Enterprise Branch and Teleworker Design
![]() This section describes design considerations for the Enterprise Branch and Enterprise Teleworker architectures.
This section describes design considerations for the Enterprise Branch and Enterprise Teleworker architectures.
 Enterprise Branch Architecture
Enterprise Branch Architecture
![]() Recall that the Cisco Enterprise Architecture, based on the Cisco SONA, includes branch modules that focus on the remote places in the network. Enterprises are seeking opportunities to protect, optimize, and grow their businesses by increasing security; consolidating voice, video, and data onto a single IP network; and investing in applications that will improve productivity and operating efficiencies. These services provide enterprises with new opportunities to reduce costs, improve productivity, and safeguard information assets in all their locations.
Recall that the Cisco Enterprise Architecture, based on the Cisco SONA, includes branch modules that focus on the remote places in the network. Enterprises are seeking opportunities to protect, optimize, and grow their businesses by increasing security; consolidating voice, video, and data onto a single IP network; and investing in applications that will improve productivity and operating efficiencies. These services provide enterprises with new opportunities to reduce costs, improve productivity, and safeguard information assets in all their locations.
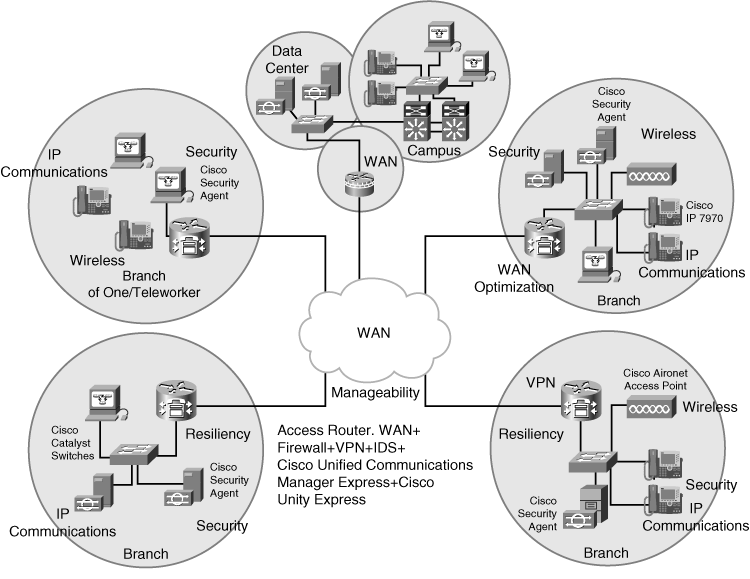
![]() The Cisco Enterprise Branch architecture takes into account the services that enterprises want to deploy at their endpoints, no matter how far away the endpoints are or how they are connected. Figure 5-23 illustrates how branch services relate to the other parts of the Cisco Enterprise architectures.
The Cisco Enterprise Branch architecture takes into account the services that enterprises want to deploy at their endpoints, no matter how far away the endpoints are or how they are connected. Figure 5-23 illustrates how branch services relate to the other parts of the Cisco Enterprise architectures.
| Note |
|
![]() The Cisco Enterprise Branch Architecture, illustrated in Figure 5-24, is an integrated, flexible, and secure framework for extending headquarters applications in real time to remote sites. The Cisco Enterprise Branch Architecture applies the SONA framework to the smaller scale of a branch location.
The Cisco Enterprise Branch Architecture, illustrated in Figure 5-24, is an integrated, flexible, and secure framework for extending headquarters applications in real time to remote sites. The Cisco Enterprise Branch Architecture applies the SONA framework to the smaller scale of a branch location.
![]() Common network components that might be implemented in the Enterprise Branch include the following:
Common network components that might be implemented in the Enterprise Branch include the following:
 Enterprise Branch Design
Enterprise Branch Design
![]() Requirements differ with the size of the branch offices. Consider to the following questions when designing the Enterprise Branch:
Requirements differ with the size of the branch offices. Consider to the following questions when designing the Enterprise Branch:
-
 How many branch locations need to be supported?
How many branch locations need to be supported? -
 How many existing devices (including end users, hosts, and network infrastructure) are to be supported at each location? The number of devices supported is limited by the physical number of ports available.
