![]() This chapter starts by describing network security, including threats and risks, and network security policies. The Cisco Self-Defending Network strategy for designing network security is explored. The chapter concludes with a discussion of Cisco network security solutions for enterprise networks.
This chapter starts by describing network security, including threats and risks, and network security policies. The Cisco Self-Defending Network strategy for designing network security is explored. The chapter concludes with a discussion of Cisco network security solutions for enterprise networks.
| Note |
|
 Network Security
Network Security
![]() The scope of a network security solution is determined by organizational requirements and by potential threats to the organization. To create a secure network, the threats against which the network has to be protected must be determined. This section discusses the rationale for network security, including various threats and risks. Creating a network security policy is key to understanding and implementing security; network security policies and processes are discussed, and using risk assessment to create a security policy is explained.
The scope of a network security solution is determined by organizational requirements and by potential threats to the organization. To create a secure network, the threats against which the network has to be protected must be determined. This section discusses the rationale for network security, including various threats and risks. Creating a network security policy is key to understanding and implementing security; network security policies and processes are discussed, and using risk assessment to create a security policy is explained.
 The Need for Network Security
The Need for Network Security
![]() In the distant past, networks were designed to be open, and network security was largely a matter of physical security. As networks become increasingly interconnected and data flows more freely, security services become critical. In the commercial world, connectivity is no longer optional; the possible risks of providing connectivity do not outweigh its benefits, including revenue generation. Therefore, security services must provide adequate protection to allow organizations to conduct business in a relatively open environment.
In the distant past, networks were designed to be open, and network security was largely a matter of physical security. As networks become increasingly interconnected and data flows more freely, security services become critical. In the commercial world, connectivity is no longer optional; the possible risks of providing connectivity do not outweigh its benefits, including revenue generation. Therefore, security services must provide adequate protection to allow organizations to conduct business in a relatively open environment.
![]() Secure networks are required not only to defend against attacks and prevent unauthorized access; legislation, industry regulations, and company policies might also require secure networks to keep data private and ensure that it is not misused.
Secure networks are required not only to defend against attacks and prevent unauthorized access; legislation, industry regulations, and company policies might also require secure networks to keep data private and ensure that it is not misused.
Network Security Requirements
![]() Network security should include the following requirements:
Network security should include the following requirements:
-
 Prevent external hackers from getting access to the network
Prevent external hackers from getting access to the network -
 Allow only authorized users into the network
Allow only authorized users into the network -
 Prevent those inside the network from executing deliberate or inadvertent attacks
Prevent those inside the network from executing deliberate or inadvertent attacks -
 Provide different levels of access for different types of users
Provide different levels of access for different types of users -
 Protect data from misuse and corruption
Protect data from misuse and corruption -
 Comply with security legislation, industry standards, and company policies
Comply with security legislation, industry standards, and company policies
![]() To be truly effective, network security must meet these requirements in a way that is transparent to users, easy to administer, and does not disrupt business.
To be truly effective, network security must meet these requirements in a way that is transparent to users, easy to administer, and does not disrupt business.
Security Legislation Examples
![]() Security legislation and industry standards might define how data has to be handled, how to make sure that private information is protected, and what kind of information can be public. Based on legislative mandates and industry directives, organizations might have to protect customer records and privacy and even encrypt data to help ensure that the network is secure. Some examples of laws and directives influencing network security include the following:
Security legislation and industry standards might define how data has to be handled, how to make sure that private information is protected, and what kind of information can be public. Based on legislative mandates and industry directives, organizations might have to protect customer records and privacy and even encrypt data to help ensure that the network is secure. Some examples of laws and directives influencing network security include the following:
-
 The U.S. Gramm-Leach-Bliley Act of 1999 (GLBA): Information that many individuals would consider private—including bank balances and account numbers—is regularly bought and sold by banks, credit card companies, and other financial institutions. The GLBA, which is also known as the Financial Services Modernization Act of 1999, provides limited privacy protections against the sale of private financial information and codifies protections against pretexting, the practice of obtaining personal information through false pretenses.
The U.S. Gramm-Leach-Bliley Act of 1999 (GLBA): Information that many individuals would consider private—including bank balances and account numbers—is regularly bought and sold by banks, credit card companies, and other financial institutions. The GLBA, which is also known as the Financial Services Modernization Act of 1999, provides limited privacy protections against the sale of private financial information and codifies protections against pretexting, the practice of obtaining personal information through false pretenses. -
 The U.S. Health Insurance Portability and Accountability Act (HIPAA): HIPAA is U.S. federal legislation that was passed into law in August 1996. The overall purpose of the act is to enable better access to health insurance, reduce fraud and abuse, and lower the overall cost of health care in the United States. The HIPAA security regulations apply to protected health information that is electronically maintained or used in an electronic transmission. Thousands of U.S. organizations must comply with the HIPAA security rule.
The U.S. Health Insurance Portability and Accountability Act (HIPAA): HIPAA is U.S. federal legislation that was passed into law in August 1996. The overall purpose of the act is to enable better access to health insurance, reduce fraud and abuse, and lower the overall cost of health care in the United States. The HIPAA security regulations apply to protected health information that is electronically maintained or used in an electronic transmission. Thousands of U.S. organizations must comply with the HIPAA security rule. -
 European Union data protection Directive 95/46/EC: This directive requires that European Union member states protect people’s privacy rights when processing personal data, and that the flow of personal data between member states must not be restricted or prohibited because of these privacy rights.
European Union data protection Directive 95/46/EC: This directive requires that European Union member states protect people’s privacy rights when processing personal data, and that the flow of personal data between member states must not be restricted or prohibited because of these privacy rights. -
 The U.S. Sarbanes-Oxley Act of 2002 (SOX): This U.S. Federal law, passed in response to a number of major corporate scandals, is also known as the Public Company Accounting Reform and Investor Protection Act. SOX establishes new or enhanced auditing and financial standards for all U.S. public company boards, management, and public accounting firms. The act contains 11 sections, ranging from additional corporate board responsibilities to criminal penalties, and requires the U.S. Securities and Exchange Commission to implement rulings on requirements to comply with the new law.
