Designing Site-to-Site VPNs
![]() Site-to-site VPNs are an alternative WAN infrastructure used to connect branch offices, home offices, or business partners to all or portions of an enterprise network. VPNs do not inherently change private WAN requirements, such as support for multiple protocols, high reliability, and extensive scalability, but instead meet these requirements more cost-effectively and with greater flexibility. Site-to-site VPNs use the most pervasive transport technologies available today, such as the public Internet or service provider IP networks, by using tunneling and encryption for data privacy and quality of service (QoS) for transport reliability.
Site-to-site VPNs are an alternative WAN infrastructure used to connect branch offices, home offices, or business partners to all or portions of an enterprise network. VPNs do not inherently change private WAN requirements, such as support for multiple protocols, high reliability, and extensive scalability, but instead meet these requirements more cost-effectively and with greater flexibility. Site-to-site VPNs use the most pervasive transport technologies available today, such as the public Internet or service provider IP networks, by using tunneling and encryption for data privacy and quality of service (QoS) for transport reliability.
Site-to-Site VPN Applications
![]() Site-to-site VPNs can be used to replace costly WAN services or serve as a backup for disaster recovery purposes. Site-to-site VPNs can also help organizations meet regulatory requirements by providing encryption for sensitive data. This section examines these common uses for site-to-site IPsec VPNs.
Site-to-site VPNs can be used to replace costly WAN services or serve as a backup for disaster recovery purposes. Site-to-site VPNs can also help organizations meet regulatory requirements by providing encryption for sensitive data. This section examines these common uses for site-to-site IPsec VPNs.
 WAN Replacement Using Site-to-Site IPsec VPNs
WAN Replacement Using Site-to-Site IPsec VPNs
![]() WAN replacement is one of the biggest reasons organizations implement IPsec VPNs.
WAN replacement is one of the biggest reasons organizations implement IPsec VPNs.
![]() Up to 40 percent of typical enterprise employees work in branch offices, away from the central sites that provide mission-critical applications and services required for business operations. As these services are extended to branch office employees, requirements increase for bandwidth, security, and high availability.
Up to 40 percent of typical enterprise employees work in branch offices, away from the central sites that provide mission-critical applications and services required for business operations. As these services are extended to branch office employees, requirements increase for bandwidth, security, and high availability.
![]() IPsec VPNs can provide a cost-effective replacement for a private WAN infrastructure. Often the cost of a relatively high-bandwidth IP connection, such as an Internet service provider (ISP) connection, IP VPN service provider connection, or broadband digital subscriber line (DSL) or cable access, is lower than existing or upgraded WAN circuits.
IPsec VPNs can provide a cost-effective replacement for a private WAN infrastructure. Often the cost of a relatively high-bandwidth IP connection, such as an Internet service provider (ISP) connection, IP VPN service provider connection, or broadband digital subscriber line (DSL) or cable access, is lower than existing or upgraded WAN circuits.
![]() Organizations can use IPsec VPNs to connect remote branches or offices, teleworkers, and mobile users to the corporate resources as the central site. Organizations also use IPsec VPNs to provide extranet connectivity for business to business applications.
Organizations can use IPsec VPNs to connect remote branches or offices, teleworkers, and mobile users to the corporate resources as the central site. Organizations also use IPsec VPNs to provide extranet connectivity for business to business applications.
![]() There are four key components of site-to-site VPN:
There are four key components of site-to-site VPN:
-
 Headend VPN devices: Serve as VPN headend termination devices at a central campus
Headend VPN devices: Serve as VPN headend termination devices at a central campus -
 VPN access devices: Serve as VPN branch-end termination devices at branch office locations
VPN access devices: Serve as VPN branch-end termination devices at branch office locations -
 IPsec and generic routing encapsulation (GRE) tunnels: Interconnect the headend and branch-end devices in the VPN
IPsec and generic routing encapsulation (GRE) tunnels: Interconnect the headend and branch-end devices in the VPN -
 Internet services from ISPs: Serve as the WAN interconnection medium
Internet services from ISPs: Serve as the WAN interconnection medium
 WAN Backup Using Site-to-Site IPsec VPNs
WAN Backup Using Site-to-Site IPsec VPNs
![]() Another common business application use for IPsec VPNs is for backing up an existing WAN.