How many existing devices (including end users, hosts, and network infrastructure) are to be supported at each location? The number of devices supported is limited by the physical number of ports available. -
 How much growth is expected at each location, and therefore what level of scalability is required?
How much growth is expected at each location, and therefore what level of scalability is required? -
 What are the high availability requirements at each location?
What are the high availability requirements at each location? -
 What level of security is required in the design? Should security be managed locally or through the central location?
What level of security is required in the design? Should security be managed locally or through the central location? -
 Are there any requirements for local server farms or networks between the internal network and the external network (for example, in a demilitarized zone [DMZ])?
Are there any requirements for local server farms or networks between the internal network and the external network (for example, in a demilitarized zone [DMZ])? -
 Should network management be supported locally or via the central location?
Should network management be supported locally or via the central location? -
 What wireless services are needed, and how will they be used by the clients? What effect will the network and the environment have on the wireless devices?
What wireless services are needed, and how will they be used by the clients? What effect will the network and the environment have on the wireless devices? -
 What is the approximate budget available?
What is the approximate budget available?
![]() The number of devices, high availability, scalability, and migration to advanced services requirements also influence the model adopted. The design models for each of these types of branches are described in the following sections.
The number of devices, high availability, scalability, and migration to advanced services requirements also influence the model adopted. The design models for each of these types of branches are described in the following sections.
![]() Each of the designs in the following sections suggests using an ISR (such as the 2800 series routers) at the WAN edge, which provides various voice, security, and data services that are integrated with the LAN infrastructure. Depending on the specific ISR edge router chosen, the interfaces and modules available include the following:
Each of the designs in the following sections suggests using an ISR (such as the 2800 series routers) at the WAN edge, which provides various voice, security, and data services that are integrated with the LAN infrastructure. Depending on the specific ISR edge router chosen, the interfaces and modules available include the following:
-
 Integrated LAN interfaces (10/100/1000 Mbps)
Integrated LAN interfaces (10/100/1000 Mbps) -
 High-speed WAN interface card (HWIC) slots
High-speed WAN interface card (HWIC) slots -
 Network modules
Network modules -
 Embedded security
Embedded security
![]() Alternatively, Cisco multiservice routers (such as the 2600 series routers) can be used.
Alternatively, Cisco multiservice routers (such as the 2600 series routers) can be used.
Small Branch Office Design
![]() Small branch office designs combine an ISR access router with Layer 2 switching and end-user devices, phones, printers, and so forth; a typical design is illustrated in Figure 5-25.
Small branch office designs combine an ISR access router with Layer 2 switching and end-user devices, phones, printers, and so forth; a typical design is illustrated in Figure 5-25.
ISR and Switch Connections
![]() The ISR connects with Layer 2 switch ports in one of the following three ways:
The ISR connects with Layer 2 switch ports in one of the following three ways:
-
 Integrated switching within the ISR (or multiservice router): This option has a lower port density that supports from 16 to 48 client devices on either a Cisco EtherSwitch network module or a Cisco EtherSwitch service module. It provides a one-box solution that offers ease of management. Depending on the module, the integrated switch ports might provide power to end devices using Power over Ethernet (PoE).
Integrated switching within the ISR (or multiservice router): This option has a lower port density that supports from 16 to 48 client devices on either a Cisco EtherSwitch network module or a Cisco EtherSwitch service module. It provides a one-box solution that offers ease of management. Depending on the module, the integrated switch ports might provide power to end devices using Power over Ethernet (PoE). -
 Trunked network interface on the ISR to external access switches: In this case, there is no link redundancy between the access switches and the ISR. The access switches might provide power to end devices using PoE.
Trunked network interface on the ISR to external access switches: In this case, there is no link redundancy between the access switches and the ISR. The access switches might provide power to end devices using PoE. -
 Logical EtherChannel interface between the ISR and access switches: This approach uses an EtherSwitch module in the ISR configured as an EtherChannel. Link redundancy is provided to the access layer switches over the EtherChannel. The access switches might provide power to end devices using PoE.
Logical EtherChannel interface between the ISR and access switches: This approach uses an EtherSwitch module in the ISR configured as an EtherChannel. Link redundancy is provided to the access layer switches over the EtherChannel. The access switches might provide power to end devices using PoE.
