 Troubleshooting VLANs
Troubleshooting VLANs
![]() Switched Ethernet has been the dominant LAN technology for more than a decade. This is why a good understanding of the processes involved in Layer 2 switching is essential to any engineer who is involved in network troubleshooting. VLAN-based switched infrastructures are at the core of every campus network and being able to diagnose and resolve Layer 2 switching problems in these environments is a fundamental skill that any network engineer should have. This section first reviews the Layer 2 switching process and the associated switch data structures. Next, you will learn how to gather information from these data structures using Cisco IOS Software commands. Finally, you will learn how to interpret and analyze the gathered information in order to verify the proper operation of the Layer 2 switching process or to pinpoint and resolve problems.
Switched Ethernet has been the dominant LAN technology for more than a decade. This is why a good understanding of the processes involved in Layer 2 switching is essential to any engineer who is involved in network troubleshooting. VLAN-based switched infrastructures are at the core of every campus network and being able to diagnose and resolve Layer 2 switching problems in these environments is a fundamental skill that any network engineer should have. This section first reviews the Layer 2 switching process and the associated switch data structures. Next, you will learn how to gather information from these data structures using Cisco IOS Software commands. Finally, you will learn how to interpret and analyze the gathered information in order to verify the proper operation of the Layer 2 switching process or to pinpoint and resolve problems.
 LAN Switch Operation
LAN Switch Operation
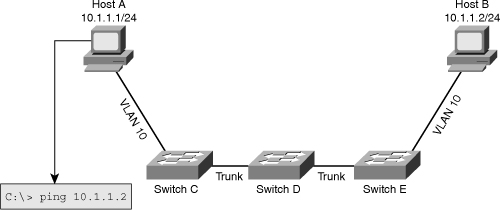
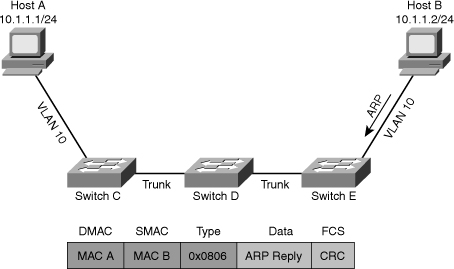
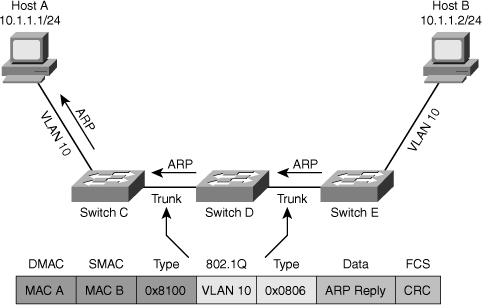
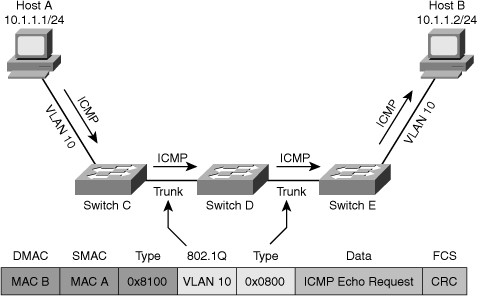
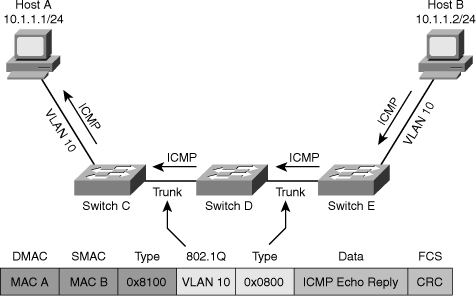
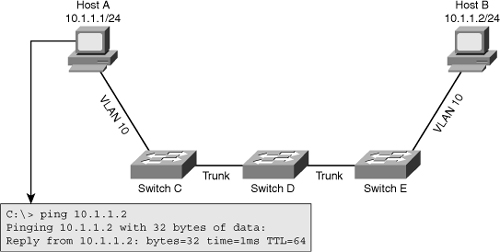
![]() As a network engineer, you must have an in-depth knowledge of the core processes performed by hosts and network devices. When things break down and devices do not function as they should, a good understanding of processes helps you determine where exactly a process breaks down. In addition, you will be able to determine which parts of the network are functioning correctly and which parts are not functioning correctly. This section examines the processes that take place when two IP hosts communicate over a switched LAN. The focus here is at the IP and lower layers; this means that the host application is in working condition and matters such as name to IP address resolution are functional. To limit the scope of the discussion to the processes involved in Layer 2 switching, assume that the two hosts reside on a common subnet (VLAN). Because the actual application being used is irrelevant to this discussion, imagine that the user of Host A would like to test connectivity to Host B using ping as per the network shown in Figure 4-1.
