Designing NAC Services
![]() Network Admission Control (NAC) is a set of technologies and solutions built on an industry initiative led by Cisco. NAC uses the network infrastructure to enforce security policy compliance on all devices seeking to access network computing resources, thereby limiting damage from emerging security threats such as viruses, worms, and spyware. Customers using NAC can allow network access to only compliant and trusted endpoint devices (PCs, servers, and personal digital assistants [PDA], for example), and can restrict the access of noncompliant devices.
Network Admission Control (NAC) is a set of technologies and solutions built on an industry initiative led by Cisco. NAC uses the network infrastructure to enforce security policy compliance on all devices seeking to access network computing resources, thereby limiting damage from emerging security threats such as viruses, worms, and spyware. Customers using NAC can allow network access to only compliant and trusted endpoint devices (PCs, servers, and personal digital assistants [PDA], for example), and can restrict the access of noncompliant devices.
Network Security with Access Control
![]() Cisco Identity Based Networking Services (IBNS) is an integrated solution combining several Cisco products that offer authentication, access control, and user policies to secure network connectivity and resources. The Cisco IBNS solution enables greater security while simultaneously offering cost-effective management of changes throughout the organization. The Cisco IBNS framework allows enterprises to manage user mobility and reduce the overhead costs associated with granting and managing access to network resources. IEEE 802.1x authenticates clients requesting Layer 2 (data link layer) access to the network. However, with Cisco 802.1x, users and devices are authenticated and allowed admission to the network based on who or what they are, but not their condition.
Cisco Identity Based Networking Services (IBNS) is an integrated solution combining several Cisco products that offer authentication, access control, and user policies to secure network connectivity and resources. The Cisco IBNS solution enables greater security while simultaneously offering cost-effective management of changes throughout the organization. The Cisco IBNS framework allows enterprises to manage user mobility and reduce the overhead costs associated with granting and managing access to network resources. IEEE 802.1x authenticates clients requesting Layer 2 (data link layer) access to the network. However, with Cisco 802.1x, users and devices are authenticated and allowed admission to the network based on who or what they are, but not their condition.
![]() NAC helps ensure that only healthy client devices, such as workstations and end-user PCs, are granted full network access. The Cisco NAC Appliance Agent (NAA) loaded on the client device queries antivirus, patch management, and personal firewall client software to assess the condition or posture of a client device before allowing that device to access the network. NAC helps ensure that a network client has an up-to-date virus signature set, the most current operating system patches, and is not infected. If the client requires an antivirus signature update or an operating system update, NAC directs the client to complete the necessary updates before allowing access to the protected network resources. If the client has been compromised or if a virus outbreak is occurring on the network, NAC places the client into a quarantined network segment. After the client has completed its update process or disinfection, the client is checked again. Clients with a healthy status are permitted normal network access.
NAC helps ensure that only healthy client devices, such as workstations and end-user PCs, are granted full network access. The Cisco NAC Appliance Agent (NAA) loaded on the client device queries antivirus, patch management, and personal firewall client software to assess the condition or posture of a client device before allowing that device to access the network. NAC helps ensure that a network client has an up-to-date virus signature set, the most current operating system patches, and is not infected. If the client requires an antivirus signature update or an operating system update, NAC directs the client to complete the necessary updates before allowing access to the protected network resources. If the client has been compromised or if a virus outbreak is occurring on the network, NAC places the client into a quarantined network segment. After the client has completed its update process or disinfection, the client is checked again. Clients with a healthy status are permitted normal network access.
![]() Cisco 802.1x/IBNS/and NAC provide complementary functions: user authentication and posture validation. Both can provide per-user group VLAN assignment and access control.
Cisco 802.1x/IBNS/and NAC provide complementary functions: user authentication and posture validation. Both can provide per-user group VLAN assignment and access control.
NAC Comparison
![]() Cisco supports two types of NAC, as illustrated in Figure 8-14 and in this list:
Cisco supports two types of NAC, as illustrated in Figure 8-14 and in this list:
-
 Cisco NAC Framework is a technology standard that integrates an intelligent network infrastructure with solutions from more than 60 manufacturers of leading antivirus and other security and management software solutions to enforce security policy compliance on all devices seeking to access network computing resources. NAC Framework is embedded software within NAC-enabled products that provides ubiquitous control across all network access methods. Posture information can be gathered and access policy enforced for hosts attempting network access through routers, switches, wireless access points, and VPN concentrators. NAC Framework leverages multiple Cisco products and vendor products that support NAC.
Cisco NAC Framework is a technology standard that integrates an intelligent network infrastructure with solutions from more than 60 manufacturers of leading antivirus and other security and management software solutions to enforce security policy compliance on all devices seeking to access network computing resources. NAC Framework is embedded software within NAC-enabled products that provides ubiquitous control across all network access methods. Posture information can be gathered and access policy enforced for hosts attempting network access through routers, switches, wireless access points, and VPN concentrators. NAC Framework leverages multiple Cisco products and vendor products that support NAC. -
 Cisco NAC Appliance (formerly called Cisco Clean Access) is a turnkey solution for controlling and securing networks. Cisco NAC Appliance condenses NAC capabilities into an appliance. Cisco NAC Appliance client, server, and manager products enable network administrators to authenticate, authorize, evaluate, and remediate wired, wireless, and remote users and their machines before allowing users onto the network. Cisco NAC Appliance identifies whether networked devices such as laptops, IP phones, PDAs, or printers comply with the security policies of an organization, and repairs any vulnerabilities before permitting access to the network.
Cisco NAC Appliance (formerly called Cisco Clean Access) is a turnkey solution for controlling and securing networks. Cisco NAC Appliance condenses NAC capabilities into an appliance. Cisco NAC Appliance client, server, and manager products enable network administrators to authenticate, authorize, evaluate, and remediate wired, wireless, and remote users and their machines before allowing users onto the network. Cisco NAC Appliance identifies whether networked devices such as laptops, IP phones, PDAs, or printers comply with the security policies of an organization, and repairs any vulnerabilities before permitting access to the network.
Cisco NAC Appliance Fundamentals
![]() This topic discusses fundamentals of the Cisco NAC Appliance, including components and terminology.
This topic discusses fundamentals of the Cisco NAC Appliance, including components and terminology.
 Cisco NAC Appliance Components
Cisco NAC Appliance Components
![]() Cisco NAC Appliance provides admission control and enforces compliance.
Cisco NAC Appliance provides admission control and enforces compliance.
![]() Cisco NAC Appliance comprises four components:
Cisco NAC Appliance comprises four components:
-
 Cisco NAC Appliance Manager (Cisco NAM): The administration server for Cisco NAC Appliance deployment where the policies are defined. The secure web console of the Cisco NAM is the single point of management for up to 20 Cisco NAC Appliance Server (NAS) devices in a deployment (or 40 Cisco NAS devices in a super-NAM installation). Cisco NAM acts as the authentication proxy to the authentication servers that reside on the back end. For out-of-band (OOB) deployment, the Cisco NAM console allows control of switches and VLAN assignment of user ports through the use of SNMP.
