Overview
![]() In this chapter, you will learn how to develop a comprehensive network security policy to counter threats against information security. You will also learn about possible threats and how to describe and implement the process of developing a security policy. In this chapter, you will learn about the following topics:
In this chapter, you will learn how to develop a comprehensive network security policy to counter threats against information security. You will also learn about possible threats and how to describe and implement the process of developing a security policy. In this chapter, you will learn about the following topics:
-
 Core principles that are part of a secure network
Core principles that are part of a secure network -
 Attack methods and how to plan a defense in depth
Attack methods and how to plan a defense in depth -
 Principles behind operations security, security testing, secure life cycle, and business continuity planning
Principles behind operations security, security testing, secure life cycle, and business continuity planning -
 Cisco Self-Defending Network strategy
Cisco Self-Defending Network strategy -
 Firewall technologies
Firewall technologies -
 Static packet filters using ACLs
Static packet filters using ACLs
![]() The open nature of the Internet makes it increasingly important for growing businesses to pay attention to the security of their networks. As companies move more of their business functions to the public network, they need to take precautions to ensure that the data is not compromised or that the data does not end up in front of the wrong people.
The open nature of the Internet makes it increasingly important for growing businesses to pay attention to the security of their networks. As companies move more of their business functions to the public network, they need to take precautions to ensure that the data is not compromised or that the data does not end up in front of the wrong people.
![]() Unauthorized network access by an outside hacker or disgruntled employee can cause damage or destruction to proprietary data, negatively affect company productivity, and impede the capability to compete. Unauthorized network access can also harm relationships with customers and business partners who might question the capability of a company to protect its confidential information.
Unauthorized network access by an outside hacker or disgruntled employee can cause damage or destruction to proprietary data, negatively affect company productivity, and impede the capability to compete. Unauthorized network access can also harm relationships with customers and business partners who might question the capability of a company to protect its confidential information.
Examining Network Security Fundamentals
![]() It is increasingly difficult to establish and maintain a secure network computing environment. The challenge is more difficult because of increased availability requirements and growing regulatory requirements. This section explains the breadth of the challenge to establish and maintain a secure network environment.
It is increasingly difficult to establish and maintain a secure network computing environment. The challenge is more difficult because of increased availability requirements and growing regulatory requirements. This section explains the breadth of the challenge to establish and maintain a secure network environment.
 The Need for Network Security
The Need for Network Security
![]() The easiest way to protect a network from an outside attack is to close it off completely from the outside world. A closed network provides connectivity only to trusted known parties and sites; a closed network does not allow a connection to public networks.
The easiest way to protect a network from an outside attack is to close it off completely from the outside world. A closed network provides connectivity only to trusted known parties and sites; a closed network does not allow a connection to public networks.
![]() Because there is no outside connectivity, you can consider networks designed in this way to be safe from outside attacks. However, internal threats still exist. The Computer Security Institute (CSI) in San Francisco, California, estimates that 60 percent to 80 percent of network misuse comes from inside the enterprise.
Because there is no outside connectivity, you can consider networks designed in this way to be safe from outside attacks. However, internal threats still exist. The Computer Security Institute (CSI) in San Francisco, California, estimates that 60 percent to 80 percent of network misuse comes from inside the enterprise.
![]() The overall security challenge is to find a balance between two important needs:
The overall security challenge is to find a balance between two important needs:
-
 The need to open networks to support evolving business requirements and freedom of information initiatives
The need to open networks to support evolving business requirements and freedom of information initiatives -
 The growing need to protect private, personal, and strategic business information
The growing need to protect private, personal, and strategic business information
![]() The Internet has created expectations for a company to build stronger relationships with customers, suppliers, partners, and employees. E-business challenges companies to become more agile and competitive. The benefit of this challenge is that new applications for e-commerce, supply chain management, customer care, workforce optimization, and e-learning have been created; applications that streamline and improve processes decrease turnaround times, lower costs, and increase user satisfaction.
The Internet has created expectations for a company to build stronger relationships with customers, suppliers, partners, and employees. E-business challenges companies to become more agile and competitive. The benefit of this challenge is that new applications for e-commerce, supply chain management, customer care, workforce optimization, and e-learning have been created; applications that streamline and improve processes decrease turnaround times, lower costs, and increase user satisfaction.
![]() E-business requires mission-critical networks that accommodate ever-increasing constituencies and demands greater capacity and performance. These networks also need to handle voice, video, and data traffic as networks converge into multiservice environments.
E-business requires mission-critical networks that accommodate ever-increasing constituencies and demands greater capacity and performance. These networks also need to handle voice, video, and data traffic as networks converge into multiservice environments.
Internal Threats
![]() Internal threats constitute the most serious of threats. Insiders, whether they are employees or contractors, have inside knowledge and inside access. They usually do not have to resort to technical means to achieve their security breaches. It is, in fact, unusual for inside attackers to engage in port scans or ping sweeps, because they already know where the resources exist in the network. Also, because inside attackers already have access to the network, they do not usually need to try to crack passwords or other things of this nature.
Internal threats constitute the most serious of threats. Insiders, whether they are employees or contractors, have inside knowledge and inside access. They usually do not have to resort to technical means to achieve their security breaches. It is, in fact, unusual for inside attackers to engage in port scans or ping sweeps, because they already know where the resources exist in the network. Also, because inside attackers already have access to the network, they do not usually need to try to crack passwords or other things of this nature.
![]() Technical defenses are usually ineffective against insider attacks. They are especially ineffective when administrators, or developers, or both have poor practices and do not harden the systems and applications according to the best practices of the vendor.
Technical defenses are usually ineffective against insider attacks. They are especially ineffective when administrators, or developers, or both have poor practices and do not harden the systems and applications according to the best practices of the vendor.
External Threats
![]() External threats tend to rely on technical means to achieve their goals of breaching your security. For this reason, this book focuses mainly on external threats, because your technical defenses are most effective against them. Firewalls, routers with access control lists (ACL), intrusion prevention systems (IPS), and other technical controls can effectively reduce the number of external threats to which an organization is vulnerable.
External threats tend to rely on technical means to achieve their goals of breaching your security. For this reason, this book focuses mainly on external threats, because your technical defenses are most effective against them. Firewalls, routers with access control lists (ACL), intrusion prevention systems (IPS), and other technical controls can effectively reduce the number of external threats to which an organization is vulnerable.
![]() Figure 1-1 illustrates how the increasing sophistication of hacking tools and the decreasing skill that is needed to use these tools have combined to pose increasing threats to open networks. With the development of large open networks, security threats in the past 20 years have increased significantly. Hackers have discovered more network vulnerabilities, and hacking tools have become easier to use. You can now download applications that require little or no hacking knowledge to implement. If troubleshooting applications that you use for maintaining and optimizing networks fall into the wrong hands, they can be used maliciously and pose severe threats.
Figure 1-1 illustrates how the increasing sophistication of hacking tools and the decreasing skill that is needed to use these tools have combined to pose increasing threats to open networks. With the development of large open networks, security threats in the past 20 years have increased significantly. Hackers have discovered more network vulnerabilities, and hacking tools have become easier to use. You can now download applications that require little or no hacking knowledge to implement. If troubleshooting applications that you use for maintaining and optimizing networks fall into the wrong hands, they can be used maliciously and pose severe threats.
![]() Figure 1-2 shows the number of security events that occurred from 2004 to 2008 as reported in the 2008 CSI/FBI Computer Crime and Security Survey. The numbers of security incidents cited in Figure 1-2 add up to a serious situation. Although it might appear as though the instances are decreasing, keep in mind that security measures continue to improve, and the damage done by the attackers can actually cost more nowadays with even fewer attacks.
Figure 1-2 shows the number of security events that occurred from 2004 to 2008 as reported in the 2008 CSI/FBI Computer Crime and Security Survey. The numbers of security incidents cited in Figure 1-2 add up to a serious situation. Although it might appear as though the instances are decreasing, keep in mind that security measures continue to improve, and the damage done by the attackers can actually cost more nowadays with even fewer attacks.
| Note |
|
![]() For 2008, the U.K.’s BERR reports that the total cost of security incidents is down overall by 35 percent. A large portion of this significant drop is attributable to the sharp decline in virus infections. The number of companies reporting to BERR a virus infection has gone to a level not seen since 2000.