![]() If redundant access layer links and higher-bandwidth uplinks are required, only the third option, with higher-performance devices, can be used. The choice of the edge router also depends on the voice and VPN support needed.
If redundant access layer links and higher-bandwidth uplinks are required, only the third option, with higher-performance devices, can be used. The choice of the edge router also depends on the voice and VPN support needed.
![]() The access switch provides Layer 2 services, and the Cisco ISR provides Layer 3 services such as Dynamic Host Configuration Protocol (DHCP), firewall, and Network Address Translation.
The access switch provides Layer 2 services, and the Cisco ISR provides Layer 3 services such as Dynamic Host Configuration Protocol (DHCP), firewall, and Network Address Translation.
![]() The 2811 ISR or larger ISR is suggested. Both the Cisco 2821 and 2851 ISRs support two integrated 10/100/1000 routed (Layer 3) interfaces and have one slot for a network module. The Cisco 2821 ISR supports the 16-port EtherSwitch network module and the 24-port EtherSwitch service module. The Cisco 2851, 3825, and 3845 ISRs can support the high-density 48-port EtherSwitch service module.
The 2811 ISR or larger ISR is suggested. Both the Cisco 2821 and 2851 ISRs support two integrated 10/100/1000 routed (Layer 3) interfaces and have one slot for a network module. The Cisco 2821 ISR supports the 16-port EtherSwitch network module and the 24-port EtherSwitch service module. The Cisco 2851, 3825, and 3845 ISRs can support the high-density 48-port EtherSwitch service module.
![]() Typical access switches include the Cisco Catalyst 2960, 3560, and 3750 Series switches.
Typical access switches include the Cisco Catalyst 2960, 3560, and 3750 Series switches.
![]() To keep manageability simple, the topology has no loops; however, spanning tree must be enabled and configured to protect the network from any accidental loops. As is the case in the Enterprise Campus, the recommended spanning-tree protocol is Rapid Per-VLAN Spanning Tree Plus for all Layer 2 deployments in a branch office environment.
To keep manageability simple, the topology has no loops; however, spanning tree must be enabled and configured to protect the network from any accidental loops. As is the case in the Enterprise Campus, the recommended spanning-tree protocol is Rapid Per-VLAN Spanning Tree Plus for all Layer 2 deployments in a branch office environment.
![]() The ISR is the default gateway for each VLAN configured in the topology, and all Layer 3 configurations are done on the ISR. The access switches must be configured with an IP address for management purposes.
The ISR is the default gateway for each VLAN configured in the topology, and all Layer 3 configurations are done on the ISR. The access switches must be configured with an IP address for management purposes.
WAN Services
![]() WAN services are typically provided by a T1 primary link. The Internet is used as a WAN backup, accessed by an ADSL connection.
WAN services are typically provided by a T1 primary link. The Internet is used as a WAN backup, accessed by an ADSL connection.
Network Services
![]() The EIGRP routing protocol is used. High availability across the WAN is provided by a floating static route across the ADSL Internet connection.
The EIGRP routing protocol is used. High availability across the WAN is provided by a floating static route across the ADSL Internet connection.
![]() QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
Medium Branch Office Design
![]() A typical medium branch office topology, illustrated in Figure 5-26, is similar to the small office topology, except that the WAN edge devices are larger, typically two Cisco 2821 or Cisco 2851 ISRs, and the access switches for LAN connectivity are external stackable switches.
A typical medium branch office topology, illustrated in Figure 5-26, is similar to the small office topology, except that the WAN edge devices are larger, typically two Cisco 2821 or Cisco 2851 ISRs, and the access switches for LAN connectivity are external stackable switches.
ISR and Switch Connections
![]() To scale up to 100 users, the following options are available:
To scale up to 100 users, the following options are available:
-
 Use a higher port density external access switch
Use a higher port density external access switch -
 Use an ISR module that supports switched access ports; use EtherChannel to provide a redundant connection to the access switches
Use an ISR module that supports switched access ports; use EtherChannel to provide a redundant connection to the access switches
![]() This design uses the integrated 10/100/1000 interfaces on the ISRs as Layer 3 trunks, providing the flexibility to use various access switches. The stackable Cisco Catalyst 3750 Series switch with an IP Base image or an IP Services image can be used as the access switch, supporting 24 or 48 users per switch. The IP Base image feature set includes advanced QoS, rate limiting, ACLs, and basic static and RIP routing capability. The IP Services image provides a richer set of enterprise-class features, including advanced hardware-based IP unicast and multicast routing. An additional Advanced IP Services license is also available (for example, this license is required for IPv6 routing).
