7-3: Application Inspection
![]() A stateful firewall can easily examine the source and destination parameters of packets passing through it. Many applications use protocols that also embed address or port information inside the packet, requiring special handling for examination.
A stateful firewall can easily examine the source and destination parameters of packets passing through it. Many applications use protocols that also embed address or port information inside the packet, requiring special handling for examination.
![]() Application inspection allows a firewall to dig inside the packets used by certain applications. The firewall can find and use the embedded information in its stateful application layer inspection engines.
Application inspection allows a firewall to dig inside the packets used by certain applications. The firewall can find and use the embedded information in its stateful application layer inspection engines.
![]() Embedded address information can also become confusing when you use NAT. If the packet addresses are being translated, the firewall must also perform the same translation on any corresponding embedded addresses.
Embedded address information can also become confusing when you use NAT. If the packet addresses are being translated, the firewall must also perform the same translation on any corresponding embedded addresses.
![]() Application inspection also monitors any secondary channels or “buddy ports” that are opened as a part of an application connection. Only the primary or well-known port needs to be configured for the application inspection. In addition, only the primary port needs to be permitted in an access list applied to a firewall interface.
Application inspection also monitors any secondary channels or “buddy ports” that are opened as a part of an application connection. Only the primary or well-known port needs to be configured for the application inspection. In addition, only the primary port needs to be permitted in an access list applied to a firewall interface.
![]() This becomes important for inbound connections, where permitted ports must be explicitly configured in the access list. Any secondary connections that are negotiated are tracked, and the appropriate access (additional xlate and conn entries) is added automatically.
This becomes important for inbound connections, where permitted ports must be explicitly configured in the access list. Any secondary connections that are negotiated are tracked, and the appropriate access (additional xlate and conn entries) is added automatically.
![]() To illustrate how this works, consider a simple example with the passive FTP application protocol, as shown in Figure 7-5. An FTP client is located on the outside of a firewall, and the FTP server is inside. The access list applied to the outside interface only permits inbound connections to TCP port 21, the FTP control channel. As soon as the client opens a connection to port 21, the server responds with the port number of the data channel the client should use next.
To illustrate how this works, consider a simple example with the passive FTP application protocol, as shown in Figure 7-5. An FTP client is located on the outside of a firewall, and the FTP server is inside. The access list applied to the outside interface only permits inbound connections to TCP port 21, the FTP control channel. As soon as the client opens a connection to port 21, the server responds with the port number of the data channel the client should use next.
![]() When the client initiates the inbound data connection to the server’s negotiated port number, the firewall does not have an explicit access list statement to permit it. In fact, because the new connection port is negotiated within a previous FTP exchange over the control channel, the port number cannot be known ahead of time. However, the FTP application inspection understands the FTP protocol and listens to the packet exchange between the client and server. The firewall overhears the data channel port negotiation and can automatically create xlate and conn entries for it dynamically.
When the client initiates the inbound data connection to the server’s negotiated port number, the firewall does not have an explicit access list statement to permit it. In fact, because the new connection port is negotiated within a previous FTP exchange over the control channel, the port number cannot be known ahead of time. However, the FTP application inspection understands the FTP protocol and listens to the packet exchange between the client and server. The firewall overhears the data channel port negotiation and can automatically create xlate and conn entries for it dynamically.
![]() In releases before ASA 7.0(1), application inspection is called a fixup. If a fixup is enabled, it is used to examine all traffic passing through the firewall. Beginning with ASA 7.0(1) and FWSM 3.1(1), application inspection is much more flexible. Inspection engines can be used to examine specific types of traffic.
In releases before ASA 7.0(1), application inspection is called a fixup. If a fixup is enabled, it is used to examine all traffic passing through the firewall. Beginning with ASA 7.0(1) and FWSM 3.1(1), application inspection is much more flexible. Inspection engines can be used to examine specific types of traffic.
![]() Table 7-6 lists the applications and well-known ports supported for application inspection on Cisco firewall platforms running PIX software.
Table 7-6 lists the applications and well-known ports supported for application inspection on Cisco firewall platforms running PIX software.
|
|
|
|
|
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 Configuring Application Inspection
Configuring Application Inspection
![]() By default, PIX 6.3 enables only the CU-SeeMe, DNS, FTP, H.323, HTTP, ILS/LDAP, NetBIOS, RSH, RTSP, SIP, SKINNY/SCCP, SMTP, SQL*Net, SunRPC, TFTP, VDO Live, Windows Media, and XDMCP fixups. If the fixup command is configured for an application protocol, then the firewall inspects that traffic with an inspection engine.
By default, PIX 6.3 enables only the CU-SeeMe, DNS, FTP, H.323, HTTP, ILS/LDAP, NetBIOS, RSH, RTSP, SIP, SKINNY/SCCP, SMTP, SQL*Net, SunRPC, TFTP, VDO Live, Windows Media, and XDMCP fixups. If the fixup command is configured for an application protocol, then the firewall inspects that traffic with an inspection engine.
![]() On an ASA or FWSM platform, application inspection occurs only on traffic that has been classified and applied to a policy. When you use the inspect command, as in the following command syntax, only the inspection engine that you specify examines traffic identified by the class map:
On an ASA or FWSM platform, application inspection occurs only on traffic that has been classified and applied to a policy. When you use the inspect command, as in the following command syntax, only the inspection engine that you specify examines traffic identified by the class map:
 Firewall(config-pmap-c)# inspect inspect_name [options]
Firewall(config-pmap-c)# inspect inspect_name [options]![]() As you might imagine, application layer inspection depends heavily on the MPF structure that is described in Section “7-2: Defining Security Policies in a Modular Policy Framework.” Within a single policy map, you can configure Layer 3/4 traffic policies, as well as application layer inspection engine definitions.
As you might imagine, application layer inspection depends heavily on the MPF structure that is described in Section “7-2: Defining Security Policies in a Modular Policy Framework.” Within a single policy map, you can configure Layer 3/4 traffic policies, as well as application layer inspection engine definitions.
![]() As soon as an inspection policy is configured, you can monitor its activity with the following command:
As soon as an inspection policy is configured, you can monitor its activity with the following command:
Firewall# show service-policy
![]() This command displays each active service policy, along with the class map and action breakdown. If inspect commands are configured as part of a service policy, each one is listed, along with counters for packets inspected and dropped and connections reset. The inspection engines configured in the default global policy global_policy are shown in the following example:
This command displays each active service policy, along with the class map and action breakdown. If inspect commands are configured as part of a service policy, each one is listed, along with counters for packets inspected and dropped and connections reset. The inspection engines configured in the default global policy global_policy are shown in the following example:
Firewall# show service-policy
Global policy:
Service-policy: global_policy
Class-map: inspection_default
Inspect: dns maximum-length 512, packet 10, drop 0, reset-drop 0
Inspect: ftp, packet 39, drop 0, reset-drop 0
Inspect: h323 h225, packet 0, drop 0, reset-drop 0
Inspect: h323 ras, packet 0, drop 0, reset-drop 0
Inspect: rsh, packet 0, drop 0, reset-drop 0
Inspect: rtsp, packet 0, drop 0, reset-drop 0
Inspect: esmtp, packet 28, drop 0, reset-drop 0
Inspect: sqlnet, packet 0, drop 0, reset-drop 0
Inspect: skinny, packet 0, drop 0, reset-drop 0
Inspect: sunrpc, packet 0, drop 0, reset-drop 0
Inspect: xdmcp, packet 0, drop 0, reset-drop 0
Inspect: sip, packet 0, drop 0, reset-drop 0
Inspect: netbios, packet 27, drop 0, reset-drop 0
Inspect: tftp, packet 0, drop 0, reset-drop 0
Inspect: icmp error, packet 0, drop 0, reset-drop 0
Inspect: icmp, packet 76800, drop 13628, reset-drop 0
![]() You can configure any of the supported application layer inspection engines by using the configuration command syntax listed in Table 7-7.
You can configure any of the supported application layer inspection engines by using the configuration command syntax listed in Table 7-7.
|
|
| |
|---|---|---|
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
| |
|
|
|
![]() FWSM and ASA (releases 7.0[1] or later) use the inspect command. In releases prior to ASA 7.0(1), the fixup command configures application inspection and default port numbers.
FWSM and ASA (releases 7.0[1] or later) use the inspect command. In releases prior to ASA 7.0(1), the fixup command configures application inspection and default port numbers.
![]() Table 7-7 lists the command syntax to configure each type of inspection engine for ASA, FWSM, and PIX 6.3 platforms. For application inspection engines that are more advanced, refer to the section of this chapter referenced in the table.
Table 7-7 lists the command syntax to configure each type of inspection engine for ASA, FWSM, and PIX 6.3 platforms. For application inspection engines that are more advanced, refer to the section of this chapter referenced in the table.
![]() Notice that none of the ASA or FWSM inspection engine configuration commands accepts a port number. These firewall platforms have a default concept of application port numbers, so you don’t have to define them. Any traffic that is matched by a class map will be processed through the appropriate inspection engine, using the default port number.
Notice that none of the ASA or FWSM inspection engine configuration commands accepts a port number. These firewall platforms have a default concept of application port numbers, so you don’t have to define them. Any traffic that is matched by a class map will be processed through the appropriate inspection engine, using the default port number.
![]() If a nondefault port is needed, traffic must be matched against the nondefault port in a class map and then sent to an inspection engine specified in a policy map.
If a nondefault port is needed, traffic must be matched against the nondefault port in a class map and then sent to an inspection engine specified in a policy map.
![]() In Table 7-7, notice that the inspect command does not accept any port numbers for the case in which the default application port needs to be changed. The default port numbers are defined by the match default-inspection-traffic command, which is configured by default.
In Table 7-7, notice that the inspect command does not accept any port numbers for the case in which the default application port needs to be changed. The default port numbers are defined by the match default-inspection-traffic command, which is configured by default.
![]() You can change the default port by matching traffic based on the new port number and then using a policy to subject that traffic to the inspection engine.
You can change the default port by matching traffic based on the new port number and then using a policy to subject that traffic to the inspection engine.
![]() For example, the inspect http command uses default TCP port 80 for its inspection. If you need to use TCP 8080 instead, use the following commands:
For example, the inspect http command uses default TCP port 80 for its inspection. If you need to use TCP 8080 instead, use the following commands:
Firewall(config)# class-map http_8080
Firewall(config-cmap)# match port tcp eq 8080
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicies
Firewall(config-pmap)# class http_8080
Firewall(config-pmap-c)# inspect http
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicies interface inside
![]() That isn’t to say that once you choose a different port for an inspection engine, the original port cannot still be used. Because the structure of policy maps and class maps is modular, you can add another class-map to match another port. The following example shows a policy-map configuration that uses the HTTP inspection engine to use TCP port 80, as well as TCP port 8080.
That isn’t to say that once you choose a different port for an inspection engine, the original port cannot still be used. Because the structure of policy maps and class maps is modular, you can add another class-map to match another port. The following example shows a policy-map configuration that uses the HTTP inspection engine to use TCP port 80, as well as TCP port 8080.
Firewall(config)# class-map http_8080
Firewall(config-cmap)# match port tcp eq 8080
Firewall(config-cmap)# exit
Firewall(config)# class-map http_80
Firewall(config-cmap)# match port tcp eq 80
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicies
Firewall(config-pmap)# class http_8080
Firewall(config-pmap-c)# inspect http
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# class http_80
Firewall(config-pmap-c)# inspect http
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicies interface inside
![]() As the ASA software releases progress, the MPF continues to get more flexible and versatile. There are now so many pieces to the MPF puzzle that you can become overwhelmed on where to start and how to approach the configuration.
As the ASA software releases progress, the MPF continues to get more flexible and versatile. There are now so many pieces to the MPF puzzle that you can become overwhelmed on where to start and how to approach the configuration.
![]() Figure 7-6 shows the entire range of things you can configure as a part of the MPF structure. As well, dotted lines show how one piece of the MPF is configured and then referenced in another piece. Refer to this figure to keep your bearings as you configure various class maps and policy maps in the remainder of this chapter.
Figure 7-6 shows the entire range of things you can configure as a part of the MPF structure. As well, dotted lines show how one piece of the MPF is configured and then referenced in another piece. Refer to this figure to keep your bearings as you configure various class maps and policy maps in the remainder of this chapter.
Matching Text with Regular Expressions
![]() Beginning with ASA 7.2(1), you can define a regular expression to use when matching text fields in many of the application layer inspection engines. Regular expressions can be defined in two ways:
Beginning with ASA 7.2(1), you can define a regular expression to use when matching text fields in many of the application layer inspection engines. Regular expressions can be defined in two ways:
-
 A single regular expression configured with the following command:
A single regular expression configured with the following command: Firewall(config)# regex regex_name regular_expression
Firewall(config)# regex regex_name regular_expression -
 A group of regular expressions configured as a class map with the following commands:
A group of regular expressions configured as a class map with the following commands: Firewall(config)# class-map type regex match-any regex_cmap_name
Firewall(config)# class-map type regex match-any regex_cmap_name
Firewall(config-cmap)# match regex regex_name The class map consists of one or more match regex commands, each referencing a single regular expression configured with the regex command.
The class map consists of one or more match regex commands, each referencing a single regular expression configured with the regex command.
![]() Within a regex command, you have to define the actual regular expression as a string of up to 100 characters. You can use regular characters in the regular_expression string to match text literally, and you can include special metacharacters to match text in a more abstract way.
Within a regex command, you have to define the actual regular expression as a string of up to 100 characters. You can use regular characters in the regular_expression string to match text literally, and you can include special metacharacters to match text in a more abstract way.
![]() Table 7-8 lists the metacharacters and their functions.
Table 7-8 lists the metacharacters and their functions.
|
|
| |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() As an example of a regular expression configuration, two standalone regex commands are used to match against “cisco.com” and “mysite0.com”, “mysite1.com”, and so on.
As an example of a regular expression configuration, two standalone regex commands are used to match against “cisco.com” and “mysite0.com”, “mysite1.com”, and so on.
Firewall(config)# regex Group1 cisco\.com
Firewall(config)# regex Group2 mysite[0-9]\.com
![]() Suppose you want to apply both of these regular expressions to a policy. You can group them together into a single regex class map with the following commands:
Suppose you want to apply both of these regular expressions to a policy. You can group them together into a single regex class map with the following commands:
Firewall(config)# class-map type regex match-any my_regex_groups
Firewall(config-cmap)# match regex Group1
Firewall(config-cmap)# match regex Group2
Firewall(config-cmap)# exit
![]() Regular expressions can be difficult to formulate, especially when metacharacters are used. You can experiment with a regular expression from the regular EXEC level prompt—without having to make any configuration changes first. Use the following command to test a regular expression:
Regular expressions can be difficult to formulate, especially when metacharacters are used. You can experiment with a regular expression from the regular EXEC level prompt—without having to make any configuration changes first. Use the following command to test a regular expression:
Firewall# test regex input_text regular_expression
![]() Enter some sample input_text, as if the firewall is searching through a URL or some other text field. Enter the regular expression you want to test. If the input text or regular expression contains any spaces, be sure to surround the text string with quotation marks.
Enter some sample input_text, as if the firewall is searching through a URL or some other text field. Enter the regular expression you want to test. If the input text or regular expression contains any spaces, be sure to surround the text string with quotation marks.
![]() The firewall will return the result of the regular expression match. In the following examples, the firewall has announced if the regular expression match has succeeded or failed. Remember that a failed match does not necessarily indicate that your regular expression is incorrect or poorly formed—your regular expression needs correcting only if it produces results that do not match your expectations.
The firewall will return the result of the regular expression match. In the following examples, the firewall has announced if the regular expression match has succeeded or failed. Remember that a failed match does not necessarily indicate that your regular expression is incorrect or poorly formed—your regular expression needs correcting only if it produces results that do not match your expectations.
Firewall# test regex "see the dog run" "dog | cat"
INFO: Regular expression match succeeded.
Firewall# test regex "see the pig run" "dog | cat"
INFO: Regular expression match failed.
Firewall# test regex "the frog is big" "[dfhl]og"
INFO: Regular expression match failed.
Configuring DCERPC Inspection
![]() Distributed Computing Environment Remote Procedure Call (DCERPC) is a Microsoft protocol used by client machines to run software remotely from a server. The clients communicate with an Endpoint Mapper, which sets up secondary connections for the clients to use when they begin remote program execution.
Distributed Computing Environment Remote Procedure Call (DCERPC) is a Microsoft protocol used by client machines to run software remotely from a server. The clients communicate with an Endpoint Mapper, which sets up secondary connections for the clients to use when they begin remote program execution.
![]() Beginning with ASA 7.2(1), you can enable DCERPC inspection with an optional inspection policy map. Use the following steps to configure DCERPC inspection:
Beginning with ASA 7.2(1), you can enable DCERPC inspection with an optional inspection policy map. Use the following steps to configure DCERPC inspection:
-
 (Optional) Define a DCERPC inspection policy map:
(Optional) Define a DCERPC inspection policy map: Firewall(config)# policy-map type inspect dcerpc dcerrpc_pmap_name
Firewall(config)# policy-map type inspect dcerpc dcerrpc_pmap_name -
 Set DCERPC parameters:
Set DCERPC parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode, then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode, then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# timeout
pinhole hh:mm:ss Adjust the pinhole timer; by default, DCERPC pinholes are closed after 2 minutes.
Adjust the pinhole timer; by default, DCERPC pinholes are closed after 2 minutes.