Cisco NAC Appliance Manager (Cisco NAM): The administration server for Cisco NAC Appliance deployment where the policies are defined. The secure web console of the Cisco NAM is the single point of management for up to 20 Cisco NAC Appliance Server (NAS) devices in a deployment (or 40 Cisco NAS devices in a super-NAM installation). Cisco NAM acts as the authentication proxy to the authentication servers that reside on the back end. For out-of-band (OOB) deployment, the Cisco NAM console allows control of switches and VLAN assignment of user ports through the use of SNMP. -
 Cisco NAC Appliance Server (Cisco NAS): The enforcement server between the untrusted (managed) network and the trusted network. Cisco NAS enforces the policies defined in the Cisco NAM web console, including network access privileges, authentication requirements, bandwidth restrictions, and Cisco NAC Appliance system requirements. It can be deployed in-band (always in line with user traffic) or OOB (in line with user traffic only during authentication and posture assessment). It can also be deployed in Layer 2 mode (users are adjacent to Cisco NAS) or Layer 3 mode (users are multiple hops away from the Cisco NAS).
Cisco NAC Appliance Server (Cisco NAS): The enforcement server between the untrusted (managed) network and the trusted network. Cisco NAS enforces the policies defined in the Cisco NAM web console, including network access privileges, authentication requirements, bandwidth restrictions, and Cisco NAC Appliance system requirements. It can be deployed in-band (always in line with user traffic) or OOB (in line with user traffic only during authentication and posture assessment). It can also be deployed in Layer 2 mode (users are adjacent to Cisco NAS) or Layer 3 mode (users are multiple hops away from the Cisco NAS). -
 Cisco NAC Appliance Agent (Cisco NAA): An optional read-only agent that resides on Microsoft Windows clients. Cisco NAA checks applications, files, services, or Registry keys to ensure that clients meet specified network and software requirements before gaining access to the network.
Cisco NAC Appliance Agent (Cisco NAA): An optional read-only agent that resides on Microsoft Windows clients. Cisco NAA checks applications, files, services, or Registry keys to ensure that clients meet specified network and software requirements before gaining access to the network. -
 Cisco NAC Appliance policy updates: Regular updates of prepackaged policies and rules that can be used to check the up-to-date status of operating systems and antivirus, antispyware, and other client software. The Cisco NAC Appliance policy updates currently provide built-in support for 24 antivirus vendors and 17 antispyware vendors.
Cisco NAC Appliance policy updates: Regular updates of prepackaged policies and rules that can be used to check the up-to-date status of operating systems and antivirus, antispyware, and other client software. The Cisco NAC Appliance policy updates currently provide built-in support for 24 antivirus vendors and 17 antispyware vendors.
 Cisco NAC Appliance Policy Updates
Cisco NAC Appliance Policy Updates
![]() Cisco provides automatic security policy updates as part of the standard software maintenance package. These updates deliver predefined policies for the most common network access criteria, including policies that check for critical operating system updates, common antivirus software virus definition updates, and common antispyware definition updates.
Cisco provides automatic security policy updates as part of the standard software maintenance package. These updates deliver predefined policies for the most common network access criteria, including policies that check for critical operating system updates, common antivirus software virus definition updates, and common antispyware definition updates.
![]() The Cisco NAC Appliance is preconfigured to offer policy checks for more than 200 applications from 50 vendors.
The Cisco NAC Appliance is preconfigured to offer policy checks for more than 200 applications from 50 vendors.
| Note |
|
![]() In addition to the preconfigured checks, the customer has full access to the Cisco NAC Appliance rules engine and can create any custom check or rule for any other third-party application.
In addition to the preconfigured checks, the customer has full access to the Cisco NAC Appliance rules engine and can create any custom check or rule for any other third-party application.
 Process Flow with the Cisco NAC Appliance
Process Flow with the Cisco NAC Appliance
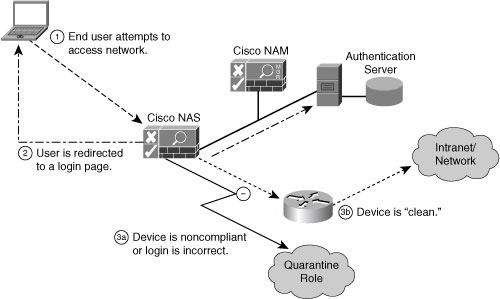
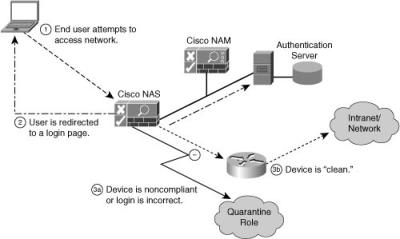
![]() Figure 8-15 illustrates the process flow with the Cisco NAC Appliance.
Figure 8-15 illustrates the process flow with the Cisco NAC Appliance.
![]() Following are the steps of the process:
Following are the steps of the process:
|
|
| |||
|
|
| |||
|
|
| |||
|
|
|
Cisco NAS Scaling
![]() There are three levels of Cisco NAM for supporting Cisco NAC Appliance solutions:
There are three levels of Cisco NAM for supporting Cisco NAC Appliance solutions:
-
 Cisco NAC Appliance Lite Manager manages up to 3 Cisco NAS devices, supporting 100, 250, or 500 users per server.
Cisco NAC Appliance Lite Manager manages up to 3 Cisco NAS devices, supporting 100, 250, or 500 users per server. -
 Cisco NAC Appliance Standard Manager manages up to 20 Cisco NAS devices supporting from 1500 to 3500 users per (NAS) depending on which model is deployed.
Cisco NAC Appliance Standard Manager manages up to 20 Cisco NAS devices supporting from 1500 to 3500 users per (NAS) depending on which model is deployed. -
 Cisco NAC Appliance Super Manager manages up to 40 Cisco NAS devices supporting from 1500 to 3500 users per (NAS) depending on which model is deployed.
Cisco NAC Appliance Super Manager manages up to 40 Cisco NAS devices supporting from 1500 to 3500 users per (NAS) depending on which model is deployed.
![]() The number of users supported on a server is a measure of concurrent users that have been scanned for posture compliance, not network devices such as printers or IP phones.
The number of users supported on a server is a measure of concurrent users that have been scanned for posture compliance, not network devices such as printers or IP phones.
![]() The number of users supported per server is influenced by many factors that consume CPU and server resources:
The number of users supported per server is influenced by many factors that consume CPU and server resources:
-
 The number of new user authentications per second
The number of new user authentications per second -
 The number of posture assessments per second
The number of posture assessments per second -
 How many checks are in each posture assessment
How many checks are in each posture assessment -
 The number of agentless network scans per second
The number of agentless network scans per second -
 The number of plug-ins per scan
The number of plug-ins per scan -
 Rescan timer intervals
Rescan timer intervals -
 Per-role and total online timer intervals
Per-role and total online timer intervals -
 Bandwidth controls
Bandwidth controls -
 Filters and access controls
Filters and access controls
| Note |
|
Cisco NAS Deployment Options
![]() This topic describes the deployment options for Cisco NAS.
This topic describes the deployment options for Cisco NAS.
