The Principles of Defense in Depth
![]() This section describes the concept of defense in depth.
This section describes the concept of defense in depth.
![]() It is often said that the security of a system is only as strong as its weakest link, which is universally understood by almost everyone, but is rarely addressed by security designers. The complexity of modern systems makes it difficult to identify all weak links, let alone identify the weakest one. Sometimes, it is desirable to eliminate a weak link or to augment its security.
It is often said that the security of a system is only as strong as its weakest link, which is universally understood by almost everyone, but is rarely addressed by security designers. The complexity of modern systems makes it difficult to identify all weak links, let alone identify the weakest one. Sometimes, it is desirable to eliminate a weak link or to augment its security.
![]() Securing information and systems against all threats requires multiple, overlapping protection approaches that address the people, technology, and operational aspects of information technology. Using multiple, overlapping protection approaches ensures that the system is never unprotected from the failure or circumvention of any individual protection approach.
Securing information and systems against all threats requires multiple, overlapping protection approaches that address the people, technology, and operational aspects of information technology. Using multiple, overlapping protection approaches ensures that the system is never unprotected from the failure or circumvention of any individual protection approach.
![]() When a system is designed and implemented, its quality should always be questioned through design reviews and testing. Identification of various failure modes might help a designer evaluate the probability of element failure, and identify the links that are the most critical for the security of the whole system. Many systems have a security-based single point of failure, an element of functionality or protection, which, if compromised, would cause the compromise of the whole system. It is desirable to eliminate or at least harden such single points of failure in a high-assurance system.
When a system is designed and implemented, its quality should always be questioned through design reviews and testing. Identification of various failure modes might help a designer evaluate the probability of element failure, and identify the links that are the most critical for the security of the whole system. Many systems have a security-based single point of failure, an element of functionality or protection, which, if compromised, would cause the compromise of the whole system. It is desirable to eliminate or at least harden such single points of failure in a high-assurance system.
![]() Defense in depth is a philosophy that provides layered security to a system by using multiple security mechanisms:
Defense in depth is a philosophy that provides layered security to a system by using multiple security mechanisms:
-
 Security mechanisms should back each other up and provide diversity and redundancy of protection.
Security mechanisms should back each other up and provide diversity and redundancy of protection. -
 Security mechanisms should not depend on each other, so that their security does not depend on other factors outside their control.
Security mechanisms should not depend on each other, so that their security does not depend on other factors outside their control. -
 Using defense in depth, you can eliminate single points of failure and augment weak links in the system to provide stronger protection with multiple layers.
Using defense in depth, you can eliminate single points of failure and augment weak links in the system to provide stronger protection with multiple layers.
![]() The defense-in-depth strategy recommends several principles:
The defense-in-depth strategy recommends several principles:
-
 Defend in multiple places: Given that insiders or outsiders can attack a target from multiple points, an organization must deploy protection mechanisms at multiple locations to resist all classes of attacks. At a minimum, you should include three defensive focus areas:
Defend in multiple places: Given that insiders or outsiders can attack a target from multiple points, an organization must deploy protection mechanisms at multiple locations to resist all classes of attacks. At a minimum, you should include three defensive focus areas:-
 Defend the networks and infrastructure: Protect the local- and wide-area communications networks from attacks, such as DoS attacks. Provide confidentiality and integrity protection for data that is transmitted over the networks; for example, use encryption and traffic flow security measures to resist passive monitoring.
Defend the networks and infrastructure: Protect the local- and wide-area communications networks from attacks, such as DoS attacks. Provide confidentiality and integrity protection for data that is transmitted over the networks; for example, use encryption and traffic flow security measures to resist passive monitoring. -
 Defend the enclave boundaries: Deploy firewalls and intrusion detection systems (IDS) or intrusion prevention systems (IPS) or both to resist active network attacks.
Defend the enclave boundaries: Deploy firewalls and intrusion detection systems (IDS) or intrusion prevention systems (IPS) or both to resist active network attacks. -
 Defend the computing environment: Provide access controls and host intrusion prevention systems (HIPS) on hosts and servers to resist insider, close-in, and distribution attacks.
Defend the computing environment: Provide access controls and host intrusion prevention systems (HIPS) on hosts and servers to resist insider, close-in, and distribution attacks.
-
-
 Build layered defenses: Even the best available information assurance products have inherent weaknesses. Therefore, it is only a matter of time before an adversary finds an exploitable vulnerability. An effective countermeasure is to deploy multiple defense mechanisms between the adversary and the target. Each of these mechanisms must present unique obstacles to the adversary. Further, each mechanism should include both protection and detection measures. These measures increase the risk of detection for adversaries while reducing their chances of success or makes successful penetrations unaffordable. One example of a layered defense is to have nested firewalls (each coupled with IDS or IPS) that are deployed at outer and inner network boundaries. The inner firewalls may support more granular access control and data filtering.
Build layered defenses: Even the best available information assurance products have inherent weaknesses. Therefore, it is only a matter of time before an adversary finds an exploitable vulnerability. An effective countermeasure is to deploy multiple defense mechanisms between the adversary and the target. Each of these mechanisms must present unique obstacles to the adversary. Further, each mechanism should include both protection and detection measures. These measures increase the risk of detection for adversaries while reducing their chances of success or makes successful penetrations unaffordable. One example of a layered defense is to have nested firewalls (each coupled with IDS or IPS) that are deployed at outer and inner network boundaries. The inner firewalls may support more granular access control and data filtering. -
 Use robust components: Specify the security robustness (that is, strength and assurance) of each information assurance component as a function of the value of what it is protecting and the threat at the point of application. For example, it is often more effective and operationally suitable to deploy stronger mechanisms at the network boundaries than at the user desktop.
Use robust components: Specify the security robustness (that is, strength and assurance) of each information assurance component as a function of the value of what it is protecting and the threat at the point of application. For example, it is often more effective and operationally suitable to deploy stronger mechanisms at the network boundaries than at the user desktop. -
 Employ robust key management: Deploy robust encryption key management and public key infrastructures that support all the incorporated information assurance technologies and that are highly resistant to attack.
Employ robust key management: Deploy robust encryption key management and public key infrastructures that support all the incorporated information assurance technologies and that are highly resistant to attack. -
 Deploy IDS or IPS: Deploy infrastructures to detect and prevent intrusions and to analyze and correlate the results and react accordingly. These infrastructures should help the operations staff answer the following questions:
Deploy IDS or IPS: Deploy infrastructures to detect and prevent intrusions and to analyze and correlate the results and react accordingly. These infrastructures should help the operations staff answer the following questions: Am I under attack?
Am I under attack? Who is the source?
Who is the source? What is the target?
What is the target? Who else is under attack?
Who else is under attack? What are my options?
What are my options?
![]() To achieve high assurance in authentication, many trusted systems require “two-factor authentication”; they require a subject to include at least two types of proofs of identity, such as something they know and something they have. An example of two-factor authentication is an access control system that requires a smart card (something the user has) and a password (something the user knows). With two-factor authentication, a compromise of one factor does not lead to a compromise of the system. A password might become known, but it is useless without the smart card. Conversely, if the smart card is stolen, it cannot be used without the password.
To achieve high assurance in authentication, many trusted systems require “two-factor authentication”; they require a subject to include at least two types of proofs of identity, such as something they know and something they have. An example of two-factor authentication is an access control system that requires a smart card (something the user has) and a password (something the user knows). With two-factor authentication, a compromise of one factor does not lead to a compromise of the system. A password might become known, but it is useless without the smart card. Conversely, if the smart card is stolen, it cannot be used without the password.
![]() Credit card processing centers use monitoring of usage patterns and spending limits to control possible damage. A stolen credit card is therefore subject to two layers of protection: Abnormal usage signatures are detected, and the thief cannot spend more than a predetermined amount of money with a stolen card.
Credit card processing centers use monitoring of usage patterns and spending limits to control possible damage. A stolen credit card is therefore subject to two layers of protection: Abnormal usage signatures are detected, and the thief cannot spend more than a predetermined amount of money with a stolen card.
![]() You can configure the Cisco Adaptive Security Appliances (ASA) to require two layers of protection:
You can configure the Cisco Adaptive Security Appliances (ASA) to require two layers of protection:
-
 The translation rules, without which no traffic can pass through the firewall
The translation rules, without which no traffic can pass through the firewall -
 The access rules, which specify the traffic that can pass over the firewall to the protected network if translation rules are in place
The access rules, which specify the traffic that can pass over the firewall to the protected network if translation rules are in place
| Note |
|
![]() The defense-in-depth idea goes back to medieval castles, which offered multiple layers of defense to resist lengthy sieges. In addition to multiple layers of walls (perimeters), a medieval castle might use an array of the following protection mechanisms, often complementing each other:
The defense-in-depth idea goes back to medieval castles, which offered multiple layers of defense to resist lengthy sieges. In addition to multiple layers of walls (perimeters), a medieval castle might use an array of the following protection mechanisms, often complementing each other:
-
 The barbican, which is a row of pointed wooden stakes that are placed across the front of the castle
The barbican, which is a row of pointed wooden stakes that are placed across the front of the castle -
 A moat, which is a ditch that is wide and full of water and which surrounds the castle walls
A moat, which is a ditch that is wide and full of water and which surrounds the castle walls -
 A drawbridge, which is a bridge that crosses the moat and can be raised at the first sign of danger
A drawbridge, which is a bridge that crosses the moat and can be raised at the first sign of danger -
 A portcullis, which is an iron grille that covers and protects the raised drawbridge
A portcullis, which is an iron grille that covers and protects the raised drawbridge -
 A narrowed arched passageway to the inside that hinders and contains invaders
A narrowed arched passageway to the inside that hinders and contains invaders -
 The outer courtyard, called the bailey, which is another open area that is within the range of archers
The outer courtyard, called the bailey, which is another open area that is within the range of archers -
 The inside court, which contains more walls and more archers
The inside court, which contains more walls and more archers -
 The inside palace, which is another fortress within the castle and is where the nobles live
The inside palace, which is another fortress within the castle and is where the nobles live -
 The keep, which is the main commanding tower, is the oldest part of the castle and its final defense
The keep, which is the main commanding tower, is the oldest part of the castle and its final defense
![]() Figure 1-6 shows another application of the defense-in-depth principle used in the context of an enterprise firewall, which must convey email from the Internet to the inside messaging system. In this network, email is relayed to an enterprise using two different email relays in series, the public email gateway and the inside email gateway, to avoid any implementation or configuration bugs that might be present in a single email relay. Both email relays are simple pieces of software that would both have to be compromised sequentially before the attacker can exploit the inside email gateway.
Figure 1-6 shows another application of the defense-in-depth principle used in the context of an enterprise firewall, which must convey email from the Internet to the inside messaging system. In this network, email is relayed to an enterprise using two different email relays in series, the public email gateway and the inside email gateway, to avoid any implementation or configuration bugs that might be present in a single email relay. Both email relays are simple pieces of software that would both have to be compromised sequentially before the attacker can exploit the inside email gateway.
![]() Figure 1-6 also illustrates an unfortunate side effect of defense in depth. By adding more layers of security, the complexity of the system increases, possibly reducing other aspects of its security (for example, ease of proper configuration) and reliability (a more complex system is more likely to fail). Careful balancing is needed to provide an optimal solution; each defense-in-depth decision must be analyzed for its side effects. Sometimes to maintain overall simplicity, only the most critical security mechanisms are backed up.