Firewall(config-pmap-p)# endpoint-
mapper [epm-service-only] [lookup-
operation [timeout hh:mm:ss]] Tune the endpoint mapper service: Use epm-service-only to enforce the use of the endpoint mapper service during binding, lookup-operation to enable the lookup function, and timeout to set the timeout value for pinholes created during lookup.
Tune the endpoint mapper service: Use epm-service-only to enforce the use of the endpoint mapper service during binding, lookup-operation to enable the lookup function, and timeout to set the timeout value for pinholes created during lookup. -
 Enable DCERPC inspection:
Enable DCERPC inspection: Firewall(config-pmap-c)# inspect dcerpc [dcerpc_pmap_name]
Firewall(config-pmap-c)# inspect dcerpc [dcerpc_pmap_name] The inspect dcerpc command must be entered as an action in a policy map. If you have configured a DCERPC inspection class map, you can identify it here as dcerpc_pmap_name.
The inspect dcerpc command must be entered as an action in a policy map. If you have configured a DCERPC inspection class map, you can identify it here as dcerpc_pmap_name.
![]() As an example, DCERPC inspection is enabled with a pinhole timeout of 5 minutes. You could use the following commands to accomplish this purpose:
As an example, DCERPC inspection is enabled with a pinhole timeout of 5 minutes. You could use the following commands to accomplish this purpose:
Firewall(config)# policy-map type inspect dcerpc_policy
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# timeout pinhole 0:5:0
!
Firewall(config)# class-map MyClass
Firewall(config-cmap)# match any
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class MyClass
Firewall(config-pmap-c)# inspect dcerpc dcerpc_policy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring DNS Inspection
![]() If DNS inspection is enabled, a firewall will tear down the DNS connection after the first reply from a DNS server is seen. The DNS record is also examined, and the A-record is rewritten according to any address translation stemming from the alias, static, and nat commands. By default, the DNS message length is held to 512 bytes.
If DNS inspection is enabled, a firewall will tear down the DNS connection after the first reply from a DNS server is seen. The DNS record is also examined, and the A-record is rewritten according to any address translation stemming from the alias, static, and nat commands. By default, the DNS message length is held to 512 bytes.
![]() Beginning with ASA 7.2(1), DNS inspection parameters can be defined in an inspection policy map, which is applied to the DNS inspection engine. You can use the following steps to configure DNS inspection:
Beginning with ASA 7.2(1), DNS inspection parameters can be defined in an inspection policy map, which is applied to the DNS inspection engine. You can use the following steps to configure DNS inspection:
-
 (Optional) Define a DNS inspection policy map:
(Optional) Define a DNS inspection policy map: Firewall(config)# policy-map type inspect dns [match-any | match-all] pmap_name
Firewall(config)# policy-map type inspect dns [match-any | match-all] pmap_name By default, the policy map matches the first condition found, if multiple match commands are configured. This is the same as giving the match-any keyword. You can use the match-all keyword instead, to require that every match command is met.
By default, the policy map matches the first condition found, if multiple match commands are configured. This is the same as giving the match-any keyword. You can use the match-all keyword instead, to require that every match command is met. -
 Define matching conditions and their actions:
Define matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
dns-class {eq value | IN} | {range min
max}}
Firewall(config-pmap-c)# {drop |
drop-connection | enforce-tsig}
[log] Match: DNS class as a value (0–65535) or IN or a range.
Match: DNS class as a value (0–65535) or IN or a range. Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional.
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
dns-type {eq value} | {range min
max}}
Firewall(config-pmap-c)# {drop |
drop-connection | enforce-tsig}
[log] Match: DNS query or resource record type. Type value can be 0–65535 or one of the following keywords: A (IPv4 address record), AXFR (zone transfer), CNAME (canonical name), IXFR (incremental transfer), NS (authoritative name server), SOA (start of authority), TSIG (transaction signature). Type can also be a range of values.
Match: DNS query or resource record type. Type value can be 0–65535 or one of the following keywords: A (IPv4 address record), AXFR (zone transfer), CNAME (canonical name), IXFR (incremental transfer), NS (authoritative name server), SOA (start of authority), TSIG (transaction signature). Type can also be a range of values. Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional. Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
domain-name regex {regex | class
regex_class_name}
Firewall(config-pmap-c)# {drop |
drop-connection | enforce-tsig}
[log] Match: Domain name, as a regular expression.
Match: Domain name, as a regular expression. Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, enforce a TSIG resource record; log optional.
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
header-flag value
Firewall(config-pmap-c)# {drop |
drop-connection | mask | enforce-
tsig} [log] Match: Header flag, a hex value 0x0-0xffff or one of the following keywords: AA (authoritative answer), QR (query), RA (recursion available), RD (recursion desired), or TC (truncation).
Match: Header flag, a hex value 0x0-0xffff or one of the following keywords: AA (authoritative answer), QR (query), RA (recursion available), RD (recursion desired), or TC (truncation). Action: Drop the packet, drop or reset the connection, mask the header flag, or enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, mask the header flag, or enforce a TSIG resource record; log optional.
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
question
Firewall(config-pmap-c)# {drop |
drop-connection | enforce-tsig}
[log] Match: DNS question field.
Match: DNS question field. Action: Drop the packet, drop or reset the connection, or enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, or enforce a TSIG resource record; log optional.
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
resource-record {additional | answer
| authority}
Firewall(config-pmap-c)# {drop |
drop-connection | enforce-tsig}
[log] Match: DNS resource record type.
Match: DNS resource record type. Action: Drop the packet, drop or reset the connection, or enforce a TSIG resource record; log optional.
Action: Drop the packet, drop or reset the connection, or enforce a TSIG resource record; log optional. As well, you can configure a DNS inspection class map with the class-map type inspection dns dns_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple DNS inspection policies.
As well, you can configure a DNS inspection class map with the class-map type inspection dns dns_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple DNS inspection policies. Then you can reference the inspection class map in the inspection policy map with the following command:
Then you can reference the inspection class map in the inspection policy map with the following command: Firewall(config-pmap)# class dns_cmap_name
Firewall(config-pmap)# class dns_cmap_name By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again.
By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again. -
 Set DNS parameters:
Set DNS parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# dns-guard Enable the DNS Guard feature (enabled by default).
Enable the DNS Guard feature (enabled by default).

Firewall(config-pmap-p)# id-mismatch
{count number seconds} action log Log when ID mismatches occur over a threshold of number in seconds (default 30 in 3 seconds).
Log when ID mismatches occur over a threshold of number in seconds (default 30 in 3 seconds).
 Firewall(config-pmap-p)# id-
Firewall(config-pmap-p)# id-
randomization Randomize the DNS identifier to help prevent DNS poisoning attacks; by default, the DNS identifier field is passed through the firewall unchanged.
Randomize the DNS identifier to help prevent DNS poisoning attacks; by default, the DNS identifier field is passed through the firewall unchanged.

Firewall(config-pmap-p)# message-
length maximum {max_length | {client
max_length [auto]} | {server
max_length [auto]}} Set the maximum DNS message size globally as max_length (512-65535 bytes) or for the client or the server.
Set the maximum DNS message size globally as max_length (512-65535 bytes) or for the client or the server.

Firewall(config-pmap-p)# nat-
rewrite Rewrite the A record according to NAT (the default)
Rewrite the A record according to NAT (the default)

Firewall(config-pmap-p)# protocol-
enforcement Examine DNS messages for strict protocol checks (the default)
Examine DNS messages for strict protocol checks (the default)

Firewall(config-pmap-p)# tsig
enforced action [drop] log Require TSIG resource records; if they are not found in DNS messages, a log message is generated. Add drop to drop the messages, too.
Require TSIG resource records; if they are not found in DNS messages, a log message is generated. Add drop to drop the messages, too. -
 Enable DNS inspection:
Enable DNS inspection: Firewall(config-pmap-c)# inspect dns [dns_pmap_name]
Firewall(config-pmap-c)# inspect dns [dns_pmap_name] The inspect dns command must be entered as an action in a policy map. You can also apply a DNS inspection policy map by giving its name pmap_name.
The inspect dns command must be entered as an action in a policy map. You can also apply a DNS inspection policy map by giving its name pmap_name.
![]() As an example, a DNS inspection policy map is configured to match zone transfer requests and to drop and log them. The inspection engine is also configured to randomize the ID field. The following commands can be used to configure DNS inspection:
As an example, a DNS inspection policy map is configured to match zone transfer requests and to drop and log them. The inspection engine is also configured to randomize the ID field. The following commands can be used to configure DNS inspection:
Firewall(config)# policy-map type inspect dns match-any MyDNSPolicy
Firewall(config-pmap)# match dns-type eq AXFR
Firewall(config-pmap-c)# drop log
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# id-randomization
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect dns MyDNSPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring ESMTP Inspection
![]() ESMTP inspection can be used to detect a variety of suspicious email activity. As well, it can block specific senders, receivers, and attempts at mail relay.
ESMTP inspection can be used to detect a variety of suspicious email activity. As well, it can block specific senders, receivers, and attempts at mail relay.
![]() Beginning with ASA 7.2(1), ESMTP inspection parameters can be defined in an inspection policy map, which is applied to the ESMTP inspection engine. You can use the following steps to configure ESMTP inspection:
Beginning with ASA 7.2(1), ESMTP inspection parameters can be defined in an inspection policy map, which is applied to the ESMTP inspection engine. You can use the following steps to configure ESMTP inspection:
-
 (Optional) Define an ESMTP inspection policy map:
(Optional) Define an ESMTP inspection policy map: Firewall(config)# policy-map type inspect esmtp esmtp_pmap_name
Firewall(config)# policy-map type inspect esmtp esmtp_pmap_name -
 Define any matching conditions and their actions:
Define any matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description

Firewall(config-pmap)# match [not] body
{length gt length} | {line gt length}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: Mail message body length (length) or line length (line, 1–998 characters).
Match: Mail message body length (length) or line length (line, 1–998 characters). Action: Drop or reset the connection; log optional.
Action: Drop or reset the connection; log optional.

Firewall(config-pmap)# match [not] cmd
{{RCPT count gt number} | {line length gt
length} | {verb verb}}
Firewall(config-pmap-c)# {drop-
connection | reset | rate-limit rate |
mask} [log] Match: ESMTP command; RCPT number is number of recipients (1–10,000), line length (1–998 characters), verb is one of the following ESMTP verbs: AUTH, DATA, EHLO, ETRN, HELO, HELP, MAIL, NOOP, QUIT, RCPT, RSET, SAML, SOML, or VRFY.
Match: ESMTP command; RCPT number is number of recipients (1–10,000), line length (1–998 characters), verb is one of the following ESMTP verbs: AUTH, DATA, EHLO, ETRN, HELO, HELP, MAIL, NOOP, QUIT, RCPT, RSET, SAML, SOML, or VRFY. Action: Drop or reset the connection, rate limit the messages to rate messages per second, mask the message; log optional.
Action: Drop or reset the connection, rate limit the messages to rate messages per second, mask the message; log optional.