As a network engineer, you must have an in-depth knowledge of the core processes performed by hosts and network devices. When things break down and devices do not function as they should, a good understanding of processes helps you determine where exactly a process breaks down. In addition, you will be able to determine which parts of the network are functioning correctly and which parts are not functioning correctly. This section examines the processes that take place when two IP hosts communicate over a switched LAN. The focus here is at the IP and lower layers; this means that the host application is in working condition and matters such as name to IP address resolution are functional. To limit the scope of the discussion to the processes involved in Layer 2 switching, assume that the two hosts reside on a common subnet (VLAN). Because the actual application being used is irrelevant to this discussion, imagine that the user of Host A would like to test connectivity to Host B using ping as per the network shown in Figure 4-1.
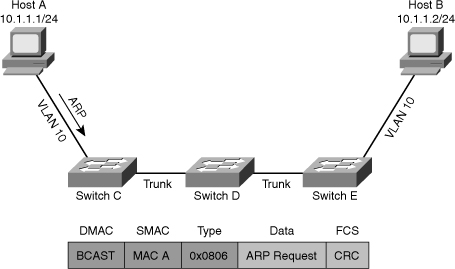
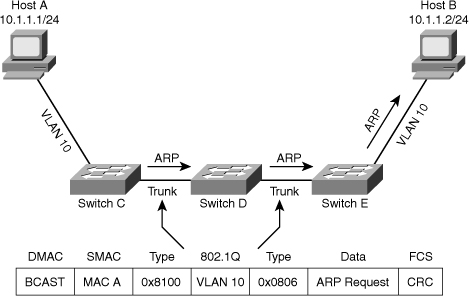
![]() This process can be broken down into the following steps:
This process can be broken down into the following steps:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Although this process might seem trivial, listing the steps clearly shows that even for the simplest communication, an elaborate chain of events take place. If at any point this chain is broken due to faulty cabling, failing devices, or misconfiguration, the communication will fail. Therefore, you must leverage your knowledge of these processes to diagnose and solve problems in a switched environment. Possible issues that could cause the communication to fail include the following:
Although this process might seem trivial, listing the steps clearly shows that even for the simplest communication, an elaborate chain of events take place. If at any point this chain is broken due to faulty cabling, failing devices, or misconfiguration, the communication will fail. Therefore, you must leverage your knowledge of these processes to diagnose and solve problems in a switched environment. Possible issues that could cause the communication to fail include the following:
-
 Bad, missing, or miswired cables
Bad, missing, or miswired cables -
 Bad ports
Bad ports -
 Power failure
Power failure -
 Device problems
Device problems -
 Software bugs
Software bugs -
 Performance problems
Performance problems -
 Misconfiguration
Misconfiguration -
 Missing or wrong VLANs
Missing or wrong VLANs -
 Misconfigured VLAN Trunking Protocol (VTP) settings
Misconfigured VLAN Trunking Protocol (VTP) settings -
 Wrong VLAN setting on access ports
Wrong VLAN setting on access ports -
 Missing or misconfigured trunks
Missing or misconfigured trunks -
 Native VLAN mismatch
Native VLAN mismatch -
 VLANs not allowed on trunk
VLANs not allowed on trunk
| Note |
|
![]() To keep the focus specifically on LAN switching, this chapter does not discuss any generic physical problems. However, you will learn how specific commands available on the Cisco Catalyst LAN switches could supplement your troubleshooting toolkit to help troubleshoot data link and physical layer problems.
To keep the focus specifically on LAN switching, this chapter does not discuss any generic physical problems. However, you will learn how specific commands available on the Cisco Catalyst LAN switches could supplement your troubleshooting toolkit to help troubleshoot data link and physical layer problems.
