterprise campus architecture design, as shown in Figure 2-4, in which VLANs used at the access layer should extend no further than their associated distribution switch. For example VLANs 1, 10 and VLANs 2, 20 are confined to only a local access switch. Traffic is routed from the local VLAN as it is passed from the distribution layer into the core. It is usually recommended to have two to three VLANs per access block rather than span all the VLANs across all access blocks. This design can mitigate Layer 2 troubleshooting issues that occur when a single VLAN traverses the switches throughout a campus network. In addition, because STP is configured for redundancy, the switch limits the STP to only the access and distribution switches that help to reduce the network complexity in times of failure.
Local VLANs are part of the enterprise campus architecture design, as shown in Figure 2-4, in which VLANs used at the access layer should extend no further than their associated distribution switch. For example VLANs 1, 10 and VLANs 2, 20 are confined to only a local access switch. Traffic is routed from the local VLAN as it is passed from the distribution layer into the core. It is usually recommended to have two to three VLANs per access block rather than span all the VLANs across all access blocks. This design can mitigate Layer 2 troubleshooting issues that occur when a single VLAN traverses the switches throughout a campus network. In addition, because STP is configured for redundancy, the switch limits the STP to only the access and distribution switches that help to reduce the network complexity in times of failure.
![]() Implementing the enterprise campus architecture design using local VLANs provides the following benefits:
Implementing the enterprise campus architecture design using local VLANs provides the following benefits:
-
 Deterministic traffic flow: The simple layout provides a predictable Layer 2 and Layer 3 traffic path. If a failure occurs that was not mitigated by the redundancy features, the simplicity of the model facilitates expedient problem isolation and resolution within the switch block.
Deterministic traffic flow: The simple layout provides a predictable Layer 2 and Layer 3 traffic path. If a failure occurs that was not mitigated by the redundancy features, the simplicity of the model facilitates expedient problem isolation and resolution within the switch block. -
 Active redundant paths: When implementing Per VLAN Spanning Tree (PVST) or Multiple Spanning Tree Protocol (MSTP) because there is no loop, all links can be used to make use of the redundant paths.
Active redundant paths: When implementing Per VLAN Spanning Tree (PVST) or Multiple Spanning Tree Protocol (MSTP) because there is no loop, all links can be used to make use of the redundant paths. -
 High availability: Redundant paths exist at all infrastructure levels. Local VLAN traffic on access switches can be passed to the building distribution switches across an alternative Layer 2 path if a primary path failure occurs. Router redundancy protocols can provide failover if the default gateway for the access VLAN fails. When both the Spanning Tree Protocol (STP) instance and VLAN are confined to a specific access and distribution block, Layer 2 and Layer 3 redundancy measures and protocols can be configured to failover in a coordinated manner.
High availability: Redundant paths exist at all infrastructure levels. Local VLAN traffic on access switches can be passed to the building distribution switches across an alternative Layer 2 path if a primary path failure occurs. Router redundancy protocols can provide failover if the default gateway for the access VLAN fails. When both the Spanning Tree Protocol (STP) instance and VLAN are confined to a specific access and distribution block, Layer 2 and Layer 3 redundancy measures and protocols can be configured to failover in a coordinated manner. -
 Finite failure domain: If VLANs are local to a switch block, and the number of devices on each VLAN is kept small, failures at Layer 2 are confined to a small subset of users.
Finite failure domain: If VLANs are local to a switch block, and the number of devices on each VLAN is kept small, failures at Layer 2 are confined to a small subset of users. -
 Scalable design: Following the enterprise campus architecture design, new access switches can be easily incorporated, and new submodules can be added when necessary.
Scalable design: Following the enterprise campus architecture design, new access switches can be easily incorporated, and new submodules can be added when necessary.
 Planning VLAN Implementation
Planning VLAN Implementation
![]() The type of VLAN module used in the network affects how the implementation and verification plan is developed and executed. In this section, we focus only on implementing the Layer 2 end-to-end VLAN model. In later sections, we focus on the local VLAN model used by the campus enterprise architecture.