Another common business application use for IPsec VPNs is for backing up an existing WAN.
![]() When a primary network connection malfunctions, the remote branch office can rely on Internet VPN connectivity while waiting for the primary connection to be restored.
When a primary network connection malfunctions, the remote branch office can rely on Internet VPN connectivity while waiting for the primary connection to be restored.
![]() IPsec VPNs over a high-speed ISP connection or broadband cable or DSL access can provide a cost-effective secondary WAN connection for branch offices. Many customers continue to route their most critical traffic across their private WAN circuits, and route higher-bandwidth, less-critical traffic across IPsec VPNs as a secondary connection path. If a failure occurs on their primary WAN circuit, the IPsec VPN can also function as an established backup path.
IPsec VPNs over a high-speed ISP connection or broadband cable or DSL access can provide a cost-effective secondary WAN connection for branch offices. Many customers continue to route their most critical traffic across their private WAN circuits, and route higher-bandwidth, less-critical traffic across IPsec VPNs as a secondary connection path. If a failure occurs on their primary WAN circuit, the IPsec VPN can also function as an established backup path.
| Note |
|
 Regulatory Encryption Using Site-to-Site IPsec VPNs
Regulatory Encryption Using Site-to-Site IPsec VPNs
![]() Another common business application use for IPsec VPNs is for mandatory or regulatory encryption.
Another common business application use for IPsec VPNs is for mandatory or regulatory encryption.
![]() Regulations such as the Health Insurance Portability and Accountability Act (HIPAA), the Sarbanes-Oxley Act (SOX), and the Basel II agreement recommend or mandate the need for companies to implement all reasonable safeguards to protect personal, customer, and corporate information. IPsec VPNs inherently provide a high degree of data privacy through establishment of trust points between communicating devices, and data encryption with the Triple Data Encryption Standard (3DES) or Advanced Encryption Standard (AES).
Regulations such as the Health Insurance Portability and Accountability Act (HIPAA), the Sarbanes-Oxley Act (SOX), and the Basel II agreement recommend or mandate the need for companies to implement all reasonable safeguards to protect personal, customer, and corporate information. IPsec VPNs inherently provide a high degree of data privacy through establishment of trust points between communicating devices, and data encryption with the Triple Data Encryption Standard (3DES) or Advanced Encryption Standard (AES).
![]() Site-to-site VPNs support regulatory constraints and business policies. As network security risks increase and regulatory compliance becomes essential, organizations are using IPsec VPNs to encrypt and protect data such as medical records, corporate or personal financial data, and sensitive information such as legal, police, and academic records, whether a private WAN, IP VPN, or the Internet is used for connectivity.
Site-to-site VPNs support regulatory constraints and business policies. As network security risks increase and regulatory compliance becomes essential, organizations are using IPsec VPNs to encrypt and protect data such as medical records, corporate or personal financial data, and sensitive information such as legal, police, and academic records, whether a private WAN, IP VPN, or the Internet is used for connectivity.
Site-to-Site VPN Design Considerations
![]() The design of site-to-site VPNS is impacted by the organization’s routing and addressing schema. Other important design considerations are the size, scale, and performance expectations for the site-to-site VPN. These requirements drive the selection of and appropriate platform to provision the service. The following section examines these elements and their impact on site-to-site VPN design.
The design of site-to-site VPNS is impacted by the organization’s routing and addressing schema. Other important design considerations are the size, scale, and performance expectations for the site-to-site VPN. These requirements drive the selection of and appropriate platform to provision the service. The following section examines these elements and their impact on site-to-site VPN design.
 IP Addressing and Routing
IP Addressing and Routing
![]() An IPsec VPN is an overlay on an existing IP network.
An IPsec VPN is an overlay on an existing IP network.
![]() The VPN termination devices need routable IP addresses for the outside Internet connection. Private IP addresses can be used on the inside of the VPN. Just as good IP network design supports summarization, the VPN address space needs to be designed to allow for network summarization. NAT may be needed to support overlapping address space between sites in an organization.
The VPN termination devices need routable IP addresses for the outside Internet connection. Private IP addresses can be used on the inside of the VPN. Just as good IP network design supports summarization, the VPN address space needs to be designed to allow for network summarization. NAT may be needed to support overlapping address space between sites in an organization.