The U.S. Sarbanes-Oxley Act of 2002 (SOX): This U.S. Federal law, passed in response to a number of major corporate scandals, is also known as the Public Company Accounting Reform and Investor Protection Act. SOX establishes new or enhanced auditing and financial standards for all U.S. public company boards, management, and public accounting firms. The act contains 11 sections, ranging from additional corporate board responsibilities to criminal penalties, and requires the U.S. Securities and Exchange Commission to implement rulings on requirements to comply with the new law. -
 Payment Card Industry (PCI) Data Security Standard (DSS): The PCI DSS was developed to ensure safe handling of sensitive payment information, such as the storage and transfer of credit card information. The PCI DSS is the umbrella program for other programs, such as the Visa Cardholder Information Security program and MasterCard Site Data Protection program.
Payment Card Industry (PCI) Data Security Standard (DSS): The PCI DSS was developed to ensure safe handling of sensitive payment information, such as the storage and transfer of credit card information. The PCI DSS is the umbrella program for other programs, such as the Visa Cardholder Information Security program and MasterCard Site Data Protection program. -
 The Canadian Personal Information Protection and Electronic Documents Act (PIPEDA): This act establishes rules for managing personal information by organizations involved in commercial activities. It aims to strike a balance between an individual’s right to the protection of personal information and the need of organizations to obtain and handle such information for legitimate business purposes.
The Canadian Personal Information Protection and Electronic Documents Act (PIPEDA): This act establishes rules for managing personal information by organizations involved in commercial activities. It aims to strike a balance between an individual’s right to the protection of personal information and the need of organizations to obtain and handle such information for legitimate business purposes.
 Terminology Related to Security
Terminology Related to Security
![]() This section defines some terms related to security used throughout the rest of the chapter.
This section defines some terms related to security used throughout the rest of the chapter.
![]() Most of us equate hacking with malicious activities. In fact, hacking really means to work diligently on a computer system until it performs optimally. The popular use of the term hacking is more related to cracking, which is defined as the act of unlawfully accessing a network infrastructure to perform unethical activities. But for the purposes of this book, the widely accepted term hacking denotes malicious activities directed at networks and systems.
Most of us equate hacking with malicious activities. In fact, hacking really means to work diligently on a computer system until it performs optimally. The popular use of the term hacking is more related to cracking, which is defined as the act of unlawfully accessing a network infrastructure to perform unethical activities. But for the purposes of this book, the widely accepted term hacking denotes malicious activities directed at networks and systems.
![]() A virus is a program that triggers a damaging outcome. Viruses often disguise themselves as executables with clever filenames like “You won.” Viruses can be delivered via an e-mail or a website; a virus requires a human action, such as opening an e-mail attachment, to be activated. A worm is a virus that can self-duplicate. A worm might also be able to scan a network and infect neighboring workstations.
A virus is a program that triggers a damaging outcome. Viruses often disguise themselves as executables with clever filenames like “You won.” Viruses can be delivered via an e-mail or a website; a virus requires a human action, such as opening an e-mail attachment, to be activated. A worm is a virus that can self-duplicate. A worm might also be able to scan a network and infect neighboring workstations.
![]() A Trojan horse pretends to be an inoffensive application when in fact it might contain a destructive payload. An example of a Trojan horse is an attachment that, after being opened, shows a picture of a cute puppy, but in the background, the code is reading the e-mail addresses of the user’s address book and forwarding those addresses to a hacker’s repository for future spam use.
A Trojan horse pretends to be an inoffensive application when in fact it might contain a destructive payload. An example of a Trojan horse is an attachment that, after being opened, shows a picture of a cute puppy, but in the background, the code is reading the e-mail addresses of the user’s address book and forwarding those addresses to a hacker’s repository for future spam use.
![]() Attacks are becoming more complex. Malware is a generic term that describes malicious software such as viruses and Trojan horses. Combo malware is a hybrid menace that combines destructive components of different threats. A worm that carries a viral payload is an example of combo malware.
Attacks are becoming more complex. Malware is a generic term that describes malicious software such as viruses and Trojan horses. Combo malware is a hybrid menace that combines destructive components of different threats. A worm that carries a viral payload is an example of combo malware.
![]() Spam is unsolicited, unwanted e-mail. Spam might contain viruses or other threats, or point to infected or dangerous websites.
Spam is unsolicited, unwanted e-mail. Spam might contain viruses or other threats, or point to infected or dangerous websites.
![]() Spyware is a program that gathers information without the user’s knowledge or consent and sends it back to the hacker. For example, spyware could log keystrokes, upload information (such as all addresses in the victim’s address book), or download a program (known as a zombie) that waits for further instructions from the hacker.
Spyware is a program that gathers information without the user’s knowledge or consent and sends it back to the hacker. For example, spyware could log keystrokes, upload information (such as all addresses in the victim’s address book), or download a program (known as a zombie) that waits for further instructions from the hacker.
![]() Phishing e-mails try to convince the victim to release personal information; the e-mail appears to come from a legitimate source, and it directs the victim to website that looks legitimate. When the victim enters his or her information (such as usernames and passwords) on the counterfeit website, it is sent to the hacker.
Phishing e-mails try to convince the victim to release personal information; the e-mail appears to come from a legitimate source, and it directs the victim to website that looks legitimate. When the victim enters his or her information (such as usernames and passwords) on the counterfeit website, it is sent to the hacker.
![]() Spear phishing is a very targeted phishing attack. For example, a hacker sends an e-mail that appears to be from a company’s Human Resources department, asking all employees to confirm their banking information, or they won’t get paid. If any employees reply with their information, the hacker may use it to gain access to their bank accounts.
Spear phishing is a very targeted phishing attack. For example, a hacker sends an e-mail that appears to be from a company’s Human Resources department, asking all employees to confirm their banking information, or they won’t get paid. If any employees reply with their information, the hacker may use it to gain access to their bank accounts.
![]() Social engineering is the practice of obtaining confidential information by manipulating legitimate users. Examples include the following:
Social engineering is the practice of obtaining confidential information by manipulating legitimate users. Examples include the following:
-
 Getting physical access: A hacker might get confidential information and passwords by having physical access to the organization. For example, the hacker might visit an organization and see passwords that are insecurely posted in an office or cubicle.
Getting physical access: A hacker might get confidential information and passwords by having physical access to the organization. For example, the hacker might visit an organization and see passwords that are insecurely posted in an office or cubicle. -
 Using a psychological approach: A hacker might exploit human nature to obtain access to confidential information. For example, a hacker might send an e-mail or call and ask for passwords, pretending that the information is required to maintain the victim’s account.
Using a psychological approach: A hacker might exploit human nature to obtain access to confidential information. For example, a hacker might send an e-mail or call and ask for passwords, pretending that the information is required to maintain the victim’s account.