Figure 1-6 also illustrates an unfortunate side effect of defense in depth. By adding more layers of security, the complexity of the system increases, possibly reducing other aspects of its security (for example, ease of proper configuration) and reliability (a more complex system is more likely to fail). Careful balancing is needed to provide an optimal solution; each defense-in-depth decision must be analyzed for its side effects. Sometimes to maintain overall simplicity, only the most critical security mechanisms are backed up.
![]() Figure 1-7 shows a series of Cisco ASAs that were deployed according to the defense-in-depth philosophy. If one Cisco ASA fails, the other Cisco ASA still protects the inside network. However, all Cisco ASAs are configured using the same management tool, such as Cisco Security Manager, which uploads a policy to both firewalls using an abstract definition of access rules.
Figure 1-7 shows a series of Cisco ASAs that were deployed according to the defense-in-depth philosophy. If one Cisco ASA fails, the other Cisco ASA still protects the inside network. However, all Cisco ASAs are configured using the same management tool, such as Cisco Security Manager, which uploads a policy to both firewalls using an abstract definition of access rules.
![]() If there is a defect in the management tool, it might generate faulty rules on all the devices under its control, nullifying the defense-in-depth potential of multiple devices in a series, because they would both pass unauthorized connections.
If there is a defect in the management tool, it might generate faulty rules on all the devices under its control, nullifying the defense-in-depth potential of multiple devices in a series, because they would both pass unauthorized connections.
![]() To counter this vulnerability, you can use two different Cisco Security Manager servers to configure different Cisco ASAs.
To counter this vulnerability, you can use two different Cisco Security Manager servers to configure different Cisco ASAs.
 IP Spoofing Attacks
IP Spoofing Attacks
![]() This section covers how hackers use IP spoofing to launch various types of attacks.
This section covers how hackers use IP spoofing to launch various types of attacks.
![]() The prime goal of an IP spoofing attack is to establish a connection that allows the attacker to gain root access to the host and to create a backdoor entry path into the target system.
The prime goal of an IP spoofing attack is to establish a connection that allows the attacker to gain root access to the host and to create a backdoor entry path into the target system.
![]() IP spoofing is a technique used to gain unauthorized access to computers whereby the intruder sends messages to a computer with an IP address that indicates the message is coming from a trusted host. The attacker learns the IP address of a trusted host and modifies the packet headers so that it appears that the packets are coming from that trusted host.
IP spoofing is a technique used to gain unauthorized access to computers whereby the intruder sends messages to a computer with an IP address that indicates the message is coming from a trusted host. The attacker learns the IP address of a trusted host and modifies the packet headers so that it appears that the packets are coming from that trusted host.
![]() At a high level, the concept of IP spoofing is easy to comprehend. Routers determine the best route between distant computers by examining the destination address, and ignore the source address. In a spoofing attack, an attacker outside your network pretends to be a trusted computer by using a trusted internal or external IP address.
At a high level, the concept of IP spoofing is easy to comprehend. Routers determine the best route between distant computers by examining the destination address, and ignore the source address. In a spoofing attack, an attacker outside your network pretends to be a trusted computer by using a trusted internal or external IP address.
![]() If an attacker manages to change the routing tables to divert network packets to the spoofed IP address, the attacker can receive all the network packets addressed to the spoofed address and reply just as any trusted user can.
If an attacker manages to change the routing tables to divert network packets to the spoofed IP address, the attacker can receive all the network packets addressed to the spoofed address and reply just as any trusted user can.
![]() IP spoofing can also provide access to user accounts and passwords. For example, an attacker can emulate one of your internal users in ways that prove embarrassing for your organization. The attacker could send email messages to business partners that appear to have originated from someone within your organization. Such attacks are easier to perpetrate when an attacker has a user account and password, but they are also possible when attackers combine simple spoofing attacks with their knowledge of messaging protocols.
IP spoofing can also provide access to user accounts and passwords. For example, an attacker can emulate one of your internal users in ways that prove embarrassing for your organization. The attacker could send email messages to business partners that appear to have originated from someone within your organization. Such attacks are easier to perpetrate when an attacker has a user account and password, but they are also possible when attackers combine simple spoofing attacks with their knowledge of messaging protocols.
Technical Discussion on IP Spoofing
![]() Recall that TCP/IP works at Layer 3 and Layer 4 of the Open Systems Interconnection (OSI) model, IP at Layer 3 and TCP at Layer 4. IP is a connectionless model, which means that packet headers do not contain information about that transaction state that is used to route packets on a network. There is no method in place to ensure proper delivery of a packet to the destination.
Recall that TCP/IP works at Layer 3 and Layer 4 of the Open Systems Interconnection (OSI) model, IP at Layer 3 and TCP at Layer 4. IP is a connectionless model, which means that packet headers do not contain information about that transaction state that is used to route packets on a network. There is no method in place to ensure proper delivery of a packet to the destination.
![]() The IP header contains the source and destination IP addresses. Using one of several tools, an attacker can easily modify the source address field. Note that in IP each datagram is independent of all others because of the stateless nature of IP. To engage in IP spoofing, hackers find the IP address of a trusted host and modify their own packet headers to appear as though packets are coming from that trusted host (source address).
The IP header contains the source and destination IP addresses. Using one of several tools, an attacker can easily modify the source address field. Note that in IP each datagram is independent of all others because of the stateless nature of IP. To engage in IP spoofing, hackers find the IP address of a trusted host and modify their own packet headers to appear as though packets are coming from that trusted host (source address).
![]() TCP uses a connection-oriented design. This design means that the participants in a TCP session must first build a connection using the three-way handshake, as shown in Figure 1-8.
TCP uses a connection-oriented design. This design means that the participants in a TCP session must first build a connection using the three-way handshake, as shown in Figure 1-8.
![]() After the connection is established, TCP ensures data reliability by applying the same process to every packet as the two machines update one another on progress. The sequence and acknowledgments take place as follows:
After the connection is established, TCP ensures data reliability by applying the same process to every packet as the two machines update one another on progress. The sequence and acknowledgments take place as follows:
-
 The client selects and transmits an initial sequence number.
The client selects and transmits an initial sequence number. -
 The server acknowledges the initial sequence number and sends its own sequence number.
The server acknowledges the initial sequence number and sends its own sequence number. -
 The client acknowledges the server sequence number, and the connection is open to data transmission.
The client acknowledges the server sequence number, and the connection is open to data transmission.
Sequence Prediction
![]() The basis of IP spoofing lies in an inherent security weakness in TCP known as sequence prediction. Hackers can guess or predict the TCP sequence numbers that are used to construct a TCP packet without receiving any responses from the server. Their prediction allows them to spoof a trusted host on a local network. To mount an IP spoofing attack, the hacker listens to communications between two systems. The hacker sends packets to the target system with the source IP address of the trusted system, as shown in Figure 1-9.
The basis of IP spoofing lies in an inherent security weakness in TCP known as sequence prediction. Hackers can guess or predict the TCP sequence numbers that are used to construct a TCP packet without receiving any responses from the server. Their prediction allows them to spoof a trusted host on a local network. To mount an IP spoofing attack, the hacker listens to communications between two systems. The hacker sends packets to the target system with the source IP address of the trusted system, as shown in Figure 1-9.
![]() If the packets from the hacker have the sequence numbers that the target system is expecting, and if these packets arrive before the packets from the real trusted system, the hacker becomes the trusted host.
If the packets from the hacker have the sequence numbers that the target system is expecting, and if these packets arrive before the packets from the real trusted system, the hacker becomes the trusted host.
![]() To engage in IP spoofing, hackers must first use a variety of techniques to find an IP address of a trusted host and then modify their packet headers to appear as though packets are coming from that trusted host. Further, the attacker can engage other unsuspecting hosts to generate traffic that appears as though it too is coming from the trusted host, thus flooding the network.
To engage in IP spoofing, hackers must first use a variety of techniques to find an IP address of a trusted host and then modify their packet headers to appear as though packets are coming from that trusted host. Further, the attacker can engage other unsuspecting hosts to generate traffic that appears as though it too is coming from the trusted host, thus flooding the network.
![]() IP spoofing attacks fall into one of two categories:
IP spoofing attacks fall into one of two categories:
-
 Nonblind spoofing: This type of attack takes place when the attacker is on the same subnet as the victim. The attacker sniffs the sequence and acknowledgment numbers to eliminate the potential difficulty of calculating them accurately. The biggest threat of spoofing in this instance would be session hijacking. The attacker corrupts the data stream of an established connection, and then reestablishes the data stream with the attack machine using the correct sequence and acknowledgment numbers. Using this technique, an attacker could effectively bypass any authentication measures taken place to build the connection. A nonblind spoofing attack requires the use of a network packet sniffer.
Nonblind spoofing: This type of attack takes place when the attacker is on the same subnet as the victim. The attacker sniffs the sequence and acknowledgment numbers to eliminate the potential difficulty of calculating them accurately. The biggest threat of spoofing in this instance would be session hijacking. The attacker corrupts the data stream of an established connection, and then reestablishes the data stream with the attack machine using the correct sequence and acknowledgment numbers. Using this technique, an attacker could effectively bypass any authentication measures taken place to build the connection. A nonblind spoofing attack requires the use of a network packet sniffer. -
 Blind spoofing: This type of attack is a more sophisticated attack because the sequence and acknowledgment numbers are unreachable. To circumvent this issue, the attacker sends several packets to the target machine to sample sequence numbers. This is a difficult task, but not impossible. Blind attacks rely on routing and transport protocols to compromise the target.
Blind spoofing: This type of attack is a more sophisticated attack because the sequence and acknowledgment numbers are unreachable. To circumvent this issue, the attacker sends several packets to the target machine to sample sequence numbers. This is a difficult task, but not impossible. Blind attacks rely on routing and transport protocols to compromise the target.
![]() Both types of IP spoofing are forms of a common security violation known as a man-in-the-middle attack. In these attacks, a malicious party intercepts a legitimate communication between two friendly parties. The malicious host then controls the flow of communication and can eliminate or alter the information sent by one of the original participants without the knowledge of either the original sender or the recipient. In this way, an attacker can fool a victim into disclosing confidential information by “spoofing” the identity of the original sender, who is presumably trusted by the recipient.
Both types of IP spoofing are forms of a common security violation known as a man-in-the-middle attack. In these attacks, a malicious party intercepts a legitimate communication between two friendly parties. The malicious host then controls the flow of communication and can eliminate or alter the information sent by one of the original participants without the knowledge of either the original sender or the recipient. In this way, an attacker can fool a victim into disclosing confidential information by “spoofing” the identity of the original sender, who is presumably trusted by the recipient.
![]() IP spoofing is also part of most DoS and distributed DoS (DDoS) attacks because the attackers do not want to be easily identified.
IP spoofing is also part of most DoS and distributed DoS (DDoS) attacks because the attackers do not want to be easily identified.
Source Routing
![]() Source routing is the ability of the source to specify within the IP header a full routing path between endpoints. However, the destination must reply along a reverse path back to the source, as shown in Figure 1-10.
Source routing is the ability of the source to specify within the IP header a full routing path between endpoints. However, the destination must reply along a reverse path back to the source, as shown in Figure 1-10.