For 2008, the U.K.’s BERR reports that the total cost of security incidents is down overall by 35 percent. A large portion of this significant drop is attributable to the sharp decline in virus infections. The number of companies reporting to BERR a virus infection has gone to a level not seen since 2000.
-
 Almost 18 percent of those respondents who suffered one or more kinds of security incident also said they had suffered a “targeted attack,” defined as a malware attack that was aimed exclusively at their organization or at organizations within a small subset of the general population.
Almost 18 percent of those respondents who suffered one or more kinds of security incident also said they had suffered a “targeted attack,” defined as a malware attack that was aimed exclusively at their organization or at organizations within a small subset of the general population. -
 Financial fraud overtook virus attacks as the source of the greatest financial losses. Virus losses, which had been the leading cause of loss for seven straight years, fell to second place.
Financial fraud overtook virus attacks as the source of the greatest financial losses. Virus losses, which had been the leading cause of loss for seven straight years, fell to second place.Note  For 2008, the BERR report lists virus infection in fourth place as the leading cause of loss.
For 2008, the BERR report lists virus infection in fourth place as the leading cause of loss. -
 If the separate categories that are concerned with the loss of customer and proprietary data are grouped together, that combined category would be the second-worst cause of financial loss. Another significant cause of loss was system penetration by outsiders.
If the separate categories that are concerned with the loss of customer and proprietary data are grouped together, that combined category would be the second-worst cause of financial loss. Another significant cause of loss was system penetration by outsiders. -
 Insider abuse of network access or email, such as trafficking in pornography or pirated software, edged out virus incidents as the most prevalent security problem, with 59 percent of the respondents reporting insider abuse, and 52 percent of respondents reporting virus incidents.
Insider abuse of network access or email, such as trafficking in pornography or pirated software, edged out virus incidents as the most prevalent security problem, with 59 percent of the respondents reporting insider abuse, and 52 percent of respondents reporting virus incidents. -
 When the companies were asked generally whether they had suffered a security incident, 46 percent of respondents said yes, which is down from 53 percent in 2006 and 56 percent in 2005.
When the companies were asked generally whether they had suffered a security incident, 46 percent of respondents said yes, which is down from 53 percent in 2006 and 56 percent in 2005.Note  According to the 2008 BERR report, 45 percent of small companies reported having been the victim of a security incident, compared to 72 percent for large companies and 96 percent for very large enterprises. The mean number of incidents reported by small business was 100 (with a median of 6); the large companies reported having been the victim of 200 incidents (with a median of 15), and the very large enterprises recorded more than 1300 incidents (with a median over 400).
According to the 2008 BERR report, 45 percent of small companies reported having been the victim of a security incident, compared to 72 percent for large companies and 96 percent for very large enterprises. The mean number of incidents reported by small business was 100 (with a median of 6); the large companies reported having been the victim of 200 incidents (with a median of 15), and the very large enterprises recorded more than 1300 incidents (with a median over 400). -
 The percentage of organizations reporting computer intrusions to law enforcement has continued to increase after reversing a multiyear decline over the past two years, standing now at 29 percent as compared to 25 percent in the 2006 report.
The percentage of organizations reporting computer intrusions to law enforcement has continued to increase after reversing a multiyear decline over the past two years, standing now at 29 percent as compared to 25 percent in the 2006 report.
![]() Research reveals that hackers are increasingly motivated by profit, as shown in Figure 1-3. In these instances, hackers are not looking for attention, so their exploits are harder to find. Few signatures exist or will ever be written to capture these “custom” threats. To be successful in defending your environments, you must employ a new model to catch threats across the infrastructure.
Research reveals that hackers are increasingly motivated by profit, as shown in Figure 1-3. In these instances, hackers are not looking for attention, so their exploits are harder to find. Few signatures exist or will ever be written to capture these “custom” threats. To be successful in defending your environments, you must employ a new model to catch threats across the infrastructure.
![]() Application attacks, not lower-layer platform exploits, are the target of 75 percent of all attacks today. Most companies have many, perhaps hundreds, of different web applications, and their administrative interfaces are scattered throughout the IT environment. Current employees, ex-employees, contractors, integrators, or third-party outsourced developers, most of whom have never had any formal security training, might have written the code. In addition, web developers are constantly updating this code to respond to business needs, not security requirements.
Application attacks, not lower-layer platform exploits, are the target of 75 percent of all attacks today. Most companies have many, perhaps hundreds, of different web applications, and their administrative interfaces are scattered throughout the IT environment. Current employees, ex-employees, contractors, integrators, or third-party outsourced developers, most of whom have never had any formal security training, might have written the code. In addition, web developers are constantly updating this code to respond to business needs, not security requirements.
![]() There are no signatures or patches for your own customized application code. As a result, traditional firewalls, intrusion detection system (IDS) and IPS products, patch management tools, and remediation tools do nothing for custom applications. Even the best vulnerability scanners miss the majority of application security flaws in custom code because they use a database of static signatures to scan for known flaws.
There are no signatures or patches for your own customized application code. As a result, traditional firewalls, intrusion detection system (IDS) and IPS products, patch management tools, and remediation tools do nothing for custom applications. Even the best vulnerability scanners miss the majority of application security flaws in custom code because they use a database of static signatures to scan for known flaws.
![]() This problem is compounded by the fact that the applications themselves are dynamic and complex, so new holes are almost certain to open up the moment you fix the old ones. The result is that unless you write and maintain perfect code, hackers can exploit vulnerabilities in your customized software to gain direct access to the critical data of your company.
This problem is compounded by the fact that the applications themselves are dynamic and complex, so new holes are almost certain to open up the moment you fix the old ones. The result is that unless you write and maintain perfect code, hackers can exploit vulnerabilities in your customized software to gain direct access to the critical data of your company.
| Note |
|
![]() In addition to protecting the data for company reasons, many companies must comply with regulatory mandates, with serious consequences if they cannot document their attempts to secure critical data, whether that data is customer credit card numbers, health records, or other sensitive, private information with which the company is entrusted.
In addition to protecting the data for company reasons, many companies must comply with regulatory mandates, with serious consequences if they cannot document their attempts to secure critical data, whether that data is customer credit card numbers, health records, or other sensitive, private information with which the company is entrusted.
| Note |
|
 Network Security Objectives
Network Security Objectives
![]() As networks become increasingly interconnected and data flows more freely, enabling networks to provide security services becomes very important. In the commercial world, connectivity is no longer optional, and the possible risks of connectivity do not outweigh its benefits. Therefore, security services must provide adequate protection to conduct business in a relatively open environment.
As networks become increasingly interconnected and data flows more freely, enabling networks to provide security services becomes very important. In the commercial world, connectivity is no longer optional, and the possible risks of connectivity do not outweigh its benefits. Therefore, security services must provide adequate protection to conduct business in a relatively open environment.
Basic Security Assumptions
![]() Several new assumptions have to be made about computer networks because of their evolution over the years:
Several new assumptions have to be made about computer networks because of their evolution over the years:
-
 Modern networks are very large, very interconnected, and run both ubiquitous protocols, such as IP, and proprietary protocols. Therefore, they are often open to access, and a potential attacker can often easily attach to, or remotely access, such networks. Widespread IP internetworking increases the probability that more attacks will be carried out over large, heavily interconnected networks, such as the Internet.
Modern networks are very large, very interconnected, and run both ubiquitous protocols, such as IP, and proprietary protocols. Therefore, they are often open to access, and a potential attacker can often easily attach to, or remotely access, such networks. Widespread IP internetworking increases the probability that more attacks will be carried out over large, heavily interconnected networks, such as the Internet. -
 Computer systems and applications that are attached to these networks are becoming increasingly complex. In terms of security, it becomes more difficult to analyze, secure, and properly test the security of the computer systems and applications, even more so when virtualization is involved. When these systems and their applications are attached to large networks, the risk to computing dramatically increases.
Computer systems and applications that are attached to these networks are becoming increasingly complex. In terms of security, it becomes more difficult to analyze, secure, and properly test the security of the computer systems and applications, even more so when virtualization is involved. When these systems and their applications are attached to large networks, the risk to computing dramatically increases.