 Threats and Risks
Threats and Risks
![]() Designing a secure network requires an understanding of the types of attacks that can compromise system security and their associated risks. The threats to network security can be classified into the following three categories:
Designing a secure network requires an understanding of the types of attacks that can compromise system security and their associated risks. The threats to network security can be classified into the following three categories:
-
 Reconnaissance: Reconnaissance is the active gathering of information about an enemy or target; the idea is to learn as much as possible about the target and the involved systems. In the network security area, reconnaissance is usually the prelude to a more focused attack against a particular target.
Reconnaissance: Reconnaissance is the active gathering of information about an enemy or target; the idea is to learn as much as possible about the target and the involved systems. In the network security area, reconnaissance is usually the prelude to a more focused attack against a particular target. -
 Gaining unauthorized system access: After information about the target system is known, the next step is gaining access to the system by exploiting the system or using social engineering techniques.
Gaining unauthorized system access: After information about the target system is known, the next step is gaining access to the system by exploiting the system or using social engineering techniques. -
 Denial of service (DoS): Even if direct access to a system is not possible, another type of threat is DoS. A DoS attack is used to make systems unusable by overloading their resources such as CPU or bandwidth. When multiple sources conduct a DoS attack, it is called a distributed DoS (DDoS) attack.
Denial of service (DoS): Even if direct access to a system is not possible, another type of threat is DoS. A DoS attack is used to make systems unusable by overloading their resources such as CPU or bandwidth. When multiple sources conduct a DoS attack, it is called a distributed DoS (DDoS) attack.
![]() To provide adequate protection of network resources, the network procedures and technologies need to address the following security risks:
To provide adequate protection of network resources, the network procedures and technologies need to address the following security risks:
-
 Confidentiality of data: Confidentiality should ensure that only authorized users can view sensitive information, to prevent theft, legal liabilities, and damage to the organization.
Confidentiality of data: Confidentiality should ensure that only authorized users can view sensitive information, to prevent theft, legal liabilities, and damage to the organization. -
 Integrity of data: Integrity should ensure that only authorized users can change sensitive information and guarantee the authenticity of data.
Integrity of data: Integrity should ensure that only authorized users can change sensitive information and guarantee the authenticity of data. -
 System and data availability: Availability should ensure uninterrupted access to important computing resources to prevent business disruption and loss of productivity.
System and data availability: Availability should ensure uninterrupted access to important computing resources to prevent business disruption and loss of productivity.
![]() Given the broad range of potential threats, everything in the network is a potential target. Hosts are typically the preferred target for worms and viruses. For example, host files could be corrupted in an attack, and the compromised host could be used to launch attacks against other hosts, creating a botnet. However, other high-value targets include the following:
Given the broad range of potential threats, everything in the network is a potential target. Hosts are typically the preferred target for worms and viruses. For example, host files could be corrupted in an attack, and the compromised host could be used to launch attacks against other hosts, creating a botnet. However, other high-value targets include the following:
-
 Network infrastructure devices, including routers and switches
Network infrastructure devices, including routers and switches -
 Support services, such as Dynamic Host Configuration Protocol (DHCP) and Domain Name System servers
Support services, such as Dynamic Host Configuration Protocol (DHCP) and Domain Name System servers -
 Endpoints, including IP phones, management stations, and user endpoints (such as PCs and laptops)
Endpoints, including IP phones, management stations, and user endpoints (such as PCs and laptops) -
 Network infrastructure, including the network capacity or bandwidth
Network infrastructure, including the network capacity or bandwidth -
 Security devices, including firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS)
Security devices, including firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS)
![]() The various threats and risks are described further in the following sections.
The various threats and risks are described further in the following sections.
Threat: Reconnaissance Attacks
![]() Reconnaissance attacks aim to discover information about a network, including the following:
Reconnaissance attacks aim to discover information about a network, including the following:
-
 Active targets
Active targets -
 Network services that are running
Network services that are running -
 Trust relationships
Trust relationships -
 File permissions
File permissions -
 User account information
User account information
![]() A common technique to find active targets such as networking devices and user endpoints is port scanning, in which data is sent to various TCP and User Datagram Protocol (UDP) ports on a device and the response from the device is evaluated.
A common technique to find active targets such as networking devices and user endpoints is port scanning, in which data is sent to various TCP and User Datagram Protocol (UDP) ports on a device and the response from the device is evaluated.
![]() To avoid reconnaissance attacks, a network should be tested to see how much it would reveal if attacked. The following are some examples of port-scanning tools:
To avoid reconnaissance attacks, a network should be tested to see how much it would reveal if attacked. The following are some examples of port-scanning tools:
-
 Network Mapper (Nmap): Nmap is a free open-source utility for network exploration or security auditing. It was designed to rapidly scan large networks; it also maps single hosts.
Network Mapper (Nmap): Nmap is a free open-source utility for network exploration or security auditing. It was designed to rapidly scan large networks; it also maps single hosts. -
 NetStumbler: NetStumbler is a tool for Microsoft Windows that facilitates detection of WLANs using the IEEE 802.11b, 802.11a, and 802.11g WLAN standards. A trimmed-down version of the tool called MiniStumbler is available for Windows CE.
NetStumbler: NetStumbler is a tool for Microsoft Windows that facilitates detection of WLANs using the IEEE 802.11b, 802.11a, and 802.11g WLAN standards. A trimmed-down version of the tool called MiniStumbler is available for Windows CE. -
 SuperScan: SuperScan is a popular Windows port-scanning tool with high scanning speed, host detection, extensive banner grabbing, and Windows host enumeration capability.
SuperScan: SuperScan is a popular Windows port-scanning tool with high scanning speed, host detection, extensive banner grabbing, and Windows host enumeration capability. -
 Kismet: Kismet is an 802.11 Layer 2 wireless network detector, sniffer, and IDS that can sniff 802.11b, 802.11a, and 802.11g traffic. It identifies networks by passively collecting packets and detecting standard named networks, detecting hidden networks, and inferring the presence of nonbeaconing networks (networks that do not advertise themselves) via data traffic.
Kismet: Kismet is an 802.11 Layer 2 wireless network detector, sniffer, and IDS that can sniff 802.11b, 802.11a, and 802.11g traffic. It identifies networks by passively collecting packets and detecting standard named networks, detecting hidden networks, and inferring the presence of nonbeaconing networks (networks that do not advertise themselves) via data traffic.