![]() Most IPsec VPNs forward data across the network using IPsec tunnel mode, which encapsulates and protects an entire IP packet. Because tunnel mode encapsulates or hides the IP header of the pre-encrypted packet, a new IP header is added so that the packet can be successfully forwarded.
Most IPsec VPNs forward data across the network using IPsec tunnel mode, which encapsulates and protects an entire IP packet. Because tunnel mode encapsulates or hides the IP header of the pre-encrypted packet, a new IP header is added so that the packet can be successfully forwarded.
![]() Many larger enterprise WANs need dynamic routing protocols such as Enhanced Interior Gateway Routing Protocol (EIGRP) and Open Shortest Path First (OSPF) to provide routing and maintain link state and path resiliency. All Interior Gateway Protocol (IGP) routing protocols use either broadcast or IP multicast as a method of transmitting routing table information. However, basic IPsec designs cannot transport IGP dynamic routing protocols or IP multicast traffic. When support for one or more of these features are required, IPsec should be used in conjunction with other technologies such as GRE.
Many larger enterprise WANs need dynamic routing protocols such as Enhanced Interior Gateway Routing Protocol (EIGRP) and Open Shortest Path First (OSPF) to provide routing and maintain link state and path resiliency. All Interior Gateway Protocol (IGP) routing protocols use either broadcast or IP multicast as a method of transmitting routing table information. However, basic IPsec designs cannot transport IGP dynamic routing protocols or IP multicast traffic. When support for one or more of these features are required, IPsec should be used in conjunction with other technologies such as GRE.
 Scaling, Sizing, and Performance
Scaling, Sizing, and Performance
![]() The task of scaling large IPsec VPNs while maintaining performance and high availability is challenging and requires careful planning and design. Many factors affect scalability of an IPsec VPN design, including the number of route sites, access connection speeds, routing peer limits, IPsec encryption engine throughput, features to be supported, and applications that will be transported over the IPsec VPN.
The task of scaling large IPsec VPNs while maintaining performance and high availability is challenging and requires careful planning and design. Many factors affect scalability of an IPsec VPN design, including the number of route sites, access connection speeds, routing peer limits, IPsec encryption engine throughput, features to be supported, and applications that will be transported over the IPsec VPN.
![]() The number of remote sites is a primary factor in determining scalability of a design and affects the routing plan, high-availability design, and ultimately the overall throughput that must be aggregated by the VPN headend routers. Different routers can support different numbers of tunnels.
The number of remote sites is a primary factor in determining scalability of a design and affects the routing plan, high-availability design, and ultimately the overall throughput that must be aggregated by the VPN headend routers. Different routers can support different numbers of tunnels.
![]() IPsec VPN throughput depends on several factors, including connection speeds, capacity of the crypto engine, and CPU limits of the router. An IPsec crypto engine in a Cisco IOS router is a unidirectional device that must process bidirectional packets. Outbound packets must be encrypted by the IPsec crypto engine, and inbound packets must be decrypted by the same device. For each interface having packets encrypted, it is necessary to consider the bidirectional speed of the interface. For example, a T1 connection speed is 1.544 Mb/s, but the IPsec throughput required is 3.088 Mb/s.
IPsec VPN throughput depends on several factors, including connection speeds, capacity of the crypto engine, and CPU limits of the router. An IPsec crypto engine in a Cisco IOS router is a unidirectional device that must process bidirectional packets. Outbound packets must be encrypted by the IPsec crypto engine, and inbound packets must be decrypted by the same device. For each interface having packets encrypted, it is necessary to consider the bidirectional speed of the interface. For example, a T1 connection speed is 1.544 Mb/s, but the IPsec throughput required is 3.088 Mb/s.
![]() Cisco recommends the following practices for VPN device performance limits:
Cisco recommends the following practices for VPN device performance limits:
-
 The redundant headend device should be deployed in a configuration that results in CPU utilization less than 50 percent. The 50 percent target includes all overhead incurred by IPsec and any other enabled features such as firewall, routing, intrusion-detection system (IDS), and logging. This performance limit will allow the headend device to handle failover of the other headend device.