![]() There are four deployment variables with Cisco NAS deployments:
There are four deployment variables with Cisco NAS deployments:
-
 Virtual or real gateway mode: Determines whether the Cisco NAS acts as a Layer 2 or Layer 3 device in the network
Virtual or real gateway mode: Determines whether the Cisco NAS acts as a Layer 2 or Layer 3 device in the network -
 In-band or out-of-band operating mode: Defines when traffic flows through the Cisco NAS
In-band or out-of-band operating mode: Defines when traffic flows through the Cisco NAS -
 Layer 2 or Layer 3 client access mode: Defines whether user devices are Layer 2 or Layer 3 adjacent to the Cisco NAS
Layer 2 or Layer 3 client access mode: Defines whether user devices are Layer 2 or Layer 3 adjacent to the Cisco NAS -
 Central or edge physical deployment: Determines whether the Cisco NAS device is physically in line with the traffic path
Central or edge physical deployment: Determines whether the Cisco NAS device is physically in line with the traffic path
 Cisco NAS Gateway Modes
Cisco NAS Gateway Modes
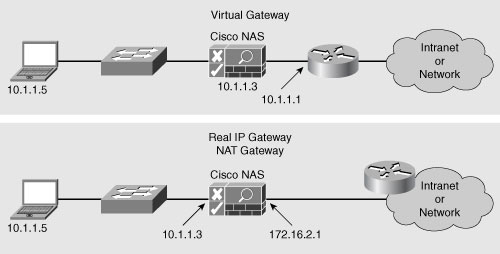
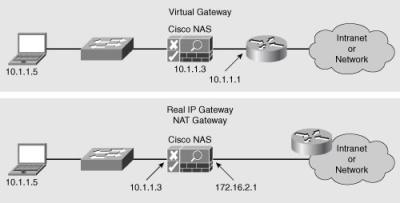
![]() There are three Cisco NAS gateway modes, as shown in Figure 8-16.
There are three Cisco NAS gateway modes, as shown in Figure 8-16.
![]() The Cisco NAS can operate as a logical Layer 2 or Layer 3 network device depending on the gateway mode configured.
The Cisco NAS can operate as a logical Layer 2 or Layer 3 network device depending on the gateway mode configured.
-
 Virtual gateway mode: Cisco NAS operates as a standard Layer 2 Ethernet bridge, but with added functionality provided by the IP filter and IP Security (IPsec) module. This configuration is typically used when the untrusted network already has a Layer 3 gateway. It is the most common deployment option.
Virtual gateway mode: Cisco NAS operates as a standard Layer 2 Ethernet bridge, but with added functionality provided by the IP filter and IP Security (IPsec) module. This configuration is typically used when the untrusted network already has a Layer 3 gateway. It is the most common deployment option. -
 Real IP gateway mode: Cisco NAS operates as the Layer 3 default gateway for untrusted network (managed) clients. All traffic between the untrusted and trusted network passes through Cisco NAS, which applies the IP filtering rules, access policies, and any other traffic-handling mechanisms that are configured. Cisco NAS is designated as a static route for the managed subnet and can perform DHCP services or act as a DHCP relay.
Real IP gateway mode: Cisco NAS operates as the Layer 3 default gateway for untrusted network (managed) clients. All traffic between the untrusted and trusted network passes through Cisco NAS, which applies the IP filtering rules, access policies, and any other traffic-handling mechanisms that are configured. Cisco NAS is designated as a static route for the managed subnet and can perform DHCP services or act as a DHCP relay. -
 NAT gateway mode: Cisco NAS functions similarly to the way it does in the real IP gateway configuration, as a Layer 3 gateway, but with added NAT services. With NAT, clients are assigned IP addresses dynamically from a private address pool. The Cisco NAS performs the translation between the private and public addresses as traffic is routed between the untrusted (managed) and external network. Cisco NAS supports standard, dynamic, and one-to-one NAT. In one-to-one NAT, a one-to-one correlation exists between public and private addresses and port numbers, and IP addresses can be mapped for translation.
NAT gateway mode: Cisco NAS functions similarly to the way it does in the real IP gateway configuration, as a Layer 3 gateway, but with added NAT services. With NAT, clients are assigned IP addresses dynamically from a private address pool. The Cisco NAS performs the translation between the private and public addresses as traffic is routed between the untrusted (managed) and external network. Cisco NAS supports standard, dynamic, and one-to-one NAT. In one-to-one NAT, a one-to-one correlation exists between public and private addresses and port numbers, and IP addresses can be mapped for translation.
![]() The installation type and operating mode determines the services Cisco NAS will provide. For example, Cisco NAS can operate as a bridge between the untrusted and trusted network, or it can operate as a gateway for the untrusted network.
The installation type and operating mode determines the services Cisco NAS will provide. For example, Cisco NAS can operate as a bridge between the untrusted and trusted network, or it can operate as a gateway for the untrusted network.
 Cisco NAS Operating Modes
Cisco NAS Operating Modes
![]() Cisco NAS has two traffic flow deployment models: in-band or out-of-band.
Cisco NAS has two traffic flow deployment models: in-band or out-of-band.
![]() Any Cisco NAS can be configured for either method, but only one Cisco NAS method can be deployed at a time. Selection of mode is based on whether the customer wants to remove the Cisco NAS from the data path after posture assessment.
Any Cisco NAS can be configured for either method, but only one Cisco NAS method can be deployed at a time. Selection of mode is based on whether the customer wants to remove the Cisco NAS from the data path after posture assessment.
![]() In-band traffic flow is the easiest deployment option. The Cisco NAS remains in the traffic path before and after posture assessment. In-band operation provides ongoing ACL filtering and bandwidth throttling, and role-based access control.
In-band traffic flow is the easiest deployment option. The Cisco NAS remains in the traffic path before and after posture assessment. In-band operation provides ongoing ACL filtering and bandwidth throttling, and role-based access control.
![]() In out-of-band traffic flow, the Cisco NAS is in the traffic path only during the posture assessment. Out-of-band mode provides VLAN port-based and role-based access control. ACL filtering and bandwidth throttling are provided only during posture assessment.
In out-of-band traffic flow, the Cisco NAS is in the traffic path only during the posture assessment. Out-of-band mode provides VLAN port-based and role-based access control. ACL filtering and bandwidth throttling are provided only during posture assessment.
| Note |
|
 Cisco NAS Client Access Modes
Cisco NAS Client Access Modes
![]() The client access deployment mode selection is based on whether the client is Layer 2 adjacent to the Cisco NAS.
The client access deployment mode selection is based on whether the client is Layer 2 adjacent to the Cisco NAS.
-
 Layer 2 mode: The MAC address of the client device is used to uniquely identify the device. This mode supports both virtual and real IP gateway operations in both in-band and out-of-band deployments. This is the most common deployment model for LANs.
Layer 2 mode: The MAC address of the client device is used to uniquely identify the device. This mode supports both virtual and real IP gateway operations in both in-band and out-of-band deployments. This is the most common deployment model for LANs. -
 Layer 3 mode: The client device is not Layer 2 adjacent to the Cisco NAS. The IP address (and MAC address, starting with Cisco NAA Version 4.0 in Layer 3 OOB applications) of the client is used to identify the device. This mode supports both virtual and real IP gateway operations with in-band and out-of-band deployments.
Layer 3 mode: The client device is not Layer 2 adjacent to the Cisco NAS. The IP address (and MAC address, starting with Cisco NAA Version 4.0 in Layer 3 OOB applications) of the client is used to identify the device. This mode supports both virtual and real IP gateway operations with in-band and out-of-band deployments.
![]() Any Cisco NAS can be configured for either client access method, but only one Cisco NAS method can be configured at a time. Client access mode is configured independently from Cisco NAS operating mode.
Any Cisco NAS can be configured for either client access method, but only one Cisco NAS method can be configured at a time. Client access mode is configured independently from Cisco NAS operating mode.
 Physical Deployment Models
Physical Deployment Models
![]() The edge deployment model is the easiest physical deployment option to understand. The Cisco NAS is physically and logically in line to the traffic path. VLAN IDs are passed straight through the device when in virtual gateway mode. This deployment option can become complex when there are multiple access closets.