![]() Port-scanning tools are designed to scan large networks and determine which hosts are up and the services they offer. The tools support a large number of scanning techniques, such as UDP, TCP connect (open), TCP SYN (half open), FTP proxy (bounce attack), Internet Control Message Protocol (ICMP) (ping sweep), FIN, ACK sweep, Xmas Tree (which sets the FIN, PSH, and URG flags and therefore appears to light up the packet like a Christmas tree), SYN sweep, IP Protocol, and Null scans. After TCP or UDP ports are discovered using one of the scan methods, version detection communicates with those ports to try to determine more about what is actually running.
Port-scanning tools are designed to scan large networks and determine which hosts are up and the services they offer. The tools support a large number of scanning techniques, such as UDP, TCP connect (open), TCP SYN (half open), FTP proxy (bounce attack), Internet Control Message Protocol (ICMP) (ping sweep), FIN, ACK sweep, Xmas Tree (which sets the FIN, PSH, and URG flags and therefore appears to light up the packet like a Christmas tree), SYN sweep, IP Protocol, and Null scans. After TCP or UDP ports are discovered using one of the scan methods, version detection communicates with those ports to try to determine more about what is actually running.
![]() Other tools, called vulnerability scanners, help find known vulnerabilities in a network. The tools use either passive scanning (by analyzing network traffic) or active testing (by sending packets through the network). The following are examples of vulnerability scanning tools:
Other tools, called vulnerability scanners, help find known vulnerabilities in a network. The tools use either passive scanning (by analyzing network traffic) or active testing (by sending packets through the network). The following are examples of vulnerability scanning tools:
-
 Nessus: Nessus is an open-source product designed to automate the testing and discovery of known security problems. A Windows graphical front end is available, although the core Nessus product requires Linux or UNIX to run.
Nessus: Nessus is an open-source product designed to automate the testing and discovery of known security problems. A Windows graphical front end is available, although the core Nessus product requires Linux or UNIX to run. -
 Microsoft Baseline Security Analyzer (MBSA): Although it’s not a true vulnerability scanner, companies that rely primarily on Microsoft Windows products can use the freely available MBSA. MBSA scans the system and identifies whether any patches are missing for products such as the Windows operating systems, Internet Information Server, SQL Server, Exchange Server, Internet Explorer, Windows Media Player, and Microsoft Office products. MBSA also identifies missing or weak passwords and other common security issues.
Microsoft Baseline Security Analyzer (MBSA): Although it’s not a true vulnerability scanner, companies that rely primarily on Microsoft Windows products can use the freely available MBSA. MBSA scans the system and identifies whether any patches are missing for products such as the Windows operating systems, Internet Information Server, SQL Server, Exchange Server, Internet Explorer, Windows Media Player, and Microsoft Office products. MBSA also identifies missing or weak passwords and other common security issues. -
 Security Administrator’s Integrated Network Tool (SAINT): SAINT is a commercial vulnerability assessment tool that runs exclusively on UNIX.
Security Administrator’s Integrated Network Tool (SAINT): SAINT is a commercial vulnerability assessment tool that runs exclusively on UNIX.
![]() The following are some sites where published vulnerability information is available:
The following are some sites where published vulnerability information is available:
-
 CERT Coordination Center (CERT/CC): http://www.cert.org/certcc.html
CERT Coordination Center (CERT/CC): http://www.cert.org/certcc.html -
 MITRE Common Vulnerabilities and Exposures: http://www.cve.mitre.org/
MITRE Common Vulnerabilities and Exposures: http://www.cve.mitre.org/ -
 Microsoft Security Bulletin Summaries and Webcasts: http://www.microsoft.com/technet/security/bulletin/summary.mspx
Microsoft Security Bulletin Summaries and Webcasts: http://www.microsoft.com/technet/security/bulletin/summary.mspx -
 Cisco Security Notices: http://www.cisco.com/en/US/products/products_security_advisories_listing.html
Cisco Security Notices: http://www.cisco.com/en/US/products/products_security_advisories_listing.html
Threat: Gaining Unauthorized Access to Systems
![]() There are many ways that hackers gain access to systems. One often-seen threat is the knowledge of usernames and passwords by unauthorized persons. For example, known vulnerabilities in operating systems or services could be exploited, usernames and passwords could be captured or cracked, or the default administrative or service accounts might be accessible. It might be possible to decrypt or crack passwords from a system password file or by capturing passwords when they are being transmitted over the network. If a hacker gains access to a sufficiently privileged account, that person might gain access to all files on the system and might also be able to exploit other systems based on the user trust relationships across systems.
There are many ways that hackers gain access to systems. One often-seen threat is the knowledge of usernames and passwords by unauthorized persons. For example, known vulnerabilities in operating systems or services could be exploited, usernames and passwords could be captured or cracked, or the default administrative or service accounts might be accessible. It might be possible to decrypt or crack passwords from a system password file or by capturing passwords when they are being transmitted over the network. If a hacker gains access to a sufficiently privileged account, that person might gain access to all files on the system and might also be able to exploit other systems based on the user trust relationships across systems.
![]() Another way that hackers gain access to a system is through various methods of social engineering. As mentioned, this could include exploiting human nature and gaining physical access to an organization. The impact of gaining system access could include exposure or compromise of sensitive data or machines, and the execution of arbitrary commands on the system.
Another way that hackers gain access to a system is through various methods of social engineering. As mentioned, this could include exploiting human nature and gaining physical access to an organization. The impact of gaining system access could include exposure or compromise of sensitive data or machines, and the execution of arbitrary commands on the system.
Threat: DoS
![]() DoS attacks attempt to compromise the availability of a network, host, or application. DoS and DDoS attacks are considered a major risk because they can easily interrupt business processes and cause significant loss. DoS attacks are relatively simple to conduct, even by an unskilled attacker.
DoS attacks attempt to compromise the availability of a network, host, or application. DoS and DDoS attacks are considered a major risk because they can easily interrupt business processes and cause significant loss. DoS attacks are relatively simple to conduct, even by an unskilled attacker.
![]() Two methods of causing a DoS attack are by sending malformed data and by sending a large quantity of data. A successful DoS attack is usually the consequence of one of the following failures:
Two methods of causing a DoS attack are by sending malformed data and by sending a large quantity of data. A successful DoS attack is usually the consequence of one of the following failures:
-
 The incapability of a network, host, or application to handle an enormous quantity of data, which renders the system unresponsive or brings it to a halt. The difficulty of defending against such an attack lies in the difficulty of distinguishing legitimate data from attack data.