The redundant headend device should be deployed in a configuration that results in CPU utilization less than 50 percent. The 50 percent target includes all overhead incurred by IPsec and any other enabled features such as firewall, routing, intrusion-detection system (IDS), and logging. This performance limit will allow the headend device to handle failover of the other headend device. -
 Because branch devices will need to support fewer additional tunnels in a failover event, branch devices can be deployed in a configuration with less than 65 percent CPU utilization.
Because branch devices will need to support fewer additional tunnels in a failover event, branch devices can be deployed in a configuration with less than 65 percent CPU utilization.
Cisco Router Performance with IPsec VPNs
![]() Because IPsec VPN connections do not normally have a bandwidth associated with them, the overall physical interface connection speeds of both the headend and branch routers largely determine the maximum speeds at which the IPsec VPN must operate. Table 9-1 shows best-case scenarios with minimal features running IPsec VPNs in a lab with 1400-byte packets.
Because IPsec VPN connections do not normally have a bandwidth associated with them, the overall physical interface connection speeds of both the headend and branch routers largely determine the maximum speeds at which the IPsec VPN must operate. Table 9-1 shows best-case scenarios with minimal features running IPsec VPNs in a lab with 1400-byte packets.
|
|
|
|
|
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() However, the packets-per-second (PPS) rate matters more than throughput bandwidth (in bits per second) for the connection speeds being terminated or aggregated. In general, routers and crypto engines have upper boundaries for processing a given number of packets per second. The size of packets used for testing and throughput evaluations can understate or overstate true performance. For example, if a device can support 20 Kb/s, 100-byte packets lead to 16 Mb/s throughput, and 1400-byte packets at the same packet rate lead to 224 Mb/s throughput. Because of such a wide variance in throughput, it is generally better to use packets per second for scalability than bits per second.
However, the packets-per-second (PPS) rate matters more than throughput bandwidth (in bits per second) for the connection speeds being terminated or aggregated. In general, routers and crypto engines have upper boundaries for processing a given number of packets per second. The size of packets used for testing and throughput evaluations can understate or overstate true performance. For example, if a device can support 20 Kb/s, 100-byte packets lead to 16 Mb/s throughput, and 1400-byte packets at the same packet rate lead to 224 Mb/s throughput. Because of such a wide variance in throughput, it is generally better to use packets per second for scalability than bits per second.
![]() Each time a crypto engine encrypts or decrypts a packet, it performs mathematical computations on the IP packet payload using the unique crypto key for the trustpoint, agreed upon by the sender and receiver. If more than one IPsec tunnel is terminated on a router, the router has multiple trust points and therefore multiple crypto keys. When packets are to be sent to or received from a different tunnel from the last packet sent or received, the crypto engine must swap keys to use the right key matched with the trust point. This key swapping can degrade the performance of a crypto engine, depending on its architecture, and increase the router CPU utilization. For some Cisco platforms, such as Cisco 7200VXR series routers with Cisco Service Adapter VPN Acceleration Module 2+ (SA-VAM2+), as the number of tunnels increases, throughput of the IPsec crypto engine decreases. For other Cisco platforms, such as Cisco 7600 series routers with VPN Shared Port Adapter (SPA), performance is relatively linear, with relatively the same throughput for a single tunnel as for 1000 or even 5000 tunnels.
Each time a crypto engine encrypts or decrypts a packet, it performs mathematical computations on the IP packet payload using the unique crypto key for the trustpoint, agreed upon by the sender and receiver. If more than one IPsec tunnel is terminated on a router, the router has multiple trust points and therefore multiple crypto keys. When packets are to be sent to or received from a different tunnel from the last packet sent or received, the crypto engine must swap keys to use the right key matched with the trust point. This key swapping can degrade the performance of a crypto engine, depending on its architecture, and increase the router CPU utilization. For some Cisco platforms, such as Cisco 7200VXR series routers with Cisco Service Adapter VPN Acceleration Module 2+ (SA-VAM2+), as the number of tunnels increases, throughput of the IPsec crypto engine decreases. For other Cisco platforms, such as Cisco 7600 series routers with VPN Shared Port Adapter (SPA), performance is relatively linear, with relatively the same throughput for a single tunnel as for 1000 or even 5000 tunnels.