This design uses the integrated 10/100/1000 interfaces on the ISRs as Layer 3 trunks, providing the flexibility to use various access switches. The stackable Cisco Catalyst 3750 Series switch with an IP Base image or an IP Services image can be used as the access switch, supporting 24 or 48 users per switch. The IP Base image feature set includes advanced QoS, rate limiting, ACLs, and basic static and RIP routing capability. The IP Services image provides a richer set of enterprise-class features, including advanced hardware-based IP unicast and multicast routing. An additional Advanced IP Services license is also available (for example, this license is required for IPv6 routing).
![]() With Cisco StackWise technology, a single 32-Gbps switching unit can be created, using up to nine Cisco Catalyst 3750 Series switches. Cisco StackWise technology uses special stack-interconnect cables and stacking software. The stack behaves as a single switching unit that is managed by a master switch elected from one of the member switches. The master switch automatically creates and updates all the switching and optional routing tables. The number of PoE ports supported depends on the specific access switch selected.
With Cisco StackWise technology, a single 32-Gbps switching unit can be created, using up to nine Cisco Catalyst 3750 Series switches. Cisco StackWise technology uses special stack-interconnect cables and stacking software. The stack behaves as a single switching unit that is managed by a master switch elected from one of the member switches. The master switch automatically creates and updates all the switching and optional routing tables. The number of PoE ports supported depends on the specific access switch selected.
WAN Services
![]() WAN services are typically provided by a private WAN—for example, with dual Frame Relay links.
WAN services are typically provided by a private WAN—for example, with dual Frame Relay links.
Network Services
![]() The EIGRP routing protocol is used. High availability across the WAN is provided by dual routers running router redundancy protocols such as Hot Standby Router Protocol (HSRP), Virtual Router Redundancy Protocol (VRRP), and Gateway Load-Balancing Protocol (GLBP) (as described in Chapter 4). QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
The EIGRP routing protocol is used. High availability across the WAN is provided by dual routers running router redundancy protocols such as Hot Standby Router Protocol (HSRP), Virtual Router Redundancy Protocol (VRRP), and Gateway Load-Balancing Protocol (GLBP) (as described in Chapter 4). QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
Large Branch Office Design
![]() In a typical large branch office design, illustrated in Figure 5-27, dual ISRs are used for redundancy at the WAN edge. Firewall functionality is provided by dual adaptive security appliances (ASA), and dual multilayer switches (stackable or modular) are deployed at the distribution layer.
In a typical large branch office design, illustrated in Figure 5-27, dual ISRs are used for redundancy at the WAN edge. Firewall functionality is provided by dual adaptive security appliances (ASA), and dual multilayer switches (stackable or modular) are deployed at the distribution layer.
ISR and Switch Connections
![]() In addition to supporting more users, a large office might need higher LAN switching capability if supporting a server farm or DMZ. Support for some of these services requires the use of appliance devices if higher throughput is required. To meet these requirements, a distribution layer is added to the topology by introducing a multilayer switch that provides the required LAN switching capabilities, port density, and flexibility to support additional appliances.
In addition to supporting more users, a large office might need higher LAN switching capability if supporting a server farm or DMZ. Support for some of these services requires the use of appliance devices if higher throughput is required. To meet these requirements, a distribution layer is added to the topology by introducing a multilayer switch that provides the required LAN switching capabilities, port density, and flexibility to support additional appliances.
![]() Either a stackable switch (for example, a Cisco Catalyst 3750 Series switch) or a Cisco Catalyst 4500 Series switch could be used at the distribution layer. This LAN topology is highly available, scalable, and manageable. High-availability requirements are met by the link redundancy and device redundancy built into the design. For example, redundant links are used to provide high availability between the distribution and edge layers.