Firewall(config-pmap)# match [not] ehlo-
reply-parameter {8bitmime | auth |
binarymime | checkpoint | dsn | ecode | etrn
| others | pipelining | size | vrfy}
Firewall(config-pmap-c)# {drop-
connection | reset | mask} [log] Match: EHLO reply parameter.
Match: EHLO reply parameter. Action: Drop or reset the connection or mask the message; log optional.
Action: Drop or reset the connection or mask the message; log optional.

Firewall(config-pmap)# match [not]
header {{length gt length} | {line length
gt length} | {to-fields count count}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: Mail message header length, line count (1–998 characters), or the number of To: fields (1–10,000).
Match: Mail message header length, line count (1–998 characters), or the number of To: fields (1–10,000). Action: Drop or reset the connection; log optional.
Action: Drop or reset the connection; log optional.

Firewall(config-pmap)# match [not]
invalid-recipients count gt count
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: Maximum number of 5xx error messages from invalid recipients; count (1–1000 recipients).
Match: Maximum number of 5xx error messages from invalid recipients; count (1–1000 recipients). Action: Drop or reset the connection; log optional.
Action: Drop or reset the connection; log optional.
Firewall(config-pmap)# match [not] mime
{encoding {7bit | 8bit | base64 | binary |
others | quoted-printable}} | {filename
length gt length} | {filetype regex {regex | class regex_cmap_name}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: MIME encoding type, filename length (1–1000 characters), or filetype (regular expression).
Match: MIME encoding type, filename length (1–1000 characters), or filetype (regular expression). Action: Drop or reset the connection; log optional.
Action: Drop or reset the connection; log optional.

Firewall(config-pmap)# match [not]
sender-address {{length gt length} |
{regex {regex | class regex_cmap_name}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: Sender address length (1–1000 characters) or content (regular expression).
Match: Sender address length (1–1000 characters) or content (regular expression). Action: Drop or reset the connection; log optional.
Action: Drop or reset the connection; log optional. -
 Set ESMTP parameters:
Set ESMTP parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode, then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode, then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# mail-relay
domain_name action [drop-connection] log For a mail relay using the domain name, either drop the connection and/or log.
For a mail relay using the domain name, either drop the connection and/or log.
 Firewall(config-pmap-p)# mask-banner
Firewall(config-pmap-p)# mask-banner Mask or obfuscate the mail server banner.
Mask or obfuscate the mail server banner.

Firewall(config-pmap-p)# special-
character action [drop-connection] log If special characters pipe (|), back quote (′), or NUL are present in the sender or receiver address, drop the connection and/or log.
If special characters pipe (|), back quote (′), or NUL are present in the sender or receiver address, drop the connection and/or log. -
 Enable ESMTP inspection:
Enable ESMTP inspection: Firewall(config-pmap-c)# inspect esmtp [esmtp_pmap_name]
Firewall(config-pmap-c)# inspect esmtp [esmtp_pmap_name] The inspect esmtp command must be entered as an action in a policy map. You can also apply an ESMTP inspection policy map by giving its name esmtp_pmap_name.
The inspect esmtp command must be entered as an action in a policy map. You can also apply an ESMTP inspection policy map by giving its name esmtp_pmap_name.
![]() As an example, an ESMTP application inspection policy map is configured to reset and log connections when more than 100 email recipients are given in a message.
As an example, an ESMTP application inspection policy map is configured to reset and log connections when more than 100 email recipients are given in a message.
![]() As well, the security policies prevent anyone from sending email using an address that is outside the domain name “mycompany.com.” A regular expression PermittedSenders is configured to match against email addresses containing “@mycompany.com”. The policy map matches against any sender address that does not contain the regular expression. Connections attempting to send to those addresses are simply reset and logged.
As well, the security policies prevent anyone from sending email using an address that is outside the domain name “mycompany.com.” A regular expression PermittedSenders is configured to match against email addresses containing “@mycompany.com”. The policy map matches against any sender address that does not contain the regular expression. Connections attempting to send to those addresses are simply reset and logged.
![]() Finally, any connections attempting to use a mail relay in the domain “mycompany.com” will be dropped and logged.
Finally, any connections attempting to use a mail relay in the domain “mycompany.com” will be dropped and logged.
![]() The following configuration commands can be used to configure these ESMTP inspection policies:
The following configuration commands can be used to configure these ESMTP inspection policies:
Firewall(config)# regex PermittedSenders "@mycompany.com"
Firewall(config)# policy-map type inspect esmtp MyESMTPPolicy
Firewall(config-pmap)# match cmd RCPT count gt 100
Firewall(config-pmap-c)# reset log
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# match not sender-address regex PermittedSenders
Firewall(config-pmap-c)# reset log
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# mail-relay mycompany.com action drop-connection log
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect esmtp MyESMTPPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring FTP Inspection—ASA 7.2(1) or Later
![]() FTP can be used to exchange files between a client and a server. FTP is defined in RFC 959. By default, the regular FTP inspection engine maintains any secondary connections negotiated by FTP clients and servers. FTP commands and responses are also tracked.
FTP can be used to exchange files between a client and a server. FTP is defined in RFC 959. By default, the regular FTP inspection engine maintains any secondary connections negotiated by FTP clients and servers. FTP commands and responses are also tracked.
![]() You can use the following steps to configure FTP inspection in ASA 7.2(1) or later:
You can use the following steps to configure FTP inspection in ASA 7.2(1) or later:
-
 (Optional) Define an FTP inspection policy map:
(Optional) Define an FTP inspection policy map: Firewall(config)# policy-map type inspect ftp ftp_pmap_name
Firewall(config)# policy-map type inspect ftp ftp_pmap_name -
 (Optional) Define any matching conditions and their actions:
(Optional) Define any matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description

Firewall(config-pmap)# match [not]
filename regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# reset Match: Filename with regular expression
Match: Filename with regular expression Action: Reset the connection
Action: Reset the connection

Firewall(config-pmap)# match [not]
filetype regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# reset Match: File type with a regular expression
Match: File type with a regular expression Action: Reset the connection
Action: Reset the connection

Firewall(config-pmap)# match [not]
server regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# reset Match: Server banner information with a regular expression
Match: Server banner information with a regular expression Action: Reset the connection
Action: Reset the connection
Firewall(config-pmap)# match [not]
username regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# reset Match: Username with a regular expression
Match: Username with a regular expression Action: Reset the connection
Action: Reset the connection

Firewall(config-pmap)# match [not]
request-command command1 [command2]
...[commandn]
Firewall(config-pmap-c)# reset Match: One or more FTP commands, from the following list: appe (append to a file), cdup (change to the parent directory), dele (delete a file on the server), get (get a file), help (get server help), mkd (create a directory), put (put a file), rmd (remove a directory), rnfr (rename from), rnto (rename to), site (server specific command), or stou (store a file with a unique name). Specify multiple commands by separating them with spaces.
Match: One or more FTP commands, from the following list: appe (append to a file), cdup (change to the parent directory), dele (delete a file on the server), get (get a file), help (get server help), mkd (create a directory), put (put a file), rmd (remove a directory), rnfr (rename from), rnto (rename to), site (server specific command), or stou (store a file with a unique name). Specify multiple commands by separating them with spaces. Action: Reset the connection
Action: Reset the connection As well, you can configure an FTP inspection class map with the class-map type inspection ftp ftp_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple FTP inspection policies.
As well, you can configure an FTP inspection class map with the class-map type inspection ftp ftp_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple FTP inspection policies. Then you can reference the inspection class map in the inspection policy map with the following command:
Then you can reference the inspection class map in the inspection policy map with the following command: Firewall(config-pmap)# class ftp_cmap_name
Firewall(config-pmap)# class ftp_cmap_name By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again.
By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again. -
 Set FTP parameters:
Set FTP parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the following commands:
First, enter the parameters mode and then configure one or more parameters with the following commands: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description
 Firewall(config-pmap-p)# mask-banner
Firewall(config-pmap-p)# mask-banner Mask or obfuscate the server banner
Mask or obfuscate the server banner
 Firewall(config-pmap-p)# mask-syst-reply
Firewall(config-pmap-p)# mask-syst-reply Hide the server response from the clients
Hide the server response from the clients -
 Enable FTP inspection:
Enable FTP inspection: Firewall(config-pmap-c)# inspect ftp [ftp_pmap_name]
Firewall(config-pmap-c)# inspect ftp [ftp_pmap_name] The inspect ftp command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as ftp_pmap_name.
The inspect ftp command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as ftp_pmap_name.
![]() As an example, an FTP inspection policy map is configured to reset any connection where the client attempts to use any FTP command other than the read-only CDUP, GET, and HELP commands. As well, the inspection engine will mask any FTP server’s banner so that clients cannot glean any details about the server from it. The following commands can be used to configure the FTP inspection policies:
As an example, an FTP inspection policy map is configured to reset any connection where the client attempts to use any FTP command other than the read-only CDUP, GET, and HELP commands. As well, the inspection engine will mask any FTP server’s banner so that clients cannot glean any details about the server from it. The following commands can be used to configure the FTP inspection policies:
Firewall(config)# policy-map type inspect ftp MyFTPPolicy
Firewall(config-pmap)# match not request-command cdup get help
Firewall(config-pmap-c)# reset
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# mask-banner
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect ftp MyFTPPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring FTP Inspection—FWSM and ASA 7.0-7.1
![]() For ASA releases prior to 7.2(1) and FWSM, you can use the following commands to configure FTP inspection and an FTP map:
For ASA releases prior to 7.2(1) and FWSM, you can use the following commands to configure FTP inspection and an FTP map:
-
 Define the FTP map name:
Define the FTP map name: Firewall(config)# ftp-map ftp_map_name
Firewall(config)# ftp-map ftp_map_name The FTP map is named ftp_map_name (up to 64 characters).
The FTP map is named ftp_map_name (up to 64 characters). -
 (Optional) Deny specific FTP request commands:
(Optional) Deny specific FTP request commands: Firewall(config-ftp-map)# deny-request-cmd request_list
Firewall(config-ftp-map)# deny-request-cmd request_list The firewall drops FTP commands listed in request_list before they reach the server. You can list one or more of the following FTP command keywords, separated by spaces: appe (append to a file), cdup (change to the parent directory), dele (delete a file), get (retrieve a file), help (get help from the FTP server), mkd (make a new directory), put (store a file), rmd (remove a directory), rnfr (rename a file from), rnto (rename a file to), site (a server-specific command), or stou (store a file with a unique name).
The firewall drops FTP commands listed in request_list before they reach the server. You can list one or more of the following FTP command keywords, separated by spaces: appe (append to a file), cdup (change to the parent directory), dele (delete a file), get (retrieve a file), help (get help from the FTP server), mkd (make a new directory), put (store a file), rmd (remove a directory), rnfr (rename a file from), rnto (rename a file to), site (a server-specific command), or stou (store a file with a unique name). -
 (Optional) Mask the reply to a syst command:
(Optional) Mask the reply to a syst command: Firewall(config-ftp-map)# mask-syst-reply
Firewall(config-ftp-map)# mask-syst-reply An FTP client can send the syst command to find out which operating system the FTP server uses. When the mask-syst-reply command is used, the firewall masks the server’s reply with Xs so that the information remains hidden.
An FTP client can send the syst command to find out which operating system the FTP server uses. When the mask-syst-reply command is used, the firewall masks the server’s reply with Xs so that the information remains hidden. -
 Enable the FTP inspection engine
Enable the FTP inspection engine Firewall(config-pmap-c)# inspect ftp [strict [ftp_map_name]]
Firewall(config-pmap-c)# inspect ftp [strict [ftp_map_name]] With the strict keyword, FTP connections will be inspected for compliance with the RFC. If you defined an FTP map, it can be applied here as ftp_map_name.
With the strict keyword, FTP connections will be inspected for compliance with the RFC. If you defined an FTP map, it can be applied here as ftp_map_name.
![]() As an example, suppose FTP inspection is configured to deny any FTP command operation that would alter files or directories on the FTP server. You could use the following commands to accomplish this purpose:
As an example, suppose FTP inspection is configured to deny any FTP command operation that would alter files or directories on the FTP server. You could use the following commands to accomplish this purpose:
Firewall(config)# ftp-map MyFTPfilter
Firewall(config-ftp-map)# deny-request-cmd appe dele mkd put rmd rnfr rnto stou
Firewall(config-ftp-map)# exit
!
Firewall(config)# class-map _MyClass
Firewall(config-cmap)# match any
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class MyClass
Firewall(config-pmap-c)# inspect ftp strict MyFTPfilter
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring GTP Inspection—ASA 7.2(1) and Later
![]() GPRS Tunneling Protocol (GTP) is used to tunnel multiprotocol packets through a General Packet Radio Service (GPRS) network between different GPRS Support Nodes (GSN).
GPRS Tunneling Protocol (GTP) is used to tunnel multiprotocol packets through a General Packet Radio Service (GPRS) network between different GPRS Support Nodes (GSN).
![]() Beginning with ASA 7.2(1), you can enable GTP inspection with an optional inspection policy map. Use the following steps to configure GTP inspection:
Beginning with ASA 7.2(1), you can enable GTP inspection with an optional inspection policy map. Use the following steps to configure GTP inspection:
-
 (Optional) Define a GTP inspection policy map:
(Optional) Define a GTP inspection policy map: Firewall(config)# policy-map type inspect gtp gtp_pmap_name
Firewall(config)# policy-map type inspect gtp gtp_pmap_name -
 Define matching conditions and their actions:
Define matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description
 Firewall(config-pmap)# match [not]
Firewall(config-pmap)# match [not]
apn regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop | drop-
connection | reset} [log] Match: Access point name using regular expression.
Match: Access point name using regular expression. Action: Drop the packet, drop or reset the connection; log optional.
Action: Drop the packet, drop or reset the connection; log optional.

Firewall(config-pmap)# match
[not]message id {message_id | range
low high}
Firewall(config-pmap-c)# {drop | drop-
connection | reset} [log] Match: GTP message ID as a value or range of values 1–255.
Match: GTP message ID as a value or range of values 1–255. Action: Drop the packet, drop or reset the connection; log optional.
Action: Drop the packet, drop or reset the connection; log optional.
Firewall(config-pmap)# match [not]
message length min min_length max
max_length
Firewall(config-pmap-c)# {drop | drop-
connection | reset}} [log] Match: GTP message length within a range; min_length and max_length are 1–65535; length is GTP header plus body.
Match: GTP message length within a range; min_length and max_length are 1–65535; length is GTP header plus body. Action: Drop the packet, drop or reset the connection; log optional.
Action: Drop the packet, drop or reset the connection; log optional.