![]() With this mechanism, the attacker can locally create an interface with a bogus (spoofed) IP address, source connections from it using the source route options, and the target would return the packets along the reverse path to the spoofed address.
With this mechanism, the attacker can locally create an interface with a bogus (spoofed) IP address, source connections from it using the source route options, and the target would return the packets along the reverse path to the spoofed address.
![]() Two types of source routing, as defined in RFC 791, are possible:
Two types of source routing, as defined in RFC 791, are possible:
-
 Loose Source and Route Record (LSRR): The sender specifies a list of IP addresses that the datagram must traverse, but the datagram can also traverse other routers between any two addresses in the list.
Loose Source and Route Record (LSRR): The sender specifies a list of IP addresses that the datagram must traverse, but the datagram can also traverse other routers between any two addresses in the list. -
 Strict Source and Route Record (SSRR): The sender specifies the exact path that the IP datagram must follow.
Strict Source and Route Record (SSRR): The sender specifies the exact path that the IP datagram must follow.
Man-in-the-Middle Attacks
![]() A complex form of IP spoofing is called man-in-the-middle attack, where the hacker monitors the traffic and introduces himself as a stealth intermediary between the sender and the receiver.
A complex form of IP spoofing is called man-in-the-middle attack, where the hacker monitors the traffic and introduces himself as a stealth intermediary between the sender and the receiver.
![]() Hackers use man-in-the-middle attacks to perform many security violations:
Hackers use man-in-the-middle attacks to perform many security violations:
-
 Theft of information
Theft of information -
 Hijacking of an ongoing session to gain access to your internal network resources
Hijacking of an ongoing session to gain access to your internal network resources -
 Analysis of traffic to derive information about your network and its users
Analysis of traffic to derive information about your network and its users -
 DoS
DoS -
 Corruption of transmitted data
Corruption of transmitted data -
 Introduction of new information into network sessions
Introduction of new information into network sessions
| Note |
|
![]() TCP session hijacking is a common variant of the man-in-the-middle attack. The attacker sniffs to identify the client and server IP addresses and relative port numbers. The attacker then modifies his or her packet headers to spoof TCP/IP packets from the client, and then waits to receive an ACK packet from the client communicating with the server. The ACK packet contains the sequence number of the next packet that the client is expecting. The attacker replies to the client using a modified packet with the source address of the server and the destination address of the client. This packet results in a reset that disconnects the legitimate client. The attacker takes over communications with the server by spoofing the expected sequence number from the ACK that was previously sent from the legitimate client to the server.
TCP session hijacking is a common variant of the man-in-the-middle attack. The attacker sniffs to identify the client and server IP addresses and relative port numbers. The attacker then modifies his or her packet headers to spoof TCP/IP packets from the client, and then waits to receive an ACK packet from the client communicating with the server. The ACK packet contains the sequence number of the next packet that the client is expecting. The attacker replies to the client using a modified packet with the source address of the server and the destination address of the client. This packet results in a reset that disconnects the legitimate client. The attacker takes over communications with the server by spoofing the expected sequence number from the ACK that was previously sent from the legitimate client to the server.
| Note |
|
 Confidentiality Attacks
Confidentiality Attacks
![]() Confidentiality breaches can occur when an attacker attempts to obtain access to read-sensitive data. These attacks can be extremely difficult to detect because the attacker can copy sensitive data without the knowledge of the owner and without leaving a trace.
Confidentiality breaches can occur when an attacker attempts to obtain access to read-sensitive data. These attacks can be extremely difficult to detect because the attacker can copy sensitive data without the knowledge of the owner and without leaving a trace.
![]() A confidentiality breach can occur simply because of incorrect file protections. For instance, a sensitive file could mistakenly be given global read-access. Unauthorized copying or examination of the file would probably be difficult to track without having some type of audit mechanism running that logs every file operation. If a user had no reason to suspect unwanted access, however, the audit file would probably never be examined.
A confidentiality breach can occur simply because of incorrect file protections. For instance, a sensitive file could mistakenly be given global read-access. Unauthorized copying or examination of the file would probably be difficult to track without having some type of audit mechanism running that logs every file operation. If a user had no reason to suspect unwanted access, however, the audit file would probably never be examined.
![]() In Figure 1-12, the attacker is able to compromise an exposed web server. Using this server as a beachhead, the attacker then gains full access to the database server from which customer data is downloaded. The attacker then uses the information from the database, such as username, password, and email address, to intercept and read-sensitive email messages destined for a user in the branch office. This attack is difficult to detect because the attacker did not modify or delete any data. The data was only read and downloaded. Without some kind of auditing mechanism on the server, it is unlikely that this attack will be discovered.
In Figure 1-12, the attacker is able to compromise an exposed web server. Using this server as a beachhead, the attacker then gains full access to the database server from which customer data is downloaded. The attacker then uses the information from the database, such as username, password, and email address, to intercept and read-sensitive email messages destined for a user in the branch office. This attack is difficult to detect because the attacker did not modify or delete any data. The data was only read and downloaded. Without some kind of auditing mechanism on the server, it is unlikely that this attack will be discovered.
![]() Attackers can use many methods to compromise confidentiality, the most common of which are as follows:
Attackers can use many methods to compromise confidentiality, the most common of which are as follows:
-
 Packet sniffing: Intercepting and logging traffic that passes over a digital network or part of a network.
Packet sniffing: Intercepting and logging traffic that passes over a digital network or part of a network. -
 Port scanning: Searching a network host for open ports.
Port scanning: Searching a network host for open ports. -
 Dumpster diving: Searching through company dumpsters or trash cans looking for information, such as phone books, organization charts, manuals, memos, charts, and other documentation that can provide a valuable source of information for hackers.
Dumpster diving: Searching through company dumpsters or trash cans looking for information, such as phone books, organization charts, manuals, memos, charts, and other documentation that can provide a valuable source of information for hackers. -
 Emanations capturing: Capturing electrical transmissions from the equipment of an organization to deduce information regarding the organization.
Emanations capturing: Capturing electrical transmissions from the equipment of an organization to deduce information regarding the organization. -
 Wiretapping: Monitoring the telephone or Internet conversations of a third party, often covertly.
Wiretapping: Monitoring the telephone or Internet conversations of a third party, often covertly. -
 Social engineering: Using social skills or relationships to manipulate people inside the network to provide the information needed to access the network.
Social engineering: Using social skills or relationships to manipulate people inside the network to provide the information needed to access the network. -
 Overt channels: Obvious and visible method of communications. Overt channels can be used for covert communication.
Overt channels: Obvious and visible method of communications. Overt channels can be used for covert communication. -
 Covert channels: The ability to hide information within a transmission channel that is based on encoding data using another set of events.
Covert channels: The ability to hide information within a transmission channel that is based on encoding data using another set of events.
| Note |
|
Port Scans and Ping Sweeps
![]() As legitimate tools, port scan and ping sweep applications run a series of tests against hosts and devices to identify vulnerable services that need attention. IP addresses and port or banner data from both TCP and User Datagram Protocol (UDP) ports are examined to gather information.
As legitimate tools, port scan and ping sweep applications run a series of tests against hosts and devices to identify vulnerable services that need attention. IP addresses and port or banner data from both TCP and User Datagram Protocol (UDP) ports are examined to gather information.
![]() In an illegitimate situation, a port scan can be a series of messages sent by someone attempting to break into a computer to learn which computer network services (each service is associated with a well-known port number) the computer provides. Port scanning can be automated to scan a range of TCP or UDP port numbers on a host to detect listening services. Port scanning, a favorite computer hacker approach, provides information to the assailant about where to probe for weaknesses. Essentially, a port scan consists of sending a message to each port, one at a time. The kind of response received indicates whether the port is being used and needs further probing.
In an illegitimate situation, a port scan can be a series of messages sent by someone attempting to break into a computer to learn which computer network services (each service is associated with a well-known port number) the computer provides. Port scanning can be automated to scan a range of TCP or UDP port numbers on a host to detect listening services. Port scanning, a favorite computer hacker approach, provides information to the assailant about where to probe for weaknesses. Essentially, a port scan consists of sending a message to each port, one at a time. The kind of response received indicates whether the port is being used and needs further probing.
![]() The first step to protect against port scanning is to shut all unused ports on what can be a targeted computer, such as a server. Many server operating systems come with multiple ports open to provide a service, such as TCP port 80 for HTTP, or TCP ports 20 and 21 to provide FTP traffic. If the server is not providing FTP service, for example, make sure you disable TCP port 20 and 21.
The first step to protect against port scanning is to shut all unused ports on what can be a targeted computer, such as a server. Many server operating systems come with multiple ports open to provide a service, such as TCP port 80 for HTTP, or TCP ports 20 and 21 to provide FTP traffic. If the server is not providing FTP service, for example, make sure you disable TCP port 20 and 21.
![]() A ping sweep, also known as an Internet Control Message Protocol (ICMP) sweep, is a basic network scanning technique used to determine which IP addresses map to live hosts (computers). A ping sweep consists of ICMP echo requests (pings) sent to multiple hosts, whereas a single ping consists of ICMP echo requests sent to one specific host computer. If a given address is live, that host returns an ICMP echo reply. The goal of the ping sweep is to find hosts available on the network to probe for vulnerabilities. Ping sweeps are among the oldest and slowest methods used to scan a network. Moreover, firewalls limit the capability of an outside ping sweep to penetrate inside the corporate network.
A ping sweep, also known as an Internet Control Message Protocol (ICMP) sweep, is a basic network scanning technique used to determine which IP addresses map to live hosts (computers). A ping sweep consists of ICMP echo requests (pings) sent to multiple hosts, whereas a single ping consists of ICMP echo requests sent to one specific host computer. If a given address is live, that host returns an ICMP echo reply. The goal of the ping sweep is to find hosts available on the network to probe for vulnerabilities. Ping sweeps are among the oldest and slowest methods used to scan a network. Moreover, firewalls limit the capability of an outside ping sweep to penetrate inside the corporate network.
Network Sniffer
![]() In an Ethernet LAN, promiscuous mode is a mode of operation in which a network interface card (NIC) can receive and read every data packet that is transmitted. Promiscuous mode is the opposite of nonpromiscuous mode. When a NIC is operating in promiscuous mode, it passes all the traffic it receives to the CPU. When the NIC is not operating in promiscuous mode, it passes only the traffic whose destination MAC address matches the NIC MAC address to the CPU. Therefore, by operating in promiscuous mode, a NIC can then see more traffic than it would ordinarily be programmed to see.
In an Ethernet LAN, promiscuous mode is a mode of operation in which a network interface card (NIC) can receive and read every data packet that is transmitted. Promiscuous mode is the opposite of nonpromiscuous mode. When a NIC is operating in promiscuous mode, it passes all the traffic it receives to the CPU. When the NIC is not operating in promiscuous mode, it passes only the traffic whose destination MAC address matches the NIC MAC address to the CPU. Therefore, by operating in promiscuous mode, a NIC can then see more traffic than it would ordinarily be programmed to see.
![]() A packet sniffer is a software application that uses a NIC in promiscuous mode to capture all network packets sent across a LAN. Packet sniffers work only in a single collision domain unless a switch is compromised or an attacker launches a Layer 2 attack, such as Address Resolution Protocol (ARP) spoofing or a content-addressable memory (CAM) table overflow. These Layer 2 attacks are discussed in the “Mitigating Layer 2 Attacks” section in Chapter 7, “LAN, SAN, Voice, and Endpoint Security Overview.”