The edge deployment model is the easiest physical deployment option to understand. The Cisco NAS is physically and logically in line to the traffic path. VLAN IDs are passed straight through the device when in virtual gateway mode. This deployment option can become complex when there are multiple access closets.
![]() The central deployment model is the most common option and the easiest deployment option. In this option, the Cisco NAS is logically in line, but not physically in line. The VLAN IDs need to be mapped across the Cisco NAS when in virtual gateway mode. This deployment option is the most scalable option for large environments because each Cisco NAS can support devices from multiple access switches.
The central deployment model is the most common option and the easiest deployment option. In this option, the Cisco NAS is logically in line, but not physically in line. The VLAN IDs need to be mapped across the Cisco NAS when in virtual gateway mode. This deployment option is the most scalable option for large environments because each Cisco NAS can support devices from multiple access switches.
Cisco NAC Appliance Designs
![]() This topic reviews some common Cisco NAC Appliance designs.
This topic reviews some common Cisco NAC Appliance designs.
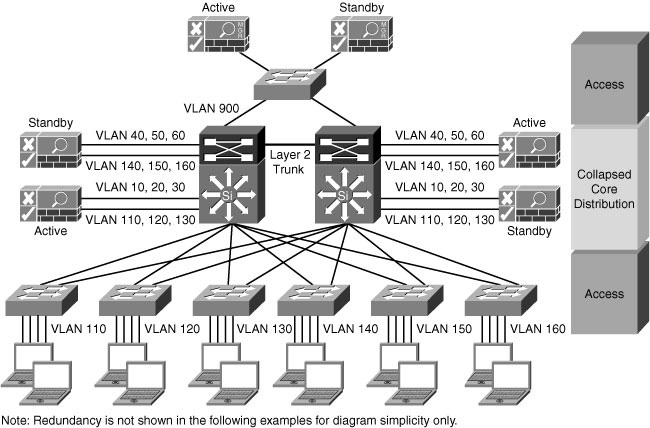
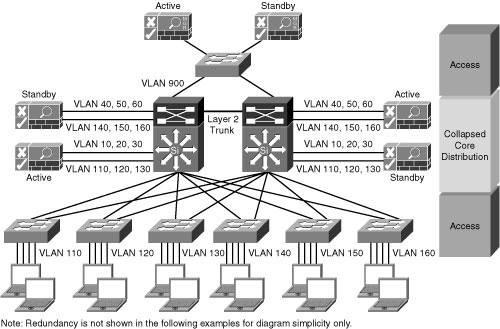
![]() As a recommended practice, the Cisco NAC Appliance solutions are implemented with full redundancy. A failover bundle is either a pair of Cisco NAM devices or NAS devices. The Cisco NAM failover bundle provides management redundancy. The Cisco NAS failover bundle provides redundant Cisco NAS operations for the protected devices.
As a recommended practice, the Cisco NAC Appliance solutions are implemented with full redundancy. A failover bundle is either a pair of Cisco NAM devices or NAS devices. The Cisco NAM failover bundle provides management redundancy. The Cisco NAS failover bundle provides redundant Cisco NAS operations for the protected devices.
![]() In the Figure 8-17, the network has two sets of Cisco NAS failover bundles. One Cisco NAS failover bundle supports devices on VLANs 110, 120, and 130. The other Cisco NAS failover bundle supports devices on VLANs 140, 150, and 160. All components in the design are in an active/standby state. Each failover bundle shares a virtual MAC and virtual IP address. Because of the shared MAC address, Layer 2 connectivity is required between components. The redundant distribution switches are interconnected with a Layer 2 trunk.
In the Figure 8-17, the network has two sets of Cisco NAS failover bundles. One Cisco NAS failover bundle supports devices on VLANs 110, 120, and 130. The other Cisco NAS failover bundle supports devices on VLANs 140, 150, and 160. All components in the design are in an active/standby state. Each failover bundle shares a virtual MAC and virtual IP address. Because of the shared MAC address, Layer 2 connectivity is required between components. The redundant distribution switches are interconnected with a Layer 2 trunk.
| Note |
|
![]() Cisco NAM devices connect to the redundant distribution switches and support all the Cisco NAS devices in the network.
Cisco NAM devices connect to the redundant distribution switches and support all the Cisco NAS devices in the network.
| Note |
|
 Layer 2 In-Band Designs
Layer 2 In-Band Designs
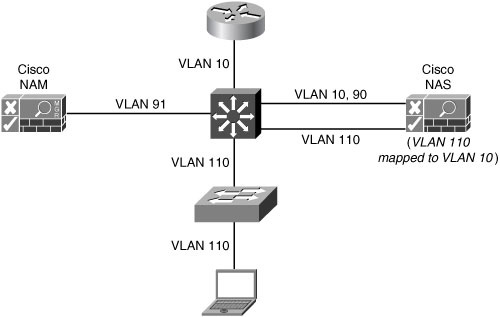
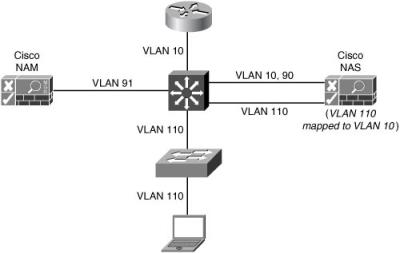
![]() The Layer 2 in-band topology is the most common deployment option. The Cisco NAS is logically in line with the client traffic, but is not physically in line. When the virtual gateway mode is implemented, the VLAN IDs are mapped by the Cisco NAS.
The Layer 2 in-band topology is the most common deployment option. The Cisco NAS is logically in line with the client traffic, but is not physically in line. When the virtual gateway mode is implemented, the VLAN IDs are mapped by the Cisco NAS.
![]() In Figure 8-18, VLAN 110 is mapped to VLAN 10 by the Cisco NAS. All client traffic passes through the Cisco NAS. The Cisco NAS securely manages all traffic after posture assessment. The MAC address of the client is used to identify the device. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and the NAM.
In Figure 8-18, VLAN 110 is mapped to VLAN 10 by the Cisco NAS. All client traffic passes through the Cisco NAS. The Cisco NAS securely manages all traffic after posture assessment. The MAC address of the client is used to identify the device. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and the NAM.
![]() This is the most scalable design in large environments, because this design can be transparently implemented in the existing network supporting multiple access layer switches. It will support all network infrastructure equipment. The Cisco NAS supports per-user ACLs.
This is the most scalable design in large environments, because this design can be transparently implemented in the existing network supporting multiple access layer switches. It will support all network infrastructure equipment. The Cisco NAS supports per-user ACLs.