Firewall(config-pmap)# match [not]
version {version_id | low high}
Firewall(config-pmap-c)# {drop | drop-
connection | reset}} [log] Match: GTP message version as a value (0–255) or range.
Match: GTP message version as a value (0–255) or range. Action: Drop the packet, drop or reset the connection; log optional.
Action: Drop the packet, drop or reset the connection; log optional. -
 Set GTP parameters:
Set GTP parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description
 Firewall(config-pmap-p)# permit errors
Firewall(config-pmap-p)# permit errors Allow invalid GTP packets.
Allow invalid GTP packets.

Firewall(config-pmap-p)# permit
response to-object-group
to_obj_group_id from-object-group
from_obj_group_id Allow GTP responses from GSNs other than the original target, if GSNs are operating as a pool. A pool is defined in a network object group (object-group network obj_group_id).
Allow GTP responses from GSNs other than the original target, if GSNs are operating as a pool. A pool is defined in a network object group (object-group network obj_group_id).

Firewall(config-pmap-p)# request-queue
max_requests Set the maximum number (default 200) of GTP requests that will be queued while waiting for a response.
Set the maximum number (default 200) of GTP requests that will be queued while waiting for a response.

Firewall(config-pmap-p)# timeout {gsn |
pdp-context | request | signaling | t3-
response | tunnel} hh:mm:ss Set the inactivity timers as gsn (inactivity time before a GSN is removed), pdp-context (maximum time to begin receiving PDP context), request (maximum time to begin receiving a GTP message), signaling (inactivity time before GTP signaling is removed), t3-response (maximum wait time for a response before GTP connection is removed), or tunnel (inactivity time before GTP tunnel is torn down).
Set the inactivity timers as gsn (inactivity time before a GSN is removed), pdp-context (maximum time to begin receiving PDP context), request (maximum time to begin receiving a GTP message), signaling (inactivity time before GTP signaling is removed), t3-response (maximum wait time for a response before GTP connection is removed), or tunnel (inactivity time before GTP tunnel is torn down).

Firewall(config-pmap-p)# tunnel-limit
max_tunnels Set the maximum number of active GTP tunnels.
Set the maximum number of active GTP tunnels. -
 Enable GTP inspection:
Enable GTP inspection: Firewall(config-pmap-c)# inspect gtp [gtp_pmap_name]
Firewall(config-pmap-c)# inspect gtp [gtp_pmap_name] The inspect gtp command must be entered as an action in a policy map. If you have configured a GTP inspection class map, you can identify it here as gtp_pmap_name.
The inspect gtp command must be entered as an action in a policy map. If you have configured a GTP inspection class map, you can identify it here as gtp_pmap_name.
![]() As an example, a GTP inspection policy map is configured to drop connections that have GTP messages other than a minimum length of 1 and maximum length of 2048. A GTP tunnel limit of 100 is also enforced. The following commands can be used to configure the GTP policies:
As an example, a GTP inspection policy map is configured to drop connections that have GTP messages other than a minimum length of 1 and maximum length of 2048. A GTP tunnel limit of 100 is also enforced. The following commands can be used to configure the GTP policies:
Firewall(config)# policy-map type inspect gtp MyGTPPolicy
Firewall(config-pmap)# match not message length min 1 max 2048
Firewall(config-pmap-c)# drop-connection
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# tunnel-limit 100
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect gtp MyGTPPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring GTP Inspection—FWSM and ASA 7.0-7.1
![]() GPRS Tunneling Protocol (GTP) is used to tunnel multiprotocol packets through a General Packet Radio Service (GPRS) network between different GPRS Support Nodes (GSN).
GPRS Tunneling Protocol (GTP) is used to tunnel multiprotocol packets through a General Packet Radio Service (GPRS) network between different GPRS Support Nodes (GSN).
![]() Follow these steps to configure a GTP map for use with the inspect gtp command:
Follow these steps to configure a GTP map for use with the inspect gtp command:
-
 Define the GTP map name:
Define the GTP map name: Firewall(config)# gtp-map gtp_map_name
Firewall(config)# gtp-map gtp_map_name The GTP map is named gtp_map_name (up to 64 characters). You must apply the GTP map in a policy map with the following command before it can be used:
The GTP map is named gtp_map_name (up to 64 characters). You must apply the GTP map in a policy map with the following command before it can be used:
inspect gtp gtp_map_name -
 (Optional) Add a GTP map description:
(Optional) Add a GTP map description: Firewall(config-gtpmap)# description string
Firewall(config-gtpmap)# description string You can add an arbitrary text string (up to 200 characters) as a description of the GTP map.
You can add an arbitrary text string (up to 200 characters) as a description of the GTP map. -
 Customize GTP options.
Customize GTP options. You can use any of the commands listed in Table 7-9 to set a specific GTP inspection parameter in GTP map configuration mode.
You can use any of the commands listed in Table 7-9 to set a specific GTP inspection parameter in GTP map configuration mode.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() For example, the following commands configure a GTP map that allows GTP packets only from Mobile Country Code 310, Mobile Network Codes 001 and 002. All others are dropped. In addition, GTP messages must be between 1 and 2048 bytes in length. Up to 100 GTP tunnels are allowed to pass through the firewall. The GTP map is then applied to the inspect gtp command as part of a policy map.
For example, the following commands configure a GTP map that allows GTP packets only from Mobile Country Code 310, Mobile Network Codes 001 and 002. All others are dropped. In addition, GTP messages must be between 1 and 2048 bytes in length. Up to 100 GTP tunnels are allowed to pass through the firewall. The GTP map is then applied to the inspect gtp command as part of a policy map.
Firewall(config)# gtp-map Secure_gtp
Firewall(config-gtp-map)# mcc 310 mnc 001
Firewall(config-gtp-map)# mcc 310 mnc 002
Firewall(config-gtp-map)# message-length min 1 max 2048
Firewall(config-gtp-map)# tunnel-limit 100
Firewall(config-gtp-map)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect gtp Secure_gtp
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring H.323 Inspection
![]() Beginning in ASA 7.2(1), you can configure an H.323 application layer inspection engine. This feature tracks H.323 connections, as well as the subsequent H.245 and RTP port numbers and traffic flows.
Beginning in ASA 7.2(1), you can configure an H.323 application layer inspection engine. This feature tracks H.323 connections, as well as the subsequent H.245 and RTP port numbers and traffic flows.
![]() You can use the following steps to configure H.323 inspection:
You can use the following steps to configure H.323 inspection:
-
 (Optional) Define an H.323 inspection policy map:
(Optional) Define an H.323 inspection policy map: Firewall(config)# policy-map type inspect h323 h323_pmap_name
Firewall(config)# policy-map type inspect h323 h323_pmap_name -
 (Optional) Define any matching conditions and their actions:
(Optional) Define any matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description

Firewall(config-pmap)# match [not]
called-party regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop | drop-
connection | reset} Match: Called party.
Match: Called party. Action: Drop the packet, drop the connection, or reset the connection
Action: Drop the packet, drop the connection, or reset the connection

Firewall(config-pmap)# match [not]
calling-party regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop | drop-
connection | reset} Match: Calling party.
Match: Calling party. Action: Drop the packet, drop the connection, or reset the connection
Action: Drop the packet, drop the connection, or reset the connection

Firewall(config-pmap)# match media-type
{audio | video | data}
Firewall(config-pmap-c)# drop Match: Media type
Match: Media type Action: Drop the packet
Action: Drop the packet As well, you can configure an H.323 inspection class map with the class-map type inspection h323 h323_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple H.323 inspection policies.
As well, you can configure an H.323 inspection class map with the class-map type inspection h323 h323_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple H.323 inspection policies. Then you can reference the inspection class map in the inspection policy map with the following command:
Then you can reference the inspection class map in the inspection policy map with the following command: Firewall(config-pmap)# class h323_cmap_name
Firewall(config-pmap)# class h323_cmap_name By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again.
By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again. -
 Set H.323 parameters:
Set H.323 parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the following commands:
First, enter the parameters mode and then configure one or more parameters with the following commands: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# call-duration-
limit {hh:mm:ss | 0} Set the call duration time limit or 0 for no limit
Set the call duration time limit or 0 for no limit

Firewall(config-pmap-p)# call-party-
numbers Enforce sending call party numbers during the call setup
Enforce sending call party numbers during the call setup

Firewall(config-pmap-p)# h245-tunnel-
block action {drop-connection |log} When an H.245 tunnel is detected, either drop the connection or generate a log
When an H.245 tunnel is detected, either drop the connection or generate a log

Firewall(config-pmap-p)# hsi-group group Set the HSI group number
Set the HSI group number
Firewall(config-pmap-p)# rtp-conformance
[enforce-payloadtype] Make sure pinhole RTP packets conform to the RFC; use enforce-payloadtype to enforce audio or video, according to signaling
Make sure pinhole RTP packets conform to the RFC; use enforce-payloadtype to enforce audio or video, according to signaling
 Firewall(config-pmap-p)# state-checking
Firewall(config-pmap-p)# state-checking Check the state of H.323 connections
Check the state of H.323 connections -
 Enable H.323 inspection:
Enable H.323 inspection: Firewall(config-pmap-c)# inspect h323 [h323_pmap_name]
Firewall(config-pmap-c)# inspect h323 [h323_pmap_name] The inspect h323 command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as h323_pmap_name.
The inspect h323 command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as h323_pmap_name.
![]() As an example, an H.323 inspection policy map is configured to permit only calls from calling parties beginning with the “859555” prefix (4 digits to follow) and to called parties beginning with the “502555” prefix (4 digits to follow). The inspection engine will also require call party numbers to be included during call setup. It will also enforce RFC conformance for the RTP traffic and will track the state of the H.323 connection. The following commands can be used to configure the H.323 inspection engine policies:
As an example, an H.323 inspection policy map is configured to permit only calls from calling parties beginning with the “859555” prefix (4 digits to follow) and to called parties beginning with the “502555” prefix (4 digits to follow). The inspection engine will also require call party numbers to be included during call setup. It will also enforce RFC conformance for the RTP traffic and will track the state of the H.323 connection. The following commands can be used to configure the H.323 inspection engine policies:
Firewall(config)# regex Party1 "859555...."
Firewall(config)# regex Party2 "502555...."
Firewall(config)# policy-map type inspect h323 MyH323Policy
Firewall(config-pmap)# match not calling-party regex Party1
Firewall(config-pmap-c)# drop-connection
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# match not called-party regex Party2
Firewall(config-pmap-c)# drop-connection
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# call-party-numbers
Firewall(config-pmap-p)# rtp-conformance
Firewall(config-pmap-p)# state-checking
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect h323 MyH323Policy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring HTTP Inspection—ASA 7.2(1) and Later
![]() You can use the following steps to configure the HTTP application layer inspection engine in ASA 7.2(1) or later:
You can use the following steps to configure the HTTP application layer inspection engine in ASA 7.2(1) or later:
-
 (Optional) Define an HTTP inspection policy map:
(Optional) Define an HTTP inspection policy map: Firewall(config)# policy-map type inspect http http_pmap_name
Firewall(config)# policy-map type inspect http http_pmap_name -
 (Optional) Define any matching conditions and their actions:
(Optional) Define any matching conditions and their actions:  Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description

Firewall(config-pmap)# match [not]
req-resp content-type mismatch
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP content type mismatch
Match: HTTP content type mismatch Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
request args {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP request arguments with a regular expression
Match: HTTP request arguments with a regular expression Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
request body {length gt length |
regex {regex | class
regex_cmap_name}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP request body length (in bytes) or content (with a regular expression)
Match: HTTP request body length (in bytes) or content (with a regular expression) Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
request header field {count gt
count | length gt length |
regex {regex | class regex_cmap_name}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP request header field as a keyword from the list shown in Table 7-10.
Match: HTTP request header field as a keyword from the list shown in Table 7-10. count tallies the number of instances (0-127) of the header field, length measures the length (1-32767 characters) of the header field, regex matches against a regular expression.
count tallies the number of instances (0-127) of the header field, length measures the length (1-32767 characters) of the header field, regex matches against a regular expression. Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
request method method
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP request method type as a keyword from the list shown in Table 7-10.
Match: HTTP request method type as a keyword from the list shown in Table 7-10. Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
request uri {length gt length | regex
{regex | class regex_cmap_name}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP request URI field length (1-65535 characters) or context (regular expression)
Match: HTTP request URI field length (1-65535 characters) or context (regular expression) Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional

Firewall(config-pmap)# match [not]
response body {active-x | java-
applet | length length | regex {regex
| class regex_cmap_name}}
Firewall(config-pmap-c)# {drop-
connection | reset} [log] Match: HTTP response body content (ActiveX or Java), body length, or body content (regular expression)
Match: HTTP response body content (ActiveX or Java), body length, or body content (regular expression) Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional Match: HTTP response header field as a keyword from the list shown in Table 7-10.
Match: HTTP response header field as a keyword from the list shown in Table 7-10. count tallies the number of instances (0-127) of the header field, length measures the length (1-32767 characters) of the header field, regex matches against a regular expression.
count tallies the number of instances (0-127) of the header field, length measures the length (1-32767 characters) of the header field, regex matches against a regular expression. Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional
 Firewall(config-pmap)# match [not] response status-line regex {regex | class regex_cmap_name}
Firewall(config-pmap)# match [not] response status-line regex {regex | class regex_cmap_name}
Firewall(config-pmap-c)# {drop-connection | reset} [log] Match: HTTP response status line content (regular expression)
Match: HTTP response status line content (regular expression) Action: Drop or reset the connection; log optional
Action: Drop or reset the connection; log optional Table 7-10: Keywords for HTTP Match Request/Response Header and Method Commands
Table 7-10: Keywords for HTTP Match Request/Response Header and Method Commands Open table as spreadsheet
Open table as spreadsheet Command
Command Acceptable Keywords
Acceptable Keywords match request header field
match request header field  accept, accept-charset, accept-encoding, accept-language, allow, authorization, cache-control, connection, content-encoding, content-language, content-length, content-location, content-md5, content-range, content-type, cookie, count, date, expect, expires, from, host, if-match, if-modified-since, if-none-match, if-range, if-unmodified-since, last-modified, length, max-forwards, non-ascii, pragma, proxy-authorization, range, referer, te, trailer, transfer-encoding, upgrade, user-agent, via, warning
accept, accept-charset, accept-encoding, accept-language, allow, authorization, cache-control, connection, content-encoding, content-language, content-length, content-location, content-md5, content-range, content-type, cookie, count, date, expect, expires, from, host, if-match, if-modified-since, if-none-match, if-range, if-unmodified-since, last-modified, length, max-forwards, non-ascii, pragma, proxy-authorization, range, referer, te, trailer, transfer-encoding, upgrade, user-agent, via, warning  match request method method
match request method method  bcopy, bdelete, bmove, bpropfind, bproppatch, connect, copy, delete, edit, get, getattribute, getattributenames, getproperties, head, index, lock, mkcol, mkdir, move, notify, options, poll, post, propfind, proppatch, put, revadd, revlabel, revlog, revnum, save, search, setattribute, startrev, stoprev, subscribe, trace, unedit, unlock, unsubscribe
bcopy, bdelete, bmove, bpropfind, bproppatch, connect, copy, delete, edit, get, getattribute, getattributenames, getproperties, head, index, lock, mkcol, mkdir, move, notify, options, poll, post, propfind, proppatch, put, revadd, revlabel, revlog, revnum, save, search, setattribute, startrev, stoprev, subscribe, trace, unedit, unlock, unsubscribe  match response header field
match response header field  accept-ranges, age, allow, cache-control, connection, content-encoding, content-language, content-length, content-location, content-md5, content-range, content-type, count, date, eTag, expires, last-modified, length, location, non-ascii, pragma, proxy-authenticate, retry-after, server, set-cookie, trailer, transfer-encoding, upgrade, vary, via, warning, www-authenticate
accept-ranges, age, allow, cache-control, connection, content-encoding, content-language, content-length, content-location, content-md5, content-range, content-type, count, date, eTag, expires, last-modified, length, location, non-ascii, pragma, proxy-authenticate, retry-after, server, set-cookie, trailer, transfer-encoding, upgrade, vary, via, warning, www-authenticate  As well, you can configure an HTTP inspection class map with the class-map type inspection http http_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple HTTP inspection policies.
As well, you can configure an HTTP inspection class map with the class-map type inspection http http_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple HTTP inspection policies. Then you can reference the inspection class map in the inspection policy map with the following command:
Then you can reference the inspection class map in the inspection policy map with the following command: Firewall(config-pmap)# class http_cmap_name
Firewall(config-pmap)# class http_cmap_name By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again.
By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again. -
 Set HTTP parameters:
Set HTTP parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the following commands:
First, enter the parameters mode and then configure one or more parameters with the following commands: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# body-match-
maximum [size] Set the maximum number of characters to search in the body content.
Set the maximum number of characters to search in the body content.

Firewall(config-pmap-p)# protocol-
violation [{drop-connection | reset}
[log]] Check for HTTP protocol violations; if any are found, drop or reset the connection; log optional
Check for HTTP protocol violations; if any are found, drop or reset the connection; log optional