Basic Security Requirements
![]() To provide adequate protection of network resources, the procedures and technologies that you deploy need to guarantee three things, sometimes referred to as the CIA triad:
To provide adequate protection of network resources, the procedures and technologies that you deploy need to guarantee three things, sometimes referred to as the CIA triad:
-
 Confidentiality: Providing confidentiality of data guarantees that only authorized users can view sensitive information.
Confidentiality: Providing confidentiality of data guarantees that only authorized users can view sensitive information. -
 Integrity: Providing integrity of data guarantees that only authorized subjects can change sensitive information; this might also guarantee the authenticity of data.
Integrity: Providing integrity of data guarantees that only authorized subjects can change sensitive information; this might also guarantee the authenticity of data. -
 System and data availability: System and data availability provides uninterrupted access by authorized users to important computing resources and data.
System and data availability: System and data availability provides uninterrupted access by authorized users to important computing resources and data.
![]() When designing network security, a designer must be aware of the following:
When designing network security, a designer must be aware of the following:
-
 The threats (possible attacks) that could compromise security
The threats (possible attacks) that could compromise security -
 The associated risks of the threats (that is, how relevant those threats are for a particular system)
The associated risks of the threats (that is, how relevant those threats are for a particular system) -
 The cost to implement the proper security countermeasures for a threat
The cost to implement the proper security countermeasures for a threat -
 A cost versus benefit analysis to determine whether it is worthwhile to implement the security countermeasures
A cost versus benefit analysis to determine whether it is worthwhile to implement the security countermeasures
Confidentiality
![]() You usually manage the risk of confidentiality breaches by enforcing access control in various ways. The following are examples of this type of enforcement:
You usually manage the risk of confidentiality breaches by enforcing access control in various ways. The following are examples of this type of enforcement:
-
 Limiting access to network resources using network access control, such as physical separation of networks, restrictive firewalls, and VLANs
Limiting access to network resources using network access control, such as physical separation of networks, restrictive firewalls, and VLANs -
 Limiting access to files and objects using operating system-based access controls, such as UNIX host security and Windows domain security
Limiting access to files and objects using operating system-based access controls, such as UNIX host security and Windows domain security -
 Limiting user access to data by application level controls, such as different user profiles for different roles
Limiting user access to data by application level controls, such as different user profiles for different roles -
 Limiting the readability of information should there be a breach, through encryption
Limiting the readability of information should there be a breach, through encryption
![]() Confidentiality breaches can occur when an attacker attempts to obtain access to read-sensitive data. It can be extremely difficult to detect these attacks because the attacker can copy sensitive data without the knowledge of the owner and without leaving a trace.
Confidentiality breaches can occur when an attacker attempts to obtain access to read-sensitive data. It can be extremely difficult to detect these attacks because the attacker can copy sensitive data without the knowledge of the owner and without leaving a trace.
![]() A confidentiality breach can occur simply because of incorrect file protections. For instance, a sensitive file could mistakenly be given global read-access permissions. It is difficult to track an unauthorized copying or examination of the file without some type of audit mechanism running that logs every file operation. However, if users had no reason to suspect unwanted access, they would probably never examine the audit file.
A confidentiality breach can occur simply because of incorrect file protections. For instance, a sensitive file could mistakenly be given global read-access permissions. It is difficult to track an unauthorized copying or examination of the file without some type of audit mechanism running that logs every file operation. However, if users had no reason to suspect unwanted access, they would probably never examine the audit file.
Integrity
![]() The basic meaning of data integrity is data that has not been subjected to unauthorized change. Other definitions of integrity add freshness of information, or authenticity of source, or both to integrity (protection against change).
The basic meaning of data integrity is data that has not been subjected to unauthorized change. Other definitions of integrity add freshness of information, or authenticity of source, or both to integrity (protection against change).
![]() The following are some examples of where data integrity would be helpful:
The following are some examples of where data integrity would be helpful:
-
 Changing grades in a school database
Changing grades in a school database -
 Modifying figures that are displayed online for the financials of a company
Modifying figures that are displayed online for the financials of a company -
 Defacing a web server
Defacing a web server
![]() Integrity violations can occur when the attacker attempts to change sensitive data without proper authorization. For example, the attacker obtains permission to write to sensitive data and changes it or deletes it. The owner may not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Many businesses treat integrity violations as the most serious threat to their business, because of the difficulty in detecting changes and the possible cascading consequences of late detection.
Integrity violations can occur when the attacker attempts to change sensitive data without proper authorization. For example, the attacker obtains permission to write to sensitive data and changes it or deletes it. The owner may not detect such a change until it is too late, perhaps when the change has already resulted in tangible loss. Many businesses treat integrity violations as the most serious threat to their business, because of the difficulty in detecting changes and the possible cascading consequences of late detection.
Availability
![]() In general, availability refers to providing uninterrupted access to computing resources and data even during accidental or deliberate network or computer disruptions. The availability service is increasingly recognized as one of the most important security services and possibly the most difficult to provide.
In general, availability refers to providing uninterrupted access to computing resources and data even during accidental or deliberate network or computer disruptions. The availability service is increasingly recognized as one of the most important security services and possibly the most difficult to provide.
![]() Businesses can experience loss of profit and productivity when customers, suppliers, and employees cannot access critical sites or software applications. Several factors can affect the availability of resources, such as bandwidth bottlenecks, improperly configured networks, and host or client overload, any of which can be due to legitimate use, illegitimate use, or both.
Businesses can experience loss of profit and productivity when customers, suppliers, and employees cannot access critical sites or software applications. Several factors can affect the availability of resources, such as bandwidth bottlenecks, improperly configured networks, and host or client overload, any of which can be due to legitimate use, illegitimate use, or both.
![]() Denial-of-service (DoS) attacks attempt to compromise the availability of a network, host, or application. They are considered a major risk because they can easily interrupt a business process and cause significant loss in productivity and possible revenue. These attacks are relatively simple to conduct, even by an unskilled attacker.
Denial-of-service (DoS) attacks attempt to compromise the availability of a network, host, or application. They are considered a major risk because they can easily interrupt a business process and cause significant loss in productivity and possible revenue. These attacks are relatively simple to conduct, even by an unskilled attacker.
![]() For example, a Montreal teenager was sentenced in 2001 for his admitted guilt in paralyzing the websites of companies such as Yahoo!, Amazon.com, eBay, E*Trade Financial, and Dell. His DoS attacks flooded the networks of the companies with fake information requests that caused networks to shut down, which resulted in lost business. This attack also reportedly caused stock prices to drop.
For example, a Montreal teenager was sentenced in 2001 for his admitted guilt in paralyzing the websites of companies such as Yahoo!, Amazon.com, eBay, E*Trade Financial, and Dell. His DoS attacks flooded the networks of the companies with fake information requests that caused networks to shut down, which resulted in lost business. This attack also reportedly caused stock prices to drop.
![]() DoS attacks are usually the consequence of two things:
DoS attacks are usually the consequence of two things:
-
 A host or application fails to handle an unexpected condition, such as maliciously formatted input data, an unexpected interaction of system components, or simple resource exhaustion.
A host or application fails to handle an unexpected condition, such as maliciously formatted input data, an unexpected interaction of system components, or simple resource exhaustion. -
 A network, host, or application is unable to handle an enormous quantity of data, causing the system to crash or brings it to a halt. It is difficult to defend against such an attack because it is difficult to distinguish legitimate data from attacker data.
A network, host, or application is unable to handle an enormous quantity of data, causing the system to crash or brings it to a halt. It is difficult to defend against such an attack because it is difficult to distinguish legitimate data from attacker data.
![]() The following are two examples of DoS attacks:
The following are two examples of DoS attacks:
-
 An attacker sends a poisonous packet (an improperly formatted packet or a packet which the receiving device improperly processes) to a device, which causes it to crash or halt upon receipt. This attack can cause all communications to and from the device to be disrupted.
An attacker sends a poisonous packet (an improperly formatted packet or a packet which the receiving device improperly processes) to a device, which causes it to crash or halt upon receipt. This attack can cause all communications to and from the device to be disrupted. -
 An attacker sends a continuous stream of packets, which overwhelms the available bandwidth of some network links; in most cases, it is impossible to differentiate between an attacker and legitimate traffic, and it is impossible to trace an attack quickly back to its source. In general, success correlates to bandwidth resources, and whoever has more bandwidth, prevails. If attackers compromise many systems in the Internet core, they might be able to take advantage of virtually unlimited bandwidth to unleash packet storms at their targets. This type of attack has already happened on the Internet and is called a distributed DoS (DDoS) attack.