The type of VLAN module used in the network affects how the implementation and verification plan is developed and executed. In this section, we focus only on implementing the Layer 2 end-to-end VLAN model. In later sections, we focus on the local VLAN model used by the campus enterprise architecture.
![]() This section describes the steps necessary to create a plan for the implementation of VLANs in a campus environment. In general, planning end-to-end VLAN implementation involves the following tasks:
This section describes the steps necessary to create a plan for the implementation of VLANs in a campus environment. In general, planning end-to-end VLAN implementation involves the following tasks:
 Best Practices for VLAN Design
Best Practices for VLAN Design
![]() Usually, network designers design and implement the VLANs and their components depending on the business needs and requirements, but this section provides general best practices for implementing VLAN in a campus network.
Usually, network designers design and implement the VLANs and their components depending on the business needs and requirements, but this section provides general best practices for implementing VLAN in a campus network.
![]() Following are some of the practices for VLAN design:
Following are some of the practices for VLAN design:
-
 For the Local VLANs model, it is usually recommended to have only one to three VLANs per access module and, as discussed, limit those VLANs to a couple of access switches and the distribution switches.
For the Local VLANs model, it is usually recommended to have only one to three VLANs per access module and, as discussed, limit those VLANs to a couple of access switches and the distribution switches. -
 Avoid using VLAN 1 as the “blackhole” for all unused ports. Use any other VLAN except 1 to assign all the unused ports to it.
Avoid using VLAN 1 as the “blackhole” for all unused ports. Use any other VLAN except 1 to assign all the unused ports to it. -
 Try to always have separate voice VLANs, data VLANs, management VLANs, native VLANs, blackhole VLANs, and default VLANs (VLAN 1).
Try to always have separate voice VLANs, data VLANs, management VLANs, native VLANs, blackhole VLANs, and default VLANs (VLAN 1). -
 In the local VLANs model, avoid VTP; it is feasible to use manually allowed VLANs in a network on trunks.
In the local VLANs model, avoid VTP; it is feasible to use manually allowed VLANs in a network on trunks. -
 For trunk ports, turn off DTP and configure it manually. Use IEEE 802.1Q rather than ISL because it has better support for QoS and is a standard protocol.
For trunk ports, turn off DTP and configure it manually. Use IEEE 802.1Q rather than ISL because it has better support for QoS and is a standard protocol. -
 Manually configure access ports that are not specifically intended for a trunk link.
Manually configure access ports that are not specifically intended for a trunk link. -
 Prevent all data traffic from VLAN 1; only permit control protocols to run on VLAN 1 (DTP, VTP, STP BPDUs, PAgP, LACP, CDP, and such.).
Prevent all data traffic from VLAN 1; only permit control protocols to run on VLAN 1 (DTP, VTP, STP BPDUs, PAgP, LACP, CDP, and such.). -
 Avoid using Telnet because of security risks; enable SSH support on management VLANs.
Avoid using Telnet because of security risks; enable SSH support on management VLANs.
 Configuring VLANs
Configuring VLANs
![]() All Cisco Catalyst switches support VLANs. That said, each Cisco Catalyst switch supports a different number of VLANs, with high-end Cisco Catalyst switches supporting as many as 4096 VLANs. Table 2-1 notes the maximum number of VLANs supported by each model of Catalyst switch.
All Cisco Catalyst switches support VLANs. That said, each Cisco Catalyst switch supports a different number of VLANs, with high-end Cisco Catalyst switches supporting as many as 4096 VLANs. Table 2-1 notes the maximum number of VLANs supported by each model of Catalyst switch.
|
|
|
|
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
VLAN Ranges
![]() Cisco Catalyst switches support up to 4096 VLANs depending on the platform and software version. Table 2-2 illustrates the VLAN division for Cisco Catalyst switches.
Cisco Catalyst switches support up to 4096 VLANs depending on the platform and software version. Table 2-2 illustrates the VLAN division for Cisco Catalyst switches.
|
|
|
|
|
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|
![]() To create a new VLAN in global configuration mode, follow these steps:
To create a new VLAN in global configuration mode, follow these steps:
|
|
|
|
|
|
|
|
|
![]() Example 2-1 shows how to configure a VLAN in global configuration mode.