Firewall(config-pmap-p)# spoof-server
text Set the spoof server field to the string text.
Set the spoof server field to the string text. -
 Enable HTTP inspection:
Enable HTTP inspection: Firewall(config-pmap-c)# inspect http [http_pmap_name]
Firewall(config-pmap-c)# inspect http [http_pmap_name] The inspect http command must be entered as an action in a policy map. You can also apply an HTTP inspection policy map by giving its name as http_pmap_name.
The inspect http command must be entered as an action in a policy map. You can also apply an HTTP inspection policy map by giving its name as http_pmap_name.
![]() As an example, an HTTP inspection policy map MyHTTPPolicy is used to enforce two policies:
As an example, an HTTP inspection policy map MyHTTPPolicy is used to enforce two policies:
-
 Drop connections that have a content type mismatch or a URI length of more than 1024 characters
Drop connections that have a content type mismatch or a URI length of more than 1024 characters -
 Log but permit connections that return ActiveX or Java applet content
Log but permit connections that return ActiveX or Java applet content
![]() The policies are configured as two HTTP inspection class maps. The following commands can be used to configure the HTTP inspection policies:
The policies are configured as two HTTP inspection class maps. The following commands can be used to configure the HTTP inspection policies:
Firewall(config)# class-map type inspect http match-any MyHTTPClass_drop
Firewall(config-cmap)# match req-resp-content-type mismatch
Firewall(config-cmap)# match request uri length gt 1024
Firewall(config-cmap)# exit
Firewall(config)# class-map type inspect http match-any MyHTTPClass_log
Firewall(config-cmap)# match response body active-x
Firewall(config-cmap)# match response body java-applet
Firewall(config-cmap)# exit
!
Firewall(config)# policy-map type inspect http MyHTTPPolicy
Firewall(config-pmap)# class MyHTTPClass_drop
Firewall(config-pmap-c)# drop-connection
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# class MyHTTPClass_log
Firewall(config-pmap-c)# log
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect http MyHTTPPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring HTTP Inspection—FWSM and ASA 7.0-7.1
![]() HTTP is used to exchange data between a client and a server. Most often, this is used between a client’s web browser and a web server. HTTP is defined in RFC 1945 (HTTP v1.0) and RFC 2616 (HTTP v1.1). The basic HTTP inspection engine (beginning with PIX 6.3 fixup http) performs URL logging and Java and ActiveX filtering and enables the use of Websense or N2H2 for URL filtering.
HTTP is used to exchange data between a client and a server. Most often, this is used between a client’s web browser and a web server. HTTP is defined in RFC 1945 (HTTP v1.0) and RFC 2616 (HTTP v1.1). The basic HTTP inspection engine (beginning with PIX 6.3 fixup http) performs URL logging and Java and ActiveX filtering and enables the use of Websense or N2H2 for URL filtering.
![]() Beginning with ASA 7.0(1) and FWSM 3.1(1), HTTP application inspection can be enhanced with any of the following criteria:
Beginning with ASA 7.0(1) and FWSM 3.1(1), HTTP application inspection can be enhanced with any of the following criteria:
-
 HTTP traffic must conform to RFC 2616 (HTTP 1.1)
HTTP traffic must conform to RFC 2616 (HTTP 1.1) -
 Allowed message body or content length size
Allowed message body or content length size -
 Message content type matches the HTTP header
Message content type matches the HTTP header -
 Allowed request and response header size
Allowed request and response header size -
 Allowed URI length
Allowed URI length -
 Allowed use of port 80 for non-HTTP applications
Allowed use of port 80 for non-HTTP applications -
 Allowed request methods
Allowed request methods
![]() To configure enhanced HTTP inspection, you can follow these steps to configure an HTTP map for use with the inspect http command:
To configure enhanced HTTP inspection, you can follow these steps to configure an HTTP map for use with the inspect http command:
-
 Define the HTTP map name:
Define the HTTP map name: Firewall(config)# http-map http_map_name
Firewall(config)# http-map http_map_name The HTTP map is named http_map_name (up to 64 characters). The HTTP map must be applied with the following command in a policy map before it can be used:
The HTTP map is named http_map_name (up to 64 characters). The HTTP map must be applied with the following command in a policy map before it can be used:
inspect http http_map_name -
 (Optional) Check the message content length:
(Optional) Check the message content length: Firewall(config-http-map)# content-length {[min minimum] [max maximum]}
Firewall(config-http-map)# content-length {[min minimum] [max maximum]}
action {allow | drop | reset} [log] If the HTTP message content is larger than minimum (1 to 65535 bytes) and smaller than maximum (1 to 50,000,000 bytes), it is allowed to pass. If it fails this test, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
If the HTTP message content is larger than minimum (1 to 65535 bytes) and smaller than maximum (1 to 50,000,000 bytes), it is allowed to pass. If it fails this test, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. If the min keyword is omitted, the content length must be less than maximum. If max is omitted, the length must be greater than minimum. You can also use the log keyword to generate Syslog messages based on the action taken.
If the min keyword is omitted, the content length must be less than maximum. If max is omitted, the length must be greater than minimum. You can also use the log keyword to generate Syslog messages based on the action taken. You can configure only one content-length command in an HTTP map.
You can configure only one content-length command in an HTTP map. For example, the following commands allow message lengths greater than 256 bytes to pass. Packets smaller than 256 bytes fail the test, triggering the action to reset the TCP connection and generate a Syslog message:
For example, the following commands allow message lengths greater than 256 bytes to pass. Packets smaller than 256 bytes fail the test, triggering the action to reset the TCP connection and generate a Syslog message: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# content-length min 256 action reset log
Firewall(config-http-map)# exit -
 (Optional) Verify the message content type:
(Optional) Verify the message content type: Firewall(config-http-map)# content-type-verification [match-req-rsp] action
Firewall(config-http-map)# content-type-verification [match-req-rsp] action
{allow | drop | reset} [log] Each HTTP message is examined to make sure the content type stated in the HTTP header matches the message’s actual content and that the content is an acceptable type. You can add the match-req-rsp keyword to verify that the content type in each HTTP request header matches the content type returned in the corresponding HTTP response header.
Each HTTP message is examined to make sure the content type stated in the HTTP header matches the message’s actual content and that the content is an acceptable type. You can add the match-req-rsp keyword to verify that the content type in each HTTP request header matches the content type returned in the corresponding HTTP response header. Table 7-11 lists the acceptable content types.
Table 7-11 lists the acceptable content types. Table 7-11: Acceptable HTTP Message Content Types
Table 7-11: Acceptable HTTP Message Content Types Open table as spreadsheet
Open table as spreadsheet Content
Content Type
Type application/
application/ msword, octet-stream, pdf, postscript, vnd.ms-excel, vnd.ms-powerpoint, x-gzip, x-java-arching, x-java-xm, zip
msword, octet-stream, pdf, postscript, vnd.ms-excel, vnd.ms-powerpoint, x-gzip, x-java-arching, x-java-xm, zip audio/
audio/ *, basic, midi, mpeg, x-adpcm, x-aiff, x-ogg, x-wav
*, basic, midi, mpeg, x-adpcm, x-aiff, x-ogg, x-wav image/
image/ *, cgf, gif, jpeg, png, tiff, x-3ds, x-bitmap, x-niff, x-portable-bitmap, x-portable-greymap, x-xpm
*, cgf, gif, jpeg, png, tiff, x-3ds, x-bitmap, x-niff, x-portable-bitmap, x-portable-greymap, x-xpm text/
text/ *, css, html, plain, richtext, sgml, xmcd, xml
*, css, html, plain, richtext, sgml, xmcd, xml video/
video/ *, -flc, mpeg, quicktime, sgi, x-avi, x-fli, x-mng, x-msvideo
*, -flc, mpeg, quicktime, sgi, x-avi, x-fli, x-mng, x-msvideo If all these tests pass, the packet is allowed to pass. If a packet fails the tests, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
If all these tests pass, the packet is allowed to pass. If a packet fails the tests, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. For example, the following commands allow verified messages to pass. If the verification fails, those packets are also allowed (action allow), but a Syslog message is generated:
For example, the following commands allow verified messages to pass. If the verification fails, those packets are also allowed (action allow), but a Syslog message is generated: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# content-type-verification match-req-rsp action
allow log
Firewall(config-http-map)# exit -
 (Optional) Check the header length:
(Optional) Check the header length: Firewall(config-http-map)# max-header-length {[request length] [response
Firewall(config-http-map)# max-header-length {[request length] [response
length]} action {allow | drop | reset} [log] If you use the request keyword, the HTTP request header length must be less than length (0 to 65535 bytes). If you use the response keyword, the corresponding HTTP response header must be less than length (0 to 65535 bytes).
If you use the request keyword, the HTTP request header length must be less than length (0 to 65535 bytes). If you use the response keyword, the corresponding HTTP response header must be less than length (0 to 65535 bytes). If a packet fails this test, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
If a packet fails this test, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. For example, the following commands allow HTTP request messages with header lengths of less than 200 bytes. The corresponding HTTP response headers must also be less than 200 bytes. Otherwise, the HTTP connection is reset.
For example, the following commands allow HTTP request messages with header lengths of less than 200 bytes. The corresponding HTTP response headers must also be less than 200 bytes. Otherwise, the HTTP connection is reset. Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# max-header-length request 200 response 200
action reset log
Firewall(config-http-map)# exit -
 (Optional) Check the Uniform Resource Identifier URI length:
(Optional) Check the Uniform Resource Identifier URI length: Firewall(config-http-map)# max-uri-length length action {allow | drop |
Firewall(config-http-map)# max-uri-length length action {allow | drop |
reset} [log] The length of the URI in an HTTP request message must be less than length (1 to 65535) bytes. If its length is greater, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
The length of the URI in an HTTP request message must be less than length (1 to 65535) bytes. If its length is greater, one of the following actions is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. For example, the following commands allow HTTP requests with URIs shorter than 256 bytes to pass. If the URIs are longer, the HTTP connection is reset:
For example, the following commands allow HTTP requests with URIs shorter than 256 bytes to pass. If the URIs are longer, the HTTP connection is reset: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# max-uri-length 256 action reset log
Firewall(config-http-map)# exit -
 (Optional) Test for HTTP port cloaking:
(Optional) Test for HTTP port cloaking: Firewall(config-http-map)# port-misuse {default | im | p2p | tunnelling}
Firewall(config-http-map)# port-misuse {default | im | p2p | tunnelling}
action {allow | drop | reset} [log] HTTP port cloaking is used to transport traffic from a non-HTTP application over the standard HTTP port. These applications appear to use regular HTTP, as if they were web-based applications. The firewall can detect some misuses of the HTTP port by examining the entire contents of each HTTP packet.
HTTP port cloaking is used to transport traffic from a non-HTTP application over the standard HTTP port. These applications appear to use regular HTTP, as if they were web-based applications. The firewall can detect some misuses of the HTTP port by examining the entire contents of each HTTP packet. You can use one of the following keywords to detect a specific tunneling application:
You can use one of the following keywords to detect a specific tunneling application:-
 im— Instant messaging applications. In PIX 7.0, only Yahoo Messenger is detected.
im— Instant messaging applications. In PIX 7.0, only Yahoo Messenger is detected. -
 p2p— Peer-to-peer applications. In PIX 7.0, Kazaa and Gnutella can be detected.
p2p— Peer-to-peer applications. In PIX 7.0, Kazaa and Gnutella can be detected. -
 tunnelling— Data from arbitrary applications is tunneled inside HTTP request messages to bypass normal firewalls. In PIX 7.0, the following tunneling applications can be detected:
tunnelling— Data from arbitrary applications is tunneled inside HTTP request messages to bypass normal firewalls. In PIX 7.0, the following tunneling applications can be detected:-
 HTTPort/HTTHost— http://www.htthost.com
HTTPort/HTTHost— http://www.htthost.com -
 GNU Httptunnel— http://www.nocrew.org/software/httptunnel.html
GNU Httptunnel— http://www.nocrew.org/software/httptunnel.html -
 GotoMyPC— http://www.gotomypc.com
GotoMyPC— http://www.gotomypc.com -
 Firethru Fire Extinguisher— http://www.firethru.com
Firethru Fire Extinguisher— http://www.firethru.com -
 Http-tunnel.com Client— http://www.http-tunnel.com
Http-tunnel.com Client— http://www.http-tunnel.com
-
 If the application is detected, the corresponding action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
If the application is detected, the corresponding action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. You can also use the default keyword to define an action to be taken for any HTTP port misuse application that is not one of the keywords listed.
You can also use the default keyword to define an action to be taken for any HTTP port misuse application that is not one of the keywords listed. You can repeat this command to define multiple applications to detect.
You can repeat this command to define multiple applications to detect. For example, the following commands reset connections if a peer-to-peer application, a tunneling application, or any other unrecognized port-cloaking application is detected. Only instant messaging applications are allowed to pass through.
For example, the following commands reset connections if a peer-to-peer application, a tunneling application, or any other unrecognized port-cloaking application is detected. Only instant messaging applications are allowed to pass through. Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# port-misuse im action allow
Firewall(config-http-map)# port-misuse default action reset log
Firewall(config-http-map)# exit -
-
 (Optional) Check the HTTP request method:
(Optional) Check the HTTP request method: Firewall(config-http-map)# request-method {rfc | ext} {method | default}
Firewall(config-http-map)# request-method {rfc | ext} {method | default}
action {allow | drop | reset} [log] By default, all HTTP request methods are allowed. You can define a policy for a specific request method based on whether it is a request method defined in RFC 2616 (rfc) or an HTTP extension method (ext).
By default, all HTTP request methods are allowed. You can define a policy for a specific request method based on whether it is a request method defined in RFC 2616 (rfc) or an HTTP extension method (ext). For rfc, you can use one of the following method keywords: connect, delete, get, head, options, post, put, or trace.
For rfc, you can use one of the following method keywords: connect, delete, get, head, options, post, put, or trace. For ext, you can use one of the following method keywords: copy, edit, getattribute, getattributenames, getproperties, index, lock, mkdir, move, revadd, revlabel, revlog, revnum, save, setattribute, startrev, stoprev, unedit, or unlock.
For ext, you can use one of the following method keywords: copy, edit, getattribute, getattributenames, getproperties, index, lock, mkdir, move, revadd, revlabel, revlog, revnum, save, setattribute, startrev, stoprev, unedit, or unlock. You can also use the default keyword to define an action to be taken for any request method not explicitly configured.
You can also use the default keyword to define an action to be taken for any request method not explicitly configured. If the specified method is detected, the corresponding action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
If the specified method is detected, the corresponding action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. You can repeat this command to define multiple request method policies.
You can repeat this command to define multiple request method policies. For example, the following commands allow any of the RFC 2616 request methods to pass. If any of the extension’s request methods is detected, the HTTP connection is reset:
For example, the following commands allow any of the RFC 2616 request methods to pass. If any of the extension’s request methods is detected, the HTTP connection is reset: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# request-method rfc default action allow
Firewall(config-http-map)# request-method ext default action reset log
Firewall(config-http-map)# exit -
 (Optional) Check for RFC 2616 compliance:
(Optional) Check for RFC 2616 compliance: Firewall(config-http-map)# strict-http action {allow | drop | reset}
Firewall(config-http-map)# strict-http action {allow | drop | reset}
[log] By default, HTTP packets that are not compliant with RFC 2616 are dropped. You can specify a different action to take when noncompliant traffic is detected: allow the packet to pass, drop the packet, or reset the HTTP connection.
By default, HTTP packets that are not compliant with RFC 2616 are dropped. You can specify a different action to take when noncompliant traffic is detected: allow the packet to pass, drop the packet, or reset the HTTP connection. You can add the log keyword to generate Syslog messages when the action is taken.
You can add the log keyword to generate Syslog messages when the action is taken. For example, the following commands allow noncompliant HTTP messages to be forwarded. As an audit trail, Syslog messages are sent when this occurs:
For example, the following commands allow noncompliant HTTP messages to be forwarded. As an audit trail, Syslog messages are sent when this occurs: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# strict-http action allow log
Firewall(config-http-map)# exit -
 (Optional) Check the transfer encoding type:
(Optional) Check the transfer encoding type: Firewall(config-http-map)# transfer-encoding type {type | default}
Firewall(config-http-map)# transfer-encoding type {type | default}
action {allow | drop | reset} [log] Transfer encoding is used to convert a document into a form that can be transported over HTTP. You can specify a transfer encoding type as one of the keywords listed in Table 7-12.
Transfer encoding is used to convert a document into a form that can be transported over HTTP. You can specify a transfer encoding type as one of the keywords listed in Table 7-12. Table 7-12: Transfer Encoding Types for HTTP
Table 7-12: Transfer Encoding Types for HTTP Open table as spreadsheet
Open table as spreadsheet Transfer Encoding type
Transfer Encoding type  Description
Description chunked
chunked  The message is sent as a series of “chunks”
The message is sent as a series of “chunks” compress
compress  UNIX file compression
UNIX file compression deflate
deflate  zlib format (RFC 1950) and deflate compression (RFC 1951)
zlib format (RFC 1950) and deflate compression (RFC 1951) gzip
gzip  GNU zip (RFC 1952)
GNU zip (RFC 1952) identity
identity  No transfer encoding is used
No transfer encoding is used You can also use the default keyword to match all transfer encoding types other than the ones you explicitly configure.
You can also use the default keyword to match all transfer encoding types other than the ones you explicitly configure. When this transfer encoding type is detected in an HTTP message, the specified action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection.
When this transfer encoding type is detected in an HTTP message, the specified action is taken: allow the packet to pass, drop the packet, or reset the HTTP connection. For example, the following commands allow the identity and gzip encodings, and all other types cause the HTTP connection to be reset:
For example, the following commands allow the identity and gzip encodings, and all other types cause the HTTP connection to be reset: Firewall(config)# http-map Filter_http
Firewall(config)# http-map Filter_http
Firewall(config-http-map)# transfer-encoding type identity action allow
Firewall(config-http-map)# transfer-encoding type gzip action allow
Firewall(config-http-map)# transfer-encoding type default action reset log
Firewall(config-http-map)# exit
!
Firewall(config)# class-map _MyClass
Firewall(config-cmap)# match port tcp eq 80
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class MyClass
Firewall(config-pmap-c)# inspect http Filter_http
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring ICMP Inspection
![]() Internet Control Message Protocol (ICMP) is used in a variety of ways to test and exchange network parameters between devices. For example, the ping “application” can be used to send echo requests from one host to another; the target host is expected to return echo replies. This tests the hosts’ livelihood and the network’s connectivity.
Internet Control Message Protocol (ICMP) is used in a variety of ways to test and exchange network parameters between devices. For example, the ping “application” can be used to send echo requests from one host to another; the target host is expected to return echo replies. This tests the hosts’ livelihood and the network’s connectivity.
![]() In platform releases prior to ASA 7.0(1) and FWSM 3.1(1), a firewall can allow ICMP traffic to pass through, but only if interface access lists are configured to explicitly permit it. As ICMP packets cross from one firewall interface to another, a special ICMP xlate entry is created. However, this xlate is used only to provide the translation—not to provide ICMP inspection. ICMP xlate entries have a fixed idle time of about 30 seconds.
In platform releases prior to ASA 7.0(1) and FWSM 3.1(1), a firewall can allow ICMP traffic to pass through, but only if interface access lists are configured to explicitly permit it. As ICMP packets cross from one firewall interface to another, a special ICMP xlate entry is created. However, this xlate is used only to provide the translation—not to provide ICMP inspection. ICMP xlate entries have a fixed idle time of about 30 seconds.
![]() Outbound pings might be allowed, but the return traffic is blocked at the outside interface unless that access list permits it to enter. It becomes difficult to know which outside addresses will return legitimate ICMP traffic, so a permit icmp any any is often added to the outside access list. Obviously, such a broad rule leaves the door open for malicious users to abuse inbound ICMP into a network.
Outbound pings might be allowed, but the return traffic is blocked at the outside interface unless that access list permits it to enter. It becomes difficult to know which outside addresses will return legitimate ICMP traffic, so a permit icmp any any is often added to the outside access list. Obviously, such a broad rule leaves the door open for malicious users to abuse inbound ICMP into a network.
![]() Beginning with FWSM 3.1(1) and ASA 7.0(1), an ICMP inspection engine is available. Rather than explicitly configuring access list rules to permit inbound ICMP traffic, the firewall can selectively (and automatically) permit return traffic based on the original outbound requests.
Beginning with FWSM 3.1(1) and ASA 7.0(1), an ICMP inspection engine is available. Rather than explicitly configuring access list rules to permit inbound ICMP traffic, the firewall can selectively (and automatically) permit return traffic based on the original outbound requests.
![]() For example, as an inside host sends an ICMP echo packet toward an outside host, the firewall builds the ICMP xlate entry. The source and destination addresses are examined, along with the ICMP message type and code, the ICMP identifier, and the ICMP sequence number fields. This forms a five-tuple of information that can be inspected and matched.
For example, as an inside host sends an ICMP echo packet toward an outside host, the firewall builds the ICMP xlate entry. The source and destination addresses are examined, along with the ICMP message type and code, the ICMP identifier, and the ICMP sequence number fields. This forms a five-tuple of information that can be inspected and matched.
![]() For example, the following output represents the ICMP xlate entry that was created when inside host 192.168.198.199 (translated to global address 10.10.1.1) sent one ICMP echo request packet to outside host 10.10.10.10:
For example, the following output represents the ICMP xlate entry that was created when inside host 192.168.198.199 (translated to global address 10.10.1.1) sent one ICMP echo request packet to outside host 10.10.10.10:
%ASA-6-305011: Built dynamic ICMP translation from inside:192.168.198.199/512 to
outside:10.10.1.1/1
Firewall# show xlate
5 in use, 12 most used
PAT Global 10.10.1.1(1) Local 192.168.198.199 ICMP id 512
[output omitted]
![]() Here, /512 and ICMP id 512 represent the inside host’s ICMP identifier field value. During the dynamic address translation, the firewall creates a dynamic ICMP identifier for the outside target. This is shown as /1 and (1) after the 10.10.1.1 address lines.
Here, /512 and ICMP id 512 represent the inside host’s ICMP identifier field value. During the dynamic address translation, the firewall creates a dynamic ICMP identifier for the outside target. This is shown as /1 and (1) after the 10.10.1.1 address lines.
![]() The ICMP inspection engine examines return ICMP traffic, looking for packets that are expected in response to a prior request. ICMP is IP protocol 1. It does not include any mechanisms for establishing a connection or tracking the state of a message exchange. The ICMP inspection engine must use the five-tuple of ICMP information gathered from request and response packets to approximate a connection state.
The ICMP inspection engine examines return ICMP traffic, looking for packets that are expected in response to a prior request. ICMP is IP protocol 1. It does not include any mechanisms for establishing a connection or tracking the state of a message exchange. The ICMP inspection engine must use the five-tuple of ICMP information gathered from request and response packets to approximate a connection state.
![]() In fact, after an ICMP xlate is created and a request packet goes out, the firewall creates a special ICMP connection entry apart from the normal conn table entries. The following Syslog message was generated when the special connection was created:
In fact, after an ICMP xlate is created and a request packet goes out, the firewall creates a special ICMP connection entry apart from the normal conn table entries. The following Syslog message was generated when the special connection was created:
%ASA-6-302020: Built ICMP connection for faddr 10.10.10.10/0 gaddr 10.10.1.1/1
laddr 192.168.198.199/512
![]() Finally, the ICMP inspection engine permits only one response to return for every request that is sent out. The ICMP sequence numbers must also match between a request and a reply packet. With “stateful” ICMP inspection, the ICMP connections and xlate entries can be quickly torn down as soon as the appropriate reply is received.
Finally, the ICMP inspection engine permits only one response to return for every request that is sent out. The ICMP sequence numbers must also match between a request and a reply packet. With “stateful” ICMP inspection, the ICMP connections and xlate entries can be quickly torn down as soon as the appropriate reply is received.
![]() You can see this in the following Syslog output, which resulted from one ICMP echo request packet being sent from inside host 192.168.198.199 (translated to global address 10.10.1.1) to outside host 10.10.10.10. (Message ID 711001 was produced because the debug icmp trace command was also used.)
You can see this in the following Syslog output, which resulted from one ICMP echo request packet being sent from inside host 192.168.198.199 (translated to global address 10.10.1.1) to outside host 10.10.10.10. (Message ID 711001 was produced because the debug icmp trace command was also used.)
%ASA-6-609001: Built local-host outside:10.10.10.10
%ASA-6-305011: Built dynamic ICMP translation from inside:192.168.198.199/512 to
outside:10.10.1.1/2
%ASA-6-302020: Built ICMP connection for faddr 10.10.10.10/0 gaddr 10.10.1.1/2
laddr 192.168.198.199/512
%ASA-7-711001: ICMP echo request (len 32 id 512 seq 25344) 192.168.198.199 >
10.10.10.10
%ASA-7-711001: ICMP echo reply (len 32 id 2 seq 25344) 10.10.10.10 > 10.10.1.1
%ASA-6-302021: Teardown ICMP connection for faddr 10.10.10.10/0 gaddr 10.10.1.1/2
laddr 192.168.198.199/512
%ASA-6-609002: Teardown local-host outside:10.10.10.10 duration 0:00:00
![]() The time from when the xlate entries were first created until the ICMP connection entry was deleted and the xlates torn down is shown to be 0:00:00 (less than 1 second)! The ICMP inspection engine allows the connectionless and stateless ICMP protocol to be used through a firewall while maintaining a high level of security.
The time from when the xlate entries were first created until the ICMP connection entry was deleted and the xlates torn down is shown to be 0:00:00 (less than 1 second)! The ICMP inspection engine allows the connectionless and stateless ICMP protocol to be used through a firewall while maintaining a high level of security.
![]() By default, ICMP inspection is not enabled. To enable it, you can add the following command to a policy map as an action:
By default, ICMP inspection is not enabled. To enable it, you can add the following command to a policy map as an action:
Firewall(config-pmap-c)# inspect icmp
![]() For example, you might want to add ICMP inspection to the default service policy that is applied to all firewall interfaces. To do so, you only need to add the inspect icmp command to the default global_policy policy map that is already defined. This policy map is already applied as a global service policy, so you do not need to define it separately. You can use the following commands to add the inspection to the default policy map:
For example, you might want to add ICMP inspection to the default service policy that is applied to all firewall interfaces. To do so, you only need to add the inspect icmp command to the default global_policy policy map that is already defined. This policy map is already applied as a global service policy, so you do not need to define it separately. You can use the following commands to add the inspection to the default policy map:
Firewall(config)# policy-map global_policy
Firewall(config-pmap)# class inspection_default
Firewall(config-pmap-c)# inspect icmp
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)#
![]() By default, ICMP inspection does not permit any ICMP error packets to return through an address translation. This is because an ICMP error message can be sent from an address other than the original ICMP target. For example, if the IP time-to-live (TTL) value expires on an ICMP echo request that was sent to an outside host, an intervening router sends an ICMP error message back to the inside host. That packet uses the router’s own IP address as the source address—not the ICMP echo target host’s address.
By default, ICMP inspection does not permit any ICMP error packets to return through an address translation. This is because an ICMP error message can be sent from an address other than the original ICMP target. For example, if the IP time-to-live (TTL) value expires on an ICMP echo request that was sent to an outside host, an intervening router sends an ICMP error message back to the inside host. That packet uses the router’s own IP address as the source address—not the ICMP echo target host’s address.
![]() When a router replies with an ICMP error packet, it must also include the first 64 bytes of the original IP packet as the error message payload. When a host receives the error packet, it can look inside the payload to see the original source and destination addresses, protocol, port numbers, and so on.
When a router replies with an ICMP error packet, it must also include the first 64 bytes of the original IP packet as the error message payload. When a host receives the error packet, it can look inside the payload to see the original source and destination addresses, protocol, port numbers, and so on.
![]() You can use the following command to enable ICMP error processing as part of the ICMP inspection:
You can use the following command to enable ICMP error processing as part of the ICMP inspection:
Firewall(config-pmap-c)# inspect icmp error
![]() Now the firewall examines ICMP error packet payloads to find the original packet details. If it can match those to known ICMP “connections” and xlate entries, it can work out the address translation and permits the ICMP error packet to reach the original sender.
Now the firewall examines ICMP error packet payloads to find the original packet details. If it can match those to known ICMP “connections” and xlate entries, it can work out the address translation and permits the ICMP error packet to reach the original sender.
Configuring Instant Messaging (IM) Inspection
![]() Beginning in ASA 7.2(1), you can configure an application layer inspection engine that enforces policies related to instant messaging applications. Use the following steps to configure and tune the IM inspection engine:
Beginning in ASA 7.2(1), you can configure an application layer inspection engine that enforces policies related to instant messaging applications. Use the following steps to configure and tune the IM inspection engine:
-
 (Optional) Define an IM inspection policy map:
(Optional) Define an IM inspection policy map: Firewall(config)# policy-map type inspect im im_pmap_name
Firewall(config)# policy-map type inspect im im_pmap_name -
 (Optional) Define any matching conditions and their actions:
(Optional) Define any matching conditions and their actions: Open table as spreadsheet
Open table as spreadsheet Match and Action Command Syntax
Match and Action Command Syntax Description
Description

