Designing Advanced Routing
![]() This section discusses elements of advanced routing solution design using route summarization and default routing. It also discusses using route filtering in advanced routing designs.
This section discusses elements of advanced routing solution design using route summarization and default routing. It also discusses using route filtering in advanced routing designs.
![]() Upon mastering this section, you will be able to describe and use various concepts to perform advanced routing design. This ability includes being able to meet these objectives:
Upon mastering this section, you will be able to describe and use various concepts to perform advanced routing design. This ability includes being able to meet these objectives:
-
 Describe why route summarization and default routing should be used in a routing design
Describe why route summarization and default routing should be used in a routing design -
 Describe why route filtering should be used in a routing design
Describe why route filtering should be used in a routing design -
 Describe why redistribution should be used in a routing design
Describe why redistribution should be used in a routing design
Route Summarization and Default Routing
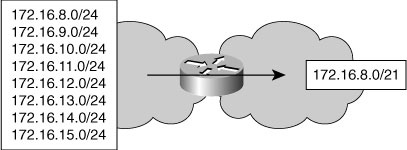
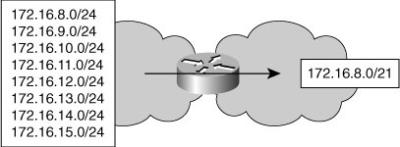
![]() Route summarization procedures condense routing information. Without summarization, each router in a network must retain a route to every subnet in the network. With summarization, routers can reduce some sets of routes to a single advertisement, reducing both the load on the router and the perceived complexity of the network. The importance of route summarization increases with network size (see Figure 3-1).
Route summarization procedures condense routing information. Without summarization, each router in a network must retain a route to every subnet in the network. With summarization, routers can reduce some sets of routes to a single advertisement, reducing both the load on the router and the perceived complexity of the network. The importance of route summarization increases with network size (see Figure 3-1).
![]() Medium-to-large networks often require the use of more routing protocol features than a small network would. The bigger the network, the more important it is to have a careful design with attention to scaling the routing protocol properly. Stability, control, predictability, and security of routing are also important. And as converged networks are increasingly used to support voice, IP telephony, storage, and other drop-sensitive traffic, networks must be designed for fast routing convergence.
Medium-to-large networks often require the use of more routing protocol features than a small network would. The bigger the network, the more important it is to have a careful design with attention to scaling the routing protocol properly. Stability, control, predictability, and security of routing are also important. And as converged networks are increasingly used to support voice, IP telephony, storage, and other drop-sensitive traffic, networks must be designed for fast routing convergence.
![]() Route summarization is one key network design element for supporting manageable and fast-converging routing. The Building Scalable Cisco Internetworks (BSCI) course covers configuring route summarization and the concepts of how summarization is beneficial to routing and for troubleshooting.
Route summarization is one key network design element for supporting manageable and fast-converging routing. The Building Scalable Cisco Internetworks (BSCI) course covers configuring route summarization and the concepts of how summarization is beneficial to routing and for troubleshooting.
![]() The design recommendations for summarizations are straightforward:
The design recommendations for summarizations are straightforward:
-
 Use route summarization to scale routing designs.
Use route summarization to scale routing designs. -
 Design addressing using address blocks that can be summarized.
Design addressing using address blocks that can be summarized. -
 Default routing can be thought of as a particularly simple form of route summarization where all other routes are summarized in the default.
Default routing can be thought of as a particularly simple form of route summarization where all other routes are summarized in the default.
 Originating Default
Originating Default
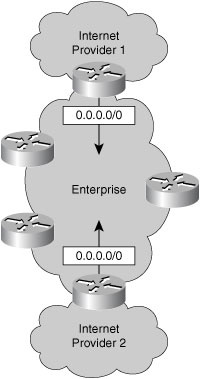
![]() The concept of originating default is useful for summarization in routing. Most networks use some form of default routing. It is wise to have the default route (0.0.0.0 /0) advertised dynamically into the rest of the network by the router or routers that connect to Internet service providers (ISPs). This route advertises the path to any route not found more specifically in the routing table (see Figure 3-2).
The concept of originating default is useful for summarization in routing. Most networks use some form of default routing. It is wise to have the default route (0.0.0.0 /0) advertised dynamically into the rest of the network by the router or routers that connect to Internet service providers (ISPs). This route advertises the path to any route not found more specifically in the routing table (see Figure 3-2).