An attacker sends a continuous stream of packets, which overwhelms the available bandwidth of some network links; in most cases, it is impossible to differentiate between an attacker and legitimate traffic, and it is impossible to trace an attack quickly back to its source. In general, success correlates to bandwidth resources, and whoever has more bandwidth, prevails. If attackers compromise many systems in the Internet core, they might be able to take advantage of virtually unlimited bandwidth to unleash packet storms at their targets. This type of attack has already happened on the Internet and is called a distributed DoS (DDoS) attack.
 Data Classification
Data Classification
![]() To optimally allocate resources and secure assets, it is essential that some form of data classification exists. By identifying which data has the most worth, administrators can make the greatest effort to secure that data. Without classification, data custodians find it almost impossible to adequately secure the data, and IT management finds it equally difficult to optimally allocate resources.
To optimally allocate resources and secure assets, it is essential that some form of data classification exists. By identifying which data has the most worth, administrators can make the greatest effort to secure that data. Without classification, data custodians find it almost impossible to adequately secure the data, and IT management finds it equally difficult to optimally allocate resources.
![]() Sometimes information classification is a regulatory requirement, and there can be liability issues that relate to the proper care of data that are factors. By classifying data correctly, data custodians can apply the appropriate confidentiality, integrity, and availability controls to adequately secure the data, based on regulatory, liability, and ethical requirements. When an organization takes classification seriously, it illustrates to everyone that the company is taking information security seriously.
Sometimes information classification is a regulatory requirement, and there can be liability issues that relate to the proper care of data that are factors. By classifying data correctly, data custodians can apply the appropriate confidentiality, integrity, and availability controls to adequately secure the data, based on regulatory, liability, and ethical requirements. When an organization takes classification seriously, it illustrates to everyone that the company is taking information security seriously.
![]() The methods and labels applied to data differ all around the world, but some patterns do emerge. The following is a common way to classify data that many government organizations, including the military, use:
The methods and labels applied to data differ all around the world, but some patterns do emerge. The following is a common way to classify data that many government organizations, including the military, use:
-
 Unclassified: Data that has little or no confidentiality, integrity, or availability requirements and therefore little effort is made to secure it.
Unclassified: Data that has little or no confidentiality, integrity, or availability requirements and therefore little effort is made to secure it. -
 Sensitive But Unclassified (SBU): Data that could prove embarrassing if revealed, but no great security breach will occur.
Sensitive But Unclassified (SBU): Data that could prove embarrassing if revealed, but no great security breach will occur. -
 Confidential: Data that must comply with confidentiality requirements. This is the lowest level of classified data in this scheme.
Confidential: Data that must comply with confidentiality requirements. This is the lowest level of classified data in this scheme. -
 Secret: Data for which you take significant effort to keep secure. The number of individuals who have access to this data is usually considerably fewer than the number of people who are authorized to access confidential data.
Secret: Data for which you take significant effort to keep secure. The number of individuals who have access to this data is usually considerably fewer than the number of people who are authorized to access confidential data. -
 Top secret: Data for which you make great effort and sometimes incur considerable cost to guarantee its secrecy. Usually a small number of individuals have access to top-secret data, on condition that there is a need to know.
Top secret: Data for which you make great effort and sometimes incur considerable cost to guarantee its secrecy. Usually a small number of individuals have access to top-secret data, on condition that there is a need to know.
![]() It is important to point out that there is no actual standard for private-sector classification. Furthermore, different countries tend to have different approaches and labels. Nevertheless, it can be instructive to examine a common, private sector classification scheme:
It is important to point out that there is no actual standard for private-sector classification. Furthermore, different countries tend to have different approaches and labels. Nevertheless, it can be instructive to examine a common, private sector classification scheme:
-
 Public: Companies often display public data in marketing literature or on publicly accessible websites.
Public: Companies often display public data in marketing literature or on publicly accessible websites. -
 Sensitive: Data in this classification is similar to the SBU classification in the government model. Some embarrassment might occur if this data is revealed, but no serious security breach is involved.
Sensitive: Data in this classification is similar to the SBU classification in the government model. Some embarrassment might occur if this data is revealed, but no serious security breach is involved. -
 Private: Private data is important to an organization. You make an effort to maintain the secrecy and accuracy of this data.
Private: Private data is important to an organization. You make an effort to maintain the secrecy and accuracy of this data. -
 Confidential: Companies make the greatest effort to secure confidential data. Trade secrets and employee personnel files are examples of what a company would commonly classify as confidential.
Confidential: Companies make the greatest effort to secure confidential data. Trade secrets and employee personnel files are examples of what a company would commonly classify as confidential.
![]() Regardless of the classification labeling used, what is certain is that as the security classification of a document increases, the amount of staff that should have access to this document should decrease, as illustrated in Figure 1-4.
Regardless of the classification labeling used, what is certain is that as the security classification of a document increases, the amount of staff that should have access to this document should decrease, as illustrated in Figure 1-4.
![]() Many factors go into the decision of how to classify certain data. These factors include the following:
Many factors go into the decision of how to classify certain data. These factors include the following:
-
 Value: Value is the number one criterion. Not all data has the same value. The home address and medical information of an employee is considerably more sensitive (valuable) than the name of the chief executive officer (CEO) and the main telephone number of the company.
Value: Value is the number one criterion. Not all data has the same value. The home address and medical information of an employee is considerably more sensitive (valuable) than the name of the chief executive officer (CEO) and the main telephone number of the company. -
 Age: For many types of data, its importance changes with time. For example, a general will go to great lengths to restrict access to military secrets. But after the war is over, the information is gradually less and less useful and eventually is declassified.
Age: For many types of data, its importance changes with time. For example, a general will go to great lengths to restrict access to military secrets. But after the war is over, the information is gradually less and less useful and eventually is declassified. -
 Useful life: Often data is valuable for only a set window of time, and after that window has expired there is no need to keep it classified. An example of this type of data is confidential information about the products of a company. The useful life of the trade secrets of the products typically expires when the company no longer sells the product.
Useful life: Often data is valuable for only a set window of time, and after that window has expired there is no need to keep it classified. An example of this type of data is confidential information about the products of a company. The useful life of the trade secrets of the products typically expires when the company no longer sells the product. -
 Personal association: Data of this type usually involves something of a personal nature. Much of the government data regarding employees is of this nature. Steps are usually taken to protect this data until the person is deceased.
Personal association: Data of this type usually involves something of a personal nature. Much of the government data regarding employees is of this nature. Steps are usually taken to protect this data until the person is deceased.
| Note |
|
![]() When an organization decides on a classification scheme, the next typical step is to decide how to classify the data, who is responsible for securing the data, and the level of security to be applied to the data. Generally, the information classification procedure is as follows:
When an organization decides on a classification scheme, the next typical step is to decide how to classify the data, who is responsible for securing the data, and the level of security to be applied to the data. Generally, the information classification procedure is as follows:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]() Sometimes exigent circumstances, such as court orders, supersede a classification policy. In this situation, you make information available to officers of the court and attorneys and their staffs that would otherwise not be available for public view. To do otherwise would be to disobey a lawful order.
Sometimes exigent circumstances, such as court orders, supersede a classification policy. In this situation, you make information available to officers of the court and attorneys and their staffs that would otherwise not be available for public view. To do otherwise would be to disobey a lawful order.
![]() Certain government contracts require contractors to reveal confidential data before the contract is awarded. For example, if the defense department of a country awards a contract to an IT outsourcing company, they will likely insist on having a list of all individuals who will be working in their facility, and a lot of personal information about each of these individuals, to run background checks. In this instance, normal classification rules are set aside.
Certain government contracts require contractors to reveal confidential data before the contract is awarded. For example, if the defense department of a country awards a contract to an IT outsourcing company, they will likely insist on having a list of all individuals who will be working in their facility, and a lot of personal information about each of these individuals, to run background checks. In this instance, normal classification rules are set aside.
![]() It is also the prerogative of senior management to declassify, reclassify, or even release classified data if it is required.