The incapability of a network, host, or application to handle an enormous quantity of data, which renders the system unresponsive or brings it to a halt. The difficulty of defending against such an attack lies in the difficulty of distinguishing legitimate data from attack data. -
 The failure of a host or application to handle an unexpected condition, such as maliciously formatted input data, an unexpected interaction of system components, or simple resource exhaustion.
The failure of a host or application to handle an unexpected condition, such as maliciously formatted input data, an unexpected interaction of system components, or simple resource exhaustion.
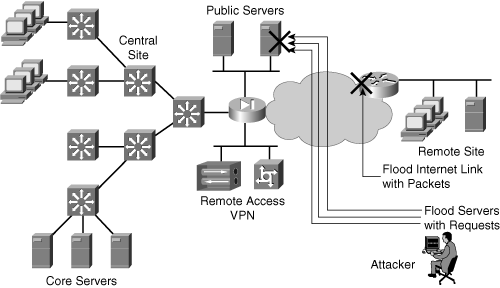
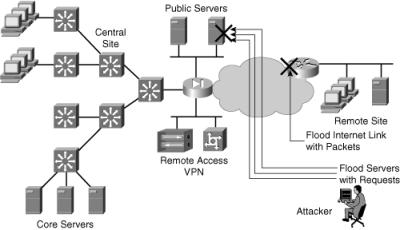
![]() Figure 10-1 depicts potential availability threats to network resources that an attacker might exploit. In this network, an attacker might do the following if adequate protection is not in place:
Figure 10-1 depicts potential availability threats to network resources that an attacker might exploit. In this network, an attacker might do the following if adequate protection is not in place:
-
 Flood the Internet connection with random traffic in an attempt to consume as much bandwidth as possible. This can deny service to legitimate users of that connection.
Flood the Internet connection with random traffic in an attempt to consume as much bandwidth as possible. This can deny service to legitimate users of that connection. -
 Flood a public server with an enormous number of connection requests, thereby rendering the server unresponsive to legitimate users.
Flood a public server with an enormous number of connection requests, thereby rendering the server unresponsive to legitimate users.
![]() Most DoS attacks rely on spoofing and flooding techniques. The impact of DoS attacks can be managed in the following ways:
Most DoS attacks rely on spoofing and flooding techniques. The impact of DoS attacks can be managed in the following ways:
-
 Use DHCP snooping to verify DHCP transactions and protect against rogue DHCP servers. DHCP snooping filters DHCP packets; it prevents a rogue DHCP server from handing out IP addresses on a network by blocking all replies to a DHCP request from an interface (port) unless that port is allowed to reply. DHCP snooping also builds and maintains a DHCP-snooping binding table, which includes MAC address and IP address information for DHCP clients on untrusted interfaces.
Use DHCP snooping to verify DHCP transactions and protect against rogue DHCP servers. DHCP snooping filters DHCP packets; it prevents a rogue DHCP server from handing out IP addresses on a network by blocking all replies to a DHCP request from an interface (port) unless that port is allowed to reply. DHCP snooping also builds and maintains a DHCP-snooping binding table, which includes MAC address and IP address information for DHCP clients on untrusted interfaces. -
 Use Dynamic Address Resolution Protocol (ARP) Inspection (DAI) to intercept all ARP requests and replies on untrusted interfaces (ports), and use the DHCP-snooping binding table information to verify that ARP packets have valid IP-to-MAC address bindings.
Use Dynamic Address Resolution Protocol (ARP) Inspection (DAI) to intercept all ARP requests and replies on untrusted interfaces (ports), and use the DHCP-snooping binding table information to verify that ARP packets have valid IP-to-MAC address bindings. -
 Implement unicast reverse path forwarding checks to verify if the source IP address is reachable so that packets from malformed or forged source IP addresses are prevented from entering the network.
Implement unicast reverse path forwarding checks to verify if the source IP address is reachable so that packets from malformed or forged source IP addresses are prevented from entering the network. -
 Implement access control lists (ACL) to filter traffic.
Implement access control lists (ACL) to filter traffic. -
 Rate-limit traffic such as incoming ARP and DHCP requests.
Rate-limit traffic such as incoming ARP and DHCP requests.
Risk: Integrity Violations and Confidentiality Breaches
![]() Key security risks are integrity violations and confidentiality breaches.
Key security risks are integrity violations and confidentiality breaches.
![]() An example of an integrity violation is when an attacker obtains permission to write to sensitive data and then changes or deletes it. The owner of the data might not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Because of the difficulty of detecting changes and the possible cascading consequences of late detection, many businesses treat integrity violations as the most serious threat to their business.
An example of an integrity violation is when an attacker obtains permission to write to sensitive data and then changes or deletes it. The owner of the data might not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Because of the difficulty of detecting changes and the possible cascading consequences of late detection, many businesses treat integrity violations as the most serious threat to their business.
![]() Confidentiality attacks can be extremely difficult to detect because the attacker can copy sensitive data without the owner’s knowledge and without leaving a trace.
Confidentiality attacks can be extremely difficult to detect because the attacker can copy sensitive data without the owner’s knowledge and without leaving a trace.
![]() The risks of both integrity violations and confidentiality breaches are usually managed by enforcing access control in various ways, including the following:
The risks of both integrity violations and confidentiality breaches are usually managed by enforcing access control in various ways, including the following:
-
 Limiting access to network resources using network access control, such as physical separation of networks, restrictive firewalls, and VLANs.
Limiting access to network resources using network access control, such as physical separation of networks, restrictive firewalls, and VLANs. -
 Limiting access to files and objects using operating system-based access controls, such as UNIX host security and Windows domain security.
Limiting access to files and objects using operating system-based access controls, such as UNIX host security and Windows domain security. -
 Limiting users’ access to data by using application-level controls, such as different user profiles for different roles.
Limiting users’ access to data by using application-level controls, such as different user profiles for different roles. -
 Using cryptography to protect data outside the application. Examples include encryption to provide confidentiality, and secure fingerprints or digital signatures to provide data authenticity and integrity. (These methods are described in the later “Secure Connectivity” section.)
Using cryptography to protect data outside the application. Examples include encryption to provide confidentiality, and secure fingerprints or digital signatures to provide data authenticity and integrity. (These methods are described in the later “Secure Connectivity” section.)