A packet sniffer is a software application that uses a NIC in promiscuous mode to capture all network packets sent across a LAN. Packet sniffers work only in a single collision domain unless a switch is compromised or an attacker launches a Layer 2 attack, such as Address Resolution Protocol (ARP) spoofing or a content-addressable memory (CAM) table overflow. These Layer 2 attacks are discussed in the “Mitigating Layer 2 Attacks” section in Chapter 7, “LAN, SAN, Voice, and Endpoint Security Overview.”
![]() Several network applications distribute packets in plaintext. Plaintext is information that is sent across the network without encryption. Sending plaintext in packets can be a problem because if the packets are sniffed an attacker can easily read the contents.
Several network applications distribute packets in plaintext. Plaintext is information that is sent across the network without encryption. Sending plaintext in packets can be a problem because if the packets are sniffed an attacker can easily read the contents.
![]() A network protocol specifies the format and protocol operations. Because the specifications for network protocols, such as TCP/IP, are widely published, a third party can easily interpret the packets and develop a packet sniffer. Numerous freeware and shareware packet sniffers are available that do not require the user to understand anything about the underlying protocols.
A network protocol specifies the format and protocol operations. Because the specifications for network protocols, such as TCP/IP, are widely published, a third party can easily interpret the packets and develop a packet sniffer. Numerous freeware and shareware packet sniffers are available that do not require the user to understand anything about the underlying protocols.
Emanations Capturing
![]() TEMPEST is a U.S. government code word that identifies a classified set of standards for limiting electric or electromagnetic radiation emanations from electronic equipment. Microchips, monitors, printers, and all electronic devices emit electromagnetic radiation (EMI) through the air or through conductors (such as wiring or water pipes). For example, when you use a kitchen appliance while watching television, the static on your TV screen is caused by emanation.
TEMPEST is a U.S. government code word that identifies a classified set of standards for limiting electric or electromagnetic radiation emanations from electronic equipment. Microchips, monitors, printers, and all electronic devices emit electromagnetic radiation (EMI) through the air or through conductors (such as wiring or water pipes). For example, when you use a kitchen appliance while watching television, the static on your TV screen is caused by emanation.
![]() During the 1950s, the U.S. government became concerned that emanations could be captured and then reconstructed. If the emanations were recorded, interpreted, and then played back on a similar device, it would be extremely easy to reveal the content of an encrypted message. Research showed it was possible to capture emanations from a distance, and as a response, the TEMPEST program was started.
During the 1950s, the U.S. government became concerned that emanations could be captured and then reconstructed. If the emanations were recorded, interpreted, and then played back on a similar device, it would be extremely easy to reveal the content of an encrypted message. Research showed it was possible to capture emanations from a distance, and as a response, the TEMPEST program was started.
![]() The purpose of the program was to introduce standards that would reduce the chances of “leakage” from devices that are used to process, transmit, or store sensitive information. Government agencies and contractors use TEMPEST computers and peripherals (printers, scanners, tape drives, mice, and so on) to protect data from the monitoring of emanations. This protection is typically done by shielding the device, or sometimes a room or entire building, with copper or other conductive materials. There are also active measures for “jamming” electromagnetic signals.
The purpose of the program was to introduce standards that would reduce the chances of “leakage” from devices that are used to process, transmit, or store sensitive information. Government agencies and contractors use TEMPEST computers and peripherals (printers, scanners, tape drives, mice, and so on) to protect data from the monitoring of emanations. This protection is typically done by shielding the device, or sometimes a room or entire building, with copper or other conductive materials. There are also active measures for “jamming” electromagnetic signals.
![]() Purchasing TEMPEST standard hardware is not cheap, and because of the cost, a lesser standard called ZONE has been developed. ZONE hardware does not offer the same level of protection as TEMPEST hardware, but it is less expensive.
Purchasing TEMPEST standard hardware is not cheap, and because of the cost, a lesser standard called ZONE has been developed. ZONE hardware does not offer the same level of protection as TEMPEST hardware, but it is less expensive.
![]() Emanation standards are not just confined to the United States. The North Atlantic Treaty Organization (NATO) has a similar standard called the AMSG 720B Compromising Emanations Laboratory Test Standard. In Germany, the TEMPEST program is administered by the National Telecom Board. In the United Kingdom, Government Communications Headquarters (GCHQ) has a similar program.
Emanation standards are not just confined to the United States. The North Atlantic Treaty Organization (NATO) has a similar standard called the AMSG 720B Compromising Emanations Laboratory Test Standard. In Germany, the TEMPEST program is administered by the National Telecom Board. In the United Kingdom, Government Communications Headquarters (GCHQ) has a similar program.
Overt and Covert Channel
![]() Overt and covert channels refer to the capability to hide information within or using other information:
Overt and covert channels refer to the capability to hide information within or using other information:
-
 Overt channel: A transmission channel that is based on tunneling one protocol inside of another
Overt channel: A transmission channel that is based on tunneling one protocol inside of another -
 Covert channel: A transmission channel that is based on encoding data using another set of events
Covert channel: A transmission channel that is based on encoding data using another set of events
![]() There are numerous ways that Internet protocols and the data that is transferred over them can provide overt and covert channels. The bad news is that firewalls generally cannot detect these channels; therefore, attackers can use them to receive confidential information in an unauthorized manner.
There are numerous ways that Internet protocols and the data that is transferred over them can provide overt and covert channels. The bad news is that firewalls generally cannot detect these channels; therefore, attackers can use them to receive confidential information in an unauthorized manner.
![]() With an overt channel, one protocol is tunneled within another to bypass the security policy; for example Telnet over FTP, instant messaging over HTTP, and IP over Post Office Protocol version 3 (POP3). Another example of an overt channel is to use watermarks in JPEG images to leak confidential information.
With an overt channel, one protocol is tunneled within another to bypass the security policy; for example Telnet over FTP, instant messaging over HTTP, and IP over Post Office Protocol version 3 (POP3). Another example of an overt channel is to use watermarks in JPEG images to leak confidential information.
![]() One common use of overt channel is for instant messaging (IM). Most organization firewalls allow outbound HTTP but block IM. A user on the inside of the network can leak confidential information using IM over an HTTP session.
One common use of overt channel is for instant messaging (IM). Most organization firewalls allow outbound HTTP but block IM. A user on the inside of the network can leak confidential information using IM over an HTTP session.
| Note |
|
![]() Steganography is another example of an overt channel. Steganography (the root is from the Greek word steganos, meaning “covered” or “secret”) literally means covered or secret writing. The combination of CPU power and interest in privacy has led to the development of techniques for hiding messages in digital pictures and digitized audio.
Steganography is another example of an overt channel. Steganography (the root is from the Greek word steganos, meaning “covered” or “secret”) literally means covered or secret writing. The combination of CPU power and interest in privacy has led to the development of techniques for hiding messages in digital pictures and digitized audio.
![]() For example, certain bits of a digital graphic can be used to hide messages. The key to knowing which bits are special is shared between two parties that want to communicate privately. The private message typically has so few bits relative to the total number of bits in the image that changing them is not visually noticeable. Without a direct comparison of the original and the processed image, it is practically impossible to tell that anything has been changed. Still, it might be detected by statistical analysis that detects non-randomness. This non-randomness in a file indicates that information is being passed inside of the file.
For example, certain bits of a digital graphic can be used to hide messages. The key to knowing which bits are special is shared between two parties that want to communicate privately. The private message typically has so few bits relative to the total number of bits in the image that changing them is not visually noticeable. Without a direct comparison of the original and the processed image, it is practically impossible to tell that anything has been changed. Still, it might be detected by statistical analysis that detects non-randomness. This non-randomness in a file indicates that information is being passed inside of the file.
| Note |
|
![]() With a covert channel, information is encoded as another set of events. For example, an attacker could install a Trojan horse on a target host. The Trojan horse could be written to send binary information back to the server of the attacker. The client, infected with the Trojan horse, could return to the hacker’s server a ping status report in a binary format where a 0 would represent a successful ping over a one-minute period, and a 1 would represent two successful pings over a one-minute period. The hacker is keeping connectivity statistics for all the compromised clients he has around the world.
With a covert channel, information is encoded as another set of events. For example, an attacker could install a Trojan horse on a target host. The Trojan horse could be written to send binary information back to the server of the attacker. The client, infected with the Trojan horse, could return to the hacker’s server a ping status report in a binary format where a 0 would represent a successful ping over a one-minute period, and a 1 would represent two successful pings over a one-minute period. The hacker is keeping connectivity statistics for all the compromised clients he has around the world.
![]() If ICMP is not permitted through a firewall, another idea is to have the client visit the web page of the attacker. The Trojan horse software, now installed on the client, has a “call home” feature that automatically opens a connection to TCP port 80 at a specific IP address, the address of the hacker’s web server. All this so that the hacker can keep precise statistics of how many compromised workstations he possesses around the world. One visit per day would be represented by a 1, and no visits would be represented by a 0. As you might imagine, this technique is usually quite limited in bandwidth.
If ICMP is not permitted through a firewall, another idea is to have the client visit the web page of the attacker. The Trojan horse software, now installed on the client, has a “call home” feature that automatically opens a connection to TCP port 80 at a specific IP address, the address of the hacker’s web server. All this so that the hacker can keep precise statistics of how many compromised workstations he possesses around the world. One visit per day would be represented by a 1, and no visits would be represented by a 0. As you might imagine, this technique is usually quite limited in bandwidth.
| Note |
|
Phishing and Pharming
![]() In computing, phishing is an attempt to criminally acquire sensitive information, such as usernames, passwords, and credit card details, by masquerading as a trustworthy entity. Phishing is typically carried out by email or IM, and often directs users to enter details at a website, although sometimes phone contact is attempted. Phishing is an example of social engineering.
In computing, phishing is an attempt to criminally acquire sensitive information, such as usernames, passwords, and credit card details, by masquerading as a trustworthy entity. Phishing is typically carried out by email or IM, and often directs users to enter details at a website, although sometimes phone contact is attempted. Phishing is an example of social engineering.
![]() Pharming is an attack aimed at redirecting the traffic of a website to another website. Pharming is conducted either by changing the hosts file on a victim computer or by exploiting a vulnerable Domain Name System (DNS) server. Pharming has become a major concern to businesses hosting e-commerce and online banking websites.
Pharming is an attack aimed at redirecting the traffic of a website to another website. Pharming is conducted either by changing the hosts file on a victim computer or by exploiting a vulnerable Domain Name System (DNS) server. Pharming has become a major concern to businesses hosting e-commerce and online banking websites.
| Note |
|
 Integrity Attacks
Integrity Attacks
![]() Integrity violations can occur when the attacker attempts to change sensitive data without proper authorization. For example, the attacker obtains permission to write to sensitive data and changes or deletes it. The owner might not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Many businesses treat integrity violations as the most serious threat to their business, because of the difficulty in detecting changes and the possible cascading consequences of late detection.