It is also the prerogative of senior management to declassify, reclassify, or even release classified data if it is required.
| Note |
|
![]() For a classification system to work, there must be different roles that are fulfilled. The most common of these roles are as follows:
For a classification system to work, there must be different roles that are fulfilled. The most common of these roles are as follows:
-
 Owner: The owner is the person who is ultimately responsible for the information, usually senior-level management who is in charge of a business unit. The owner classifies the data and usually selects custodians of the data and directs their actions. It is important that the owner periodically review the classified data because the owner is ultimately responsible for the data.
Owner: The owner is the person who is ultimately responsible for the information, usually senior-level management who is in charge of a business unit. The owner classifies the data and usually selects custodians of the data and directs their actions. It is important that the owner periodically review the classified data because the owner is ultimately responsible for the data. -
 Custodian: The custodian is usually a member of the IT staff who has the day-to-day responsibility for data maintenance. Because the owner of the data is not required to have technical knowledge, the owner decides the security controls but the custodian marks the data to enforce these security controls. To maintain the availability of the data, the custodian regularly backs up the data and ensures that the backup media is secure. Custodians also periodically review the security settings of the data as part of their maintenance responsibilities.
Custodian: The custodian is usually a member of the IT staff who has the day-to-day responsibility for data maintenance. Because the owner of the data is not required to have technical knowledge, the owner decides the security controls but the custodian marks the data to enforce these security controls. To maintain the availability of the data, the custodian regularly backs up the data and ensures that the backup media is secure. Custodians also periodically review the security settings of the data as part of their maintenance responsibilities. -
 User: Users bear no responsibility for the classification of data or even the maintenance of the classified data. However, users do bear responsibility for using the data in accordance with established operational procedures so that they maintain the security of the data while it is in their possession.
User: Users bear no responsibility for the classification of data or even the maintenance of the classified data. However, users do bear responsibility for using the data in accordance with established operational procedures so that they maintain the security of the data while it is in their possession.
 Security Controls
Security Controls
![]() Once the owner classifies the data, the custodian is responsible for securing the data. If the custodian has only technical controls available to secure the data, the custodian is severely limited. Most inside attackers do not rely on technical means to accomplish their attacks. Therefore, if the only defense custodians have is a technical one, it is likely that they will fail at maintaining the security of the data.
Once the owner classifies the data, the custodian is responsible for securing the data. If the custodian has only technical controls available to secure the data, the custodian is severely limited. Most inside attackers do not rely on technical means to accomplish their attacks. Therefore, if the only defense custodians have is a technical one, it is likely that they will fail at maintaining the security of the data.
![]() In a comprehensive security program, organizations rely on a variety of controls to accomplish defense in depth. These controls fall into one of three categories:
In a comprehensive security program, organizations rely on a variety of controls to accomplish defense in depth. These controls fall into one of three categories:
-
 Administrative: Controls that are largely policies and procedures
Administrative: Controls that are largely policies and procedures -
 Technical: Controls that involve electronics, hardware, software, and so on
Technical: Controls that involve electronics, hardware, software, and so on
| Note |
|
Administrative Controls
![]() Administrative controls are largely policy and procedure driven. You will find many of the administrative controls that help with information security in the enterprise in the human resources department. Some of these controls are as follows:
Administrative controls are largely policy and procedure driven. You will find many of the administrative controls that help with information security in the enterprise in the human resources department. Some of these controls are as follows:
-
 Security-awareness training
Security-awareness training -
 Security policies and standards
Security policies and standards -
 Change controls and configuration controls
Change controls and configuration controls -
 Security audits and tests
Security audits and tests -
 Good hiring practices
Good hiring practices -
 Background checks of contractors and employees
Background checks of contractors and employees
![]() For example, if an organization has strict hiring practices that require drug testing and background checks for all employees, the organization will likely hire fewer individuals of questionable character. With fewer people of questionable character working for the company, it is likely that there will be fewer problems with internal security issues. These controls do not single-handedly secure an enterprise, but they are an important part of an information security program.
For example, if an organization has strict hiring practices that require drug testing and background checks for all employees, the organization will likely hire fewer individuals of questionable character. With fewer people of questionable character working for the company, it is likely that there will be fewer problems with internal security issues. These controls do not single-handedly secure an enterprise, but they are an important part of an information security program.
Technical Controls
![]() Members of IT staffs tend to think of information security solely in terms of technical controls. Although technical controls are extremely important to a good information security program, they are not the only part. The following are examples of technical controls:
Members of IT staffs tend to think of information security solely in terms of technical controls. Although technical controls are extremely important to a good information security program, they are not the only part. The following are examples of technical controls:
-
 Firewalls
Firewalls -
 IPSs
IPSs -
 Virtual private network (VPN) concentrators and clients
Virtual private network (VPN) concentrators and clients -
 TACACS+ and RADIUS servers
TACACS+ and RADIUS servers -
 One-time password (OTP) solutions
One-time password (OTP) solutions -
 Smart cards
Smart cards -
 Network Admission Control (NAC) systems
Network Admission Control (NAC) systems -
 Routers with ACLs
Routers with ACLs
| Note |
|
Physical Controls
![]() While trying to secure an environment with good technical and administrative controls, it is also necessary that you lock the doors in the data center. This is an example of a physical control. Other examples of physical controls include the following:
While trying to secure an environment with good technical and administrative controls, it is also necessary that you lock the doors in the data center. This is an example of a physical control. Other examples of physical controls include the following:
-
 Intruder detection systems
Intruder detection systems -
 Security guards
Security guards -
 Locks
Locks -
 Safes
Safes -
 Racks
Racks -
 Uninterruptible power supplies (UPS)
Uninterruptible power supplies (UPS) -
 Fire-suppression systems
Fire-suppression systems -
 Positive air-flow systems
Positive air-flow systems
![]() When security professionals examine physical security requirements, protecting life safety (protecting human life) should be their number one concern. Good planning is needed to balance life safety concerns against security. For example, permanently barring a door to prevent unauthorized physical access might prevent individuals from escaping in the event of a fire.
When security professionals examine physical security requirements, protecting life safety (protecting human life) should be their number one concern. Good planning is needed to balance life safety concerns against security. For example, permanently barring a door to prevent unauthorized physical access might prevent individuals from escaping in the event of a fire.
![]() Controls are also categorized by the type of control they are:
Controls are also categorized by the type of control they are:
-
 Preventive: The control prevents access.
Preventive: The control prevents access. -
 Deterrent: The control deters access.
Deterrent: The control deters access. -
 Detective: The control detects access.
Detective: The control detects access.
![]() All three categories of controls can be any one of the three types of controls; for example, a preventive control can be administrative, physical, or technical.
All three categories of controls can be any one of the three types of controls; for example, a preventive control can be administrative, physical, or technical.
| Note |
|
![]() Preventive controls exist to prevent compromise. This statement is true whether the control is administrative, technical, or physical. The ultimate purpose for these controls is the prevention of security breaches.
Preventive controls exist to prevent compromise. This statement is true whether the control is administrative, technical, or physical. The ultimate purpose for these controls is the prevention of security breaches.
![]() However, a good security design also prepares for failure, recognizing that prevention will not always work. Therefore, detective controls are also part of a comprehensive security program because they enable you to detect a security breach and to determine how the network was breached. With this knowledge, you should be able to better secure the data the next time.
However, a good security design also prepares for failure, recognizing that prevention will not always work. Therefore, detective controls are also part of a comprehensive security program because they enable you to detect a security breach and to determine how the network was breached. With this knowledge, you should be able to better secure the data the next time.
![]() With effective detective controls in place, the incident response can use the detective controls to figure out what went wrong, allowing you to immediately make changes to policies to eliminate a repeat of that same breach. Without detective controls, it is extremely difficult to determine what you need to change.
With effective detective controls in place, the incident response can use the detective controls to figure out what went wrong, allowing you to immediately make changes to policies to eliminate a repeat of that same breach. Without detective controls, it is extremely difficult to determine what you need to change.
![]() Deterrent controls are designed to scare away a certain percentage of adversaries to reduce the number of incidents. Cameras in bank lobbies are a good example of a deterrent control. The cameras most likely deter at least some potential bank robbers. The cameras also act as a detective control.