![]() It is generally a bad idea to configure a static default route on every router, even if recursive routing is used. In recursive routing, for any route in the routing table whose next-hop IP address is not a directly connected interface of the router, the routing algorithm looks recursively into the routing table until it finds a directly connected interface to which it can forward the packets. If you configure a static default route on every router to the ISP router, the next hop is the ISP-connected router rather than a directly connected peer router. This approach can lead to black holes in the network if there is not a path to the ISP-connected router. This approach also needs to be reconfigured on every router if the exit point changes or if a second ISP connection is added.
It is generally a bad idea to configure a static default route on every router, even if recursive routing is used. In recursive routing, for any route in the routing table whose next-hop IP address is not a directly connected interface of the router, the routing algorithm looks recursively into the routing table until it finds a directly connected interface to which it can forward the packets. If you configure a static default route on every router to the ISP router, the next hop is the ISP-connected router rather than a directly connected peer router. This approach can lead to black holes in the network if there is not a path to the ISP-connected router. This approach also needs to be reconfigured on every router if the exit point changes or if a second ISP connection is added.
![]() If manually configured next hops are used, more configurations are needed. This approach can also lead to routing loops and is hard to change. If there are alternative paths, this static approach might fail to take advantage of them.
If manually configured next hops are used, more configurations are needed. This approach can also lead to routing loops and is hard to change. If there are alternative paths, this static approach might fail to take advantage of them.
![]() The recommended alternative is to configure each ISP-connected router with a static default route and redistribute that into the dynamic routing protocol. This needs to be done only at the network edge devices. All other routers pick up the route dynamically, and traffic out of the enterprise will use the closest exit. If the ISP-connected router loses connectivity to the ISP or fails, the default route will no longer be advertised in the organization.
The recommended alternative is to configure each ISP-connected router with a static default route and redistribute that into the dynamic routing protocol. This needs to be done only at the network edge devices. All other routers pick up the route dynamically, and traffic out of the enterprise will use the closest exit. If the ISP-connected router loses connectivity to the ISP or fails, the default route will no longer be advertised in the organization.
![]() You may need to use the default-information originate command, with options, to redistribute the default route into the dynamic routing protocol.
You may need to use the default-information originate command, with options, to redistribute the default route into the dynamic routing protocol.
 Stub Areas and Default Route
Stub Areas and Default Route
![]() Explicit route summarization is not the only way to achieve the benefits of summarization. The various kinds of OSPF stub areas can be thought of as a simpler form of summarization. The point of using OSPF stub areas, totally stubby areas, not-so-stubby areas (NSSA), is to reduce the amount of routing information advertised into an area. The information that is suppressed is replaced by the default route 0.0.0.0/0 or 0/0.
Explicit route summarization is not the only way to achieve the benefits of summarization. The various kinds of OSPF stub areas can be thought of as a simpler form of summarization. The point of using OSPF stub areas, totally stubby areas, not-so-stubby areas (NSSA), is to reduce the amount of routing information advertised into an area. The information that is suppressed is replaced by the default route 0.0.0.0/0 or 0/0.
![]() OSPF cannot filter prefixes within an area. It only filters routes as they are passed between areas at an Area Border Router (ABR).
OSPF cannot filter prefixes within an area. It only filters routes as they are passed between areas at an Area Border Router (ABR).
![]() OSPF stub areas do not work to IP Security (IPsec) virtual private network (VPN) sites such as with generic routing encapsulation (GRE) over IPsec tunnels. For IPsec VPN remote sites, the 0/0 route must point to the ISP, so stub areas cannot be used. An alternative to the default route is to advertise a summary route for the organization as a “corporate default” route and filter unnecessary prefixes at the ABR. Because OSPF cannot filter routes within an area, there still will be within-area flooding of link-state advertisements (LSA).
OSPF stub areas do not work to IP Security (IPsec) virtual private network (VPN) sites such as with generic routing encapsulation (GRE) over IPsec tunnels. For IPsec VPN remote sites, the 0/0 route must point to the ISP, so stub areas cannot be used. An alternative to the default route is to advertise a summary route for the organization as a “corporate default” route and filter unnecessary prefixes at the ABR. Because OSPF cannot filter routes within an area, there still will be within-area flooding of link-state advertisements (LSA).
![]() You can use this approach with the EIGRP, too. The ip default-network network-number command is used to configure the last-resort gateway or default route. A router configured with this command considers the network listed in the command as the candidate route for computing the gateway of last resort. This network must be in the routing table either as a static route or an Interior Gateway Protocol (IGP) route before the router will announce the network as a candidate default route to other EIGRP routers. The network must be an EIGRP-derived network in the routing table or be generated by a static route, which has been redistributed into EIGRP.