 Verifying Layer 2 Forwarding
Verifying Layer 2 Forwarding
![]() A common method to troubleshoot Layer 2 switching problems is to follow the path of the frames through the switches. Following the actual frames themselves in real time takes a lot of time and effort because it requires packet captures at various points in the network; that is neither practical nor feasible. Instead of trying to follow the frame in real time, you must follow the trail of the frame. The objective is to confirm that frames have passed through the switches and to verify how each switch made its forwarding decisions. If you find a point where the trail suddenly stops or if you find that the information that the switch uses to forward frames does not match our expectations, you will gain important clues. These clues will help in reducing the scope of the possible problem areas, and it helps in formulating a hypothesis on the cause of the problem; it may even outright point at the cause of the problem. Consequently, a troubleshooter needs to learn how to follow the trail of the frame, and know which data structure proves whether frames have passed through the switch.
A common method to troubleshoot Layer 2 switching problems is to follow the path of the frames through the switches. Following the actual frames themselves in real time takes a lot of time and effort because it requires packet captures at various points in the network; that is neither practical nor feasible. Instead of trying to follow the frame in real time, you must follow the trail of the frame. The objective is to confirm that frames have passed through the switches and to verify how each switch made its forwarding decisions. If you find a point where the trail suddenly stops or if you find that the information that the switch uses to forward frames does not match our expectations, you will gain important clues. These clues will help in reducing the scope of the possible problem areas, and it helps in formulating a hypothesis on the cause of the problem; it may even outright point at the cause of the problem. Consequently, a troubleshooter needs to learn how to follow the trail of the frame, and know which data structure proves whether frames have passed through the switch.
![]() One key data structure that you can consult is the switch’s MAC address table. In this table, the switch registers the source MAC address of each frame that it receives, and records the port and VLAN on which the frame was received. When you see an entry for a particular MAC address in this table, it proves that at some point, usually up to five minutes ago, this switch received frames from that source. This does not necessarily tell you anything about a particular frame or how long ago the last frame was received. Therefore, it might be a good practice to clear the MAC entry from the table by using the clear mac-address-table dynamic command and verify that the MAC address is learned again when you reinitiate the connection. Second, the MAC address table enables you to verify that frames are received on the port and VLAN where they are expected. If the output does not match your expectations and assumptions, use it as a clue in forming a hypothesis about the cause of the problem. Because there are many possible findings and conclusions that you might draw from, the following is a short list of some common findings and plausible conclusions:
One key data structure that you can consult is the switch’s MAC address table. In this table, the switch registers the source MAC address of each frame that it receives, and records the port and VLAN on which the frame was received. When you see an entry for a particular MAC address in this table, it proves that at some point, usually up to five minutes ago, this switch received frames from that source. This does not necessarily tell you anything about a particular frame or how long ago the last frame was received. Therefore, it might be a good practice to clear the MAC entry from the table by using the clear mac-address-table dynamic command and verify that the MAC address is learned again when you reinitiate the connection. Second, the MAC address table enables you to verify that frames are received on the port and VLAN where they are expected. If the output does not match your expectations and assumptions, use it as a clue in forming a hypothesis about the cause of the problem. Because there are many possible findings and conclusions that you might draw from, the following is a short list of some common findings and plausible conclusions:
-
 Frames are not received on the correct VLAN: This could point to VLAN or trunk misconfiguration as the cause of the problem.
Frames are not received on the correct VLAN: This could point to VLAN or trunk misconfiguration as the cause of the problem. -
 Frames are received on a different port than you expected: This could point to a physical problem, spanning-tree issues, or duplicate MAC addresses.
Frames are received on a different port than you expected: This could point to a physical problem, spanning-tree issues, or duplicate MAC addresses. -
 The MAC address is not registered in the MAC address table: This tells you that the problem is most likely upstream from this switch. You should retrace your steps and investigate between the last point where you know that frames were received and this switch.
The MAC address is not registered in the MAC address table: This tells you that the problem is most likely upstream from this switch. You should retrace your steps and investigate between the last point where you know that frames were received and this switch.
![]() The next step is to use your knowledge of the forwarding process combined with the information you can gather using the switch’s diagnostic commands output to determine what the next step in the process must be. Again, you should validate the facts that you gather about the switch’s forwarding behavior against your expectations and assumptions. After you have confirmed that the behavior of the switch matches your expectations, you have successfully reduced the possible scope of the problem—You have confirmed that everything works as expected up to this point.
The next step is to use your knowledge of the forwarding process combined with the information you can gather using the switch’s diagnostic commands output to determine what the next step in the process must be. Again, you should validate the facts that you gather about the switch’s forwarding behavior against your expectations and assumptions. After you have confirmed that the behavior of the switch matches your expectations, you have successfully reduced the possible scope of the problem—You have confirmed that everything works as expected up to this point.