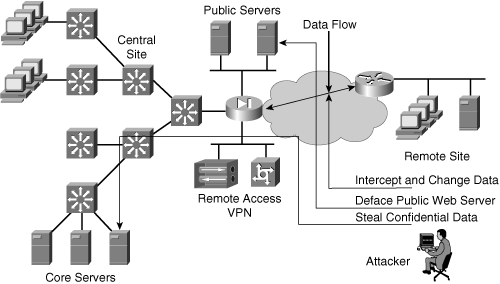
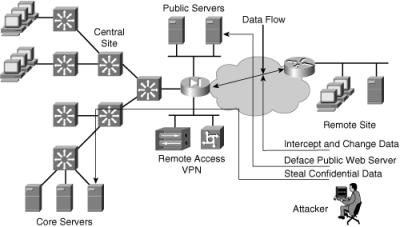
![]() Figure 10-2 illustrates potential confidentiality and integrity risks to network resources that an outside attacker might exploit. In this sample network, an attacker might do the following if adequate protection is not in place:
Figure 10-2 illustrates potential confidentiality and integrity risks to network resources that an outside attacker might exploit. In this sample network, an attacker might do the following if adequate protection is not in place:
-
 Access an internal server and copy confidential data (a confidentiality breach)
Access an internal server and copy confidential data (a confidentiality breach) -
 Deface (change) the corporate web page (an integrity breach)
Deface (change) the corporate web page (an integrity breach) -
 Intercept data sent over the Internet between a branch office and the central site, and change or read it in transit (a confidentiality or integrity breach)
Intercept data sent over the Internet between a branch office and the central site, and change or read it in transit (a confidentiality or integrity breach)
 Network Security Policy and Process
Network Security Policy and Process
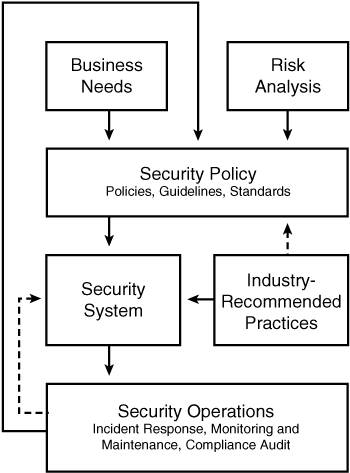
![]() Network security is an integral part of the system life cycle, as illustrated in Figure 10-3.
Network security is an integral part of the system life cycle, as illustrated in Figure 10-3.
![]() Network security is a continuous process, built around a security policy. Business needs (organizational requirements) and risk analysis are inputs to the development of a security policy. Regardless of the security implications, business needs must come first; if the business cannot function because of security constraints, the organization will have a major problem.
Network security is a continuous process, built around a security policy. Business needs (organizational requirements) and risk analysis are inputs to the development of a security policy. Regardless of the security implications, business needs must come first; if the business cannot function because of security constraints, the organization will have a major problem.
![]() The following are the key areas to consider when designing a secure network:
The following are the key areas to consider when designing a secure network:
-
 Business needs: What the organization wants to do with the network
Business needs: What the organization wants to do with the network -
 Risk analysis: The risk-versus-cost balance
Risk analysis: The risk-versus-cost balance -
 Security policy: The policies, standards, and guidelines that address business needs and risk
Security policy: The policies, standards, and guidelines that address business needs and risk -
 Industry-recommended practices: The reliable, well-understood, and recommended security practices in the industry
Industry-recommended practices: The reliable, well-understood, and recommended security practices in the industry -
 Security operations: The process for incident response, monitoring, maintenance, and compliance auditing of the system
Security operations: The process for incident response, monitoring, maintenance, and compliance auditing of the system
Security Policy
![]() A very good introduction to security policies and the components that should be in a security policy is available in RFC 2196, Site Security Handbook. This RFC is a guide to developing computer security policies and procedures for sites that have systems on the Internet. The purpose of the handbook is to provide practical guidance to administrators trying to secure their information and services. The subjects covered include policy content and formation, a broad range of technical system and network security topics, and security incident response. This RFC defines a security policy as “a formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide.”
A very good introduction to security policies and the components that should be in a security policy is available in RFC 2196, Site Security Handbook. This RFC is a guide to developing computer security policies and procedures for sites that have systems on the Internet. The purpose of the handbook is to provide practical guidance to administrators trying to secure their information and services. The subjects covered include policy content and formation, a broad range of technical system and network security topics, and security incident response. This RFC defines a security policy as “a formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide.”
The Need for a Security Policy
![]() The main purpose of a security policy is to inform users, staff, and managers of the requirements and their responsibilities for protecting technology and information assets. The policy specifies the mechanisms through which these requirements are met. A security policy sets the framework for the security implementation, including the following:
The main purpose of a security policy is to inform users, staff, and managers of the requirements and their responsibilities for protecting technology and information assets. The policy specifies the mechanisms through which these requirements are met. A security policy sets the framework for the security implementation, including the following:
-
 Defines organizational assets and how to use them
Defines organizational assets and how to use them -
 Defines and communicates roles
Defines and communicates roles -
 Helps determine the tools and procedures necessary to implement the policy
Helps determine the tools and procedures necessary to implement the policy -
 Defines how to identify and handle security incidents
Defines how to identify and handle security incidents
![]() Some questions you might need to ask when developing a security policy include the following:
Some questions you might need to ask when developing a security policy include the following:
-
 What data and assets will be covered by the security policy?
What data and assets will be covered by the security policy? -
 Under what conditions is communication allowed between networked hosts?
Under what conditions is communication allowed between networked hosts? -
 How will implementation of the policies be verified?
How will implementation of the policies be verified? -
 How will policy violations be detected?
How will policy violations be detected? -
 What is the impact of a policy violation?
What is the impact of a policy violation? -
 What actions are required if a policy is violated?
What actions are required if a policy is violated?
![]() Another purpose of a security policy is to provide a baseline of the current security situation from which to acquire, configure, and audit computer systems and networks for compliance with the policy. The policy defines behaviors that are allowed and those that are not allowed and informs users of their responsibilities and the ramifications of asset misuse. Attempting to use security tools in the absence of at least an implied security policy is meaningless.
Another purpose of a security policy is to provide a baseline of the current security situation from which to acquire, configure, and audit computer systems and networks for compliance with the policy. The policy defines behaviors that are allowed and those that are not allowed and informs users of their responsibilities and the ramifications of asset misuse. Attempting to use security tools in the absence of at least an implied security policy is meaningless.
![]() As part of developing a security policy, you should perform a risk assessment and cost-benefit analysis, including considering the latest attack techniques. Remember that the security system must be designed to accommodate the goals of the business, not hinder them.
As part of developing a security policy, you should perform a risk assessment and cost-benefit analysis, including considering the latest attack techniques. Remember that the security system must be designed to accommodate the goals of the business, not hinder them.