You can use this approach with the EIGRP, too. The ip default-network network-number command is used to configure the last-resort gateway or default route. A router configured with this command considers the network listed in the command as the candidate route for computing the gateway of last resort. This network must be in the routing table either as a static route or an Interior Gateway Protocol (IGP) route before the router will announce the network as a candidate default route to other EIGRP routers. The network must be an EIGRP-derived network in the routing table or be generated by a static route, which has been redistributed into EIGRP.
![]() EIGRP networks will typically configure the default route at ISP connection points. Filters can then be used so that only the default and any other critical prefixes are sent to remote sites.
EIGRP networks will typically configure the default route at ISP connection points. Filters can then be used so that only the default and any other critical prefixes are sent to remote sites.
![]() In a site-to-site IPsec VPN network, it can be useful to also advertise a corporate summary route or corporate default route (which might be 10.0.0.0 /8) to remote sites. The advantage of doing so is that all other corporate prefixes need not be advertised to the IPsec VPN site. Even if the IPsec network uses two or three hub sites, dynamic failover will occur based on the corporate default. For the corporate default advertisement to work properly under failure conditions, all the site-specific prefixes need to be advertised between the hub sites.
In a site-to-site IPsec VPN network, it can be useful to also advertise a corporate summary route or corporate default route (which might be 10.0.0.0 /8) to remote sites. The advantage of doing so is that all other corporate prefixes need not be advertised to the IPsec VPN site. Even if the IPsec network uses two or three hub sites, dynamic failover will occur based on the corporate default. For the corporate default advertisement to work properly under failure conditions, all the site-specific prefixes need to be advertised between the hub sites.
![]() Filtering the unnecessary routes out can save on the bandwidth and router CPU that is expended to provide routing information to remote sites. This increases the stability and efficiency of the network. Removing the clutter from routing tables also makes troubleshooting more effective.
Filtering the unnecessary routes out can save on the bandwidth and router CPU that is expended to provide routing information to remote sites. This increases the stability and efficiency of the network. Removing the clutter from routing tables also makes troubleshooting more effective.
| | ||
 | | Chapter 3 - Developing an Optimum Design for Layer 3 Designing Cisco Network Service Architectures (ARCH) (Authorized Self-Study Guide), Second Edition |
|
 Route Filtering in the Network Design
Route Filtering in the Network Design
![]() This topic discusses the appropriate use of route filtering in network design. Route filtering can be used to manage traffic flows in the network, avoid inappropriate transit traffic through remote nodes, and provide a defense against inaccurate or inappropriate routing updates. You can use different techniques to apply route filtering in various routing protocols.
This topic discusses the appropriate use of route filtering in network design. Route filtering can be used to manage traffic flows in the network, avoid inappropriate transit traffic through remote nodes, and provide a defense against inaccurate or inappropriate routing updates. You can use different techniques to apply route filtering in various routing protocols.
 Inappropriate Transit Traffic
Inappropriate Transit Traffic
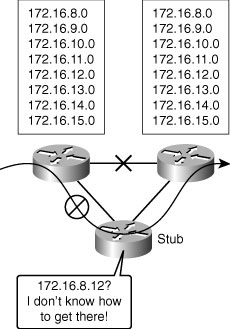
![]() Transit traffic is external traffic passing through a network or site (see Figure 3-3).
Transit traffic is external traffic passing through a network or site (see Figure 3-3).
![]() Remote sites generally are connected with lower bandwidth than is present in the network core. Remote sites are rarely desirable as transit networks to forward network from one place to another. Remote sites typically cannot handle the traffic volume needed to be a viable routing alternative to the core network. In general, when core connectivity fails, routing should not detour via a remote site.
Remote sites generally are connected with lower bandwidth than is present in the network core. Remote sites are rarely desirable as transit networks to forward network from one place to another. Remote sites typically cannot handle the traffic volume needed to be a viable routing alternative to the core network. In general, when core connectivity fails, routing should not detour via a remote site.
![]() In OSPF, there is little control over intra-area traffic. LSAs cannot be filtered within an area. OSPF does not allow traffic to arbitrarily route into and then out of an area. The exception is area 0, which can be used for transit when another area becomes discontiguous.
In OSPF, there is little control over intra-area traffic. LSAs cannot be filtered within an area. OSPF does not allow traffic to arbitrarily route into and then out of an area. The exception is area 0, which can be used for transit when another area becomes discontiguous.