Cisco Router Security Performance
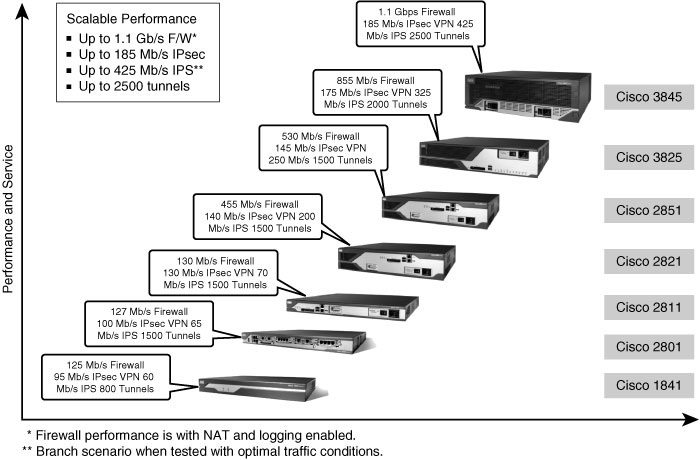
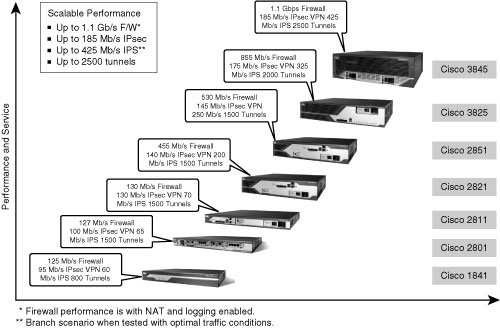
![]() The Cisco Integrated Services Routers (ISR) are built with fast processors and cryptography to support high-performance security features. The Cisco IOS advanced security feature set combines a rich VPN feature set with advanced firewall, intrusion-prevention, and extensive Cisco IOS Software capabilities, including QoS, multiprotocol, multicast, and advanced routing support. The figure shows some best-case performance measures for individual security features. The VPN throughput numbers are with 1400-byte packets and Advanced Integration Module (AIM) acceleration cards installed. Figure 9-4 illustrates the performance metrics associated with the ISR series routers.
The Cisco Integrated Services Routers (ISR) are built with fast processors and cryptography to support high-performance security features. The Cisco IOS advanced security feature set combines a rich VPN feature set with advanced firewall, intrusion-prevention, and extensive Cisco IOS Software capabilities, including QoS, multiprotocol, multicast, and advanced routing support. The figure shows some best-case performance measures for individual security features. The VPN throughput numbers are with 1400-byte packets and Advanced Integration Module (AIM) acceleration cards installed. Figure 9-4 illustrates the performance metrics associated with the ISR series routers.
| Note |
|
Cisco ASA 5500 Series Performance
![]() ASA 5500 series all-in-one Adaptive Security Appliances deliver enterprise-class security and VPN services to small- and medium-size businesses and large enterprise networks in a modular, purpose-built appliance. The ASA 5500 series incorporates a wide range of integrated security services, including firewall, intrusion-prevention system (IPS), and anti-X services with SSL and IPsec VPN services in an easy-to-deploy, high-performance solution. The ASA 5500 series is the most feature-rich solution for SSL and IPsec-based remote access that Cisco offers, and it supports robust site-to-site connectivity. The series provides higher scalability and greater throughput capabilities than the widely deployed Cisco VPN 3000 series concentrators.
ASA 5500 series all-in-one Adaptive Security Appliances deliver enterprise-class security and VPN services to small- and medium-size businesses and large enterprise networks in a modular, purpose-built appliance. The ASA 5500 series incorporates a wide range of integrated security services, including firewall, intrusion-prevention system (IPS), and anti-X services with SSL and IPsec VPN services in an easy-to-deploy, high-performance solution. The ASA 5500 series is the most feature-rich solution for SSL and IPsec-based remote access that Cisco offers, and it supports robust site-to-site connectivity. The series provides higher scalability and greater throughput capabilities than the widely deployed Cisco VPN 3000 series concentrators.
![]() Table 9-2 shows some best-case performance measures for the ASA 5500 series.
Table 9-2 shows some best-case performance measures for the ASA 5500 series.
|
|
|
|
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|
Typical VPN Device Deployments
![]() Table 9-3 shows where Cisco VPN devices are typically deployed.