Example: Layer 2 In-Band Virtual Gateway
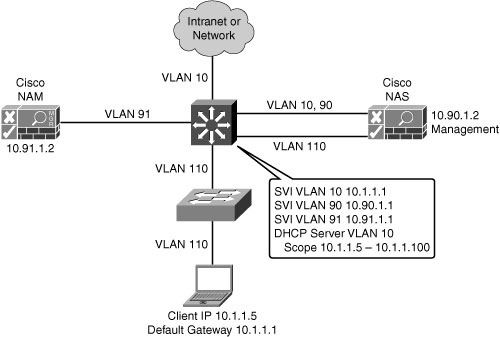
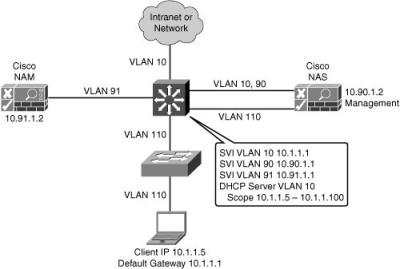
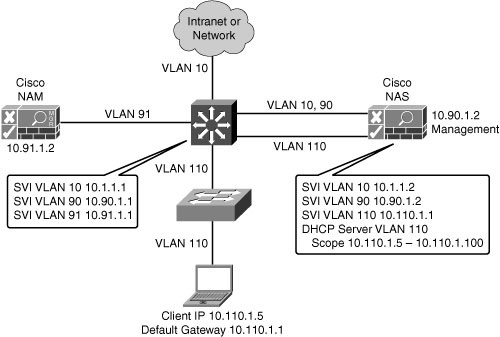
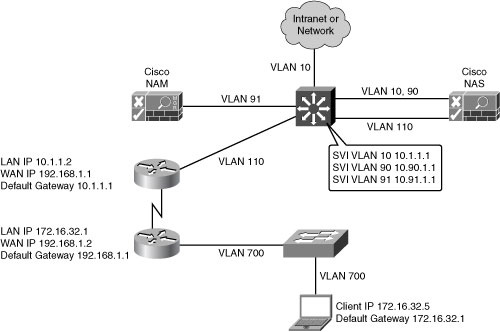
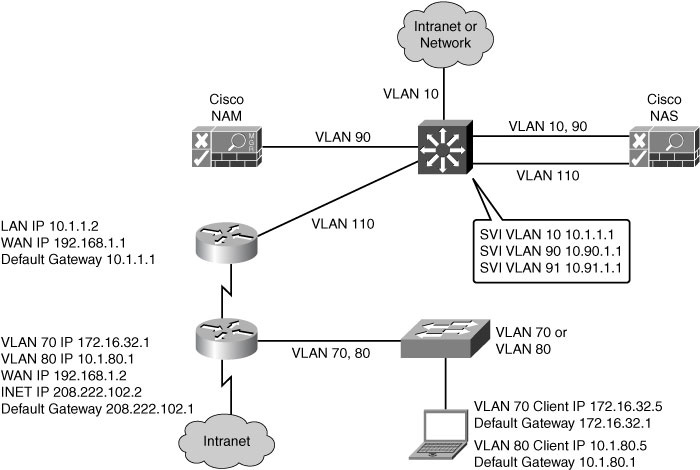
![]() Figure 8-19 illustrates a Layer 2 in-band virtual gateway design. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and NAM. The Layer 3 distribution switch has switch virtual interfaces (SVI) for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the DHCP server and the default gateway for the access layer devices. The existing IP addressing in the network is not changed when the virtual gateway is implemented.
Figure 8-19 illustrates a Layer 2 in-band virtual gateway design. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and NAM. The Layer 3 distribution switch has switch virtual interfaces (SVI) for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the DHCP server and the default gateway for the access layer devices. The existing IP addressing in the network is not changed when the virtual gateway is implemented.
Example: Layer 2 In-Band Real IP Gateway
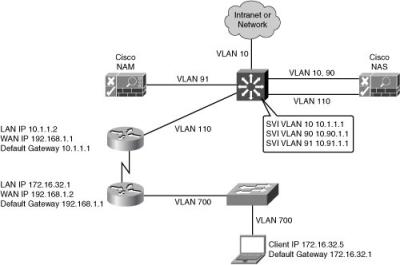
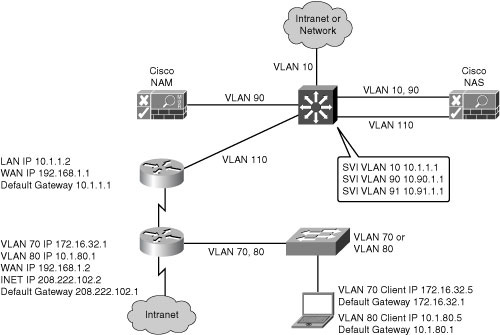
![]() Figure 8-20 illustrates a Layer 2 in-band real IP gateway design. The Cisco NAS is now the DHCP server and the default gateway for the access layer devices. The Cisco NAS has static routes to the other subnets in the organization. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The existing IP addressing in the network changes when the real IP gateway is implemented. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and NAM.
Figure 8-20 illustrates a Layer 2 in-band real IP gateway design. The Cisco NAS is now the DHCP server and the default gateway for the access layer devices. The Cisco NAS has static routes to the other subnets in the organization. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The existing IP addressing in the network changes when the real IP gateway is implemented. VLAN 90 and VLAN 91 are the management VLANs for the Cisco NAS and NAM.
 Layer 2 Out-of-Band Designs
Layer 2 Out-of-Band Designs
![]() The connections of the Layer 2 out-of-band design are similar to the Layer 2 in-band design, except that the link from the access switch to the distribution switch is now a trunk supporting both the posture assessment VLAN and the network access VLAN.
The connections of the Layer 2 out-of-band design are similar to the Layer 2 in-band design, except that the link from the access switch to the distribution switch is now a trunk supporting both the posture assessment VLAN and the network access VLAN.
![]() The client is in line with the Cisco NAS before and during posture assessment. The user VLAN is changed and Cisco NAS is bypassed only after a successful login and assessment. The Cisco NAS securely manages traffic only during assessment. ACLs to manage users need to be applied to the user-assigned VLAN, not the Cisco NAS, because after posture assessment, user traffic does not pass through the Cisco NAS.
The client is in line with the Cisco NAS before and during posture assessment. The user VLAN is changed and Cisco NAS is bypassed only after a successful login and assessment. The Cisco NAS securely manages traffic only during assessment. ACLs to manage users need to be applied to the user-assigned VLAN, not the Cisco NAS, because after posture assessment, user traffic does not pass through the Cisco NAS.
| Note |
|
![]() This design requires use of supported out-of-band switches such as the Cisco Catalyst series 2950, 2960, 3500XL, 3550, 3560, 3750, 4500, and 6500 switches with the appropriate software image.
This design requires use of supported out-of-band switches such as the Cisco Catalyst series 2950, 2960, 3500XL, 3550, 3560, 3750, 4500, and 6500 switches with the appropriate software image.
| Note |
|
![]() Cisco NAM uses SNMP for traps to detect user access and perform switch configuration.
Cisco NAM uses SNMP for traps to detect user access and perform switch configuration.
Example: Layer 2 Out-of-Band Virtual Gateway
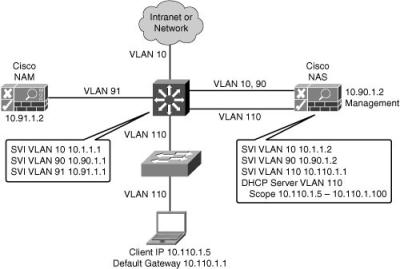
![]() Figure 8-21 shows addressing with a Layer 3 out-of-band virtual gateway design. Cisco NAS maps traffic from VLAN 110 to VLAN 10 during the posture assessment. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the DHCP server, and the default gateway for the access layer devices. The existing IP addressing in the network is not changed when the virtual gateway is implemented.
Figure 8-21 shows addressing with a Layer 3 out-of-band virtual gateway design. Cisco NAS maps traffic from VLAN 110 to VLAN 10 during the posture assessment. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the DHCP server, and the default gateway for the access layer devices. The existing IP addressing in the network is not changed when the virtual gateway is implemented.
 Layer 3 In-Band Designs
Layer 3 In-Band Designs
![]() In the Layer 3 in-band topology, the client device is not adjacent to the Cisco NAS. The IP address of the client is used to identify the device because the MAC address provided to the Cisco NAS is not from the client. This design is used to securely manage traffic from remote sites or for VPN concentrators.