![]() With EIGRP, it can be desirable to configure EIGRP stub networks. This informs central routers that they should not use a remote site as a transit network. In addition, the use of stub networks damps unnecessary EIGRP queries, speeding network convergence. Filtering can help manage which parts of the network are available for transit in an EIGRP network.
With EIGRP, it can be desirable to configure EIGRP stub networks. This informs central routers that they should not use a remote site as a transit network. In addition, the use of stub networks damps unnecessary EIGRP queries, speeding network convergence. Filtering can help manage which parts of the network are available for transit in an EIGRP network.
![]() With BGP, the most common concern about transit traffic is when a site has two Internet connections. If there is no filtering, the connections advertise routes. This advertisement can put the site at risk of becoming a transit network. This should not be a problem with two connections to the same ISP, because the autonomous system number is present in the autonomous system path. Based on the autonomous system path, the ISP router ignores any routes advertised from the ISP to the site and then back to the ISP.
With BGP, the most common concern about transit traffic is when a site has two Internet connections. If there is no filtering, the connections advertise routes. This advertisement can put the site at risk of becoming a transit network. This should not be a problem with two connections to the same ISP, because the autonomous system number is present in the autonomous system path. Based on the autonomous system path, the ISP router ignores any routes advertised from the ISP to the site and then back to the ISP.
![]() When two ISPs are involved, the site might inadvertently become a transit site. The best approach is to filter routes advertised outbound to the ISPs, and ensure that only the company or site prefixes are advertised outward. Tagging routes with a BGP community is an easy way to do this. All inbound routes received from the ISP should be filtered, too, so that you accept only the routes the ISP should be sending you.
When two ISPs are involved, the site might inadvertently become a transit site. The best approach is to filter routes advertised outbound to the ISPs, and ensure that only the company or site prefixes are advertised outward. Tagging routes with a BGP community is an easy way to do this. All inbound routes received from the ISP should be filtered, too, so that you accept only the routes the ISP should be sending you.
 Defensive Filtering
Defensive Filtering
![]() Route filtering can also be used defensively against inaccurate or inappropriate routing traffic (see Figure 3-4).
Route filtering can also be used defensively against inaccurate or inappropriate routing traffic (see Figure 3-4).
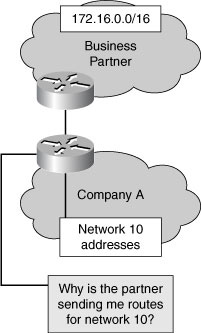
![]() One common problem some organizations have is that they learn inappropriate routes from another organization, such as a business partner. Your business partner should not be advertising your routing prefixes back to your network. Those destinations are not reached through the partner, unless you have a very odd network design. The default route should not be reached via the partner, unless the partner is providing your network with Internet connectivity.
One common problem some organizations have is that they learn inappropriate routes from another organization, such as a business partner. Your business partner should not be advertising your routing prefixes back to your network. Those destinations are not reached through the partner, unless you have a very odd network design. The default route should not be reached via the partner, unless the partner is providing your network with Internet connectivity.
![]() Inappropriate partner advertisements can disrupt routing without filtering. For example, a partner may define a static route to your data center. If this route leaks into your routing process, a portion of your network might think that the data center has moved to a location behind the router of the partner.
Inappropriate partner advertisements can disrupt routing without filtering. For example, a partner may define a static route to your data center. If this route leaks into your routing process, a portion of your network might think that the data center has moved to a location behind the router of the partner.
![]() Defensive filtering protects the network from disruptions due to incorrect advertisements of others. You configure which routing updates your routers should accept from the partner and which routing updates should be ignored. For example, you would not accept routing updates about how to get to your own prefixes or about default routing.
Defensive filtering protects the network from disruptions due to incorrect advertisements of others. You configure which routing updates your routers should accept from the partner and which routing updates should be ignored. For example, you would not accept routing updates about how to get to your own prefixes or about default routing.
![]() For security reasons, you should advertise to a partner only the prefixes that you want them to be able to reach. This provides the partner with minimum information about your network and is part of a layered security approach. It also ensures that if there is an accidental leak of another partner’s routes or static routes into the dynamic routing process, the inappropriate information does not also leak to others.
For security reasons, you should advertise to a partner only the prefixes that you want them to be able to reach. This provides the partner with minimum information about your network and is part of a layered security approach. It also ensures that if there is an accidental leak of another partner’s routes or static routes into the dynamic routing process, the inappropriate information does not also leak to others.