![]() You must definitely have a good grasp of the switch diagnostic commands and use them effectively. You will use these commands to gather the information from the switch that is needed to validate your assumptions. Some commonly used diagnostic commands that help you obtain information about the Layer 2 switching process, VLANs, and trunks are as follows:
You must definitely have a good grasp of the switch diagnostic commands and use them effectively. You will use these commands to gather the information from the switch that is needed to validate your assumptions. Some commonly used diagnostic commands that help you obtain information about the Layer 2 switching process, VLANs, and trunks are as follows:
-
 show mac-address-table: This is the main command to verify Layer 2 forwarding. It shows you the MAC addresses learned by the switch and their corresponding port and VLAN associations. This command gives you an indication if frames sourced by a particular host have succeeded in reaching this switch. It will also help you verify whether these frames were received on the correct inbound interface. Note that if the MAC address table becomes full, no more learning can happen. During troubleshooting, always check to see whether the table is full.
show mac-address-table: This is the main command to verify Layer 2 forwarding. It shows you the MAC addresses learned by the switch and their corresponding port and VLAN associations. This command gives you an indication if frames sourced by a particular host have succeeded in reaching this switch. It will also help you verify whether these frames were received on the correct inbound interface. Note that if the MAC address table becomes full, no more learning can happen. During troubleshooting, always check to see whether the table is full. -
 show vlan: This command enables you to verify VLAN existence and port-to-VLAN associations. This command lists all VLANS that were created on the switch (either manually or through VTP). It will also list the ports that are associated to each of the VLANs. Note that trunks are not listed because they do not belong to any particular VLAN.
show vlan: This command enables you to verify VLAN existence and port-to-VLAN associations. This command lists all VLANS that were created on the switch (either manually or through VTP). It will also list the ports that are associated to each of the VLANs. Note that trunks are not listed because they do not belong to any particular VLAN. -
 show interfaces trunk: This command displays all interfaces that are configured as trunks. It will also display on each trunk which VLANs are allowed and what the native VLAN is.
show interfaces trunk: This command displays all interfaces that are configured as trunks. It will also display on each trunk which VLANs are allowed and what the native VLAN is. -
 show interfaces switchport: This command combines some of the information found in show vlan and show interfaces trunk commands. It is most useful if you are not looking for a switch-wide overview of trunk or VLAN related information, but if you would rather have a quick summary of all VLAN-related information for a single interface.
show interfaces switchport: This command combines some of the information found in show vlan and show interfaces trunk commands. It is most useful if you are not looking for a switch-wide overview of trunk or VLAN related information, but if you would rather have a quick summary of all VLAN-related information for a single interface. -
 show platform forward interface: You can use many parameters with this command and find out how the hardware would forward a frame that matches the specified parameters, on the specified interface.
show platform forward interface: You can use many parameters with this command and find out how the hardware would forward a frame that matches the specified parameters, on the specified interface. -
 traceroute mac: You specify a source and destination MAC address with this command to see the list of switch hops that a frame from that source MAC address to that destination MAC address passes through. Use this command to discover the Layer 2 path frames take from the specified source MAC address to the specified destination MAC address. This command requires that Cisco Discovery Protocol (CDP) be enabled on all the switches in the network (or at least within the path).
traceroute mac: You specify a source and destination MAC address with this command to see the list of switch hops that a frame from that source MAC address to that destination MAC address passes through. Use this command to discover the Layer 2 path frames take from the specified source MAC address to the specified destination MAC address. This command requires that Cisco Discovery Protocol (CDP) be enabled on all the switches in the network (or at least within the path).
![]() Based on the information they provide, the commands listed can be categorized. To display the MAC address table, use the show mac-address-table command. To display VLAN database and port-to-VLAN mapping, use the show vlan command. To see the trunk port settings and port-to-VLAN associations, use the show interfaces switchport and show interfaces trunk commands. To directly verify frame forwarding, use the show platform forward and the traceroute mac commands.
Based on the information they provide, the commands listed can be categorized. To display the MAC address table, use the show mac-address-table command. To display VLAN database and port-to-VLAN mapping, use the show vlan command. To see the trunk port settings and port-to-VLAN associations, use the show interfaces switchport and show interfaces trunk commands. To directly verify frame forwarding, use the show platform forward and the traceroute mac commands.

0 comments
Post a Comment