Firewall(config-pmap)# match [not]
filename regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop-connection
| reset} Match: Filename in file transfer (except MSN Messenger)
Match: Filename in file transfer (except MSN Messenger) Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not] ip-
address ip_address subnet_mask
Firewall(config-pmap-c)# {drop-connection
| reset} Match: Client IP address
Match: Client IP address Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not] login-
name regex {regex | class regex_cmap_name}
Firewall(config-pmap-c)# {drop-connection
| reset} Match: Client’s IM login name
Match: Client’s IM login name Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not] peer-
ip-address ip_address subnet_mask
Firewall(config-pmap-c)# {drop-connection
| reset} Match: Peer IP address (client or server)
Match: Peer IP address (client or server) Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not] peer-
login-name regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop-connection
| reset} Match: Peer’s IM login name (client only)
Match: Peer’s IM login name (client only) Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not]
protocol [msn-im] [yahoo-im]
Firewall(config-pmap-c)# {drop-connection
| reset} Match: IM protocol
Match: IM protocol Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not]
service {chat | conference | file-transfer
| games | voice-chat | webcam}
Firewall(config-pmap-c)# {drop-connection
| reset} Match: IM service
Match: IM service Action: Drop or reset the connection
Action: Drop or reset the connection

Firewall(config-pmap)# match [not]
version regex {regex | class
regex_cmap_name}
Firewall(config-pmap-c)# {drop-connection
| reset} Match: IM file transfer service version
Match: IM file transfer service version Action: Drop or reset the connection
Action: Drop or reset the connection As well, you can configure an IM inspection class map with the class-map type inspection im im_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple IM inspection policies.
As well, you can configure an IM inspection class map with the class-map type inspection im im_cmap_name command. That inspection class map can contain any of the match commands listed here, along with their associated action commands. The idea is to group match and action commands that might be needed in multiple IM inspection policies. Then you can reference the inspection class map in the inspection policy map with the following command:
Then you can reference the inspection class map in the inspection policy map with the following command: Firewall(config-pmap)# class im_cmap_name
Firewall(config-pmap)# class im_cmap_name By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again.
By referencing the inspection class map in several places, you save yourself the trouble of configuring the same match and action commands again and again. There are no parameters to set for the IM inspection policy map.
There are no parameters to set for the IM inspection policy map. -
 Enable IM inspection:
Enable IM inspection: Firewall(config-pmap-c)# inspect im [im_pmap_name]
Firewall(config-pmap-c)# inspect im [im_pmap_name] The inspect im command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as pmap_name.
The inspect im command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as pmap_name.
![]() As an example, an IM inspection engine policy is configured to reset connections when clients attempt to transfer files with “.exe” in their names. As well, webcam services are prevented by resetting the connections. The following commands can be used to configure the IM inspection policies:
As an example, an IM inspection engine policy is configured to reset connections when clients attempt to transfer files with “.exe” in their names. As well, webcam services are prevented by resetting the connections. The following commands can be used to configure the IM inspection policies:
Firewall(config)# regex IMblock1 ".*\.exe"
Firewall(config)# policy-map type inspect im MyIMPolicy
Firewall(config-pmap)# match filename regex IMblock1
Firewall(config-pmap-c)# reset
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# match service webcam
Firewall(config-pmap-c)# reset
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect im MyIMPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring IPSec Passthru Inspection
![]() Beginning with ASA 7.2(1), a firewall can be configured to inspect IPSec tunnels that pass through it. Because the IPSec tunnels do not terminate on the firewall directly, the firewall is not able to inspect the traffic in any detail.
Beginning with ASA 7.2(1), a firewall can be configured to inspect IPSec tunnels that pass through it. Because the IPSec tunnels do not terminate on the firewall directly, the firewall is not able to inspect the traffic in any detail.
![]() Instead, the tunneled traffic is likely encrypted and secured; the firewall can only monitor the number of tunnels passing through to individual client IP addresses and the amount of time the tunnels have been idle.
Instead, the tunneled traffic is likely encrypted and secured; the firewall can only monitor the number of tunnels passing through to individual client IP addresses and the amount of time the tunnels have been idle.
![]() You can use the following steps to configure IPSec Passthru inspection in ASA 7.2(1) or later:
You can use the following steps to configure IPSec Passthru inspection in ASA 7.2(1) or later:
-
 (Optional) Define an IPSec Passthru inspection policy map:
(Optional) Define an IPSec Passthru inspection policy map: Firewall(config)# policy-map type inspect ipsec-pass-thru ipsec_pmap_name
Firewall(config)# policy-map type inspect ipsec-pass-thru ipsec_pmap_name No matching conditions need to be configured for this inspection engine.
No matching conditions need to be configured for this inspection engine. -
 Set IPSec Passthru parameters:
Set IPSec Passthru parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the following commands:
First, enter the parameters mode and then configure one or more parameters with the following commands: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# ah [per-
client-max number] [timeout hh:mm:ss] Set the maximum number of AH mode tunnels allowed from any one client (per-client-max, 0–65,535) or the tunnel idle timeout (timeout).
Set the maximum number of AH mode tunnels allowed from any one client (per-client-max, 0–65,535) or the tunnel idle timeout (timeout).

Firewall(config-pmap-p)# esp [per-
client-max number] [timeout hh:mm:ss] Set the maximum number of ESP mode tunnels allowed from any one client (per-client-max, 0–65,535) or the tunnel idle timeout (timeout).
Set the maximum number of ESP mode tunnels allowed from any one client (per-client-max, 0–65,535) or the tunnel idle timeout (timeout). -
 Enable IPSec Passthru inspection:
Enable IPSec Passthru inspection: Firewall(config-pmap-c)# inspect ipsec-pass-thru [ipsec_pmap_name]
Firewall(config-pmap-c)# inspect ipsec-pass-thru [ipsec_pmap_name] The inspect ipsec-pass-thru command must be entered as an action in a policy map. You can also apply an IPSec Passthru inspection policy map by giving its name as ipsec_pmap_name.
The inspect ipsec-pass-thru command must be entered as an action in a policy map. You can also apply an IPSec Passthru inspection policy map by giving its name as ipsec_pmap_name.
![]() As an example, an IPSec Passthru policy map is configured to enforce an idle timeout of 12 hours on client ESP tunnels passing through the firewall. The following commands can be used to configure the IPSec Passthru policy and inspection engine:
As an example, an IPSec Passthru policy map is configured to enforce an idle timeout of 12 hours on client ESP tunnels passing through the firewall. The following commands can be used to configure the IPSec Passthru policy and inspection engine:
Firewall(config)# policy-map type inspect ipsec-pass-thru MyIPsecPolicy
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# esp timeout 12:00:00
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect ipsec-pass-thru MyIPsecPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring MGCP Inspection—ASA 7.2(1) and Later
![]() Media Gateway Control Protocol (MGCP) is used by call agents to control media gateways (devices that convert telephone circuit audio to data packets). A firewall’s MGCP inspection engine can monitor the “pinholes” or connections that are built as call agents and gateways communicate.
Media Gateway Control Protocol (MGCP) is used by call agents to control media gateways (devices that convert telephone circuit audio to data packets). A firewall’s MGCP inspection engine can monitor the “pinholes” or connections that are built as call agents and gateways communicate.
![]() You can use the following steps to configure MGCP inspection in ASA 7.2(1) or later:
You can use the following steps to configure MGCP inspection in ASA 7.2(1) or later:
-
 (Optional) Define an MGCP inspection policy map:
(Optional) Define an MGCP inspection policy map: Firewall(config)# policy-map type inspect mgcp mgcp_pmap_name
Firewall(config)# policy-map type inspect mgcp mgcp_pmap_name No matching conditions need to be configured for the MGCP inspection engine.
No matching conditions need to be configured for the MGCP inspection engine. -
 Set MGCP parameters:
Set MGCP parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# call-agent
ip_address group_id Set the IP address and call group ID of the call agents that can manage gateways in the same group.
Set the IP address and call group ID of the call agents that can manage gateways in the same group.

Firewall(config-pmap-p)# gateway
ip_address group_id Set the IP address and call group ID of a gateway that can be controlled by a call agent in the same group.
Set the IP address and call group ID of a gateway that can be controlled by a call agent in the same group.