![]() The approach of blocking route advertisements is also called route hiding or route starvation. Traffic cannot get to the hidden subnets from the partner unless a summary route is also present. Packet filtering access control lists (ACL) should also be used to supplement security by route starvation.
The approach of blocking route advertisements is also called route hiding or route starvation. Traffic cannot get to the hidden subnets from the partner unless a summary route is also present. Packet filtering access control lists (ACL) should also be used to supplement security by route starvation.
Designing Redistribution
![]() Redistribution is a powerful tool for manipulating and managing routing updates, particularly when two routing protocols are present in a network (see Figure 3-5).
Redistribution is a powerful tool for manipulating and managing routing updates, particularly when two routing protocols are present in a network (see Figure 3-5).
![]() In some situations, routing redistribution is useful and even necessary. These include migration between routing protocols, corporate mergers, reorganization, and support for devices that speak only Routing Information Protocol (RIP) or OSPF.
In some situations, routing redistribution is useful and even necessary. These include migration between routing protocols, corporate mergers, reorganization, and support for devices that speak only Routing Information Protocol (RIP) or OSPF.
![]() However, redistribution should be used with planning and some degree of caution. It is very easy to create routing loops with redistribution. This is particularly true when there are multiple redistribution points, sometimes coupled with static routes, inconsistent routing summaries, or route filters.
However, redistribution should be used with planning and some degree of caution. It is very easy to create routing loops with redistribution. This is particularly true when there are multiple redistribution points, sometimes coupled with static routes, inconsistent routing summaries, or route filters.
![]() Experience teaches that it is much better to have distinct pockets of routing protocols and redistribute than to have a random mix of routers and routing protocols with ad hoc redistribution. Therefore, running corporate EIGRP with redistribution into RIP or OSPF for a region that has routers from other vendors is viable, with due care. On the other hand, freely intermixing OSPF-speaking routers with EIGRP routers in ad hoc fashion is just asking for major problems.
Experience teaches that it is much better to have distinct pockets of routing protocols and redistribute than to have a random mix of routers and routing protocols with ad hoc redistribution. Therefore, running corporate EIGRP with redistribution into RIP or OSPF for a region that has routers from other vendors is viable, with due care. On the other hand, freely intermixing OSPF-speaking routers with EIGRP routers in ad hoc fashion is just asking for major problems.
![]() When there is more than one interconnection point between two regions using different routing protocols, bidirectional redistribution is commonly considered. When running OSPF and EIGRP in two regions, it is attractive to redistribute OSPF into EIGRP, and EIGRP into OSPF.
When there is more than one interconnection point between two regions using different routing protocols, bidirectional redistribution is commonly considered. When running OSPF and EIGRP in two regions, it is attractive to redistribute OSPF into EIGRP, and EIGRP into OSPF.
 Filtered Redistribution
Filtered Redistribution
![]() When you use bidirectional redistribution, you should prevent re-advertising information back into the routing protocol region or autonomous system that it originally came from (see Figure 3-6).
When you use bidirectional redistribution, you should prevent re-advertising information back into the routing protocol region or autonomous system that it originally came from (see Figure 3-6).
![]() For example, filters should be used so that OSPF information that was redistributed into EIGRP does not get re-advertised into OSPF. You also need to prevent information that came from EIGRP into OSPF from being re-advertised back into the EIGRP part of the network. This is sometimes called a manual split horizon. Split horizon is a routing protocol feature. The idea behind it is that it is counterproductive to advertise information back to the source of that information, because the information may be out of date or incorrect, and because the source of the information is presumed to be better informed.
For example, filters should be used so that OSPF information that was redistributed into EIGRP does not get re-advertised into OSPF. You also need to prevent information that came from EIGRP into OSPF from being re-advertised back into the EIGRP part of the network. This is sometimes called a manual split horizon. Split horizon is a routing protocol feature. The idea behind it is that it is counterproductive to advertise information back to the source of that information, because the information may be out of date or incorrect, and because the source of the information is presumed to be better informed.
![]() If you do not do this filtering or use a manual split horizon, you will probably see strange convergence after an outage, you will probably see routing loops, and in general, there will be routing problems and instability.
If you do not do this filtering or use a manual split horizon, you will probably see strange convergence after an outage, you will probably see routing loops, and in general, there will be routing problems and instability.