Table 9-3 shows where Cisco VPN devices are typically deployed.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() The ASA 5500 series supports both IPsec VPNs and SSL-based remote-access VPN services deployments on a single integrated platform. Cisco ISRs and Cisco Catalyst switches support site-to-site IPsec VPNs of any topology, from hub-and-spoke to the more complex fully meshed VPNs on networks of all sizes, integrating security services with extensive Cisco IOS Software capabilities that include QoS, multiprotocol, multicast, and advanced routing support.
The ASA 5500 series supports both IPsec VPNs and SSL-based remote-access VPN services deployments on a single integrated platform. Cisco ISRs and Cisco Catalyst switches support site-to-site IPsec VPNs of any topology, from hub-and-spoke to the more complex fully meshed VPNs on networks of all sizes, integrating security services with extensive Cisco IOS Software capabilities that include QoS, multiprotocol, multicast, and advanced routing support.
 Design Topologies
Design Topologies
![]() A peer-to-peer IPsec VPN provides connectivity between two sites through a tunnel that secures traffic.
A peer-to-peer IPsec VPN provides connectivity between two sites through a tunnel that secures traffic.
![]() Typically, remote peers are connected to the central site over a shared infrastructure in a hub-and-spoke topology with tunnels from the multiple spokes to the headend hub. The hub-and-spoke topology scales well. However, a performance penalty applies because of the two encryption/decryption cycles for spoke-to-spoke traffic.
Typically, remote peers are connected to the central site over a shared infrastructure in a hub-and-spoke topology with tunnels from the multiple spokes to the headend hub. The hub-and-spoke topology scales well. However, a performance penalty applies because of the two encryption/decryption cycles for spoke-to-spoke traffic.
![]() A meshed topology may be the appropriate design to use when there are multiple locations with a large amount of traffic flowing between them. To eliminate the performance penalty due to two encryption/decryption cycles for spoke-to-spoke traffic, a partial-mesh topology can be used. The partial-mesh topology is similar to a hub-and-spoke topology, but it supports some direct spoke-to-spoke connectivity.
A meshed topology may be the appropriate design to use when there are multiple locations with a large amount of traffic flowing between them. To eliminate the performance penalty due to two encryption/decryption cycles for spoke-to-spoke traffic, a partial-mesh topology can be used. The partial-mesh topology is similar to a hub-and-spoke topology, but it supports some direct spoke-to-spoke connectivity.
![]() The full-mesh topology provides direct connectivity between all locations. There are scaling issues as the number of IPsec tunnels needed grows exponentially as number of sites increases. This topology is also more difficult to provision.
The full-mesh topology provides direct connectivity between all locations. There are scaling issues as the number of IPsec tunnels needed grows exponentially as number of sites increases. This topology is also more difficult to provision.
| Note |
|
VPN Device Placement Designs
![]() The following section provides an overview of various design options for placement of VPN devices in the network.
The following section provides an overview of various design options for placement of VPN devices in the network.
 VPN Device Parallel to Firewall
VPN Device Parallel to Firewall
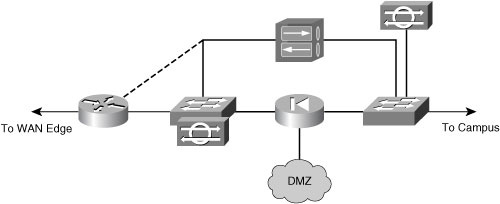
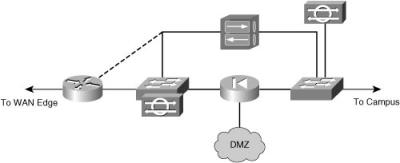
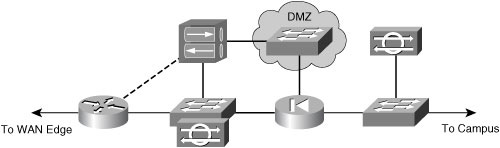
![]() The VPN device can be placed parallel to a firewall in the network, as shown in Figure 9-5.
The VPN device can be placed parallel to a firewall in the network, as shown in Figure 9-5.
![]() There are advantages in placing the VPN device parallel to the firewall:
There are advantages in placing the VPN device parallel to the firewall:
-
 Simplified deployment because firewall addressing does not need to change
Simplified deployment because firewall addressing does not need to change -
 High scalability because multiple VPN devices can be deployed in parallel with the firewall
High scalability because multiple VPN devices can be deployed in parallel with the firewall
![]() There are some disadvantages to placing the VPN device parallel to the firewall:
There are some disadvantages to placing the VPN device parallel to the firewall:
-
 IPsec decrypted traffic is not firewall inspected. This issue is a major concern if the traffic is not subject to a stateful inspection.