In the Layer 3 in-band topology, the client device is not adjacent to the Cisco NAS. The IP address of the client is used to identify the device because the MAC address provided to the Cisco NAS is not from the client. This design is used to securely manage traffic from remote sites or for VPN concentrators.
Example: Layer 3 In-Band Virtual Gateway
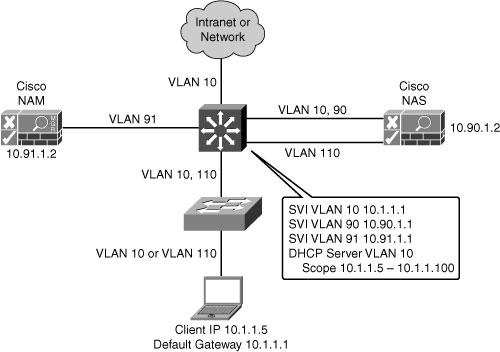
![]() Figure 8-22 illustrates a Layer 3 in-band virtual gateway design. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the default gateway for the access layer devices. The DHCP server is typically a remote router.
Figure 8-22 illustrates a Layer 3 in-band virtual gateway design. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. The Layer 3 distribution switch has SVIs for the VLANs connecting to the Cisco NAM, NAS, and access switches. The distribution switch is the default gateway for the access layer devices. The DHCP server is typically a remote router.
![]() All traffic from the remote site goes through Cisco NAS.
All traffic from the remote site goes through Cisco NAS.
![]() This design also supports VPN concentrators. Instead of the remote router pair, the VPN concentrator connects to the distribution switch. Traffic from the VPN concentrator is forwarded through the Cisco NAS for posture assessment and management.
This design also supports VPN concentrators. Instead of the remote router pair, the VPN concentrator connects to the distribution switch. Traffic from the VPN concentrator is forwarded through the Cisco NAS for posture assessment and management.
Example: Layer 3 In-Band with Multiple Remotes
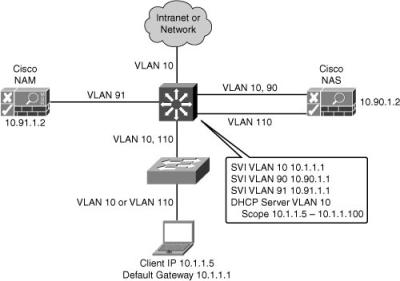
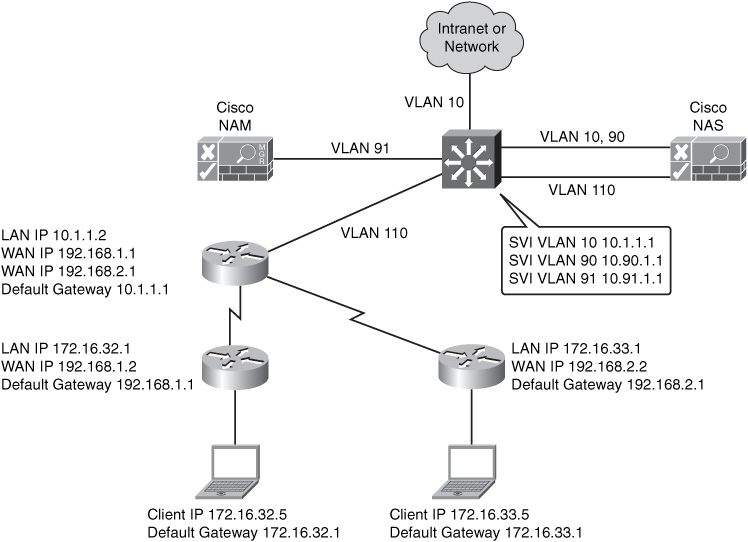
![]() Figure 8-23 illustrates a Layer 3 in-band virtual gateway design with multiple remote sites. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. Traffic to centralized hosts and Internet goes through Cisco NAS.
Figure 8-23 illustrates a Layer 3 in-band virtual gateway design with multiple remote sites. The Cisco NAS maps traffic from VLAN 110 to VLAN 10. Traffic to centralized hosts and Internet goes through Cisco NAS.
| Note |
|
 Layer 3 Out-of-Band Designs
Layer 3 Out-of-Band Designs
![]() Layer 3 support for out-of-band deployments enables administrators to deploy Cisco NAS out-of-band centrally in the core or distribution layer to support users behind Layer 3 access switches and remote users behind WAN routers in some instances. With Layer 3 out-of-band, users who are multiple Layer 3 hops away from Cisco NAS can be supported for authentication and posture assessment. After authentication and posture assessment, the client traffic no longer passes through the Cisco NAS.
Layer 3 support for out-of-band deployments enables administrators to deploy Cisco NAS out-of-band centrally in the core or distribution layer to support users behind Layer 3 access switches and remote users behind WAN routers in some instances. With Layer 3 out-of-band, users who are multiple Layer 3 hops away from Cisco NAS can be supported for authentication and posture assessment. After authentication and posture assessment, the client traffic no longer passes through the Cisco NAS.
![]() With the Layer 3 out-of-band topology, the IP address (and MAC address, starting with Cisco NAA Version 4 Layer 3 out-of-band applications) of the client is used to identify the device, because the MAC address (before the Cisco NAA Version 4 client) provided to the Cisco NAS is from the last-hop router. This design requires use of supported out-of-band switches such as the Cisco Catalyst series 2950, 2960, 3500XL, 3550, 3560, 3750, 4500, and 6500 switches with the appropriate software image. The NAM uses SNMP for traps and switch configuration. PBR is needed to direct the user traffic appropriately.
With the Layer 3 out-of-band topology, the IP address (and MAC address, starting with Cisco NAA Version 4 Layer 3 out-of-band applications) of the client is used to identify the device, because the MAC address (before the Cisco NAA Version 4 client) provided to the Cisco NAS is from the last-hop router. This design requires use of supported out-of-band switches such as the Cisco Catalyst series 2950, 2960, 3500XL, 3550, 3560, 3750, 4500, and 6500 switches with the appropriate software image. The NAM uses SNMP for traps and switch configuration. PBR is needed to direct the user traffic appropriately.
| Note |
|
Example: Layer 3 OOB with Addressing
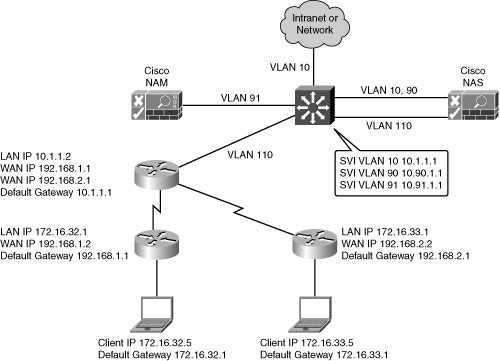
![]() Figure 8-24 shows an example of addressing with a Layer 3 out-of-band virtual gateway design supporting remote users. Cisco NAS maps traffic from VLAN 110 to VLAN 10 during the posture assessment. The Layer 3 distribution switch has SVIs for the VLANs connecting to Cisco NAM, NAS, and access switches. The remote-site edge router is the DHCP server and the default gateway for the client devices. The remote-site edge router uses a trunk to the remote-access switch to support either the production VLAN or the posture assessment VLAN. PBR is used to direct the user traffic appropriately.