Deterrent controls are designed to scare away a certain percentage of adversaries to reduce the number of incidents. Cameras in bank lobbies are a good example of a deterrent control. The cameras most likely deter at least some potential bank robbers. The cameras also act as a detective control.
| Note |
|
| Note |
|
 Response to a Security Breach
Response to a Security Breach
![]() To successfully prosecute an individual who breaches your security, it is necessary to establish three things in most countries:
To successfully prosecute an individual who breaches your security, it is necessary to establish three things in most countries:
-
 Motive: Motive is concerned with why an individual performed the illegal act. As you investigate a computer crime, it is important to start with individuals who might have been motivated to commit the crime.
Motive: Motive is concerned with why an individual performed the illegal act. As you investigate a computer crime, it is important to start with individuals who might have been motivated to commit the crime. -
 Opportunity: Having identified a list of suspects, the next thing to consider is whether they had the opportunity to commit the crime. For example, if you can establish that three of the suspects were all participating in a wedding at the time of the security breach, they may have been motivated, but they did not have the opportunity. They were probably busy doing something else.
Opportunity: Having identified a list of suspects, the next thing to consider is whether they had the opportunity to commit the crime. For example, if you can establish that three of the suspects were all participating in a wedding at the time of the security breach, they may have been motivated, but they did not have the opportunity. They were probably busy doing something else. -
 Means: The means is an important thing to prove as well. Do not accuse someone who does not have the technical knowledge to accomplish the deed. Means is the ability to perform the crime. However, keep in mind that hacking tools have become easy for even a novice to use.
Means: The means is an important thing to prove as well. Do not accuse someone who does not have the technical knowledge to accomplish the deed. Means is the ability to perform the crime. However, keep in mind that hacking tools have become easy for even a novice to use.
![]() If you do not establish these three things, it is difficult to prove that the perpetrator is guilty of the offense. When you can establish motive, opportunity, and means, you have probably identified the guilty party.
If you do not establish these three things, it is difficult to prove that the perpetrator is guilty of the offense. When you can establish motive, opportunity, and means, you have probably identified the guilty party.
| Note |
|
![]() When working with computer data as part of a forensics case, you must maintain the integrity of the data if you will rely on the data in a court of law. It is difficult to maintain the integrity of the data in the virtual world of computers where it is trivial to change time stamps or any item of data. The flipping of a single bit can sometimes be all that is required to falsely establish an alibi. In Figure 1-5, by flipping a single bit, you can change the time stamp from October 2, 2008 to October 3, 2008 (where the bit pattern for 2 is 00000010 and the bit pattern for 3 is 00000011). Therefore, strict procedures are required to guarantee the integrity of forensics data recovered as part of an investigation, such as keeping a proper chain of custody of the evidence.
When working with computer data as part of a forensics case, you must maintain the integrity of the data if you will rely on the data in a court of law. It is difficult to maintain the integrity of the data in the virtual world of computers where it is trivial to change time stamps or any item of data. The flipping of a single bit can sometimes be all that is required to falsely establish an alibi. In Figure 1-5, by flipping a single bit, you can change the time stamp from October 2, 2008 to October 3, 2008 (where the bit pattern for 2 is 00000010 and the bit pattern for 3 is 00000011). Therefore, strict procedures are required to guarantee the integrity of forensics data recovered as part of an investigation, such as keeping a proper chain of custody of the evidence.
![]() Data collection is a volatile thing in the virtual world of computers. For this reason, a common procedure in response to security breaches is the immediate isolation of the infected system. Dumping the memory to disk is required because the system flushes the memory every time a device is powered off. Multiple copies of the hard drive are usually made after the device is powered down to establish master copies. These master copies are usually locked up in a safe, and investigators use working copies for both the prosecution and the defense. You can answer any charges of tampering with data by comparing working copies to the master copy that has been secured and untouched since the beginning of the investigation.
Data collection is a volatile thing in the virtual world of computers. For this reason, a common procedure in response to security breaches is the immediate isolation of the infected system. Dumping the memory to disk is required because the system flushes the memory every time a device is powered off. Multiple copies of the hard drive are usually made after the device is powered down to establish master copies. These master copies are usually locked up in a safe, and investigators use working copies for both the prosecution and the defense. You can answer any charges of tampering with data by comparing working copies to the master copy that has been secured and untouched since the beginning of the investigation.
 Laws and Ethics
Laws and Ethics
![]() This section describes key laws and codes of ethics that are binding on information systems security (infosec) professionals.
This section describes key laws and codes of ethics that are binding on information systems security (infosec) professionals.
![]() For many businesses today, one of the biggest considerations for setting security policies is compliance with the law. For that reason, it is important for INFOSEC professionals to be at least conversant in the basics of law.
For many businesses today, one of the biggest considerations for setting security policies is compliance with the law. For that reason, it is important for INFOSEC professionals to be at least conversant in the basics of law.
![]() In most countries, there are three types of laws:
In most countries, there are three types of laws:
-
 Criminal: Concerned with crimes, and its penalties usually involve the risk of fines or imprisonment, or both. If fines are paid, they are usually to the court and are used to defray court costs.
Criminal: Concerned with crimes, and its penalties usually involve the risk of fines or imprisonment, or both. If fines are paid, they are usually to the court and are used to defray court costs. -
 Civil (also called tort): Focuses on correcting wrongs that are not crimes. An example of a civil law case is if one company sues another company for infringing on a patent. The penalty in civil law is usually monetary, although there can also be performance requirements such as ceasing to infringe on the patent. If money is awarded, it is given to the party who won the lawsuit. Imprisonment is not possible in civil law.
Civil (also called tort): Focuses on correcting wrongs that are not crimes. An example of a civil law case is if one company sues another company for infringing on a patent. The penalty in civil law is usually monetary, although there can also be performance requirements such as ceasing to infringe on the patent. If money is awarded, it is given to the party who won the lawsuit. Imprisonment is not possible in civil law. -
 Administrative: Involves government agencies enforcing regulations. For example, a company may owe its employees vacation pay. An administrative court could force the company to pay and would probably also levy a fine that is payable to the agency. Therefore, in administrative law cases, monetary awards are often split between the government agency and the victim whose wrongs have been righted.
Administrative: Involves government agencies enforcing regulations. For example, a company may owe its employees vacation pay. An administrative court could force the company to pay and would probably also levy a fine that is payable to the agency. Therefore, in administrative law cases, monetary awards are often split between the government agency and the victim whose wrongs have been righted.
![]() Ethics involves a standard that is higher than the law. It is a set of moral principles that adherents follow to be considered ethical. These ethics are often formalized in codes appropriately entitled “codes of ethics” by the professions formalizing the code.
Ethics involves a standard that is higher than the law. It is a set of moral principles that adherents follow to be considered ethical. These ethics are often formalized in codes appropriately entitled “codes of ethics” by the professions formalizing the code.
![]() The information security profession has a number of codes that have been formalized:
The information security profession has a number of codes that have been formalized:
-
 International Information Systems Security Certification Consortium, Inc (ISC)2 code of ethics
International Information Systems Security Certification Consortium, Inc (ISC)2 code of ethics -
 Computer Ethics Institute
Computer Ethics Institute -
 Internet Activities Board (IAB)
Internet Activities Board (IAB) -
 Generally Accepted System Security Principles (GASSP)
Generally Accepted System Security Principles (GASSP)
ISC2 Code of Ethics
![]() The following is a brief overview of the ISC2 code of ethics.
The following is a brief overview of the ISC2 code of ethics.
-
 Code of ethics preamble
Code of ethics preamble  Safety of the commonwealth, duty to our principals, and to each other requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior. Therefore, strict adherence to this Code is a condition of certification.
Safety of the commonwealth, duty to our principals, and to each other requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior. Therefore, strict adherence to this Code is a condition of certification. -
 Code of ethics canons
Code of ethics canons  Protect society, the commonwealth, and the infrastructure.
Protect society, the commonwealth, and the infrastructure. Act honorably, honestly, justly, responsibly, and legally.
Act honorably, honestly, justly, responsibly, and legally. Provide diligent and competent service to principals.
Provide diligent and competent service to principals. Advance and protect the profession.
Advance and protect the profession.