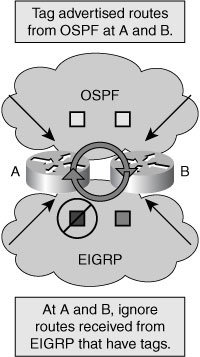
![]() Both EIGRP and OSPF support the tagging of routes. A route map can be used to add the numeric tag to specific prefixes. The tag information is then passed along in routing updates. Another router may then filter out routes that match, or do not match, the tag. This is done using a route map in a distribution list.
Both EIGRP and OSPF support the tagging of routes. A route map can be used to add the numeric tag to specific prefixes. The tag information is then passed along in routing updates. Another router may then filter out routes that match, or do not match, the tag. This is done using a route map in a distribution list.
![]() One typical use of tags is with redistribution. In the figure, routers A and B can apply tags to routes from IGP X when they are advertised outbound into IGP Y. This in effect marks them as routes from IGP X. When routers A and B receive routes from Y, they would then filter out routes marked as from X when received from IGP Y, because both routers learn such routes directly from IGP X. The process of filtering also applies in the opposite direction.
One typical use of tags is with redistribution. In the figure, routers A and B can apply tags to routes from IGP X when they are advertised outbound into IGP Y. This in effect marks them as routes from IGP X. When routers A and B receive routes from Y, they would then filter out routes marked as from X when received from IGP Y, because both routers learn such routes directly from IGP X. The process of filtering also applies in the opposite direction.
![]() The point is to get routes in the most direct way, not via an indirect information path that might be passing along old information.
The point is to get routes in the most direct way, not via an indirect information path that might be passing along old information.
 Migrating Between Routing Protocols
Migrating Between Routing Protocols
![]() This topic discusses two common approaches for migrating between routing protocols. One approach for migrating between routing protocols is to use administrative distance (AD) to migrate the routing protocols. Another approach is to use redistribution and a moving boundary.
This topic discusses two common approaches for migrating between routing protocols. One approach for migrating between routing protocols is to use administrative distance (AD) to migrate the routing protocols. Another approach is to use redistribution and a moving boundary.
![]() Migration by AD does not use redistribution. Instead, two routing protocols are run at the same time with the same routes. This assumes sufficient memory, CPU, and bandwidth are in place to support this on the routers running two routing protocols.
Migration by AD does not use redistribution. Instead, two routing protocols are run at the same time with the same routes. This assumes sufficient memory, CPU, and bandwidth are in place to support this on the routers running two routing protocols.
![]() The first step in migration by AD is to turn on the new protocol, but make sure that it has a higher AD than the existing routing protocol so it is not preferred. This step enables the protocol and allows adjacencies or neighbors and routing databases to be checked, but does not actually rely on the new routing protocol for routing decisions.
The first step in migration by AD is to turn on the new protocol, but make sure that it has a higher AD than the existing routing protocol so it is not preferred. This step enables the protocol and allows adjacencies or neighbors and routing databases to be checked, but does not actually rely on the new routing protocol for routing decisions.
![]() When the new protocol is fully deployed, various checks can be done with show commands to confirm proper deployment. Then the cutover takes place. In cutover, the AD is shifted for one of the two protocols, so that the new routing protocol will now have a lower AD.
When the new protocol is fully deployed, various checks can be done with show commands to confirm proper deployment. Then the cutover takes place. In cutover, the AD is shifted for one of the two protocols, so that the new routing protocol will now have a lower AD.
![]() Final steps in this process include the following:
Final steps in this process include the following:
-
 Check for any prefixes learned only via the old protocol.
Check for any prefixes learned only via the old protocol. -
 Check for any strange next hops (perhaps using some form of automated comparison).
Check for any strange next hops (perhaps using some form of automated comparison).
![]() With migration by redistribution, the migration is staged as a series of smaller steps. In each step, part of the network is converted from the old to the new routing protocol. In a big network, the AD approach might be used to support this conversion. In a smaller network, an overnight cutover or simpler approach might suffice.
With migration by redistribution, the migration is staged as a series of smaller steps. In each step, part of the network is converted from the old to the new routing protocol. In a big network, the AD approach might be used to support this conversion. In a smaller network, an overnight cutover or simpler approach might suffice.
![]() To provide full connectivity during migration by redistribution, the boundary routers between the two parts of the network would have to bidirectionally redistribute between protocols. Filtering via tags would be one relatively simple way to manage this. The boundary routers move as more of the region is migrated.
To provide full connectivity during migration by redistribution, the boundary routers between the two parts of the network would have to bidirectionally redistribute between protocols. Filtering via tags would be one relatively simple way to manage this. The boundary routers move as more of the region is migrated.







0 comments
Post a Comment