Integrity violations can occur when the attacker attempts to change sensitive data without proper authorization. For example, the attacker obtains permission to write to sensitive data and changes or deletes it. The owner might not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Many businesses treat integrity violations as the most serious threat to their business, because of the difficulty in detecting changes and the possible cascading consequences of late detection.
![]() As an example, a consolidator of credit card transactions proceeds to make a batch transfer to a bank of all the transactions that took place during the previous 24 hours. A hacker could intercept the batch upload, change the amount of some transactions, and proceed with the upload toward the bank, pretending to be the consolidator. Neither the consolidator nor the bank would know that some of the transaction totals were changed.
As an example, a consolidator of credit card transactions proceeds to make a batch transfer to a bank of all the transactions that took place during the previous 24 hours. A hacker could intercept the batch upload, change the amount of some transactions, and proceed with the upload toward the bank, pretending to be the consolidator. Neither the consolidator nor the bank would know that some of the transaction totals were changed.
![]() Hackers can use many types of attacks to compromise integrity:
Hackers can use many types of attacks to compromise integrity:
-
 Salami attacks: A salami attack is a series of minor data security attacks that together result in a larger attack. For example, a fraud activity in a bank where an employee steals a small amount of funds from several accounts can be considered a salami attack. A key feature to the salami attack is its resistance to detection.
Salami attacks: A salami attack is a series of minor data security attacks that together result in a larger attack. For example, a fraud activity in a bank where an employee steals a small amount of funds from several accounts can be considered a salami attack. A key feature to the salami attack is its resistance to detection. -
 Data diddling: This type of attack involves changing data before or during input into a computer. A virus, the programmer of the database or application, or anyone else involved in the process of storing information in a computer could change the data.
Data diddling: This type of attack involves changing data before or during input into a computer. A virus, the programmer of the database or application, or anyone else involved in the process of storing information in a computer could change the data. -
 Trust exploits: A trust exploitation refers to an individual taking advantage of a trust relationship within a network.
Trust exploits: A trust exploitation refers to an individual taking advantage of a trust relationship within a network. -
 Password attacks: A password attack is any attack that attempts to identify a user account, password, or both. A password attack often uses a method called a brute-force attack; however, password attacks can also employ methods such as Trojan horse programs, IP spoofing, keyloggers, and packet sniffers.
Password attacks: A password attack is any attack that attempts to identify a user account, password, or both. A password attack often uses a method called a brute-force attack; however, password attacks can also employ methods such as Trojan horse programs, IP spoofing, keyloggers, and packet sniffers. -
 Session hijacking: This attack is the exploitation of a valid computer session, sometimes also called a session key, to gain unauthorized access to information or services in a computer system. TCP session hijacking is a common variant of the man-in-the-middle attack.
Session hijacking: This attack is the exploitation of a valid computer session, sometimes also called a session key, to gain unauthorized access to information or services in a computer system. TCP session hijacking is a common variant of the man-in-the-middle attack.
| Note |
|
![]() The sections that follow describe some of the different types of strategies used by hackers to compromise the integrity of the data.
The sections that follow describe some of the different types of strategies used by hackers to compromise the integrity of the data.
Trust Exploitation
![]() Although it is not an attack in itself, trust exploitation refers to an individual taking advantage of a trust relationship within a network.
Although it is not an attack in itself, trust exploitation refers to an individual taking advantage of a trust relationship within a network.
![]() An example of a trust exploitation, consider the network in Figure 1-13, where a system in the demilitarized zone (DMZ) of a firewall, such as Server A, has a trust relationship with a system on the inside of a firewall, such as Server B. When a hacker on the outside network compromises Server A, the attacker can leverage the trust relationship Server B has with Server A to gain access to Server B.
An example of a trust exploitation, consider the network in Figure 1-13, where a system in the demilitarized zone (DMZ) of a firewall, such as Server A, has a trust relationship with a system on the inside of a firewall, such as Server B. When a hacker on the outside network compromises Server A, the attacker can leverage the trust relationship Server B has with Server A to gain access to Server B.
![]() Several trust models may exist in a network:
Several trust models may exist in a network:
-
 Windows
Windows -
 Linux and UNIX
Linux and UNIX -
 Network File System (NFS)
Network File System (NFS) -
 Network Information Services Plus (NIS+)
Network Information Services Plus (NIS+)
-
![]() The risk of trust exploitation can be reduced by introducing, among other techniques, tight constraints on trust levels within a network, such as forbidding traffic on the DMZ to access the inside network, or by insisting on strong authentication.
The risk of trust exploitation can be reduced by introducing, among other techniques, tight constraints on trust levels within a network, such as forbidding traffic on the DMZ to access the inside network, or by insisting on strong authentication.
Port Redirection
![]() A port redirection attack is a trust exploitation-based attack that uses a compromised host to pass traffic through a firewall that the firewall would otherwise drop. As an example, Figure 1-14 shows a firewall with three interfaces: Inside, Outside, and DMZ, with Host A on the DMZ interface. A host located on the outside interface can reach Host A, but cannot reach the host on the inside, Host B. Host A can reach both the host on the outside and Host B. If a hacker can compromise Host A, the hacker can install software on the DMZ host that redirects traffic from the outside host directly to the inside host (Host B). Although neither communication violates the rules implemented in the firewall, the outside host now has connectivity to the inside host through the port redirection process on the DMZ host. An example of an application that can provide this type of access is Netcat and fport.
A port redirection attack is a trust exploitation-based attack that uses a compromised host to pass traffic through a firewall that the firewall would otherwise drop. As an example, Figure 1-14 shows a firewall with three interfaces: Inside, Outside, and DMZ, with Host A on the DMZ interface. A host located on the outside interface can reach Host A, but cannot reach the host on the inside, Host B. Host A can reach both the host on the outside and Host B. If a hacker can compromise Host A, the hacker can install software on the DMZ host that redirects traffic from the outside host directly to the inside host (Host B). Although neither communication violates the rules implemented in the firewall, the outside host now has connectivity to the inside host through the port redirection process on the DMZ host. An example of an application that can provide this type of access is Netcat and fport.
![]() The primary way to mitigate port redirection is to use proper trust models that are network specific. If a system is under attack, a host-based intrusion prevention system (HIPS) can help detect a hacker and prevent the installation of such port redirect utilities on a host.
The primary way to mitigate port redirection is to use proper trust models that are network specific. If a system is under attack, a host-based intrusion prevention system (HIPS) can help detect a hacker and prevent the installation of such port redirect utilities on a host.
Password Attacks
![]() Password attacks can be implemented using several methods, including brute-force attacks, Trojan horse programs, IP spoofing, keyloggers, and packet sniffers. Although packet sniffers and IP spoofing can yield user accounts and passwords, password attacks usually refer to repeated attempts to identify a user account, password, or both. These repeated attempts are called brute-force attacks.
Password attacks can be implemented using several methods, including brute-force attacks, Trojan horse programs, IP spoofing, keyloggers, and packet sniffers. Although packet sniffers and IP spoofing can yield user accounts and passwords, password attacks usually refer to repeated attempts to identify a user account, password, or both. These repeated attempts are called brute-force attacks.
![]() To execute a brute-force attack, an attacker can use a program that runs across the network and attempts to log in to a shared resource, such as a server. When an attacker gains access to a resource, the attacker has the same access rights as the rightful user. If this account has sufficient privileges, the attacker can create a back door for future access, without concern for any status and password changes to the compromised user account.
To execute a brute-force attack, an attacker can use a program that runs across the network and attempts to log in to a shared resource, such as a server. When an attacker gains access to a resource, the attacker has the same access rights as the rightful user. If this account has sufficient privileges, the attacker can create a back door for future access, without concern for any status and password changes to the compromised user account.
![]() Just as with packet sniffers and IP spoofing attacks, a brute-force password attack can provide access to accounts that attackers then use to modify critical network files and services. For example, an attacker compromises your network integrity by modifying your network routing tables. This trick reroutes all network packets to the attacker before transmitting them to their final destination. In such a case, an attacker can monitor all network traffic, effectively becoming a man in the middle.
Just as with packet sniffers and IP spoofing attacks, a brute-force password attack can provide access to accounts that attackers then use to modify critical network files and services. For example, an attacker compromises your network integrity by modifying your network routing tables. This trick reroutes all network packets to the attacker before transmitting them to their final destination. In such a case, an attacker can monitor all network traffic, effectively becoming a man in the middle.
![]() Passwords present a security risk if they are stored as plaintext. You must encrypt passwords to overcome risks. On most systems, passwords are processed through an encryption algorithm that generates a one-way hash on passwords. You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login process, you supply an account and password, and the password encryption algorithm generates a one-way hash. The algorithm compares this hash to the hash stored on the system. If the hashes are the same, the algorithm assumes that the user supplied the proper password.
Passwords present a security risk if they are stored as plaintext. You must encrypt passwords to overcome risks. On most systems, passwords are processed through an encryption algorithm that generates a one-way hash on passwords. You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login process, you supply an account and password, and the password encryption algorithm generates a one-way hash. The algorithm compares this hash to the hash stored on the system. If the hashes are the same, the algorithm assumes that the user supplied the proper password.
![]() Remember that passing the password through an algorithm results in a password hash. The hash is not the encrypted password, but rather a result of the algorithm. The strength of the hash is such that the hash value can be re-created only by using the original user and password information, and that it is impossible to retrieve the original information from the hash. This strength makes hashes perfect for encoding passwords for storage. In granting authorization, the hashes, rather than the plain password, are calculated and compared.
Remember that passing the password through an algorithm results in a password hash. The hash is not the encrypted password, but rather a result of the algorithm. The strength of the hash is such that the hash value can be re-created only by using the original user and password information, and that it is impossible to retrieve the original information from the hash. This strength makes hashes perfect for encoding passwords for storage. In granting authorization, the hashes, rather than the plain password, are calculated and compared.
![]() Hackers use many tools and techniques to crack passwords:
Hackers use many tools and techniques to crack passwords:
-
 Word lists: These programs use lists of words, phrases, or other combinations of letters, numbers, and symbols that computer users often use as passwords. Hackers enter word after word, at high speed, called a dictionary attack, until they find a match.
Word lists: These programs use lists of words, phrases, or other combinations of letters, numbers, and symbols that computer users often use as passwords. Hackers enter word after word, at high speed, called a dictionary attack, until they find a match. -
 Brute force: This approach relies on power and repetition. It compares every possible combination and permutation of characters until it finds a match. Brute force eventually cracks any password, but it might take a long, long time. Brute force is an extremely slow process because it uses every conceivable character combination.
Brute force: This approach relies on power and repetition. It compares every possible combination and permutation of characters until it finds a match. Brute force eventually cracks any password, but it might take a long, long time. Brute force is an extremely slow process because it uses every conceivable character combination. -
 Hybrid crackers: Some password crackers mix the two techniques. This combines the best of both methods and is highly effective against poorly constructed passwords.
Hybrid crackers: Some password crackers mix the two techniques. This combines the best of both methods and is highly effective against poorly constructed passwords.