Computer Ethics Institute: 10 Commandments of Computer Ethics
![]() The Computer Ethics Institute at the Brookings Institute has formalized its code of ethics as the 10 Commandments of Computer Ethics:
The Computer Ethics Institute at the Brookings Institute has formalized its code of ethics as the 10 Commandments of Computer Ethics:
IAB Code of Ethics
![]() The IAB has issued a statement that constitutes its code of ethics as follows:
The IAB has issued a statement that constitutes its code of ethics as follows:
![]() The Internet is a national facility whose utility is largely a consequence of its wide availability and accessibility. Irresponsible use of this critical resource poses an enormous threat to its continued availability to the technical community. The U.S. government, sponsors of this system, suffers when highly disruptive abuses occur. Access to and use of the Internet is a privilege and should be treated as such by all users of this system. The IAB strongly endorses the view of the Division Advisory Panel of the National Science Foundation Division of Network, Communications Research and Infrastructure which, in paraphrase, characterized as unethical and unacceptable any activity which purposely:
The Internet is a national facility whose utility is largely a consequence of its wide availability and accessibility. Irresponsible use of this critical resource poses an enormous threat to its continued availability to the technical community. The U.S. government, sponsors of this system, suffers when highly disruptive abuses occur. Access to and use of the Internet is a privilege and should be treated as such by all users of this system. The IAB strongly endorses the view of the Division Advisory Panel of the National Science Foundation Division of Network, Communications Research and Infrastructure which, in paraphrase, characterized as unethical and unacceptable any activity which purposely:
-
 Seeks to gain unauthorized access to the resources of the Internet
Seeks to gain unauthorized access to the resources of the Internet -
 Disrupts the intended use of the Internet
Disrupts the intended use of the Internet -
 Wastes resources, such as people, capacity, and computer, through such actions
Wastes resources, such as people, capacity, and computer, through such actions -
 Destroys the integrity of computer-based information
Destroys the integrity of computer-based information -
 Compromises the privacy of users
Compromises the privacy of users
GASSP Code of Ethics
![]() The GASSP code of ethics states that information systems and the security of information systems should be provided and used in accordance with the Code of Ethical Conduct of information security professionals.
The GASSP code of ethics states that information systems and the security of information systems should be provided and used in accordance with the Code of Ethical Conduct of information security professionals.
![]() The Code of Ethical Conduct prescribes the relationships of ethics, morality, and information. As social norms for using IT systems evolve, the Code of Ethical Conduct will change, and information security professionals will spread the new concepts throughout their organizations and products. Safeguards may require an ethical judgment for use or to determine limits or controls.
The Code of Ethical Conduct prescribes the relationships of ethics, morality, and information. As social norms for using IT systems evolve, the Code of Ethical Conduct will change, and information security professionals will spread the new concepts throughout their organizations and products. Safeguards may require an ethical judgment for use or to determine limits or controls.
![]() For example, entrapment is a process for luring someone into performing an illegal or abusive act. As a security safeguard, a security professional might set up an easy-to-compromise hole in the access control system, and then monitor attempts to exploit the hole. This form of entrapment is useful in providing warning that penetration has occurred. It can also provide enough information to identify the perpetrator.
For example, entrapment is a process for luring someone into performing an illegal or abusive act. As a security safeguard, a security professional might set up an easy-to-compromise hole in the access control system, and then monitor attempts to exploit the hole. This form of entrapment is useful in providing warning that penetration has occurred. It can also provide enough information to identify the perpetrator.
![]() Due to laws, regulations, or ethical standards, it may be unethical to use data that is collected via entrapment in prosecution, but it may be ethical to use entrapment as a detection and prevention strategy. You should seek both legal and ethical advice when designing your network security.
Due to laws, regulations, or ethical standards, it may be unethical to use data that is collected via entrapment in prosecution, but it may be ethical to use entrapment as a detection and prevention strategy. You should seek both legal and ethical advice when designing your network security.
Locale-Specific Legal/Ethical Considerations
![]() Companies must take into account the legal liability for the country in which they reside. Take, for example, an Internet service provider (ISP) that has hundreds of e-businesses that rely on them to run their websites with 100 percent uptime. If a hacker or a virus takes down this ISP, there is a chance for the ISP to be found liable, if it is discovered that the ISP did not take enough precautions or did not secure the network against internal or external threats.
Companies must take into account the legal liability for the country in which they reside. Take, for example, an Internet service provider (ISP) that has hundreds of e-businesses that rely on them to run their websites with 100 percent uptime. If a hacker or a virus takes down this ISP, there is a chance for the ISP to be found liable, if it is discovered that the ISP did not take enough precautions or did not secure the network against internal or external threats.
![]() In such cases, legal liability is likely to depend on what prevention technologies and practices are available and whether these technologies and practices are reasonably cost-effective to implement.
In such cases, legal liability is likely to depend on what prevention technologies and practices are available and whether these technologies and practices are reasonably cost-effective to implement.
![]() As a result, showing due diligence includes everything from implementing technologies such as firewalls, intrusion-detection tools, content filters, traffic analyzers, and VPNs, to having best practices for continuous risk-assessment and vulnerability testing.
As a result, showing due diligence includes everything from implementing technologies such as firewalls, intrusion-detection tools, content filters, traffic analyzers, and VPNs, to having best practices for continuous risk-assessment and vulnerability testing.
![]() Due care is concerned with the operations and maintenance of the secure mechanisms put in place by practicing due diligence.
Due care is concerned with the operations and maintenance of the secure mechanisms put in place by practicing due diligence.
![]() Many U.S. government regulations have emerged to heighten the need for network and system security. The Gramm-Leach-Bliley Act (GLBA) of 1999 erased long-standing antitrust laws that prohibited banks, insurance companies, and securities firms from merging and sharing information with one another. The idea was that smaller firms would then be able to pursue acquisitions or alliances or both that would help drive competition against many of the larger financial institutions. Included in the GLBA were several consumer-privacy protections. Namely, companies must tell their customers what kinds of data they plan to share and with whom, and they must give their customers a chance to opt out of that data sharing.
Many U.S. government regulations have emerged to heighten the need for network and system security. The Gramm-Leach-Bliley Act (GLBA) of 1999 erased long-standing antitrust laws that prohibited banks, insurance companies, and securities firms from merging and sharing information with one another. The idea was that smaller firms would then be able to pursue acquisitions or alliances or both that would help drive competition against many of the larger financial institutions. Included in the GLBA were several consumer-privacy protections. Namely, companies must tell their customers what kinds of data they plan to share and with whom, and they must give their customers a chance to opt out of that data sharing.
![]() On the healthcare side, the Health Insurance Portability and Accountability Act (HIPAA) of 2000 requires the U.S. Department of Health and Human Services to develop a set of national standards for healthcare transactions and provide assurance that the electronic transfer of confidential patient information will be as safe as, or safer, than paper-based patient records.
On the healthcare side, the Health Insurance Portability and Accountability Act (HIPAA) of 2000 requires the U.S. Department of Health and Human Services to develop a set of national standards for healthcare transactions and provide assurance that the electronic transfer of confidential patient information will be as safe as, or safer, than paper-based patient records.
![]() The Sarbanes-Oxley (SOX) Act of 2002 is a U.S. law in response to a number of major corporate and accounting scandals, including those affecting Enron, Tyco International, Peregrine Systems, and WorldCom. These scandals resulted in a decline of public trust in accounting and reporting practices.
The Sarbanes-Oxley (SOX) Act of 2002 is a U.S. law in response to a number of major corporate and accounting scandals, including those affecting Enron, Tyco International, Peregrine Systems, and WorldCom. These scandals resulted in a decline of public trust in accounting and reporting practices.
![]() The Security and Freedom through Encryption Act provides that people in the United States can use any kind of encryption. It also provides that any person in the United States can sell any encryption product within the United States. Furthermore, the U.S. government cannot mandate any kind of key escrow. The bulk of the 17-page bill deals with the export of encryption products.
The Security and Freedom through Encryption Act provides that people in the United States can use any kind of encryption. It also provides that any person in the United States can sell any encryption product within the United States. Furthermore, the U.S. government cannot mandate any kind of key escrow. The bulk of the 17-page bill deals with the export of encryption products.
| Note |
|
![]() The U.S. Congress originally passed the Computer Fraud and Abuse Act in 1986 with the intention of reducing hacking. It was amended in 1994, 1996, and lastly in 2001 by the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) Act. The USA PATRIOT Act expired on December 31, 2005, but was amended and reauthorized in March 2006.