Example 2-1 shows how to configure a VLAN in global configuration mode.
Switch# configure terminal
Switch(config)# vlan 5
Switch(config-vlan)# name Engineering
Switch(config-vlan)# exit
![]() To delete a VLAN in global configuration mode, follow these steps:
To delete a VLAN in global configuration mode, follow these steps:
|
|
|
|
|
|
| Note |
|
![]() Example 2-2 shows deletion of a VLAN in global configuration mode.
Example 2-2 shows deletion of a VLAN in global configuration mode.
Switch# configure terminal
Switch(config)# no vlan 3
Switch(config)# end
![]() To assign a switch port to a previously created VLAN, follow these steps:
To assign a switch port to a previously created VLAN, follow these steps:
|
|
| |||
|
|
| |||
|
|
|
![]() Example 2-3 illustrates configuration of an interface as an access port in VLAN 200.
Example 2-3 illustrates configuration of an interface as an access port in VLAN 200.
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface FastEthernet 5/6
Switch(config-if)# description PC A
Switch(config-if)# switchport
Switch(config-if)# switchport host
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 200
Switch(configif)# no shutdown
Switch(config-if)# end
| Note |
|
 Verifying the VLAN Configuration
Verifying the VLAN Configuration
![]() As previously discussed, after you configure the VLANs, one of the important step of PPDIOO is to able to verify the configuration. To verify the VLAN configuration of a Catalyst switch, use show commands. The show vlan command from privileged EXEC mode displays information about a particular VLAN. Table 2-3 documents the fields displayed by the show vlan command.
As previously discussed, after you configure the VLANs, one of the important step of PPDIOO is to able to verify the configuration. To verify the VLAN configuration of a Catalyst switch, use show commands. The show vlan command from privileged EXEC mode displays information about a particular VLAN. Table 2-3 documents the fields displayed by the show vlan command.
|
| |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|
![]() Example 2-4 displays information about a VLAN identified by number in Cisco IOS.
Example 2-4 displays information about a VLAN identified by number in Cisco IOS.
Switch# show vlan id 3
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
3 VLAN0003 active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
3 enet 100003 1500 - - - - - 0 0
------- --------- ----------------- -------------------------------------------
![]() Example 2-5 displays information about a VLAN identified by name in Cisco IOS.
Example 2-5 displays information about a VLAN identified by name in Cisco IOS.
Switch# show vlan name VLAN0003
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------
3 VLAN0003 active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- ------ ------
3 enet 100003 1500 - - - - 0 0
![]() To display the current configuration of a particular interface, use the show running-config interface interface_type slot/port command. To display detailed information about a specific switch port, use the show interfaces command. The command show interface interface_type slot/port with the switchport keyword displays not only a switch port’s characteristics but also private VLAN and trunking information. The show-mac address-table interface interface_type slot/port command displays the MAC address table information for the specified interface in specific VLANs. During troubleshooting, this command is helpful in determining whether the attached devices are sending packets to the correct VLAN.
To display the current configuration of a particular interface, use the show running-config interface interface_type slot/port command. To display detailed information about a specific switch port, use the show interfaces command. The command show interface interface_type slot/port with the switchport keyword displays not only a switch port’s characteristics but also private VLAN and trunking information. The show-mac address-table interface interface_type slot/port command displays the MAC address table information for the specified interface in specific VLANs. During troubleshooting, this command is helpful in determining whether the attached devices are sending packets to the correct VLAN.
![]() Example 2-6 displays the configuration of a particular interface. Example 2-6 shows that the interface Ethernet 5/6 is configured with the VLAN 200 and in an access mode so that the port doesn’t negotiate for trunking.
Example 2-6 displays the configuration of a particular interface. Example 2-6 shows that the interface Ethernet 5/6 is configured with the VLAN 200 and in an access mode so that the port doesn’t negotiate for trunking.