![]() Password cracking attacks any application or service that accepts user authentication, including the following:
Password cracking attacks any application or service that accepts user authentication, including the following:
-
 NetBIOS over TCP (TCP 139)
NetBIOS over TCP (TCP 139) -
 Direct host (TCP 445)
Direct host (TCP 445) -
 FTP (TCP 21)
FTP (TCP 21) -
 Telnet (TCP 23)
Telnet (TCP 23) -
 Simple Network Management Protocol (SNMP) (UDP 161)
Simple Network Management Protocol (SNMP) (UDP 161) -
 Point-to-Point Tunneling Protocol (PPTP) (TCP 1723)
Point-to-Point Tunneling Protocol (PPTP) (TCP 1723) -
 Terminal services (TCP 3389)
Terminal services (TCP 3389)
| Note |
|
 Availability Attacks
Availability Attacks
![]() DoS attacks attempt to compromise the availability of a network, host, or application. They are considered a major risk because they can easily interrupt a business process and cause significant loss. These attacks are relatively simple to conduct, even by an unskilled attacker.
DoS attacks attempt to compromise the availability of a network, host, or application. They are considered a major risk because they can easily interrupt a business process and cause significant loss. These attacks are relatively simple to conduct, even by an unskilled attacker.
![]() DoS attacks are usually the consequence of one of the following:
DoS attacks are usually the consequence of one of the following:
-
 The failure of a host or application to handle an unexpected condition, such as maliciously formatted input data or an unexpected interaction of system components.
The failure of a host or application to handle an unexpected condition, such as maliciously formatted input data or an unexpected interaction of system components. -
 The inability of a network, host, or application to handle an enormous quantity of data, which crashes the system or brings it to a halt. Even if the firewall protects the corporate web server sitting on the DMZ from receiving a large amount of data and thus from crashing, the link connecting the corporation with its service provider will be totally clogged, and this bandwidth starvation will itself be a DoS.
The inability of a network, host, or application to handle an enormous quantity of data, which crashes the system or brings it to a halt. Even if the firewall protects the corporate web server sitting on the DMZ from receiving a large amount of data and thus from crashing, the link connecting the corporation with its service provider will be totally clogged, and this bandwidth starvation will itself be a DoS.
![]() Hackers can use many types of attacks to compromise availability:
Hackers can use many types of attacks to compromise availability:
-
 Botnets
Botnets -
 DoS
DoS -
 DDoS
DDoS -
 SYN floods
SYN floods -
 ICMP floods
ICMP floods -
 Electrical power
Electrical power -
 Computer environment
Computer environment
| Note |
|
Botnets
![]() Botnet is a term for a collection of software robots, or bots, which run autonomously and automatically. They run on groups of “zombie” computers controlled by crackers.
Botnet is a term for a collection of software robots, or bots, which run autonomously and automatically. They run on groups of “zombie” computers controlled by crackers.
![]() Although the term botnet can be used to refer to any group of bots, it is generally used to refer to a collection of compromised systems running worms, Trojan horses, or back doors, under a common command and control infrastructure. The originator of a botnet controls the group of computers remotely, usually through a means such as Internet Relay Chat (IRC).
Although the term botnet can be used to refer to any group of bots, it is generally used to refer to a collection of compromised systems running worms, Trojan horses, or back doors, under a common command and control infrastructure. The originator of a botnet controls the group of computers remotely, usually through a means such as Internet Relay Chat (IRC).
![]() Often, the command and control takes place via an IRC server or a specific channel on a public IRC network. A bot typically runs hidden. Generally, the attacker has compromised a large number of systems using various methods, such as exploits, buffer overflows, and so on. Newer bots automatically scan their environment and propagate using detected vulnerabilities and weak passwords. Sometimes a controller will hide an IRC server installation on an educational or corporate site, where high-speed connections can support a large number of other bots.
Often, the command and control takes place via an IRC server or a specific channel on a public IRC network. A bot typically runs hidden. Generally, the attacker has compromised a large number of systems using various methods, such as exploits, buffer overflows, and so on. Newer bots automatically scan their environment and propagate using detected vulnerabilities and weak passwords. Sometimes a controller will hide an IRC server installation on an educational or corporate site, where high-speed connections can support a large number of other bots.
![]() Several botnets have been found and removed from the Internet. The Dutch police found a 1.5-million node botnet and the Norwegian ISP Telenor disbanded a 10,000-node botnet. Large coordinated international efforts to shut down botnets have also been initiated. Some estimates indicate that up to 25 percent of all personal computers are part of a botnet.
Several botnets have been found and removed from the Internet. The Dutch police found a 1.5-million node botnet and the Norwegian ISP Telenor disbanded a 10,000-node botnet. Large coordinated international efforts to shut down botnets have also been initiated. Some estimates indicate that up to 25 percent of all personal computers are part of a botnet.
DoS and DDoS Attacks
![]() DoS attacks are the most publicized form of attack. They are also among the most difficult to eliminate. A DoS attack on a server sends an extremely large volume of requests over a network or the Internet. These large volumes of requests cause the attacked server to slow down dramatically. Consequently, the attacked server becomes unavailable for legitimate access and use.
DoS attacks are the most publicized form of attack. They are also among the most difficult to eliminate. A DoS attack on a server sends an extremely large volume of requests over a network or the Internet. These large volumes of requests cause the attacked server to slow down dramatically. Consequently, the attacked server becomes unavailable for legitimate access and use.
![]() DoS attacks differ from most other attacks because DoS attacks do not try to gain access to your network or the information on your network. These attacks focus on making a service unavailable for normal use. Attackers typically accomplish this by exhausting some resource limitation on the network or within an operating system or application. These attacks require little effort to execute because they typically take advantage of protocol weaknesses or because the attacks use traffic normally allowed into a network. DoS attacks are among the most difficult to completely eliminate because of the way they use protocol weaknesses and accepted traffic to attack a network. Some hackers regard DoS attacks as trivial and in bad form because they require so little effort to execute. Still, because of their ease of implementation and potentially significant damage, DoS attacks deserve special attention from security administrators.
DoS attacks differ from most other attacks because DoS attacks do not try to gain access to your network or the information on your network. These attacks focus on making a service unavailable for normal use. Attackers typically accomplish this by exhausting some resource limitation on the network or within an operating system or application. These attacks require little effort to execute because they typically take advantage of protocol weaknesses or because the attacks use traffic normally allowed into a network. DoS attacks are among the most difficult to completely eliminate because of the way they use protocol weaknesses and accepted traffic to attack a network. Some hackers regard DoS attacks as trivial and in bad form because they require so little effort to execute. Still, because of their ease of implementation and potentially significant damage, DoS attacks deserve special attention from security administrators.
![]() System administrators can install software fixes to limit the damage caused by all known DoS attacks. However, as with viruses, hackers constantly develop new DoS attacks.
System administrators can install software fixes to limit the damage caused by all known DoS attacks. However, as with viruses, hackers constantly develop new DoS attacks.
![]() A DDoS attack generates much higher levels of flooding traffic by using the combined bandwidth of multiple machines to target a single machine or network. The DDoS attack enlists a network of compromised machines that contain a remotely controlled agent, or zombie, attack program. A master control mechanism provides direction and control. When the zombies receive instructions from the master agent, they each begin generating malicious traffic aimed at the victim.
A DDoS attack generates much higher levels of flooding traffic by using the combined bandwidth of multiple machines to target a single machine or network. The DDoS attack enlists a network of compromised machines that contain a remotely controlled agent, or zombie, attack program. A master control mechanism provides direction and control. When the zombies receive instructions from the master agent, they each begin generating malicious traffic aimed at the victim.
![]() DDoS attacks are the “next generation” of DoS attacks on the Internet. This type of attack is not new. UDP and TCP SYN flooding, ICMP echo request floods, and ICMP directed broadcasts (also known as Smurf attacks) are similar to DDoS attacks; however, the scope of the attack is new. Victims of DDoS attacks experience packet flooding from many different sources, possibly spoofed IP source addresses, which brings their network connectivity to a grinding halt. In the past, the typical DoS attack involved a single attempt to flood a target host with packets. With DDoS tools, an attacker can conduct the same attack using thousands of systems.
DDoS attacks are the “next generation” of DoS attacks on the Internet. This type of attack is not new. UDP and TCP SYN flooding, ICMP echo request floods, and ICMP directed broadcasts (also known as Smurf attacks) are similar to DDoS attacks; however, the scope of the attack is new. Victims of DDoS attacks experience packet flooding from many different sources, possibly spoofed IP source addresses, which brings their network connectivity to a grinding halt. In the past, the typical DoS attack involved a single attempt to flood a target host with packets. With DDoS tools, an attacker can conduct the same attack using thousands of systems.
![]() Figure 1-15 shows the process of a DDoS attack:
Figure 1-15 shows the process of a DDoS attack:
-
 The hacker uses a terminal to scan for systems to hack.
The hacker uses a terminal to scan for systems to hack. -
 After the hacker accesses handler systems, the hacker installs zombie software on them.
After the hacker accesses handler systems, the hacker installs zombie software on them. -
 The zombies aim to scan, compromise, and infect agent systems.
The zombies aim to scan, compromise, and infect agent systems. -
 When the hacker accesses agent systems, the hacker then loads remote-control attack software to carry out the DDoS attack.
When the hacker accesses agent systems, the hacker then loads remote-control attack software to carry out the DDoS attack.
| Note |
|
TCP SYN Flood Attack
![]() Generally, in a TCP SYN flood, an attacker sends a flood of SYN segments to a target server but deliberately never completes the handshake. Servers have a limit to the number of half-open connections they will maintain before they eventually stop accepting new connections. In other words, the exhausting of the new connection resource acts as a DoS attack. The source address used on the SYN segment is usually forged, using a nonresponsive part of the address space and thus preventing resets (RST).
Generally, in a TCP SYN flood, an attacker sends a flood of SYN segments to a target server but deliberately never completes the handshake. Servers have a limit to the number of half-open connections they will maintain before they eventually stop accepting new connections. In other words, the exhausting of the new connection resource acts as a DoS attack. The source address used on the SYN segment is usually forged, using a nonresponsive part of the address space and thus preventing resets (RST).
![]() Cisco IOS Software has a TCP intercept capability designed to combat SYN flooding. When the Cisco IOS Software is configured to use intercept mode, which it is the default, it checks for incoming TCP connection requests and proxy-answers these requests on behalf of the destination server to ensure that the request is valid. After the TCP intercept has established a genuine connection with the client and the server, it then merges these two connections into a single source-destination session. It offers a zero window to the client to prevent it from sending data until the server sends a window offer back. In the case of bogus requests, TCP intercept uses aggressive timeouts on half-open connections and supports threshold levels for the number of outstanding and incoming TCP connection requests to protect servers while still allowing valid requests through. However, keep in mind that a severe attack might even have an impact on the router providing the TCP intercept protection. The Cisco ASAs implement a feature similar to TCP intercept, but using SYN cookies.
Cisco IOS Software has a TCP intercept capability designed to combat SYN flooding. When the Cisco IOS Software is configured to use intercept mode, which it is the default, it checks for incoming TCP connection requests and proxy-answers these requests on behalf of the destination server to ensure that the request is valid. After the TCP intercept has established a genuine connection with the client and the server, it then merges these two connections into a single source-destination session. It offers a zero window to the client to prevent it from sending data until the server sends a window offer back. In the case of bogus requests, TCP intercept uses aggressive timeouts on half-open connections and supports threshold levels for the number of outstanding and incoming TCP connection requests to protect servers while still allowing valid requests through. However, keep in mind that a severe attack might even have an impact on the router providing the TCP intercept protection. The Cisco ASAs implement a feature similar to TCP intercept, but using SYN cookies.