The U.S. Congress originally passed the Computer Fraud and Abuse Act in 1986 with the intention of reducing hacking. It was amended in 1994, 1996, and lastly in 2001 by the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) Act. The USA PATRIOT Act expired on December 31, 2005, but was amended and reauthorized in March 2006.
![]() The USA PATRIOT Act increases the scope and penalties of this act by doing the following:
The USA PATRIOT Act increases the scope and penalties of this act by doing the following:
-
 Raises the maximum penalty for violations to 10 years for a first offense and 20 years for a second offense
Raises the maximum penalty for violations to 10 years for a first offense and 20 years for a second offense -
 Ensures that violators need only to intend to cause damage and that damage was greater than $5000
Ensures that violators need only to intend to cause damage and that damage was greater than $5000 -
 Enhances punishment for violations that involve any damage to a government computer that is involved in criminal justice or the military
Enhances punishment for violations that involve any damage to a government computer that is involved in criminal justice or the military -
 Includes damage to foreign computers that are involved in U.S. interstate commerce
Includes damage to foreign computers that are involved in U.S. interstate commerce -
 Includes state law offenses as priors for sentencing
Includes state law offenses as priors for sentencing -
 Expands the definition of loss to expressly include time spent investigating and responding to attacks, making damage assessment and restoration important
Expands the definition of loss to expressly include time spent investigating and responding to attacks, making damage assessment and restoration important
![]() The U.S. Congress passed the Privacy Act of 1974 following revelations about the abuse of privacy during the administration of President Richard Nixon. It requires that the privacy of individuals be respected unless they consent to the release of their information in writing.
The U.S. Congress passed the Privacy Act of 1974 following revelations about the abuse of privacy during the administration of President Richard Nixon. It requires that the privacy of individuals be respected unless they consent to the release of their information in writing.
| Note |
|
![]() The Federal Information Security Management Act (FISMA) of 2002 was intended to bolster computer and network security within the U.S. government and affiliated parties by requiring yearly audits. FISMA also brought attention within the U.S. government to cyber security, which the U.S. government had largely neglected previously.
The Federal Information Security Management Act (FISMA) of 2002 was intended to bolster computer and network security within the U.S. government and affiliated parties by requiring yearly audits. FISMA also brought attention within the U.S. government to cyber security, which the U.S. government had largely neglected previously.
![]() The Economic Espionage Act of 1996 makes it a federal crime to misuse trade secrets. This law is intended to address corporate espionage, which is a huge security problem for companies with large R&D budgets.
The Economic Espionage Act of 1996 makes it a federal crime to misuse trade secrets. This law is intended to address corporate espionage, which is a huge security problem for companies with large R&D budgets.
![]() Jurisdictional problems have plagued the prosecution of computer crimes for years. Attackers would simply launch their attacks from compromised computers in one country against computers in another country. It was most effective when the two countries in question had political difficulties. In response to these jurisdictional problems, cooperative efforts have started among the countries of the world. You can find examples of international cooperation in the sharing of law enforcement information in the G8, Interpol, and European Union, among others.
Jurisdictional problems have plagued the prosecution of computer crimes for years. Attackers would simply launch their attacks from compromised computers in one country against computers in another country. It was most effective when the two countries in question had political difficulties. In response to these jurisdictional problems, cooperative efforts have started among the countries of the world. You can find examples of international cooperation in the sharing of law enforcement information in the G8, Interpol, and European Union, among others.

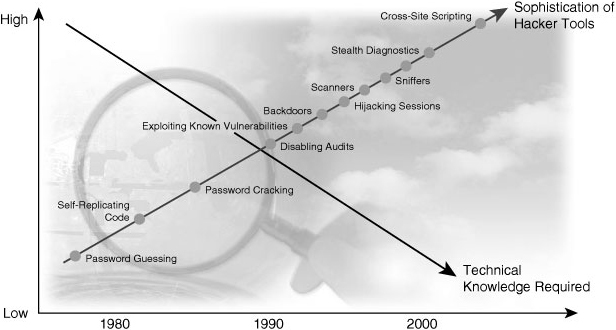
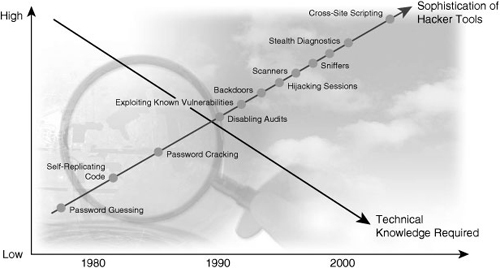
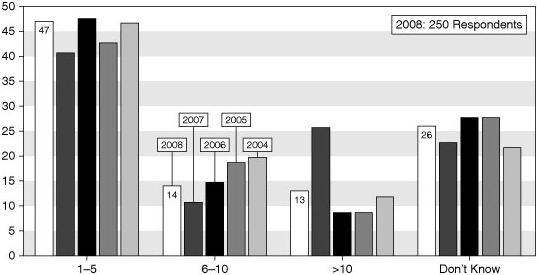
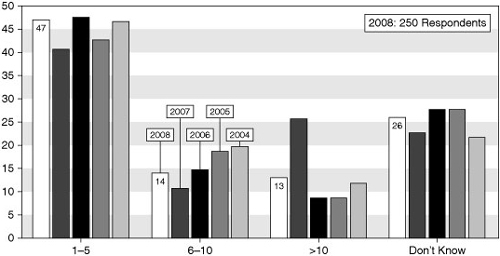
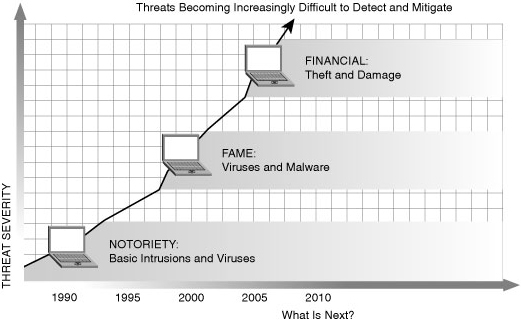
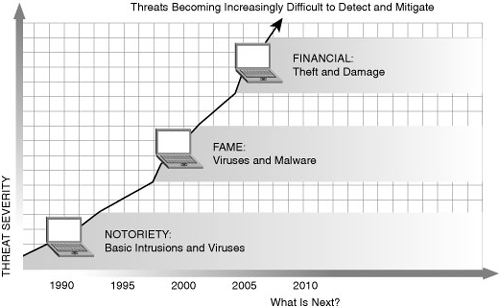
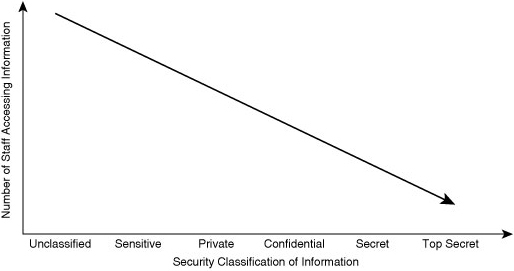
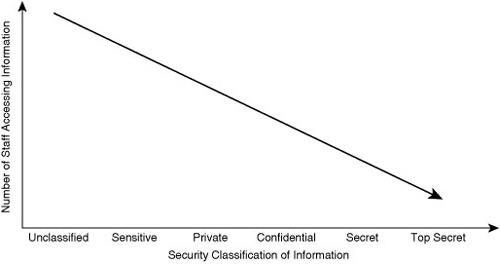
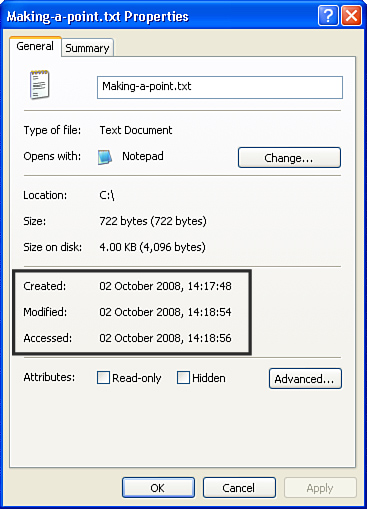
1 comments
Thanks for this helpful information I agree with all points you have given to us.Please visit once at http://www.qosnetworking.com/
Post a Comment