Either a stackable switch (for example, a Cisco Catalyst 3750 Series switch) or a Cisco Catalyst 4500 Series switch could be used at the distribution layer. This LAN topology is highly available, scalable, and manageable. High-availability requirements are met by the link redundancy and device redundancy built into the design. For example, redundant links are used to provide high availability between the distribution and edge layers.
![]() The port density of the stacked switches allows a number of access switches to be connected without compromising high availability. The distribution switches typically run the advanced IOS images, which support more features, including various routing protocols and advanced features such as policy-based routing.
The port density of the stacked switches allows a number of access switches to be connected without compromising high availability. The distribution switches typically run the advanced IOS images, which support more features, including various routing protocols and advanced features such as policy-based routing.
![]() If Cisco Catalyst 3560 or 3750 Series switches are used at the access layer, other Layer 2 security features, such as DHCP snooping, Dynamic Address Resolution Protocol (ARP) Inspection (DAI), and IP Source Guard, can be enabled, providing additional security measures.
If Cisco Catalyst 3560 or 3750 Series switches are used at the access layer, other Layer 2 security features, such as DHCP snooping, Dynamic Address Resolution Protocol (ARP) Inspection (DAI), and IP Source Guard, can be enabled, providing additional security measures.
![]() The default gateways for all the VLANs at the access layer are on the distribution layer.
The default gateways for all the VLANs at the access layer are on the distribution layer.
WAN Services
![]() WAN services in this typical design are provided by an MPLS network with dual connections.
WAN services in this typical design are provided by an MPLS network with dual connections.
Network Services
![]() The EIGRP routing protocol is used. High availability across the WAN is provided by dual routers running router redundancy protocols (such as HSRP, VRRP, and GLBP), ASA failover functionality, and object tracking.
The EIGRP routing protocol is used. High availability across the WAN is provided by dual routers running router redundancy protocols (such as HSRP, VRRP, and GLBP), ASA failover functionality, and object tracking.
![]() QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
QoS mechanisms used include traffic shaping and policing, and the implementation of a scavenger class of traffic (applied on both the switch and the ISR).
 Enterprise Teleworker (Branch of One) Design
Enterprise Teleworker (Branch of One) Design
![]() Organizations are constantly striving to reduce costs, improve employee productivity, and retain valued employees. These goals can be furthered by allowing employees to work from home with quality, function, performance, convenience, and security similar to that available in the office. With a work environment in the residence, employees can optimally manage their work schedules, allowing for higher productivity (less affected by office distractions) and greater job satisfaction (flexibility in schedule). This transparent extension of the enterprise to employee homes is the objective of the Cisco Enterprise Teleworker (or Branch of One) architecture.
Organizations are constantly striving to reduce costs, improve employee productivity, and retain valued employees. These goals can be furthered by allowing employees to work from home with quality, function, performance, convenience, and security similar to that available in the office. With a work environment in the residence, employees can optimally manage their work schedules, allowing for higher productivity (less affected by office distractions) and greater job satisfaction (flexibility in schedule). This transparent extension of the enterprise to employee homes is the objective of the Cisco Enterprise Teleworker (or Branch of One) architecture.
![]() Occasional remote users have much lighter application requirements than part-time and full-time teleworkers. They can connect through a wireless hotspot or a guest network at a hotel and have little control over network resiliency and availability.
Occasional remote users have much lighter application requirements than part-time and full-time teleworkers. They can connect through a wireless hotspot or a guest network at a hotel and have little control over network resiliency and availability.
![]() In contrast, Enterprise teleworkers can be differentiated from other forms of work-at-home or telecommuting scenarios in that the emphasis is on delivering seamless, managed accessibility to the full range of applications and services critical to the operational effectiveness of enterprises, as illustrated in Figure 5-28. The Cisco Enterprise Teleworker architecture is part of the overall secure Cisco Enterprise architecture infrastructure. It companies the capability to integrate and securely manage their remote workers within the corporate network while simultaneously providing a high-quality end-user experience supporting a full range of enterprise applications for the enterprise teleworker.