![]() A TCP SYN flood attack, a form of DoS attack, is usually initiated using IP spoofing. Figure 1-16 shows how a TCP connection is established between a client and server. After the connection between the client and the server is open, the client and server can send service-specific data.
A TCP SYN flood attack, a form of DoS attack, is usually initiated using IP spoofing. Figure 1-16 shows how a TCP connection is established between a client and server. After the connection between the client and the server is open, the client and server can send service-specific data.
![]() An avenue of attack exists at the point where the server has sent the SYN-ACK to the client but has not yet received the ACK message. This condition is a half-open connection.
An avenue of attack exists at the point where the server has sent the SYN-ACK to the client but has not yet received the ACK message. This condition is a half-open connection.
![]() Now consider that the server has built in its system memory a data structure describing all pending connections. This data structure is a finite size and can overflow if too many half-open connections are created.
Now consider that the server has built in its system memory a data structure describing all pending connections. This data structure is a finite size and can overflow if too many half-open connections are created.
![]() Hackers use IP spoofing to create half-open connections. The attacker sends SYN messages to the victim server. These messages appear to be legitimate but, in fact, refer to a client system that is unable to respond to the SYN-ACK messages. This means that the client never sends a final ACK message to the victim server and the connection remains half open.
Hackers use IP spoofing to create half-open connections. The attacker sends SYN messages to the victim server. These messages appear to be legitimate but, in fact, refer to a client system that is unable to respond to the SYN-ACK messages. This means that the client never sends a final ACK message to the victim server and the connection remains half open.
![]() The half-open connection data structure on the victim server eventually fills with messages, and the system is unable to accept any new incoming connections. Normally, a timeout period is associated with any pending connection. Half-open connections eventually expire, and the victim server recovers. However, the attacking system can simply continue sending IP-spoofed packets requesting new connections faster than the victim system can empty the table.
The half-open connection data structure on the victim server eventually fills with messages, and the system is unable to accept any new incoming connections. Normally, a timeout period is associated with any pending connection. Half-open connections eventually expire, and the victim server recovers. However, the attacking system can simply continue sending IP-spoofed packets requesting new connections faster than the victim system can empty the table.
![]() In most cases, the victim of such an attack has difficulty accepting any new incoming network connection. In these cases, the attack does not affect existing incoming connections or the ability to originate outgoing network connections. However, in some cases, the system might exhaust memory, crash, or be rendered otherwise inoperative.
In most cases, the victim of such an attack has difficulty accepting any new incoming network connection. In these cases, the attack does not affect existing incoming connections or the ability to originate outgoing network connections. However, in some cases, the system might exhaust memory, crash, or be rendered otherwise inoperative.
![]() The attacker obscures his or her location by making the source addresses in the SYN packets implausible. When the packet arrives at the victim server, there is no way to determine its true source. Because the network forwards packets based on destination address, the only way to validate the source of a packet is to use input source filtering, such as ACLs.
The attacker obscures his or her location by making the source addresses in the SYN packets implausible. When the packet arrives at the victim server, there is no way to determine its true source. Because the network forwards packets based on destination address, the only way to validate the source of a packet is to use input source filtering, such as ACLs.
ICMP Flood/Smurf Attacks
![]() Because ICMP can be a useful troubleshooting and diagnostic tool, it is often permitted by firewalls. Unfortunately, for the hosts behind such a firewall, bugs in the IP layers of the hosts can potentially be exploited.
Because ICMP can be a useful troubleshooting and diagnostic tool, it is often permitted by firewalls. Unfortunately, for the hosts behind such a firewall, bugs in the IP layers of the hosts can potentially be exploited.
![]() Some DoS tricks that use ICMP are the ping of death, which uses packets that are too large, and another technique that causes ICMP fragments to fill the reassembly buffers of a device.
Some DoS tricks that use ICMP are the ping of death, which uses packets that are too large, and another technique that causes ICMP fragments to fill the reassembly buffers of a device.
![]() ICMP flooding attacks became popular because of amplification techniques such as the Smurf attacks, which use a spoofed broadcast ping to elicit a large number of responses that then bombard a target.
ICMP flooding attacks became popular because of amplification techniques such as the Smurf attacks, which use a spoofed broadcast ping to elicit a large number of responses that then bombard a target.
![]() Smurf attacks use ICMP echo request packets directed at IP broadcast addresses from a remote site. The intent is to cause DoS. Three parties are involved in the attacks: the attacker, the intermediary, and the victim (the intermediary can also be a victim), as shown in Figure 1-17.
Smurf attacks use ICMP echo request packets directed at IP broadcast addresses from a remote site. The intent is to cause DoS. Three parties are involved in the attacks: the attacker, the intermediary, and the victim (the intermediary can also be a victim), as shown in Figure 1-17.
![]() The intermediary receives an ICMP echo request packet that is directed to the IP broadcast address of its subnet. If the intermediary does not filter ICMP traffic directed to IP broadcast addresses, many of the machines on the network receive this ICMP echo request packet and send an ICMP echo reply packet back. If many of the machines on a network respond to this ICMP echo request, the result can be a severely loaded network.
The intermediary receives an ICMP echo request packet that is directed to the IP broadcast address of its subnet. If the intermediary does not filter ICMP traffic directed to IP broadcast addresses, many of the machines on the network receive this ICMP echo request packet and send an ICMP echo reply packet back. If many of the machines on a network respond to this ICMP echo request, the result can be a severely loaded network.
![]() Attackers create forged packets that contain the spoofed source address of the intended victim. When the machines at the site of the intermediary respond to the ICMP echo requests, they send replies to the victim machine. The victim is potentially subjected to severe network congestion.
Attackers create forged packets that contain the spoofed source address of the intended victim. When the machines at the site of the intermediary respond to the ICMP echo requests, they send replies to the victim machine. The victim is potentially subjected to severe network congestion.
| Note |
|
Electrical Power Attacks
![]() There are three basic types of power attacks (or at least concerns), as shown in Table 1-1. Electrical power attacks would require that the hacker have physical access to your installation or to the grid. Regardless, organizations should be concerned about the constant and proper supply of electricity.
There are three basic types of power attacks (or at least concerns), as shown in Table 1-1. Electrical power attacks would require that the hacker have physical access to your installation or to the grid. Regardless, organizations should be concerned about the constant and proper supply of electricity.
|
|
| |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
![]() You can limit electrical supply problems by adhering to the following guidelines:
You can limit electrical supply problems by adhering to the following guidelines:
-
 Install UPSs for mission-critical Cisco network devices.
Install UPSs for mission-critical Cisco network devices. -
 Install backup generator systems for mission-critical supplies.
Install backup generator systems for mission-critical supplies. -
 Plan for and initiate regular UPS or generator testing and maintenance procedures based on the manufacturer suggested preventive maintenance schedule.
Plan for and initiate regular UPS or generator testing and maintenance procedures based on the manufacturer suggested preventive maintenance schedule. -
 Install redundant power supplies on critical devices.
Install redundant power supplies on critical devices. -
 Monitor and alarm power-related parameters at the power supply and device levels.
Monitor and alarm power-related parameters at the power supply and device levels.
Computer Environment Attacks
![]() Environmental problems address everything that is of a physical nature that is not power. Such attacks require that the hacker have physical access to your building or to the supplier of that resource. The following are concerns that are of an environmental nature that an attacker can use to try to launch a DoS attack:
Environmental problems address everything that is of a physical nature that is not power. Such attacks require that the hacker have physical access to your building or to the supplier of that resource. The following are concerns that are of an environmental nature that an attacker can use to try to launch a DoS attack:
-
 Temperature: Computer systems require cool temperatures. Outages can happen because an air-conditioning system fails.
Temperature: Computer systems require cool temperatures. Outages can happen because an air-conditioning system fails. -
 Air flow: Computer-based systems do not like dust. The best data centers have a positive air-flow system in place wherein the air pressure within the data center is greater than the air pressure outside of the data center, causing the air to blow out instead of dust blowing in when a door is opened.
Air flow: Computer-based systems do not like dust. The best data centers have a positive air-flow system in place wherein the air pressure within the data center is greater than the air pressure outside of the data center, causing the air to blow out instead of dust blowing in when a door is opened. -
 Humidity: Electronic equipment does not tolerate water. Even the minor amounts of water found in humidity can damage equipment.
Humidity: Electronic equipment does not tolerate water. Even the minor amounts of water found in humidity can damage equipment. -
 Water: Water damages electronic equipment. Controls must be in place to protect the data center from floods.
Water: Water damages electronic equipment. Controls must be in place to protect the data center from floods. -
 Gas: Gas is a flammable. It is important that electronic equipment does not create sparks in the presence of gas.
Gas: Gas is a flammable. It is important that electronic equipment does not create sparks in the presence of gas.
![]() Mission-critical Cisco network equipment should be located in wiring closets or in computer or telecommunications rooms that meet the following minimum requirements:
Mission-critical Cisco network equipment should be located in wiring closets or in computer or telecommunications rooms that meet the following minimum requirements:
-
 The room must be locked, with only authorized personnel allowed access.
The room must be locked, with only authorized personnel allowed access. -
 The room should not be accessible via a dropped ceiling, raised floor, window, ductwork, or point of entry other than the secured access point.
The room should not be accessible via a dropped ceiling, raised floor, window, ductwork, or point of entry other than the secured access point. -
 If possible, use electronic access control, with all entry attempts logged by security systems and monitored by security personnel.
If possible, use electronic access control, with all entry attempts logged by security systems and monitored by security personnel. -
 If possible, security personnel should monitor activity using security cameras with automatic recording.
If possible, security personnel should monitor activity using security cameras with automatic recording.
![]() Take the following actions to limit environmental damage to Cisco network devices:
Take the following actions to limit environmental damage to Cisco network devices:
-
 Supply the room with dependable temperature- and humidity-control systems. Always verify the recommended environmental parameters of the Cisco network equipment with the supplied product documentation.
Supply the room with dependable temperature- and humidity-control systems. Always verify the recommended environmental parameters of the Cisco network equipment with the supplied product documentation. -
 Remove any sources of electrostatic and magnetic interferences in the room.
Remove any sources of electrostatic and magnetic interferences in the room.
 Best Practices to Defeat Network Attacks
Best Practices to Defeat Network Attacks
![]() Defending your network against attack requires constant vigilance and education. The following 10 practices represent the best insurance for your network:
Defending your network against attack requires constant vigilance and education. The following 10 practices represent the best insurance for your network:
-
 Keep patches current by installing them weekly or daily, if possible, to prevent buffer-overflow and privilege-escalation attacks.
Keep patches current by installing them weekly or daily, if possible, to prevent buffer-overflow and privilege-escalation attacks. -
 Shut down unnecessary services and ports.
Shut down unnecessary services and ports. -
 Use strong passwords and change them often.
Use strong passwords and change them often. -
 Control physical access to systems.
Control physical access to systems. -
 Avoid unnecessary web page inputs. Some websites allow users to enter usernames and passwords. A hacker can enter more than just a username. For example, entering jdoe; rm -rf / might allow an attacker to remove the root file system from a UNIX server. Programmers should limit input characters and not accept invalid characters such as | ; < > as possible input.