Firewall(config-pmap-p)# command-queue
limit Set the maximum number of queued MGCP messages until a response is received.
Set the maximum number of queued MGCP messages until a response is received. -
 Enable MGCP inspection:
Enable MGCP inspection: Firewall(config-pmap-c)# inspect mgcp [mgcp_pmap_name]
Firewall(config-pmap-c)# inspect mgcp [mgcp_pmap_name] The inspect mgcp command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as pmap_name.
The inspect mgcp command must be entered as an action in a policy map. You can also apply an FTP inspection policy map by giving its name as pmap_name.
![]() As an example, an MGCP inspection policy map is configured to control which call agents can manage which gateways. Call agents 10.5.5.1 and 10.5.5.2 can manage gateways 10.1.1.100 and 10.1.1.101. Call agents 10.5.5.3 and 10.5.5.4 can manage gateways 10.1.1.200 and 10.1.1.201. The following commands can be used to configure the MGCP inspection engine policies:
As an example, an MGCP inspection policy map is configured to control which call agents can manage which gateways. Call agents 10.5.5.1 and 10.5.5.2 can manage gateways 10.1.1.100 and 10.1.1.101. Call agents 10.5.5.3 and 10.5.5.4 can manage gateways 10.1.1.200 and 10.1.1.201. The following commands can be used to configure the MGCP inspection engine policies:
Firewall(config)# policy-map type inspect mgcp MyMGCPPolicy
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# call-agent 10.5.5.1 10
Firewall(config-pmap-p)# call-agent 10.5.5.2 10
Firewall(config-pmap-p)# call-agent 10.5.5.3 20
Firewall(config-pmap-p)# call-agent 10.5.5.4 20
Firewall(config-pmap-p)# gateway 10.1.1.100 10
Firewall(config-pmap-p)# gateway 10.1.1.101 10
Firewall(config-pmap-p)# gateway 10.1.1.200 20
Firewall(config-pmap-p)# gateway 10.1.1.201 20
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect mgcp MyMGCPPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring an MGCP Map—FWSM and ASA 7.0-7.1
![]() Media Gateway Control Protocol (MGCP) is used by call agents to control media gateways (devices that convert telephone circuit audio to data packets).
Media Gateway Control Protocol (MGCP) is used by call agents to control media gateways (devices that convert telephone circuit audio to data packets).
![]() You can follow these steps to configure an MGCP map for use with the inspect mgcp command:
You can follow these steps to configure an MGCP map for use with the inspect mgcp command:
-
 Define the MGCP map name:
Define the MGCP map name: Firewall(config)# mgcp-map mgcp_map_name
Firewall(config)# mgcp-map mgcp_map_name The MGCP map is named mgcp_map_name (up to 64 characters). You must apply the MGCP map in a policy map with the following command map before it can be used:
The MGCP map is named mgcp_map_name (up to 64 characters). You must apply the MGCP map in a policy map with the following command map before it can be used:
inspect mgcp mgcp_map_name -
 Customize MGCP options:
Customize MGCP options: You can use any of the commands listed in Table 7-13 to set a specific MGCP inspection parameter in MGCP map configuration mode.
You can use any of the commands listed in Table 7-13 to set a specific MGCP inspection parameter in MGCP map configuration mode.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
![]() For example, suppose an MGCP map is configured to allow call agents at 192.168.77.10 and 192.168.77.11 to control the gateway at 192.168.100.1. Those call agents are defined as group 1. The call agents at 192.168.77.12 and 192.168.77.13 are defined as group 2 and are allowed to control a different gateway at 192.168.100.2. The MGCP map is then applied to the inspect mgcp command in a policy map. The following commands are used:
For example, suppose an MGCP map is configured to allow call agents at 192.168.77.10 and 192.168.77.11 to control the gateway at 192.168.100.1. Those call agents are defined as group 1. The call agents at 192.168.77.12 and 192.168.77.13 are defined as group 2 and are allowed to control a different gateway at 192.168.100.2. The MGCP map is then applied to the inspect mgcp command in a policy map. The following commands are used:
Firewall(config)# mgcp-map MyMGCPMap
Firewall(config-mgcp-map)# call-agent 192.168.77.10 1
Firewall(config-mgcp-map)# call-agent 192.168.77.11 1
Firewall(config-mgcp-map)# gateway 192.168.100.1 1
Firewall(config-mgcp-map)# call-agent 192.168.77.12 2
Firewall(config-mgcp-map)# call-agent 192.168.77.13 2
Firewall(config-mgcp-map)# gateway 192.168.100.2 2
Firewall(config-mgcp-map)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect mgcp MyMGCPMap
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring NetBIOS Inspection
![]() The NetBIOS Name Service (NBNS) is a protocol that is used to resolve NetBIOS names to IP addresses. A firewall can inspect NBNS traffic to update embedded IP addresses according to any active address translations. The inspection engine can also monitor the NetBIOS exchanges, to make sure everything follows the RFC that defines NetBIOS.
The NetBIOS Name Service (NBNS) is a protocol that is used to resolve NetBIOS names to IP addresses. A firewall can inspect NBNS traffic to update embedded IP addresses according to any active address translations. The inspection engine can also monitor the NetBIOS exchanges, to make sure everything follows the RFC that defines NetBIOS.
![]() You can use the following steps to configure NetBIOS inspection in ASA 7.2(1) or later:
You can use the following steps to configure NetBIOS inspection in ASA 7.2(1) or later:
-
 (Optional) Define an NetBIOS inspection policy map:
(Optional) Define an NetBIOS inspection policy map: Firewall(config)# policy-map type inspect netbios netbios_pmap_name
Firewall(config)# policy-map type inspect netbios netbios_pmap_name No matching conditions need to be configured for the NetBIOS inspection engine.
No matching conditions need to be configured for the NetBIOS inspection engine. -
 Set NetBIOS parameters:
Set NetBIOS parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table:
First, enter the parameters mode and then configure one or more parameters with the commands shown in the following table: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# protocol-
violation action [drop] log If NetBIOS packets are found to be violating the RFC, drop the connection and/or log it.
If NetBIOS packets are found to be violating the RFC, drop the connection and/or log it. -
 Enable NetBIOS inspection:
Enable NetBIOS inspection: Firewall(config-pmap-c)# inspect netbios [netbios_pmap_name]
Firewall(config-pmap-c)# inspect netbios [netbios_pmap_name] The inspect netbios command must be entered as an action in a policy map. You can also apply a NetBIOS inspection policy map by giving its name as pmap_name.
The inspect netbios command must be entered as an action in a policy map. You can also apply a NetBIOS inspection policy map by giving its name as pmap_name.
Configuring RADIUS Accounting Inspection
![]() RADIUS is a protocol that can be used for user authentication, authorization, and to keep an audit trail of user accounting information. Beginning in ASA 7.2(1), the ASA platform has an application layer inspection engine for RADIUS accounting traffic.
RADIUS is a protocol that can be used for user authentication, authorization, and to keep an audit trail of user accounting information. Beginning in ASA 7.2(1), the ASA platform has an application layer inspection engine for RADIUS accounting traffic.
![]() It is important to maintain the integrity of RADIUS accounting because it usually contains a record of customer activity for billing purposes.
It is important to maintain the integrity of RADIUS accounting because it usually contains a record of customer activity for billing purposes.
![]() You can use the following steps to configure RADIUS accounting inspection in ASA 7.2(1) or later:
You can use the following steps to configure RADIUS accounting inspection in ASA 7.2(1) or later:
-
 (Optional) Define a RADIUS accounting inspection policy map:
(Optional) Define a RADIUS accounting inspection policy map: Firewall(config)# policy-map type inspect radius-accounting radius_pmap_name
Firewall(config)# policy-map type inspect radius-accounting radius_pmap_name No matching conditions need to be configured for the RADIUS accounting inspection engine.
No matching conditions need to be configured for the RADIUS accounting inspection engine. -
 Set RADIUS accounting parameters:
Set RADIUS accounting parameters: Firewall(config-pmap)# parameters
Firewall(config-pmap)# parameters First, enter the parameters mode and then configure one or more parameters with the following commands:
First, enter the parameters mode and then configure one or more parameters with the following commands: Open table as spreadsheet
Open table as spreadsheet Parameter Command Syntax
Parameter Command Syntax Description
Description

Firewall(config-pmap-p)# host hostname
[key key_string] Identify a RADIUS host that will be inspected; hostname can be IP address or a hostname string; key_string can be up to 128 characters long.
Identify a RADIUS host that will be inspected; hostname can be IP address or a hostname string; key_string can be up to 128 characters long.

Firewall(config-pmap-p)# send response Send a RADIUS Accounting-Response Start and Stop messages to the sender of the respective request messages.
Send a RADIUS Accounting-Response Start and Stop messages to the sender of the respective request messages.

Firewall(config-pmap-p)# timeout users
hh:mm:ss Set an inactivity timer for RADIUS accounting users; a timeout of 0:0:0 will tear down the RADIUS accounting connection immediately.
Set an inactivity timer for RADIUS accounting users; a timeout of 0:0:0 will tear down the RADIUS accounting connection immediately.
 Firewall(config-pmap-p)# validate-
Firewall(config-pmap-p)# validate-
attribute attribute_number Validate the RADIUS accounting attribute number (1–191) when it appears in messages. Vendor Specific Attributes (VSA) are not supported.
Validate the RADIUS accounting attribute number (1–191) when it appears in messages. Vendor Specific Attributes (VSA) are not supported. -
 Enable RADIUS accounting inspection:
Enable RADIUS accounting inspection: Firewall(config-pmap-c)# inspect radius-accounting [radius_pmap_name]
Firewall(config-pmap-c)# inspect radius-accounting [radius_pmap_name] The inspect radius-accounting command must be entered as an action in a policy map. You can also apply a RADIUS accounting inspection policy map by giving its name as pmap_name.
The inspect radius-accounting command must be entered as an action in a policy map. You can also apply a RADIUS accounting inspection policy map by giving its name as pmap_name.
![]() As an example, a RADIUS accounting inspection policy is configured to identify the RADIUS host at 192.168.10.10 using the secret key “BigSecretKey”. The inspection engine will always send a Start and Stop message back to the requester, ensuring that the accounting records are not spoofed to exploit spoofing of billing records.
As an example, a RADIUS accounting inspection policy is configured to identify the RADIUS host at 192.168.10.10 using the secret key “BigSecretKey”. The inspection engine will always send a Start and Stop message back to the requester, ensuring that the accounting records are not spoofed to exploit spoofing of billing records.
Firewall(config)# policy-map type inspect radius-accounting MyRADIUSPolicy
Firewall(config-pmap)# parameters
Firewall(config-pmap-p)# host 192.168.10.10 key BigSecretKey
Firewall(config-pmap-p)# send response
Firewall(config-pmap-p)# exit
Firewall(config-pmap)# exit
!
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class class-default
Firewall(config-pmap-c)# inspect radius-accounting MyRADIUSPolicy
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside
Configuring SNMP Inspection
![]() Simple Network Management Protocol (SNMP) is used to monitor and manage devices with an SNMP agent from a management station. By default, all versions of SNMP are allowed to pass through a firewall, as long as SNMP itself (UDP port 161) is permitted.
Simple Network Management Protocol (SNMP) is used to monitor and manage devices with an SNMP agent from a management station. By default, all versions of SNMP are allowed to pass through a firewall, as long as SNMP itself (UDP port 161) is permitted.
![]() You can use the following steps to configure enhanced SNMP inspection, which allows specific versions of SNMP to be denied. For example, SNMPv1 has no mechanisms for security, so your network security policies might not allow that type of traffic to be used.
You can use the following steps to configure enhanced SNMP inspection, which allows specific versions of SNMP to be denied. For example, SNMPv1 has no mechanisms for security, so your network security policies might not allow that type of traffic to be used.
![]() An SNMP map is used with the inspect snmp command to define additional parameters for inspection.
An SNMP map is used with the inspect snmp command to define additional parameters for inspection.
| Tip |
|
-
 Define the SNMP map name:
Define the SNMP map name: Firewall(config)# snmp-map snmp_map_name
Firewall(config)# snmp-map snmp_map_name The SNMP map is named snmp_map_name (up to 64 characters).
The SNMP map is named snmp_map_name (up to 64 characters). -
 Deny a specific SNMP version:
Deny a specific SNMP version: Firewall(config-snmp-map)# deny version {1 | 2 | 2c | 3}
Firewall(config-snmp-map)# deny version {1 | 2 | 2c | 3} You can repeat this command to deny more than one SNMP version.
You can repeat this command to deny more than one SNMP version. -
 Enable SNMP inspection:
Enable SNMP inspection: Firewall(config-pmap-c)# inspect snmp snmp_map_name
Firewall(config-pmap-c)# inspect snmp snmp_map_name The inspect snmp command must be entered as an action in a policy map. You can also apply an SNMP inspection map by giving its name as snmp_map_name.
The inspect snmp command must be entered as an action in a policy map. You can also apply an SNMP inspection map by giving its name as snmp_map_name.
![]() For example, the following commands define an snmp-map that denies packets using SNMP versions 1 and 2 during SNMP inspection. The SNMP map is then applied to the inspect snmp command in a policy map.
For example, the following commands define an snmp-map that denies packets using SNMP versions 1 and 2 during SNMP inspection. The SNMP map is then applied to the inspect snmp command in a policy map.
Firewall(config)# snmp-map Filter_snmp
Firewall(config-snmp-map)# deny version 1
Firewall(config-snmp-map)# deny version 2
Firewall(config-snmp-map)# exit
!
Firewall(config)# class-map _MyClass
Firewall(config-cmap)# match any
Firewall(config-cmap)# exit
Firewall(config)# policy-map MyPolicy
Firewall(config-pmap)# class MyClass
Firewall(config-pmap-c)# inspect snmp Filter_snmp
Firewall(config-pmap-c)# exit
Firewall(config-pmap)# exit
Firewall(config)# service-policy MyPolicy interface outside

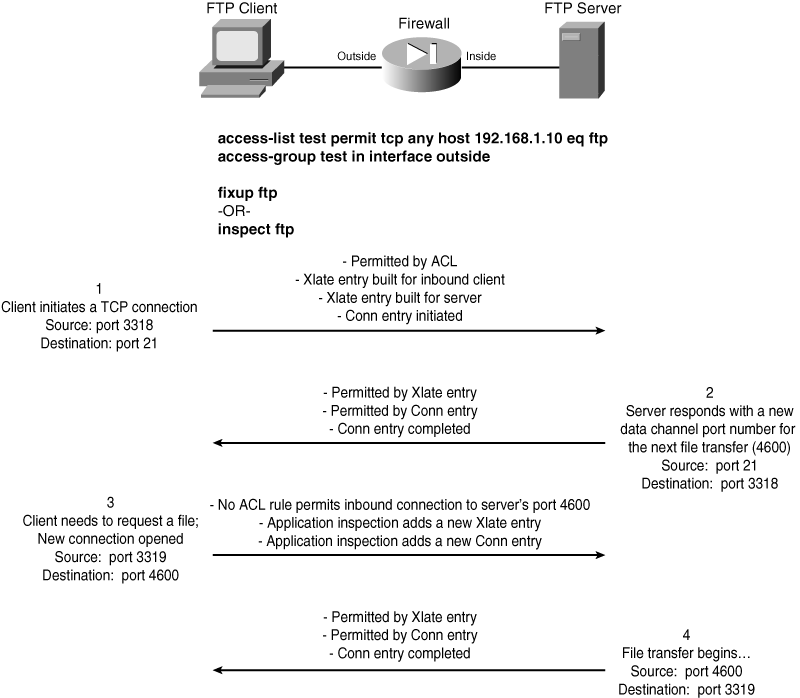
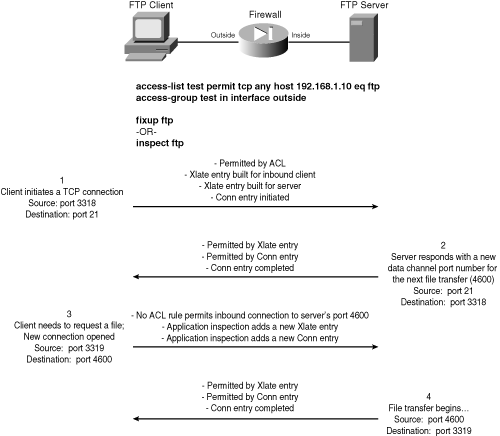

0 comments
Post a Comment