IPsec decrypted traffic is not firewall inspected. This issue is a major concern if the traffic is not subject to a stateful inspection. -
 No centralized point of logging or content inspection is implemented.
No centralized point of logging or content inspection is implemented.
 VPN Device on a Firewall DMZ
VPN Device on a Firewall DMZ
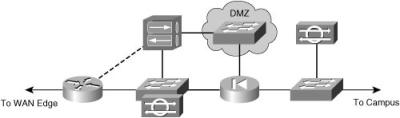
![]() The VPN device can be placed in the demilitarized zone (DMZ) on the firewall in the network, as shown here in Figure 9-6.
The VPN device can be placed in the demilitarized zone (DMZ) on the firewall in the network, as shown here in Figure 9-6.
![]() There are advantages to placing the VPN device in the DMZ of a firewall:
There are advantages to placing the VPN device in the DMZ of a firewall:
-
 The firewall can statefully inspect the decrypted VPN traffic. The design supports the layered security model and enforces firewall security policies.
The firewall can statefully inspect the decrypted VPN traffic. The design supports the layered security model and enforces firewall security policies. -
 The design supports moderate-to-high scalability by adding additional VPN devices. Migration to this design is relatively straightforward with the addition of a LAN interface to firewall.
The design supports moderate-to-high scalability by adding additional VPN devices. Migration to this design is relatively straightforward with the addition of a LAN interface to firewall.
![]() There are disadvantages to placing the VPN device in the DMZ of a firewall:
There are disadvantages to placing the VPN device in the DMZ of a firewall:
-
 The configuration complexity increases because additional configuration on the firewall is required to support the additional interfaces. The firewall must support policy routing to differentiate VPN versus non-VPN traffic.
The configuration complexity increases because additional configuration on the firewall is required to support the additional interfaces. The firewall must support policy routing to differentiate VPN versus non-VPN traffic. -
 The firewall may impose bandwidth restrictions on stacks of VPN devices.
The firewall may impose bandwidth restrictions on stacks of VPN devices.
 Integrated VPN and Firewall
Integrated VPN and Firewall
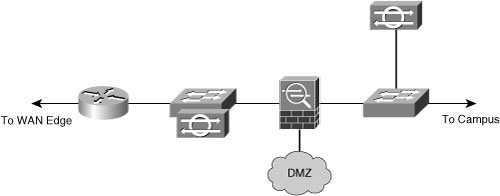
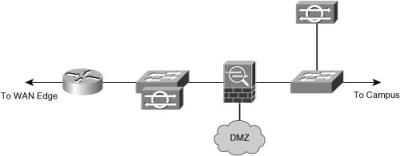
![]() Another option is an integrated VPN and firewall device in the network, as shown in Figure 9-7.
Another option is an integrated VPN and firewall device in the network, as shown in Figure 9-7.
![]() There are advantages to integrating the VPN device and the firewall:
There are advantages to integrating the VPN device and the firewall:
-
 The firewall can statefully inspect the decrypted VPN traffic. The design supports the layered security model and enforces firewall security policies.
The firewall can statefully inspect the decrypted VPN traffic. The design supports the layered security model and enforces firewall security policies. -
 The design may be easier to manage with the same or fewer devices to support.
The design may be easier to manage with the same or fewer devices to support.
![]() There are disadvantages to placing the VPN device in the DMZ of a firewall:
There are disadvantages to placing the VPN device in the DMZ of a firewall:
-
 Scalability can be an issue because a single device must scale to meet the performance requirements of multiple features.
Scalability can be an issue because a single device must scale to meet the performance requirements of multiple features. -
 The configuration complexity increases because all the configurations are applied to one device.
The configuration complexity increases because all the configurations are applied to one device.

2 comments
teamviewer 13 mac:
icecream ebook reader:
resharper license key:
vpn crack latest version:
icecream ebook reader:
s
iOS Training in Chennai
iOS Online Training
iOS Training in Bangalore
iOS Training in Pune
Post a Comment