Avoid unnecessary web page inputs. Some websites allow users to enter usernames and passwords. A hacker can enter more than just a username. For example, entering jdoe; rm -rf / might allow an attacker to remove the root file system from a UNIX server. Programmers should limit input characters and not accept invalid characters such as | ; < > as possible input. -
 Perform backups and test the backed up files on a regular basis.
Perform backups and test the backed up files on a regular basis. -
 Educate employees about the risks of social engineering and develop strategies to validate identities over the phone, via email, or in person.
Educate employees about the risks of social engineering and develop strategies to validate identities over the phone, via email, or in person. -
 Encrypt and password-protect sensitive data.
Encrypt and password-protect sensitive data. -
 Implement security hardware and software such as firewalls, IPSs, VPN devices, antivirus software, and content filtering.
Implement security hardware and software such as firewalls, IPSs, VPN devices, antivirus software, and content filtering. -
 Develop a written security policy for the company.
Develop a written security policy for the company.
![]() These methods are only a starting point for sound security management. Organizations must remain vigilant at all times to defend against continually evolving threats.
These methods are only a starting point for sound security management. Organizations must remain vigilant at all times to defend against continually evolving threats.

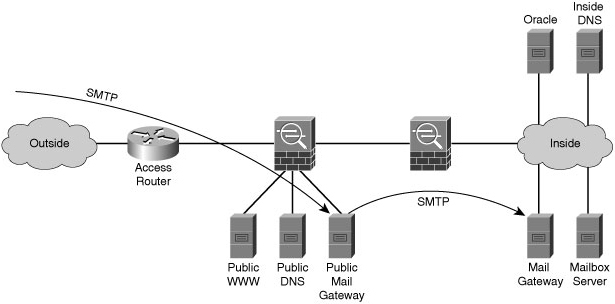
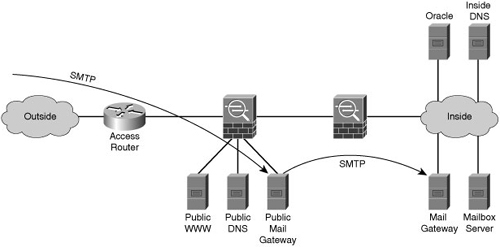
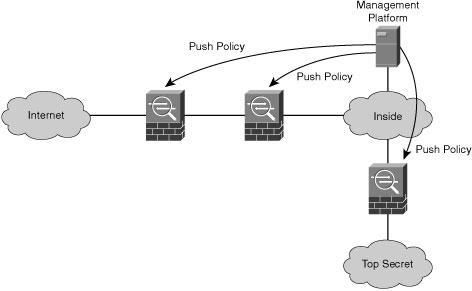
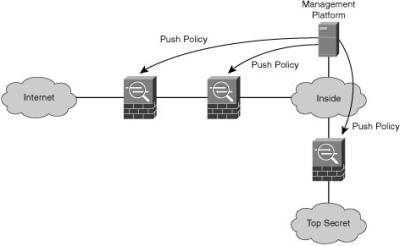
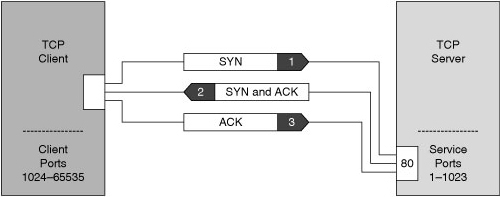
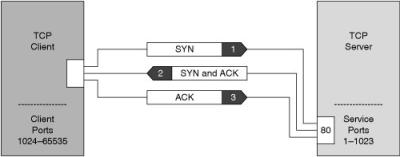
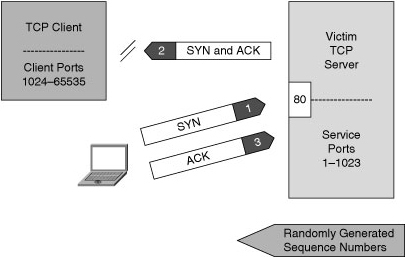
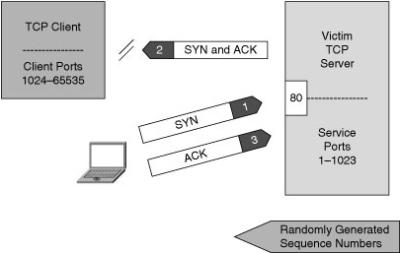
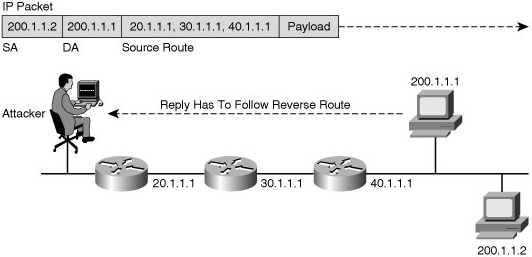
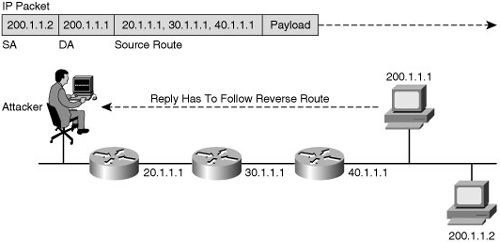
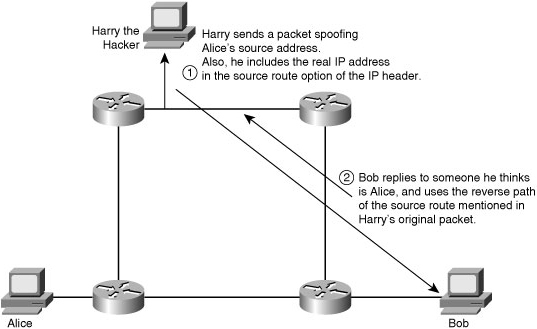
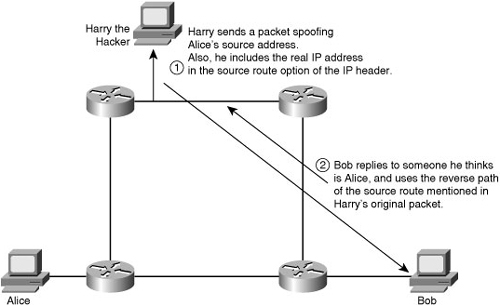
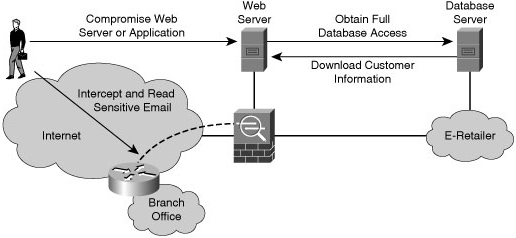
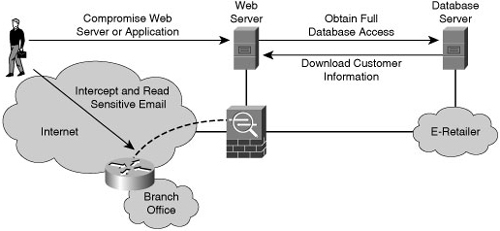
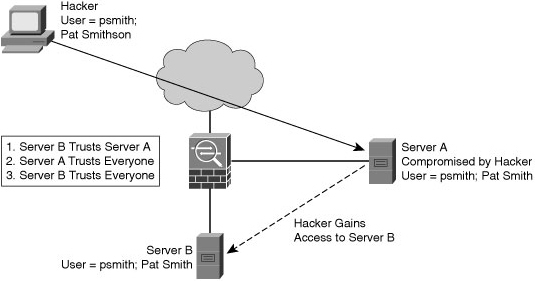
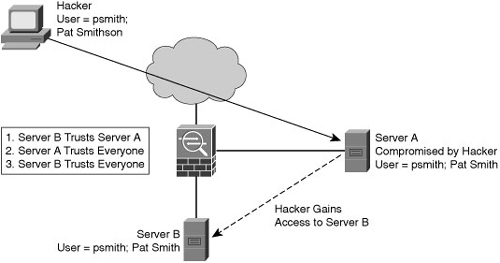
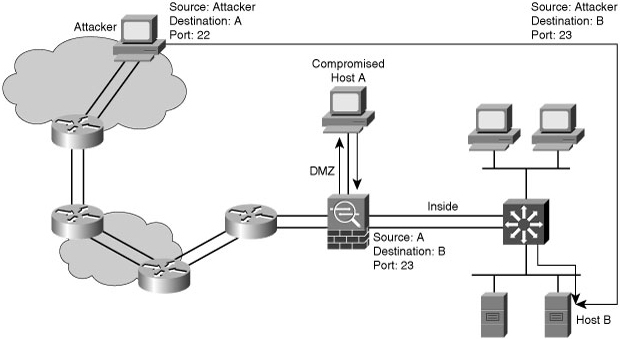
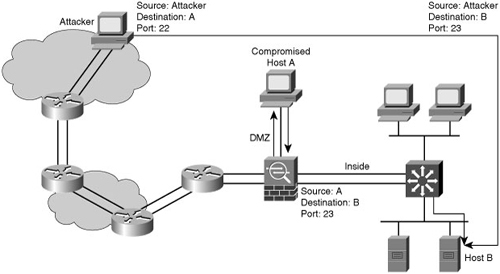
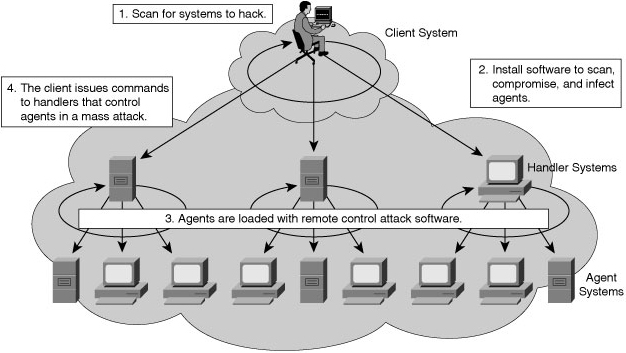
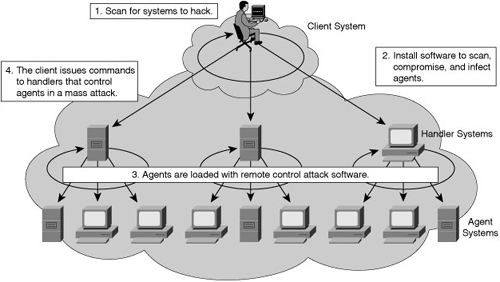
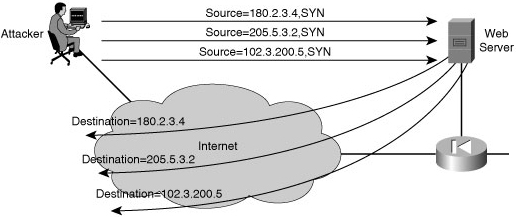
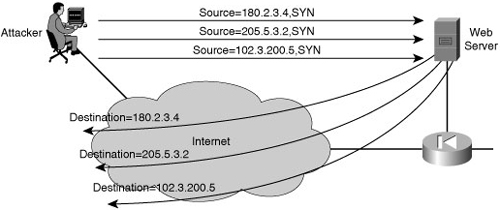
0 comments
Post a Comment