Risk Assessment and Management
![]() An organization defines an acceptable level of risk based on such factors as the following:
An organization defines an acceptable level of risk based on such factors as the following:
-
 The value of the organization’s data
The value of the organization’s data -
 The expectation of loss in the event of compromise
The expectation of loss in the event of compromise -
 The severity and probability of risks
The severity and probability of risks
![]() The weighting of these factors is called risk assessment, which is a continuously recurring procedure of knowing the following factors:
The weighting of these factors is called risk assessment, which is a continuously recurring procedure of knowing the following factors:
-
 What assets to protect
What assets to protect -
 The value of the assets
The value of the assets -
 The cost of expected loss (including financial loss) that would result from a security incident
The cost of expected loss (including financial loss) that would result from a security incident -
 The probability that an attack could be directed against the assets
The probability that an attack could be directed against the assets -
 The ability to control or minimize the risk through the security design and policy
The ability to control or minimize the risk through the security design and policy
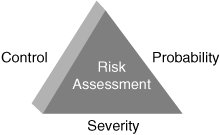
![]() Figure 10-4 summarizes these factors into three aspects of risk assessment: probability, control, and severity.
Figure 10-4 summarizes these factors into three aspects of risk assessment: probability, control, and severity.
![]() Risk assessment results in the development of a network security policy, which documents the level of risk and suggests the methods of managing the risk to an acceptable level. The network security policy describes risk management measures as they relate to potential threats. It does not usually consider security implementation details; rather, it provides a more general security philosophy that directs the implementation of security mechanisms.
Risk assessment results in the development of a network security policy, which documents the level of risk and suggests the methods of managing the risk to an acceptable level. The network security policy describes risk management measures as they relate to potential threats. It does not usually consider security implementation details; rather, it provides a more general security philosophy that directs the implementation of security mechanisms.
![]() Because the severity and probability of risks change daily, risk management and the consequent building of the security policy must be a continuous process. A good example is the use of cryptography to provide confidentiality through encryption. A company’s encryption algorithm and the length of the encryption key might have to be reconsidered if a relatively inexpensive and exceptionally fast code-cracking computer, which allows decryption of high-value secrets, becomes available. In this case, the organization must choose a stronger algorithm to provide protection against the new threat.
Because the severity and probability of risks change daily, risk management and the consequent building of the security policy must be a continuous process. A good example is the use of cryptography to provide confidentiality through encryption. A company’s encryption algorithm and the length of the encryption key might have to be reconsidered if a relatively inexpensive and exceptionally fast code-cracking computer, which allows decryption of high-value secrets, becomes available. In this case, the organization must choose a stronger algorithm to provide protection against the new threat.
![]() A security designer must evaluate the severity of a particular risk, including the damage a successful attack could cause. However, it is often difficult to associate a value with an asset. For example, consider the following:
A security designer must evaluate the severity of a particular risk, including the damage a successful attack could cause. However, it is often difficult to associate a value with an asset. For example, consider the following:
-
 A large hospital system’s medical database, in which disastrous consequences result if confidentiality is breached
A large hospital system’s medical database, in which disastrous consequences result if confidentiality is breached -
 A corporation’s public web page, which, if defaced (an integrity violation), can become a public-relations nightmare even though it might not result in any serious confidentiality breach Evaluating potential damage is also difficult, but it is possible to some degree for most scenarios. In the commercial world, it is common practice to build systems that have just enough security to bring down potential losses to the desired level. Alternatively, organizations that have higher security requirements, such as legislative mandates, might want to implement stronger measures than might appear to be economically necessary, to mitigate potential unforeseen risks.
A corporation’s public web page, which, if defaced (an integrity violation), can become a public-relations nightmare even though it might not result in any serious confidentiality breach Evaluating potential damage is also difficult, but it is possible to some degree for most scenarios. In the commercial world, it is common practice to build systems that have just enough security to bring down potential losses to the desired level. Alternatively, organizations that have higher security requirements, such as legislative mandates, might want to implement stronger measures than might appear to be economically necessary, to mitigate potential unforeseen risks.
Risk Index
![]() An organization can use a risk index to compare risks for potential threats. As illustrated in Table 10-1, a risk index is based on the following factors:
An organization can use a risk index to compare risks for potential threats. As illustrated in Table 10-1, a risk index is based on the following factors:
-
 The probability of risk (in other words, the likelihood that compromise will occur)
The probability of risk (in other words, the likelihood that compromise will occur) -
 The severity of loss in the event of compromise of an asset
The severity of loss in the event of compromise of an asset -
 The ability to control or manage the risk
The ability to control or manage the risk
|
|
|
|
|
|
|---|---|---|---|---|
|
| ||||
|
|
![]() All risks are identified in the first column. For each risk, each of the three factors is assigned a value between 1 (lowest) and 3 (highest). For example, for severity, a risk with high severity produces the greatest impact on user groups or particular environments and may even affect an entire site. Moderate-severity risks critically affect user environments or have some effect on an entire site (and mitigating the attack is a reasonably attainable scenario). Low-severity risks have a minor impact on user environments (and typically can be easily mitigated).
All risks are identified in the first column. For each risk, each of the three factors is assigned a value between 1 (lowest) and 3 (highest). For example, for severity, a risk with high severity produces the greatest impact on user groups or particular environments and may even affect an entire site. Moderate-severity risks critically affect user environments or have some effect on an entire site (and mitigating the attack is a reasonably attainable scenario). Low-severity risks have a minor impact on user environments (and typically can be easily mitigated).
![]() The risk index is calculated by dividing the product of the probability and severity factors by the control factor, resulting in this formula:
The risk index is calculated by dividing the product of the probability and severity factors by the control factor, resulting in this formula:
|
|
| Note |
|
![]() Therefore, higher risk indices indicate risks that will have a more severe impact if they occur, that are more likely to occur, and that are less easy to control or manage. Risks with a higher risk index therefore require constant monitoring.
Therefore, higher risk indices indicate risks that will have a more severe impact if they occur, that are more likely to occur, and that are less easy to control or manage. Risks with a higher risk index therefore require constant monitoring.
![]() Stakeholders and subject matter experts should be involved in building the risk index matrix. The security policy should identify and outline a plan of activities to manage or control each risk and the actions to take if a security incident occurs. Table 10-2 shows sample risk index calculations.