Figure 8-24 shows an example of addressing with a Layer 3 out-of-band virtual gateway design supporting remote users. Cisco NAS maps traffic from VLAN 110 to VLAN 10 during the posture assessment. The Layer 3 distribution switch has SVIs for the VLANs connecting to Cisco NAM, NAS, and access switches. The remote-site edge router is the DHCP server and the default gateway for the client devices. The remote-site edge router uses a trunk to the remote-access switch to support either the production VLAN or the posture assessment VLAN. PBR is used to direct the user traffic appropriately.
NAC Framework Overview
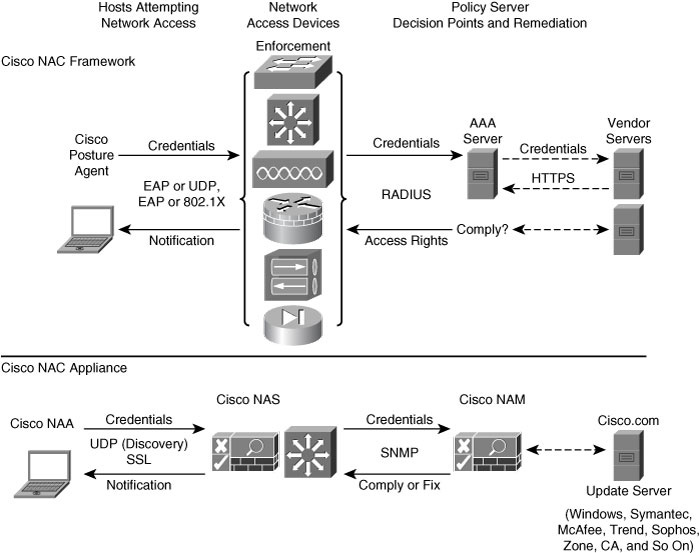
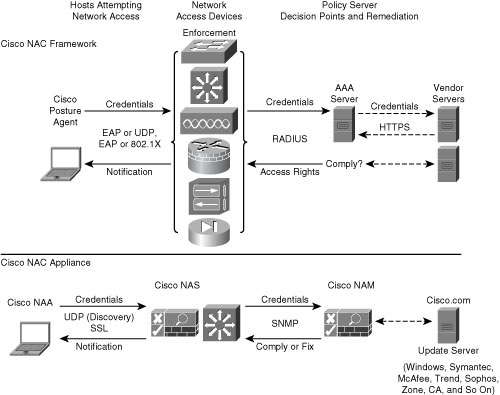
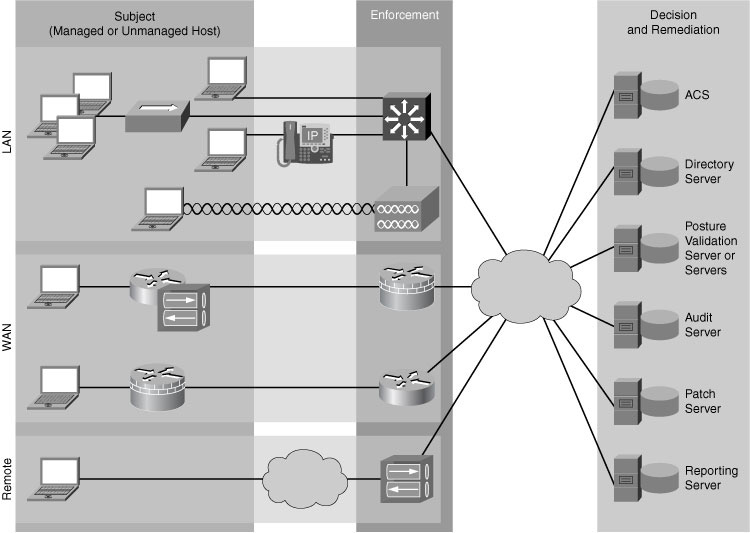
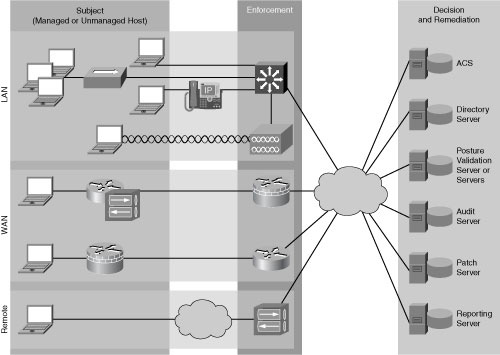
![]() NAC Framework is as an architecture-based framework solution designed to take advantage of an existing base of both Cisco network technologies and existing deployments of security and management solutions from other manufacturers. Figure 8-25 illustrates the key components of the NAC Framework Architecture covered in this section.
NAC Framework is as an architecture-based framework solution designed to take advantage of an existing base of both Cisco network technologies and existing deployments of security and management solutions from other manufacturers. Figure 8-25 illustrates the key components of the NAC Framework Architecture covered in this section.
![]() The NAC Framework assesses the state, or posture, of a host to prevent unauthorized or vulnerable endpoints from accessing the network. The Cisco NAC posture validation process has three major architectural components.
The NAC Framework assesses the state, or posture, of a host to prevent unauthorized or vulnerable endpoints from accessing the network. The Cisco NAC posture validation process has three major architectural components.
-
 Subjects: Managed or unmanaged hosts that are accessing the network on which NAC is enforced. Typical hosts are desktop computers, laptops, and servers, but may also include IP phones, network printers, and other network-attached devices. The subjects use posture agent software to communicate with NAC devices. The Cisco Trust Agent is the Cisco implementation of the posture agent.
Subjects: Managed or unmanaged hosts that are accessing the network on which NAC is enforced. Typical hosts are desktop computers, laptops, and servers, but may also include IP phones, network printers, and other network-attached devices. The subjects use posture agent software to communicate with NAC devices. The Cisco Trust Agent is the Cisco implementation of the posture agent. -
 Enforcement devices: Network devices that are acting as a NAC enforcement point. These may include Cisco access routers, VPN gateways, Cisco Catalyst Layer 2 and Layer 3 switches, and wireless access points.
Enforcement devices: Network devices that are acting as a NAC enforcement point. These may include Cisco access routers, VPN gateways, Cisco Catalyst Layer 2 and Layer 3 switches, and wireless access points. -
 Decision and remediation devices: Many network devices support the NAC Framework Architecture:
Decision and remediation devices: Many network devices support the NAC Framework Architecture:-
 Authentication, authorization, and accounting (AAA) server: The central policy server that aggregates one or more authentications or authorizations into a single system authorization decision and maps this decision to a network access profile for enforcement by the network access device (NAD). Cisco Secure Access Control Server (ACS) is the Cisco AAA server product that supports NAC.
Authentication, authorization, and accounting (AAA) server: The central policy server that aggregates one or more authentications or authorizations into a single system authorization decision and maps this decision to a network access profile for enforcement by the network access device (NAD). Cisco Secure Access Control Server (ACS) is the Cisco AAA server product that supports NAC. -
 Directory server: A centralized directory server for performing user or machine authentication. Possible directory services include Lightweight Directory Access Protocol (LDAP), Microsoft Active Directory, Novell Directory Services (NDS), and one-time token password (OTP) servers.
Directory server: A centralized directory server for performing user or machine authentication. Possible directory services include Lightweight Directory Access Protocol (LDAP), Microsoft Active Directory, Novell Directory Services (NDS), and one-time token password (OTP) servers. -
 Posture validation server (PVS): A PVS from one or more third parties acts as an application-specific policy decision point in NAC for authorizing a set of posture credentials from one or more posture plug-in against a set of policy rules. Examples include antivirus servers and security application servers.