In contrast, Enterprise teleworkers can be differentiated from other forms of work-at-home or telecommuting scenarios in that the emphasis is on delivering seamless, managed accessibility to the full range of applications and services critical to the operational effectiveness of enterprises, as illustrated in Figure 5-28. The Cisco Enterprise Teleworker architecture is part of the overall secure Cisco Enterprise architecture infrastructure. It companies the capability to integrate and securely manage their remote workers within the corporate network while simultaneously providing a high-quality end-user experience supporting a full range of enterprise applications for the enterprise teleworker.
![]() The enterprise teleworker typically connects to an ISP through a DSL or cable modem and might use an analog dialup session to back up this connection. The enterprise teleworker solution is implemented with a small ISR, such as the Cisco 871, 876, 877, or 878 ISR, with integrated switch ports, connected behind a broadband modem, as shown in Figure 5-29. This solution uses a transparent, always-on VPN tunnel back to the enterprise.
The enterprise teleworker typically connects to an ISP through a DSL or cable modem and might use an analog dialup session to back up this connection. The enterprise teleworker solution is implemented with a small ISR, such as the Cisco 871, 876, 877, or 878 ISR, with integrated switch ports, connected behind a broadband modem, as shown in Figure 5-29. This solution uses a transparent, always-on VPN tunnel back to the enterprise.
![]() Within this architecture, centralized management means that the enterprise applies security policies, pushes configurations, and periodically tests the connection through the broadband cloud and back to the corporate office to determine the latency, jitter, and packet loss experienced at any time. This solution supports advanced applications such as voice and video as part of the full suite of enterprise services for the end user. For example, a teleworker can access the central-office IP telephone system from home with comparable voice quality and can thereby take advantage of the higher-function IP telephony capabilities instead of using the PSTN.
Within this architecture, centralized management means that the enterprise applies security policies, pushes configurations, and periodically tests the connection through the broadband cloud and back to the corporate office to determine the latency, jitter, and packet loss experienced at any time. This solution supports advanced applications such as voice and video as part of the full suite of enterprise services for the end user. For example, a teleworker can access the central-office IP telephone system from home with comparable voice quality and can thereby take advantage of the higher-function IP telephony capabilities instead of using the PSTN.
![]() An alternative solution is an unmanaged VPN approach in which the end user implements a software VPN from a PC across a generic broadband router, access point, or hub appliance. This solution typically cannot support the level of feature integration, QoS, and managed support needed to reliably deliver voice, video, multimedia, and traditional data to the end user, but it might be appropriate for occasional remote users with lighter application requirements.
An alternative solution is an unmanaged VPN approach in which the end user implements a software VPN from a PC across a generic broadband router, access point, or hub appliance. This solution typically cannot support the level of feature integration, QoS, and managed support needed to reliably deliver voice, video, multimedia, and traditional data to the end user, but it might be appropriate for occasional remote users with lighter application requirements.
Summary
![]() In this chapter, you learned about remote connectivity network design with a focus on the following topics:
In this chapter, you learned about remote connectivity network design with a focus on the following topics:
-
 Definition of a WAN and the types of WAN interconnections
Definition of a WAN and the types of WAN interconnections -
 Various WAN technologies, including TDM, ISDN, Frame Relay, ATM, MPLS, Metro Ethernet, DSL, cable, wireless, SONET/SDH, DWDM, and dark fiber
Various WAN technologies, including TDM, ISDN, Frame Relay, ATM, MPLS, Metro Ethernet, DSL, cable, wireless, SONET/SDH, DWDM, and dark fiber -
 WAN design methodology, including the application and technical requirement aspects of WAN design
WAN design methodology, including the application and technical requirement aspects of WAN design -
 WAN bandwidth optimization techniques
WAN bandwidth optimization techniques -
 Use of various WAN technologies for remote access, VPNs, WAN backup, and connecting to the Internet as a backup WAN
Use of various WAN technologies for remote access, VPNs, WAN backup, and connecting to the Internet as a backup WAN -
 Enterprise Edge WAN and MAN architectures and technologies
Enterprise Edge WAN and MAN architectures and technologies -
 Selection of WAN components, including hardware and software
Selection of WAN components, including hardware and software -
 Enterprise Branch and Enterprise Teleworker design considerations
Enterprise Branch and Enterprise Teleworker design considerations











0 comments
Post a Comment