Stakeholders and subject matter experts should be involved in building the risk index matrix. The security policy should identify and outline a plan of activities to manage or control each risk and the actions to take if a security incident occurs. Table 10-2 shows sample risk index calculations.
|
|
|
|
|
|
|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
Documenting the Security Policy
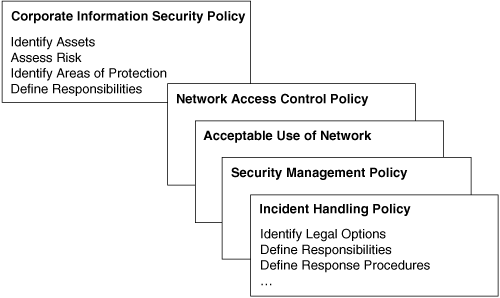
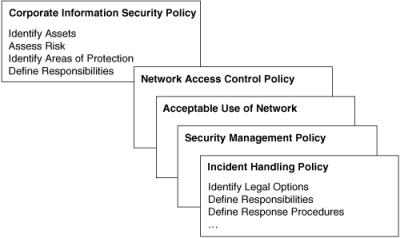
![]() Figure 10-5 illustrates a sample security policy and how it can be divided into multiple documents that are applicable to the network segments.
Figure 10-5 illustrates a sample security policy and how it can be divided into multiple documents that are applicable to the network segments.
![]() A general document describes the overall risk-management policy, identifies the corporation’s assets, and identifies where protection must be applied. It also documents how risk management responsibility is distributed throughout the enterprise. Other documents, such as the following, might address more specific areas of risk management:
A general document describes the overall risk-management policy, identifies the corporation’s assets, and identifies where protection must be applied. It also documents how risk management responsibility is distributed throughout the enterprise. Other documents, such as the following, might address more specific areas of risk management:
-
 A general Network Access Control Policy documents how data is categorized (such as confidential, internal, and top-secret) and what general access control principles are implemented in the networks.
A general Network Access Control Policy documents how data is categorized (such as confidential, internal, and top-secret) and what general access control principles are implemented in the networks. -
 An Acceptable Use of Network document is usually written in easy-to-understand language and distributed to end users. This document informs users about their risk-management roles and responsibilities and should be as explicit as possible to avoid ambiguity or misunderstanding.
An Acceptable Use of Network document is usually written in easy-to-understand language and distributed to end users. This document informs users about their risk-management roles and responsibilities and should be as explicit as possible to avoid ambiguity or misunderstanding. -
 A Security Management Policy defines how to perform secure computer infrastructure management.
A Security Management Policy defines how to perform secure computer infrastructure management. -
 An Incident Handling Policy documents, the procedures to be used to ensure the reliable and acceptable handling of emergency situations.
An Incident Handling Policy documents, the procedures to be used to ensure the reliable and acceptable handling of emergency situations.
![]() Numerous other areas can be covered in separate documents, depending on the organization’s requirements. The security policy should have the acceptance and support of all levels of employees in the organization. Therefore, representatives of all key stakeholders and affected management should be involved in creating and revising the security policy.
Numerous other areas can be covered in separate documents, depending on the organization’s requirements. The security policy should have the acceptance and support of all levels of employees in the organization. Therefore, representatives of all key stakeholders and affected management should be involved in creating and revising the security policy.
Network Security Process
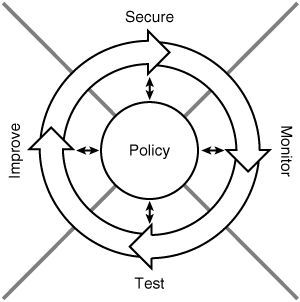
![]() A security policy should be considered a living document, continuously updated as technology and organizational requirements change. As shown in Figure 10-6, a process consisting of the following four steps helps maintain the security policy:
A security policy should be considered a living document, continuously updated as technology and organizational requirements change. As shown in Figure 10-6, a process consisting of the following four steps helps maintain the security policy:
-
 Secure: A security solution is implemented to stop or prevent unauthorized access or activities and to protect information and assets. Securing the network might include implementing filtering and stateful inspection, identity authentication, encryption, virtual private networks (VPN), vulnerability patching, and other countermeasures to implement the security policy.
Secure: A security solution is implemented to stop or prevent unauthorized access or activities and to protect information and assets. Securing the network might include implementing filtering and stateful inspection, identity authentication, encryption, virtual private networks (VPN), vulnerability patching, and other countermeasures to implement the security policy. -
 Monitor: Monitoring the security solution is required to detect violations of the security policy; monitoring might include system auditing, real-time intrusion detection and response, and content-based detection and response.
Monitor: Monitoring the security solution is required to detect violations of the security policy; monitoring might include system auditing, real-time intrusion detection and response, and content-based detection and response. -
 Test: The effectiveness of the security policy and the implemented security solution is validated by regular system auditing and assessment, and vulnerability scanning. Any applications installed and patches applied to software must be verified against the security policy.
Test: The effectiveness of the security policy and the implemented security solution is validated by regular system auditing and assessment, and vulnerability scanning. Any applications installed and patches applied to software must be verified against the security policy. -
 Improve: The information gathered from monitoring and testing the security solution, including event and data analysis and reporting, is used to make improvements to the security implementation. The security policy might have to be adjusted as new security vulnerabilities and risks are identified, and as network security intelligence improves.
Improve: The information gathered from monitoring and testing the security solution, including event and data analysis and reporting, is used to make improvements to the security implementation. The security policy might have to be adjusted as new security vulnerabilities and risks are identified, and as network security intelligence improves.
![]() Security is becoming more and more an embedded part of the network. Security services such as firewalls, IPSs, Secure Sockets Layer (SSL), and IP security (IPsec) might now reside within the network infrastructure. SSL enables a secure path between a web browser and router resources. Recall from Chapter 5, “Designing Remote Connectivity,” that IPsec is both a tunnel encapsulation protocol and a security protocol.
Security is becoming more and more an embedded part of the network. Security services such as firewalls, IPSs, Secure Sockets Layer (SSL), and IP security (IPsec) might now reside within the network infrastructure. SSL enables a secure path between a web browser and router resources. Recall from Chapter 5, “Designing Remote Connectivity,” that IPsec is both a tunnel encapsulation protocol and a security protocol.
![]() However, an integrated security and network design requires coordination not only between the network and security teams, but also with the rest of the IT organization—including, for example, the security policy and desktop operations teams.
However, an integrated security and network design requires coordination not only between the network and security teams, but also with the rest of the IT organization—including, for example, the security policy and desktop operations teams.

0 comments
Post a Comment