Posture validation server (PVS): A PVS from one or more third parties acts as an application-specific policy decision point in NAC for authorizing a set of posture credentials from one or more posture plug-in against a set of policy rules. Examples include antivirus servers and security application servers. -
 Remediation server: A management solution used to bring noncompliant hosts into compliance. This could be a specialized patch management application or as simple as a website for distributing software. The better and more efficient your host patching and remediation is, the less risk.
Remediation server: A management solution used to bring noncompliant hosts into compliance. This could be a specialized patch management application or as simple as a website for distributing software. The better and more efficient your host patching and remediation is, the less risk. -
 Audit server: A server or software that performs vulnerability assessment (VA) against a host to determine the level of compliance or risk of the host before network admission.
Audit server: A server or software that performs vulnerability assessment (VA) against a host to determine the level of compliance or risk of the host before network admission.
-
 Router Platform Support for the NAC Framework
Router Platform Support for the NAC Framework
![]() The NAC Layer 3 IP method uses Extensible Authentication Protocol over User Data Protocol (EAPoUDP). Routers that support the NAC Layer 3 IP method are considered NAC Release 1.0 devices. They can act as a network intrusion-prevention system (NIPS) device. NAC Layer 3 IP was first introduced as part of the initial release of NAC in mid-2004. NAC Layer 3 IP shipped in June 2004 in Cisco IOS Software Release 12.3(8)T. It is included in Cisco IOS Software T-train images with security; the same image which includes firewall, NIPS, and cryptographic support. NAC Layer 3 IP is a posture-only credential check that supports authorization capabilities, URL redirect, and downloadable ACLs. NAC Layer IP is triggered by a Layer 3 packet entering a router interface with an IP admission ACL configured. NAC Layer 3 IP is mainly positioned for aggregation deployments (WAN, VPN, WLAN, and so on). The current deployment options preclude the use of NAC Layer 3 IP in the distribution layer of a campus infrastructure because the Catalyst Layer 3 switches do not currently support NAC Layer 3 IP.
The NAC Layer 3 IP method uses Extensible Authentication Protocol over User Data Protocol (EAPoUDP). Routers that support the NAC Layer 3 IP method are considered NAC Release 1.0 devices. They can act as a network intrusion-prevention system (NIPS) device. NAC Layer 3 IP was first introduced as part of the initial release of NAC in mid-2004. NAC Layer 3 IP shipped in June 2004 in Cisco IOS Software Release 12.3(8)T. It is included in Cisco IOS Software T-train images with security; the same image which includes firewall, NIPS, and cryptographic support. NAC Layer 3 IP is a posture-only credential check that supports authorization capabilities, URL redirect, and downloadable ACLs. NAC Layer IP is triggered by a Layer 3 packet entering a router interface with an IP admission ACL configured. NAC Layer 3 IP is mainly positioned for aggregation deployments (WAN, VPN, WLAN, and so on). The current deployment options preclude the use of NAC Layer 3 IP in the distribution layer of a campus infrastructure because the Catalyst Layer 3 switches do not currently support NAC Layer 3 IP.
![]() NAC agentless host (NAH) is a mechanism in NAC that allows network access to hosts that do not or cannot perform NAC or other compliance authorizations. NADs that fall into this category often include printers, scanners, photocopiers, cameras, sensors, badge readers, and specialized equipment. NAH devices may also include computers with unsupported operating systems, hardened operating systems, embedded operating systems, and personal firewalls. Static exceptions can be configured to allow hosts to bypass the posture validation process based on specified MAC or IP address. Static exceptions can be configured in ACS to allow any specified hosts to bypass the posture validation process based on MAC address. Both individual and wildcard addresses can be specified. NAH is supported in Cisco IOS Software Release 12.4(6)T. Table 8-1 illustrates which router platforms support the NAC Framework.
NAC agentless host (NAH) is a mechanism in NAC that allows network access to hosts that do not or cannot perform NAC or other compliance authorizations. NADs that fall into this category often include printers, scanners, photocopiers, cameras, sensors, badge readers, and specialized equipment. NAH devices may also include computers with unsupported operating systems, hardened operating systems, embedded operating systems, and personal firewalls. Static exceptions can be configured to allow hosts to bypass the posture validation process based on specified MAC or IP address. Static exceptions can be configured in ACS to allow any specified hosts to bypass the posture validation process based on MAC address. Both individual and wildcard addresses can be specified. NAH is supported in Cisco IOS Software Release 12.4(6)T. Table 8-1 illustrates which router platforms support the NAC Framework.
|
| |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Devices that support either the NAC Layer 2 IP method that uses EAPoUDP, or the NAC Layer 2 802.1x (EAP over 802.1x) method, are NAC Release 2.0 devices. NAC Layer 2 IP is triggered by ARP or optionally DHCP traffic on a switch interface. NAC Layer 2 IP is also a posture-only credential check that supports authorization capabilities, URL redirect, and downloadable ACLs. NAC Layer 2 IP sessions are active for as long as the host responds to periodic status query messages implemented using ARP probes or until they are terminated. The ACLs that set the default policy for the switch port on the NAC Layer 2 IP switches are implemented in hardware. One of the main benefits of NAC Layer 2 IP is that it was designed to support multiple hosts per port. The network administrator needs to be aware that unlike NAC Layer 3 IP, only a limited number of hosts per port can be supported in NAC Layer 2 IP. Some network module switches for the Cisco Integrated Services Router platforms support NAC Layer 2 IP or the NAC Layer 2 802.1x.
Devices that support either the NAC Layer 2 IP method that uses EAPoUDP, or the NAC Layer 2 802.1x (EAP over 802.1x) method, are NAC Release 2.0 devices. NAC Layer 2 IP is triggered by ARP or optionally DHCP traffic on a switch interface. NAC Layer 2 IP is also a posture-only credential check that supports authorization capabilities, URL redirect, and downloadable ACLs. NAC Layer 2 IP sessions are active for as long as the host responds to periodic status query messages implemented using ARP probes or until they are terminated. The ACLs that set the default policy for the switch port on the NAC Layer 2 IP switches are implemented in hardware. One of the main benefits of NAC Layer 2 IP is that it was designed to support multiple hosts per port. The network administrator needs to be aware that unlike NAC Layer 3 IP, only a limited number of hosts per port can be supported in NAC Layer 2 IP. Some network module switches for the Cisco Integrated Services Router platforms support NAC Layer 2 IP or the NAC Layer 2 802.1x.
| Note |
|
 Switch Platform Support for the NAC Framework
Switch Platform Support for the NAC Framework
![]() Table 8-2 shows NAC Framework support in Cisco Catalyst switches. NAC performs posture validation at the Layer 2 network edge for hosts with or without 802.1x enabled. Vulnerable and noncompliant hosts can be isolated, given reduced network access, or directed to remediation servers based on organizational policy. By ensuring that every host complies with security policy, organizations can significantly reduce the damage caused by infected hosts.
Table 8-2 shows NAC Framework support in Cisco Catalyst switches. NAC performs posture validation at the Layer 2 network edge for hosts with or without 802.1x enabled. Vulnerable and noncompliant hosts can be isolated, given reduced network access, or directed to remediation servers based on organizational policy. By ensuring that every host complies with security policy, organizations can significantly reduce the damage caused by infected hosts.
|
|
|
|
|
|
|
|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Note |
|

0 comments
Post a Comment