Switch# show running-config interface FastEthernet 5/6
Building configuration...
!
Current configuration :33 bytes
interface FastEthernet 5/6
switchport access vlan 200
switchport mode access
switchport host
end
![]() Example 2-7 displays detailed switch port information as the port VLAN and operation modes. As shown in Example 2-7, the fastethernet port 4/1 is configured as the switchport port means Layer 2 port, working as an access port in VLAN 2.
Example 2-7 displays detailed switch port information as the port VLAN and operation modes. As shown in Example 2-7, the fastethernet port 4/1 is configured as the switchport port means Layer 2 port, working as an access port in VLAN 2.
BXB-6500-10:8A# show interfaces FastEthernet 4/1 switchport
Name: Fa4/1
Switchport: Enabled
Administrative Mode: static access
Operational Mode: static access
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 2 (VLAN0002)
Trunking Native Mode VLAN: 1 (default)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Voice VLAN: none (Inactive)
Appliance trust: none
![]() Example 2-8 displays the MAC address table information for a specific interface in VLAN 1.
Example 2-8 displays the MAC address table information for a specific interface in VLAN 1.
Switch# show mac-address-table interface GigabitEthernet 0/1 vlan 1
Mac Address Table
------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- -----
1 0008.2199.2bc1 DYNAMIC Gi0/1
Total Mac Addresses for this criterion: 1
 Troubleshooting VLANs
Troubleshooting VLANs
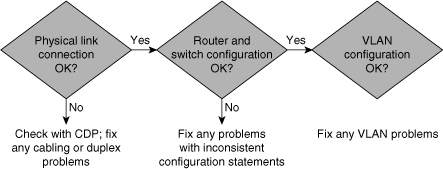
![]() When troubleshooting problems related to VLANs, always review the following items:
When troubleshooting problems related to VLANs, always review the following items:
-
 Physical connections
Physical connections -
 Switch configuration
Switch configuration -
 VLAN configuration
VLAN configuration
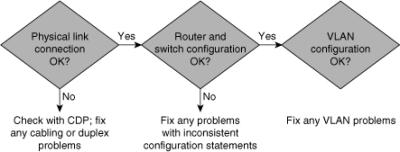
![]() Figure 2-5 shows, at a high level, VLAN problems that can occur on a switch.
Figure 2-5 shows, at a high level, VLAN problems that can occur on a switch.
![]() The following sections cover several common VLAN issues and the action plan to troubleshoot these issues.
The following sections cover several common VLAN issues and the action plan to troubleshoot these issues.
Troubleshooting Slow Throughput
![]() To troubleshoot slow-throughput issues within the same VLAN, perform the following steps:
To troubleshoot slow-throughput issues within the same VLAN, perform the following steps:
|
|
|
|
|
|
|
|
|
![]() If you see from the output of the show interface command that the number of collisions is increasing rapidly, the problem might be an oversubscribed half-duplex link, faulty hardware, a bad cable, or a duplex mismatch.
If you see from the output of the show interface command that the number of collisions is increasing rapidly, the problem might be an oversubscribed half-duplex link, faulty hardware, a bad cable, or a duplex mismatch.
Troubleshooting Communication Issues
![]() When one device cannot communicate with another device within a VLAN, troubleshoot the problem by doing the following:
When one device cannot communicate with another device within a VLAN, troubleshoot the problem by doing the following:
-
 Ensure that the VLAN membership of the switch ports is correct by using the show interface, show mac, and show running commands, as discussed in the previous “Verifying VLAN” section.
Ensure that the VLAN membership of the switch ports is correct by using the show interface, show mac, and show running commands, as discussed in the previous “Verifying VLAN” section. -
 Make sure the switch ports are up and connected using the show interface command. Try to reset the port by using the shut and no shut commands under the switch interface.
Make sure the switch ports are up and connected using the show interface command. Try to reset the port by using the shut and no shut commands under the switch interface.


1 comments
Thank you for great post really it help us , please visit once at http://www.qosnetworking.com/
Post a Comment